Assessment Report: Technology, Security and Personnel for MegaMax Corp
VerifiedAdded on 2020/12/30
|9
|2678
|230
Report
AI Summary
This report provides a comprehensive analysis of MegaMax Corporation's technology adoption, focusing on the challenges and solutions related to security, data storage, and personnel management. It explores the legal and security issues arising from the implementation of new systems, emphasizing the importance of data protection, and compliance with legal regulations. The report recommends the use of Amazon Web Services (AWS) for secure data storage, backup, and consistency, highlighting the features like EC2, S3, EBS, and security groups. It also addresses the personnel requirements, including training and maintenance, to ensure effective utilization of the new technologies. The report concludes by summarizing the key findings and recommendations for MegaMax Corporation to successfully implement and manage its new technology infrastructure.

Assessment
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................3
Technology Used........................................................................................................................3
Legal and security issues related with technology......................................................................4
Suitable storage with backup and security along with consistency and accuracy of data
applications.................................................................................................................................5
Requirements for personnel as well as skills for development, maintenance and their
utilisation.....................................................................................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
Introduction......................................................................................................................................3
Technology Used........................................................................................................................3
Legal and security issues related with technology......................................................................4
Suitable storage with backup and security along with consistency and accuracy of data
applications.................................................................................................................................5
Requirements for personnel as well as skills for development, maintenance and their
utilisation.....................................................................................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9

Introduction
Technology is defined as accumulation of skills, processes, methods and techniques
which are being used for manufacturing of services or goods for achievement of objectives like
scientific investigation (Laudon and Laudon, 2015). Basically, technology can be referred to
devices, systems and methods which have been attained by usage of scientific knowledge and is
used for practical goals. This assessment is based on MegaMax Corporation which sell widgets
to large as well as small organisations and they develop services which can be sold by online
means. This part deals with issues which organisation will face while development of a new
issues. They may be related with security, backup, integrity and consistency. Along with this,
with adoption of new system, it may become difficult for employees to work on that system.
Technology Used
MegaMax is opting to make use of new system and for this they are making use of
various technologies, software and server. They are shown below:
Software: Netbeans IDE
Framework: JavaServer Faces, Java EE
For testing developed project Oracle GlassFish Server 4.1.1 has been used as an enterprise server
and uniform resource locator (URL) to access web application.
Database: JavaDB
Services: Cloud AWS, Amazon's Domain Name System, Virtual Private Cloud (VPC),
Relational database services.
These are the software's and services which are being used MegaMax to implement their
new system.
Legal and security issues related with technology.
Technology refers to knowledge or science of putting things into practical use for
inventing and solving problems associated with tools. When online medium comes in between
there also arises certain limitations though it provides lots of benefits to organisation. MegaMax
is opting for new system so before this they need to acknowledge various security and legal
issues associated with this (Stallings and et. al., 2012). There is a broad reason behind this as if
organisation do not follow the legal laws then they will fall into trouble and same goes with
Technology is defined as accumulation of skills, processes, methods and techniques
which are being used for manufacturing of services or goods for achievement of objectives like
scientific investigation (Laudon and Laudon, 2015). Basically, technology can be referred to
devices, systems and methods which have been attained by usage of scientific knowledge and is
used for practical goals. This assessment is based on MegaMax Corporation which sell widgets
to large as well as small organisations and they develop services which can be sold by online
means. This part deals with issues which organisation will face while development of a new
issues. They may be related with security, backup, integrity and consistency. Along with this,
with adoption of new system, it may become difficult for employees to work on that system.
Technology Used
MegaMax is opting to make use of new system and for this they are making use of
various technologies, software and server. They are shown below:
Software: Netbeans IDE
Framework: JavaServer Faces, Java EE
For testing developed project Oracle GlassFish Server 4.1.1 has been used as an enterprise server
and uniform resource locator (URL) to access web application.
Database: JavaDB
Services: Cloud AWS, Amazon's Domain Name System, Virtual Private Cloud (VPC),
Relational database services.
These are the software's and services which are being used MegaMax to implement their
new system.
Legal and security issues related with technology.
Technology refers to knowledge or science of putting things into practical use for
inventing and solving problems associated with tools. When online medium comes in between
there also arises certain limitations though it provides lots of benefits to organisation. MegaMax
is opting for new system so before this they need to acknowledge various security and legal
issues associated with this (Stallings and et. al., 2012). There is a broad reason behind this as if
organisation do not follow the legal laws then they will fall into trouble and same goes with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

respect to security that if security is breached then it can have adverse impact on overall
organisation.
In context of legal and security aspects, MegaMax needs to make sure that the services
which they are making use do not contain any kind of vulnerabilities and provide enhanced
security. These both risks are interrelated with respect to technology as when security is
breached then organisation will land into legal trouble (Elmaghraby and Losavio, 2014). When
user enters into a site of MegaMax then they are being asked about details like contact number,
bank information and records of transaction along with order & stock information. An example
can be taken into consideration in this aspect like organisation “X” illegally gets access to system
of MegaMax then they can completely get entire information of their clients and can even make
false transactions by name of organisation. When client will come to know about this like their
personal details have been accessed by someone else then they can file a case against MegaMax
as they were not able to secure information of their potential clients.
At present scenario, it has became easy for intruders or hackers to access the information
of anyone by different methods as there exists lots of vulnerabilities in software and they can
break into them by making use of existing loophole. MegaMax need to make sure that the
services which they are using provides enhanced security option in terms of security of their
database, servers and systems. This will assist them to stay away from legal trouble (Hashizume
and et. al., 2013). For this they opted to make use of Amazon Web Services which have been
illustrated below.
Suitable storage with backup and security along with consistency and accuracy of data
applications.
It is essential for an organisation to maintain their information and when services are
being provided online then this implies that there there is need for this so that customers can
have complete access to information associated with specific service (Marchewka, 2014).
MegaMax has opted to make their services available online, therefore it is necessary for them to
have effectual storage and backup space. For this they can use Amazon Web Services (AWS), it
is a subsidiary of Amazon which renders cloud computing platforms on-demand to government,
companies or individuals on the basis of pay-as-you-go. MegaMax can make use of AWS EC2
which is a web service that render secured and resizeable compute capacity as the name implies
Elastic Compute Cloud (Youssef, 2012).
organisation.
In context of legal and security aspects, MegaMax needs to make sure that the services
which they are making use do not contain any kind of vulnerabilities and provide enhanced
security. These both risks are interrelated with respect to technology as when security is
breached then organisation will land into legal trouble (Elmaghraby and Losavio, 2014). When
user enters into a site of MegaMax then they are being asked about details like contact number,
bank information and records of transaction along with order & stock information. An example
can be taken into consideration in this aspect like organisation “X” illegally gets access to system
of MegaMax then they can completely get entire information of their clients and can even make
false transactions by name of organisation. When client will come to know about this like their
personal details have been accessed by someone else then they can file a case against MegaMax
as they were not able to secure information of their potential clients.
At present scenario, it has became easy for intruders or hackers to access the information
of anyone by different methods as there exists lots of vulnerabilities in software and they can
break into them by making use of existing loophole. MegaMax need to make sure that the
services which they are using provides enhanced security option in terms of security of their
database, servers and systems. This will assist them to stay away from legal trouble (Hashizume
and et. al., 2013). For this they opted to make use of Amazon Web Services which have been
illustrated below.
Suitable storage with backup and security along with consistency and accuracy of data
applications.
It is essential for an organisation to maintain their information and when services are
being provided online then this implies that there there is need for this so that customers can
have complete access to information associated with specific service (Marchewka, 2014).
MegaMax has opted to make their services available online, therefore it is necessary for them to
have effectual storage and backup space. For this they can use Amazon Web Services (AWS), it
is a subsidiary of Amazon which renders cloud computing platforms on-demand to government,
companies or individuals on the basis of pay-as-you-go. MegaMax can make use of AWS EC2
which is a web service that render secured and resizeable compute capacity as the name implies
Elastic Compute Cloud (Youssef, 2012).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
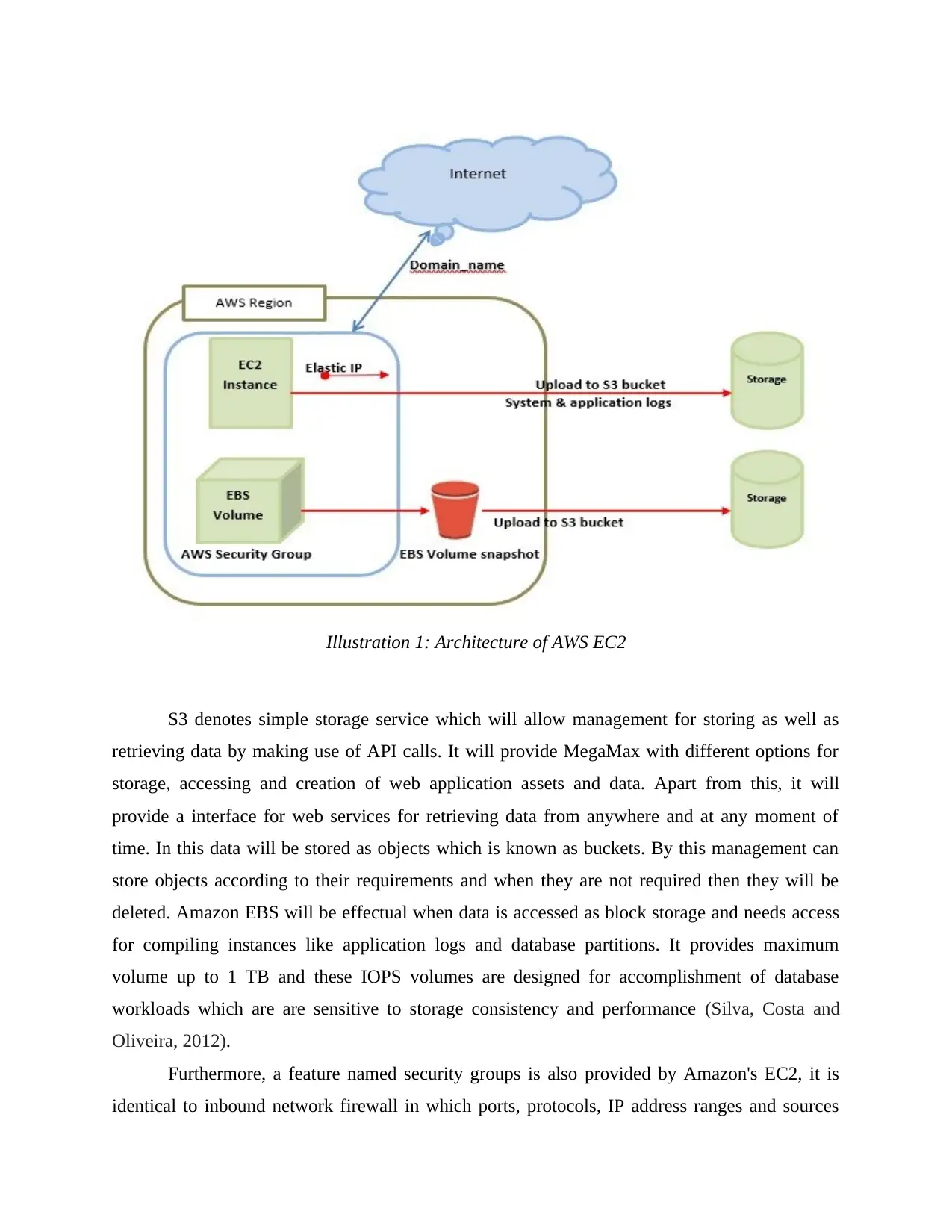
S3 denotes simple storage service which will allow management for storing as well as
retrieving data by making use of API calls. It will provide MegaMax with different options for
storage, accessing and creation of web application assets and data. Apart from this, it will
provide a interface for web services for retrieving data from anywhere and at any moment of
time. In this data will be stored as objects which is known as buckets. By this management can
store objects according to their requirements and when they are not required then they will be
deleted. Amazon EBS will be effectual when data is accessed as block storage and needs access
for compiling instances like application logs and database partitions. It provides maximum
volume up to 1 TB and these IOPS volumes are designed for accomplishment of database
workloads which are are sensitive to storage consistency and performance (Silva, Costa and
Oliveira, 2012).
Furthermore, a feature named security groups is also provided by Amazon's EC2, it is
identical to inbound network firewall in which ports, protocols, IP address ranges and sources
Illustration 1: Architecture of AWS EC2
retrieving data by making use of API calls. It will provide MegaMax with different options for
storage, accessing and creation of web application assets and data. Apart from this, it will
provide a interface for web services for retrieving data from anywhere and at any moment of
time. In this data will be stored as objects which is known as buckets. By this management can
store objects according to their requirements and when they are not required then they will be
deleted. Amazon EBS will be effectual when data is accessed as block storage and needs access
for compiling instances like application logs and database partitions. It provides maximum
volume up to 1 TB and these IOPS volumes are designed for accomplishment of database
workloads which are are sensitive to storage consistency and performance (Silva, Costa and
Oliveira, 2012).
Furthermore, a feature named security groups is also provided by Amazon's EC2, it is
identical to inbound network firewall in which ports, protocols, IP address ranges and sources
Illustration 1: Architecture of AWS EC2

can be specified so that they can reach to specific EC2 instances. With respect to this, each EC2
instance can be applied various groups as per the number of users visiting the website so that
traffic routes appropriately to each instance (Amazon Web Services, 2019). IT department of
MegaMax can configure security groups by making use of IP addresses or subnets which will
bound access to EC2 instances. Apart from this, AWS IAM (Identity and Access Management)
allow admins for defining and managing access to resources. Amazon Inspector analyses an
AWS environment with respect to vulnerabilities which creates an impact on compliance and
security. For this Amazon provide an option of Amazon Macie which can be utilised by
MegaMax to secure sensitive data on cloud. Apart from this, Amazon also provides hardware as
well as software encryption to secure against attacks like DDoS (Distributed denial of service)
attacks, transport layer security and provisions for secure sockets layer along with filtering of
harmful traffic to web applications (Arora, Wadhawan and Ahuja, 2012).
Feature of ACID is provided by AWS when Relational database is used by organisation.
It is a accumulation of data items and relationship shared among them. Information related with
objects is stored within tables which are illustrated within database. Data transactions needs to be
atomic, consistent, isolated and durable, this will make sure integrity of data. In atomicity,
operations of either all the units are executed or none. Consistency within database implies that
a consistent state is attained when transactions are done. Like if before execution data was
consistent and it will remain same after execution also. Durability denotes that database is
durable enough for holding latest updates if system restarts or fails. When multiple transactions
are carried out in parallel and simultaneously then property of isolation takes as a single
transaction & creates no impact on any of them. This will help them MegaMax to secure their
information within cloud along with high security and options for backup. Furthermore, there
will be consistency and accuracy in data as well as application, as they can be accessed from
anywhere and can be opted for when they are needed (Kalin, 2013).
Requirements for personnel as well as skills for development, maintenance and their utilisation.
As MegaMax is looking forward to make investment in new technologies and systems, it
is ensure that they will have to face issues related with this. The reason behind this can be as
employees both management and other staff may not have the working knowledge of latest
software along with this they have been adapted to present working scenario (Noe and et. al.,
2017). It is essential for management of organisation to make each employee aware of the new
instance can be applied various groups as per the number of users visiting the website so that
traffic routes appropriately to each instance (Amazon Web Services, 2019). IT department of
MegaMax can configure security groups by making use of IP addresses or subnets which will
bound access to EC2 instances. Apart from this, AWS IAM (Identity and Access Management)
allow admins for defining and managing access to resources. Amazon Inspector analyses an
AWS environment with respect to vulnerabilities which creates an impact on compliance and
security. For this Amazon provide an option of Amazon Macie which can be utilised by
MegaMax to secure sensitive data on cloud. Apart from this, Amazon also provides hardware as
well as software encryption to secure against attacks like DDoS (Distributed denial of service)
attacks, transport layer security and provisions for secure sockets layer along with filtering of
harmful traffic to web applications (Arora, Wadhawan and Ahuja, 2012).
Feature of ACID is provided by AWS when Relational database is used by organisation.
It is a accumulation of data items and relationship shared among them. Information related with
objects is stored within tables which are illustrated within database. Data transactions needs to be
atomic, consistent, isolated and durable, this will make sure integrity of data. In atomicity,
operations of either all the units are executed or none. Consistency within database implies that
a consistent state is attained when transactions are done. Like if before execution data was
consistent and it will remain same after execution also. Durability denotes that database is
durable enough for holding latest updates if system restarts or fails. When multiple transactions
are carried out in parallel and simultaneously then property of isolation takes as a single
transaction & creates no impact on any of them. This will help them MegaMax to secure their
information within cloud along with high security and options for backup. Furthermore, there
will be consistency and accuracy in data as well as application, as they can be accessed from
anywhere and can be opted for when they are needed (Kalin, 2013).
Requirements for personnel as well as skills for development, maintenance and their utilisation.
As MegaMax is looking forward to make investment in new technologies and systems, it
is ensure that they will have to face issues related with this. The reason behind this can be as
employees both management and other staff may not have the working knowledge of latest
software along with this they have been adapted to present working scenario (Noe and et. al.,
2017). It is essential for management of organisation to make each employee aware of the new
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

tools as well as techniques which are implemented by MegaMax so that at least they can
acknowledge what all changes have been made and what they are with respect to name of
hardware & software as they have to work on them. It is crucial for management to make sure
that there employees can work in required manner and there performance do not get hampered
by these new system.
It is crucial for management of organisation to ensure that they provide appropriate
training sessions to their employees so that they can have working hands on latest systems
implemented by organisation (Littlejohn, Beetham and McGill, 2012). This will assist them to
get a knowledge about software in which they have to work and how it can be done. This session
must not be for a day as when things are carried out just for sake for acknowledging technology
then it will just a overview and might be they gain knowledge about the same but it will be
difficult for them to practically implement everything which they have been taught even if they
have got notes related with same. With respect to this management can either opt for giving them
hands on session or two day training. After 2 day period they can continue their work and in case
if they face any kind of problem then they can have another 1 day session to address queries of
employees. This help employees to work efficiently on the systems which are being used by
MegaMax.
Management can observe relevant change in performance of employees as they have
learnt about new system but still it will take time for them to adapt to these systems. Overall
impact of new system will be fluctuating but this will help employees to gain knowledge about
new trends and technologies within environment along with this they will be working on it.
Apart from this, other major issue which is faced by employees of MegaMax is maintenance of
this system (Schwalbe, 2015). It includes support services, network software and hardware
fixing. With respect to support & hardware there exists remedial and preventive services which
can optimize hardware which involves per-incident repair and contract maintenance. Along with
this, it comprises of telephone and online technical assistance and troubleshooting for setup as
well as fee based warranty upgrades of hardware. In context of software maintenance & support
services, MegaMax can opt for incident- based (pay-as-you-go) and long term support contracts.
Software support contracts comprises of support and remote troubleshooting through online
channels and telephone along with primary usability and installation assistance. Software support
services will aid MegaMax in new installation services, product updates, migrations and other
acknowledge what all changes have been made and what they are with respect to name of
hardware & software as they have to work on them. It is crucial for management to make sure
that there employees can work in required manner and there performance do not get hampered
by these new system.
It is crucial for management of organisation to ensure that they provide appropriate
training sessions to their employees so that they can have working hands on latest systems
implemented by organisation (Littlejohn, Beetham and McGill, 2012). This will assist them to
get a knowledge about software in which they have to work and how it can be done. This session
must not be for a day as when things are carried out just for sake for acknowledging technology
then it will just a overview and might be they gain knowledge about the same but it will be
difficult for them to practically implement everything which they have been taught even if they
have got notes related with same. With respect to this management can either opt for giving them
hands on session or two day training. After 2 day period they can continue their work and in case
if they face any kind of problem then they can have another 1 day session to address queries of
employees. This help employees to work efficiently on the systems which are being used by
MegaMax.
Management can observe relevant change in performance of employees as they have
learnt about new system but still it will take time for them to adapt to these systems. Overall
impact of new system will be fluctuating but this will help employees to gain knowledge about
new trends and technologies within environment along with this they will be working on it.
Apart from this, other major issue which is faced by employees of MegaMax is maintenance of
this system (Schwalbe, 2015). It includes support services, network software and hardware
fixing. With respect to support & hardware there exists remedial and preventive services which
can optimize hardware which involves per-incident repair and contract maintenance. Along with
this, it comprises of telephone and online technical assistance and troubleshooting for setup as
well as fee based warranty upgrades of hardware. In context of software maintenance & support
services, MegaMax can opt for incident- based (pay-as-you-go) and long term support contracts.
Software support contracts comprises of support and remote troubleshooting through online
channels and telephone along with primary usability and installation assistance. Software support
services will aid MegaMax in new installation services, product updates, migrations and other
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

software which can assist organisation to enhance their productivity along with other reactive or
proactive on-site services (Stallings and et. al., 2012).
Management of MegaMax can utilise the services which are being provided by support
services and try to acquire lots of information from the same so that in future they do not face
any minor issues with this.
Conclusion
From above report, it can be concluded that technology can be defined as a system which
aids humans to make there work more smoother, easier and faster. An organisation when opts
latest technologies then they have to face several issues, few of them were analysed here. And it
has been observed though at initial stage after implementation of technology organisation may
have some hindrances in their processes but by taking into consideration long aspects, they will
render high benefits. This will also assist them to remain up to date in terms of current
technology as well as have optimised use of resources. Security is hardly breached but it also
depends upon services which are being opted by organisation.
proactive on-site services (Stallings and et. al., 2012).
Management of MegaMax can utilise the services which are being provided by support
services and try to acquire lots of information from the same so that in future they do not face
any minor issues with this.
Conclusion
From above report, it can be concluded that technology can be defined as a system which
aids humans to make there work more smoother, easier and faster. An organisation when opts
latest technologies then they have to face several issues, few of them were analysed here. And it
has been observed though at initial stage after implementation of technology organisation may
have some hindrances in their processes but by taking into consideration long aspects, they will
render high benefits. This will also assist them to remain up to date in terms of current
technology as well as have optimised use of resources. Security is hardly breached but it also
depends upon services which are being opted by organisation.

References
Books & Journals
Arora, P., Wadhawan, R. C. and Ahuja, E. S. P., 2012. Cloud computing security issues in
infrastructure as a service. International journal of advanced research in computer
science and software engineering. 2(1).
Elmaghraby, A. S. and Losavio, M. M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research. 5(4). pp.491-497.
Hashizume, K. and et. al., 2013. An analysis of security issues for cloud computing. Journal of
internet services and applications. 4(1). p.5.
Kalin, M., 2013. Java Web Services: Up and Running: A Quick, Practical, and Thorough
Introduction. " O'Reilly Media, Inc.".
Laudon, K. C. and Laudon, J. P., 2015. Management Information Systems: Managing the Digital
Firm Plus MyMISLab with Pearson eText--Access Card Package. Prentice Hall Press.
Littlejohn, A., Beetham, H. and McGill, L., 2012. Learning at the digital frontier: a review of
digital literacies in theory and practice. Journal of computer assisted learning. 28(6).
pp.547-556.
Marchewka, J. T., 2014. Information technology project management. John Wiley & Sons.
Noe, R. A. and et. al., 2017. Human resource management: Gaining a competitive advantage.
New York, NY: McGraw-Hill Education.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Silva, L. A. B., Costa, C. and Oliveira, J. L., 2012. A PACS archive architecture supported on
cloud services. International journal of computer assisted radiology and surgery. 7(3).
pp.349-358.
Stallings, W. and et. al., 2012. Computer security: principles and practice (pp. 978-0). Upper
Saddle River (NJ: Pearson Education.
Youssef, A. E., 2012. Exploring cloud computing services and applications. Journal of Emerging
Trends in Computing and Information Sciences. 3(6). pp.838-847.
Online
Amazon Web Services. 2019. [Online]. Available through:
<https://searchaws.techtarget.com/definition/Amazon-Web-Services>
Books & Journals
Arora, P., Wadhawan, R. C. and Ahuja, E. S. P., 2012. Cloud computing security issues in
infrastructure as a service. International journal of advanced research in computer
science and software engineering. 2(1).
Elmaghraby, A. S. and Losavio, M. M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research. 5(4). pp.491-497.
Hashizume, K. and et. al., 2013. An analysis of security issues for cloud computing. Journal of
internet services and applications. 4(1). p.5.
Kalin, M., 2013. Java Web Services: Up and Running: A Quick, Practical, and Thorough
Introduction. " O'Reilly Media, Inc.".
Laudon, K. C. and Laudon, J. P., 2015. Management Information Systems: Managing the Digital
Firm Plus MyMISLab with Pearson eText--Access Card Package. Prentice Hall Press.
Littlejohn, A., Beetham, H. and McGill, L., 2012. Learning at the digital frontier: a review of
digital literacies in theory and practice. Journal of computer assisted learning. 28(6).
pp.547-556.
Marchewka, J. T., 2014. Information technology project management. John Wiley & Sons.
Noe, R. A. and et. al., 2017. Human resource management: Gaining a competitive advantage.
New York, NY: McGraw-Hill Education.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Silva, L. A. B., Costa, C. and Oliveira, J. L., 2012. A PACS archive architecture supported on
cloud services. International journal of computer assisted radiology and surgery. 7(3).
pp.349-358.
Stallings, W. and et. al., 2012. Computer security: principles and practice (pp. 978-0). Upper
Saddle River (NJ: Pearson Education.
Youssef, A. E., 2012. Exploring cloud computing services and applications. Journal of Emerging
Trends in Computing and Information Sciences. 3(6). pp.838-847.
Online
Amazon Web Services. 2019. [Online]. Available through:
<https://searchaws.techtarget.com/definition/Amazon-Web-Services>
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





