Analysis of Recent Trends in Malware and Security Threats: A Report
VerifiedAdded on 2020/03/23
|13
|2780
|336
Report
AI Summary
This report provides a comprehensive overview of recent trends in malware attacks, highlighting the evolving threat landscape. It begins by defining malware and its various types, including viruses, worms, Trojan horses, spyware, adware, and ransomware. The report then delves into current trends, such as the WannaCry attack, browser setting modifications, and the increasing number of malware families, particularly targeting mobile devices. It explores the challenges posed by malware, including the human factor, threats to mobile devices, and the rise of botnets. Relevant technologies like USB drives and the internet's role in malware distribution are also discussed. The report identifies issues not fully addressed, such as ransomware attacks, and emphasizes the importance of implementing strong security measures, using updated software, and practicing safe online behavior to prevent malware infections. The report concludes by summarizing the key findings and reiterating the need for proactive cybersecurity strategies in the face of rapidly evolving threats. The report is contributed by a student to be published on the website Desklib. Desklib is a platform which provides all the necessary AI based study tools for students.

Running head: RECENT TRENDS IN MALWARE
Recent Trends in Malware
Name of the Student
Name of the University
Author’s note
Recent Trends in Malware
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
RECENT TRENDS IN MALWARE
Executive Summary
This report discusses about the recent trends of the malware attacks that are taking place in this
era of technology. Malware attacks have become a serious security threat and a major concern
for the people. There are several types of malware attacks like viruses and ransomware. This
report has described the recent malware attack called WannaCry attack that took place in the
month of May, 2017. This report gave an overview of the challenges that are faced and the
relevant technologies like USB and Internet that play a major role in the malware attack. This
report also discussed about the lesson learnt regarding prevention of malware attacks.
RECENT TRENDS IN MALWARE
Executive Summary
This report discusses about the recent trends of the malware attacks that are taking place in this
era of technology. Malware attacks have become a serious security threat and a major concern
for the people. There are several types of malware attacks like viruses and ransomware. This
report has described the recent malware attack called WannaCry attack that took place in the
month of May, 2017. This report gave an overview of the challenges that are faced and the
relevant technologies like USB and Internet that play a major role in the malware attack. This
report also discussed about the lesson learnt regarding prevention of malware attacks.

2
RECENT TRENDS IN MALWARE
Table of Contents
Introduction..........................................................................................................................3
Discussion............................................................................................................................3
Malware and its Types.....................................................................................................3
Recent Trends in Malware...............................................................................................4
Challenges and Problems.................................................................................................7
Relevant Technologies and its Applications in Malware................................................8
Issues Discussed..............................................................................................................8
Important Issues that are not addressed and its impact....................................................9
Important Lessons............................................................................................................9
Conclusion.........................................................................................................................10
References..........................................................................................................................11
RECENT TRENDS IN MALWARE
Table of Contents
Introduction..........................................................................................................................3
Discussion............................................................................................................................3
Malware and its Types.....................................................................................................3
Recent Trends in Malware...............................................................................................4
Challenges and Problems.................................................................................................7
Relevant Technologies and its Applications in Malware................................................8
Issues Discussed..............................................................................................................8
Important Issues that are not addressed and its impact....................................................9
Important Lessons............................................................................................................9
Conclusion.........................................................................................................................10
References..........................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
RECENT TRENDS IN MALWARE
Introduction
Malware or malicious software is a type of deliberate security threat. It has been designed
by the attacker with a malicious intention. Malware can harm and damage the system or network
in which it is injected (Uscilowski, 2013). Malware is capable of disrupting or denying
operations, exploiting vulnerabilities and gaining unauthorized access to the victim’s system. In
this era of ICT, malware threats are increasing at a fast pace. The developers of malware are
finding various advanced techniques for preventing or bypassing detection.
This report discusses about the recent trends in malware. It gives an overview about the
various types of malware that are present in the current market. This report also discusses about
the relevant technologies that play a major role in malware attacks and also figure outs its
application. This report discusses about the missed out issues that are not given much
importance. It also gives a brief explanation about the significance of these issues. This report
also talks about the lessons that are learnt from the recent trends in malware.
Discussion
Malware and its Types
Malware is one of the most important and harmful security threats in the present
generation (Wang, Streff & Raman, 2012). It is a malicious code that is injected in a system to
gain unauthorized access to sensitive and valuable data in order to gain money or harm the user.
There are various types of malware like:
RECENT TRENDS IN MALWARE
Introduction
Malware or malicious software is a type of deliberate security threat. It has been designed
by the attacker with a malicious intention. Malware can harm and damage the system or network
in which it is injected (Uscilowski, 2013). Malware is capable of disrupting or denying
operations, exploiting vulnerabilities and gaining unauthorized access to the victim’s system. In
this era of ICT, malware threats are increasing at a fast pace. The developers of malware are
finding various advanced techniques for preventing or bypassing detection.
This report discusses about the recent trends in malware. It gives an overview about the
various types of malware that are present in the current market. This report also discusses about
the relevant technologies that play a major role in malware attacks and also figure outs its
application. This report discusses about the missed out issues that are not given much
importance. It also gives a brief explanation about the significance of these issues. This report
also talks about the lessons that are learnt from the recent trends in malware.
Discussion
Malware and its Types
Malware is one of the most important and harmful security threats in the present
generation (Wang, Streff & Raman, 2012). It is a malicious code that is injected in a system to
gain unauthorized access to sensitive and valuable data in order to gain money or harm the user.
There are various types of malware like:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
RECENT TRENDS IN MALWARE
Viruses: This is a piece of executable code or program that can be run on a system
without its permission (Zhou & Jiang, 2012). This is executed in a secret manner so that the
system is unaware of it. Viruses do not have the capability to duplicate on its own
Worms: These have the capability to replicate unlike viruses. Worms generally take the
help of a network to send its copies to the other systems that are present in the same network
(Gandotra, Bansal & Sofat, 2014). They are considered to be malignant in nature and consume
huge network bandwidth.
Trojan Horses: These are applications that appear as legitimate and useful applications
but have hidden malicious codes inside them. They can pretend that they are scanning to find any
spyware but they are actually stealing personal details from the system.
Spyware: This is a type of malware that acts as a spy and collects data from the system in
a hidden manner. It monitors the system without letting the user know about it.
Adware: This is advertisement software that plays in an automatic manner and displays
different types of advertisements in the system. Adware is developed for the purpose of
generating revenue for the author of the software.
Ransomware: This is a type of malicious code that blocks the user to access sensitive
information and releases the data only after a ransom amount of money is paid (O'Gorman &
McDonald, 2012).
Recent Trends in Malware
The security concerns relating to malware is increasing with a fast pace in the recent
times. The incidents related to malware attacks are increasing by a huge margin. The design of
RECENT TRENDS IN MALWARE
Viruses: This is a piece of executable code or program that can be run on a system
without its permission (Zhou & Jiang, 2012). This is executed in a secret manner so that the
system is unaware of it. Viruses do not have the capability to duplicate on its own
Worms: These have the capability to replicate unlike viruses. Worms generally take the
help of a network to send its copies to the other systems that are present in the same network
(Gandotra, Bansal & Sofat, 2014). They are considered to be malignant in nature and consume
huge network bandwidth.
Trojan Horses: These are applications that appear as legitimate and useful applications
but have hidden malicious codes inside them. They can pretend that they are scanning to find any
spyware but they are actually stealing personal details from the system.
Spyware: This is a type of malware that acts as a spy and collects data from the system in
a hidden manner. It monitors the system without letting the user know about it.
Adware: This is advertisement software that plays in an automatic manner and displays
different types of advertisements in the system. Adware is developed for the purpose of
generating revenue for the author of the software.
Ransomware: This is a type of malicious code that blocks the user to access sensitive
information and releases the data only after a ransom amount of money is paid (O'Gorman &
McDonald, 2012).
Recent Trends in Malware
The security concerns relating to malware is increasing with a fast pace in the recent
times. The incidents related to malware attacks are increasing by a huge margin. The design of

5
RECENT TRENDS IN MALWARE
the evasive malware is to aggressively harm the systems. There are vulnerabilities in the two
factor method of authentication in the mobile phones. The mobile phone attacks are increasing
with time. There are several cloud leakages due to malware attacks. There is a chance of Monero
ransomware that will appear in the recent future. The developers of malware are trying to use
the code signing approach. These developers try to obtain a valid certificate to enter the systems.
The recent ransomware attack called WannaCry hit around 100 countries in the world including
Egypt, Spain, India, China as well as UK (Mohurle & Patil, 2017). Around 1000 computers
were affected in Russia. The name of the malicious software that was used in this attack is called
WannaCry or WanaCryptor 2.0. It demanded 300 dollars of Bitcoin from the users. This has
been the most harmful and recent malware attack that took place in the month of May, 2017.
One of the most recent trends that have been observed in the last few years is the
modification of the browser settings. Malware attacks have modified the settings of the browsers
like Google Chrome, Opera, Safari and Internet Explorer. Most of the malware attempted to
change the proxy settings of the users. The recent trends have observed a malware that tried to
crack weak passwords to enter the system. The malware family is increasing with time. The
malware families have increased by sixty nine per cent between the year 2012 and 2013
(Uscilowski, 2013). There were around 121 android malware families in 2012 which became 204
in the year 2013.
RECENT TRENDS IN MALWARE
the evasive malware is to aggressively harm the systems. There are vulnerabilities in the two
factor method of authentication in the mobile phones. The mobile phone attacks are increasing
with time. There are several cloud leakages due to malware attacks. There is a chance of Monero
ransomware that will appear in the recent future. The developers of malware are trying to use
the code signing approach. These developers try to obtain a valid certificate to enter the systems.
The recent ransomware attack called WannaCry hit around 100 countries in the world including
Egypt, Spain, India, China as well as UK (Mohurle & Patil, 2017). Around 1000 computers
were affected in Russia. The name of the malicious software that was used in this attack is called
WannaCry or WanaCryptor 2.0. It demanded 300 dollars of Bitcoin from the users. This has
been the most harmful and recent malware attack that took place in the month of May, 2017.
One of the most recent trends that have been observed in the last few years is the
modification of the browser settings. Malware attacks have modified the settings of the browsers
like Google Chrome, Opera, Safari and Internet Explorer. Most of the malware attempted to
change the proxy settings of the users. The recent trends have observed a malware that tried to
crack weak passwords to enter the system. The malware family is increasing with time. The
malware families have increased by sixty nine per cent between the year 2012 and 2013
(Uscilowski, 2013). There were around 121 android malware families in 2012 which became 204
in the year 2013.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
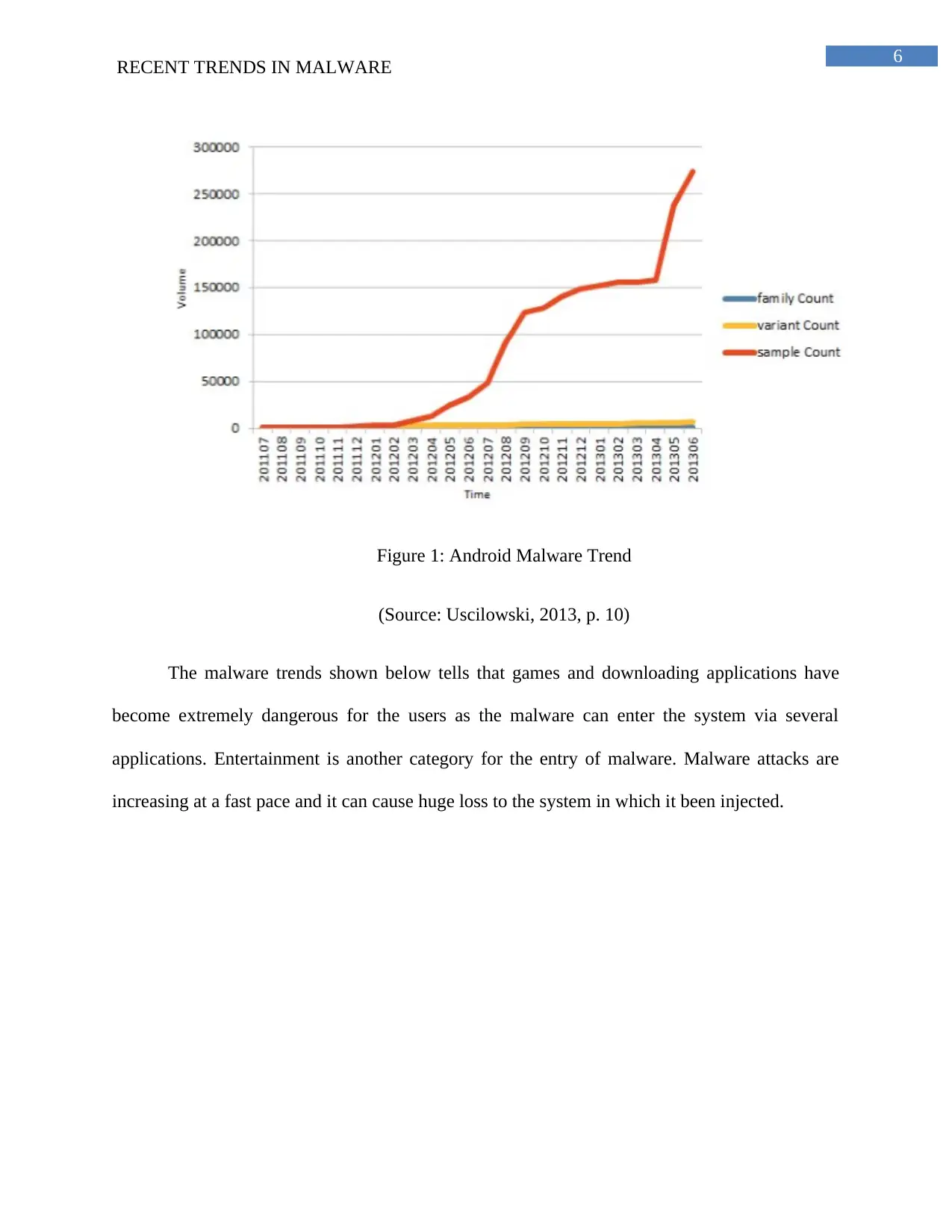
6
RECENT TRENDS IN MALWARE
Figure 1: Android Malware Trend
(Source: Uscilowski, 2013, p. 10)
The malware trends shown below tells that games and downloading applications have
become extremely dangerous for the users as the malware can enter the system via several
applications. Entertainment is another category for the entry of malware. Malware attacks are
increasing at a fast pace and it can cause huge loss to the system in which it been injected.
RECENT TRENDS IN MALWARE
Figure 1: Android Malware Trend
(Source: Uscilowski, 2013, p. 10)
The malware trends shown below tells that games and downloading applications have
become extremely dangerous for the users as the malware can enter the system via several
applications. Entertainment is another category for the entry of malware. Malware attacks are
increasing at a fast pace and it can cause huge loss to the system in which it been injected.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
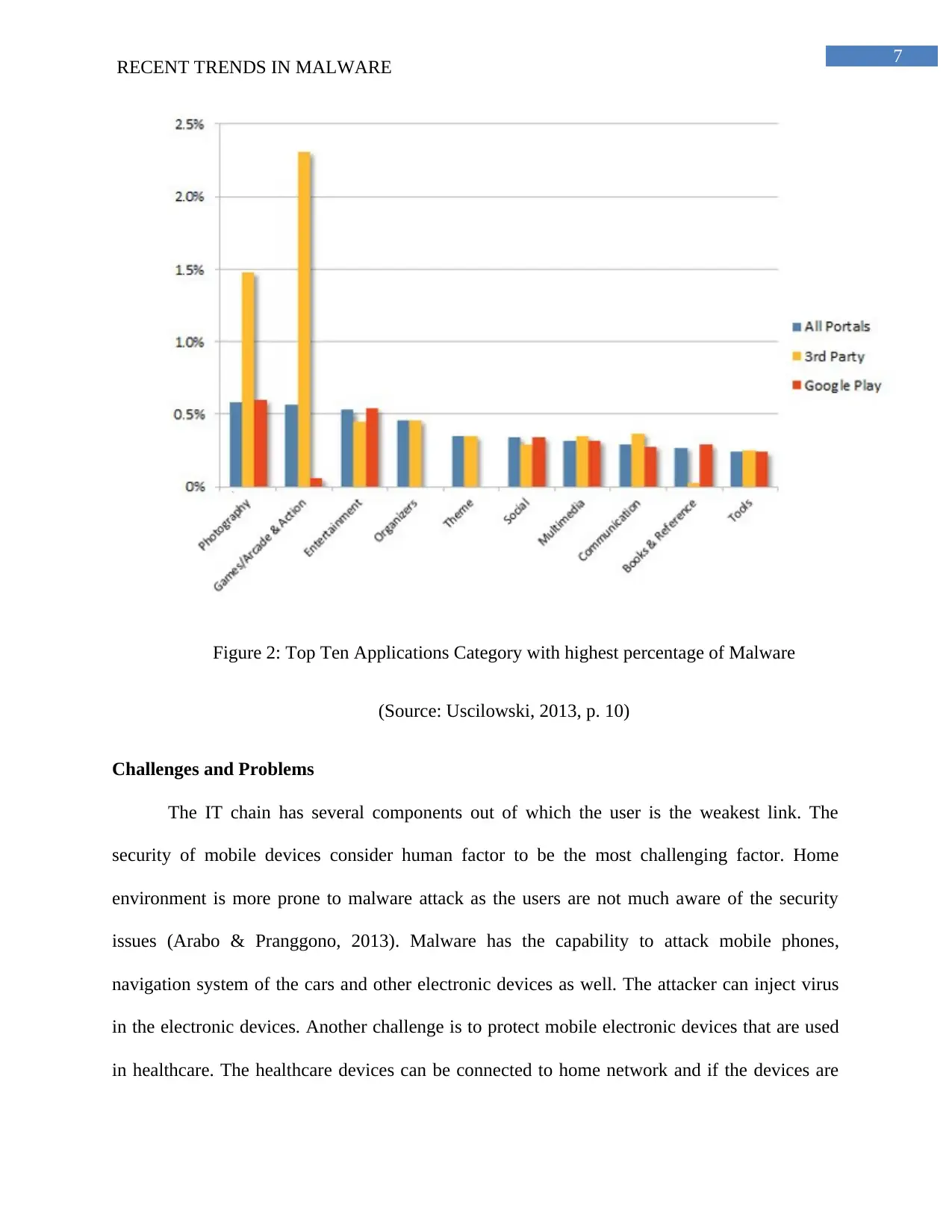
7
RECENT TRENDS IN MALWARE
Figure 2: Top Ten Applications Category with highest percentage of Malware
(Source: Uscilowski, 2013, p. 10)
Challenges and Problems
The IT chain has several components out of which the user is the weakest link. The
security of mobile devices consider human factor to be the most challenging factor. Home
environment is more prone to malware attack as the users are not much aware of the security
issues (Arabo & Pranggono, 2013). Malware has the capability to attack mobile phones,
navigation system of the cars and other electronic devices as well. The attacker can inject virus
in the electronic devices. Another challenge is to protect mobile electronic devices that are used
in healthcare. The healthcare devices can be connected to home network and if the devices are
RECENT TRENDS IN MALWARE
Figure 2: Top Ten Applications Category with highest percentage of Malware
(Source: Uscilowski, 2013, p. 10)
Challenges and Problems
The IT chain has several components out of which the user is the weakest link. The
security of mobile devices consider human factor to be the most challenging factor. Home
environment is more prone to malware attack as the users are not much aware of the security
issues (Arabo & Pranggono, 2013). Malware has the capability to attack mobile phones,
navigation system of the cars and other electronic devices as well. The attacker can inject virus
in the electronic devices. Another challenge is to protect mobile electronic devices that are used
in healthcare. The healthcare devices can be connected to home network and if the devices are

8
RECENT TRENDS IN MALWARE
not properly secured then they can transmit data to attacker who can change the device settings
leading to harmful consequences. The device can get reconfigured. Most of the people perform
online transactions. The attacker can access the financial details of the user and gain money.
Some of the malware attacks sends message and charges premium. Botnet is considered to be a
major challenge. These are responsible for sending spam emails, DDoS attacks and hosting of
malware as well as phishing sites. These are targeting mobile devices in the recent times. The
mobile devices do not incorporate strong security features in its system and this is increasing the
rate of malware attacks.
Relevant Technologies and its Applications in Malware
Universal serial bus or USB sticks play a major role in spreading malware from one
device to another. USB has the capability to harm systems that are not part of any unsecured
network (Poeplau & Gassen, 2012). Users transfer files from one computer to another without
understanding about the spread of malware that is taking place. The devices that are trusted
should not be connected to any USB because it might harm the data which is present in the
system. Internet technology plays a significant role in spreading malware from one device to
another (Chen et al., 2012). Malicious codes can be present in a file that is downloaded by the
user in its system. Emails can be infected with malware and opening these types of email can
inject malware in the system. The emergence and growth of ICT have paved a way for malware
attacks.
Issues Discussed
The issues that have been discussed are related to mobile malware and the malware
attacks that take place in smart devices. Botnets are a type of malware attack that is responsible
for sending email spam and carrying out DDoS (Arabo & Pranggono, 2013). These are
RECENT TRENDS IN MALWARE
not properly secured then they can transmit data to attacker who can change the device settings
leading to harmful consequences. The device can get reconfigured. Most of the people perform
online transactions. The attacker can access the financial details of the user and gain money.
Some of the malware attacks sends message and charges premium. Botnet is considered to be a
major challenge. These are responsible for sending spam emails, DDoS attacks and hosting of
malware as well as phishing sites. These are targeting mobile devices in the recent times. The
mobile devices do not incorporate strong security features in its system and this is increasing the
rate of malware attacks.
Relevant Technologies and its Applications in Malware
Universal serial bus or USB sticks play a major role in spreading malware from one
device to another. USB has the capability to harm systems that are not part of any unsecured
network (Poeplau & Gassen, 2012). Users transfer files from one computer to another without
understanding about the spread of malware that is taking place. The devices that are trusted
should not be connected to any USB because it might harm the data which is present in the
system. Internet technology plays a significant role in spreading malware from one device to
another (Chen et al., 2012). Malicious codes can be present in a file that is downloaded by the
user in its system. Emails can be infected with malware and opening these types of email can
inject malware in the system. The emergence and growth of ICT have paved a way for malware
attacks.
Issues Discussed
The issues that have been discussed are related to mobile malware and the malware
attacks that take place in smart devices. Botnets are a type of malware attack that is responsible
for sending email spam and carrying out DDoS (Arabo & Pranggono, 2013). These are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
RECENT TRENDS IN MALWARE
responsible for hosting malware as well as phishing sites. The malicious codes can run in any
electronic devices to misuse the sensitive data (Chandramohan & Tan, 2012). The reasons
behind attacking mobile devices are its computational powers, ubiquity, use of rooted devices
and these devices operate on open platforms. ZeuS botnet is a banking malware that has targeted
different mobile platforms like iPhones, Symbian devices and Blackberry devices (Etaher, Weir
& Alazab, 2015). It is considered to be the most dangerous banking malware in the financial
sector.
Important Issues that are not addressed and its impact
Ransomware attacks have not been discussed in the literature review. Ransomware
attacks are malware attacks that lock the access to the data of the system and also threaten to
remove or delete all the documents present in the system if the users fail to pay a ransom amount
(Mercaldo et al., 2016). The users are generally asked to pay the ransom in Bitcoins. The
attacker after receiving the Bitcoin gives the decryption key to the users. Ransomware can enter
the systems through attached files that have malicious codes inside them. Malicious websites can
also cause ransomware attacks. These attacks can cause permanent or temporary loss of valuable
information, disrupt regular or daily operations and cause potential damage to the reputation of
an organization. The victim will even face financial loss in the course of recovering and restoring
the system.
Important Lessons
The malware attacks can be prevented by incorporating strong and advanced security
architecture in the electronic devices and systems. Updated and latest versions of the operating
system must be used. The users must download and install only those applications that have been
downloaded by most of the people. The system must have Anti-Virus software downloaded in it
RECENT TRENDS IN MALWARE
responsible for hosting malware as well as phishing sites. The malicious codes can run in any
electronic devices to misuse the sensitive data (Chandramohan & Tan, 2012). The reasons
behind attacking mobile devices are its computational powers, ubiquity, use of rooted devices
and these devices operate on open platforms. ZeuS botnet is a banking malware that has targeted
different mobile platforms like iPhones, Symbian devices and Blackberry devices (Etaher, Weir
& Alazab, 2015). It is considered to be the most dangerous banking malware in the financial
sector.
Important Issues that are not addressed and its impact
Ransomware attacks have not been discussed in the literature review. Ransomware
attacks are malware attacks that lock the access to the data of the system and also threaten to
remove or delete all the documents present in the system if the users fail to pay a ransom amount
(Mercaldo et al., 2016). The users are generally asked to pay the ransom in Bitcoins. The
attacker after receiving the Bitcoin gives the decryption key to the users. Ransomware can enter
the systems through attached files that have malicious codes inside them. Malicious websites can
also cause ransomware attacks. These attacks can cause permanent or temporary loss of valuable
information, disrupt regular or daily operations and cause potential damage to the reputation of
an organization. The victim will even face financial loss in the course of recovering and restoring
the system.
Important Lessons
The malware attacks can be prevented by incorporating strong and advanced security
architecture in the electronic devices and systems. Updated and latest versions of the operating
system must be used. The users must download and install only those applications that have been
downloaded by most of the people. The system must have Anti-Virus software downloaded in it
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
RECENT TRENDS IN MALWARE
(Hsu et al., 2012). Implementing personal firewalls can prevent the mobile devices from illegal
access. Applications must be used from sources that are trusted. Multi level approach is needed
for the purpose of providing a high level security solution.
Conclusion
This report concluded that with the emergence and growth of ICT, the malware attacks
are increasing at a fast pace. This report gave an overview of the various types of malware. It
discussed about viruses, worms, Trojans as well as ransomware. It said that viruses can be
transferred from one system to another by the user. They can be transferred through files and
documents making the user believe that it is an essential document. Viruses can harm a single
computer and it does not harm the other systems in the network. Worms have the capacity to
encrypt files to blackmail the user. They even have the capacity to install backdoors for
controlling systems. This report discussed about the recent trends in malware and gave a brief
overview about the recent and the world famous WannaCry ransomware attack that took place in
the month of May, 2017. This report also discussed about the relevant technologies like USB and
Internet that play a major role in malware attacks and also figure outs its application. This report
explained about the missed out issues that have not been given much importance. It also gave a
brief explanation about the significance of these issues. This report concluded that incorporation
of strong security policies would prevent the chances of malware attacks.
RECENT TRENDS IN MALWARE
(Hsu et al., 2012). Implementing personal firewalls can prevent the mobile devices from illegal
access. Applications must be used from sources that are trusted. Multi level approach is needed
for the purpose of providing a high level security solution.
Conclusion
This report concluded that with the emergence and growth of ICT, the malware attacks
are increasing at a fast pace. This report gave an overview of the various types of malware. It
discussed about viruses, worms, Trojans as well as ransomware. It said that viruses can be
transferred from one system to another by the user. They can be transferred through files and
documents making the user believe that it is an essential document. Viruses can harm a single
computer and it does not harm the other systems in the network. Worms have the capacity to
encrypt files to blackmail the user. They even have the capacity to install backdoors for
controlling systems. This report discussed about the recent trends in malware and gave a brief
overview about the recent and the world famous WannaCry ransomware attack that took place in
the month of May, 2017. This report also discussed about the relevant technologies like USB and
Internet that play a major role in malware attacks and also figure outs its application. This report
explained about the missed out issues that have not been given much importance. It also gave a
brief explanation about the significance of these issues. This report concluded that incorporation
of strong security policies would prevent the chances of malware attacks.

11
RECENT TRENDS IN MALWARE
References
Arabo, A., & Pranggono, B. (2013, May). Mobile malware and smart device security: Trends,
challenges and solutions. In Control Systems and Computer Science (CSCS), 2013 19th
International Conference on (pp. 526-531). IEEE.
Chandramohan, M., & Tan, H. B. K. (2012). Detection of mobile malware in the
wild. Computer, 45(9), 65-71.
Chen, Z., Roussopoulos, M., Liang, Z., Zhang, Y., Chen, Z., & Delis, A. (2012). Malware
characteristics and threats on the internet ecosystem. Journal of Systems and
Software, 85(7), 1650-1672.
Erturk, E. (2012, June). A case study in open source software security and privacy: Android
adware. In Internet Security (WorldCIS), 2012 World Congress on (pp. 189-191). IEEE.
Etaher, N., Weir, G. R., & Alazab, M. (2015, August). From zeus to zitmo: Trends in banking
malware. In Trustcom/BigDataSE/ISPA, 2015 IEEE (Vol. 1, pp. 1386-1391). IEEE.
Gandotra, E., Bansal, D., & Sofat, S. (2014). Malware analysis and classification: A
survey. Journal of Information Security, 5(02), 56.
Hsu, F. H., Wu, M. H., Tso, C. K., Hsu, C. H., & Chen, C. W. (2012). Antivirus software shield
against antivirus terminators. IEEE Transactions on Information Forensics and
Security, 7(5), 1439-1447.
Mercaldo, F., Nardone, V., Santone, A., & Visaggio, C. A. (2016, June). Ransomware steals
your phone. formal methods rescue it. In International Conference on Formal
RECENT TRENDS IN MALWARE
References
Arabo, A., & Pranggono, B. (2013, May). Mobile malware and smart device security: Trends,
challenges and solutions. In Control Systems and Computer Science (CSCS), 2013 19th
International Conference on (pp. 526-531). IEEE.
Chandramohan, M., & Tan, H. B. K. (2012). Detection of mobile malware in the
wild. Computer, 45(9), 65-71.
Chen, Z., Roussopoulos, M., Liang, Z., Zhang, Y., Chen, Z., & Delis, A. (2012). Malware
characteristics and threats on the internet ecosystem. Journal of Systems and
Software, 85(7), 1650-1672.
Erturk, E. (2012, June). A case study in open source software security and privacy: Android
adware. In Internet Security (WorldCIS), 2012 World Congress on (pp. 189-191). IEEE.
Etaher, N., Weir, G. R., & Alazab, M. (2015, August). From zeus to zitmo: Trends in banking
malware. In Trustcom/BigDataSE/ISPA, 2015 IEEE (Vol. 1, pp. 1386-1391). IEEE.
Gandotra, E., Bansal, D., & Sofat, S. (2014). Malware analysis and classification: A
survey. Journal of Information Security, 5(02), 56.
Hsu, F. H., Wu, M. H., Tso, C. K., Hsu, C. H., & Chen, C. W. (2012). Antivirus software shield
against antivirus terminators. IEEE Transactions on Information Forensics and
Security, 7(5), 1439-1447.
Mercaldo, F., Nardone, V., Santone, A., & Visaggio, C. A. (2016, June). Ransomware steals
your phone. formal methods rescue it. In International Conference on Formal
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



