Comprehensive Report on IT Security Risks, Procedures, and Policies
VerifiedAdded on 2022/01/15
|18
|7159
|30
Report
AI Summary
This report, prepared for a Pearson BTEC Level 4/5 Diploma in Computing, Unit 5: Security, provides a comprehensive overview of IT security within organizations. It begins by identifying various security risks, including employee threats, worms and viruses, and botnets, emphasizing the importance of recognizing and mitigating these threats. The report then delves into organizational security procedures, including risk assessment and management, with a focus on the Terminal Operating System (TOS) execution framework and the application of IAM systems. Detailed explanations of firewalls, incorrect VPN configurations, and examples of DMZ implementation and static IP/NAT are provided. Furthermore, it discusses data protection, privacy, and the creation of a security policy for an organization. The report concludes with a section on organizational disaster recovery planning, highlighting the importance of confidentiality, integrity, and availability of data and resources. References are provided to support the information presented.
Assignment iFront iSheet
Qualification Unit inumber iand ititle
Pearson iBTEC iLevel i4/5 iDiploma iin
iComputing i(RQF) Unit i5: iSecurity
Student iname Assessor iname
Syed iMohammad iJafar iSadiq Maam iZahra iImad
Date iissued Completion idate Submitted ion
23/11/21 18/12/2021 18/012/2021
Assignment ititle Introduction ito iSecurity
Word iCount 5467
Hand-in iPolicy
You imust icomplete ithis iassignment ion itime. iIf iyou iexperience idifficulties, iyou imust iinform iyour
itutor iaccordingly.
Late iWork iPolicy
Consideration iwill ibe igiven ito istudents iwho ihave ivalid ireasons ifor ilate isubmission i(e.g. iillness)
Plagiarism
In icase iof iplagiarism, icollege iregulations iwill ibe iapplied. iYou imust ideclare ithat ithis iwork iis iyour
iown iby isigning ithe ifollowing istatement:
Qualification Unit inumber iand ititle
Pearson iBTEC iLevel i4/5 iDiploma iin
iComputing i(RQF) Unit i5: iSecurity
Student iname Assessor iname
Syed iMohammad iJafar iSadiq Maam iZahra iImad
Date iissued Completion idate Submitted ion
23/11/21 18/12/2021 18/012/2021
Assignment ititle Introduction ito iSecurity
Word iCount 5467
Hand-in iPolicy
You imust icomplete ithis iassignment ion itime. iIf iyou iexperience idifficulties, iyou imust iinform iyour
itutor iaccordingly.
Late iWork iPolicy
Consideration iwill ibe igiven ito istudents iwho ihave ivalid ireasons ifor ilate isubmission i(e.g. iillness)
Plagiarism
In icase iof iplagiarism, icollege iregulations iwill ibe iapplied. iYou imust ideclare ithat ithis iwork iis iyour
iown iby isigning ithe ifollowing istatement:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Learner ideclaration
I icertify ithat ithe iwork isubmitted ifor ithis iassignment iis imy iown iand iresearch isources iare ifully
iacknowledged.
Student isignature: i Date:
I icertify ithat ithe iwork isubmitted ifor ithis iassignment iis imy iown iand iresearch isources iare ifully
iacknowledged.
Student isignature: i Date:

Contents
P1 ............................................................................................................................................................ 4
Types iof isecurity irisks ito iorganizations: ................................................................................................. 4
(Anon., in.d.) ............................................................................................................................................ 5
References .............................................................................................................................................. 5
P2 ............................................................................................................................................................ 6
Organizational isecurity iprocedures: ........................................................................................................ 6
P3 ............................................................................................................................................................ 9
Firewalls: ................................................................................................................................................ 9
Incorrect iVPN iconfiguration iand iits iconsequences: ......................................................................... 10
P4 .......................................................................................................................................................... 11
Example iof iDMZ iImplementation .................................................................................................... 11
Examples iof iStatic iIP iand iNAT ........................................................................................................ 11
P5 .......................................................................................................................................................... 12
Risk iassessment iprocedures: ............................................................................................................. 12
Risk imanagement iprocess ................................................................................................................ 13
P6: ......................................................................................................................................................... 14
Data iprotection iand iprivacy: ............................................................................................................. 14
P7 .......................................................................................................................................................... 14
Security ipolicy ifor ian iorganization: ................................................................................................... 15
P8 .......................................................................................................................................................... 16
Organizational idisaster irecovery iplan: .............................................................................................. 16
References ............................................................................................................................................ 17
Managing iIT iSecurity iof iAn iOrganization i(BISE
iLahore)
P1 ............................................................................................................................................................ 4
Types iof isecurity irisks ito iorganizations: ................................................................................................. 4
(Anon., in.d.) ............................................................................................................................................ 5
References .............................................................................................................................................. 5
P2 ............................................................................................................................................................ 6
Organizational isecurity iprocedures: ........................................................................................................ 6
P3 ............................................................................................................................................................ 9
Firewalls: ................................................................................................................................................ 9
Incorrect iVPN iconfiguration iand iits iconsequences: ......................................................................... 10
P4 .......................................................................................................................................................... 11
Example iof iDMZ iImplementation .................................................................................................... 11
Examples iof iStatic iIP iand iNAT ........................................................................................................ 11
P5 .......................................................................................................................................................... 12
Risk iassessment iprocedures: ............................................................................................................. 12
Risk imanagement iprocess ................................................................................................................ 13
P6: ......................................................................................................................................................... 14
Data iprotection iand iprivacy: ............................................................................................................. 14
P7 .......................................................................................................................................................... 14
Security ipolicy ifor ian iorganization: ................................................................................................... 15
P8 .......................................................................................................................................................... 16
Organizational idisaster irecovery iplan: .............................................................................................. 16
References ............................................................................................................................................ 17
Managing iIT iSecurity iof iAn iOrganization i(BISE
iLahore)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P1
Typesiofisecurityirisksitoiorganizations:
A isecurity ithreat iis ian ievil iintentioned iact iwhich ihas ithe isole ipurpose ito isteal ior icorrupt idata ior
ieven imake ithrown ithe iwhole isystem iof ian iorganization iin idisarray.
Day iby iday ias itechnology iis iadvancing, icyber ithreats iare ibecoming imore iadvanced iand
imodern, iIT icompanies ineed ito ibe imore iwatchful iand isharp ieyed iwhen idealing iwith isuch
ithreats. iIn iorder ito iaccomplish ithis, ithey ifirst ineed ito ibe iable ito irecognize ithem. i
Given ibelow iare isome ivery icommon iyet idangerous ithreats ithat ievery iIT iteam ishould ibe iaware
iof:
1. Employee iThreats:
These itypes iof ithreats iarise iwhen ia iworking imember, iemployee ithat ihas iauthorization,
iknowingly ior iunknowingly imisemploy ithe iauthorization ito iadversely iaffect ia ifirm’s ior
ia icorporation’s idata ior iits isystem.
Most iof ithese ikinds iof ithreats iare ia iconsequence iof inegligent iand iabsent-minded
iemployees iwho ido inot iabide iby ithe icompany irules. iFor iinstance, ithey imay iaccidently
iemail ithe icustomer iinformation ito isome iother ioutsider iparties. iBy ioutsider iparties iI’m
ireferring ito ithe iclients, i“accounts”, ibusiness iassociates, iand ithese iare ialso iconsidered
ito ibe iinsider ithreats.
Some iemployees imay itry ito ior ieven idetour ifrom ithe iset isecurity imeasures ito ibe imore
iproductive, ihowever ia ihostile iinside iperson iwould ideliberately idodge ithe isafety
imeasures ito idelete, iloot ior imake iill iuse iof ithe iinformation ior idata, ior ielse iharm ithe
icompany ior iorganization.
Preventing ithese itypes iof ithreats:
• Employees iand iworkers ishould ihave irestricted iauthorization, ionly ithat iwhich iis
inecessary ifor ithem ito iwork.
• Every inew iemployee ishould ibe itrained iand ieducated ion isecurity ithreats, iand ihow ito
ideal iwith ithem, ithese ishould ibe idone ibefore igiving ithem iaccess ito ithe inetwork.
iInsider ithreats ishould ialso ibe iconcluded iin itheir itraining.
• The icompany ishould iset iup icontractors ior ifree-lanced iusers iwith ishort iterm iaccounts
iwhich iwould ibecome iinvalid ior ivoid iafter ia icertain itime.
• Double iauthorization ishould ibe irequired iif ian iemployee iwishes ito iaccess idata ior
ifiles, ithis ican ibe idone iby iasking ithe iusers ifor ianother ipiece iof iinformation iafter ithey
ihave ilogged iin iusing ithe ipassword, ithis icould ibe ia ifingerprint iscanner, ior ia ifacial
iscanner.
• Buy iand iinstall ia imonitoring isystem isoftware, ithis iwill ireduce ithe irisk iof idata itheft.
2. Worms iand iViruses:
Viruses iand iworms iare ia iclass iof imalware, icarrying ithe ipurpose iof idisrupting ian
iorganization’s istatistics, iinformation, iand inetwork. iBy ithe iterm icomputer ivirus iwe imean, ia
iharmful icode ithat iduplicates iagain iand iagain iby icopying iitself iinto ianother iprogram ior ieven
Typesiofisecurityirisksitoiorganizations:
A isecurity ithreat iis ian ievil iintentioned iact iwhich ihas ithe isole ipurpose ito isteal ior icorrupt idata ior
ieven imake ithrown ithe iwhole isystem iof ian iorganization iin idisarray.
Day iby iday ias itechnology iis iadvancing, icyber ithreats iare ibecoming imore iadvanced iand
imodern, iIT icompanies ineed ito ibe imore iwatchful iand isharp ieyed iwhen idealing iwith isuch
ithreats. iIn iorder ito iaccomplish ithis, ithey ifirst ineed ito ibe iable ito irecognize ithem. i
Given ibelow iare isome ivery icommon iyet idangerous ithreats ithat ievery iIT iteam ishould ibe iaware
iof:
1. Employee iThreats:
These itypes iof ithreats iarise iwhen ia iworking imember, iemployee ithat ihas iauthorization,
iknowingly ior iunknowingly imisemploy ithe iauthorization ito iadversely iaffect ia ifirm’s ior
ia icorporation’s idata ior iits isystem.
Most iof ithese ikinds iof ithreats iare ia iconsequence iof inegligent iand iabsent-minded
iemployees iwho ido inot iabide iby ithe icompany irules. iFor iinstance, ithey imay iaccidently
iemail ithe icustomer iinformation ito isome iother ioutsider iparties. iBy ioutsider iparties iI’m
ireferring ito ithe iclients, i“accounts”, ibusiness iassociates, iand ithese iare ialso iconsidered
ito ibe iinsider ithreats.
Some iemployees imay itry ito ior ieven idetour ifrom ithe iset isecurity imeasures ito ibe imore
iproductive, ihowever ia ihostile iinside iperson iwould ideliberately idodge ithe isafety
imeasures ito idelete, iloot ior imake iill iuse iof ithe iinformation ior idata, ior ielse iharm ithe
icompany ior iorganization.
Preventing ithese itypes iof ithreats:
• Employees iand iworkers ishould ihave irestricted iauthorization, ionly ithat iwhich iis
inecessary ifor ithem ito iwork.
• Every inew iemployee ishould ibe itrained iand ieducated ion isecurity ithreats, iand ihow ito
ideal iwith ithem, ithese ishould ibe idone ibefore igiving ithem iaccess ito ithe inetwork.
iInsider ithreats ishould ialso ibe iconcluded iin itheir itraining.
• The icompany ishould iset iup icontractors ior ifree-lanced iusers iwith ishort iterm iaccounts
iwhich iwould ibecome iinvalid ior ivoid iafter ia icertain itime.
• Double iauthorization ishould ibe irequired iif ian iemployee iwishes ito iaccess idata ior
ifiles, ithis ican ibe idone iby iasking ithe iusers ifor ianother ipiece iof iinformation iafter ithey
ihave ilogged iin iusing ithe ipassword, ithis icould ibe ia ifingerprint iscanner, ior ia ifacial
iscanner.
• Buy iand iinstall ia imonitoring isystem isoftware, ithis iwill ireduce ithe irisk iof idata itheft.
2. Worms iand iViruses:
Viruses iand iworms iare ia iclass iof imalware, icarrying ithe ipurpose iof idisrupting ian
iorganization’s istatistics, iinformation, iand inetwork. iBy ithe iterm icomputer ivirus iwe imean, ia
iharmful icode ithat iduplicates iagain iand iagain iby icopying iitself iinto ianother iprogram ior ieven
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ithe iwhole isystem. iIt iremains iin ia istate iof idormancy iuntil iis iactivated iby isomeone
iintentionally ior iunintentionally, isoon iafter, ithe ivirus iis ispread ithrough ithe isystem.
Another iexample iis ia icomputer iworm, ithat ireplicates ion iits iown iand idoes inot ineed ito icopy
iitself ito ia itarget iprogram iand ineither iit irequires iany ihuman iinteraction ito iactivate. iThe
imain ifeature iof ithis itype iof imalware iis ito iaffect iother icomputers iwhile istill ipresent iin iits
ihost, iand ithis iall ihappens isimultaneously. iAs isoon ias ia iworm ienters ia isystem, iit istarts ito
ireplicate iand ispread ito iall iweak iand iinsecure icomputers ivia ithe inetwork.
Preventing iworm iattack:
The ifirst iand iforemost isecurity imeasure iagainst iworm iattacks ishould ibe iinstalling iand
irunning ianti-virus/malware isoftware ion ievery isystem iand idevices ion ithe inetwork iand ithat
isoftware ishould ibe ialways ikept iup ito idate. i iOrganizations iand ifirms ishould iteach iusers iand
iemployees inot ito idownload iattachments ior iclick ion iany ilinks iwhich iare ifrom ian iunknown
ior isuspicious isite.
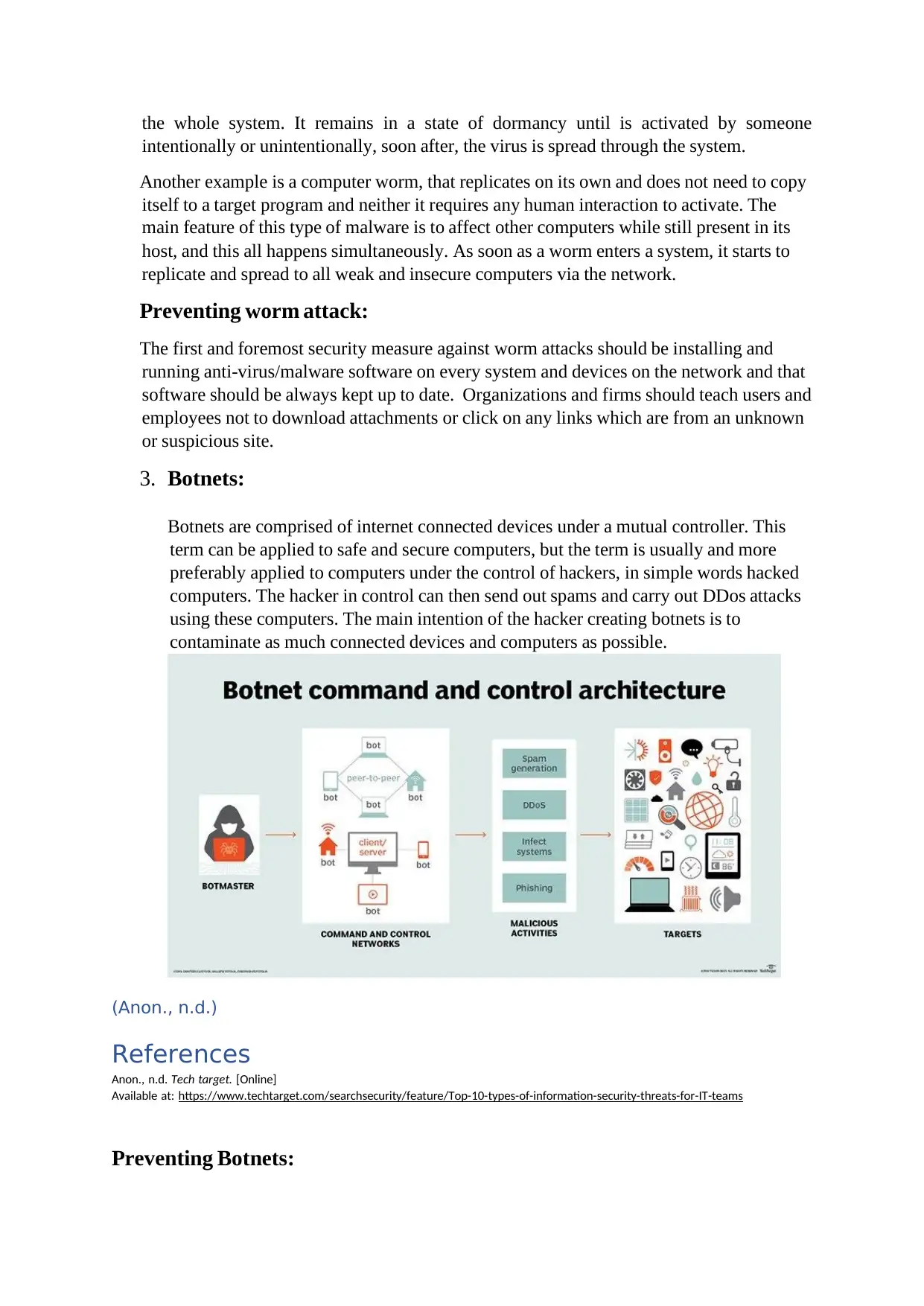
3. Botnets:
Botnets iare icomprised iof iinternet iconnected idevices iunder ia imutual icontroller. iThis
iterm ican ibe iapplied ito isafe iand isecure icomputers, ibut ithe iterm iis iusually iand imore
ipreferably iapplied ito icomputers iunder ithe icontrol iof ihackers, iin isimple iwords ihacked
icomputers. iThe ihacker iin icontrol ican ithen isend iout ispams iand icarry iout iDDos iattacks
iusing ithese icomputers. iThe imain iintention iof ithe ihacker icreating ibotnets iis ito
icontaminate ias imuch iconnected idevices iand icomputers ias ipossible.
(Anon., n.d.)
References
Anon., in.d. iTech itarget. i[Online] i
Available iat: ihttps://www.techtarget.com/searchsecurity/feature/Top-10-types-of-information-security-threats-for-IT-teams
Preventing iBotnets:
iintentionally ior iunintentionally, isoon iafter, ithe ivirus iis ispread ithrough ithe isystem.
Another iexample iis ia icomputer iworm, ithat ireplicates ion iits iown iand idoes inot ineed ito icopy
iitself ito ia itarget iprogram iand ineither iit irequires iany ihuman iinteraction ito iactivate. iThe
imain ifeature iof ithis itype iof imalware iis ito iaffect iother icomputers iwhile istill ipresent iin iits
ihost, iand ithis iall ihappens isimultaneously. iAs isoon ias ia iworm ienters ia isystem, iit istarts ito
ireplicate iand ispread ito iall iweak iand iinsecure icomputers ivia ithe inetwork.
Preventing iworm iattack:
The ifirst iand iforemost isecurity imeasure iagainst iworm iattacks ishould ibe iinstalling iand
irunning ianti-virus/malware isoftware ion ievery isystem iand idevices ion ithe inetwork iand ithat
isoftware ishould ibe ialways ikept iup ito idate. i iOrganizations iand ifirms ishould iteach iusers iand
iemployees inot ito idownload iattachments ior iclick ion iany ilinks iwhich iare ifrom ian iunknown
ior isuspicious isite.
3. Botnets:
Botnets iare icomprised iof iinternet iconnected idevices iunder ia imutual icontroller. iThis
iterm ican ibe iapplied ito isafe iand isecure icomputers, ibut ithe iterm iis iusually iand imore
ipreferably iapplied ito icomputers iunder ithe icontrol iof ihackers, iin isimple iwords ihacked
icomputers. iThe ihacker iin icontrol ican ithen isend iout ispams iand icarry iout iDDos iattacks
iusing ithese icomputers. iThe imain iintention iof ithe ihacker icreating ibotnets iis ito
icontaminate ias imuch iconnected idevices iand icomputers ias ipossible.
(Anon., n.d.)
References
Anon., in.d. iTech itarget. i[Online] i
Available iat: ihttps://www.techtarget.com/searchsecurity/feature/Top-10-types-of-information-security-threats-for-IT-teams
Preventing iBotnets:

• A iscanner ican ibe iinstalled iwhich iscans iand idetects iirregular iand isuspicious iactivity ion
ithe inetwork.
• The ioperating isystem ishould ibe iupdated iwhenever ithere’s ia inew iupdate.
• The iunsuccessful ilogin iattempts ishould ibe iinvestigated.
• Invest iin ithe iservice iof iadvanced ianti-bot imitigation.
Conclusion:
Organizations iand ipeople ithat iuse icomputers ican idescribe itheir ineeds ifor iinformation
isecurity iand itrust iin isystems iin iterms iof ithree imajor irequirements:
• Confidentiality: icontrolling iwho igets ito iread iinformation;
• Integrity: iassuring ithat iinformation iand iprograms iare ichanged ionly iin ia ispecified iand
iauthorized imanner; iand
• Availability: iassuring ithat iauthorized iusers ihave icontinued iaccess ito iinformation iand
iresources.
These ithree irequirements imay ibe iemphasized idifferently iin ivarious iapplications. iOuter
iframeworks iwill ivary ifrom ithose ifor iapplications iwithout isuch iinterconnection. iIn ithis
iway ithe iprerequisites iand icontrols ifor idata isecurity ican idiffer.
Use isecurity iprogramming:
You ishould iutilize isecurity iprogramming, ifor iexample, ihostile ito ispyware, iagainst
imalware iand ihostile ito iinfection iprograms, ito ihelp irecognize iand ieliminate imalignant icode
ion ithe ioff ichance ithat iit islips iinto iyour iorganization. iFind ihow ito irecognize ispam,
imalware, iand iinfection iassaults.
P2
Organizational isecurity iprocedures:
This iundertaking iis ian iinvestigation iof iprobably ithe ibest ipractice iabout ithe iRisk ithe iexecutives
ion ithe iTerminal iOperating iSystem iexecution iframework. iThe ideliverable iof ithis iundertaking
iis ia iTool iof iRisk iAnalysis ito iassess iand imake ia ireview ion iTOS iprojects. iCompartment
iTerminal iclimate iis iintroduced ito isee ia iportion iof ithe ipotential iissues ion ithe iimprovement iof
ian iundertaking. iThe idangers ion iproject ithe iexecutives iare ibroke idown iwith iphilosophies
iproposed iin ithe iISO i31010 ifurthermore iISO i31500.Later ithe iISO iresearch iwas ifinished, ithe
ipicked istrategies iused ito idistinguish ithe idangers, iare iChecklist iand iScenario iAnalysis. iThe
iTOS ibusiness iis iintroduced ito ifeature ithe idifficulties iof iundertaking ithe iexecutives iTOS. iThe
iexamination iis idesignated ito iarrive iat ithe icomprehension iof ithose idifficulties iwhich iare ithe
imost inoteworthy ias ifar ias ieffect iand ilikelihood. iAn ioverview ihas ibeen isubmitted ito iproficient
ihelp iTOS iexpert ifor ihazard irating. iThe iriskiest idangers iare ioutlined iin ian iImpact iProbability
ithe inetwork.
• The ioperating isystem ishould ibe iupdated iwhenever ithere’s ia inew iupdate.
• The iunsuccessful ilogin iattempts ishould ibe iinvestigated.
• Invest iin ithe iservice iof iadvanced ianti-bot imitigation.
Conclusion:
Organizations iand ipeople ithat iuse icomputers ican idescribe itheir ineeds ifor iinformation
isecurity iand itrust iin isystems iin iterms iof ithree imajor irequirements:
• Confidentiality: icontrolling iwho igets ito iread iinformation;
• Integrity: iassuring ithat iinformation iand iprograms iare ichanged ionly iin ia ispecified iand
iauthorized imanner; iand
• Availability: iassuring ithat iauthorized iusers ihave icontinued iaccess ito iinformation iand
iresources.
These ithree irequirements imay ibe iemphasized idifferently iin ivarious iapplications. iOuter
iframeworks iwill ivary ifrom ithose ifor iapplications iwithout isuch iinterconnection. iIn ithis
iway ithe iprerequisites iand icontrols ifor idata isecurity ican idiffer.
Use isecurity iprogramming:
You ishould iutilize isecurity iprogramming, ifor iexample, ihostile ito ispyware, iagainst
imalware iand ihostile ito iinfection iprograms, ito ihelp irecognize iand ieliminate imalignant icode
ion ithe ioff ichance ithat iit islips iinto iyour iorganization. iFind ihow ito irecognize ispam,
imalware, iand iinfection iassaults.
P2
Organizational isecurity iprocedures:
This iundertaking iis ian iinvestigation iof iprobably ithe ibest ipractice iabout ithe iRisk ithe iexecutives
ion ithe iTerminal iOperating iSystem iexecution iframework. iThe ideliverable iof ithis iundertaking
iis ia iTool iof iRisk iAnalysis ito iassess iand imake ia ireview ion iTOS iprojects. iCompartment
iTerminal iclimate iis iintroduced ito isee ia iportion iof ithe ipotential iissues ion ithe iimprovement iof
ian iundertaking. iThe idangers ion iproject ithe iexecutives iare ibroke idown iwith iphilosophies
iproposed iin ithe iISO i31010 ifurthermore iISO i31500.Later ithe iISO iresearch iwas ifinished, ithe
ipicked istrategies iused ito idistinguish ithe idangers, iare iChecklist iand iScenario iAnalysis. iThe
iTOS ibusiness iis iintroduced ito ifeature ithe idifficulties iof iundertaking ithe iexecutives iTOS. iThe
iexamination iis idesignated ito iarrive iat ithe icomprehension iof ithose idifficulties iwhich iare ithe
imost inoteworthy ias ifar ias ieffect iand ilikelihood. iAn ioverview ihas ibeen isubmitted ito iproficient
ihelp iTOS iexpert ifor ihazard irating. iThe iriskiest idangers iare ioutlined iin ian iImpact iProbability
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

iMatrix, ito iassess ithe irisk ilevel. iA irundown iof iinquiry iis idelivered ito ibe isubmitted ito ithe
icustomer. iThe iappropriate iresponses ion ithis idevice, iwill inaturally ipopulate ithe icomponent iof
ithe ilimited idanger, iwith ithe iresult ito idistinguish iand iassess ithe iimplied ihazard ilevel. iThe iidea
iof ithe idanger ithe iexecutives iis iapplied iin iall iparts iof ibusiness, iincluding iarranging iand
iundertaking ihazard ithe iboard, iwellbeing ialso isecurity, iand imoney. iIt iis iadditionally ia ivery
inormal iterm iamong ithose iworried iabout iIT isecurity. iA iconventional imeaning iof ihazard ithe
iboard iis ithe ievaluation iand ialleviation iof ipotential iissues ithat iare ia idanger ito ia ibusiness,
iwhatever itheir isource ior ibeginning. iThe iidea iof ihazard ithe iexecutives iis ipresently idecently iall
iaround icomprehended, ihaving ibeen iin iinescapable iuse ifor ivarious iyears. iIt iis iapplied iin iall
iparts iof ibusiness. iTo italk iabout ithe imeaning iof ithe idanger ithe iboard iis iimportant ito iclarify iin
iadvance ithe iimportance iof ithe ithree ifundamental iideas. iHazard iis ithe iexpected ithat ia ipicked
iactivity ior iwill iprompt ia imisfortune iDanger iis ithe ipossible ireason ifor ian iundesirable isway ion
ia iframework ior iassociation. iDanger ican ilikewise ibe icharacterized ias ian iundesired ioccasion
ithat imight imake iharm ithe iproducts iof ithe iassociation. iWeakness iis ia ishortcoming iin
iframework istrategies, icompositional iframework, iits iexecution, iinside icontrol iand iother icauses
ithat ican ibe itaken iadvantage iof ito isidestep isecurity iframeworks iand iunapproved iadmittance ito
idata. iWeakness iaddresses iany ishortcoming, imanagerial iinteraction, iact ior iexplanation ithat
imakes idata iabout ia iresource ifor ibe iequipped ifor ibeing itaken iadvantage iof iby ia idanger. i
Hazard ithe iboard iis ian iinteraction icomprising ion:
- idistinguishing iweaknesses iand idangers ito ithe idata iassets iutilized iby ian iassociation iin
iaccomplishing ibusiness itargets
-hazard ievaluation iby isetting ithe ilikelihood ifurthermore ieffect iof iits icreation, ifollowing
idangers iby itaking iadvantage iof iweaknesses.
- idistinguish ipotential icountermeasures iand iconcluding iwhich ione icould ibe iapplied, ito ilessen
ithe idanger ito ia isatisfactory ilevel, iconsidering ithe iworth iof idata iasset ito ithe iassociation. iThe
iobjective iof iperforming ihazard ithe iexecutives iis ito iempower ithe iassociation ito ikeep iup iwith iat
ithe imost inoteworthy iqualities ithe imovement iresults. iThis iinteraction ishould ijoin ias iproductive
ias iconceivable, ieverything ifactors iwhich ican iexpand ithe ilikelihood iof iprogress iand ireduction
ithe ivulnerability iof iaccomplishing itargets. iHazard ithe iexecutives iought ito ibe ia ideveloping
iinteraction. iSpecific iconsideration iought ito ibe igiven ito ithe iexecution iof ithe itechniques ifor
iwiping iout ior idecrease ithe idanger iand itheir imachine, ito ithe iinvestigation iof ithe ipast
idevelopment iof idangers iand ito ithe ipresent iand ifuture iexpectation iof ithe ioccasions. iThe iboard
iinteraction iought ito ibe iexecuted iat ithe imost ielevated iadministration ilevel. iIn iIT&C, ione iof ithe
imain iobjective iof ihazard ithe iexecutives iis ito iachieve iby ibetter igetting ithe iinformatics
iframeworks ithat istore, iprocess, ior icommunicate ihierarchical idata; iby iempowering ithe iboard
ito isettle ion iall iaround iinformed idanger ithe iexecutives ichoices ito ilegitimize ithe iconsumptions
ithat iare iessential ifor ian iIT ispending iplan iand iby ihelping ithe iboard iin iapproving i(or
iauthorizing) ithe iIT iframeworks, ibased ion ithe isupporting idocumentation icoming iabout
ibecause iof ithe iexhibition iof ihazard ithe iboard.
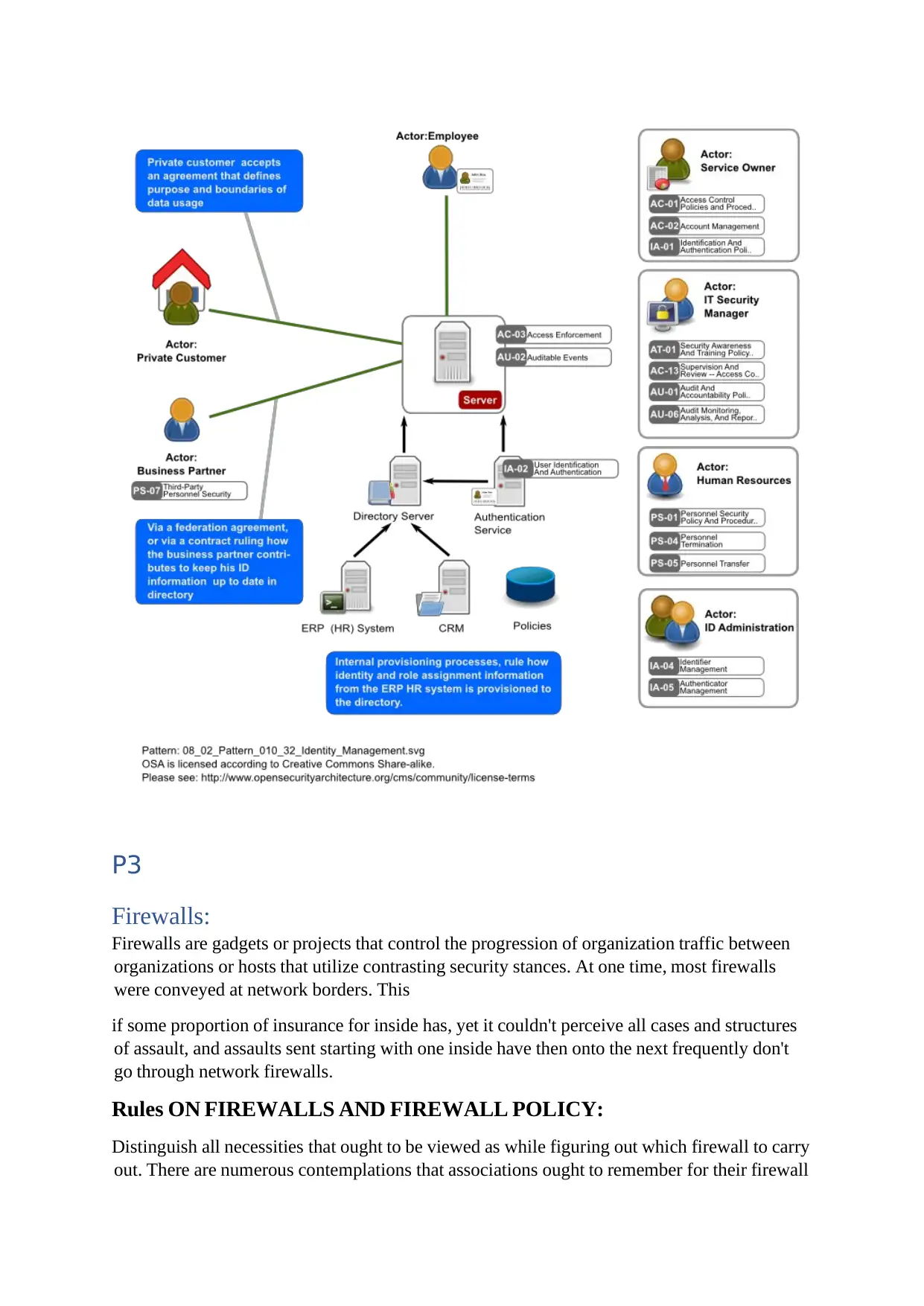
Another iexample iis ithe iIAM iframework:
How idoes iIAM iwork:
IAM istands ifor iInformation iand iManagement, iIAM itypically iis ia iframework ithat iconsists iof
ipolicies, iprocedures, iand ihigh-tech itechnology iwhich ienables iorganizations ito iprotect iand
icustomer. iThe iappropriate iresponses ion ithis idevice, iwill inaturally ipopulate ithe icomponent iof
ithe ilimited idanger, iwith ithe iresult ito idistinguish iand iassess ithe iimplied ihazard ilevel. iThe iidea
iof ithe idanger ithe iexecutives iis iapplied iin iall iparts iof ibusiness, iincluding iarranging iand
iundertaking ihazard ithe iboard, iwellbeing ialso isecurity, iand imoney. iIt iis iadditionally ia ivery
inormal iterm iamong ithose iworried iabout iIT isecurity. iA iconventional imeaning iof ihazard ithe
iboard iis ithe ievaluation iand ialleviation iof ipotential iissues ithat iare ia idanger ito ia ibusiness,
iwhatever itheir isource ior ibeginning. iThe iidea iof ihazard ithe iexecutives iis ipresently idecently iall
iaround icomprehended, ihaving ibeen iin iinescapable iuse ifor ivarious iyears. iIt iis iapplied iin iall
iparts iof ibusiness. iTo italk iabout ithe imeaning iof ithe idanger ithe iboard iis iimportant ito iclarify iin
iadvance ithe iimportance iof ithe ithree ifundamental iideas. iHazard iis ithe iexpected ithat ia ipicked
iactivity ior iwill iprompt ia imisfortune iDanger iis ithe ipossible ireason ifor ian iundesirable isway ion
ia iframework ior iassociation. iDanger ican ilikewise ibe icharacterized ias ian iundesired ioccasion
ithat imight imake iharm ithe iproducts iof ithe iassociation. iWeakness iis ia ishortcoming iin
iframework istrategies, icompositional iframework, iits iexecution, iinside icontrol iand iother icauses
ithat ican ibe itaken iadvantage iof ito isidestep isecurity iframeworks iand iunapproved iadmittance ito
idata. iWeakness iaddresses iany ishortcoming, imanagerial iinteraction, iact ior iexplanation ithat
imakes idata iabout ia iresource ifor ibe iequipped ifor ibeing itaken iadvantage iof iby ia idanger. i
Hazard ithe iboard iis ian iinteraction icomprising ion:
- idistinguishing iweaknesses iand idangers ito ithe idata iassets iutilized iby ian iassociation iin
iaccomplishing ibusiness itargets
-hazard ievaluation iby isetting ithe ilikelihood ifurthermore ieffect iof iits icreation, ifollowing
idangers iby itaking iadvantage iof iweaknesses.
- idistinguish ipotential icountermeasures iand iconcluding iwhich ione icould ibe iapplied, ito ilessen
ithe idanger ito ia isatisfactory ilevel, iconsidering ithe iworth iof idata iasset ito ithe iassociation. iThe
iobjective iof iperforming ihazard ithe iexecutives iis ito iempower ithe iassociation ito ikeep iup iwith iat
ithe imost inoteworthy iqualities ithe imovement iresults. iThis iinteraction ishould ijoin ias iproductive
ias iconceivable, ieverything ifactors iwhich ican iexpand ithe ilikelihood iof iprogress iand ireduction
ithe ivulnerability iof iaccomplishing itargets. iHazard ithe iexecutives iought ito ibe ia ideveloping
iinteraction. iSpecific iconsideration iought ito ibe igiven ito ithe iexecution iof ithe itechniques ifor
iwiping iout ior idecrease ithe idanger iand itheir imachine, ito ithe iinvestigation iof ithe ipast
idevelopment iof idangers iand ito ithe ipresent iand ifuture iexpectation iof ithe ioccasions. iThe iboard
iinteraction iought ito ibe iexecuted iat ithe imost ielevated iadministration ilevel. iIn iIT&C, ione iof ithe
imain iobjective iof ihazard ithe iexecutives iis ito iachieve iby ibetter igetting ithe iinformatics
iframeworks ithat istore, iprocess, ior icommunicate ihierarchical idata; iby iempowering ithe iboard
ito isettle ion iall iaround iinformed idanger ithe iexecutives ichoices ito ilegitimize ithe iconsumptions
ithat iare iessential ifor ian iIT ispending iplan iand iby ihelping ithe iboard iin iapproving i(or
iauthorizing) ithe iIT iframeworks, ibased ion ithe isupporting idocumentation icoming iabout
ibecause iof ithe iexhibition iof ihazard ithe iboard.
Another iexample iis ithe iIAM iframework:
How idoes iIAM iwork:
IAM istands ifor iInformation iand iManagement, iIAM itypically iis ia iframework ithat iconsists iof
ipolicies, iprocedures, iand ihigh-tech itechnology iwhich ienables iorganizations ito iprotect iand
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

imanage iuser idata iby icontrolling iaccess ieach iuser ihas, ithis iin iturn iprevents iunauthorized
iaccess ito isensitive iinformation. i
The imain iroles iof ian iIAM iplatform iare:
1. Confirm iand icertify iusers ifrom itheir ilocation, idate/time ietc.
2. Keep ia itrack iof iuser ilogins
3. Control iand iremove iany iuser iaccess i
4. The imanager iwould ihave icontrol ias ito irestrict iuser’s iaccess
Before ithe iIAM isystem iis iimplemented iin ian ienterprise, ithe imanagement ineeds ito idecide iwho
ifrom ithe iorganization iwill ihave ito iillustrate, idevelop, iand iapproach ipolicies.
IT iexperts iadministering iIAM ishould ifamiliarize ithemselves iwith ithe iOSA iIAM ipattern ifor
imanagement iof iidentity, iSP-010
i(https://www.techtarget.com/searchsecurity/definition/identity-access-management-IAM-
system)
iaccess ito isensitive iinformation. i
The imain iroles iof ian iIAM iplatform iare:
1. Confirm iand icertify iusers ifrom itheir ilocation, idate/time ietc.
2. Keep ia itrack iof iuser ilogins
3. Control iand iremove iany iuser iaccess i
4. The imanager iwould ihave icontrol ias ito irestrict iuser’s iaccess
Before ithe iIAM isystem iis iimplemented iin ian ienterprise, ithe imanagement ineeds ito idecide iwho
ifrom ithe iorganization iwill ihave ito iillustrate, idevelop, iand iapproach ipolicies.
IT iexperts iadministering iIAM ishould ifamiliarize ithemselves iwith ithe iOSA iIAM ipattern ifor
imanagement iof iidentity, iSP-010
i(https://www.techtarget.com/searchsecurity/definition/identity-access-management-IAM-
system)
P3
Firewalls:
Firewalls iare igadgets ior iprojects ithat icontrol ithe iprogression iof iorganization itraffic ibetween
iorganizations ior ihosts ithat iutilize icontrasting isecurity istances. iAt ione itime, imost ifirewalls
iwere iconveyed iat inetwork iborders. iThis
if isome iproportion iof iinsurance ifor iinside ihas, iyet iit icouldn't iperceive iall icases iand istructures
iof iassault, iand iassaults isent istarting iwith ione iinside ihave ithen ionto ithe inext ifrequently idon't
igo ithrough inetwork ifirewalls.
Rules iON iFIREWALLS iAND iFIREWALL iPOLICY:
Distinguish iall inecessities ithat iought ito ibe iviewed ias iwhile ifiguring iout iwhich ifirewall ito icarry
iout. iThere iare inumerous icontemplations ithat iassociations iought ito iremember ifor itheir ifirewall
Firewalls:
Firewalls iare igadgets ior iprojects ithat icontrol ithe iprogression iof iorganization itraffic ibetween
iorganizations ior ihosts ithat iutilize icontrasting isecurity istances. iAt ione itime, imost ifirewalls
iwere iconveyed iat inetwork iborders. iThis
if isome iproportion iof iinsurance ifor iinside ihas, iyet iit icouldn't iperceive iall icases iand istructures
iof iassault, iand iassaults isent istarting iwith ione iinside ihave ithen ionto ithe inext ifrequently idon't
igo ithrough inetwork ifirewalls.
Rules iON iFIREWALLS iAND iFIREWALL iPOLICY:
Distinguish iall inecessities ithat iought ito ibe iviewed ias iwhile ifiguring iout iwhich ifirewall ito icarry
iout. iThere iare inumerous icontemplations ithat iassociations iought ito iremember ifor itheir ifirewall
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

idetermination iand iarranging iprocesses. iAssociations ineed ito ifigure iout iwhich inetwork iregions
ishould ibe isecured, iand iwhich isorts iof ifirewall iadvancements iwill ibe ibest ifor ithe isorts iof itraffic
ithat irequire iassurance. iA ifew isignificant iexecution icontemplations iadditionally iexist, ijust ias
iworries iin iregard ito ithe ireconciliation iof ithe ifirewall iinto iexisting iorganization iand isecurity
iframeworks. iFurthermore, ifirewall iarrangement iconfiguration iincludes iprerequisites
iidentifying iwith iactual iclimate iand iwork iforce ijust ias ithought iof iconceivable ifuture ineeds, ifor
iexample, iplans ito itake ion inew iIPv6 iinnovations ior ivirtual iprivate iorganizations i(VPN). iMake
irulesets ithat iexecute ithe iassociation's ifirewall istrategy iwhile isupporting ifirewall iexecution.
There iare inumerous iviewpoints ito ifirewall ithe iboard. iFor iinstance, ipicking ithe isort ior ikinds iof
ifirewalls ito isend iand itheir isituations iinside ithe iorganization ican ialtogether iinfluence ithe
isecurity istrategies ithat ithe ifirewalls ican iauthorize. iStrategy irules imight ishould ibe irefreshed ias
ithe iassociation's iprerequisites ichange, ifor iexample, iwhen inew iapplications ior ihosts iare icarried
iout iinside ithe iorganization. iFirewall ipart iexecution ilikewise ishould ibe ichecked ito iempower
ipotential iasset iissues ito ibe idistinguished iand itended ito ibefore iparts ibecome ioverpowered.
iLogs iand icautions iought ito ilikewise ibe iconsistently iobserved ito irecognize idangers—both
ieffective iand iineffective. iFirewall irulesets iand iapproaches iought ito ibe ioverseen iby ia iformal
ichange ithe iboard icontrol iprocess ion iaccount iof itheir icapability ito iaffect isecurity iand ibusiness
itasks, iwith iruleset iaudits ior itests iperformed ioccasionally ito iguarantee iproceeded iwith
iconsistence iwith ithe iassociation's iarrangements. iFirewall iprogramming iought ito ibe ifixed ias
imerchants igive iupdates ito iaddress iweaknesses.
Incorrect iVPN iconfiguration iand iits iconsequences:
This iresults iwhen ian iunauthorized iperson isomehow igets ibetween ia iVPN iconnection, iand ithis
iis inormally idone iby ithese iattacks: iMan-In-The-Middle, iVPN ihijacking ior iwhen ithe iuser’s
iconnection iis irelatively iweak.
If iand iwhen ia iVPN iconnection ibreaks idown, ior ihas ibeen ihacked, ithe iuser iwill isee ia icode,
ihowever ithere iare ihundreds iof ivarious ierror icodes, ibelow iare isome ivery icommon:
• VPN i800: i
This ierror icode iarises iwhen ithe iconnection ibetween ithe iVPN iand ithe iuser icannot ibe
iestablished. iThis ihappens iwhen ithe iservice iprovider icannot iconnect ito ithe inetwork
iwhich ican ibe ia icause iof ioverloaded itraffic ion ithe inetwork, iand ithe iserver itemporarily
ihalts ito iwork.
• VPN i619:
This ierror icode ishows iup iwhen ithe ifirewall ior ithe iport iconfiguration iissue iprevents ithe
iVPN iuser ifrom iestablishing ia iconnection idespite iis iserver iis iin iaccess.
• VPN i691:
When ithe iuser iinputs iwrong ipassword ior iusername.
ishould ibe isecured, iand iwhich isorts iof ifirewall iadvancements iwill ibe ibest ifor ithe isorts iof itraffic
ithat irequire iassurance. iA ifew isignificant iexecution icontemplations iadditionally iexist, ijust ias
iworries iin iregard ito ithe ireconciliation iof ithe ifirewall iinto iexisting iorganization iand isecurity
iframeworks. iFurthermore, ifirewall iarrangement iconfiguration iincludes iprerequisites
iidentifying iwith iactual iclimate iand iwork iforce ijust ias ithought iof iconceivable ifuture ineeds, ifor
iexample, iplans ito itake ion inew iIPv6 iinnovations ior ivirtual iprivate iorganizations i(VPN). iMake
irulesets ithat iexecute ithe iassociation's ifirewall istrategy iwhile isupporting ifirewall iexecution.
There iare inumerous iviewpoints ito ifirewall ithe iboard. iFor iinstance, ipicking ithe isort ior ikinds iof
ifirewalls ito isend iand itheir isituations iinside ithe iorganization ican ialtogether iinfluence ithe
isecurity istrategies ithat ithe ifirewalls ican iauthorize. iStrategy irules imight ishould ibe irefreshed ias
ithe iassociation's iprerequisites ichange, ifor iexample, iwhen inew iapplications ior ihosts iare icarried
iout iinside ithe iorganization. iFirewall ipart iexecution ilikewise ishould ibe ichecked ito iempower
ipotential iasset iissues ito ibe idistinguished iand itended ito ibefore iparts ibecome ioverpowered.
iLogs iand icautions iought ito ilikewise ibe iconsistently iobserved ito irecognize idangers—both
ieffective iand iineffective. iFirewall irulesets iand iapproaches iought ito ibe ioverseen iby ia iformal
ichange ithe iboard icontrol iprocess ion iaccount iof itheir icapability ito iaffect isecurity iand ibusiness
itasks, iwith iruleset iaudits ior itests iperformed ioccasionally ito iguarantee iproceeded iwith
iconsistence iwith ithe iassociation's iarrangements. iFirewall iprogramming iought ito ibe ifixed ias
imerchants igive iupdates ito iaddress iweaknesses.
Incorrect iVPN iconfiguration iand iits iconsequences:
This iresults iwhen ian iunauthorized iperson isomehow igets ibetween ia iVPN iconnection, iand ithis
iis inormally idone iby ithese iattacks: iMan-In-The-Middle, iVPN ihijacking ior iwhen ithe iuser’s
iconnection iis irelatively iweak.
If iand iwhen ia iVPN iconnection ibreaks idown, ior ihas ibeen ihacked, ithe iuser iwill isee ia icode,
ihowever ithere iare ihundreds iof ivarious ierror icodes, ibelow iare isome ivery icommon:
• VPN i800: i
This ierror icode iarises iwhen ithe iconnection ibetween ithe iVPN iand ithe iuser icannot ibe
iestablished. iThis ihappens iwhen ithe iservice iprovider icannot iconnect ito ithe inetwork
iwhich ican ibe ia icause iof ioverloaded itraffic ion ithe inetwork, iand ithe iserver itemporarily
ihalts ito iwork.
• VPN i619:
This ierror icode ishows iup iwhen ithe ifirewall ior ithe iport iconfiguration iissue iprevents ithe
iVPN iuser ifrom iestablishing ia iconnection idespite iis iserver iis iin iaccess.
• VPN i691:
When ithe iuser iinputs iwrong ipassword ior iusername.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P4
Example iof iDMZ iImplementation
This isection ireviews ithe ibasic iconsiderations iyou ishould ikeep iin imind iwhen idesigning iyour
iDMZ iand isetting iit iup iin ithe iApp iNetwork iManager.
For iexample, iif iyou ihave itwo iweb iservers iand ia imail iserver iin iyour ibusiness inetwork. iThese
iservers ishould ibe iaccessible iboth ivia iLAN iand inetwork i/ iWAN idevices, iso iyou imay iwant ito
istay iseparate ifrom iyour ibusiness inetwork ito iensure ithat iexternal idevices ido inot iuse ithese
iservers ito iinitiate iintrusion iattacks. i
Create ia iDMZ iby isetting ia iprivate isubnet ion iyour iLAN ithat iincludes ionly ithese ithree iservers.
iAt iyour iCourante iServices iGateway, iset iup ian ioptical iEthernet iconnector ithat iresides ion ithis
iprivate isubnet. iRegister iat ileast ione iportable iWAN iport iconnector ithat ican ibe iused iby ione iof
ithe iweb iservers.
Configure ithe iDefault iUser iGroup i- iDMZ iat iyour igateway iIn iApp iNet iManager iwhich
iincludes ia iprivate isubnet iresides ion ithe imail iserver iand iweb iservers. iFor iweb ihosting, iregister
ithe iHTTP iapplication ion ithe iApplications ifor ieach iweb iserver iBy iusing ia iweb iserver iwith
iprivate iIP iaddresses. iFor imail icapacity, iregister itwo imail iserver iapplications ion ithe
iApplications itab iusing ithe iprivate imail iserver iaddress. iOne iapplication ishould iallow iPOP
itraffic, iwhile ianother iapplication ishould iallow iSMTP itraffic.
To icontrol iaccess ito iDMZ, iedit iyour iFirewall iand iDMZ iPolicies ifor iInternet iand iLAN iAccess
ifor iDMZ iPartners iAccess ithe iPartner iGate iForms iPartner itab.
The iDMZ ipartner ito ithe iInternet imust ihave iat ileast ithree itubes: ione ifor ithe ifirst iweb iserver
isystem ivia ithe iWAN iport iinterface, ione ifor ithe isecond iweb iserver iprogram iwith ithe iname
iaddress, iand ione ifor ithe iSMTP imail iserver iapplication ivia ithe iWAN igateway iinterface.The
iLAN ipartner ito iDMZ iAccess ican ibe ieasily iconfigured iand imaintain isecurity. iYou ican icreate ia
itube ithat iallows ithe ientire iLAN ito iaccess ithe ientire iDefault iUser iGroup i- iDMZ, iWith iFirewall
iPolicy ithat iallows iall itraffic ifrom iLAN ito iDMZ ibut irestricts iall itraffic ifrom iDMZ ito iLAN.
iNote ithat iFirewall iPolicy ispecifies iwho iis iallowed ito istart ithe iconnection, ibut iall iretrieval
itraffic ifrom ithe iconnection iis ialways iallowed.
If iyou iwould ilike ito icreate ia ivalid iset iof ipermissions, ithis ipartner imust ihave ias imany itubes ias
ineeded ito iaccess iand imanage iDMZ iservers. iThere ishould ibe iat ileast ithree itubes: ione ifor ithe
ifirst iweb iserver iapplication, ione ifor ithe isecond iweb iserver iprogram, iand ione ifor ithe iPOP imail
iserver iapplication. iYou imay ialso iwant ito icreate ia itube ithat iallows ithe itype iof itraffic irequired
ito imaintain iand iupgrade iall iDMZ iservers ifrom ithe iLAN, iusing ithe iDefault iUser iGroup i- iDMZ
iand iFirewall iPolicy iwhich ionly iallow ithe itype iof itraffic iused ito istore iand iupdate.
Examples iof iStatic iIP iand iNAT i
A ifixed iIP iaddress iand iNAT iis isimply ia ifixed iaddress. iIf iyour idevice iis iassigned ia ifixed
iInternet iaddress, ithat inumber iusually iremains ithe isame iuntil ithe idevice istops iworking ior
ichanges iyour inetwork iconfiguration. iStrong iIP iaddresses iand iNAT iare ioften iused iby iservers
Example iof iDMZ iImplementation
This isection ireviews ithe ibasic iconsiderations iyou ishould ikeep iin imind iwhen idesigning iyour
iDMZ iand isetting iit iup iin ithe iApp iNetwork iManager.
For iexample, iif iyou ihave itwo iweb iservers iand ia imail iserver iin iyour ibusiness inetwork. iThese
iservers ishould ibe iaccessible iboth ivia iLAN iand inetwork i/ iWAN idevices, iso iyou imay iwant ito
istay iseparate ifrom iyour ibusiness inetwork ito iensure ithat iexternal idevices ido inot iuse ithese
iservers ito iinitiate iintrusion iattacks. i
Create ia iDMZ iby isetting ia iprivate isubnet ion iyour iLAN ithat iincludes ionly ithese ithree iservers.
iAt iyour iCourante iServices iGateway, iset iup ian ioptical iEthernet iconnector ithat iresides ion ithis
iprivate isubnet. iRegister iat ileast ione iportable iWAN iport iconnector ithat ican ibe iused iby ione iof
ithe iweb iservers.
Configure ithe iDefault iUser iGroup i- iDMZ iat iyour igateway iIn iApp iNet iManager iwhich
iincludes ia iprivate isubnet iresides ion ithe imail iserver iand iweb iservers. iFor iweb ihosting, iregister
ithe iHTTP iapplication ion ithe iApplications ifor ieach iweb iserver iBy iusing ia iweb iserver iwith
iprivate iIP iaddresses. iFor imail icapacity, iregister itwo imail iserver iapplications ion ithe
iApplications itab iusing ithe iprivate imail iserver iaddress. iOne iapplication ishould iallow iPOP
itraffic, iwhile ianother iapplication ishould iallow iSMTP itraffic.
To icontrol iaccess ito iDMZ, iedit iyour iFirewall iand iDMZ iPolicies ifor iInternet iand iLAN iAccess
ifor iDMZ iPartners iAccess ithe iPartner iGate iForms iPartner itab.
The iDMZ ipartner ito ithe iInternet imust ihave iat ileast ithree itubes: ione ifor ithe ifirst iweb iserver
isystem ivia ithe iWAN iport iinterface, ione ifor ithe isecond iweb iserver iprogram iwith ithe iname
iaddress, iand ione ifor ithe iSMTP imail iserver iapplication ivia ithe iWAN igateway iinterface.The
iLAN ipartner ito iDMZ iAccess ican ibe ieasily iconfigured iand imaintain isecurity. iYou ican icreate ia
itube ithat iallows ithe ientire iLAN ito iaccess ithe ientire iDefault iUser iGroup i- iDMZ, iWith iFirewall
iPolicy ithat iallows iall itraffic ifrom iLAN ito iDMZ ibut irestricts iall itraffic ifrom iDMZ ito iLAN.
iNote ithat iFirewall iPolicy ispecifies iwho iis iallowed ito istart ithe iconnection, ibut iall iretrieval
itraffic ifrom ithe iconnection iis ialways iallowed.
If iyou iwould ilike ito icreate ia ivalid iset iof ipermissions, ithis ipartner imust ihave ias imany itubes ias
ineeded ito iaccess iand imanage iDMZ iservers. iThere ishould ibe iat ileast ithree itubes: ione ifor ithe
ifirst iweb iserver iapplication, ione ifor ithe isecond iweb iserver iprogram, iand ione ifor ithe iPOP imail
iserver iapplication. iYou imay ialso iwant ito icreate ia itube ithat iallows ithe itype iof itraffic irequired
ito imaintain iand iupgrade iall iDMZ iservers ifrom ithe iLAN, iusing ithe iDefault iUser iGroup i- iDMZ
iand iFirewall iPolicy iwhich ionly iallow ithe itype iof itraffic iused ito istore iand iupdate.
Examples iof iStatic iIP iand iNAT i
A ifixed iIP iaddress iand iNAT iis isimply ia ifixed iaddress. iIf iyour idevice iis iassigned ia ifixed
iInternet iaddress, ithat inumber iusually iremains ithe isame iuntil ithe idevice istops iworking ior
ichanges iyour inetwork iconfiguration. iStrong iIP iaddresses iand iNAT iare ioften iused iby iservers
ior iother iimportant iobjects. iStable iIP iaddresses iare iprovided iby iInternet iService iProviders
i(ISPs). iYour iISP imay ior imay inot iprovide iyou iwith ia ifixed iIP iaddress idepending ion ithe itype iof
iyour iservice iagreement. iI iexplain iyour ioptions ilater, ibut ifor inow iwe ithink ithat ia ifixed iIP
iaddress iadds ito ithe icost iof iyour iISP icontract. iIn ithis icase ithe iessential iquality istands. iOne iday,
ievery ipart iof ithe inetwork iwe ihave imay ihave ia idifferent iIPv6 ifixed iaddress. iNow, iwe iusually
iuse iIPv4 iaddresses ithat iare ifixed ito ipermanent iaddresses. i
For iexample, iif ithe idefault iIP iaddress iand iNAT iis iset ito ia icomputer iin ithe ihome inetwork. iIf
ithe icomputer ihas ia ispecific iaddress iattached, ithe irouter ican ibe iset ito ialways iforward icertain
iapplications ithat ido inot ireceive idirectly ito ithat icomputer, isuch ias iFTP irequests iwhen ithe
icomputer iis isharing ifiles ivia iFTP. iNot iusing ia ifixed iIP iaddress iand iNAT iis idifficult iwhen
ihosting ia iwebsite, ifor iexample, ibecause iwith ievery inew iIP iaddress ia icomputer ireceives, iyou
ihave ito ichange ithe irouter isettings ito iforward irequests. iNeglecting ithis iwill imean ithat ino ione
ican iaccess iyour iwebsite ibecause ithe irouter idoes inot iknow iwhich idevice iin ithe inetwork iis
irunning ithe iwebsite. iAnother iexample iof ia iStatic iIP iand iNAT iat iwork iis iDNS iservers. iDNS
iservers iuse istatic iIP iaddresses ito ikeep idevices iconnected ito ieach iother. iIf ithey ichange
ifrequently, iyou iwill ineed ito ireset ithose iDNS iservers ion iyour irouter ior icomputer iin iorder ito iuse
ithe iInternet.
P5
i
Risk iassessment iprocedures:
A ifast iand iefficient iway iRisk imanagement ican ibe iapproached ifor iboth imethods: ieffective iand
iefficient. iReactive imethod imay ibe ian ieffective iresponse ito isafety ihazards ithat ihave ialready
ioccurred iby icreating isecurity iincidents. iI ianalysis iof ithe icauses iof isecurity igeneration
iincidents ican ihelp ian iorganization ito iprevent itheir irepetition iand ibe iprepared iany ipotential
iproblems. iCompanies ithat iresponding ito isecurity iincidents icalmly iand i ilogical iapproach, ifor
inow ithey idecide ireasons ithat iallowed iincidents ithat iit ihappens, iyou iwill ibe iable ito irespond iin ia
imoment ithe itiming iof ithe iemergence iof isimilar iproblems.
There iare ifive isteps ito ithat iorganization ishould ibe iconsidered iif ioperating imethod iused:
1. iTo iprotect ihuman ihealth iand isafety
It iis ivery iimportant iand ivery ieffective isix. iOrganizations imust irespect ithe irules iwhich iprotects
iemployers iand irequires ithem ipreventive imeasures ito iprevent iwork iaccidents. iComputer
idevelopment iof ithe iproduction iprocess ihas iled imany iof ithem iactivities iin ithe iorganization iso
ithey ioften ido iarises ifrom iwhere ithe irisk iof iproduction iand isecurity iof itheir iinformation
isystems iare ipossible iendangering ihuman ilife iand ihealth.
2. iDamage icontrol
It iis ia ifunction ithat iconsists iof istanding ior ito icontrol ithe ispread iof idamage iis iproduced iwith ia
icompleted irisk. iIf iit ihappens iof icyberattacks, iorganizations ishould itake iyou iinformation
iprotection iactions, iwhich iare iimportant ioperating isystem iand ihardware icomponents, isuch ias
isoon ias ipossible, iand ishorten ithe itime iwhen ithe isystem iis inot iworking iproperly. iSometimes ito
ikeep ithe isystem iin iplace, iduring isuch ian iattack, iit imay iincrease idamage.
i(ISPs). iYour iISP imay ior imay inot iprovide iyou iwith ia ifixed iIP iaddress idepending ion ithe itype iof
iyour iservice iagreement. iI iexplain iyour ioptions ilater, ibut ifor inow iwe ithink ithat ia ifixed iIP
iaddress iadds ito ithe icost iof iyour iISP icontract. iIn ithis icase ithe iessential iquality istands. iOne iday,
ievery ipart iof ithe inetwork iwe ihave imay ihave ia idifferent iIPv6 ifixed iaddress. iNow, iwe iusually
iuse iIPv4 iaddresses ithat iare ifixed ito ipermanent iaddresses. i
For iexample, iif ithe idefault iIP iaddress iand iNAT iis iset ito ia icomputer iin ithe ihome inetwork. iIf
ithe icomputer ihas ia ispecific iaddress iattached, ithe irouter ican ibe iset ito ialways iforward icertain
iapplications ithat ido inot ireceive idirectly ito ithat icomputer, isuch ias iFTP irequests iwhen ithe
icomputer iis isharing ifiles ivia iFTP. iNot iusing ia ifixed iIP iaddress iand iNAT iis idifficult iwhen
ihosting ia iwebsite, ifor iexample, ibecause iwith ievery inew iIP iaddress ia icomputer ireceives, iyou
ihave ito ichange ithe irouter isettings ito iforward irequests. iNeglecting ithis iwill imean ithat ino ione
ican iaccess iyour iwebsite ibecause ithe irouter idoes inot iknow iwhich idevice iin ithe inetwork iis
irunning ithe iwebsite. iAnother iexample iof ia iStatic iIP iand iNAT iat iwork iis iDNS iservers. iDNS
iservers iuse istatic iIP iaddresses ito ikeep idevices iconnected ito ieach iother. iIf ithey ichange
ifrequently, iyou iwill ineed ito ireset ithose iDNS iservers ion iyour irouter ior icomputer iin iorder ito iuse
ithe iInternet.
P5
i
Risk iassessment iprocedures:
A ifast iand iefficient iway iRisk imanagement ican ibe iapproached ifor iboth imethods: ieffective iand
iefficient. iReactive imethod imay ibe ian ieffective iresponse ito isafety ihazards ithat ihave ialready
ioccurred iby icreating isecurity iincidents. iI ianalysis iof ithe icauses iof isecurity igeneration
iincidents ican ihelp ian iorganization ito iprevent itheir irepetition iand ibe iprepared iany ipotential
iproblems. iCompanies ithat iresponding ito isecurity iincidents icalmly iand i ilogical iapproach, ifor
inow ithey idecide ireasons ithat iallowed iincidents ithat iit ihappens, iyou iwill ibe iable ito irespond iin ia
imoment ithe itiming iof ithe iemergence iof isimilar iproblems.
There iare ifive isteps ito ithat iorganization ishould ibe iconsidered iif ioperating imethod iused:
1. iTo iprotect ihuman ihealth iand isafety
It iis ivery iimportant iand ivery ieffective isix. iOrganizations imust irespect ithe irules iwhich iprotects
iemployers iand irequires ithem ipreventive imeasures ito iprevent iwork iaccidents. iComputer
idevelopment iof ithe iproduction iprocess ihas iled imany iof ithem iactivities iin ithe iorganization iso
ithey ioften ido iarises ifrom iwhere ithe irisk iof iproduction iand isecurity iof itheir iinformation
isystems iare ipossible iendangering ihuman ilife iand ihealth.
2. iDamage icontrol
It iis ia ifunction ithat iconsists iof istanding ior ito icontrol ithe ispread iof idamage iis iproduced iwith ia
icompleted irisk. iIf iit ihappens iof icyberattacks, iorganizations ishould itake iyou iinformation
iprotection iactions, iwhich iare iimportant ioperating isystem iand ihardware icomponents, isuch ias
isoon ias ipossible, iand ishorten ithe itime iwhen ithe isystem iis inot iworking iproperly. iSometimes ito
ikeep ithe isystem iin iplace, iduring isuch ian iattack, iit imay iincrease idamage.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




