M2M Solutions Network Design Report - University Assignment
VerifiedAdded on 2020/03/04
|12
|2286
|174
Report
AI Summary
This report presents a comprehensive network design for M2M Solutions, focusing on the implementation of a Transmission Control Protocol/Internet Protocol (TCP/IP) network across multiple sites. The design utilizes a private IP address scheme (10.0.0.0) with Variable Length Subnet Masks (VLSMs) to optimize IP address allocation across various departments, including Information Technology, Finance, Transport, Research, Head Office, and Sales. The report details the IP addressing requirements for each department, considering the number of workstations and potential growth, and illustrates the network topology with diagrams. Furthermore, the report explores the role of network analyzers, particularly Wireshark, in troubleshooting and monitoring the network's performance and security. The analysis highlights the importance of network analyzers in diagnosing issues, detecting intrusions, and verifying changes within the network, providing a valuable tool for network administrators.

Running header: M2M SOLUTIONS NETWORK DESIGN REPORT
1
M2M SOLUTIONS NETWORK DESIGN REPORT
1
M2M SOLUTIONS NETWORK DESIGN REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
M2M SOLUTIONS NETWORK DESIGN REPORT
Executive summary
M2M will be well suited by a Transmission Control Protocol/Internet Protocol. The network will
be well coordinated with six routers, one at each of the five sites across Sydney and one at the
head office. The network designed will utilize the 10.0.0.0 private Internet Protocol Address. All
the departments in their respective sites will have a subnet that connects with the one in the Head
office. The subnets will still utilize the 10.0.0.0 private Internet Protocol address and therefore all
the information and data will be sent out of the subnet only after Network Address Translation
(Postel, January 1980). The subnetworks will consist of Switches and Access Points to enable all
the workstations connect to the router. The number of switches and Access points in every
subnet will depend on the total number of workstations expected and the span of the department.
Some departments may have all the users in a workstation centered at one location where an
access point could serve them all while other departments may be having users in a workstation
spread such that an access point will not fit many of them. The IP addressing under class A will
be done in a manner that will account for all the current workstations and give room for more as
the company may continue to grow (Comer, 2000). The IP addresses given to a workstation will
not be so much wasteful of the available IP addresses.
M2M SOLUTIONS NETWORK DESIGN REPORT
Executive summary
M2M will be well suited by a Transmission Control Protocol/Internet Protocol. The network will
be well coordinated with six routers, one at each of the five sites across Sydney and one at the
head office. The network designed will utilize the 10.0.0.0 private Internet Protocol Address. All
the departments in their respective sites will have a subnet that connects with the one in the Head
office. The subnets will still utilize the 10.0.0.0 private Internet Protocol address and therefore all
the information and data will be sent out of the subnet only after Network Address Translation
(Postel, January 1980). The subnetworks will consist of Switches and Access Points to enable all
the workstations connect to the router. The number of switches and Access points in every
subnet will depend on the total number of workstations expected and the span of the department.
Some departments may have all the users in a workstation centered at one location where an
access point could serve them all while other departments may be having users in a workstation
spread such that an access point will not fit many of them. The IP addressing under class A will
be done in a manner that will account for all the current workstations and give room for more as
the company may continue to grow (Comer, 2000). The IP addresses given to a workstation will
not be so much wasteful of the available IP addresses.
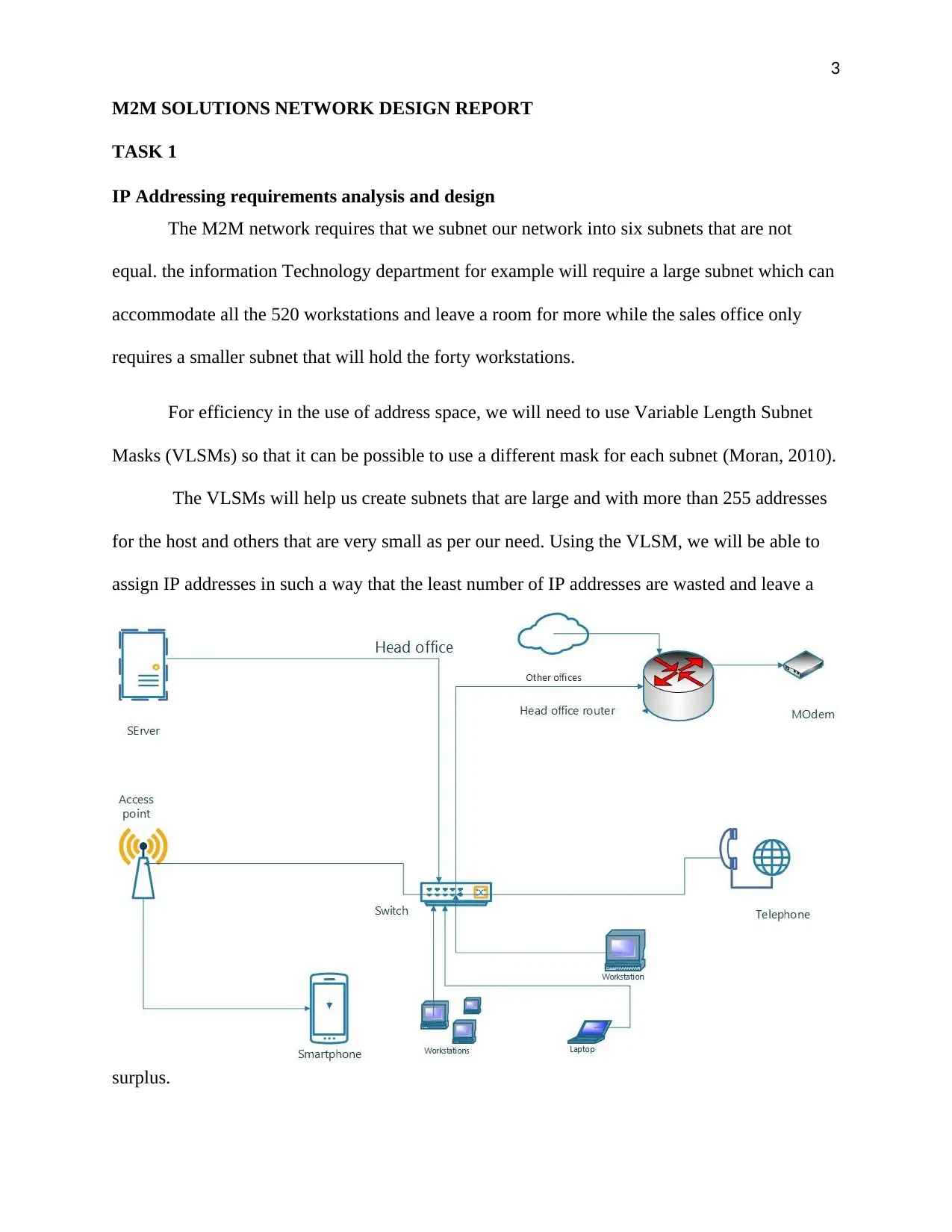
3
M2M SOLUTIONS NETWORK DESIGN REPORT
TASK 1
IP Addressing requirements analysis and design
The M2M network requires that we subnet our network into six subnets that are not
equal. the information Technology department for example will require a large subnet which can
accommodate all the 520 workstations and leave a room for more while the sales office only
requires a smaller subnet that will hold the forty workstations.
For efficiency in the use of address space, we will need to use Variable Length Subnet
Masks (VLSMs) so that it can be possible to use a different mask for each subnet (Moran, 2010).
The VLSMs will help us create subnets that are large and with more than 255 addresses
for the host and others that are very small as per our need. Using the VLSM, we will be able to
assign IP addresses in such a way that the least number of IP addresses are wasted and leave a
surplus.
M2M SOLUTIONS NETWORK DESIGN REPORT
TASK 1
IP Addressing requirements analysis and design
The M2M network requires that we subnet our network into six subnets that are not
equal. the information Technology department for example will require a large subnet which can
accommodate all the 520 workstations and leave a room for more while the sales office only
requires a smaller subnet that will hold the forty workstations.
For efficiency in the use of address space, we will need to use Variable Length Subnet
Masks (VLSMs) so that it can be possible to use a different mask for each subnet (Moran, 2010).
The VLSMs will help us create subnets that are large and with more than 255 addresses
for the host and others that are very small as per our need. Using the VLSM, we will be able to
assign IP addresses in such a way that the least number of IP addresses are wasted and leave a
surplus.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
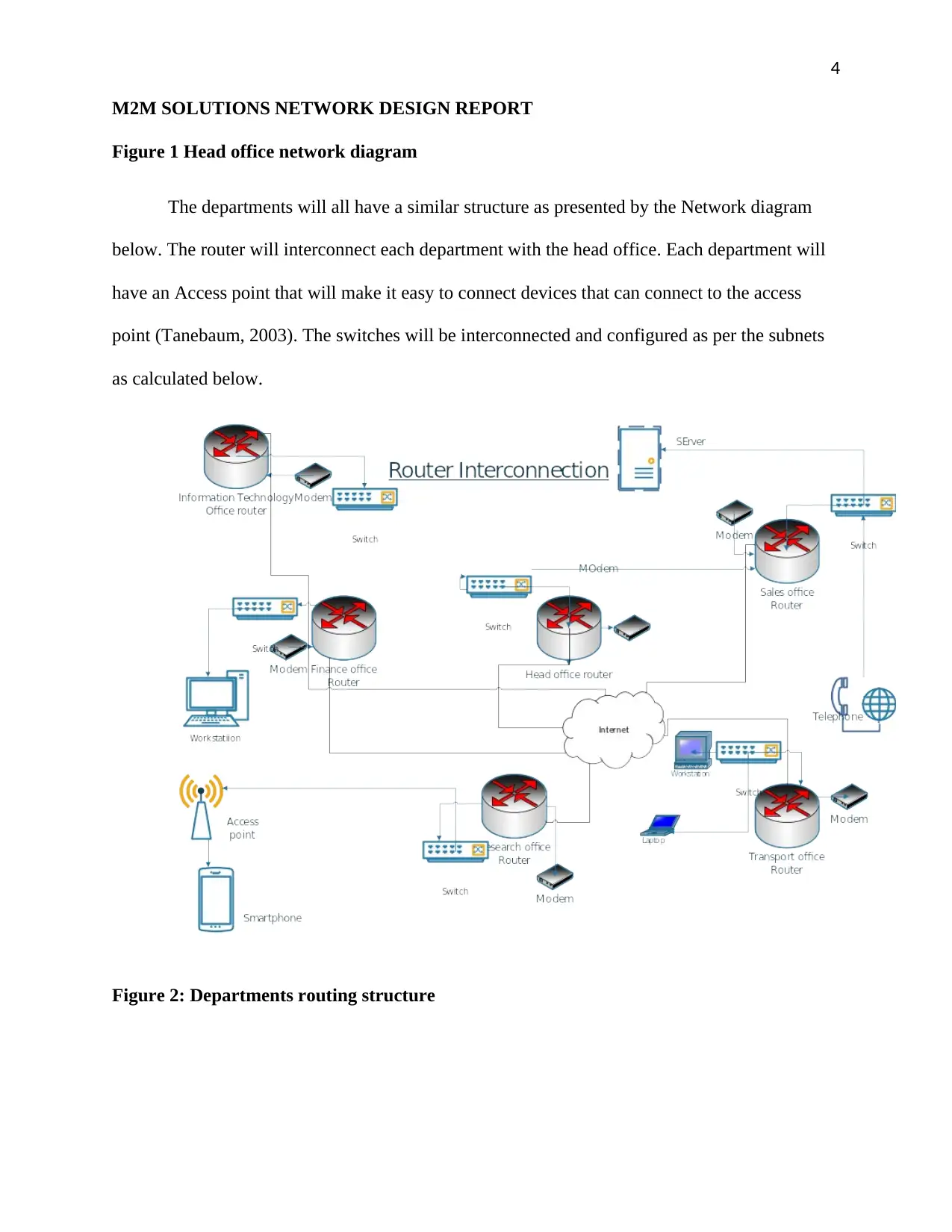
4
M2M SOLUTIONS NETWORK DESIGN REPORT
Figure 1 Head office network diagram
The departments will all have a similar structure as presented by the Network diagram
below. The router will interconnect each department with the head office. Each department will
have an Access point that will make it easy to connect devices that can connect to the access
point (Tanebaum, 2003). The switches will be interconnected and configured as per the subnets
as calculated below.
Figure 2: Departments routing structure
M2M SOLUTIONS NETWORK DESIGN REPORT
Figure 1 Head office network diagram
The departments will all have a similar structure as presented by the Network diagram
below. The router will interconnect each department with the head office. Each department will
have an Access point that will make it easy to connect devices that can connect to the access
point (Tanebaum, 2003). The switches will be interconnected and configured as per the subnets
as calculated below.
Figure 2: Departments routing structure
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
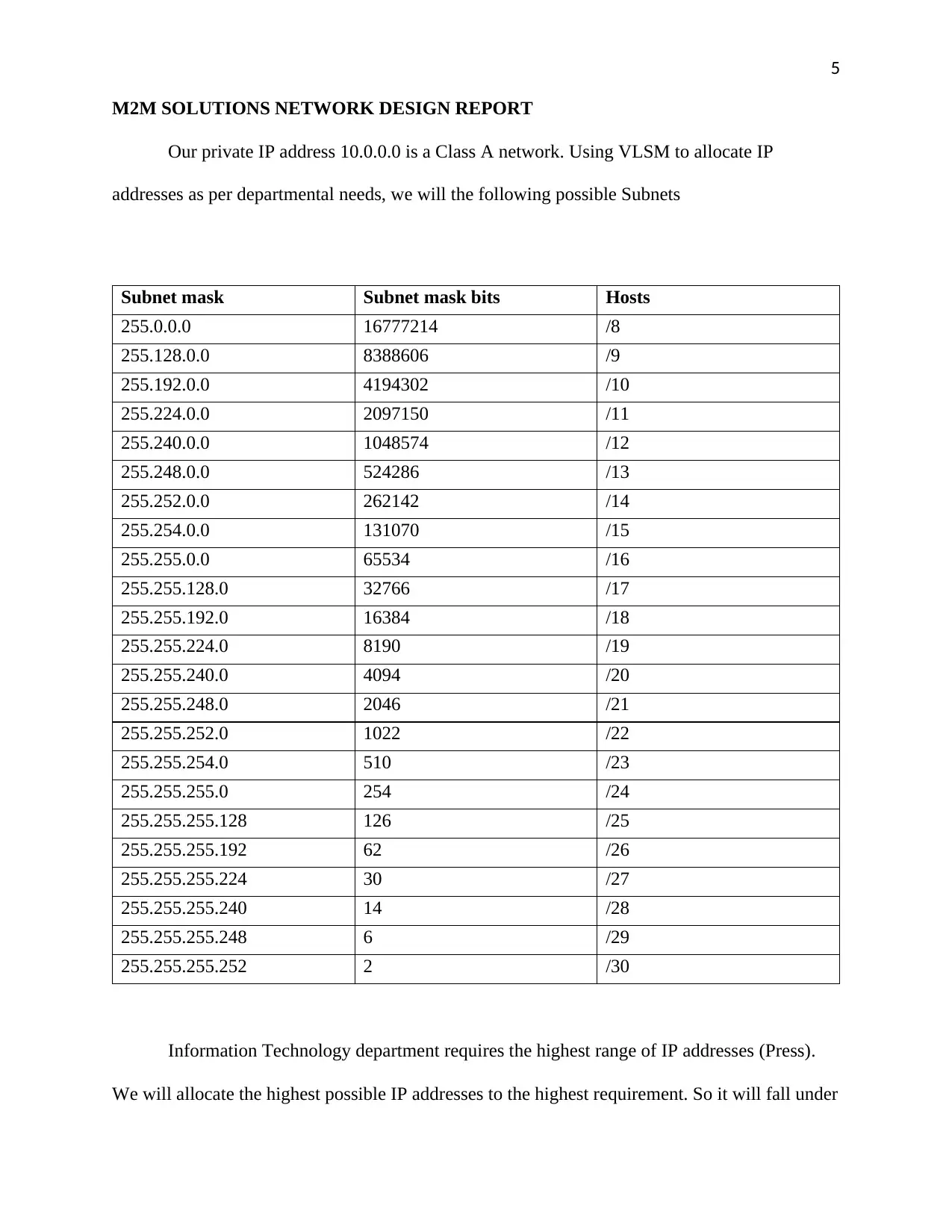
5
M2M SOLUTIONS NETWORK DESIGN REPORT
Our private IP address 10.0.0.0 is a Class A network. Using VLSM to allocate IP
addresses as per departmental needs, we will the following possible Subnets
Subnet mask Subnet mask bits Hosts
255.0.0.0 16777214 /8
255.128.0.0 8388606 /9
255.192.0.0 4194302 /10
255.224.0.0 2097150 /11
255.240.0.0 1048574 /12
255.248.0.0 524286 /13
255.252.0.0 262142 /14
255.254.0.0 131070 /15
255.255.0.0 65534 /16
255.255.128.0 32766 /17
255.255.192.0 16384 /18
255.255.224.0 8190 /19
255.255.240.0 4094 /20
255.255.248.0 2046 /21
255.255.252.0 1022 /22
255.255.254.0 510 /23
255.255.255.0 254 /24
255.255.255.128 126 /25
255.255.255.192 62 /26
255.255.255.224 30 /27
255.255.255.240 14 /28
255.255.255.248 6 /29
255.255.255.252 2 /30
Information Technology department requires the highest range of IP addresses (Press).
We will allocate the highest possible IP addresses to the highest requirement. So it will fall under
M2M SOLUTIONS NETWORK DESIGN REPORT
Our private IP address 10.0.0.0 is a Class A network. Using VLSM to allocate IP
addresses as per departmental needs, we will the following possible Subnets
Subnet mask Subnet mask bits Hosts
255.0.0.0 16777214 /8
255.128.0.0 8388606 /9
255.192.0.0 4194302 /10
255.224.0.0 2097150 /11
255.240.0.0 1048574 /12
255.248.0.0 524286 /13
255.252.0.0 262142 /14
255.254.0.0 131070 /15
255.255.0.0 65534 /16
255.255.128.0 32766 /17
255.255.192.0 16384 /18
255.255.224.0 8190 /19
255.255.240.0 4094 /20
255.255.248.0 2046 /21
255.255.252.0 1022 /22
255.255.254.0 510 /23
255.255.255.0 254 /24
255.255.255.128 126 /25
255.255.255.192 62 /26
255.255.255.224 30 /27
255.255.255.240 14 /28
255.255.255.248 6 /29
255.255.255.252 2 /30
Information Technology department requires the highest range of IP addresses (Press).
We will allocate the highest possible IP addresses to the highest requirement. So it will fall under

6
M2M SOLUTIONS NETWORK DESIGN REPORT
subnet mask 255.255.252.0 which will be 10.0.0.0/22. Its start IP address will be 10.0.0.1 and
end IP address will be 10.0.3.254 (Mogul & J., August 1985).
Finance office will be the second in the order of highest IP address requirement with a
subnet mask of 255.255.254.0 which will be the IP addresses with 10.0.0.0/23. The finance
office’s Start Host IP address will be 10.0.0.1 and end IP address will be 10.0.1.254
Transport office will be the third in requirements for IP address and will have a subnet
mask of 255.255.255.0 and will have IP addresses with 10.0.0.0/24. The start IP address will be
10.0.0.1 and the end IP address will be 10.0.0.254
Research office has an approximate of 120 workstations and will therefore fall in subnet
mask 255.255.255.128 which will have and IP address with 25 subnet mask bits, 10.0.0.0/25.
The start IP will be 10.0.0.1 and the end IP will be 10.0.0.126
Head office is the second last with an approximate of sixty work stations. It will have the
subnet mask of 255.255.255.192 with an IP address having twenty-six subnet mask bits,
10.0.0.0/26. The start IP address will be 10.0.0.1 and the end IP address will be 10.0.0.62
The sales office will require the least number of hosts with an approximate workstation
count of 40. It will use the subnet mask of 255.255.255.192. The sales office will have an IP
address with 26 subnet mask bits too, 10.0.0.0/26. The start IP will be 10.0.0.1 and the end IP
will be 10.0.0.62.
All the addressing solution leaves room for growth in each department and makes sure
the wasted IP addresses are minimal (Institute). The research office with an approximate of 120
M2M SOLUTIONS NETWORK DESIGN REPORT
subnet mask 255.255.252.0 which will be 10.0.0.0/22. Its start IP address will be 10.0.0.1 and
end IP address will be 10.0.3.254 (Mogul & J., August 1985).
Finance office will be the second in the order of highest IP address requirement with a
subnet mask of 255.255.254.0 which will be the IP addresses with 10.0.0.0/23. The finance
office’s Start Host IP address will be 10.0.0.1 and end IP address will be 10.0.1.254
Transport office will be the third in requirements for IP address and will have a subnet
mask of 255.255.255.0 and will have IP addresses with 10.0.0.0/24. The start IP address will be
10.0.0.1 and the end IP address will be 10.0.0.254
Research office has an approximate of 120 workstations and will therefore fall in subnet
mask 255.255.255.128 which will have and IP address with 25 subnet mask bits, 10.0.0.0/25.
The start IP will be 10.0.0.1 and the end IP will be 10.0.0.126
Head office is the second last with an approximate of sixty work stations. It will have the
subnet mask of 255.255.255.192 with an IP address having twenty-six subnet mask bits,
10.0.0.0/26. The start IP address will be 10.0.0.1 and the end IP address will be 10.0.0.62
The sales office will require the least number of hosts with an approximate workstation
count of 40. It will use the subnet mask of 255.255.255.192. The sales office will have an IP
address with 26 subnet mask bits too, 10.0.0.0/26. The start IP will be 10.0.0.1 and the end IP
will be 10.0.0.62.
All the addressing solution leaves room for growth in each department and makes sure
the wasted IP addresses are minimal (Institute). The research office with an approximate of 120
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
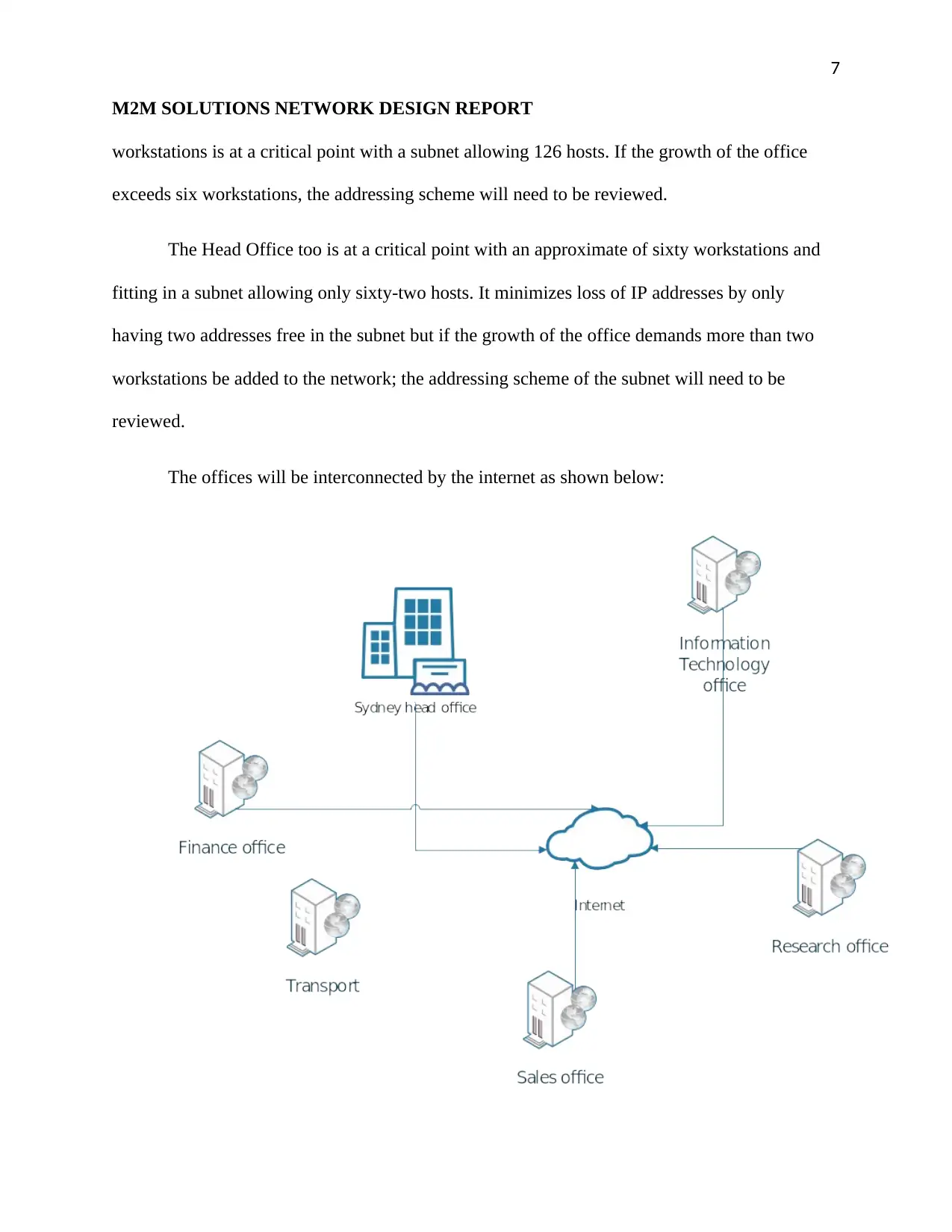
7
M2M SOLUTIONS NETWORK DESIGN REPORT
workstations is at a critical point with a subnet allowing 126 hosts. If the growth of the office
exceeds six workstations, the addressing scheme will need to be reviewed.
The Head Office too is at a critical point with an approximate of sixty workstations and
fitting in a subnet allowing only sixty-two hosts. It minimizes loss of IP addresses by only
having two addresses free in the subnet but if the growth of the office demands more than two
workstations be added to the network; the addressing scheme of the subnet will need to be
reviewed.
The offices will be interconnected by the internet as shown below:
M2M SOLUTIONS NETWORK DESIGN REPORT
workstations is at a critical point with a subnet allowing 126 hosts. If the growth of the office
exceeds six workstations, the addressing scheme will need to be reviewed.
The Head Office too is at a critical point with an approximate of sixty workstations and
fitting in a subnet allowing only sixty-two hosts. It minimizes loss of IP addresses by only
having two addresses free in the subnet but if the growth of the office demands more than two
workstations be added to the network; the addressing scheme of the subnet will need to be
reviewed.
The offices will be interconnected by the internet as shown below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
M2M SOLUTIONS NETWORK DESIGN REPORT
Figure 3: Offices Interconnection
The simple Variable Length Subnet Mask addressing solution works best for these
subnets since there are some that are very large with more than the normal 255 host addresses
like the Information Technology subnet and need to be addressed in a way that will allow future
growth if the department continues to grow or have more staff and workstations. There is also a
great need for very small subnets that would otherwise mean a very huge loss of addresses. With
the method, only a few addresses are lost which give the room for growth.
TASK 2
Network analysers and their efficiency in troubleshooting processes
Networks need a close checkup often to ensure they are working correctly and that every
device or workstation connected never loses connection (Press., 2004). It is also important to
keep an eye on the security of the network to ensure no intruder gets access to any information
and no workstation gets information they are not supposed to get. A network administrator is
responsible of giving a timely report on the efficiency of the network. However, if a network is
continually growing and getting bigger, it gets hard for the administrators to diagnose the
network and detect any configurational or operational issues early enough before their effects
(Dye, McDonald, & Rufi, 2007).
Roles of network analysers
Network analysers can play a very crucial role in assisting the administrator for
diagnostic and troubleshooting purposes (Cerf, A protocol for Packet Network
Intercommunication., 1974). The administrator will have an easy time trouble shooting the
M2M SOLUTIONS NETWORK DESIGN REPORT
Figure 3: Offices Interconnection
The simple Variable Length Subnet Mask addressing solution works best for these
subnets since there are some that are very large with more than the normal 255 host addresses
like the Information Technology subnet and need to be addressed in a way that will allow future
growth if the department continues to grow or have more staff and workstations. There is also a
great need for very small subnets that would otherwise mean a very huge loss of addresses. With
the method, only a few addresses are lost which give the room for growth.
TASK 2
Network analysers and their efficiency in troubleshooting processes
Networks need a close checkup often to ensure they are working correctly and that every
device or workstation connected never loses connection (Press., 2004). It is also important to
keep an eye on the security of the network to ensure no intruder gets access to any information
and no workstation gets information they are not supposed to get. A network administrator is
responsible of giving a timely report on the efficiency of the network. However, if a network is
continually growing and getting bigger, it gets hard for the administrators to diagnose the
network and detect any configurational or operational issues early enough before their effects
(Dye, McDonald, & Rufi, 2007).
Roles of network analysers
Network analysers can play a very crucial role in assisting the administrator for
diagnostic and troubleshooting purposes (Cerf, A protocol for Packet Network
Intercommunication., 1974). The administrator will have an easy time trouble shooting the

9
M2M SOLUTIONS NETWORK DESIGN REPORT
network when a diagnosis is ready what happened to the network than doing the diagnosis
himself especially for our M2M company that is continually growing bigger and the networking
getting larger and harder to do a manual diagnosis.
The network analysers will provide a data source for all monitoring and management of
our network. This is because of their ease in monitoring Wide Area Networks and the security of
endpoints and continuous update of the network status and statistics. By having a continuous
status update of the network, the analyser will be able to automatically deduce any arising
problem when any workstation fails to broadcast their statistics (Abbate, 2000). It will also be
possible detect an intruder as early as they attempt and detect any inappropriate use of the
network by all the staff.
The network analyser will aid in monitoring all the data packet being sent and received
by the nodes and therefore make it possible to filter and block any suspected contents from our
network (Cerf, The introduction of packet satellite communication, 1979). They will also be used
for verification of any changes that occur in the network, and deduce whether they happened
with awareness of the administrators and for the right purposes. It will also be possible to check
on usefulness and working of filters and other fitted internal control systems such as proxies and
firewalls.
Need for network analysers in M2M
Our network will therefore be better placed if a network analyser is considered. Our
network has grown to having six subnets and all are using a private network addressing protocol.
It is important to therefore have a central way of diagnosing our network problem and
troubleshoot with ease (C., 2016). The network administrator working without a network
M2M SOLUTIONS NETWORK DESIGN REPORT
network when a diagnosis is ready what happened to the network than doing the diagnosis
himself especially for our M2M company that is continually growing bigger and the networking
getting larger and harder to do a manual diagnosis.
The network analysers will provide a data source for all monitoring and management of
our network. This is because of their ease in monitoring Wide Area Networks and the security of
endpoints and continuous update of the network status and statistics. By having a continuous
status update of the network, the analyser will be able to automatically deduce any arising
problem when any workstation fails to broadcast their statistics (Abbate, 2000). It will also be
possible detect an intruder as early as they attempt and detect any inappropriate use of the
network by all the staff.
The network analyser will aid in monitoring all the data packet being sent and received
by the nodes and therefore make it possible to filter and block any suspected contents from our
network (Cerf, The introduction of packet satellite communication, 1979). They will also be used
for verification of any changes that occur in the network, and deduce whether they happened
with awareness of the administrators and for the right purposes. It will also be possible to check
on usefulness and working of filters and other fitted internal control systems such as proxies and
firewalls.
Need for network analysers in M2M
Our network will therefore be better placed if a network analyser is considered. Our
network has grown to having six subnets and all are using a private network addressing protocol.
It is important to therefore have a central way of diagnosing our network problem and
troubleshoot with ease (C., 2016). The network administrator working without a network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
M2M SOLUTIONS NETWORK DESIGN REPORT
analyser will have a hard time detecting an intrusion in the Information Technology department
when working in the head office or tell the possible problem that occurred to a server in the head
office when he was at the sales office without having a network analyser that kept monitoring the
server.
Network analyser tools analysis
There are many network analyser tools by different software developers and vendors.
Their main differences are on how each intercepts and logs traffic on the network (James F.
Kurose, 2008). Wireshark is one of the network analysers. Wireshark uses a disk to save a
captured file and stores the data in a network which a user can freely browse and see the logs. It
works in both Unix and Windows based machines.
Wireshark will be our best network analyser to choose since unlike other network
analysers, it can view Transmission Control Protocol session streams across many media types
and many protocols. Many other network analysers are based on consoles while in Wireshark,
the console is an inclusion.
M2M SOLUTIONS NETWORK DESIGN REPORT
analyser will have a hard time detecting an intrusion in the Information Technology department
when working in the head office or tell the possible problem that occurred to a server in the head
office when he was at the sales office without having a network analyser that kept monitoring the
server.
Network analyser tools analysis
There are many network analyser tools by different software developers and vendors.
Their main differences are on how each intercepts and logs traffic on the network (James F.
Kurose, 2008). Wireshark is one of the network analysers. Wireshark uses a disk to save a
captured file and stores the data in a network which a user can freely browse and see the logs. It
works in both Unix and Windows based machines.
Wireshark will be our best network analyser to choose since unlike other network
analysers, it can view Transmission Control Protocol session streams across many media types
and many protocols. Many other network analysers are based on consoles while in Wireshark,
the console is an inclusion.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
M2M SOLUTIONS NETWORK DESIGN REPORT
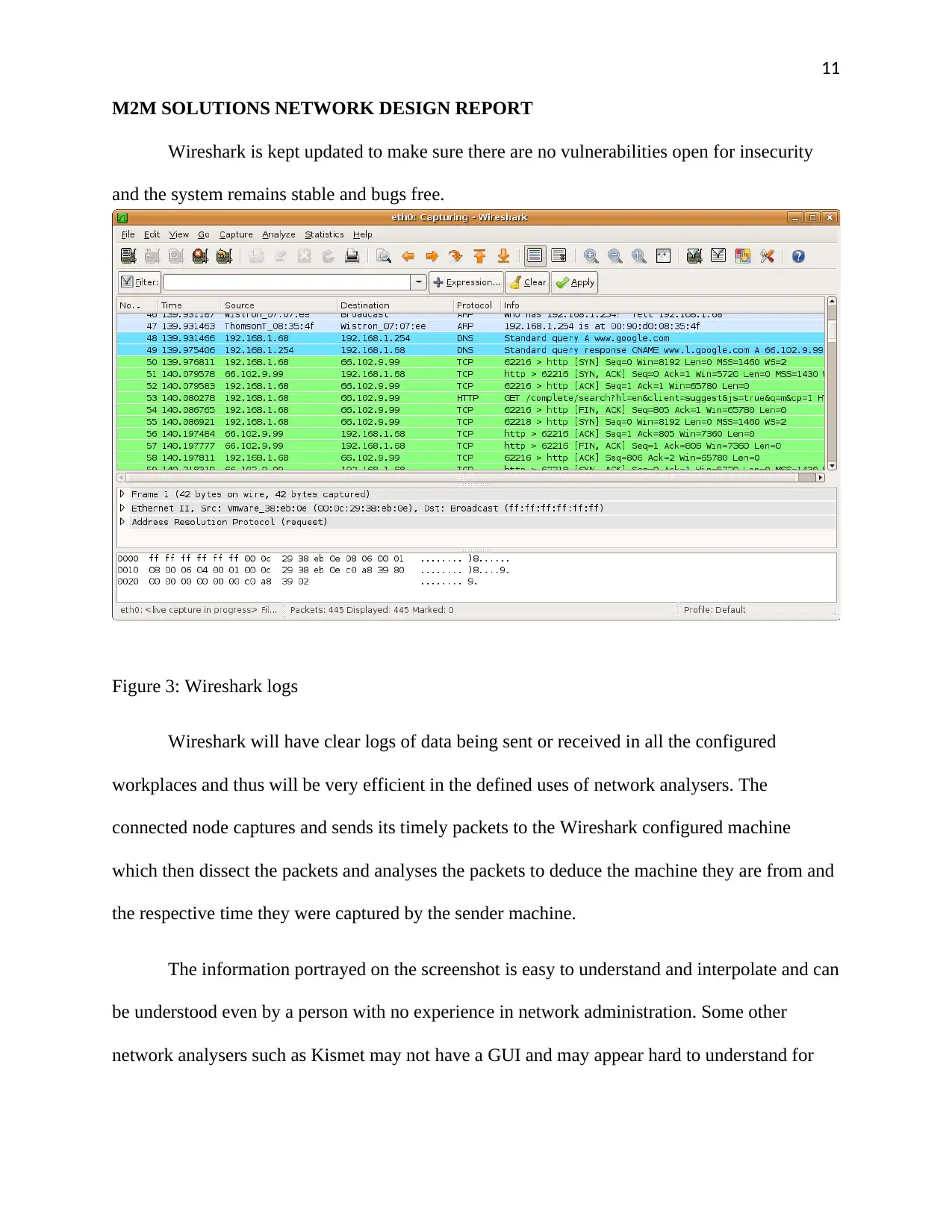
Wireshark is kept updated to make sure there are no vulnerabilities open for insecurity
and the system remains stable and bugs free.
Figure 3: Wireshark logs
Wireshark will have clear logs of data being sent or received in all the configured
workplaces and thus will be very efficient in the defined uses of network analysers. The
connected node captures and sends its timely packets to the Wireshark configured machine
which then dissect the packets and analyses the packets to deduce the machine they are from and
the respective time they were captured by the sender machine.
The information portrayed on the screenshot is easy to understand and interpolate and can
be understood even by a person with no experience in network administration. Some other
network analysers such as Kismet may not have a GUI and may appear hard to understand for
M2M SOLUTIONS NETWORK DESIGN REPORT
Wireshark is kept updated to make sure there are no vulnerabilities open for insecurity
and the system remains stable and bugs free.
Figure 3: Wireshark logs
Wireshark will have clear logs of data being sent or received in all the configured
workplaces and thus will be very efficient in the defined uses of network analysers. The
connected node captures and sends its timely packets to the Wireshark configured machine
which then dissect the packets and analyses the packets to deduce the machine they are from and
the respective time they were captured by the sender machine.
The information portrayed on the screenshot is easy to understand and interpolate and can
be understood even by a person with no experience in network administration. Some other
network analysers such as Kismet may not have a GUI and may appear hard to understand for

12
M2M SOLUTIONS NETWORK DESIGN REPORT
persons with no networking knowledge. Wireshark is also open source and therefore is free of
charge and updates may be easier to acquire.
References
Abbate, J. (2000). Inventing the Internet. Cambridge: MIT Press.
C., S. (2016). Network Security Architectures.
Cerf, V. G. (1974). A protocol for Packet Network Intercommunication.
Cerf, V. G. (1979). The introduction of packet satellite communication.
Comer, D. (2000). Internetworking with TCP/IP Principles, protocols and architectures.
Dye, M., McDonald, R., & Rufi, A. (2007). Network Fundamentals, CCNA Exploration Companion
guide. Cisco Press.
Institute, I. S. (n.d.). Internet Protocol. Internet Program Protocol Specification. Retrieved from
www.tools.ietf.org/html/frc791#page-7
James F. Kurose, K. W. (2008). Computer Networking.
Mogul, J., & J., P. (August 1985). Internet Standard Subnetting Procedure.
Moran, J. (2010, September 1). Understanding and resolving IP Address conflict. Retrieved from
www.webopedia.com
Postel, J. (January 1980). Model of Operation. In I. S. Institute, DOD Standard Internet (p. 5).
Marina del Rey, California: University of California.
Press, C. (n.d.). IP addressing guide. . Retrieved from
www.cisco.com/web/about/ciscoitatwork/downloads/ciscoitatwork/pdf/
Cisco_IT_IP_Addressing_Best_Practices.pdf
Press., C. (2004). Network Security Architectures. General Design Considerations for Secure
Networks.
M2M SOLUTIONS NETWORK DESIGN REPORT
persons with no networking knowledge. Wireshark is also open source and therefore is free of
charge and updates may be easier to acquire.
References
Abbate, J. (2000). Inventing the Internet. Cambridge: MIT Press.
C., S. (2016). Network Security Architectures.
Cerf, V. G. (1974). A protocol for Packet Network Intercommunication.
Cerf, V. G. (1979). The introduction of packet satellite communication.
Comer, D. (2000). Internetworking with TCP/IP Principles, protocols and architectures.
Dye, M., McDonald, R., & Rufi, A. (2007). Network Fundamentals, CCNA Exploration Companion
guide. Cisco Press.
Institute, I. S. (n.d.). Internet Protocol. Internet Program Protocol Specification. Retrieved from
www.tools.ietf.org/html/frc791#page-7
James F. Kurose, K. W. (2008). Computer Networking.
Mogul, J., & J., P. (August 1985). Internet Standard Subnetting Procedure.
Moran, J. (2010, September 1). Understanding and resolving IP Address conflict. Retrieved from
www.webopedia.com
Postel, J. (January 1980). Model of Operation. In I. S. Institute, DOD Standard Internet (p. 5).
Marina del Rey, California: University of California.
Press, C. (n.d.). IP addressing guide. . Retrieved from
www.cisco.com/web/about/ciscoitatwork/downloads/ciscoitatwork/pdf/
Cisco_IT_IP_Addressing_Best_Practices.pdf
Press., C. (2004). Network Security Architectures. General Design Considerations for Secure
Networks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





