INF30020 - Risk Management Case Study: City of Melbourne Analysis
VerifiedAdded on 2022/09/28
|15
|3462
|29
Case Study
AI Summary
This case study examines the risk management practices of the City of Melbourne (CoM), highlighting various IT and operational risks. The analysis covers the use of mobile devices, social media, and cloud computing, and the challenges associated with these technologies. The study identifies vulnerabilities related to data security, payment gateways, and the legacy CoM-ONE system. It emphasizes the importance of transparency, accountability, and the need for a robust risk management framework. The case study proposes a framework including integration, design, implementation, evaluation, and improvement phases. It defines roles and responsibilities for risk management, including risk assessment, policy articulation, internal process examination, and framework development. The document concludes by discussing the potential for credit card fraud and the importance of ensuring the credibility of the organization in managing funds. It also suggests an audit of the case evidence to identify areas for improvement and mitigation strategies.

Running head: CoM CASE STUDY
CoM CASE STUDY
Name of the Student
Name of the Organization
Author Note
CoM CASE STUDY
Name of the Student
Name of the Organization
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CoM CASE STUDY
Proposal for Target Risk Appetite
The CoM or the City of Melbourne has been observed to be greatly exploring the way
digital technology can be helping a lot for keeping the city great for working, playing as well
as in the specific century of 21st. The employees of CoM have been provided normally with a
huge autonomy for making various decisions which will be involving the operational as well
as the tactical ones for quickly ascertaining if there is a need for complying or rather lodging
any kind of exception to all the various agencies of government which will be relevant of the
host country. The officers of CoM have been observed to be greatly operating in a number of
various countries and are being equipped normally with a full set of various devices of
mobile communication. This actually involves a very short range of devices of
communication which they will be distributing to some of the workings of local staffs on
certain kinds of projects, a phone, a satellite phone and even a laptop as well. All the various
staffs are greatly responsible for reporting to the specific local office in a periodic basis for
providing all sorts of updates on the specific CDA, various communities, themselves as well
as upon the entire team. Staffs are even allowed to bring all of their various devices of their
own for the main areas of operation for various reasons like they have very long gone in the
memory which is corporate. This may be bringing a number of risks to the CoM. Staffs even
bring in their own phones as well as laptops with the main reason being familiarity to that of
the specific device. CoM has been recognising the importance of offering higher transparency
as well as accountability of its utilisation of various resources which have been offered by
various donors. For expanding the market which is actually targeted towards all the various
potential donors, CoM has been really very much active in a number of various activities of
marketing. By specifically recognising the strength of social media, it has been observed that
CoM has been aggressively pursuing a specific strategy of marketing on the internet. There
are a number of various appeals which have been greatly launched via the specific website. It
CoM CASE STUDY
Proposal for Target Risk Appetite
The CoM or the City of Melbourne has been observed to be greatly exploring the way
digital technology can be helping a lot for keeping the city great for working, playing as well
as in the specific century of 21st. The employees of CoM have been provided normally with a
huge autonomy for making various decisions which will be involving the operational as well
as the tactical ones for quickly ascertaining if there is a need for complying or rather lodging
any kind of exception to all the various agencies of government which will be relevant of the
host country. The officers of CoM have been observed to be greatly operating in a number of
various countries and are being equipped normally with a full set of various devices of
mobile communication. This actually involves a very short range of devices of
communication which they will be distributing to some of the workings of local staffs on
certain kinds of projects, a phone, a satellite phone and even a laptop as well. All the various
staffs are greatly responsible for reporting to the specific local office in a periodic basis for
providing all sorts of updates on the specific CDA, various communities, themselves as well
as upon the entire team. Staffs are even allowed to bring all of their various devices of their
own for the main areas of operation for various reasons like they have very long gone in the
memory which is corporate. This may be bringing a number of risks to the CoM. Staffs even
bring in their own phones as well as laptops with the main reason being familiarity to that of
the specific device. CoM has been recognising the importance of offering higher transparency
as well as accountability of its utilisation of various resources which have been offered by
various donors. For expanding the market which is actually targeted towards all the various
potential donors, CoM has been really very much active in a number of various activities of
marketing. By specifically recognising the strength of social media, it has been observed that
CoM has been aggressively pursuing a specific strategy of marketing on the internet. There
are a number of various appeals which have been greatly launched via the specific website. It

2
CoM CASE STUDY
is to be remembered that there may be number of risks which may be associated with the
social media implementation of CoM and a number of things are to be kept in mind.
There has been a well-concentrated effort as well for properly targeting all the various
users of sites of social networking. It can be well sufficed that the specific profile of CoM
within the social media has literally incremented in a dramatic way in the last 2 years. It has
been observed that there is a great need for the proper management of the gateways of
payment and the data of the customers which they basically capture via the site of CoM.
Again, it has been noticed that CoM has been running a kind of corporate system which has
been named CoM-ONE. It is basically a system which has been custom made-designed in the
year of 1990. Even though it is a system which is robust, it has been very much tough to
maintain in the last few years. There have been a number of various patches as well as
extensions of CoM-ONE. Such kinds of extensions have not at all been integrated with the
CoM-ONE but possess the capability of feeding as well as drawing information from the
actual database of that of CoM-ONE. For this development of extensions, it has been noticed
that CoM has greatly worked with a number of vendors of software who have offered service
free of cost. Most of these vendors have been actually all start-ups and their main reason
behind offering free service have been the purpose of building credibility. Meanwhile, the
HR team of CoM have taken a decision for not at all waiting for the appropriate functionality
to be offered as a part of CoM-ONE. There is a great need for solving the issue of the CoM-
ONE. They have been actually considered serious for going to the cloud. The manager of HR
has been observed to have attended a specific presentation on SaaS in the area of HR and has
been greatly impressed at all the various advantages which can be gained by utilising the
specific platform of HR which will be based upon cloud. The manager of HR has the main
aim upon especially funding from that of CFO and then utilise that fund for purchasing the
CoM CASE STUDY
is to be remembered that there may be number of risks which may be associated with the
social media implementation of CoM and a number of things are to be kept in mind.
There has been a well-concentrated effort as well for properly targeting all the various
users of sites of social networking. It can be well sufficed that the specific profile of CoM
within the social media has literally incremented in a dramatic way in the last 2 years. It has
been observed that there is a great need for the proper management of the gateways of
payment and the data of the customers which they basically capture via the site of CoM.
Again, it has been noticed that CoM has been running a kind of corporate system which has
been named CoM-ONE. It is basically a system which has been custom made-designed in the
year of 1990. Even though it is a system which is robust, it has been very much tough to
maintain in the last few years. There have been a number of various patches as well as
extensions of CoM-ONE. Such kinds of extensions have not at all been integrated with the
CoM-ONE but possess the capability of feeding as well as drawing information from the
actual database of that of CoM-ONE. For this development of extensions, it has been noticed
that CoM has greatly worked with a number of vendors of software who have offered service
free of cost. Most of these vendors have been actually all start-ups and their main reason
behind offering free service have been the purpose of building credibility. Meanwhile, the
HR team of CoM have taken a decision for not at all waiting for the appropriate functionality
to be offered as a part of CoM-ONE. There is a great need for solving the issue of the CoM-
ONE. They have been actually considered serious for going to the cloud. The manager of HR
has been observed to have attended a specific presentation on SaaS in the area of HR and has
been greatly impressed at all the various advantages which can be gained by utilising the
specific platform of HR which will be based upon cloud. The manager of HR has the main
aim upon especially funding from that of CFO and then utilise that fund for purchasing the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
CoM CASE STUDY
specific service of that of SaaS HRM systems provider. It must be well remembered that
there are a number of risks which may be associated with the deployment of cloud in CoM.
It has been very much essential for developing a risk assessment as a number of risks
have been observed in a number of areas of the CoM which can be well understood by some
of the activities which have been mentioned above.
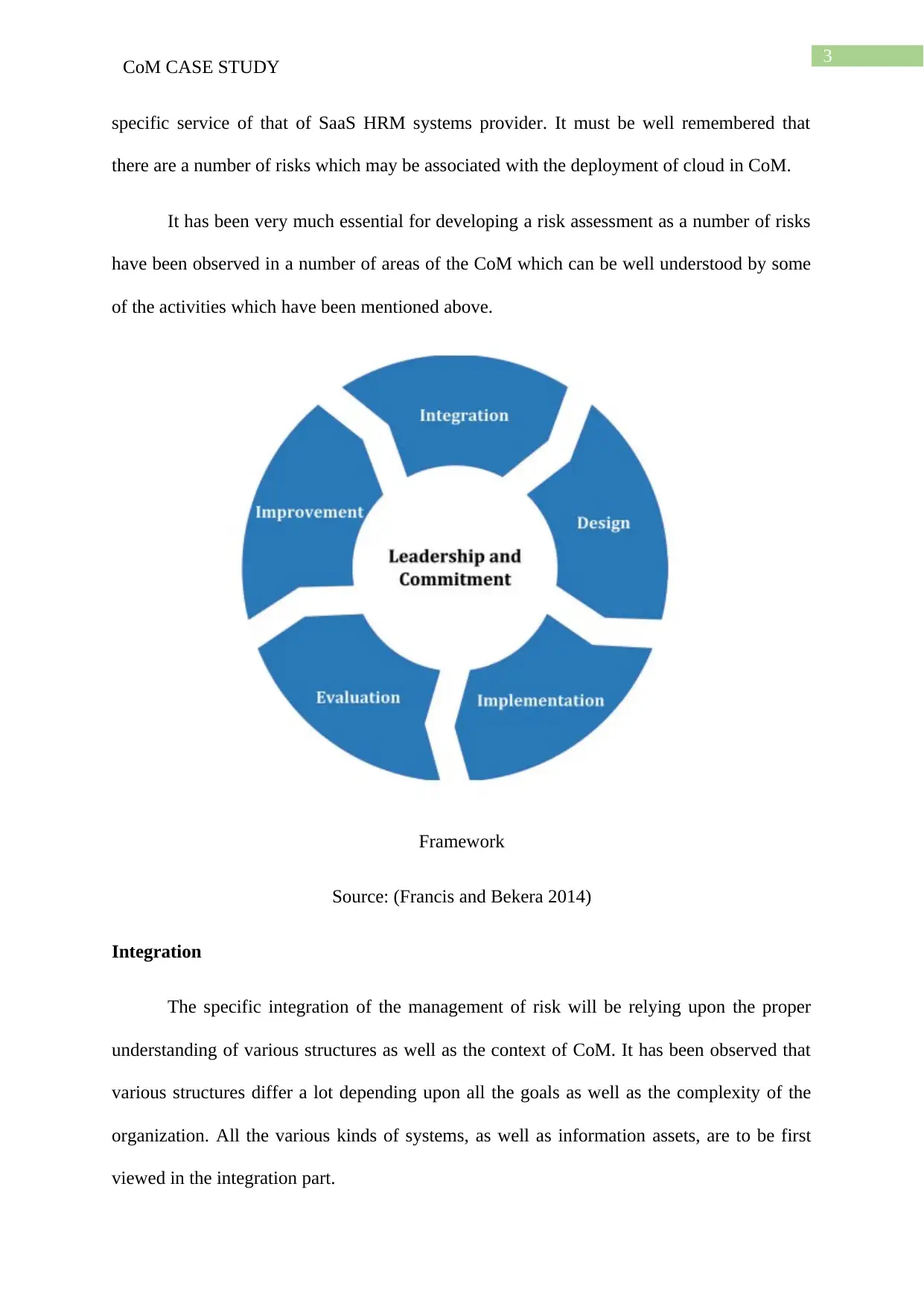
Framework
Source: (Francis and Bekera 2014)
Integration
The specific integration of the management of risk will be relying upon the proper
understanding of various structures as well as the context of CoM. It has been observed that
various structures differ a lot depending upon all the goals as well as the complexity of the
organization. All the various kinds of systems, as well as information assets, are to be first
viewed in the integration part.
CoM CASE STUDY
specific service of that of SaaS HRM systems provider. It must be well remembered that
there are a number of risks which may be associated with the deployment of cloud in CoM.
It has been very much essential for developing a risk assessment as a number of risks
have been observed in a number of areas of the CoM which can be well understood by some
of the activities which have been mentioned above.
Framework
Source: (Francis and Bekera 2014)
Integration
The specific integration of the management of risk will be relying upon the proper
understanding of various structures as well as the context of CoM. It has been observed that
various structures differ a lot depending upon all the goals as well as the complexity of the
organization. All the various kinds of systems, as well as information assets, are to be first
viewed in the integration part.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CoM CASE STUDY
Design
In the designing part, there must be a proper understanding of CoM, articulation of the
commitment of the management of risk, assigning of all the various roles as well as the
responsibilities, allocation of various kinds of resources and lastly the establishment of clear
communication.
Implementation
CoM must then properly implement the specific kind of framework in the
management of risk by the development of a proper plan involving all the various resources
as well as time. A successful framework implementation will be needing proper engagement
of various stakeholders of the organization.
Evaluation
For the purpose of evaluating the framework of risk management, CoM must be
periodically measuring the specific performance of the management of risk against all the
various plans as well as the purpose. It must also be determining if it particular remains
perfect for supporting the achievement of various organizational objectives.
Improvement
Lastly, CoM must continually improve the specific effectiveness of the framework of
the management of risk and also the particular way the procedure of risk management will be
actually integrated. The organization must be developing various tasks as well as plans and
properly assign to all of those which will be particularly accountable for the specific kinds of
implementation. Once the implementation will be done, all of the various improvements must
be definitely contributing towards the huge enhancement of the management of risks.
CoM CASE STUDY
Design
In the designing part, there must be a proper understanding of CoM, articulation of the
commitment of the management of risk, assigning of all the various roles as well as the
responsibilities, allocation of various kinds of resources and lastly the establishment of clear
communication.
Implementation
CoM must then properly implement the specific kind of framework in the
management of risk by the development of a proper plan involving all the various resources
as well as time. A successful framework implementation will be needing proper engagement
of various stakeholders of the organization.
Evaluation
For the purpose of evaluating the framework of risk management, CoM must be
periodically measuring the specific performance of the management of risk against all the
various plans as well as the purpose. It must also be determining if it particular remains
perfect for supporting the achievement of various organizational objectives.
Improvement
Lastly, CoM must continually improve the specific effectiveness of the framework of
the management of risk and also the particular way the procedure of risk management will be
actually integrated. The organization must be developing various tasks as well as plans and
properly assign to all of those which will be particularly accountable for the specific kinds of
implementation. Once the implementation will be done, all of the various improvements must
be definitely contributing towards the huge enhancement of the management of risks.

5
CoM CASE STUDY
Roles and Responsibilities
Roles:
1. To assess the particular risk profile of the CoM and the main areas of various risks in
particular.
2. To specifically articulate the policy of the CoM for the appropriate management of
various risks of different operations of CoM.
3. To properly examine as well as determine the great sufficiency of all the various internal
processes of the CoM for the management of various areas of risk.
4. To develop a proper framework for the management of risk.
5. To undertake special kinds of investigations into various areas of risk which will be
corporate and also a number of break downs within the internal controlling.
6. To properly report all the various trends upon the risk profile of the CoM and then report
on those kinds of specific risks and also the specific status of the procedure of risk
management.
Responsibilities:
Definition of the specific appetite of CoM.
Properly exercising the specific oversight of the various responsibilities of the
management and specifically review CoM for ensuring that risk is not at all much
higher than the specific appetite of risk which is actually determined.
Ensuring CoM is taking all the proper measures which are needed for achieving the
specific balance between the risk and the specific reward in all the various activities
of CoM.
CoM CASE STUDY
Roles and Responsibilities
Roles:
1. To assess the particular risk profile of the CoM and the main areas of various risks in
particular.
2. To specifically articulate the policy of the CoM for the appropriate management of
various risks of different operations of CoM.
3. To properly examine as well as determine the great sufficiency of all the various internal
processes of the CoM for the management of various areas of risk.
4. To develop a proper framework for the management of risk.
5. To undertake special kinds of investigations into various areas of risk which will be
corporate and also a number of break downs within the internal controlling.
6. To properly report all the various trends upon the risk profile of the CoM and then report
on those kinds of specific risks and also the specific status of the procedure of risk
management.
Responsibilities:
Definition of the specific appetite of CoM.
Properly exercising the specific oversight of the various responsibilities of the
management and specifically review CoM for ensuring that risk is not at all much
higher than the specific appetite of risk which is actually determined.
Ensuring CoM is taking all the proper measures which are needed for achieving the
specific balance between the risk and the specific reward in all the various activities
of CoM.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CoM CASE STUDY
Reviewing as well as assessing the integrity as well as the effectiveness of the systems
of the management of risk and ensuring that the policies of risks are managed in an
effective manner.
Ensuring that CoM has greatly implemented an effective procedure for the
identification of risks for measuring the huge impact against all the various sets of
assumptions.
Overseeing all the various reviews of the activities which will be greatly associated
with the specific effects of the management of risk.
Proper monitoring of all the developments which will be directly related to the
reporting all the various risks which will be associated.
Proper reviewing of all the various processes for particularly ensuring the great
effectiveness of various internal control systems such that the ability of decision
making can be well maintained at a level which is optimal.
Ensuring that there is a culture of risk awareness through the entire CoM.
Auditing the case evidence
There are a number of evidence within the case study which shows a number of paths
for the entry of various kinds of risks. Firstly, the officers of CoM have been greatly
operating in a number of countries and are greatly equipped with a collection of various
mobile devices for communication. Not only smartphones, but they are also even provided
with laptops as well. But it has been seen that the officers are bringing in their own mobile
devices as well as laptops for various areas of operation. They are providing with a number of
reasons and most of them are bringing in “familiarity to the device” as the actual reason. The
main thing which is really shocking is that the programme coordinator of CoM has been
allowing it. In a number of cases where various staffs are allowed to bring it their respective
devices may be bringing in a number of various issues related to the operation. It may even
CoM CASE STUDY
Reviewing as well as assessing the integrity as well as the effectiveness of the systems
of the management of risk and ensuring that the policies of risks are managed in an
effective manner.
Ensuring that CoM has greatly implemented an effective procedure for the
identification of risks for measuring the huge impact against all the various sets of
assumptions.
Overseeing all the various reviews of the activities which will be greatly associated
with the specific effects of the management of risk.
Proper monitoring of all the developments which will be directly related to the
reporting all the various risks which will be associated.
Proper reviewing of all the various processes for particularly ensuring the great
effectiveness of various internal control systems such that the ability of decision
making can be well maintained at a level which is optimal.
Ensuring that there is a culture of risk awareness through the entire CoM.
Auditing the case evidence
There are a number of evidence within the case study which shows a number of paths
for the entry of various kinds of risks. Firstly, the officers of CoM have been greatly
operating in a number of countries and are greatly equipped with a collection of various
mobile devices for communication. Not only smartphones, but they are also even provided
with laptops as well. But it has been seen that the officers are bringing in their own mobile
devices as well as laptops for various areas of operation. They are providing with a number of
reasons and most of them are bringing in “familiarity to the device” as the actual reason. The
main thing which is really shocking is that the programme coordinator of CoM has been
allowing it. In a number of cases where various staffs are allowed to bring it their respective
devices may be bringing in a number of various issues related to the operation. It may even
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CoM CASE STUDY
happen that there may be a direct introduction of various kinds of codes which will be hugely
malicious for the system and this may be hugely affecting all the various regional or local
operations. It may be happening that the code which is problematic can be actually brought
up by all the privately-owned devices which have been brought by all the staffs.
It is very much important to clearly understand the specific kind of competitive
environment around the specific environment of charity. It is very much important to
understand the specific competition for specifically funding the organizations of charity. Both
the accountability as well as the transparency of several funds are very much high upon all
the potential list of various donors. CoM must be well recognizing the great importance of
offering much higher transparency of the utilization of various resources which will be
offered by the donors. CoM must be possessing the ability to especially assure all the various
donors about credibility of the organization in the management of funds.
CoM has been observed to be utilising the strength of social media and a number of
various appeals have already been launched by its specific website. It has been observed to be
receiving a huge amount of donations from that of the public via a number of means. In most
of the cases, it has been noticed that the donors donate a huge amount of money via the credit
cards. With the specific initiative which is based upon the web, CoM has the capability of
allowing all the various transactions which will be based upon web. Here, it can be said there
may be a huge chance of inviting a number of credit card frauds which can possess a huge
impact upon the transaction which will be done.
On the other hand, it has been observed that CoM has been running a corporate
system named CoM-ONE. In the development of the extensions of CoM-ONE, CoM has
been observed to have been working with a number of start-up companies for free. It is to be
well pointed as Board will be unaware of any kinds of IT issue related to CoM-ONE, there is
CoM CASE STUDY
happen that there may be a direct introduction of various kinds of codes which will be hugely
malicious for the system and this may be hugely affecting all the various regional or local
operations. It may be happening that the code which is problematic can be actually brought
up by all the privately-owned devices which have been brought by all the staffs.
It is very much important to clearly understand the specific kind of competitive
environment around the specific environment of charity. It is very much important to
understand the specific competition for specifically funding the organizations of charity. Both
the accountability as well as the transparency of several funds are very much high upon all
the potential list of various donors. CoM must be well recognizing the great importance of
offering much higher transparency of the utilization of various resources which will be
offered by the donors. CoM must be possessing the ability to especially assure all the various
donors about credibility of the organization in the management of funds.
CoM has been observed to be utilising the strength of social media and a number of
various appeals have already been launched by its specific website. It has been observed to be
receiving a huge amount of donations from that of the public via a number of means. In most
of the cases, it has been noticed that the donors donate a huge amount of money via the credit
cards. With the specific initiative which is based upon the web, CoM has the capability of
allowing all the various transactions which will be based upon web. Here, it can be said there
may be a huge chance of inviting a number of credit card frauds which can possess a huge
impact upon the transaction which will be done.
On the other hand, it has been observed that CoM has been running a corporate
system named CoM-ONE. In the development of the extensions of CoM-ONE, CoM has
been observed to have been working with a number of start-up companies for free. It is to be
well pointed as Board will be unaware of any kinds of IT issue related to CoM-ONE, there is

8
CoM CASE STUDY
a need for CFO who will be breaking down the issues of IT to huge numbers and with a huge
expense.
The HR team manager of CoM has decided to go cloud and has even attended the
presentation about SaaS in the area of HR and for this, she has her intention of obtaining the
funding from that of CEO and then utilise that particular fund for purchasing the specific
service of SaaS HRM systems provider.
Threats and Vulnerabilities
Software bugs: It is basically an error or fault in a program of computer which makes it
produce a totally incorrect solution. This may arise because of bringing in own devices in the
organization.
Malicious apps: Bringing in own devices within the organization can be bringing in malicious
apps with it which can be entirely damaging any system of the CoM.
Hacking: There is also a high chance of hacking of account number of other details during the
online transactions done between the donor and the organization.
Phishing: Online transactions may also be bringing in phishing which is basically an attack
where all the hackers may be stealing the data of the user involving all the numbers of credit
card and other credentials.
Credit card frauds: Credit card frauds is mainly a term for the theft as well as the fraud which
can be committed utilising the payment card like the debit or credit ones.
DDoS attacks: The deployment of cloud can be bringing in various attacks of DDoS which re
actually attempts for disrupting the normal traffic of a server which will be targeted.
CoM CASE STUDY
a need for CFO who will be breaking down the issues of IT to huge numbers and with a huge
expense.
The HR team manager of CoM has decided to go cloud and has even attended the
presentation about SaaS in the area of HR and for this, she has her intention of obtaining the
funding from that of CEO and then utilise that particular fund for purchasing the specific
service of SaaS HRM systems provider.
Threats and Vulnerabilities
Software bugs: It is basically an error or fault in a program of computer which makes it
produce a totally incorrect solution. This may arise because of bringing in own devices in the
organization.
Malicious apps: Bringing in own devices within the organization can be bringing in malicious
apps with it which can be entirely damaging any system of the CoM.
Hacking: There is also a high chance of hacking of account number of other details during the
online transactions done between the donor and the organization.
Phishing: Online transactions may also be bringing in phishing which is basically an attack
where all the hackers may be stealing the data of the user involving all the numbers of credit
card and other credentials.
Credit card frauds: Credit card frauds is mainly a term for the theft as well as the fraud which
can be committed utilising the payment card like the debit or credit ones.
DDoS attacks: The deployment of cloud can be bringing in various attacks of DDoS which re
actually attempts for disrupting the normal traffic of a server which will be targeted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
CoM CASE STUDY
Data Breaches: It is considered to be confirmed incident within which various sensitive
information or data can be fully disclosed in a fashion which will be totally unauthorized.
This may also be resulting from the deployment of the cloud.
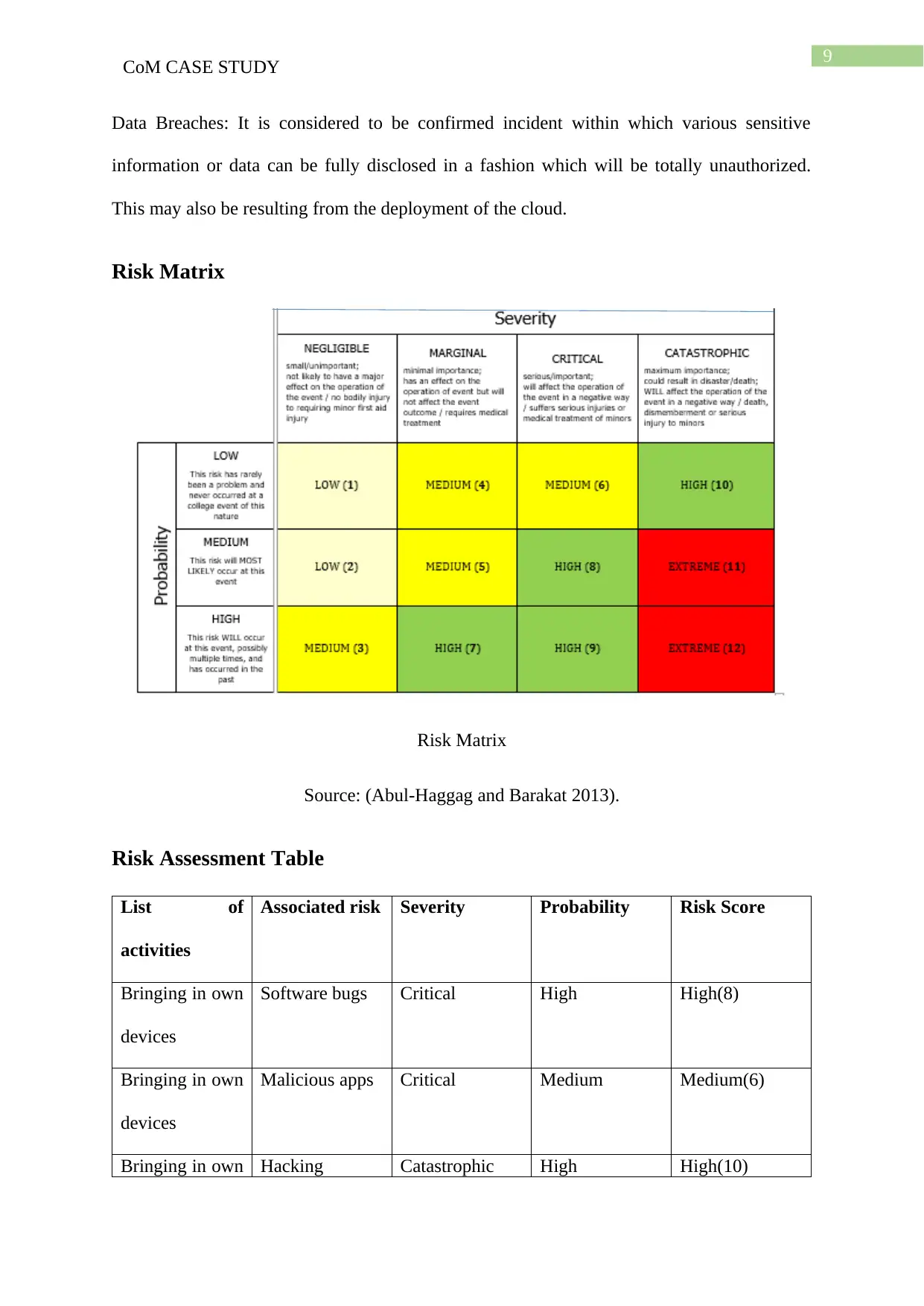
Risk Matrix
Risk Matrix
Source: (Abul-Haggag and Barakat 2013).
Risk Assessment Table
List of
activities
Associated risk Severity Probability Risk Score
Bringing in own
devices
Software bugs Critical High High(8)
Bringing in own
devices
Malicious apps Critical Medium Medium(6)
Bringing in own Hacking Catastrophic High High(10)
CoM CASE STUDY
Data Breaches: It is considered to be confirmed incident within which various sensitive
information or data can be fully disclosed in a fashion which will be totally unauthorized.
This may also be resulting from the deployment of the cloud.
Risk Matrix
Risk Matrix
Source: (Abul-Haggag and Barakat 2013).
Risk Assessment Table
List of
activities
Associated risk Severity Probability Risk Score
Bringing in own
devices
Software bugs Critical High High(8)
Bringing in own
devices
Malicious apps Critical Medium Medium(6)
Bringing in own Hacking Catastrophic High High(10)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
CoM CASE STUDY
devices
Online
transactions
Phishing Critical Medium Medium(6)
Online
Transactions
Credit card
frauds
Catastrophic High High(10)
Deployment of
cloud
DDoS attacks Catastrophic High High(10)
Deployment of
cloud
Data breaches Critical Medium Medium(6)
It can be recommended that all the various risks which have been identified must be
well taken care of and must be identified very much carefully. It is to be remembered that all
of these various risks can be bringing in a number of problems to CoM and hence while
performing all the various operations, a number of things are to be kept in mind.
CoM CASE STUDY
devices
Online
transactions
Phishing Critical Medium Medium(6)
Online
Transactions
Credit card
frauds
Catastrophic High High(10)
Deployment of
cloud
DDoS attacks Catastrophic High High(10)
Deployment of
cloud
Data breaches Critical Medium Medium(6)
It can be recommended that all the various risks which have been identified must be
well taken care of and must be identified very much carefully. It is to be remembered that all
of these various risks can be bringing in a number of problems to CoM and hence while
performing all the various operations, a number of things are to be kept in mind.

11
CoM CASE STUDY
Bibliography
Abul-Haggag, O.Y. and Barakat, W., 2013. Application of fuzzy logic for risk assessment
using risk matrix. International Journal of Emerging Technology and Advanced
Engineering, 3(1), pp.49-54.
Akram, S., Shafiq, M. and Akbar, M.A., 2016. Automated Risk Analysis Model for Software
Development Enhancement. International Journal of Multidisciplinary Sciences and
Engineering, 7(8), pp.23-27.
Andrat, H. and Jaswal, S., 2015, December. An alternative approach for risk assessment in
Scrum. In 2015 International Conference on Computing and Network Communications
(CoCoNet) (pp. 535-539). IEEE.
Ashley-Smith, J., 2013. Risk assessment for object conservation. Routledge.
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Aydogan, G. and Koksal, A., 2013. An analysis of international construction risk factors on
partner selection by applying ANP approach. In ICCREM 2013: Construction and Operation
in the Context of Sustainability (pp. 658-669).
Covello, V.T. and Merkhoher, M.W., 2013. Risk assessment methods: approaches for
assessing health and environmental risks. Springer Science & Business Media.
De Vries Robbé, M., de Vogel, V., Douglas, K.S. and Nijman, H.L., 2015. Changes in
dynamic risk and protective factors for violence during inpatient forensic psychiatric
treatment: Predicting reductions in postdischarge community recidivism. Law and Human
Behavior, 39(1), p.53.
CoM CASE STUDY
Bibliography
Abul-Haggag, O.Y. and Barakat, W., 2013. Application of fuzzy logic for risk assessment
using risk matrix. International Journal of Emerging Technology and Advanced
Engineering, 3(1), pp.49-54.
Akram, S., Shafiq, M. and Akbar, M.A., 2016. Automated Risk Analysis Model for Software
Development Enhancement. International Journal of Multidisciplinary Sciences and
Engineering, 7(8), pp.23-27.
Andrat, H. and Jaswal, S., 2015, December. An alternative approach for risk assessment in
Scrum. In 2015 International Conference on Computing and Network Communications
(CoCoNet) (pp. 535-539). IEEE.
Ashley-Smith, J., 2013. Risk assessment for object conservation. Routledge.
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Aydogan, G. and Koksal, A., 2013. An analysis of international construction risk factors on
partner selection by applying ANP approach. In ICCREM 2013: Construction and Operation
in the Context of Sustainability (pp. 658-669).
Covello, V.T. and Merkhoher, M.W., 2013. Risk assessment methods: approaches for
assessing health and environmental risks. Springer Science & Business Media.
De Vries Robbé, M., de Vogel, V., Douglas, K.S. and Nijman, H.L., 2015. Changes in
dynamic risk and protective factors for violence during inpatient forensic psychiatric
treatment: Predicting reductions in postdischarge community recidivism. Law and Human
Behavior, 39(1), p.53.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





