Forensic Analysis Report: M57 Jean Laptop Data Leakage Investigation
VerifiedAdded on 2020/04/21
|15
|4700
|348
Report
AI Summary
This report details a digital forensic investigation of a laptop belonging to M57's Jean, focusing on potential data leakage. The analysis covers the forensic process, from identification and preservation to collection, imaging, examination, and analysis. The report examines the hard drive's structure and performance, the forensic tools used (including Sleuthkit), and the investigation process, including data recovery and Windows registry analysis. The investigator sought to determine if security audits were enabled and examined Windows Shellbags. The report also includes investigator information, case description, and forensic tool statistics, culminating in findings related to user communications and system configuration. The goal was to identify evidence related to data leakage and unauthorized activities, providing a comprehensive overview of the digital forensic investigation.

File System Forensic Analysis Report
Jean – M57
Investigator Name:
Date:
Jean – M57
Investigator Name:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
This research work concentrates on determining and evaluating hard disk drive from
M57’s Jeans laptop in digital forensic analysis. The dramatic rise in cyber-crime has been
brought about by the use of computer and internet and therefore, the need for digital
forensics. Digital forensic utilities have been created s as to aid the analysts in conducting
assessment and evaluation of digital crimes. Over the years, computer forensics has
grown to be a critical area of research for military organizations, national intelligence,
and law enforcement. Digital forensics is the science of recognizing, deriving, assessing
and presenting evidence which are digital and are located in digital media to be used in
legal proceedings. The complexity of analyzing and processing digital information has
grown due to more data being stored in digital format. Digital forensic practice is still
new and helps in assessing and evaluating digital information in order to extract
evidence. The use of computers both at home and in business has led to advancement and
evolution of digital forensic techniques to beat the fast evolving cyber-crimes. When
computers became common in homes and businesses, the police more and more often
came across computers which contained forensic evidence.
This research work concentrates on determining and evaluating hard disk drive from
M57’s Jeans laptop in digital forensic analysis. The dramatic rise in cyber-crime has been
brought about by the use of computer and internet and therefore, the need for digital
forensics. Digital forensic utilities have been created s as to aid the analysts in conducting
assessment and evaluation of digital crimes. Over the years, computer forensics has
grown to be a critical area of research for military organizations, national intelligence,
and law enforcement. Digital forensics is the science of recognizing, deriving, assessing
and presenting evidence which are digital and are located in digital media to be used in
legal proceedings. The complexity of analyzing and processing digital information has
grown due to more data being stored in digital format. Digital forensic practice is still
new and helps in assessing and evaluating digital information in order to extract
evidence. The use of computers both at home and in business has led to advancement and
evolution of digital forensic techniques to beat the fast evolving cyber-crimes. When
computers became common in homes and businesses, the police more and more often
came across computers which contained forensic evidence.

Table of Contents
Abstract................................................................................................................................2
Introduction..........................................................................................................................4
The Basics of Digital Storage Media...................................................................................4
Performance of Hard Drive in Forensic Applications.........................................................4
Digital Forensics..................................................................................................................4
Forensic Analysis Process...................................................................................................5
Investigator Information......................................................................................................5
Case Description..................................................................................................................5
Forensic Tool Statistics........................................................................................................5
Investigation Process...........................................................................................................6
Identification....................................................................................................................6
Preservation.....................................................................................................................6
Collection.........................................................................................................................6
Image Mounting...........................................................................................................6
Examination and Analysis...................................................................................................8
Analysis of Windows Registry........................................................................................8
System config user info...................................................................................................9
User communications: E-mails and URLs................................................................10
Presentation................................................................................................................12
Conclusion.........................................................................................................................13
Bibliography......................................................................................................................13
Abstract................................................................................................................................2
Introduction..........................................................................................................................4
The Basics of Digital Storage Media...................................................................................4
Performance of Hard Drive in Forensic Applications.........................................................4
Digital Forensics..................................................................................................................4
Forensic Analysis Process...................................................................................................5
Investigator Information......................................................................................................5
Case Description..................................................................................................................5
Forensic Tool Statistics........................................................................................................5
Investigation Process...........................................................................................................6
Identification....................................................................................................................6
Preservation.....................................................................................................................6
Collection.........................................................................................................................6
Image Mounting...........................................................................................................6
Examination and Analysis...................................................................................................8
Analysis of Windows Registry........................................................................................8
System config user info...................................................................................................9
User communications: E-mails and URLs................................................................10
Presentation................................................................................................................12
Conclusion.........................................................................................................................13
Bibliography......................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
Recently, digital forensic field has grown very fast, as computer forensic assessment use
has proven priceless in legal processes. Not only is digital forensics used in computer
crimes such as distribution of illegal digital item distribution, data fabrication and
network intrusion but also investigation of exhibits located I digital devices digitally. It is
combined with the rising dependence on and gathering of digital evidence on storage
media such as hard drive [1]. The sudden increase in in storage needs has not been
attributed to forensics analysis, rather, to reduced data duplication techniques which is
widely used in primary resource storage software. This report describes the essence of
data available in the hard disk for forensic investigation and evaluation.
The Basics of Digital Storage Media
Regardless of the exceptional rise in use of mobile devices like personal digital assistant
and cellphones in the recent times, the focus of computer forensic investigation has
remained to be the hard drive. The modification of the hard disk design over the years has
remained minimal since it was first introduced, however, adjustment of the individual
parts has led to extraordinary advancements in reliability, capacity and speed. When the
hard drive internal structure is exposed, four major components will be identified, the
include; head arm, the chassis and disk platter.
Performance of Hard Drive in Forensic Applications
Forensic imaging is sequential in nature and therefore, the benefit of large on-disk cache
buffers and the rate of fast interface transfer are largely eliminated. The claims of high
interface transfers fools even the experienced forensic analyst. Today, standard hard drive
uses SATA standard interface.
Digital Forensics
Digital forensics refers to the use of derived and proven scientific means in the
identification, collection, analysis, validation, interpretation, presentation, documentation,
and preservation of digital exhibits extracted from digital sources aiming to speed up and
further reformation of events identified to be a crime, or to aid in recognizing actions
which seems disruptive and unauthorized to planned activities [2]. Digital forensic
investigation is made up of six steps; identification, preservation, collection, examination,
analysis and presentation. Therefore, the science of recognizing, deriving, assessing and
Recently, digital forensic field has grown very fast, as computer forensic assessment use
has proven priceless in legal processes. Not only is digital forensics used in computer
crimes such as distribution of illegal digital item distribution, data fabrication and
network intrusion but also investigation of exhibits located I digital devices digitally. It is
combined with the rising dependence on and gathering of digital evidence on storage
media such as hard drive [1]. The sudden increase in in storage needs has not been
attributed to forensics analysis, rather, to reduced data duplication techniques which is
widely used in primary resource storage software. This report describes the essence of
data available in the hard disk for forensic investigation and evaluation.
The Basics of Digital Storage Media
Regardless of the exceptional rise in use of mobile devices like personal digital assistant
and cellphones in the recent times, the focus of computer forensic investigation has
remained to be the hard drive. The modification of the hard disk design over the years has
remained minimal since it was first introduced, however, adjustment of the individual
parts has led to extraordinary advancements in reliability, capacity and speed. When the
hard drive internal structure is exposed, four major components will be identified, the
include; head arm, the chassis and disk platter.
Performance of Hard Drive in Forensic Applications
Forensic imaging is sequential in nature and therefore, the benefit of large on-disk cache
buffers and the rate of fast interface transfer are largely eliminated. The claims of high
interface transfers fools even the experienced forensic analyst. Today, standard hard drive
uses SATA standard interface.
Digital Forensics
Digital forensics refers to the use of derived and proven scientific means in the
identification, collection, analysis, validation, interpretation, presentation, documentation,
and preservation of digital exhibits extracted from digital sources aiming to speed up and
further reformation of events identified to be a crime, or to aid in recognizing actions
which seems disruptive and unauthorized to planned activities [2]. Digital forensic
investigation is made up of six steps; identification, preservation, collection, examination,
analysis and presentation. Therefore, the science of recognizing, deriving, assessing and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

presenting evidence which are digital and are located in digital media to be used in legal
proceedings is referred to as digital forensics.
Generally, the role of forensic investigation is to try and give full details of a cyber-crime
scene. Digital forensic analysis has five major objectives; to determine all unauthorized
activities that have occurred, to identify the impact of such activities on the system, to
identify the required evidence needed in the court of law, to avoid future situation by
determining the illegal ways used, and to find out the goals and intentions of the cyber-
criminal for future projections. The general concepts in digital forensic activity incudes
obtaining, conservation, and evaluation. Digital electronic evidence can be defined as
data and information located on an electronic device that have investigative value. Data
deleted by the user can still be recovered even if it was “permanently deleted.” The
methods of getting back the destroyed data are thus, important in digital forensics [3].
Digital evidence should be handled carefully because they can be easily modified so as to
prove the source of the information. The research however, concentrates on the third
objective This research focuses on the above mentioned third goal of identifying the
required evidence of suspect laptop hard drive that occurred.
Forensic Analysis Process
This section describes the processes involved in forensic evaluation employed to attain
the mentioned goal of the research work. An experimental study was carried out using
identified digital forensic tools that are essentially used practically. Since every service
perform some particular functions, an assembly of such utilities was needed to carry out
the set of processes comprehensively. Therefore, the forensic tools used to perform the
experimental examination in this research include the following; experience and skills of
the investigator is essential in the analysis phase [4]. To evaluate the data gathered about
a scenario, the analyst needs to identify where the alleged individual could have hidden
or modified the data and in what way and what programs might have been used. Data
patterns identified are very useful, once it has been recognized and assessed fully, it may
guide to getting more evidence. For an analyst to attain a successful investigation, he/she
should use several utilities such as forensic toolkit and Sleuthkit tools that is mapped with
dtSearch search tool to evaluate the collected data. The tools allow the investigator to go
through the files just like the normal file managers and displays them. Moreover,
additional features are provided that are essential in forensics for instance, opening
compressed files or showing file headers. Sleuthkit tools, for example, give more
contextual evaluation properties such as timeline view of the files and queries. However,
the analyst is accountable for manually conducting the examination and acquiring
knowledge from the collected information.
proceedings is referred to as digital forensics.
Generally, the role of forensic investigation is to try and give full details of a cyber-crime
scene. Digital forensic analysis has five major objectives; to determine all unauthorized
activities that have occurred, to identify the impact of such activities on the system, to
identify the required evidence needed in the court of law, to avoid future situation by
determining the illegal ways used, and to find out the goals and intentions of the cyber-
criminal for future projections. The general concepts in digital forensic activity incudes
obtaining, conservation, and evaluation. Digital electronic evidence can be defined as
data and information located on an electronic device that have investigative value. Data
deleted by the user can still be recovered even if it was “permanently deleted.” The
methods of getting back the destroyed data are thus, important in digital forensics [3].
Digital evidence should be handled carefully because they can be easily modified so as to
prove the source of the information. The research however, concentrates on the third
objective This research focuses on the above mentioned third goal of identifying the
required evidence of suspect laptop hard drive that occurred.
Forensic Analysis Process
This section describes the processes involved in forensic evaluation employed to attain
the mentioned goal of the research work. An experimental study was carried out using
identified digital forensic tools that are essentially used practically. Since every service
perform some particular functions, an assembly of such utilities was needed to carry out
the set of processes comprehensively. Therefore, the forensic tools used to perform the
experimental examination in this research include the following; experience and skills of
the investigator is essential in the analysis phase [4]. To evaluate the data gathered about
a scenario, the analyst needs to identify where the alleged individual could have hidden
or modified the data and in what way and what programs might have been used. Data
patterns identified are very useful, once it has been recognized and assessed fully, it may
guide to getting more evidence. For an analyst to attain a successful investigation, he/she
should use several utilities such as forensic toolkit and Sleuthkit tools that is mapped with
dtSearch search tool to evaluate the collected data. The tools allow the investigator to go
through the files just like the normal file managers and displays them. Moreover,
additional features are provided that are essential in forensics for instance, opening
compressed files or showing file headers. Sleuthkit tools, for example, give more
contextual evaluation properties such as timeline view of the files and queries. However,
the analyst is accountable for manually conducting the examination and acquiring
knowledge from the collected information.

Investigator Information
The report contains details contains details of the investigation process and evidence
collection of the M57-Jean scenario where some confidential information was leaked out
to the competing company and was only available and Jean’s laptop. The evidence was
collected later reviewed by the previous analyst to confirm its integrity, that is, confirmed
to be unaltered.
Case Description
M57’s Jean is under investigation for allegedly leaking out information to the competing
company, although she claims that she was hacked and data leaked to the latter company.
Forensic Tool Statistics
The laptop was taken from M57.Biz on 14th September 2017, 3:57:17PM to a forensic
facility which was close and secure. The laptop hard drive was removed and imaged at
the forensic lab to start testing and research. Hard drive image was assessed using a
Sleuthkit forensic tool. The tool is open source has been analyzed and found to produce
accurate and valid outcome when scanning and testing a system.
Investigation Process
Identification
Jean was asked some relevant questions related to the case under probe. She was
interrogated for the purpose of acquiring data acquisition legitimacy. The questions that
were asked include:
1. Does any other person have access to Jean’s digital devices such as laptop, phone,
tablet or flash drives?
2. Is the laptop, phone, thumb drive and other devices personal or were they issued
to Jean by the organization?
3. If the devices were issued by the organization, was Jean the second user or first?
Preservation
Search, seizer and transport of evidence
A search warrant was requested so as the legal authorities could search and seize Jean’s
premises of any device which may be assessed and regarded as digital evidence in order
to exonerate or convict her. Upon seizure, the devices regarded as evidence were
The report contains details contains details of the investigation process and evidence
collection of the M57-Jean scenario where some confidential information was leaked out
to the competing company and was only available and Jean’s laptop. The evidence was
collected later reviewed by the previous analyst to confirm its integrity, that is, confirmed
to be unaltered.
Case Description
M57’s Jean is under investigation for allegedly leaking out information to the competing
company, although she claims that she was hacked and data leaked to the latter company.
Forensic Tool Statistics
The laptop was taken from M57.Biz on 14th September 2017, 3:57:17PM to a forensic
facility which was close and secure. The laptop hard drive was removed and imaged at
the forensic lab to start testing and research. Hard drive image was assessed using a
Sleuthkit forensic tool. The tool is open source has been analyzed and found to produce
accurate and valid outcome when scanning and testing a system.
Investigation Process
Identification
Jean was asked some relevant questions related to the case under probe. She was
interrogated for the purpose of acquiring data acquisition legitimacy. The questions that
were asked include:
1. Does any other person have access to Jean’s digital devices such as laptop, phone,
tablet or flash drives?
2. Is the laptop, phone, thumb drive and other devices personal or were they issued
to Jean by the organization?
3. If the devices were issued by the organization, was Jean the second user or first?
Preservation
Search, seizer and transport of evidence
A search warrant was requested so as the legal authorities could search and seize Jean’s
premises of any device which may be assessed and regarded as digital evidence in order
to exonerate or convict her. Upon seizure, the devices regarded as evidence were
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

packaged carefully and establishment of chain of custody was done efficiently so as to
maintain evidence integrity.
The following exhibits were submitted for analysis;
Huawei Wi-Fi Modem serial number 345678906543
Samsung smartphone serial number 234567899876
SanDisk thumb drive S456787
Golden Acer Aspire 5736Z laptop serial number FRT4YZ788
Nokia Cellphone serial number 5467098789098
Collection
Image Mounting
The steps below were taken to retrieve data identified to be relevant to the case.
A new case called M57-Jean Scenario was created. The image (C:\forensic\
winlabSleuthkittools.image) was added to the case. After the loading the case, time zone
was immediately set by right clicking on the image, then Modify Time Zone. Setting the
time zone is done so as to adjust the evidence to match the same period.
Recovering any deleted or hidden files and folders on the laptop was the next step. Data
recovery facilitated searching process to be more complete and identification of activities
and processes that might have occurred to destroy or hide evidence. To carry out this
task, one can right click on the image then choose Recover Folders option.
To determine laptop specifications, a script was executed; because of the fact that another
investigator was the one creating the image from the suspect computer. The script is
normally loaded next to determine the specifications about the computer because I had
not been the one to create the image from the suspect machine. The script command can
be found in the Sleuthkit tools command list. The procedure to do so is: go to View, then
Scripts and choose the Initialize Case script which hints one to key in details of the
person carrying out the analysis. Once the details were entered, the script prompts a
person to select where to store the data, and for this situation, preferred location chosen
was under a folder called M57 Jean Analysis Report. It is also important to confirm
which information to issue out. The information chosen for presentation include: network
description, windows version and registration, user details, and time of shutdown. The
generated report is shown in the table 1 below. The essential details extracted from the
report is that the laptop was operating on NTFS file system with windows XP. The
partition had a total space of 22MB.
Volume
File System: FAT16 Drive Type: Fixed
Sectors per cluster: 1 Bytes per sector: 512
Total Sectors: 45,360 Total Capacity: 23,023,616 bytes (22MB)
Total Clusters: 44,968 Unallocated: 13,872,128 bytes (13.2MB)
Free Clusters: 27,094 Allocated: 9,151,488 bytes (8.7MB)
maintain evidence integrity.
The following exhibits were submitted for analysis;
Huawei Wi-Fi Modem serial number 345678906543
Samsung smartphone serial number 234567899876
SanDisk thumb drive S456787
Golden Acer Aspire 5736Z laptop serial number FRT4YZ788
Nokia Cellphone serial number 5467098789098
Collection
Image Mounting
The steps below were taken to retrieve data identified to be relevant to the case.
A new case called M57-Jean Scenario was created. The image (C:\forensic\
winlabSleuthkittools.image) was added to the case. After the loading the case, time zone
was immediately set by right clicking on the image, then Modify Time Zone. Setting the
time zone is done so as to adjust the evidence to match the same period.
Recovering any deleted or hidden files and folders on the laptop was the next step. Data
recovery facilitated searching process to be more complete and identification of activities
and processes that might have occurred to destroy or hide evidence. To carry out this
task, one can right click on the image then choose Recover Folders option.
To determine laptop specifications, a script was executed; because of the fact that another
investigator was the one creating the image from the suspect computer. The script is
normally loaded next to determine the specifications about the computer because I had
not been the one to create the image from the suspect machine. The script command can
be found in the Sleuthkit tools command list. The procedure to do so is: go to View, then
Scripts and choose the Initialize Case script which hints one to key in details of the
person carrying out the analysis. Once the details were entered, the script prompts a
person to select where to store the data, and for this situation, preferred location chosen
was under a folder called M57 Jean Analysis Report. It is also important to confirm
which information to issue out. The information chosen for presentation include: network
description, windows version and registration, user details, and time of shutdown. The
generated report is shown in the table 1 below. The essential details extracted from the
report is that the laptop was operating on NTFS file system with windows XP. The
partition had a total space of 22MB.
Volume
File System: FAT16 Drive Type: Fixed
Sectors per cluster: 1 Bytes per sector: 512
Total Sectors: 45,360 Total Capacity: 23,023,616 bytes (22MB)
Total Clusters: 44,968 Unallocated: 13,872,128 bytes (13.2MB)
Free Clusters: 27,094 Allocated: 9,151,488 bytes (8.7MB)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
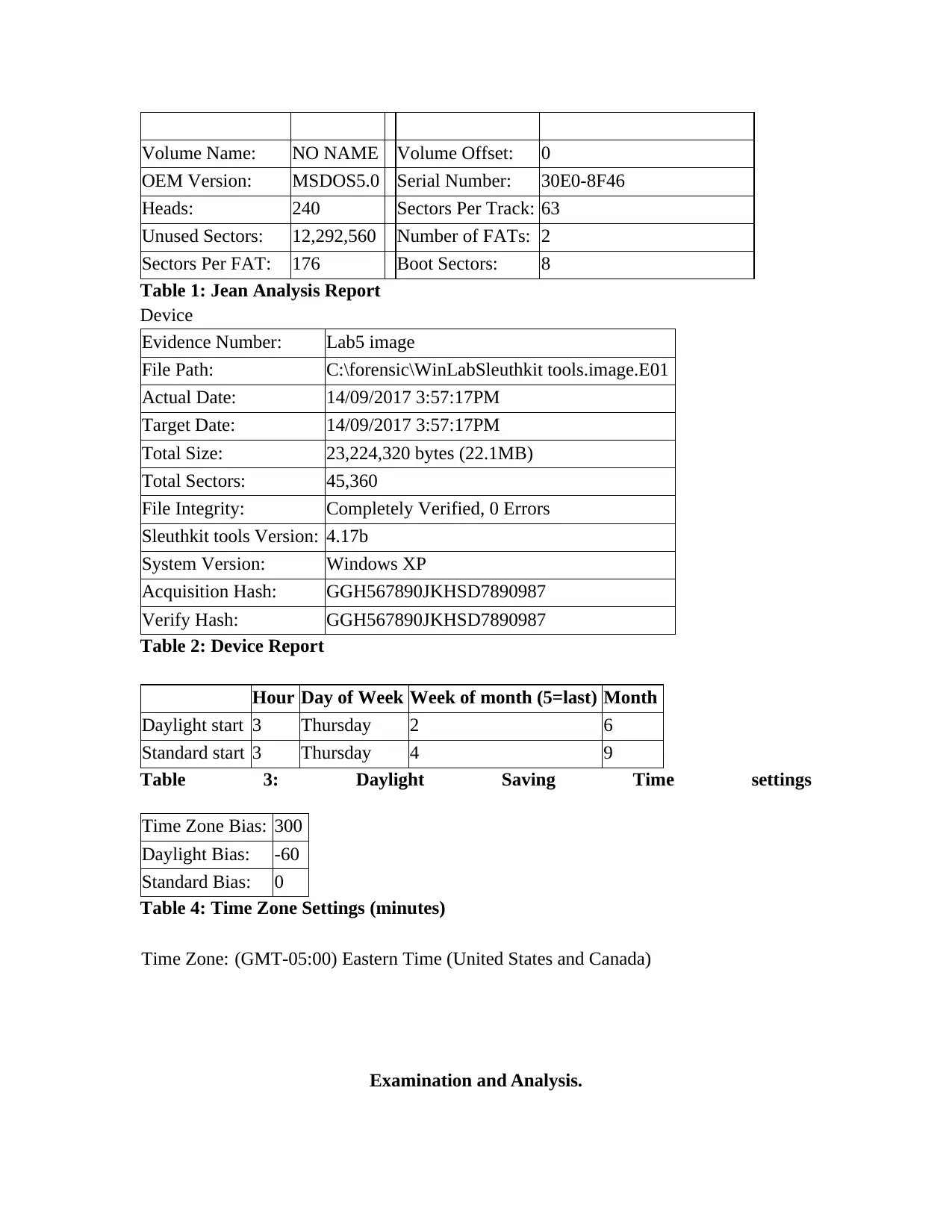
Volume Name: NO NAME Volume Offset: 0
OEM Version: MSDOS5.0 Serial Number: 30E0-8F46
Heads: 240 Sectors Per Track: 63
Unused Sectors: 12,292,560 Number of FATs: 2
Sectors Per FAT: 176 Boot Sectors: 8
Table 1: Jean Analysis Report
Device
Evidence Number: Lab5 image
File Path: C:\forensic\WinLabSleuthkit tools.image.E01
Actual Date: 14/09/2017 3:57:17PM
Target Date: 14/09/2017 3:57:17PM
Total Size: 23,224,320 bytes (22.1MB)
Total Sectors: 45,360
File Integrity: Completely Verified, 0 Errors
Sleuthkit tools Version: 4.17b
System Version: Windows XP
Acquisition Hash: GGH567890JKHSD7890987
Verify Hash: GGH567890JKHSD7890987
Table 2: Device Report
Hour Day of Week Week of month (5=last) Month
Daylight start 3 Thursday 2 6
Standard start 3 Thursday 4 9
Table 3: Daylight Saving Time settings
Time Zone Bias: 300
Daylight Bias: -60
Standard Bias: 0
Table 4: Time Zone Settings (minutes)
Time Zone: (GMT-05:00) Eastern Time (United States and Canada)
Examination and Analysis.
OEM Version: MSDOS5.0 Serial Number: 30E0-8F46
Heads: 240 Sectors Per Track: 63
Unused Sectors: 12,292,560 Number of FATs: 2
Sectors Per FAT: 176 Boot Sectors: 8
Table 1: Jean Analysis Report
Device
Evidence Number: Lab5 image
File Path: C:\forensic\WinLabSleuthkit tools.image.E01
Actual Date: 14/09/2017 3:57:17PM
Target Date: 14/09/2017 3:57:17PM
Total Size: 23,224,320 bytes (22.1MB)
Total Sectors: 45,360
File Integrity: Completely Verified, 0 Errors
Sleuthkit tools Version: 4.17b
System Version: Windows XP
Acquisition Hash: GGH567890JKHSD7890987
Verify Hash: GGH567890JKHSD7890987
Table 2: Device Report
Hour Day of Week Week of month (5=last) Month
Daylight start 3 Thursday 2 6
Standard start 3 Thursday 4 9
Table 3: Daylight Saving Time settings
Time Zone Bias: 300
Daylight Bias: -60
Standard Bias: 0
Table 4: Time Zone Settings (minutes)
Time Zone: (GMT-05:00) Eastern Time (United States and Canada)
Examination and Analysis.

Analysis of Windows Registry
Determine if Security Audits are enabled
First, the investigator checked if Jean’s laptop security audits were enabled using auditpol
plugin available in RegRipper.
perl rip.pl -r /mnt/ M57-Jean Scenario /WINDOWS/system32/config/SECURITY -p
auditpol
Result: It was found that auditing was disabled on Jean’s system.
Examining Windows Shellbags
Window XP supports the “Remember each folder view settings” and is stored in the
registry as follows:
Jean\Software\Microsoft\Windows\Shell\Bags
Jean\Software\Microsoft\Windows\Shell\BagMRU
Jean\Software\Microsoft\Windows\ShellNoRoam\Bags
Jean\Software\Microsoft\Windows\ShellNoRoam\BagMRU
The information derived from this key enabled the investigator to know extract all the
information about all the folders when, how and why they were accessed even after they
have been deleted. It reveals information deleted or modified files by the user and also
shows details on the windows explorer utilization to acess detachable storage devices and
remote shares. The plugin ‘bagtest in RegRipper is used.
Finding details stored in banners
Banners are messages that show or pop-up when a user log on to the computer. The
information is located in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows
NT\CurrentVersion\WinLogon
Registry key. To obtain nformation about the banner, ‘banner’ plugin is used.
Result: In this case Jean’s machine did not have any banners.
Getting details from SAM hive
To extract group and user details from the SAM hive file, ‘samparse’ plugin is used.
The key is perl rip.pl –r /mnt/ M57-Jean Scenario/WINDOWS/Sytstem32/config/SAM –
p samparse
Result: It was found out that the user had logged in to the system 234 times.
NukeOnDelete
‘NukeOnDelete’ is a function that enables a user to disable the recycle Bin. To check if
this function was set ‘bitbucket’ plugin is used. The registry location is; Microsoft\
Windows\CurrentVersion\Explorer\BitBucket
perl rip.pl -r /mnt/ M57-Jean Scenario /WINDOWS/system32/config/software -p
bitbucket
Result: It was found out that NukeOnDelete was not set.
Virus Detection
RegRipper provides the analyst with some specific plugins to detect presence of viruses
in the computer. Presence of ‘llomo/clampi’ was checked durng the investigation; the
Determine if Security Audits are enabled
First, the investigator checked if Jean’s laptop security audits were enabled using auditpol
plugin available in RegRipper.
perl rip.pl -r /mnt/ M57-Jean Scenario /WINDOWS/system32/config/SECURITY -p
auditpol
Result: It was found that auditing was disabled on Jean’s system.
Examining Windows Shellbags
Window XP supports the “Remember each folder view settings” and is stored in the
registry as follows:
Jean\Software\Microsoft\Windows\Shell\Bags
Jean\Software\Microsoft\Windows\Shell\BagMRU
Jean\Software\Microsoft\Windows\ShellNoRoam\Bags
Jean\Software\Microsoft\Windows\ShellNoRoam\BagMRU
The information derived from this key enabled the investigator to know extract all the
information about all the folders when, how and why they were accessed even after they
have been deleted. It reveals information deleted or modified files by the user and also
shows details on the windows explorer utilization to acess detachable storage devices and
remote shares. The plugin ‘bagtest in RegRipper is used.
Finding details stored in banners
Banners are messages that show or pop-up when a user log on to the computer. The
information is located in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows
NT\CurrentVersion\WinLogon
Registry key. To obtain nformation about the banner, ‘banner’ plugin is used.
Result: In this case Jean’s machine did not have any banners.
Getting details from SAM hive
To extract group and user details from the SAM hive file, ‘samparse’ plugin is used.
The key is perl rip.pl –r /mnt/ M57-Jean Scenario/WINDOWS/Sytstem32/config/SAM –
p samparse
Result: It was found out that the user had logged in to the system 234 times.
NukeOnDelete
‘NukeOnDelete’ is a function that enables a user to disable the recycle Bin. To check if
this function was set ‘bitbucket’ plugin is used. The registry location is; Microsoft\
Windows\CurrentVersion\Explorer\BitBucket
perl rip.pl -r /mnt/ M57-Jean Scenario /WINDOWS/system32/config/software -p
bitbucket
Result: It was found out that NukeOnDelete was not set.
Virus Detection
RegRipper provides the analyst with some specific plugins to detect presence of viruses
in the computer. Presence of ‘llomo/clampi’ was checked durng the investigation; the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Trojan is commonly determining due to existence of the file ‘Microsoft\9593275321’ in
the software hive. To carry out this function ‘clampi’ plugin is used.
perl rip.pl -r /mnt/ M57-Jean Scenario /Documents\ and\ Settings/Jean/NTUSER.DAT -p
clampi
Result: it was determined that the Trojan ‘Ilomo/Clampi’ was not present in the system.
Remote connection
The systems store information about the connections that it has had with other system
over the network. The registry key that stores this information is called ‘computer
description key’ and is located at Jean\Software\Microsoft\Windows\CurrentVersion\
Explorer\ComputerDescriptions
To determine this, plugin ‘compdesc’ is used: perl rip.pl -r /mnt/ M57-Jean Scenario
/Documents\ and\ Settings/Jean /NTUSER.DAT -p compdesc
Result; suspected system had connected to 6 other devices over the network and was
added to the investigation analysis report.
System config user info
Users information is stored in the SAM hive file found in the system registry. This file is
inaccessible even with admin privileges unless access permissions are modified manually
following some specific steps. Data stored in the SAM hive is encrypted to binary.
However, to decipher tis information, the analyst used sam.h file created by Peter
Nordahl-hagen. As such, to obtain group and user membership details, userdump
prescript is used. The user details are kept in the F value found in; SAM\SAM\Domains\
Accounts\Users\ {RID}.
A number of registry keys can be used to track actions and activities of the user. Such
keys can be found in NTUSER.DAT file. Much of the information about user activities is
contained in HKEY_CURRENT_USER hive. .
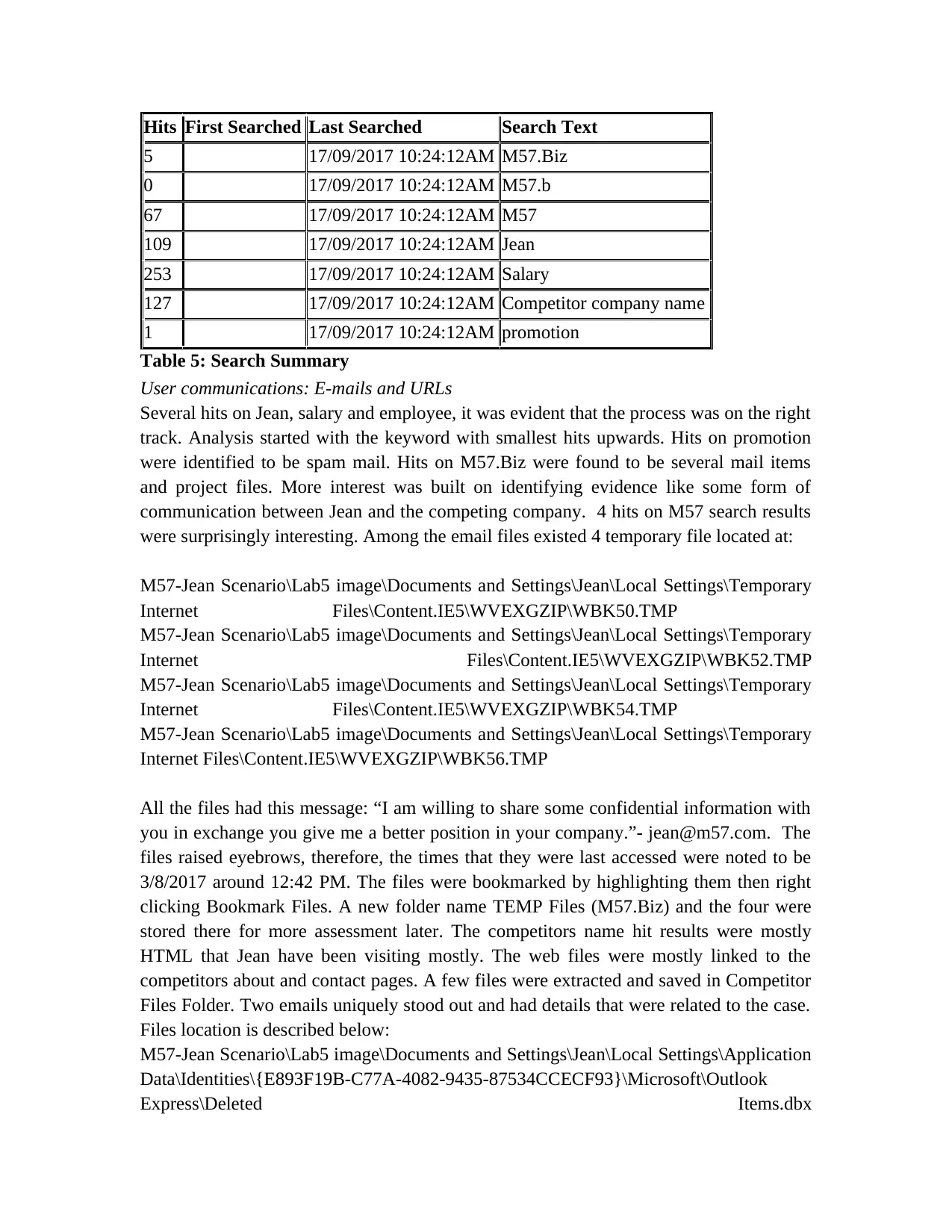
Search Key Word
The first assignment was to create a list of important terms that would be required when
searching the file system. Identifying the key words to search could aid in doing away
with irrelevant details. The list was made up of following: M57.Biz (M57 and M57.b as
different variables for that matter), Jean, Salary, Employee, Competitor company name
and Promotion. To create a list of key word, click on View-Keywords-Right Click
Keywords- Select Add New Folder and was named M57JeanFolder Keywords. Upon
folder creation, right click on M57JeanFolder Keywords and select insert keyword list.
Finally, the list of key terms is kept with the previously identified keywords. The terms
were then highlighted and search process was conducted by selecting the Search option
located at the top of the program window. Criteria used for searching involved searching
file slack, every file for key terms and highlighted key word only. Numerical search
results are displayed in the table 5 below.
the software hive. To carry out this function ‘clampi’ plugin is used.
perl rip.pl -r /mnt/ M57-Jean Scenario /Documents\ and\ Settings/Jean/NTUSER.DAT -p
clampi
Result: it was determined that the Trojan ‘Ilomo/Clampi’ was not present in the system.
Remote connection
The systems store information about the connections that it has had with other system
over the network. The registry key that stores this information is called ‘computer
description key’ and is located at Jean\Software\Microsoft\Windows\CurrentVersion\
Explorer\ComputerDescriptions
To determine this, plugin ‘compdesc’ is used: perl rip.pl -r /mnt/ M57-Jean Scenario
/Documents\ and\ Settings/Jean /NTUSER.DAT -p compdesc
Result; suspected system had connected to 6 other devices over the network and was
added to the investigation analysis report.
System config user info
Users information is stored in the SAM hive file found in the system registry. This file is
inaccessible even with admin privileges unless access permissions are modified manually
following some specific steps. Data stored in the SAM hive is encrypted to binary.
However, to decipher tis information, the analyst used sam.h file created by Peter
Nordahl-hagen. As such, to obtain group and user membership details, userdump
prescript is used. The user details are kept in the F value found in; SAM\SAM\Domains\
Accounts\Users\ {RID}.
A number of registry keys can be used to track actions and activities of the user. Such
keys can be found in NTUSER.DAT file. Much of the information about user activities is
contained in HKEY_CURRENT_USER hive. .
Search Key Word
The first assignment was to create a list of important terms that would be required when
searching the file system. Identifying the key words to search could aid in doing away
with irrelevant details. The list was made up of following: M57.Biz (M57 and M57.b as
different variables for that matter), Jean, Salary, Employee, Competitor company name
and Promotion. To create a list of key word, click on View-Keywords-Right Click
Keywords- Select Add New Folder and was named M57JeanFolder Keywords. Upon
folder creation, right click on M57JeanFolder Keywords and select insert keyword list.
Finally, the list of key terms is kept with the previously identified keywords. The terms
were then highlighted and search process was conducted by selecting the Search option
located at the top of the program window. Criteria used for searching involved searching
file slack, every file for key terms and highlighted key word only. Numerical search
results are displayed in the table 5 below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Hits First Searched Last Searched Search Text
5 17/09/2017 10:24:12AM M57.Biz
0 17/09/2017 10:24:12AM M57.b
67 17/09/2017 10:24:12AM M57
109 17/09/2017 10:24:12AM Jean
253 17/09/2017 10:24:12AM Salary
127 17/09/2017 10:24:12AM Competitor company name
1 17/09/2017 10:24:12AM promotion
Table 5: Search Summary
User communications: E-mails and URLs
Several hits on Jean, salary and employee, it was evident that the process was on the right
track. Analysis started with the keyword with smallest hits upwards. Hits on promotion
were identified to be spam mail. Hits on M57.Biz were found to be several mail items
and project files. More interest was built on identifying evidence like some form of
communication between Jean and the competing company. 4 hits on M57 search results
were surprisingly interesting. Among the email files existed 4 temporary file located at:
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Temporary
Internet Files\Content.IE5\WVEXGZIP\WBK50.TMP
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Temporary
Internet Files\Content.IE5\WVEXGZIP\WBK52.TMP
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Temporary
Internet Files\Content.IE5\WVEXGZIP\WBK54.TMP
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Temporary
Internet Files\Content.IE5\WVEXGZIP\WBK56.TMP
All the files had this message: “I am willing to share some confidential information with
you in exchange you give me a better position in your company.”- jean@m57.com. The
files raised eyebrows, therefore, the times that they were last accessed were noted to be
3/8/2017 around 12:42 PM. The files were bookmarked by highlighting them then right
clicking Bookmark Files. A new folder name TEMP Files (M57.Biz) and the four were
stored there for more assessment later. The competitors name hit results were mostly
HTML that Jean have been visiting mostly. The web files were mostly linked to the
competitors about and contact pages. A few files were extracted and saved in Competitor
Files Folder. Two emails uniquely stood out and had details that were related to the case.
Files location is described below:
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Application
Data\Identities\{E893F19B-C77A-4082-9435-87534CCECF93}\Microsoft\Outlook
Express\Deleted Items.dbx
5 17/09/2017 10:24:12AM M57.Biz
0 17/09/2017 10:24:12AM M57.b
67 17/09/2017 10:24:12AM M57
109 17/09/2017 10:24:12AM Jean
253 17/09/2017 10:24:12AM Salary
127 17/09/2017 10:24:12AM Competitor company name
1 17/09/2017 10:24:12AM promotion
Table 5: Search Summary
User communications: E-mails and URLs
Several hits on Jean, salary and employee, it was evident that the process was on the right
track. Analysis started with the keyword with smallest hits upwards. Hits on promotion
were identified to be spam mail. Hits on M57.Biz were found to be several mail items
and project files. More interest was built on identifying evidence like some form of
communication between Jean and the competing company. 4 hits on M57 search results
were surprisingly interesting. Among the email files existed 4 temporary file located at:
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Temporary
Internet Files\Content.IE5\WVEXGZIP\WBK50.TMP
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Temporary
Internet Files\Content.IE5\WVEXGZIP\WBK52.TMP
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Temporary
Internet Files\Content.IE5\WVEXGZIP\WBK54.TMP
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Temporary
Internet Files\Content.IE5\WVEXGZIP\WBK56.TMP
All the files had this message: “I am willing to share some confidential information with
you in exchange you give me a better position in your company.”- jean@m57.com. The
files raised eyebrows, therefore, the times that they were last accessed were noted to be
3/8/2017 around 12:42 PM. The files were bookmarked by highlighting them then right
clicking Bookmark Files. A new folder name TEMP Files (M57.Biz) and the four were
stored there for more assessment later. The competitors name hit results were mostly
HTML that Jean have been visiting mostly. The web files were mostly linked to the
competitors about and contact pages. A few files were extracted and saved in Competitor
Files Folder. Two emails uniquely stood out and had details that were related to the case.
Files location is described below:
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Application
Data\Identities\{E893F19B-C77A-4082-9435-87534CCECF93}\Microsoft\Outlook
Express\Deleted Items.dbx
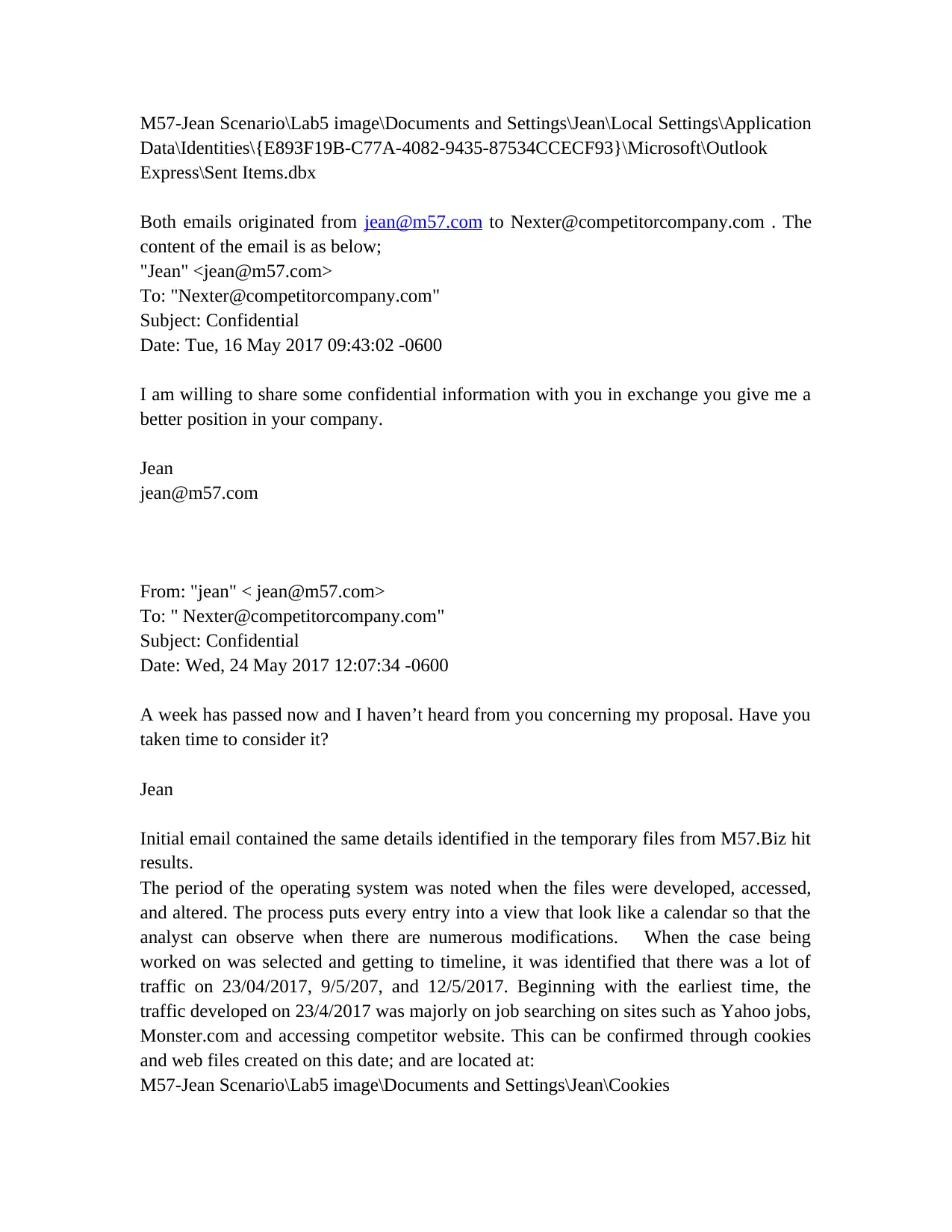
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Local Settings\Application
Data\Identities\{E893F19B-C77A-4082-9435-87534CCECF93}\Microsoft\Outlook
Express\Sent Items.dbx
Both emails originated from jean@m57.com to Nexter@competitorcompany.com . The
content of the email is as below;
"Jean" <jean@m57.com>
To: "Nexter@competitorcompany.com"
Subject: Confidential
Date: Tue, 16 May 2017 09:43:02 -0600
I am willing to share some confidential information with you in exchange you give me a
better position in your company.
Jean
jean@m57.com
From: "jean" < jean@m57.com>
To: " Nexter@competitorcompany.com"
Subject: Confidential
Date: Wed, 24 May 2017 12:07:34 -0600
A week has passed now and I haven’t heard from you concerning my proposal. Have you
taken time to consider it?
Jean
Initial email contained the same details identified in the temporary files from M57.Biz hit
results.
The period of the operating system was noted when the files were developed, accessed,
and altered. The process puts every entry into a view that look like a calendar so that the
analyst can observe when there are numerous modifications. When the case being
worked on was selected and getting to timeline, it was identified that there was a lot of
traffic on 23/04/2017, 9/5/207, and 12/5/2017. Beginning with the earliest time, the
traffic developed on 23/4/2017 was majorly on job searching on sites such as Yahoo jobs,
Monster.com and accessing competitor website. This can be confirmed through cookies
and web files created on this date; and are located at:
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Cookies
Data\Identities\{E893F19B-C77A-4082-9435-87534CCECF93}\Microsoft\Outlook
Express\Sent Items.dbx
Both emails originated from jean@m57.com to Nexter@competitorcompany.com . The
content of the email is as below;
"Jean" <jean@m57.com>
To: "Nexter@competitorcompany.com"
Subject: Confidential
Date: Tue, 16 May 2017 09:43:02 -0600
I am willing to share some confidential information with you in exchange you give me a
better position in your company.
Jean
jean@m57.com
From: "jean" < jean@m57.com>
To: " Nexter@competitorcompany.com"
Subject: Confidential
Date: Wed, 24 May 2017 12:07:34 -0600
A week has passed now and I haven’t heard from you concerning my proposal. Have you
taken time to consider it?
Jean
Initial email contained the same details identified in the temporary files from M57.Biz hit
results.
The period of the operating system was noted when the files were developed, accessed,
and altered. The process puts every entry into a view that look like a calendar so that the
analyst can observe when there are numerous modifications. When the case being
worked on was selected and getting to timeline, it was identified that there was a lot of
traffic on 23/04/2017, 9/5/207, and 12/5/2017. Beginning with the earliest time, the
traffic developed on 23/4/2017 was majorly on job searching on sites such as Yahoo jobs,
Monster.com and accessing competitor website. This can be confirmed through cookies
and web files created on this date; and are located at:
M57-Jean Scenario\Lab5 image\Documents and Settings\Jean\Cookies
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





