Impact of Information Systems on Telstra Corporation Limited Report
VerifiedAdded on 2021/09/14
|18
|4568
|60
Report
AI Summary
This report examines the Management Information System (MIS) of Telstra Corporation Limited, a major telecommunications company. It begins with an executive summary and introduction, outlining the company's operations and the various information systems in place. The report then delves into innovative approaches and creative thinking, discussing the impact of MIS on productivity, managerial roles, and decision-making. It analyzes strategic issues using SWOT analysis, identifying strengths, weaknesses, opportunities, and threats associated with Telstra's MIS. Ethical and social considerations, including information security policies like Acceptable Use Policy and Business Continuity Plan, are discussed. The report also explores global perspectives for strategy, considering market rivalry, emerging technologies like AI, cloud computing, and IoT, and the importance of data analytics. Finally, the report assesses organizational strengths and limitations, offering a conclusion that summarizes the key findings and implications for Telstra's MIS strategy. The report highlights the importance of adapting to changing business conditions, addressing cultural differences, and leveraging technology for competitive advantage. The report is available on Desklib.

MANAGEMENT INFORMATION SYSTEM
Assessment 1
Management Information System
Name of the Student
Name of the University
Assessment 1
Management Information System
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1MANAGEMENT INFORMATION SYSTEM
Executive Summary
The prime objective of this paper is to focus on the impact of the information system on
Telstra Corporation Limited. The changes occurred in the managerial role is discussed in this
paper along with the competitive advantage. The management information system of this
private business organisation evaluated in this paper. An information technology strategy is
proposed in this paper considering the social and ethical aspects. The global perspectives of
the strategy considering the developing and the developed nation are also stated in this paper
as this business organisation have its stakeholders all around the world. The paper concludes
with the strength and weakness of the organisation. The opportunities and the threats
associated with this organisation will also be stated in this paper.
Executive Summary
The prime objective of this paper is to focus on the impact of the information system on
Telstra Corporation Limited. The changes occurred in the managerial role is discussed in this
paper along with the competitive advantage. The management information system of this
private business organisation evaluated in this paper. An information technology strategy is
proposed in this paper considering the social and ethical aspects. The global perspectives of
the strategy considering the developing and the developed nation are also stated in this paper
as this business organisation have its stakeholders all around the world. The paper concludes
with the strength and weakness of the organisation. The opportunities and the threats
associated with this organisation will also be stated in this paper.

2MANAGEMENT INFORMATION SYSTEM
Table of Contents
Executive Summary...................................................................................................................1
Introduction................................................................................................................................3
Innovative approaches and creative thinking.............................................................................4
Process used to analyze strategic issues.....................................................................................5
Awareness of ethical and social considerations for strategic solutions.....................................7
Global perspectives for strategy.................................................................................................8
Awareness of ethical and social considerations for strategic issues..........................................9
Assess organizational strengths and limitations.......................................................................12
Conclusion................................................................................................................................14
Reference..................................................................................................................................15
Table of Contents
Executive Summary...................................................................................................................1
Introduction................................................................................................................................3
Innovative approaches and creative thinking.............................................................................4
Process used to analyze strategic issues.....................................................................................5
Awareness of ethical and social considerations for strategic solutions.....................................7
Global perspectives for strategy.................................................................................................8
Awareness of ethical and social considerations for strategic issues..........................................9
Assess organizational strengths and limitations.......................................................................12
Conclusion................................................................................................................................14
Reference..................................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3MANAGEMENT INFORMATION SYSTEM
Introduction
The prime determination of this paper is to find the impact of the Information
management system in Telstra Corporation Limited. This is one of the biggest
telecommunication company in Australia. The operation of this organisation is around
telecommunication network, the voice of the markets, internet access and the pay television.
There are different types of information systems installed in the working environment of this
organisation. This private organisation aims to deliver more customer oriented service to its
end users (England, 2017). There are lots of strategic and other types of issues related to the
information systems installed in Information Systems of this private business organisation.
This organisation have their stakeholders all around the world so there is huge cultural gap
between the employees of this organisation. There are many market rivals associated with
this organisation. The service provided by this organisation are fixed line and mobile
telephony, whole sale and retail internet, cable internet and different categories of mobile
internet such as mobile broadband, satellite internet and subscription of television.
The impact of the information system on the managerial role is presented in this
documented in a professional manner. The impact of the innovative information system on
the working environment of this organisation is also stated in this paper. The competitive
advantage provided by the proposed strategy is also stated in the paper considering the
business environment of the developing and the developed countries (Iskra, McIntosh &
Wood, 2017). The different types of business elements which help in the formation of an
information vision and information technology are also discussed in this paper. The process
which is used to analyse the strategic issues related to the information system is also
described in the paper with prime importance. The social and ethical considerations of the
proposed strategy along with the global perspective of the strategy are also written in this
Introduction
The prime determination of this paper is to find the impact of the Information
management system in Telstra Corporation Limited. This is one of the biggest
telecommunication company in Australia. The operation of this organisation is around
telecommunication network, the voice of the markets, internet access and the pay television.
There are different types of information systems installed in the working environment of this
organisation. This private organisation aims to deliver more customer oriented service to its
end users (England, 2017). There are lots of strategic and other types of issues related to the
information systems installed in Information Systems of this private business organisation.
This organisation have their stakeholders all around the world so there is huge cultural gap
between the employees of this organisation. There are many market rivals associated with
this organisation. The service provided by this organisation are fixed line and mobile
telephony, whole sale and retail internet, cable internet and different categories of mobile
internet such as mobile broadband, satellite internet and subscription of television.
The impact of the information system on the managerial role is presented in this
documented in a professional manner. The impact of the innovative information system on
the working environment of this organisation is also stated in this paper. The competitive
advantage provided by the proposed strategy is also stated in the paper considering the
business environment of the developing and the developed countries (Iskra, McIntosh &
Wood, 2017). The different types of business elements which help in the formation of an
information vision and information technology are also discussed in this paper. The process
which is used to analyse the strategic issues related to the information system is also
described in the paper with prime importance. The social and ethical considerations of the
proposed strategy along with the global perspective of the strategy are also written in this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4MANAGEMENT INFORMATION SYSTEM
document. The strength, opportunities, threats and limitations of this organisation are also
mentioned in the later sections of this paper.
Innovative approaches and creative thinking
This private business organization have stakeholders all around the world, changing
business conditions is the most important challenge associated with this organization. The
information management system has a great impact on the productivity, functions and
performance of Telstra (Telstra, 2018). Management in all levels can be achieved with the
help of this information management system. Decision making which is one of the key
aspects of every organization can be effectively managed with the help of this information
management system. The managerial decision can be effectively improved with the help of
this information management system. The current and the future of this organization can be
handled with the help of this information management system (Fortino et al., 2018). The
information management system used by this organization provides an added advantage to
this organization due to its enhanced specification such as the security, decision support
system and operational controls.
The different stakeholders of this organization will be involved in this information
management system. A new idea of implementation of this information system must be
adopted by this organism to achieve the desired outcomes (Downes et al., 2015). Since each
department of this organization works on different units the change should be presented in an
organized manner.
The individual and the team commitment will be maintained as the new solution will
be implemented in two phases. The first phase will be considering a small business unit, after
this a business report will be created to find the effectiveness of the new solution (Johnston,
2017). Based upon the findings the second phase will begin which will be considering all the
document. The strength, opportunities, threats and limitations of this organisation are also
mentioned in the later sections of this paper.
Innovative approaches and creative thinking
This private business organization have stakeholders all around the world, changing
business conditions is the most important challenge associated with this organization. The
information management system has a great impact on the productivity, functions and
performance of Telstra (Telstra, 2018). Management in all levels can be achieved with the
help of this information management system. Decision making which is one of the key
aspects of every organization can be effectively managed with the help of this information
management system. The managerial decision can be effectively improved with the help of
this information management system. The current and the future of this organization can be
handled with the help of this information management system (Fortino et al., 2018). The
information management system used by this organization provides an added advantage to
this organization due to its enhanced specification such as the security, decision support
system and operational controls.
The different stakeholders of this organization will be involved in this information
management system. A new idea of implementation of this information system must be
adopted by this organism to achieve the desired outcomes (Downes et al., 2015). Since each
department of this organization works on different units the change should be presented in an
organized manner.
The individual and the team commitment will be maintained as the new solution will
be implemented in two phases. The first phase will be considering a small business unit, after
this a business report will be created to find the effectiveness of the new solution (Johnston,
2017). Based upon the findings the second phase will begin which will be considering all the

5MANAGEMENT INFORMATION SYSTEM
stakeholders of this organization. The difference of culture between the employees of this
organization will also be considered while implementing this plan. Knowledge sharing should
be considered as a very important aspect for the successful implementation of the two
discussed phases (Moses, 2015). The risks and obstacles related to the organization will be
mitigated with the help of the information management system.
The effective training and the developmental plans will be very much impactful for
the effective working of the information management system. This organization should be
having an effective feedback platform which needs to be associated with all the stakeholders
of this organization so that the suggestive measures can be incorporated into the system so
that the security is maintained from both the perspective of the employees as well as from the
point of view of the organization (North, 2016). This process can be effectively used so that
the concept learning organization culture can be achieved.
Process used to analyze strategic issues
The information systems are rapidly changing with the passage of time and extensive
development in the field of information technology. Management of the information systems
is one of the main aspects of every IT organization. The effectiveness of the information
system can be achieved with the help of the many approaches (Bradlow & Jayachandra,
2015). This unit of the paper will be focusing on the approach SWOT analysis of the
Management Information System.
The management information system of Telstra is used for the tracking different
activities of the organization. The working principle of the organization can be understood by
the MIS or Managing Information System. The prime strength of MIS in Telstra is the
identification of the intruders as they deal with sensitive data and networking system. The
flow of information across different departments of Telstra is the other advantage of MIS.
stakeholders of this organization. The difference of culture between the employees of this
organization will also be considered while implementing this plan. Knowledge sharing should
be considered as a very important aspect for the successful implementation of the two
discussed phases (Moses, 2015). The risks and obstacles related to the organization will be
mitigated with the help of the information management system.
The effective training and the developmental plans will be very much impactful for
the effective working of the information management system. This organization should be
having an effective feedback platform which needs to be associated with all the stakeholders
of this organization so that the suggestive measures can be incorporated into the system so
that the security is maintained from both the perspective of the employees as well as from the
point of view of the organization (North, 2016). This process can be effectively used so that
the concept learning organization culture can be achieved.
Process used to analyze strategic issues
The information systems are rapidly changing with the passage of time and extensive
development in the field of information technology. Management of the information systems
is one of the main aspects of every IT organization. The effectiveness of the information
system can be achieved with the help of the many approaches (Bradlow & Jayachandra,
2015). This unit of the paper will be focusing on the approach SWOT analysis of the
Management Information System.
The management information system of Telstra is used for the tracking different
activities of the organization. The working principle of the organization can be understood by
the MIS or Managing Information System. The prime strength of MIS in Telstra is the
identification of the intruders as they deal with sensitive data and networking system. The
flow of information across different departments of Telstra is the other advantage of MIS.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6MANAGEMENT INFORMATION SYSTEM
The security goals of Telstra involve CIA which is confidentiality, Integrity and the
Availability. The problem solving capabilities as well as the decision making capabilities can
be significantly improved with the help of the MIS (Wright et al., 2018). The prime limitation
associated with the MIS used in Telstra is the transactions which are based on complicated
algorithms. The backend functionalities of Telstra cannot be understood by non-technical
employees of the organization, it leads to higher maintenance costs.
The other drawback of the MIS used in Telstra is the huge investment which is
required throughout the entire life cycle of the MIS. The MIS used in Telstra is very much
advanced and is very much sensitive to changes (McDougal, 2017). Since the MIS deals with
huge amount of both structured and unstructured data so any changes in the Meta data leads
to the malfunctioning of the total system. Malfunctioning of the MIS causes drastic changes
in the system as well it is causes financial loss for this business organization. The MIS have
different opportunity associated with the MIS of Telstra such as the controlling of the flow of
materials which significantly helps the organization to cut off their extra additional cost
regarding any physical or non-physical assets. The effective sales and marketing strategy are
the other kinds of issues related to the MIS of Telstra.
Selection of the employees can also be done using the MIS however it can also be
found that there are issues associated with the selection of employees due to the threats
associated with the MIS. The threats of MIS in Telstra come from security flaws f this
organization. The inappropriate design is the most important threat associated with the MIS
of Telstra (Campbell, 2017). Intruders or the cyber criminals are the other categories of
threats associated with MIS as they can alter any vital data which are transmitted from one
department to another. Misuse of the MIS by inexperienced employees of the organization is
the other type of risks associated with the MIS used in Telstra. Thus from this unit of the
The security goals of Telstra involve CIA which is confidentiality, Integrity and the
Availability. The problem solving capabilities as well as the decision making capabilities can
be significantly improved with the help of the MIS (Wright et al., 2018). The prime limitation
associated with the MIS used in Telstra is the transactions which are based on complicated
algorithms. The backend functionalities of Telstra cannot be understood by non-technical
employees of the organization, it leads to higher maintenance costs.
The other drawback of the MIS used in Telstra is the huge investment which is
required throughout the entire life cycle of the MIS. The MIS used in Telstra is very much
advanced and is very much sensitive to changes (McDougal, 2017). Since the MIS deals with
huge amount of both structured and unstructured data so any changes in the Meta data leads
to the malfunctioning of the total system. Malfunctioning of the MIS causes drastic changes
in the system as well it is causes financial loss for this business organization. The MIS have
different opportunity associated with the MIS of Telstra such as the controlling of the flow of
materials which significantly helps the organization to cut off their extra additional cost
regarding any physical or non-physical assets. The effective sales and marketing strategy are
the other kinds of issues related to the MIS of Telstra.
Selection of the employees can also be done using the MIS however it can also be
found that there are issues associated with the selection of employees due to the threats
associated with the MIS. The threats of MIS in Telstra come from security flaws f this
organization. The inappropriate design is the most important threat associated with the MIS
of Telstra (Campbell, 2017). Intruders or the cyber criminals are the other categories of
threats associated with MIS as they can alter any vital data which are transmitted from one
department to another. Misuse of the MIS by inexperienced employees of the organization is
the other type of risks associated with the MIS used in Telstra. Thus from this unit of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MANAGEMENT INFORMATION SYSTEM
paper, the steps involving the analysis of the MIS used in Telstra can be identified. The
specifications of the MIS used in Telstra are very much helpful for enhancing the business
process of this organization.
Awareness of ethical and social considerations for strategic solutions
This organization has their stakeholders from not only in Australia but also from the
other countries as well. Each of the stakeholder’s of this organization comes from a different
cultural background which makes this organization very much prone to different security
issues. This unit of the paper will be revolving around the information security policies which
will be helping to minimize the threats coming from various risks and vulnerabilities (Wu,
Straub & Liang, 2015). The proposed policies will be very much useful as they are based on
social and moral principles along with diversity.
Acceptable Use Policy should be maintained by every employee of this organization
who is accessing any asset associated with the organization. The ethical and moral principles
associated with this category of security policy are Nonmaleficence, Beneficence, Fidelity
and Justice. This policy will provide social justice to both the employees of the organization
as well as the management teams of the organization who are very much worried about the
miss utilization of the company assets.
Business Continuity plan is the other type of information security policy which needs
to be incorporated into the working environment of Telstra in order to cope up with the risks
and vulnerabilities associated with the systems. This plan can be effectively used as a disaster
recovery plan by the Telstra organization. Different assets of this organization such as the
hardware, data application can be restored with the help of this security policy. Like every
other IS organization this organization is also subjected to major changes in terms of
technology (Peltier, 2016). The reason behind these technological changes is the increasing
paper, the steps involving the analysis of the MIS used in Telstra can be identified. The
specifications of the MIS used in Telstra are very much helpful for enhancing the business
process of this organization.
Awareness of ethical and social considerations for strategic solutions
This organization has their stakeholders from not only in Australia but also from the
other countries as well. Each of the stakeholder’s of this organization comes from a different
cultural background which makes this organization very much prone to different security
issues. This unit of the paper will be revolving around the information security policies which
will be helping to minimize the threats coming from various risks and vulnerabilities (Wu,
Straub & Liang, 2015). The proposed policies will be very much useful as they are based on
social and moral principles along with diversity.
Acceptable Use Policy should be maintained by every employee of this organization
who is accessing any asset associated with the organization. The ethical and moral principles
associated with this category of security policy are Nonmaleficence, Beneficence, Fidelity
and Justice. This policy will provide social justice to both the employees of the organization
as well as the management teams of the organization who are very much worried about the
miss utilization of the company assets.
Business Continuity plan is the other type of information security policy which needs
to be incorporated into the working environment of Telstra in order to cope up with the risks
and vulnerabilities associated with the systems. This plan can be effectively used as a disaster
recovery plan by the Telstra organization. Different assets of this organization such as the
hardware, data application can be restored with the help of this security policy. Like every
other IS organization this organization is also subjected to major changes in terms of
technology (Peltier, 2016). The reason behind these technological changes is the increasing

8MANAGEMENT INFORMATION SYSTEM
demand of the end users of this organization so this business continuity plan is very much
effective for maintaining the security of this organization (NATION, 2015). There are no
ethical issues associated with this business continuity plan which is one of the main reasons
why this plan can be successfully implemented in this private organization. This security
measure will not have any impact due to the cultural difference between the stakeholders of
this organization.
Global perspectives for strategy
There are different types of market rivalry between this organization and the other
type of telecommunication companies in Australia such as the Optus and Vodafone, this s
one of the main reason behind the incorporation of the global marketing strategy. The current
international business market of the telecommunication industry is mostly based on data
analytics. With the help of the emerging technologies, the end users of these organizations are
getting the access of their products and services in a fraction of seconds (Siponen, Mahmood
& Pahnila, 2014). The extensive growth in the field of telecommunication is leading to the
growth of major technologies such as artificial intelligence which is actively used in most of
the major telecommunication industries including Telstra.
Cloud Computing and Internet of Things are the other current trends associated with
Telstra. Automated technologies and Chabot’s are used for effective communication purposes
by this organization. Virtual reality, Block chain technology and augmented reality are the
other types of technology associated with this organization. This organization uses these
technologies for different types of purposes; these technologies have a very less negative
impact due to the cultural diversity of the employees as well as the end uses. This
organization is benefitted hugely with the use of these technologies. Global competitions can
be dealt with the use of these technologies (Lowry et al., 2015). Threats are coming from new
demand of the end users of this organization so this business continuity plan is very much
effective for maintaining the security of this organization (NATION, 2015). There are no
ethical issues associated with this business continuity plan which is one of the main reasons
why this plan can be successfully implemented in this private organization. This security
measure will not have any impact due to the cultural difference between the stakeholders of
this organization.
Global perspectives for strategy
There are different types of market rivalry between this organization and the other
type of telecommunication companies in Australia such as the Optus and Vodafone, this s
one of the main reason behind the incorporation of the global marketing strategy. The current
international business market of the telecommunication industry is mostly based on data
analytics. With the help of the emerging technologies, the end users of these organizations are
getting the access of their products and services in a fraction of seconds (Siponen, Mahmood
& Pahnila, 2014). The extensive growth in the field of telecommunication is leading to the
growth of major technologies such as artificial intelligence which is actively used in most of
the major telecommunication industries including Telstra.
Cloud Computing and Internet of Things are the other current trends associated with
Telstra. Automated technologies and Chabot’s are used for effective communication purposes
by this organization. Virtual reality, Block chain technology and augmented reality are the
other types of technology associated with this organization. This organization uses these
technologies for different types of purposes; these technologies have a very less negative
impact due to the cultural diversity of the employees as well as the end uses. This
organization is benefitted hugely with the use of these technologies. Global competitions can
be dealt with the use of these technologies (Lowry et al., 2015). Threats are coming from new
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9MANAGEMENT INFORMATION SYSTEM
entrants as well as from the market competitors. These technologies are effectively used by
both the internal as well as the external stakeholders of this organization. These technological
innovations had a great impact on the growth and development of this business organization.
The risks associated with this organization as well as the subsidiary organization can be dealt
with the help of the exposure of these technologies (Soomro, Shah & Ahmed, 2016).
Ownership of the business, as well as the local economy, can be effectively managed with the
help of the elements of the global perspectives.
The discussed technological advancements can also lead to the changes in the
managerial role of this of this organization and provide them with a competitive advantage
over their market rivals. The challenges related to the cultural differences and the
international trade policies which are different in each country can be effectively dealt with
the help of this global perspective.
Awareness of ethical and social considerations for strategic issues
The quality decisions, management and the batch records are the three different
aspects related to this organization which are needed to be maintained for the overall growth
and development. The most important moral consideration in dealing with the strategic
issues are the information rights and obligations, rights associated with property,
accountability and control, quality of systems and quality of life (Da Veiga, 2015). The social
considerations associated with this organization revolves around the extensive use of the
automated technologies, the decline in the storage costs, advances in the networking and the
different categories of the data analytical techniques such as profiling and non-obvious
relationship awareness (NORA).
entrants as well as from the market competitors. These technologies are effectively used by
both the internal as well as the external stakeholders of this organization. These technological
innovations had a great impact on the growth and development of this business organization.
The risks associated with this organization as well as the subsidiary organization can be dealt
with the help of the exposure of these technologies (Soomro, Shah & Ahmed, 2016).
Ownership of the business, as well as the local economy, can be effectively managed with the
help of the elements of the global perspectives.
The discussed technological advancements can also lead to the changes in the
managerial role of this of this organization and provide them with a competitive advantage
over their market rivals. The challenges related to the cultural differences and the
international trade policies which are different in each country can be effectively dealt with
the help of this global perspective.
Awareness of ethical and social considerations for strategic issues
The quality decisions, management and the batch records are the three different
aspects related to this organization which are needed to be maintained for the overall growth
and development. The most important moral consideration in dealing with the strategic
issues are the information rights and obligations, rights associated with property,
accountability and control, quality of systems and quality of life (Da Veiga, 2015). The social
considerations associated with this organization revolves around the extensive use of the
automated technologies, the decline in the storage costs, advances in the networking and the
different categories of the data analytical techniques such as profiling and non-obvious
relationship awareness (NORA).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10MANAGEMENT INFORMATION SYSTEM
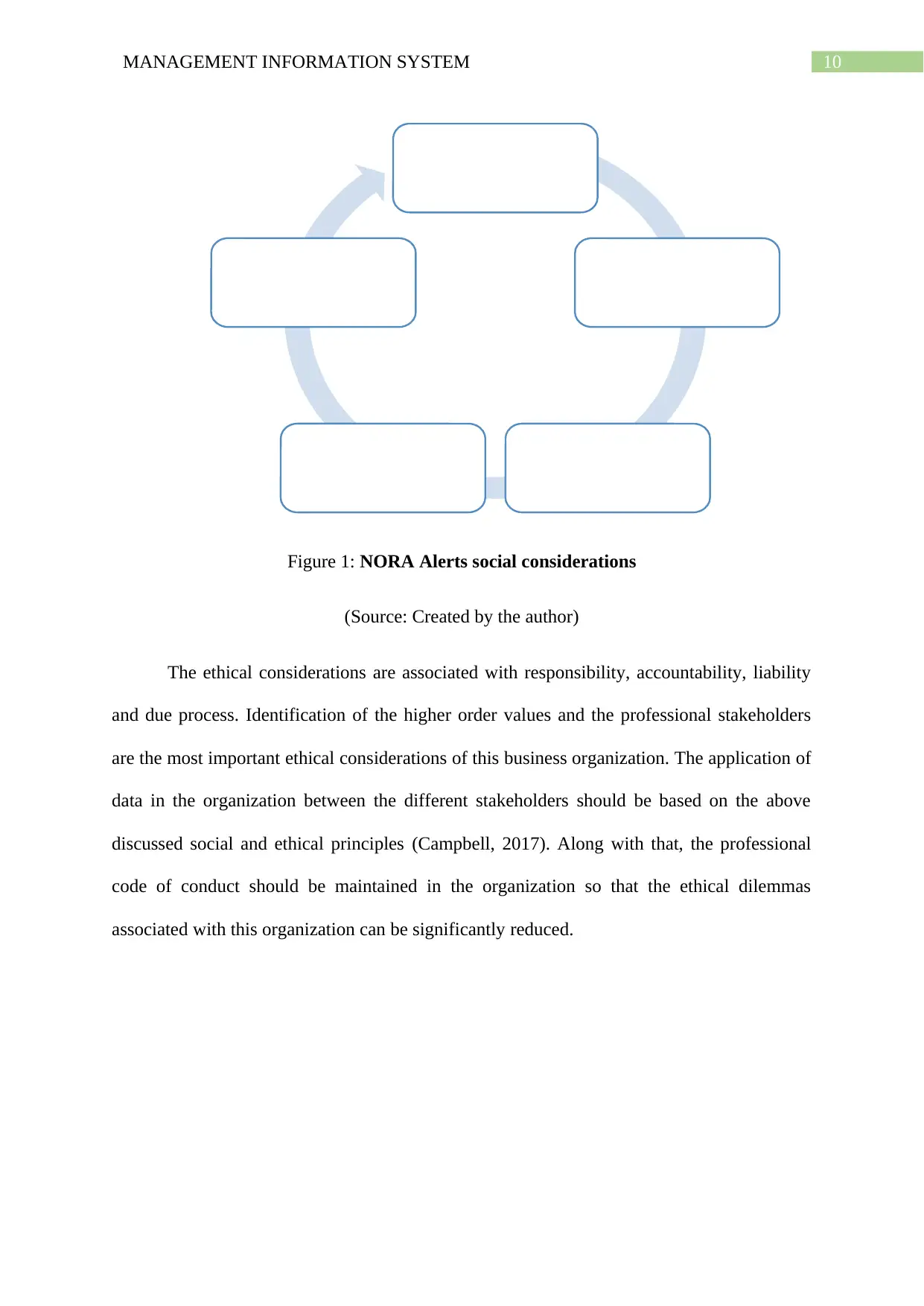
Figure 1: NORA Alerts social considerations
(Source: Created by the author)
The ethical considerations are associated with responsibility, accountability, liability
and due process. Identification of the higher order values and the professional stakeholders
are the most important ethical considerations of this business organization. The application of
data in the organization between the different stakeholders should be based on the above
discussed social and ethical principles (Campbell, 2017). Along with that, the professional
code of conduct should be maintained in the organization so that the ethical dilemmas
associated with this organization can be significantly reduced.
Watch Lists
Human resource
systems
Telehone and
other types of
records
Customer
transaction
systems
Incident and arrest
systems
Figure 1: NORA Alerts social considerations
(Source: Created by the author)
The ethical considerations are associated with responsibility, accountability, liability
and due process. Identification of the higher order values and the professional stakeholders
are the most important ethical considerations of this business organization. The application of
data in the organization between the different stakeholders should be based on the above
discussed social and ethical principles (Campbell, 2017). Along with that, the professional
code of conduct should be maintained in the organization so that the ethical dilemmas
associated with this organization can be significantly reduced.
Watch Lists
Human resource
systems
Telehone and
other types of
records
Customer
transaction
systems
Incident and arrest
systems
11MANAGEMENT INFORMATION SYSTEM
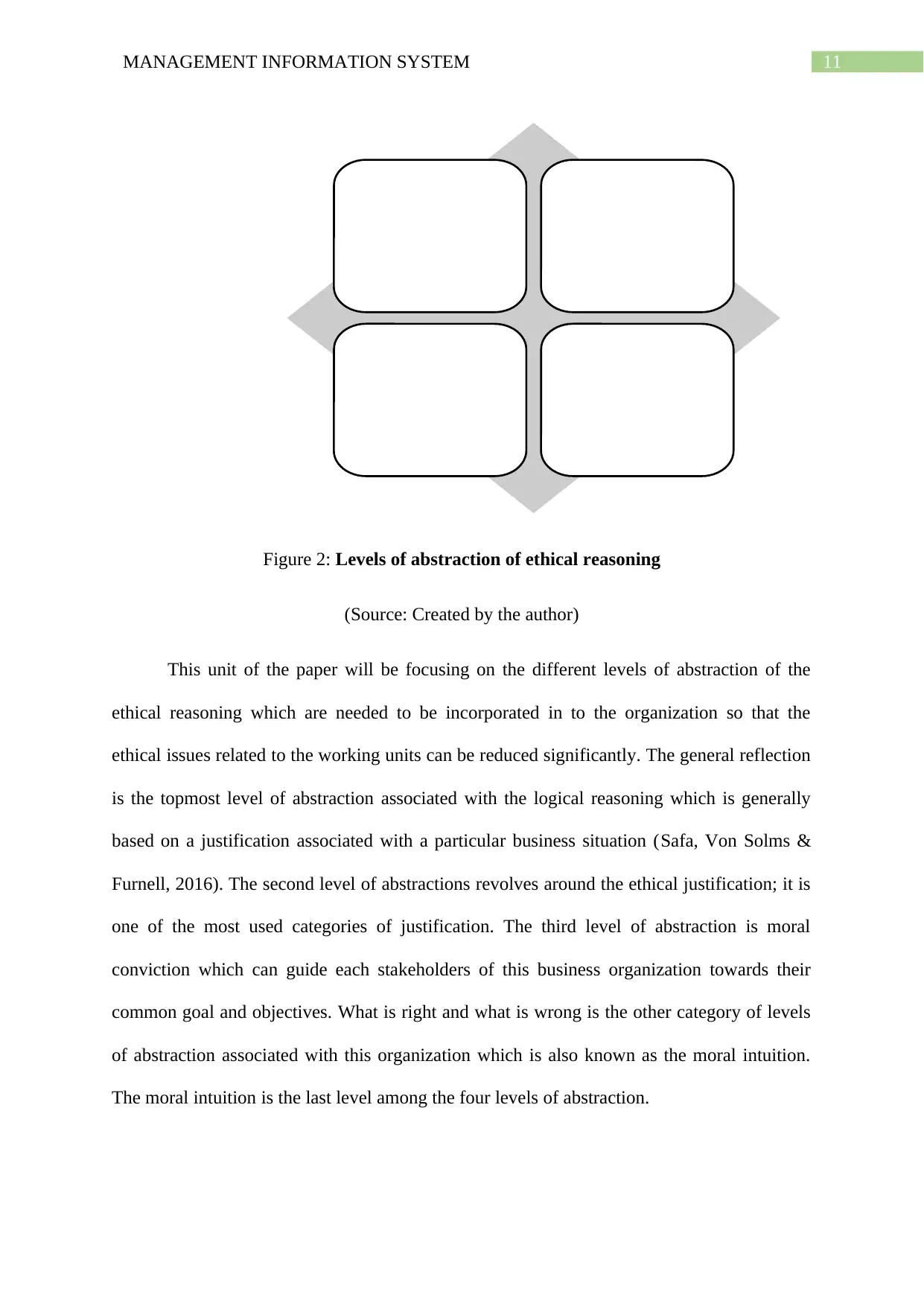
Figure 2: Levels of abstraction of ethical reasoning
(Source: Created by the author)
This unit of the paper will be focusing on the different levels of abstraction of the
ethical reasoning which are needed to be incorporated in to the organization so that the
ethical issues related to the working units can be reduced significantly. The general reflection
is the topmost level of abstraction associated with the logical reasoning which is generally
based on a justification associated with a particular business situation (Safa, Von Solms &
Furnell, 2016). The second level of abstractions revolves around the ethical justification; it is
one of the most used categories of justification. The third level of abstraction is moral
conviction which can guide each stakeholders of this business organization towards their
common goal and objectives. What is right and what is wrong is the other category of levels
of abstraction associated with this organization which is also known as the moral intuition.
The moral intuition is the last level among the four levels of abstraction.
General
Relection
Ethical
Justification
Moral
Conviction
Moral
Intuition
Figure 2: Levels of abstraction of ethical reasoning
(Source: Created by the author)
This unit of the paper will be focusing on the different levels of abstraction of the
ethical reasoning which are needed to be incorporated in to the organization so that the
ethical issues related to the working units can be reduced significantly. The general reflection
is the topmost level of abstraction associated with the logical reasoning which is generally
based on a justification associated with a particular business situation (Safa, Von Solms &
Furnell, 2016). The second level of abstractions revolves around the ethical justification; it is
one of the most used categories of justification. The third level of abstraction is moral
conviction which can guide each stakeholders of this business organization towards their
common goal and objectives. What is right and what is wrong is the other category of levels
of abstraction associated with this organization which is also known as the moral intuition.
The moral intuition is the last level among the four levels of abstraction.
General
Relection
Ethical
Justification
Moral
Conviction
Moral
Intuition
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




