MCTC School of Technology Security Labs: Password Cracking Methods
VerifiedAdded on 2022/09/29
|18
|2938
|23
Practical Assignment
AI Summary
This practical assignment from MCTC School of Technology's Security Labs focuses on password cracking techniques and web application security. Students are guided through setting up DVWA (Damn Vulnerable Web Application), a deliberately vulnerable web application, to learn about security flaws. The lab covers SQL injection to discover usernames and password hashes, and then utilizes John the Ripper to crack the hashes. The assignment also explores brute-force attacks using Hydra, including how to defend against such attacks. Students are required to answer questions throughout the lab, demonstrating their understanding of password security, SQL injection, and defensive measures. The assignment concludes with cleaning up the environment and emphasizes the importance of responsible use of the tools and techniques learned.

MCTC School of Technology Security Labs
Password cracking Methods for discovering a user’s password are
well known and easily acquired even by novice hackers. By learning
what types of passwords are more secure developers and users can
follow good practices.
Please type your name or the names of your lab team here:
Password Cracking with DVWA, Hydra and John the Ripper
As you know: all of the tools and hacking techniques in this class are to be used ONLY for LEGAL
purposes. You should NOT use any of these techniques to gain unauthorized access to any system.
It is STRONGLY recommended to work on this lab with a Live Kali DVD/USB on one of our
machines, not your own computer. If you do choose to use your own computer, make sure you
remove DVWA and shut down the web server at the end of the lab.
Please follow the directions in the lab, and answer the questions highlighted in yellow in this worksheet.
When you have finished, save this worksheet, and turn in your lab worksheet by submitting it to the
appropriate Lab dropbox in D2L. For example, this lab should be submitted to the Lab 7 dropbox.
If you have any questions, please ask me.
Part 1: Installing DVWA
DVWA = Damn Vulnerable Web Application, a web application build with many deliberate security
errors. It's designed for learning about security flaws that may be present in real web applications, to give
insight into how to avoid vulnerabilities and improve security.
In Kali, go to DVWA.co.uk and click download.
Password cracking Methods for discovering a user’s password are
well known and easily acquired even by novice hackers. By learning
what types of passwords are more secure developers and users can
follow good practices.
Please type your name or the names of your lab team here:
Password Cracking with DVWA, Hydra and John the Ripper
As you know: all of the tools and hacking techniques in this class are to be used ONLY for LEGAL
purposes. You should NOT use any of these techniques to gain unauthorized access to any system.
It is STRONGLY recommended to work on this lab with a Live Kali DVD/USB on one of our
machines, not your own computer. If you do choose to use your own computer, make sure you
remove DVWA and shut down the web server at the end of the lab.
Please follow the directions in the lab, and answer the questions highlighted in yellow in this worksheet.
When you have finished, save this worksheet, and turn in your lab worksheet by submitting it to the
appropriate Lab dropbox in D2L. For example, this lab should be submitted to the Lab 7 dropbox.
If you have any questions, please ask me.
Part 1: Installing DVWA
DVWA = Damn Vulnerable Web Application, a web application build with many deliberate security
errors. It's designed for learning about security flaws that may be present in real web applications, to give
insight into how to avoid vulnerabilities and improve security.
In Kali, go to DVWA.co.uk and click download.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MCTC School of Technology Security Labs
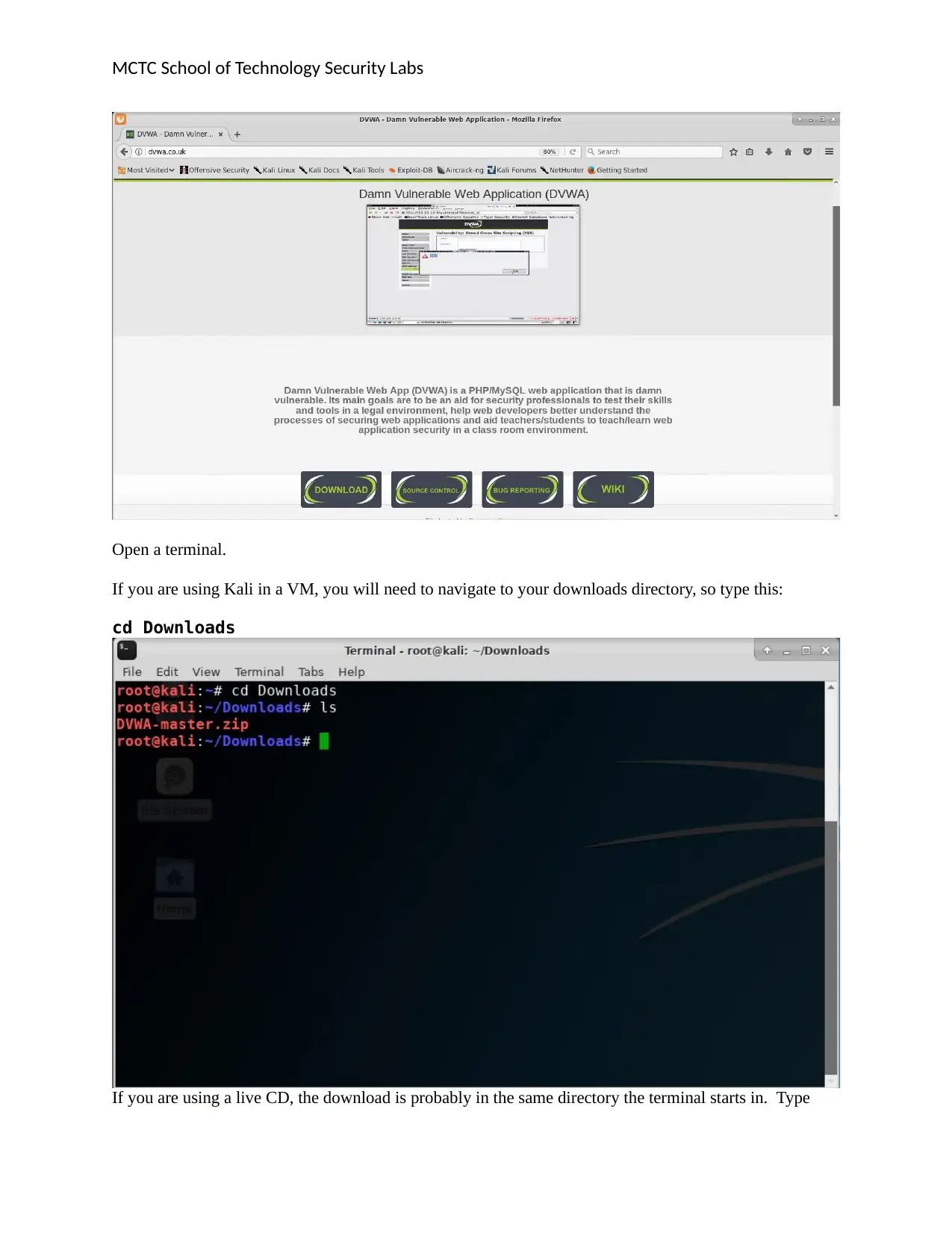
Open a terminal.
If you are using Kali in a VM, you will need to navigate to your downloads directory, so type this:
cd Downloads
If you are using a live CD, the download is probably in the same directory the terminal starts in. Type
Open a terminal.
If you are using Kali in a VM, you will need to navigate to your downloads directory, so type this:
cd Downloads
If you are using a live CD, the download is probably in the same directory the terminal starts in. Type
MCTC School of Technology Security Labs
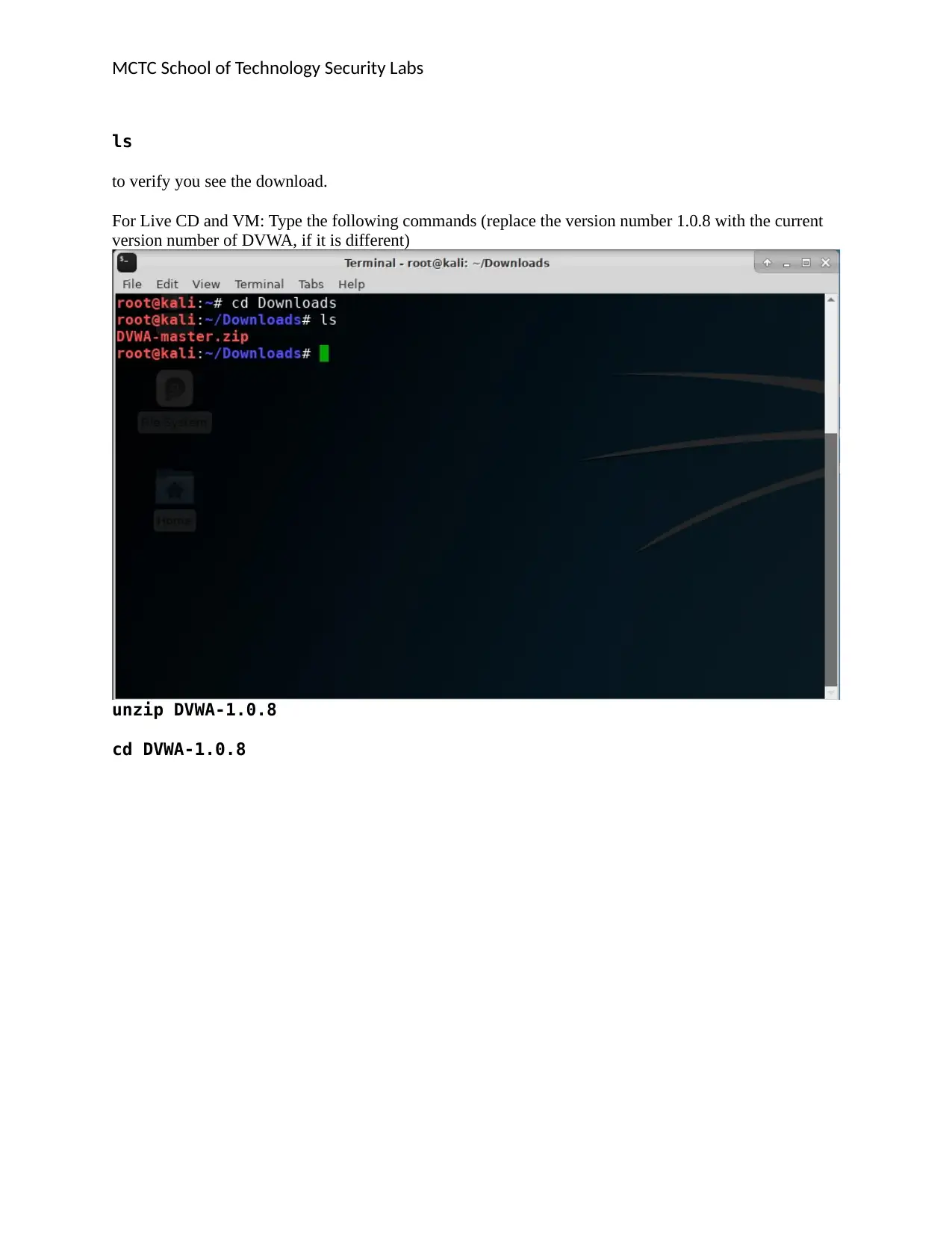
ls
to verify you see the download.
For Live CD and VM: Type the following commands (replace the version number 1.0.8 with the current
version number of DVWA, if it is different)
unzip DVWA-1.0.8
cd DVWA-1.0.8
ls
to verify you see the download.
For Live CD and VM: Type the following commands (replace the version number 1.0.8 with the current
version number of DVWA, if it is different)
unzip DVWA-1.0.8
cd DVWA-1.0.8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
MCTC School of Technology Security Labs
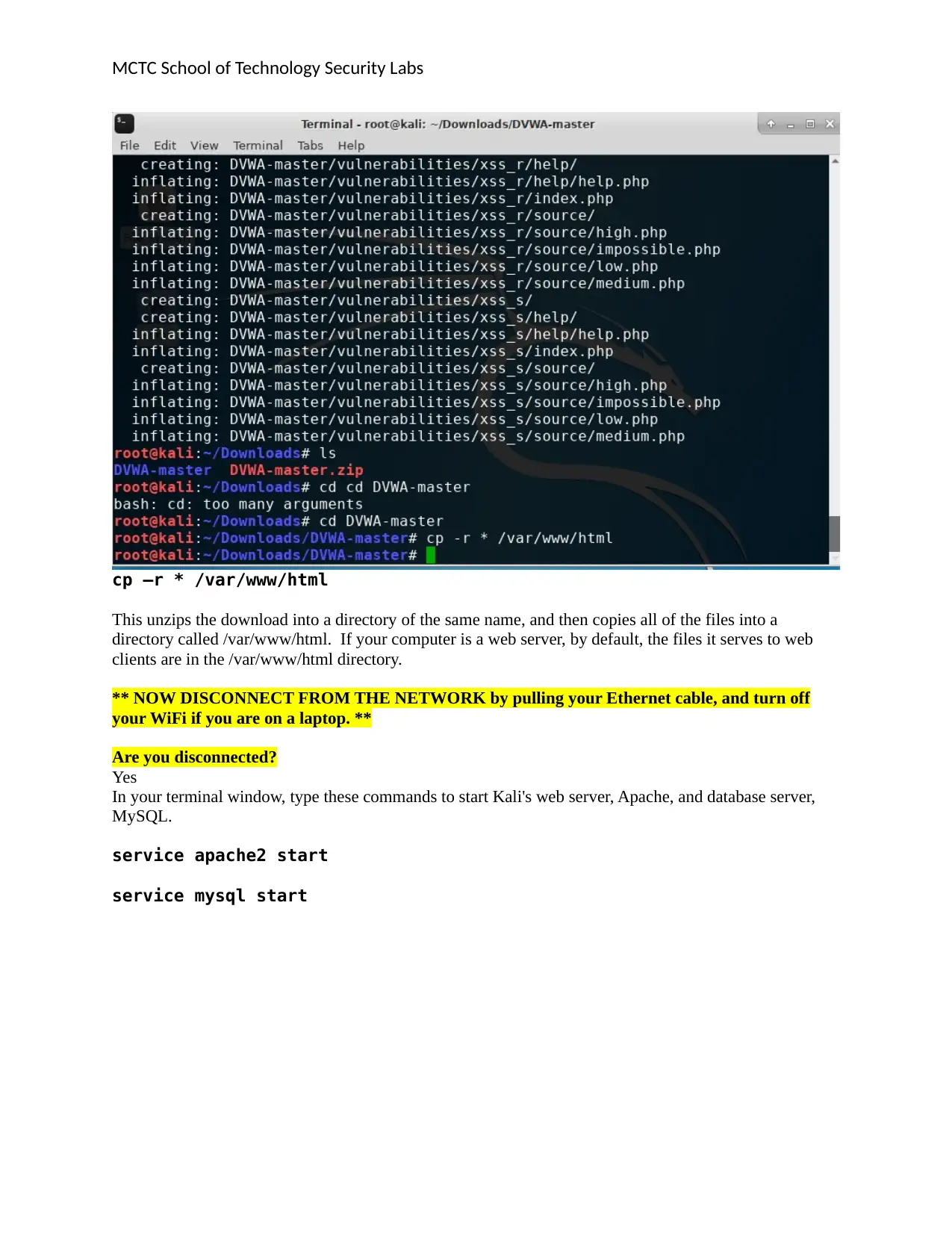
cp –r * /var/www/html
This unzips the download into a directory of the same name, and then copies all of the files into a
directory called /var/www/html. If your computer is a web server, by default, the files it serves to web
clients are in the /var/www/html directory.
** NOW DISCONNECT FROM THE NETWORK by pulling your Ethernet cable, and turn off
your WiFi if you are on a laptop. **
Are you disconnected?
Yes
In your terminal window, type these commands to start Kali's web server, Apache, and database server,
MySQL.
service apache2 start
service mysql start
cp –r * /var/www/html
This unzips the download into a directory of the same name, and then copies all of the files into a
directory called /var/www/html. If your computer is a web server, by default, the files it serves to web
clients are in the /var/www/html directory.
** NOW DISCONNECT FROM THE NETWORK by pulling your Ethernet cable, and turn off
your WiFi if you are on a laptop. **
Are you disconnected?
Yes
In your terminal window, type these commands to start Kali's web server, Apache, and database server,
MySQL.
service apache2 start
service mysql start
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MCTC School of Technology Security Labs
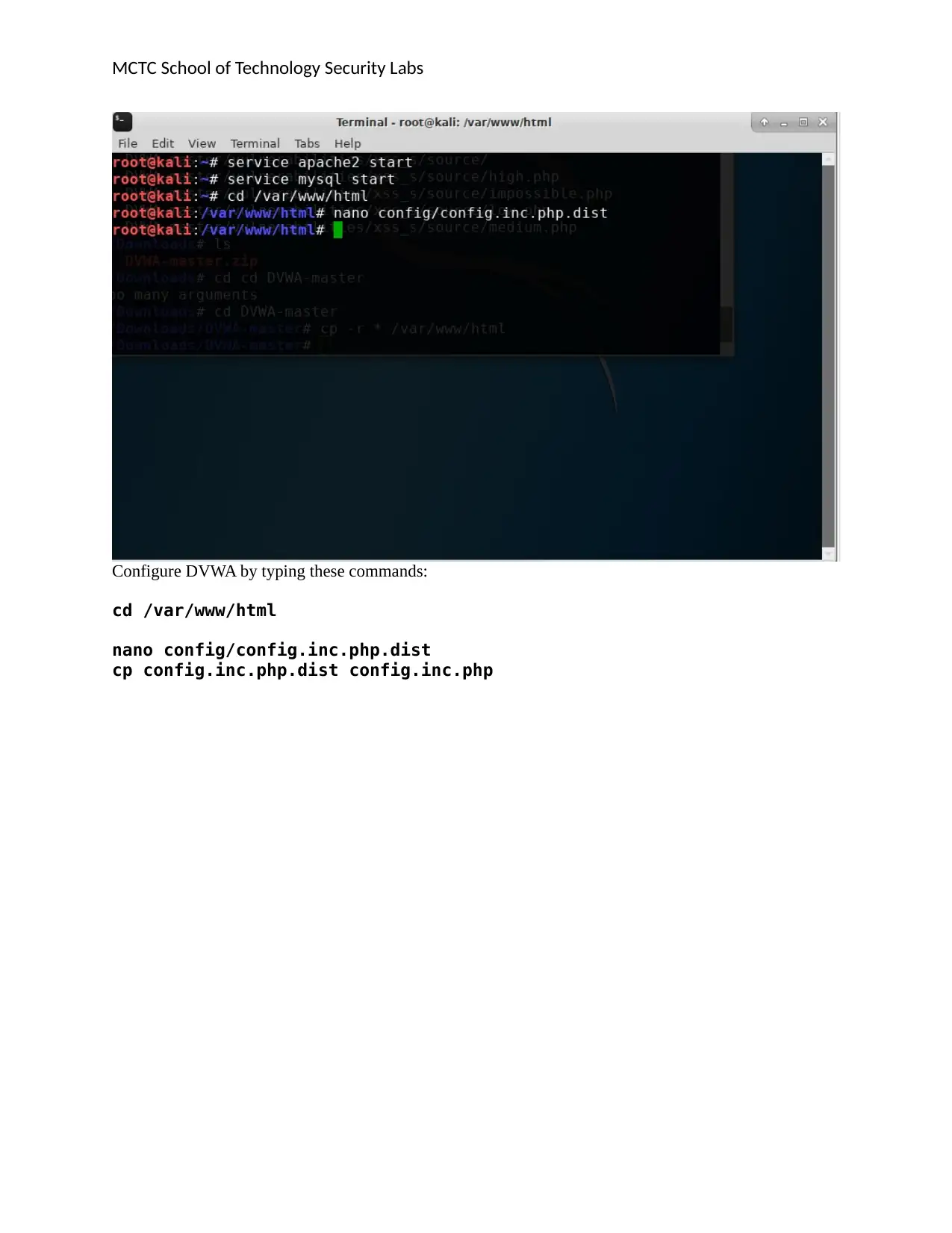
Configure DVWA by typing these commands:
cd /var/www/html
nano config/config.inc.php.dist
cp config.inc.php.dist config.inc.php
Configure DVWA by typing these commands:
cd /var/www/html
nano config/config.inc.php.dist
cp config.inc.php.dist config.inc.php
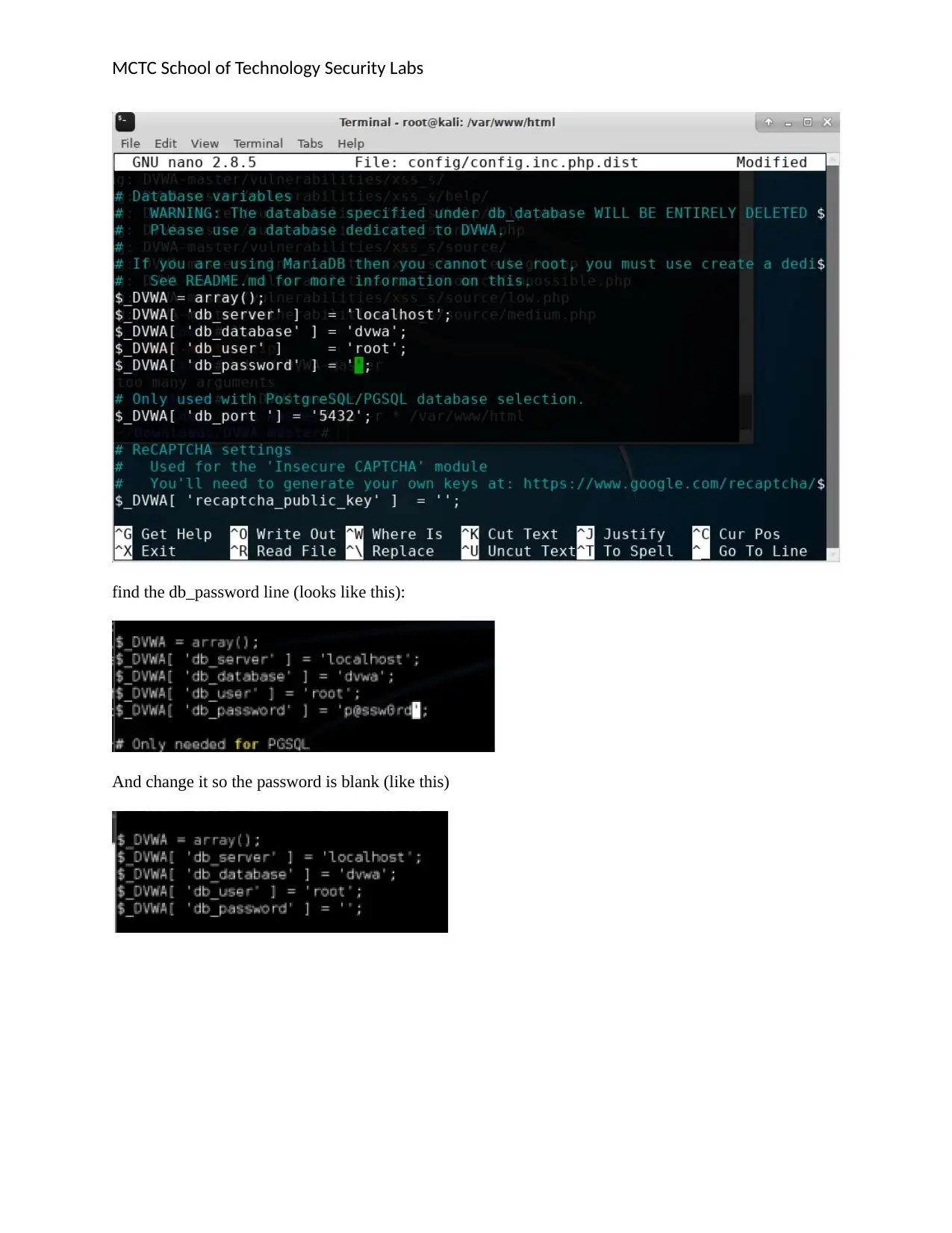
MCTC School of Technology Security Labs
find the db_password line (looks like this):
And change it so the password is blank (like this)
find the db_password line (looks like this):
And change it so the password is blank (like this)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
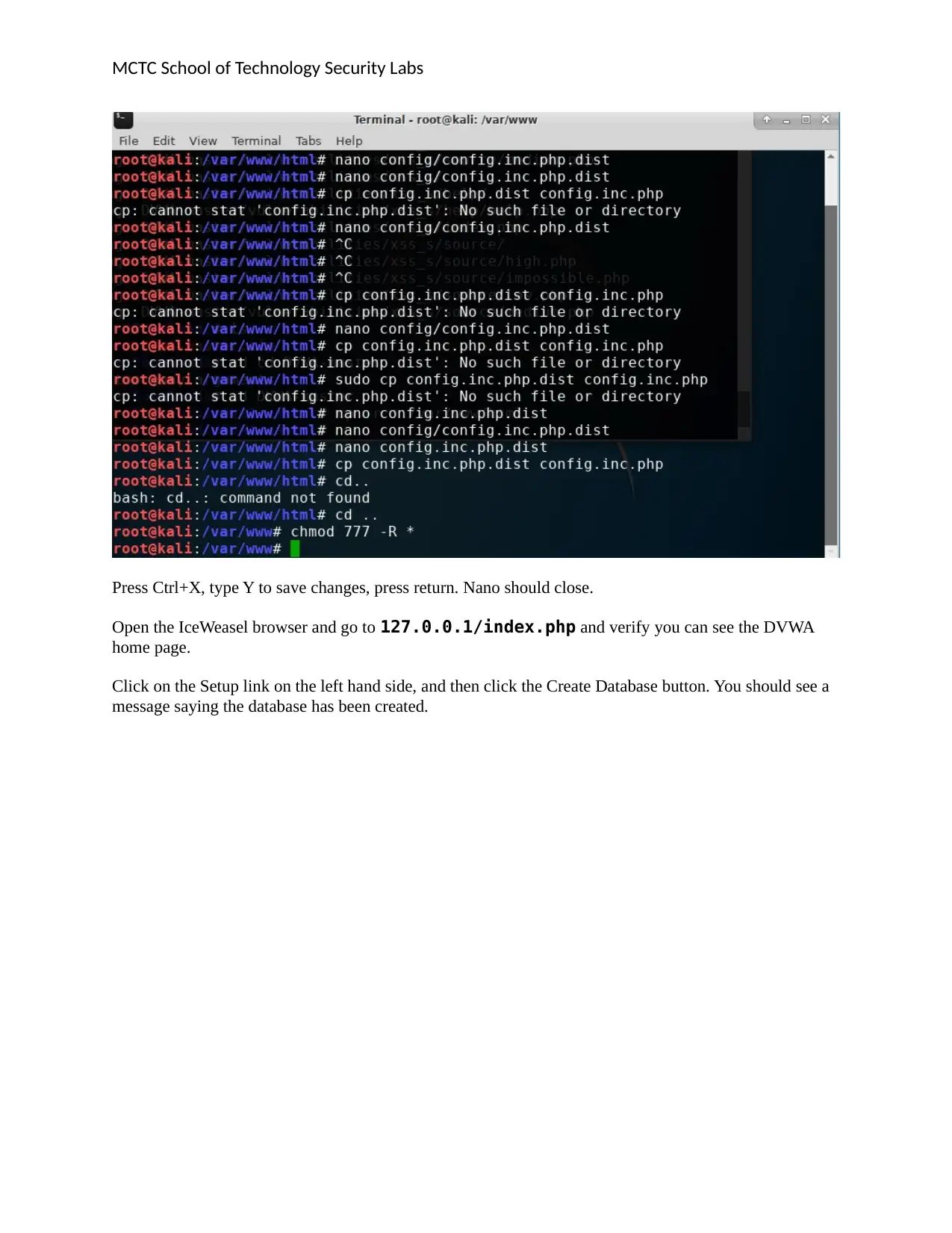
MCTC School of Technology Security Labs
Press Ctrl+X, type Y to save changes, press return. Nano should close.
Open the IceWeasel browser and go to 127.0.0.1/index.php and verify you can see the DVWA
home page.
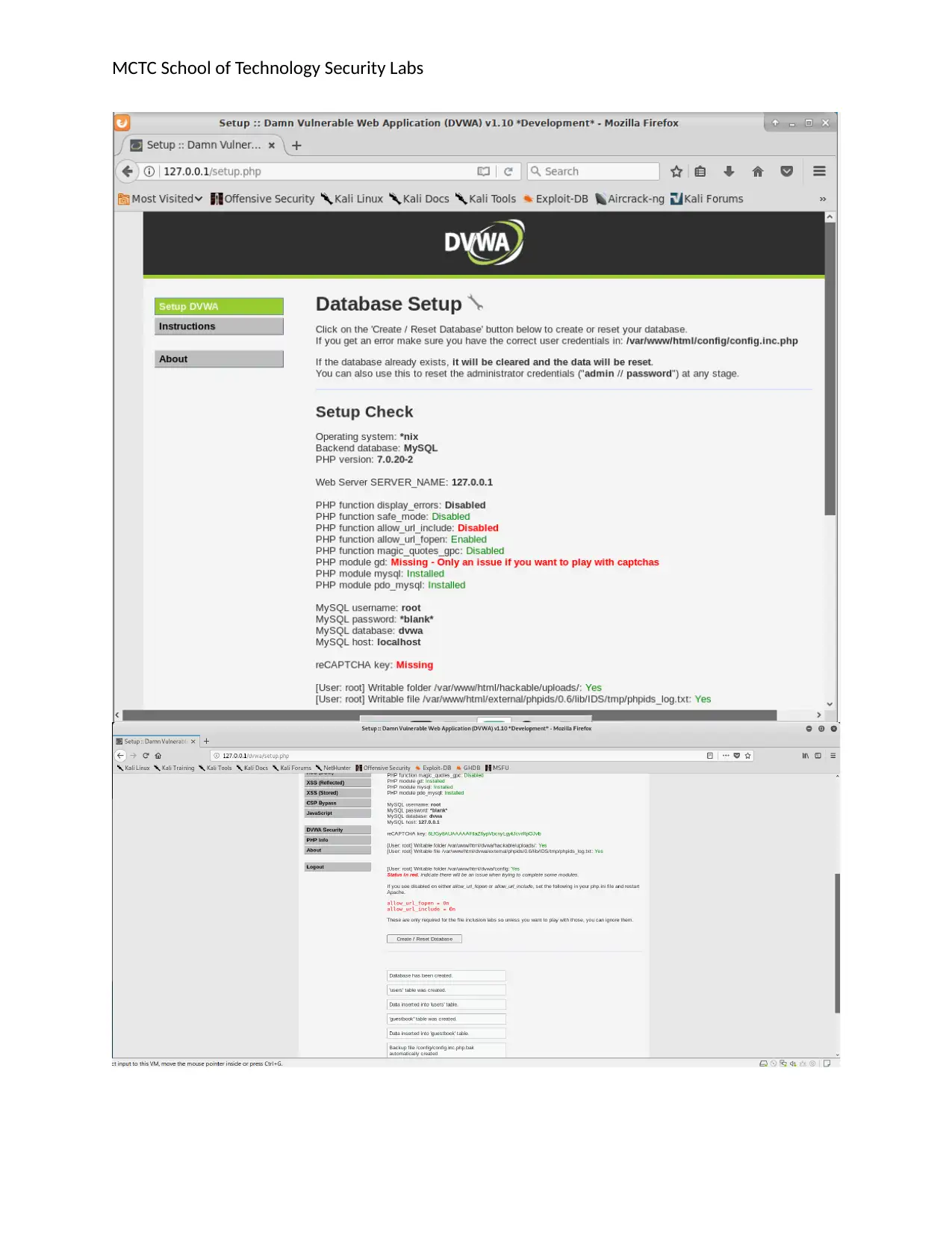
Click on the Setup link on the left hand side, and then click the Create Database button. You should see a
message saying the database has been created.
Press Ctrl+X, type Y to save changes, press return. Nano should close.
Open the IceWeasel browser and go to 127.0.0.1/index.php and verify you can see the DVWA
home page.
Click on the Setup link on the left hand side, and then click the Create Database button. You should see a
message saying the database has been created.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MCTC School of Technology Security Labs
MCTC School of Technology Security Labs
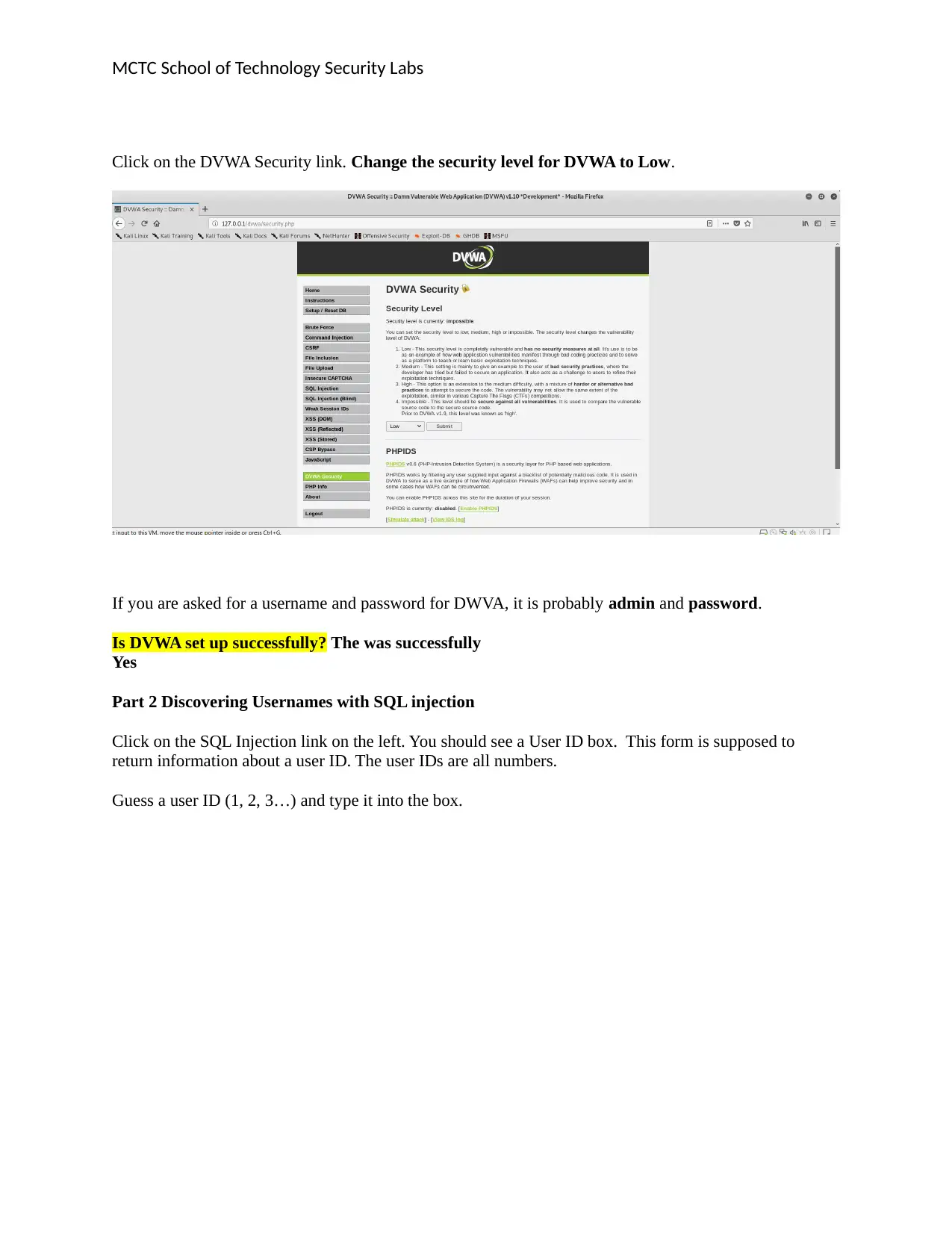
Click on the DVWA Security link. Change the security level for DVWA to Low.
If you are asked for a username and password for DWVA, it is probably admin and password.
Is DVWA set up successfully? The was successfully
Yes
Part 2 Discovering Usernames with SQL injection
Click on the SQL Injection link on the left. You should see a User ID box. This form is supposed to
return information about a user ID. The user IDs are all numbers.
Guess a user ID (1, 2, 3…) and type it into the box.
Click on the DVWA Security link. Change the security level for DVWA to Low.
If you are asked for a username and password for DWVA, it is probably admin and password.
Is DVWA set up successfully? The was successfully
Yes
Part 2 Discovering Usernames with SQL injection
Click on the SQL Injection link on the left. You should see a User ID box. This form is supposed to
return information about a user ID. The user IDs are all numbers.
Guess a user ID (1, 2, 3…) and type it into the box.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
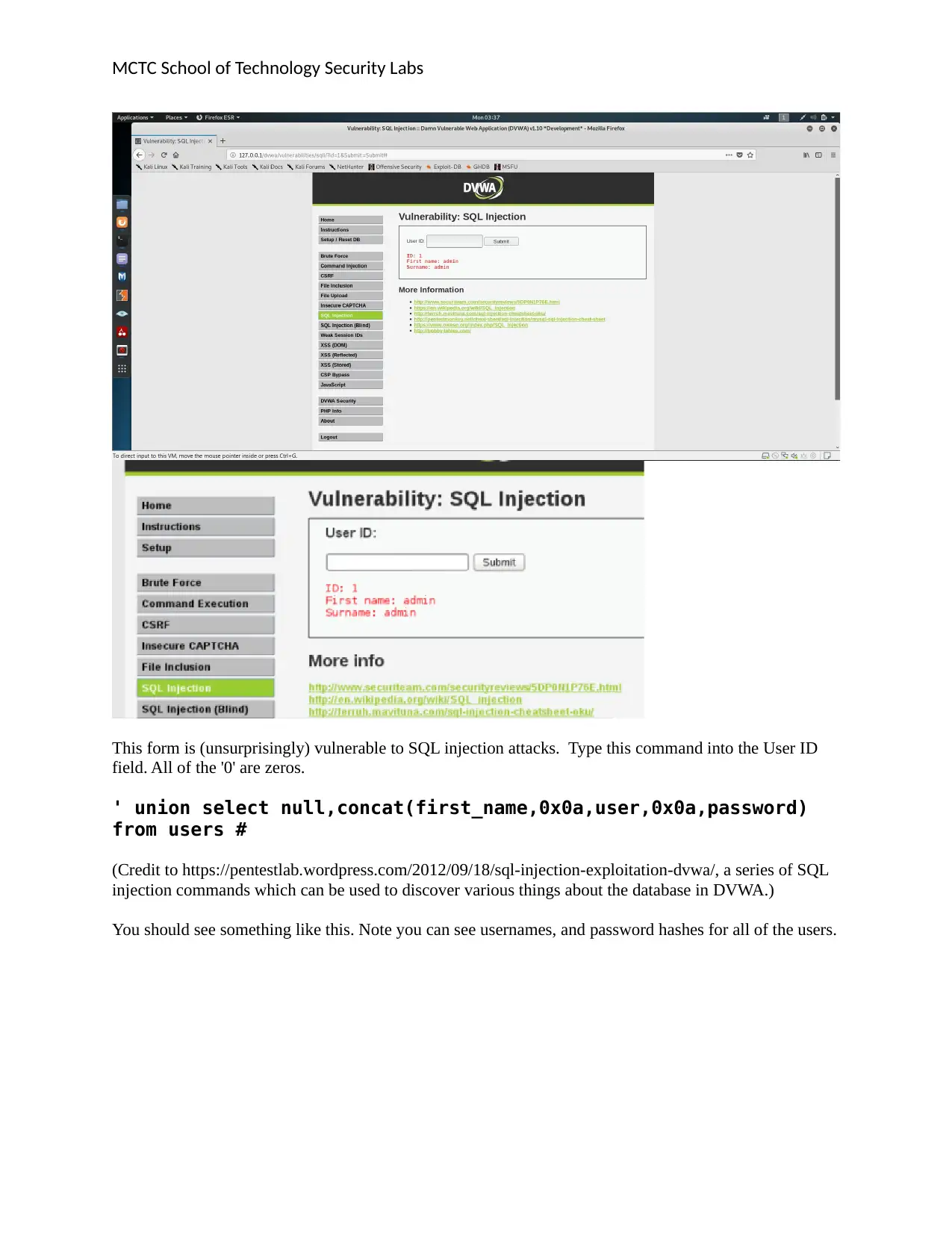
MCTC School of Technology Security Labs
This form is (unsurprisingly) vulnerable to SQL injection attacks. Type this command into the User ID
field. All of the '0' are zeros.
' union select null,concat(first_name,0x0a,user,0x0a,password)
from users #
(Credit to https://pentestlab.wordpress.com/2012/09/18/sql-injection-exploitation-dvwa/, a series of SQL
injection commands which can be used to discover various things about the database in DVWA.)
You should see something like this. Note you can see usernames, and password hashes for all of the users.
This form is (unsurprisingly) vulnerable to SQL injection attacks. Type this command into the User ID
field. All of the '0' are zeros.
' union select null,concat(first_name,0x0a,user,0x0a,password)
from users #
(Credit to https://pentestlab.wordpress.com/2012/09/18/sql-injection-exploitation-dvwa/, a series of SQL
injection commands which can be used to discover various things about the database in DVWA.)
You should see something like this. Note you can see usernames, and password hashes for all of the users.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
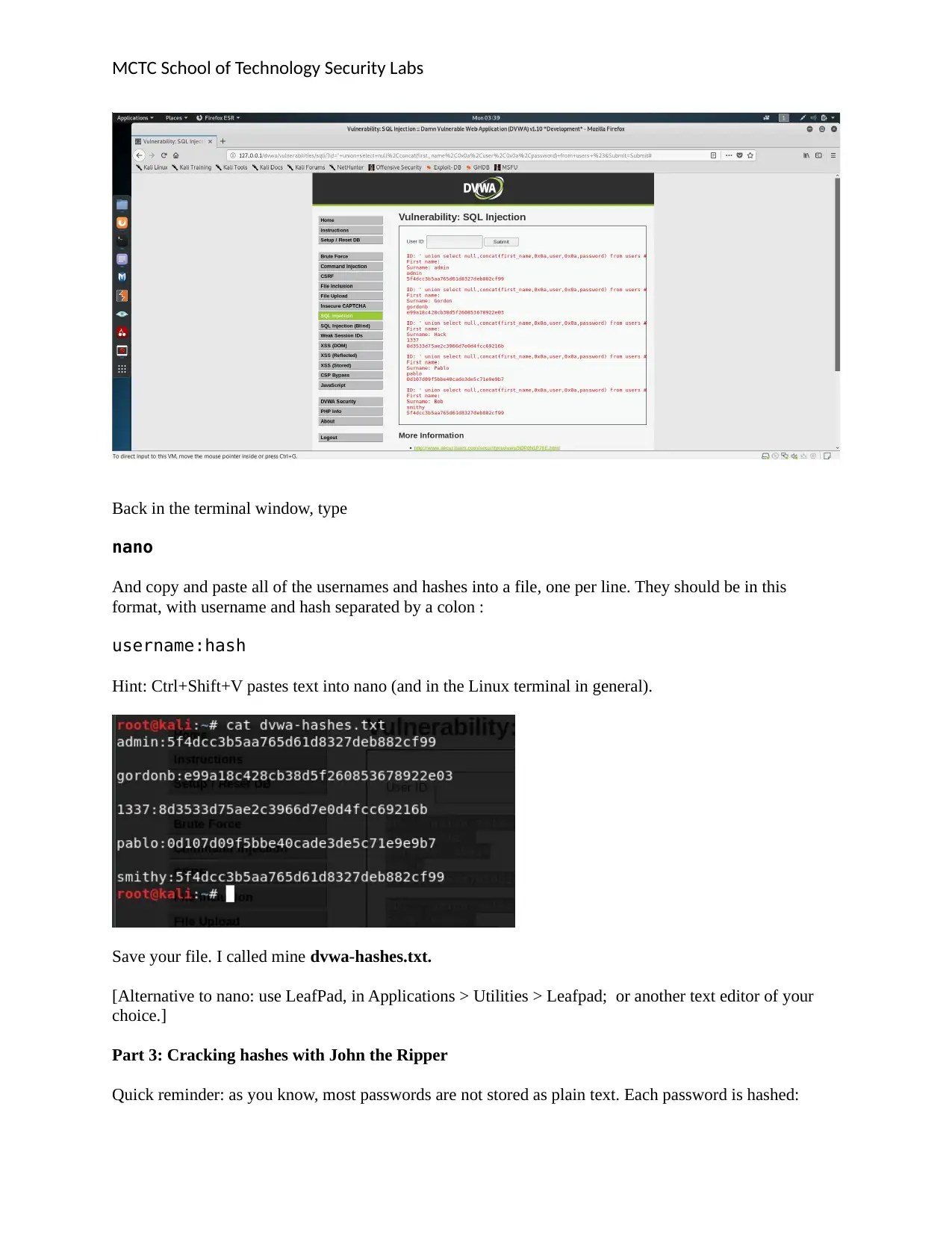
MCTC School of Technology Security Labs
Back in the terminal window, type
nano
And copy and paste all of the usernames and hashes into a file, one per line. They should be in this
format, with username and hash separated by a colon :
username:hash
Hint: Ctrl+Shift+V pastes text into nano (and in the Linux terminal in general).
Save your file. I called mine dvwa-hashes.txt.
[Alternative to nano: use LeafPad, in Applications > Utilities > Leafpad; or another text editor of your
choice.]
Part 3: Cracking hashes with John the Ripper
Quick reminder: as you know, most passwords are not stored as plain text. Each password is hashed:
Back in the terminal window, type
nano
And copy and paste all of the usernames and hashes into a file, one per line. They should be in this
format, with username and hash separated by a colon :
username:hash
Hint: Ctrl+Shift+V pastes text into nano (and in the Linux terminal in general).
Save your file. I called mine dvwa-hashes.txt.
[Alternative to nano: use LeafPad, in Applications > Utilities > Leafpad; or another text editor of your
choice.]
Part 3: Cracking hashes with John the Ripper
Quick reminder: as you know, most passwords are not stored as plain text. Each password is hashed:

MCTC School of Technology Security Labs
turned into a unique hash code by using a well-known formula. Every hash code should be unique, but the
same password will always generate the same hash code. The hashing formula is designed so that you
can't turn a hash back into a password. To log in, a user enters their password. Their password is hashed
with the same formula, and if the hash generated matches the stored hash -> this means that the hashes
were both generated from the same original password, so the user must have entered the correct
password.
It is pretty much impossible to turn a hash back into a password.
But, what happens if a password hash has been stolen? An attacker can start with a list of all possible
passwords. Create a hash of each of these passwords. Compare all of these hashes to the stolen hash.
Once you find a match, look up the password from the list. That's the original password.
John does something like this. It generates passwords, starting with "a", "aa", "ab", "ac"… creates a hash
of the password, and compares it to the stolen hashes; and alerts you when it finds a match.
More info: at http://openwall.com/john.
To have John analyze your stolen password hashes, type
john --format=raw-MD5 dvwa-hashes.txt
This command tells John what formula was used to generate the hashes, raw-MD5.
What passwords did you find?
In DVWA, click on the Brute Force Link on the left. Try logging in with some of the usernames and
passwords.
turned into a unique hash code by using a well-known formula. Every hash code should be unique, but the
same password will always generate the same hash code. The hashing formula is designed so that you
can't turn a hash back into a password. To log in, a user enters their password. Their password is hashed
with the same formula, and if the hash generated matches the stored hash -> this means that the hashes
were both generated from the same original password, so the user must have entered the correct
password.
It is pretty much impossible to turn a hash back into a password.
But, what happens if a password hash has been stolen? An attacker can start with a list of all possible
passwords. Create a hash of each of these passwords. Compare all of these hashes to the stolen hash.
Once you find a match, look up the password from the list. That's the original password.
John does something like this. It generates passwords, starting with "a", "aa", "ab", "ac"… creates a hash
of the password, and compares it to the stolen hashes; and alerts you when it finds a match.
More info: at http://openwall.com/john.
To have John analyze your stolen password hashes, type
john --format=raw-MD5 dvwa-hashes.txt
This command tells John what formula was used to generate the hashes, raw-MD5.
What passwords did you find?
In DVWA, click on the Brute Force Link on the left. Try logging in with some of the usernames and
passwords.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

