Project: Phishing Website Detection Using Machine Learning Techniques
VerifiedAdded on 2023/01/20
|16
|1468
|94
Project
AI Summary
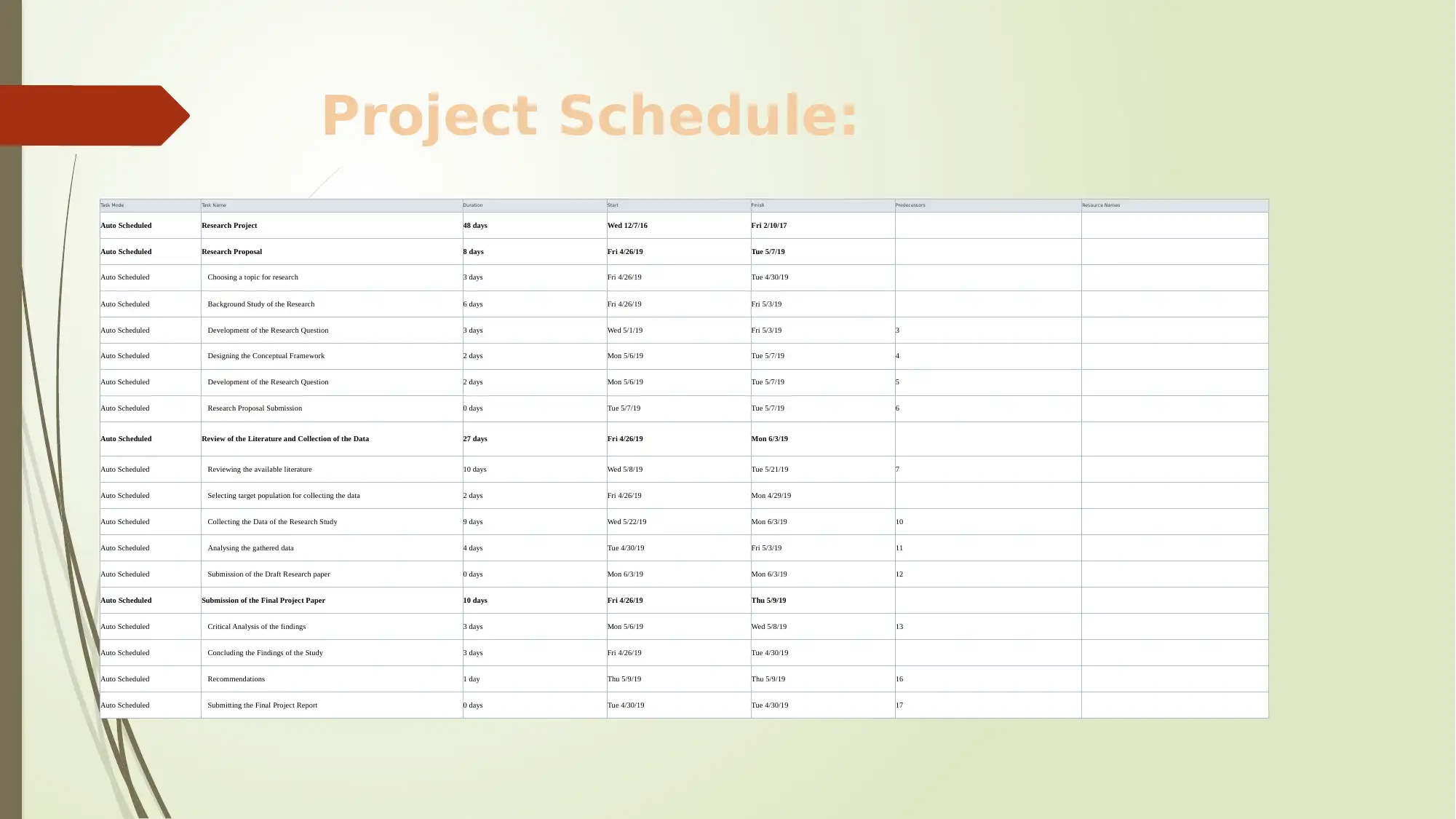
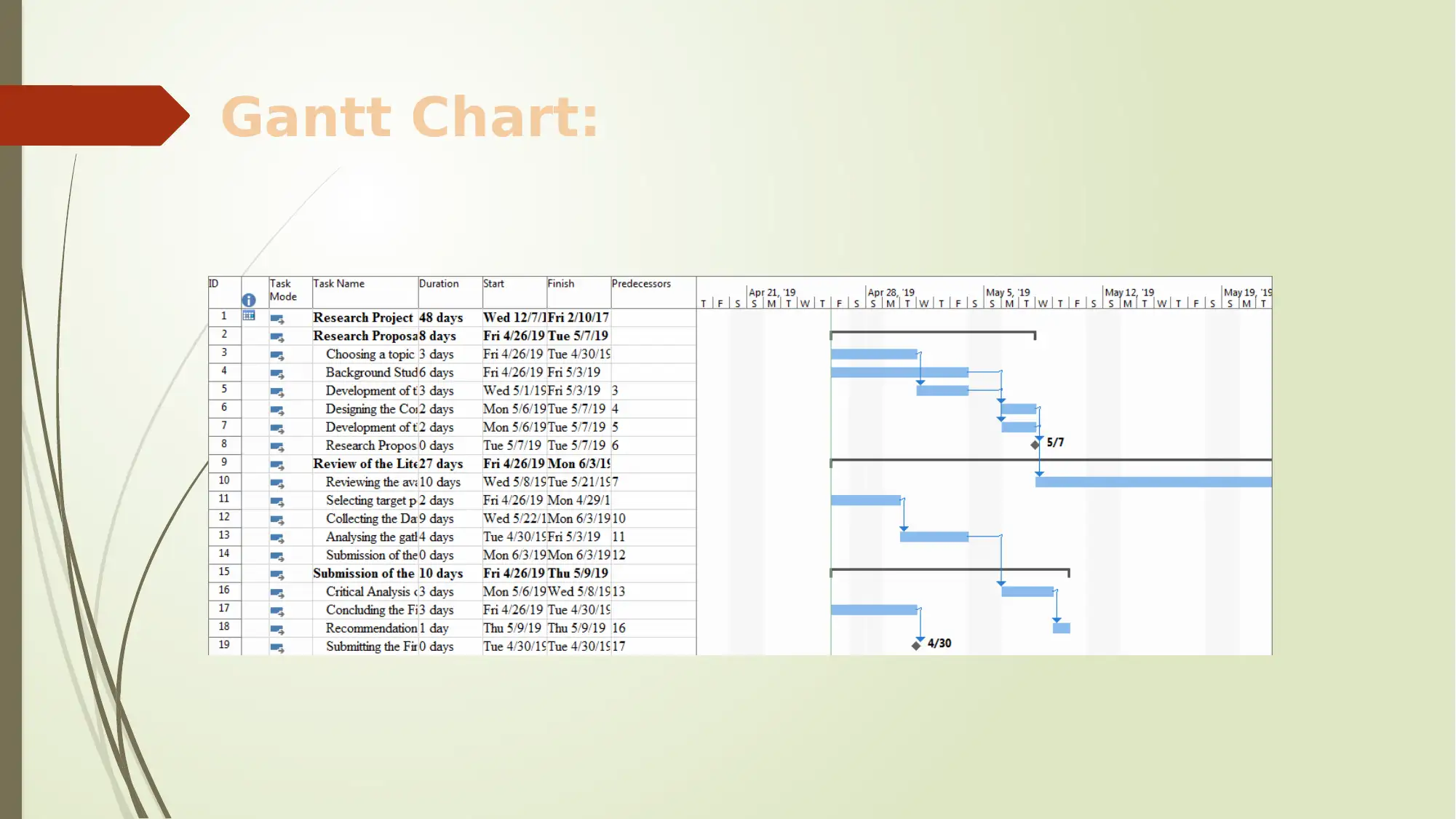
This project delves into the critical issue of phishing website detection, employing machine learning techniques to identify and mitigate the risks associated with these malicious sites. The project begins with an introduction to phishing, its goals, and objectives, emphasizing the use of machine learning in detecting phishing websites. A comprehensive literature review is conducted, comparing various machine learning algorithms and features, including lexical and host-based features, to understand their effectiveness in classifying phishing URLs. The project also highlights the importance of user education and software-based approaches in combating phishing attacks. The methodology utilizes a positivism philosophy, incorporating both human and scientific perspectives, with primary data collection planned. A detailed project schedule, including a Gantt chart, outlines the tasks, duration, and dependencies. The conclusion emphasizes the significance of online algorithms and the need for continuous adaptation to counter evolving phishing tactics, along with future research directions. The project aims to provide a framework for understanding and combating phishing attacks, contributing to enhanced cybersecurity measures.
1 out of 16















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)