MakeBelieve LLC: Network Topology Report
VerifiedAdded on 2019/09/18
|23
|4411
|286
Report
AI Summary
This document provides a comprehensive overview of MakeBelieve LLC, a startup company specializing in Networking-as-a-Service (NaaS). It details the company's profile, organizational roles, network topology, and database access protocols. The report also includes a cyber risk assessment and system audit policy, highlighting the company's commitment to security and data integrity. The document outlines the various roles within the organization, from the CEO to the Cyber Network Analysts, and their respective responsibilities. It also describes the company's network architecture, both external and internal, and the various databases used for customer and network data. The report concludes with a discussion of potential threats, risks, and vulnerabilities associated with cloud platforms, and the measures taken by MakeBelieve to mitigate these risks.

MakeBelieve, L.L.C:Network Topology
Table of Contents
Company Profile 3
Organizational Roles 5
Network Topology 7
Database Access 10
References 14
Attachment 1: Cyber Risk Assessment Report 15
Attachment 2: System Audit Policy 21
Table of Contents
Company Profile 3
Organizational Roles 5
Network Topology 7
Database Access 10
References 14
Attachment 1: Cyber Risk Assessment Report 15
Attachment 2: System Audit Policy 21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.Company Profile
MakeBelieve, LLC (MB) is a start-up company, which was founded in 2016. MakeBelieve is a
service-oriented company, which operates as a Networking-as-a-Service (Naas) provider as well
as the provision of customized network monitoring services for organizations that maintain cloud
computing applications. Due to the rise in cloud computing and virtualization technologies,
companies are increasingly opting to adopt services from third party providers as opposed to
owning and maintaining their own systems.
The emerging NaaS market is a market of vendors who provide virtual networking services for
cloud applications. As customers move towards virtualization and cloud applications, NaaS
vendors operate responsibly for handling networking activities as the emerging cloud platforms
have sought to separate segment traditional networking components. These services could
include but are not limited to Virtual Private Network (VPN), bandwidth services, multicast
protocol, security firewall, intrusion detection and prevention, content monitoring and filtering,
and antivirus software. As a relatively new startup, MB primarily focuses upon VPN, security
firewall, intrusion detection and prevention, content monitoring and filtering, and antivirus
software with plans to expand our current offering.
Cloud paradigms have gained significant popularity as customers have sought to focus primarily
on application-based architecture as opposed to maintaining the costly middlewares that are
necessary to ensure product scalability. Currently, the three services being offered besides NaaS
are Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service
2
MakeBelieve, LLC (MB) is a start-up company, which was founded in 2016. MakeBelieve is a
service-oriented company, which operates as a Networking-as-a-Service (Naas) provider as well
as the provision of customized network monitoring services for organizations that maintain cloud
computing applications. Due to the rise in cloud computing and virtualization technologies,
companies are increasingly opting to adopt services from third party providers as opposed to
owning and maintaining their own systems.
The emerging NaaS market is a market of vendors who provide virtual networking services for
cloud applications. As customers move towards virtualization and cloud applications, NaaS
vendors operate responsibly for handling networking activities as the emerging cloud platforms
have sought to separate segment traditional networking components. These services could
include but are not limited to Virtual Private Network (VPN), bandwidth services, multicast
protocol, security firewall, intrusion detection and prevention, content monitoring and filtering,
and antivirus software. As a relatively new startup, MB primarily focuses upon VPN, security
firewall, intrusion detection and prevention, content monitoring and filtering, and antivirus
software with plans to expand our current offering.
Cloud paradigms have gained significant popularity as customers have sought to focus primarily
on application-based architecture as opposed to maintaining the costly middlewares that are
necessary to ensure product scalability. Currently, the three services being offered besides NaaS
are Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service
2

(SaaS). Among these available virtualization services, NaaS operates between the SaaS layer and
the IaaS layer.
Although MakeBelieve is a relatively small company, we also provide analyst monitoring of our
customer's networks. To achieve this tasks, our analyst utilizes open-source network monitoring
tools such as wireshark to monitor our customer's network traffic. This data is directly fed into
our databases, which is directly connected to Tableau to allow for real time analysis of the
network traffic of our customers. Furthermore, our onsite Data Scientist utilizes python to
develop networking specific algorithms to provide more in-depth understanding of network
traffic patterns that could be deemed malicious or otherwise unwanted.
In the next section, we examine the various roles within the MB organization. In this section, we
examine each role and their specific responsibilities.
2. Organizational Roles
Currently, the organization maintains the following employee structure: Chief Operating Officer
(CEO), Chief Technology Officer (CTO), Principal Data Scientist, Database Administrator,
Senior Cyber Network Analyst, and Mid-Level Cyber Network Analyst. Since MakeBelieve is a
small NaaS service provider, it is essential that the organization’s members collaborate and
maintain multiple roles within the organization. Table 1 provides a basic breakdown of the
responsibilities of organization members. As a growing organization, responsibilities are wide
ranging and often times overlap with the duties of other members of the organization.
Table 1: MakeBelieve (MB) Roles and Responsibilities
3
the IaaS layer.
Although MakeBelieve is a relatively small company, we also provide analyst monitoring of our
customer's networks. To achieve this tasks, our analyst utilizes open-source network monitoring
tools such as wireshark to monitor our customer's network traffic. This data is directly fed into
our databases, which is directly connected to Tableau to allow for real time analysis of the
network traffic of our customers. Furthermore, our onsite Data Scientist utilizes python to
develop networking specific algorithms to provide more in-depth understanding of network
traffic patterns that could be deemed malicious or otherwise unwanted.
In the next section, we examine the various roles within the MB organization. In this section, we
examine each role and their specific responsibilities.
2. Organizational Roles
Currently, the organization maintains the following employee structure: Chief Operating Officer
(CEO), Chief Technology Officer (CTO), Principal Data Scientist, Database Administrator,
Senior Cyber Network Analyst, and Mid-Level Cyber Network Analyst. Since MakeBelieve is a
small NaaS service provider, it is essential that the organization’s members collaborate and
maintain multiple roles within the organization. Table 1 provides a basic breakdown of the
responsibilities of organization members. As a growing organization, responsibilities are wide
ranging and often times overlap with the duties of other members of the organization.
Table 1: MakeBelieve (MB) Roles and Responsibilities
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Role Responsibility
Chief Executive Officer
(CEO)
Responsible for developing and implementing the long-term
strategy of the organization
Chief Technology Officer
(CTO)
Responsible for technical and scientific components of
organization development
Database Administrator Responsible for managing and maintaining various database
systems
Principal Data Scientist Responsible for developing Machine learning algorithms
that can be used to process data within the company
Senior Cyber Network
Analyst
Provides direct leadership to Cyber Analyst Team
Cyber Network Analyst Analyzes network traffic behavior and provides real-time
analyses for customers
Operations Staff Manages the daily operations of MB
As presented in Table 1, the division of responsibility among members of MB is quite diverse.
As an organization, the CEO is responsible for developing and implementing the long-term
strategy of the organization. Given the relatively small stature of our organization, the CEO is
also responsible for ensuring the financial longevity of the company. Within the organization, the
CTO is responsible for overseeing the technical implementation of new technologies and
techniques within the organization. As the company continues to grow within the emerging cloud
market, the CTO is responsible for understanding and harnessing these emerging cloud
technologies for our customers. Outside of the executive personnel, MB relies heavily upon its
operations team to provide top quality service and spur the growth of our organization.
The Principal Data Scientist is primarily concerned with developing and optimizing the various
machine learning algorithms that are implemented to process the network data in real-time. The
role of the Data Scientist is essential, as the algorithms that are used to process network activity
must constantly be optimized as new patterns emerge.
4
Chief Executive Officer
(CEO)
Responsible for developing and implementing the long-term
strategy of the organization
Chief Technology Officer
(CTO)
Responsible for technical and scientific components of
organization development
Database Administrator Responsible for managing and maintaining various database
systems
Principal Data Scientist Responsible for developing Machine learning algorithms
that can be used to process data within the company
Senior Cyber Network
Analyst
Provides direct leadership to Cyber Analyst Team
Cyber Network Analyst Analyzes network traffic behavior and provides real-time
analyses for customers
Operations Staff Manages the daily operations of MB
As presented in Table 1, the division of responsibility among members of MB is quite diverse.
As an organization, the CEO is responsible for developing and implementing the long-term
strategy of the organization. Given the relatively small stature of our organization, the CEO is
also responsible for ensuring the financial longevity of the company. Within the organization, the
CTO is responsible for overseeing the technical implementation of new technologies and
techniques within the organization. As the company continues to grow within the emerging cloud
market, the CTO is responsible for understanding and harnessing these emerging cloud
technologies for our customers. Outside of the executive personnel, MB relies heavily upon its
operations team to provide top quality service and spur the growth of our organization.
The Principal Data Scientist is primarily concerned with developing and optimizing the various
machine learning algorithms that are implemented to process the network data in real-time. The
role of the Data Scientist is essential, as the algorithms that are used to process network activity
must constantly be optimized as new patterns emerge.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The Database Administrator manages the databases throughout the organization by creating,
modifying and updating the organization’s tables while ensuring the integrity of the data. As an
analytics company, which uses data to develop a platform for our service, we are highly
dependent upon the work of our Database Administrator to assist with developing and
maintaining our database system. The Database Administrator also is the responsible for
configuring our database and ensuring that the integrity of the data is maintained.
The Senior Cyber Network Analyst is responsible for coordinating the overall customer efforts
of the Cyber Network Analyst. The Senior Cyber Analyst is also responsible for overseeing the
work and activities of the more junior cyber analyst. Finally, Cyber Network Analysts are
responsible for analyzing the network activities and relaying their insights to customers. The
Operations staff assist in maintaining the daily operations of the MB organization.
3. Network Topology
Diagram 1: MakeBelieve External Network Topology
5
modifying and updating the organization’s tables while ensuring the integrity of the data. As an
analytics company, which uses data to develop a platform for our service, we are highly
dependent upon the work of our Database Administrator to assist with developing and
maintaining our database system. The Database Administrator also is the responsible for
configuring our database and ensuring that the integrity of the data is maintained.
The Senior Cyber Network Analyst is responsible for coordinating the overall customer efforts
of the Cyber Network Analyst. The Senior Cyber Analyst is also responsible for overseeing the
work and activities of the more junior cyber analyst. Finally, Cyber Network Analysts are
responsible for analyzing the network activities and relaying their insights to customers. The
Operations staff assist in maintaining the daily operations of the MB organization.
3. Network Topology
Diagram 1: MakeBelieve External Network Topology
5
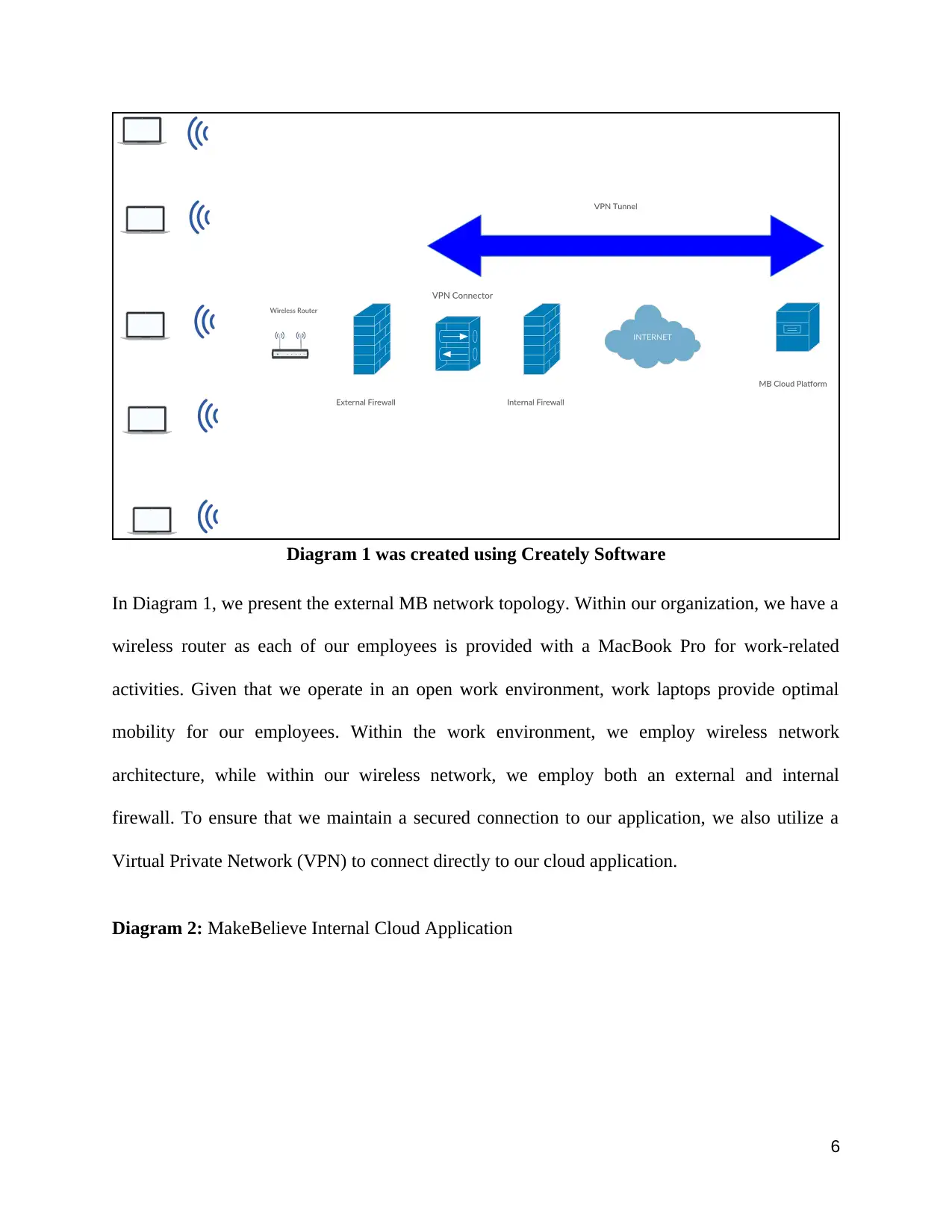
Diagram 1 was created using Creately Software
In Diagram 1, we present the external MB network topology. Within our organization, we have a
wireless router as each of our employees is provided with a MacBook Pro for work-related
activities. Given that we operate in an open work environment, work laptops provide optimal
mobility for our employees. Within the work environment, we employ wireless network
architecture, while within our wireless network, we employ both an external and internal
firewall. To ensure that we maintain a secured connection to our application, we also utilize a
Virtual Private Network (VPN) to connect directly to our cloud application.
Diagram 2: MakeBelieve Internal Cloud Application
6
In Diagram 1, we present the external MB network topology. Within our organization, we have a
wireless router as each of our employees is provided with a MacBook Pro for work-related
activities. Given that we operate in an open work environment, work laptops provide optimal
mobility for our employees. Within the work environment, we employ wireless network
architecture, while within our wireless network, we employ both an external and internal
firewall. To ensure that we maintain a secured connection to our application, we also utilize a
Virtual Private Network (VPN) to connect directly to our cloud application.
Diagram 2: MakeBelieve Internal Cloud Application
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

(ConceptDraw 2017)
Diagram 2 highlights the architecture of the MakeBelieve Cloud application. Within our
application, we utilize a full AWS cloud platform suite. Our organization opted for the private
cloud suite to allow for optimal control of our platform and to provide the greatest means of
control over our platform application. For our base infrastructure, we use the AWS cloud
application with the cloud application using an AWS Infrastructure-as-a-Service (IaaS) to host
our various databases as well as provide the computational resources for our application. As we
are a growing analytics company, the flexibility provided by IaaS offers unique opportunities for
growth as we only pay for the infrastructure services that we use. As the cloud platform is our
platform of choice, we must be cognizant of the security risks that are associated with the
platform.
7
Diagram 2 highlights the architecture of the MakeBelieve Cloud application. Within our
application, we utilize a full AWS cloud platform suite. Our organization opted for the private
cloud suite to allow for optimal control of our platform and to provide the greatest means of
control over our platform application. For our base infrastructure, we use the AWS cloud
application with the cloud application using an AWS Infrastructure-as-a-Service (IaaS) to host
our various databases as well as provide the computational resources for our application. As we
are a growing analytics company, the flexibility provided by IaaS offers unique opportunities for
growth as we only pay for the infrastructure services that we use. As the cloud platform is our
platform of choice, we must be cognizant of the security risks that are associated with the
platform.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In Table 2, we highlight the various tables that are used throughout our organization. The first
database is MB_Customers, which contains data directly related to the customers. This table is
mostly used to assist with business related analysis. The next table used within our
organizational database is the Services_Provided table. This table contains data related to the
current services provided to our customers. MB uses this table to run analysis regarding the
outlook of our company. The next table in the database is Network_Packet_Data. This table
breaks down the data related to the network packets that are passing through our customer
network layer. Our data scientist uses this table to feed through the algorithms to describe how
activity patterns are flowing for our customers. The last data table within our database is the
Customers_Network_Activity table. Within this table, we house information directly related to
the network activity on our customer's pages. This table is often used in coordination with the
Network_Packet_Table to provide more detailed analyst-led conversations with our customers.
Table 2: MakeBelieve Database Tables
MB_Customers Services_Provided Network_Packet_Data Customers_Networ
k_Activity
Customer_Name SP_Provided Port_Number IP_Address
Customer_Industry Tier_Type Protocol_Number Time_Of_Visit
Active_Account Contract_Length File_Attached_Y_N Target_Page
Customer_Type Packet_Data Last_Page_Visited
SP_Provided IP_Location
Contact_Info
4. Database Access
Table 3: Employee Access Privileges
Role MB_Customers_
Info
Services_Provi
ded
Network_Packet_
Data
Customers_Network_A
ctivity
8
database is MB_Customers, which contains data directly related to the customers. This table is
mostly used to assist with business related analysis. The next table used within our
organizational database is the Services_Provided table. This table contains data related to the
current services provided to our customers. MB uses this table to run analysis regarding the
outlook of our company. The next table in the database is Network_Packet_Data. This table
breaks down the data related to the network packets that are passing through our customer
network layer. Our data scientist uses this table to feed through the algorithms to describe how
activity patterns are flowing for our customers. The last data table within our database is the
Customers_Network_Activity table. Within this table, we house information directly related to
the network activity on our customer's pages. This table is often used in coordination with the
Network_Packet_Table to provide more detailed analyst-led conversations with our customers.
Table 2: MakeBelieve Database Tables
MB_Customers Services_Provided Network_Packet_Data Customers_Networ
k_Activity
Customer_Name SP_Provided Port_Number IP_Address
Customer_Industry Tier_Type Protocol_Number Time_Of_Visit
Active_Account Contract_Length File_Attached_Y_N Target_Page
Customer_Type Packet_Data Last_Page_Visited
SP_Provided IP_Location
Contact_Info
4. Database Access
Table 3: Employee Access Privileges
Role MB_Customers_
Info
Services_Provi
ded
Network_Packet_
Data
Customers_Network_A
ctivity
8
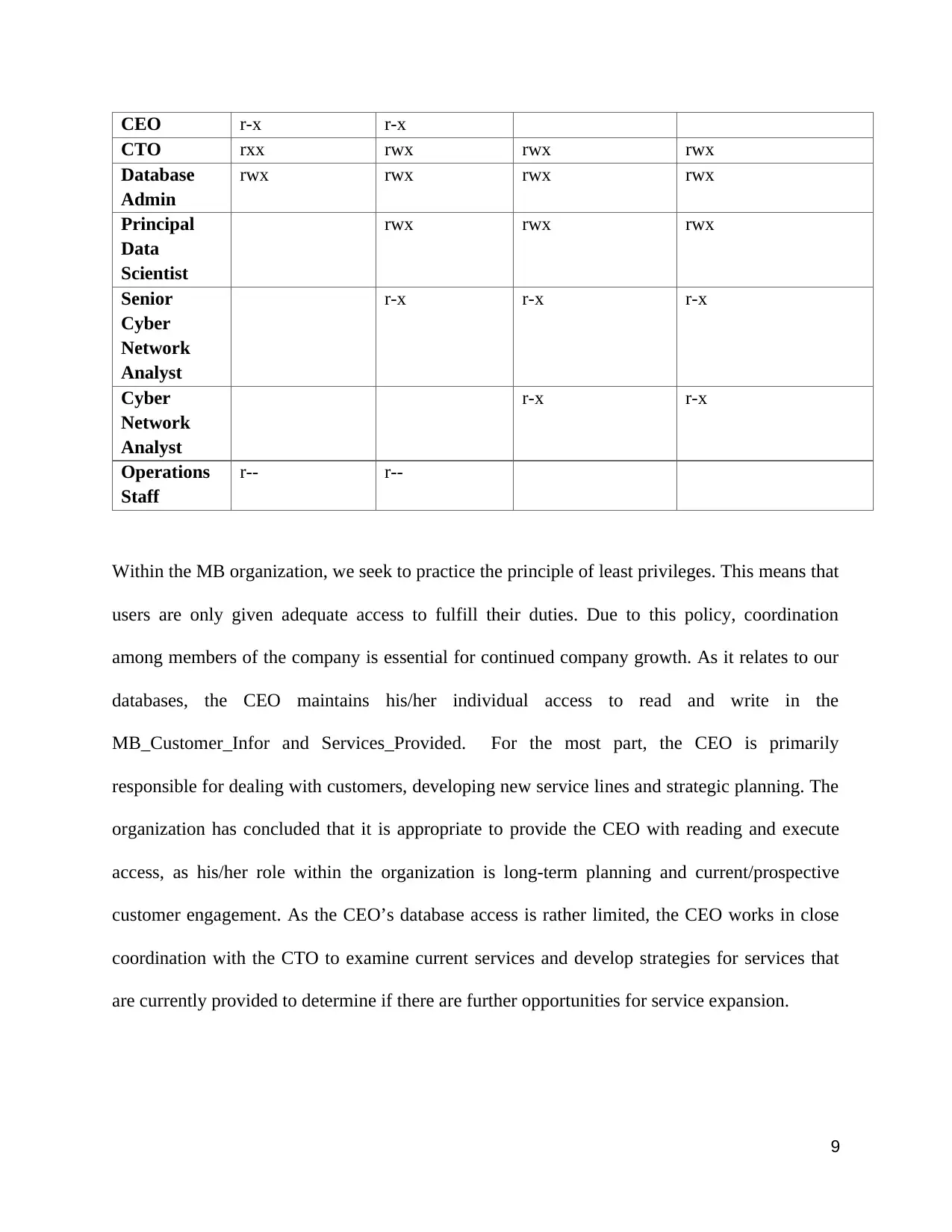
CEO r-x r-x
CTO rxx rwx rwx rwx
Database
Admin
rwx rwx rwx rwx
Principal
Data
Scientist
rwx rwx rwx
Senior
Cyber
Network
Analyst
r-x r-x r-x
Cyber
Network
Analyst
r-x r-x
Operations
Staff
r-- r--
Within the MB organization, we seek to practice the principle of least privileges. This means that
users are only given adequate access to fulfill their duties. Due to this policy, coordination
among members of the company is essential for continued company growth. As it relates to our
databases, the CEO maintains his/her individual access to read and write in the
MB_Customer_Infor and Services_Provided. For the most part, the CEO is primarily
responsible for dealing with customers, developing new service lines and strategic planning. The
organization has concluded that it is appropriate to provide the CEO with reading and execute
access, as his/her role within the organization is long-term planning and current/prospective
customer engagement. As the CEO’s database access is rather limited, the CEO works in close
coordination with the CTO to examine current services and develop strategies for services that
are currently provided to determine if there are further opportunities for service expansion.
9
CTO rxx rwx rwx rwx
Database
Admin
rwx rwx rwx rwx
Principal
Data
Scientist
rwx rwx rwx
Senior
Cyber
Network
Analyst
r-x r-x r-x
Cyber
Network
Analyst
r-x r-x
Operations
Staff
r-- r--
Within the MB organization, we seek to practice the principle of least privileges. This means that
users are only given adequate access to fulfill their duties. Due to this policy, coordination
among members of the company is essential for continued company growth. As it relates to our
databases, the CEO maintains his/her individual access to read and write in the
MB_Customer_Infor and Services_Provided. For the most part, the CEO is primarily
responsible for dealing with customers, developing new service lines and strategic planning. The
organization has concluded that it is appropriate to provide the CEO with reading and execute
access, as his/her role within the organization is long-term planning and current/prospective
customer engagement. As the CEO’s database access is rather limited, the CEO works in close
coordination with the CTO to examine current services and develop strategies for services that
are currently provided to determine if there are further opportunities for service expansion.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Within the organization, the CTO is one of two individuals within the organization with full
access to all the databases. We determined that it would be most appropriate to provide the CTO
with full access rights as they are responsible for both handling corporate responsibilities as well
as ensuring that the current technologies and algorithms being deployed within the organization
are optimized for the clients’ needs.
The Database Administrator has full read, write and execute access to all databases within the
organization. This is because he/she is fully responsible for developing and maintaining of all
our database systems. Within each table, the Database Administrator has read, write and execute
privileges. This individual works in close coordination with the CTO, Data Scientist and Senior
Cyber Analyst to develop new table schemas that could assist the team in providing effective
customer service.
One of the most central figures in the MB organization is our Principal Data Scientist. Within
this role, the Principal Data Science is responsible for reviewing and developing new algorithms
that are used by our Cyber Analyst team to establish patterns in networking behaviors. The
Principal Data Scientist has read, write and execute access to the following tables:
Services_Provided table, Network_Packet_Data, and the Customers_Network_Activity table.
The access provided to our Data Scientist is as in the previously mentioned table that provides
opportunities for algorithm development and maintenance.
The Cyber Analyst team is the most customer-facing component of our organization. These
individuals are directly responsible for providing weekly reports on networking activities for
customers. As these are regular meetings, the cyber analyst team conducts standing meetings on
10
access to all the databases. We determined that it would be most appropriate to provide the CTO
with full access rights as they are responsible for both handling corporate responsibilities as well
as ensuring that the current technologies and algorithms being deployed within the organization
are optimized for the clients’ needs.
The Database Administrator has full read, write and execute access to all databases within the
organization. This is because he/she is fully responsible for developing and maintaining of all
our database systems. Within each table, the Database Administrator has read, write and execute
privileges. This individual works in close coordination with the CTO, Data Scientist and Senior
Cyber Analyst to develop new table schemas that could assist the team in providing effective
customer service.
One of the most central figures in the MB organization is our Principal Data Scientist. Within
this role, the Principal Data Science is responsible for reviewing and developing new algorithms
that are used by our Cyber Analyst team to establish patterns in networking behaviors. The
Principal Data Scientist has read, write and execute access to the following tables:
Services_Provided table, Network_Packet_Data, and the Customers_Network_Activity table.
The access provided to our Data Scientist is as in the previously mentioned table that provides
opportunities for algorithm development and maintenance.
The Cyber Analyst team is the most customer-facing component of our organization. These
individuals are directly responsible for providing weekly reports on networking activities for
customers. As these are regular meetings, the cyber analyst team conducts standing meetings on
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Monday to review activity from the previous week. As the most customer-facing component of
our organization, the Senior Cyber Analyst has read and executed access to the
Services_Provided table, the Network_Packet_Data, and the Customers_Network_Activity table.
The non-senior members of the Cyber Analyst team have read and executed access to the the
Network_Packet_Data table and the Customers_Network_Activity table.
5. Platform Threats, Risks, and Vulnerabilities
As cloud platforms continue to grow in popularity, the relative risks associated with them also
continues to grow. According to a 2016 report released by Cloud Security Alliance, there are
Data Breaches, weak identity credential, insecure APi’s, application hijacking and data loss were
considered to be some of the biggest threats to cloud platforms (CSA 2016). Given the increasing
risks associated with cloud applications, MB has a sought to take additional steps to ensure the
integrity of our platform. In the report entitled, “MakeBelieve L.L.C. Cyber Risk Assessment
Report”, MB outlines further outlines the risks associated with our system as well as the steps
that MB has taken to mitigate that risk.
Table 4: Cloud Threat Types
Threat Type Description
Data breaches the incident where information is released without
proper approval or authorization to do so
Weak identity Credentials instances where authorized uses do not have strong
credentials to log into the site
11
our organization, the Senior Cyber Analyst has read and executed access to the
Services_Provided table, the Network_Packet_Data, and the Customers_Network_Activity table.
The non-senior members of the Cyber Analyst team have read and executed access to the the
Network_Packet_Data table and the Customers_Network_Activity table.
5. Platform Threats, Risks, and Vulnerabilities
As cloud platforms continue to grow in popularity, the relative risks associated with them also
continues to grow. According to a 2016 report released by Cloud Security Alliance, there are
Data Breaches, weak identity credential, insecure APi’s, application hijacking and data loss were
considered to be some of the biggest threats to cloud platforms (CSA 2016). Given the increasing
risks associated with cloud applications, MB has a sought to take additional steps to ensure the
integrity of our platform. In the report entitled, “MakeBelieve L.L.C. Cyber Risk Assessment
Report”, MB outlines further outlines the risks associated with our system as well as the steps
that MB has taken to mitigate that risk.
Table 4: Cloud Threat Types
Threat Type Description
Data breaches the incident where information is released without
proper approval or authorization to do so
Weak identity Credentials instances where authorized uses do not have strong
credentials to log into the site
11

System and application
vulnerability
instance where there are exploitable issues within
the code base for the system
Account hijacking the incident where a user an attack form to gain
control of the credentials of a verified user
Denial of service incident when illegitimate traffic is used to remove
availability of a website
MB Auditing
System auditing is considered the systematic process of reviewing internal records and
documentation to determine if company employees or software are adhering to predetermined
criteria. As MB is contractually obligated to perform regular audits of the MB, we have outlined
our policy in the MB System Audit attachment.
12
vulnerability
instance where there are exploitable issues within
the code base for the system
Account hijacking the incident where a user an attack form to gain
control of the credentials of a verified user
Denial of service incident when illegitimate traffic is used to remove
availability of a website
MB Auditing
System auditing is considered the systematic process of reviewing internal records and
documentation to determine if company employees or software are adhering to predetermined
criteria. As MB is contractually obligated to perform regular audits of the MB, we have outlined
our policy in the MB System Audit attachment.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
