University Report: CO4509 Memcrashed Vulnerability Assessment
VerifiedAdded on 2023/04/07
|18
|3791
|408
Report
AI Summary
This report provides a comprehensive analysis of the memcrashed vulnerability, a significant denial-of-service (DoS) attack that exploits the memcached caching system. It begins with an introduction to memcached and its function in dynamic web applications, explaining how it works as a key-value database and its use in improving website performance by caching data in RAM. The report details the memcrashed vulnerability, describing how attackers leverage memcache's design to launch amplification attacks, where small requests result in large responses, overwhelming target systems. It provides examples of memcrashed attacks, such as the one that hit Github with massive traffic, and explains the different ways these attacks can be initiated, including the exploitation of UDP. The report then discusses various solutions to mitigate memcrashed, such as using firewalls, rate limiting UDP traffic, and disabling UDP when not needed. Finally, it explores the potential future importance and effectiveness of memcached, concluding with predictions on the ongoing impact of this vulnerability in the cyber security landscape.

Running head: MEMCRASHED VULNERABILITY
MEMCRASHED VULNERABILITY
Name of the Student:
Name of the University:
Author Note:
MEMCRASHED VULNERABILITY
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1MEMCRASHED VULNERABILITY
Table of Contents
Introduction....................................................................................................................2
Memcrashed vulnerability and its working principal.....................................................3
The working of the memcrashed vulnerability:.............................................................3
Example of Memecrashed vulnerability........................................................................4
Description of memcrashed exploits:.............................................................................5
Different ways through which the memcached attacks can be initiated........................7
Solution to the memcrashed exploit...............................................................................8
Future importance and effectiveness of memcached:..................................................10
Conclusion....................................................................................................................11
References....................................................................................................................12
Table of Contents
Introduction....................................................................................................................2
Memcrashed vulnerability and its working principal.....................................................3
The working of the memcrashed vulnerability:.............................................................3
Example of Memecrashed vulnerability........................................................................4
Description of memcrashed exploits:.............................................................................5
Different ways through which the memcached attacks can be initiated........................7
Solution to the memcrashed exploit...............................................................................8
Future importance and effectiveness of memcached:..................................................10
Conclusion....................................................................................................................11
References....................................................................................................................12

2MEMCRASHED VULNERABILITY
Introduction
Memcached is the caching system which is used for the dynamic web applications.
Memcached is the open source and has been designed for working with the large number of
connections. In order to alleviate the load of the database API calls and page rendering can be
done (O’Hare, 2018). The use of memcache is getting popular among the users. The
memcrashed vulnerability is initiated through the memcache. This type of vulnerability can
be described as the latest threat for the cyberspace. Memcrashed vulnerability can be defined
as the new type of denial of service attack. The term “Memcrashed” used by the Cloudflare.
This type of vulnerability is responsible for the denial of service attack in Github.
In denial of service attack, the users cannot access their own system as the attackers
control the functionality of the system. It has been seen that the denial of service attacks
happen through the low bandwidth products and the applications of IoT (Lu & Li, 2016).
However, memcrashed vulnerability has higher bandwidth and this makes this attack to pose
more threats for the users of the cyberspace.
Another speciality of this kind of vulnerability is that for the initialization of this
attack, there is no need for the username and password. The generation of the vulnerability
can be done by running the debug command (Behzadan & Munir, 2017). The key of the data
can be revealed and the stealing of the data can be done. Apart from that the modification of
the data is possible using memcrashed.
The main objective of this paper is to evaluate the memcrashed vulnerabilities. Apart
from that different aspects of the memcrashed vulnerabilities have been discussed along with
the impact of this vulnerability in the users. The conclusion is drawn from the factors
discussed in the paper.
Introduction
Memcached is the caching system which is used for the dynamic web applications.
Memcached is the open source and has been designed for working with the large number of
connections. In order to alleviate the load of the database API calls and page rendering can be
done (O’Hare, 2018). The use of memcache is getting popular among the users. The
memcrashed vulnerability is initiated through the memcache. This type of vulnerability can
be described as the latest threat for the cyberspace. Memcrashed vulnerability can be defined
as the new type of denial of service attack. The term “Memcrashed” used by the Cloudflare.
This type of vulnerability is responsible for the denial of service attack in Github.
In denial of service attack, the users cannot access their own system as the attackers
control the functionality of the system. It has been seen that the denial of service attacks
happen through the low bandwidth products and the applications of IoT (Lu & Li, 2016).
However, memcrashed vulnerability has higher bandwidth and this makes this attack to pose
more threats for the users of the cyberspace.
Another speciality of this kind of vulnerability is that for the initialization of this
attack, there is no need for the username and password. The generation of the vulnerability
can be done by running the debug command (Behzadan & Munir, 2017). The key of the data
can be revealed and the stealing of the data can be done. Apart from that the modification of
the data is possible using memcrashed.
The main objective of this paper is to evaluate the memcrashed vulnerabilities. Apart
from that different aspects of the memcrashed vulnerabilities have been discussed along with
the impact of this vulnerability in the users. The conclusion is drawn from the factors
discussed in the paper.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3MEMCRASHED VULNERABILITY
Memcrashed vulnerability and its working principal
Memcrashed vulnerability is the type of vulnerability that has exploited memcache.
Memcache is a general purpose memory caching system which is distributed in nature.
Through caching the information into RAM this type of cache speeds up the dynamic
database in the website. Memcache is a free and open source software which is licenced by
Revised BSD License. Memcache is can be use both UNIX based system and Microsoft
Windows.
The system uses client-server architecture and maintains a key-value which is
associative array. The client can use this key to generate the query. Memcache API provides
the large hash table which is distributed over multiple network. It has been seen that the
memcrashed vulnerability has used these attributes of memcache for the deployment of
attacks.
The working of the memcrashed vulnerability:
Memcrashed attack is considered as one of the biggest and most critical denial of
service attack for the cyber space (Elleuch et al., 2016). In this context, it can be said, the
exploit of the memcache has been conducted earlier. However, the trend has been increased
in the present year.
Memcrashed vulnerability and its working principal
Memcrashed vulnerability is the type of vulnerability that has exploited memcache.
Memcache is a general purpose memory caching system which is distributed in nature.
Through caching the information into RAM this type of cache speeds up the dynamic
database in the website. Memcache is a free and open source software which is licenced by
Revised BSD License. Memcache is can be use both UNIX based system and Microsoft
Windows.
The system uses client-server architecture and maintains a key-value which is
associative array. The client can use this key to generate the query. Memcache API provides
the large hash table which is distributed over multiple network. It has been seen that the
memcrashed vulnerability has used these attributes of memcache for the deployment of
attacks.
The working of the memcrashed vulnerability:
Memcrashed attack is considered as one of the biggest and most critical denial of
service attack for the cyber space (Elleuch et al., 2016). In this context, it can be said, the
exploit of the memcache has been conducted earlier. However, the trend has been increased
in the present year.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
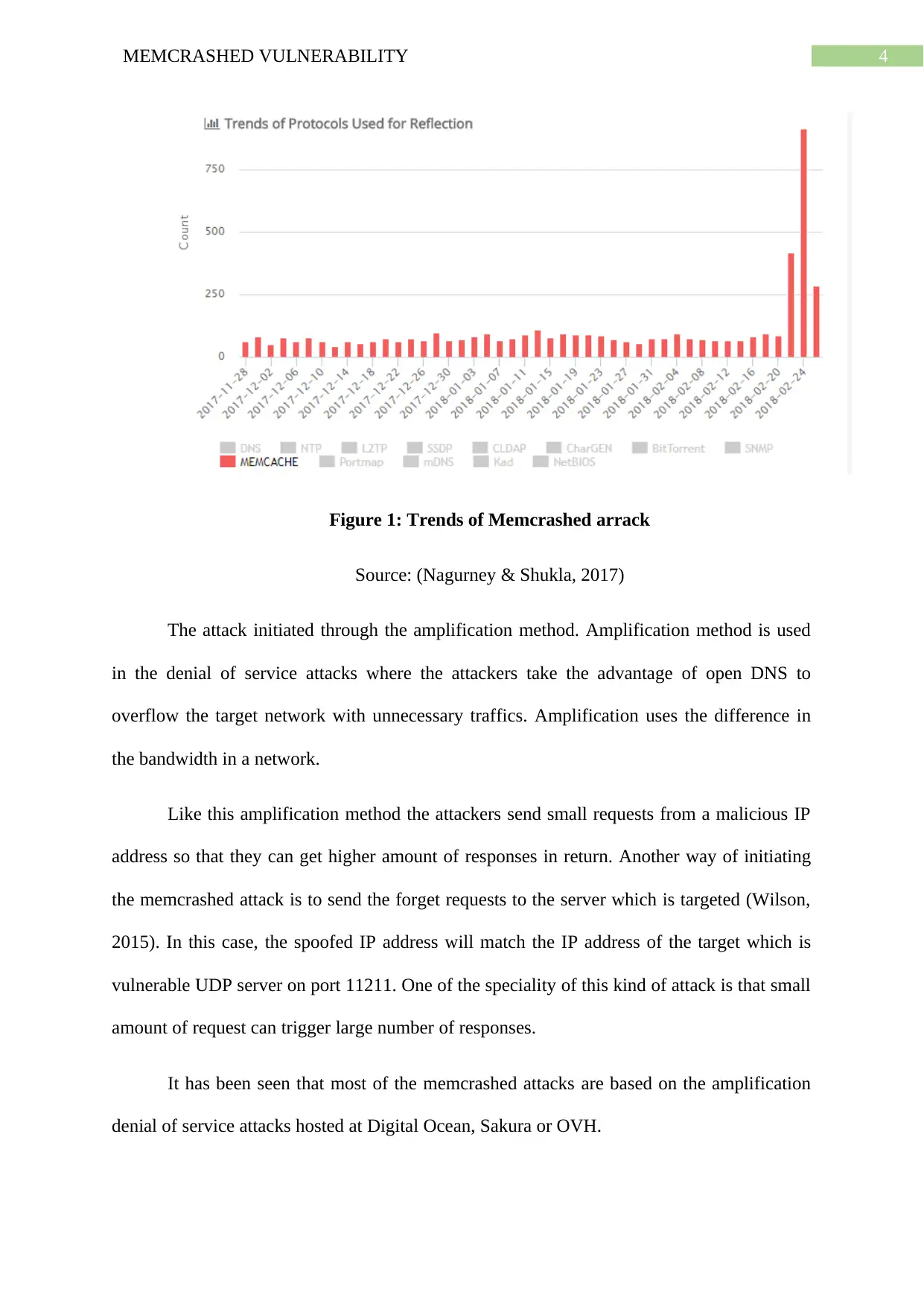
4MEMCRASHED VULNERABILITY
Figure 1: Trends of Memcrashed arrack
Source: (Nagurney & Shukla, 2017)
The attack initiated through the amplification method. Amplification method is used
in the denial of service attacks where the attackers take the advantage of open DNS to
overflow the target network with unnecessary traffics. Amplification uses the difference in
the bandwidth in a network.
Like this amplification method the attackers send small requests from a malicious IP
address so that they can get higher amount of responses in return. Another way of initiating
the memcrashed attack is to send the forget requests to the server which is targeted (Wilson,
2015). In this case, the spoofed IP address will match the IP address of the target which is
vulnerable UDP server on port 11211. One of the speciality of this kind of attack is that small
amount of request can trigger large number of responses.
It has been seen that most of the memcrashed attacks are based on the amplification
denial of service attacks hosted at Digital Ocean, Sakura or OVH.
Figure 1: Trends of Memcrashed arrack
Source: (Nagurney & Shukla, 2017)
The attack initiated through the amplification method. Amplification method is used
in the denial of service attacks where the attackers take the advantage of open DNS to
overflow the target network with unnecessary traffics. Amplification uses the difference in
the bandwidth in a network.
Like this amplification method the attackers send small requests from a malicious IP
address so that they can get higher amount of responses in return. Another way of initiating
the memcrashed attack is to send the forget requests to the server which is targeted (Wilson,
2015). In this case, the spoofed IP address will match the IP address of the target which is
vulnerable UDP server on port 11211. One of the speciality of this kind of attack is that small
amount of request can trigger large number of responses.
It has been seen that most of the memcrashed attacks are based on the amplification
denial of service attacks hosted at Digital Ocean, Sakura or OVH.

5MEMCRASHED VULNERABILITY
Example of Memecrashed vulnerability
In order to understand the impact of the memcrashed vulnerability, one of the
example of this threat can be discussed. One of the significant attack by memecrashed
vulnerability has been seen on the Github. 1.35 terabyte per second traffic has hit the Github
(Cloudflare Blog. 2019). According to the record, it is considered as one of the most powerful
distributed denial of service attack.
For the initial 10 minutes of attack, Github struggled with the outrages. After that the
website automatically asked for help from the denial of attack mitigation service Akamai
Prolexic. Akamai Prolexic routed all the traffic coming into Github and sent the data through
scrubbing centers to extract the block of malicious packets. After 8 minutes, the attack on the
Github was normalized and assault was dropped off.
Another example of memcrashed attack was faced by internet infrastructure company
Dyn in a massive scale in 2016. The traffic was moving at the rate of 1.2 terabits per second
that caused the issues in connectivity across US. However, DYN has controlled the situation
by necessary steps.
Description of memcrashed exploits:
Memcrashed attack is one kind of Denial of Service attack. Denial-of-service attack is
a kind of cyber-attack where the intruders or attackers take the control of the machine. The
control of the functionality is done by the attackers and the uses cannot operate their own
system. The attack is initiated through making the resources unavailable to the users by
disrupting the services of the host system (Wu et al., 2015). This is done by flooding the
target machine by sending the unnecessary traffics.
There are various types of denial of service attack. One type of this attack is
distributed denial of service attack. Distributed denial of service attack is type of attack where
Example of Memecrashed vulnerability
In order to understand the impact of the memcrashed vulnerability, one of the
example of this threat can be discussed. One of the significant attack by memecrashed
vulnerability has been seen on the Github. 1.35 terabyte per second traffic has hit the Github
(Cloudflare Blog. 2019). According to the record, it is considered as one of the most powerful
distributed denial of service attack.
For the initial 10 minutes of attack, Github struggled with the outrages. After that the
website automatically asked for help from the denial of attack mitigation service Akamai
Prolexic. Akamai Prolexic routed all the traffic coming into Github and sent the data through
scrubbing centers to extract the block of malicious packets. After 8 minutes, the attack on the
Github was normalized and assault was dropped off.
Another example of memcrashed attack was faced by internet infrastructure company
Dyn in a massive scale in 2016. The traffic was moving at the rate of 1.2 terabits per second
that caused the issues in connectivity across US. However, DYN has controlled the situation
by necessary steps.
Description of memcrashed exploits:
Memcrashed attack is one kind of Denial of Service attack. Denial-of-service attack is
a kind of cyber-attack where the intruders or attackers take the control of the machine. The
control of the functionality is done by the attackers and the uses cannot operate their own
system. The attack is initiated through making the resources unavailable to the users by
disrupting the services of the host system (Wu et al., 2015). This is done by flooding the
target machine by sending the unnecessary traffics.
There are various types of denial of service attack. One type of this attack is
distributed denial of service attack. Distributed denial of service attack is type of attack where
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6MEMCRASHED VULNERABILITY
intruder uses more than one unique IP address. The attack is involved into more than 3 or 5
nodes in different network. This will make the traffics from different sources to flood the
network. The functioning of the system will be interrupted through the incoming of huge
amount of traffic.
Another type of denial of service attack is application layer attack which is often
mentioned as layer 7 DDoS attack. In this case, the attack is aimed at the application layer
processes. Application layer attack disable the specific functions in the webpage or website
through over exercise of functions and features (Younis, Malaiya & Ray, 2016). According to
Akamai Technology, about 51% of the denial of service attacks are application layer denial
of service attacks.
Recently, it has been seen that the attacks in the denial of service has been increased
recently. One of the recent type of denial of service attack is memcrashed attack.
Memcache is an open source software that is capable to speed up the database access
while accessing the webpage. The denial of service will enable the attack through the
vulnerability of the memcache (Yusuf et al., 2016). The main loop whole of the memcache is
that this software works in multichannel. Proof-of-concept code has published the list of
17,000 IP addresses of vulnerable memcached servers those are capable to send forged UDP
packets to initiate memcrashed attacks. These memcached servers are obtained from
Shodan.io. According to this source, more attention is needed to be given by the users while
updating their devices (Xu et al., 2015). The technology service provider Cloudflare and
Akamai has predicted that more of the memcrashed attacks are going to occur in future.
As memcached server runs over TCP or UDP port 11211, it has been seen that most
of the attacks are targeted to UDP server on port 11211. The memecached queries can be
directed towards TCP port 11211 (Fedorchenko, Kotenko & Chechulin, 2015). However, it
intruder uses more than one unique IP address. The attack is involved into more than 3 or 5
nodes in different network. This will make the traffics from different sources to flood the
network. The functioning of the system will be interrupted through the incoming of huge
amount of traffic.
Another type of denial of service attack is application layer attack which is often
mentioned as layer 7 DDoS attack. In this case, the attack is aimed at the application layer
processes. Application layer attack disable the specific functions in the webpage or website
through over exercise of functions and features (Younis, Malaiya & Ray, 2016). According to
Akamai Technology, about 51% of the denial of service attacks are application layer denial
of service attacks.
Recently, it has been seen that the attacks in the denial of service has been increased
recently. One of the recent type of denial of service attack is memcrashed attack.
Memcache is an open source software that is capable to speed up the database access
while accessing the webpage. The denial of service will enable the attack through the
vulnerability of the memcache (Yusuf et al., 2016). The main loop whole of the memcache is
that this software works in multichannel. Proof-of-concept code has published the list of
17,000 IP addresses of vulnerable memcached servers those are capable to send forged UDP
packets to initiate memcrashed attacks. These memcached servers are obtained from
Shodan.io. According to this source, more attention is needed to be given by the users while
updating their devices (Xu et al., 2015). The technology service provider Cloudflare and
Akamai has predicted that more of the memcrashed attacks are going to occur in future.
As memcached server runs over TCP or UDP port 11211, it has been seen that most
of the attacks are targeted to UDP server on port 11211. The memecached queries can be
directed towards TCP port 11211 (Fedorchenko, Kotenko & Chechulin, 2015). However, it
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MEMCRASHED VULNERABILITY
has been seen that TCP is not considered to be in high risk zone for the memcrashed attacks.
The reason behind this is that the TCP queries cannot be reliably spoofed.
Figure 2: Exploitation of UDP
Source: (Cloudflare Blog. 2019)
Memcrashed attacks works through exploiting the memecached programs. Memcache
is used by the social network platforms like Facebook, LiveJournal as memory key value for
storing the small chunks of arbitrary data (Vida, Galeano & Cuenda, 2015). Memcache helps
these media platforms to handle large amount of input-output data and is used in the web-
server sessions to increase the speed of the website.
It has been seen that memcached enable servers have exposed to the internet through
incompetent system administrator. Memcached is not supposed to be exposed over the
internet as it has no authentication (Chen, 2018). As, there is no authentication, it is easy to
attack through the memcache. When the attackers find memcache over internet they use it to
implement denial of service attack through UDP.
has been seen that TCP is not considered to be in high risk zone for the memcrashed attacks.
The reason behind this is that the TCP queries cannot be reliably spoofed.
Figure 2: Exploitation of UDP
Source: (Cloudflare Blog. 2019)
Memcrashed attacks works through exploiting the memecached programs. Memcache
is used by the social network platforms like Facebook, LiveJournal as memory key value for
storing the small chunks of arbitrary data (Vida, Galeano & Cuenda, 2015). Memcache helps
these media platforms to handle large amount of input-output data and is used in the web-
server sessions to increase the speed of the website.
It has been seen that memcached enable servers have exposed to the internet through
incompetent system administrator. Memcached is not supposed to be exposed over the
internet as it has no authentication (Chen, 2018). As, there is no authentication, it is easy to
attack through the memcache. When the attackers find memcache over internet they use it to
implement denial of service attack through UDP.

8MEMCRASHED VULNERABILITY
When a server acknowledges the memcached get request, it collects the value from
the memory in order to give the response. The response is sent over the internet through
multiple UDP packets. The size of each packets is 1.400 bytes.
The intruders manipulate the memcached server which is open. The size limit of data
stored in memcache is of 1MB. The intruder can put large values and duplicate keys with the
single request can be made.
The larger value of data load by the attackers can initiate the attack in the system.
Through this the attackers can initiate a spoofed UDP packet request of 1MB on the basis of
single megabyte stored value (Carra & Michiardi, 2016). This spoofed data of 1MB can be
sent hundreds of times per request over default port of UDP 11211.
Moreover, the attackers do not focus on one vulnerable server. They target multiple
vulnerable servers. This makes the attack to be occurred in a massive rate.
Different ways through which the memcached attacks can be initiated
Potential attacks may involve one or more memcached servers that works with
arbitrary data. The attackers can send a series of requests through UDP port 11211. These
sources are responsible source of IP for denial of service targets. The source can be spoofed
for any target specific service (Mendonça, 2017). Apart from that the memcached servers
send and receive the large responses to the target. The response is amplified that is response
is larger than the request. The resource of the target can be depleted depending the size of the
attacks that results to the denial of service attack.
Solution to the memcrashed exploit
One of the easiest way to mitigate the possibility of the memcrashed attack is to use
the firewall that will control the network traffic. Apart from that the traffic rate limiting UDP
on source port 11211 can be used for the mitigation of this type of attack.
When a server acknowledges the memcached get request, it collects the value from
the memory in order to give the response. The response is sent over the internet through
multiple UDP packets. The size of each packets is 1.400 bytes.
The intruders manipulate the memcached server which is open. The size limit of data
stored in memcache is of 1MB. The intruder can put large values and duplicate keys with the
single request can be made.
The larger value of data load by the attackers can initiate the attack in the system.
Through this the attackers can initiate a spoofed UDP packet request of 1MB on the basis of
single megabyte stored value (Carra & Michiardi, 2016). This spoofed data of 1MB can be
sent hundreds of times per request over default port of UDP 11211.
Moreover, the attackers do not focus on one vulnerable server. They target multiple
vulnerable servers. This makes the attack to be occurred in a massive rate.
Different ways through which the memcached attacks can be initiated
Potential attacks may involve one or more memcached servers that works with
arbitrary data. The attackers can send a series of requests through UDP port 11211. These
sources are responsible source of IP for denial of service targets. The source can be spoofed
for any target specific service (Mendonça, 2017). Apart from that the memcached servers
send and receive the large responses to the target. The response is amplified that is response
is larger than the request. The resource of the target can be depleted depending the size of the
attacks that results to the denial of service attack.
Solution to the memcrashed exploit
One of the easiest way to mitigate the possibility of the memcrashed attack is to use
the firewall that will control the network traffic. Apart from that the traffic rate limiting UDP
on source port 11211 can be used for the mitigation of this type of attack.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
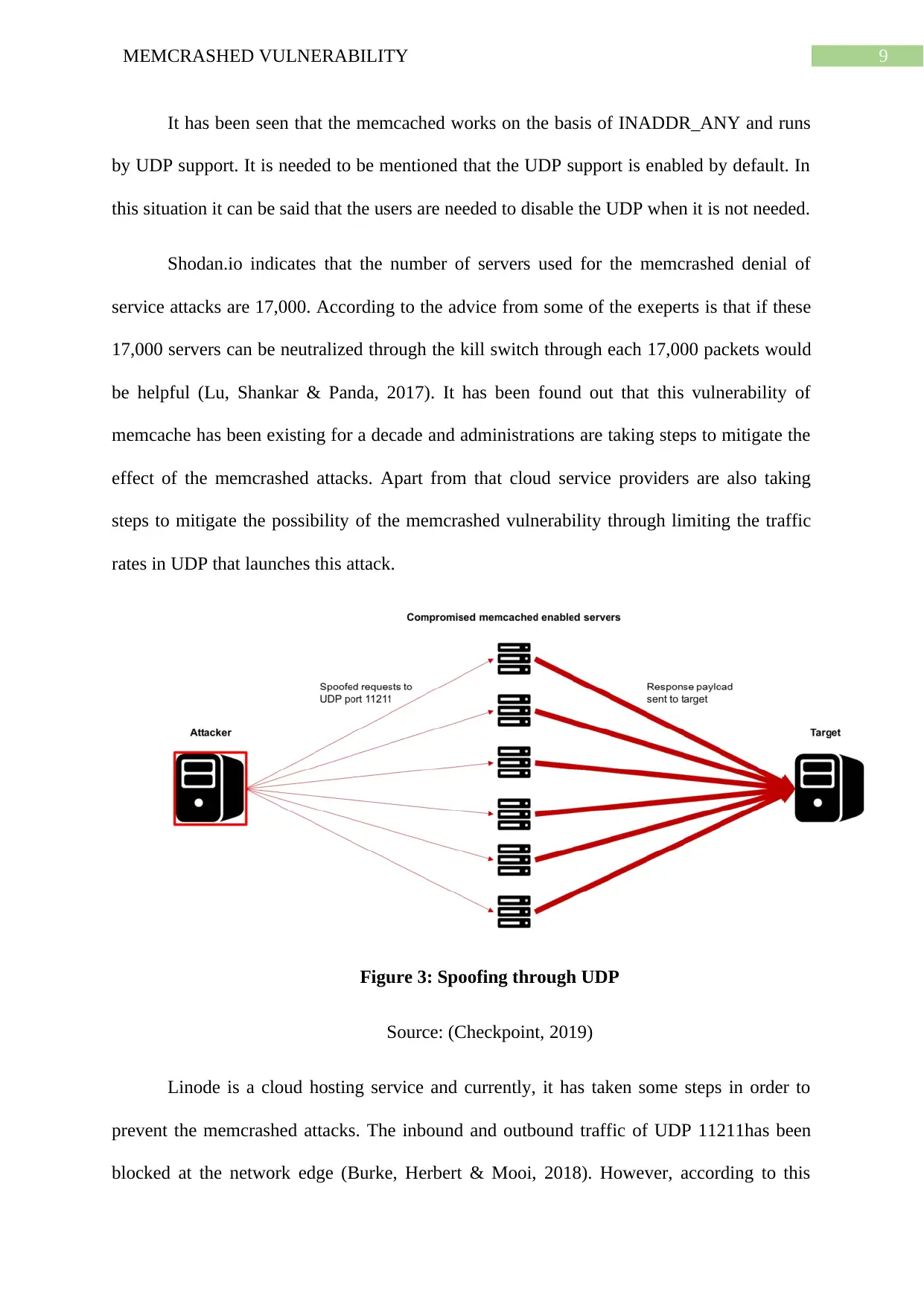
9MEMCRASHED VULNERABILITY
It has been seen that the memcached works on the basis of INADDR_ANY and runs
by UDP support. It is needed to be mentioned that the UDP support is enabled by default. In
this situation it can be said that the users are needed to disable the UDP when it is not needed.
Shodan.io indicates that the number of servers used for the memcrashed denial of
service attacks are 17,000. According to the advice from some of the exeperts is that if these
17,000 servers can be neutralized through the kill switch through each 17,000 packets would
be helpful (Lu, Shankar & Panda, 2017). It has been found out that this vulnerability of
memcache has been existing for a decade and administrations are taking steps to mitigate the
effect of the memcrashed attacks. Apart from that cloud service providers are also taking
steps to mitigate the possibility of the memcrashed vulnerability through limiting the traffic
rates in UDP that launches this attack.
Figure 3: Spoofing through UDP
Source: (Checkpoint, 2019)
Linode is a cloud hosting service and currently, it has taken some steps in order to
prevent the memcrashed attacks. The inbound and outbound traffic of UDP 11211has been
blocked at the network edge (Burke, Herbert & Mooi, 2018). However, according to this
It has been seen that the memcached works on the basis of INADDR_ANY and runs
by UDP support. It is needed to be mentioned that the UDP support is enabled by default. In
this situation it can be said that the users are needed to disable the UDP when it is not needed.
Shodan.io indicates that the number of servers used for the memcrashed denial of
service attacks are 17,000. According to the advice from some of the exeperts is that if these
17,000 servers can be neutralized through the kill switch through each 17,000 packets would
be helpful (Lu, Shankar & Panda, 2017). It has been found out that this vulnerability of
memcache has been existing for a decade and administrations are taking steps to mitigate the
effect of the memcrashed attacks. Apart from that cloud service providers are also taking
steps to mitigate the possibility of the memcrashed vulnerability through limiting the traffic
rates in UDP that launches this attack.
Figure 3: Spoofing through UDP
Source: (Checkpoint, 2019)
Linode is a cloud hosting service and currently, it has taken some steps in order to
prevent the memcrashed attacks. The inbound and outbound traffic of UDP 11211has been
blocked at the network edge (Burke, Herbert & Mooi, 2018). However, according to this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10MEMCRASHED VULNERABILITY
cloud provider this is a temporary solution. The receiving and seding of the UDP traffic on
port 11211 is not possible from outside of the Linode network.
The review and the application of the memcache version of 1.5.6 is needed to be
done. Using this version will disable the UDP by default. The users has to enable the UDP
when it is needed to be used. The organizations having the system based on the cloud and
accessing different platforms in cyberspace are needed to fix strategy that can prevent the
denial of service attacks (Czubak & Szymanek, 2017). For the cloud storage and the cloud
architecture, the organizations have to discuss with the service providers regarding the
security policies and the strategies for the prevention of memcrashed attacks. Apart from that
while selecting the service providers the organizations should consider the capacity of the
service provider to withstand with the attacks along with the ability to response quickly.
BGP or DNS based routing can be effective to prevent traffic diversion. The
memcached attacks provide a way for the denial of service attack in application layer. The
use of the in-line filtering through the application of the hardware appliance like Web
application Firewall (Wei & Fung, 2015). This will enable the protection against the
application layer attacks. Moreover, identifying the disabling attack vectors will be helpful
for removing large files and vulnerable from internet space.
Running memcache outside the firewall is needed to be avoided in order to mitigate
the possibility of memcached attacks. While running the memcached the uses should disable
the UDP support. The closing off port 11211 is also useful for the prevention of memcached
attacks (Marathe et al., 2017). Some of the service providers can provide supports for the
prevention of the denial of service attacks such as CloudFlare, Incapsula. Taking technical
support from these service providers can be helpful for the prevention of denial of service
attack.
cloud provider this is a temporary solution. The receiving and seding of the UDP traffic on
port 11211 is not possible from outside of the Linode network.
The review and the application of the memcache version of 1.5.6 is needed to be
done. Using this version will disable the UDP by default. The users has to enable the UDP
when it is needed to be used. The organizations having the system based on the cloud and
accessing different platforms in cyberspace are needed to fix strategy that can prevent the
denial of service attacks (Czubak & Szymanek, 2017). For the cloud storage and the cloud
architecture, the organizations have to discuss with the service providers regarding the
security policies and the strategies for the prevention of memcrashed attacks. Apart from that
while selecting the service providers the organizations should consider the capacity of the
service provider to withstand with the attacks along with the ability to response quickly.
BGP or DNS based routing can be effective to prevent traffic diversion. The
memcached attacks provide a way for the denial of service attack in application layer. The
use of the in-line filtering through the application of the hardware appliance like Web
application Firewall (Wei & Fung, 2015). This will enable the protection against the
application layer attacks. Moreover, identifying the disabling attack vectors will be helpful
for removing large files and vulnerable from internet space.
Running memcache outside the firewall is needed to be avoided in order to mitigate
the possibility of memcached attacks. While running the memcached the uses should disable
the UDP support. The closing off port 11211 is also useful for the prevention of memcached
attacks (Marathe et al., 2017). Some of the service providers can provide supports for the
prevention of the denial of service attacks such as CloudFlare, Incapsula. Taking technical
support from these service providers can be helpful for the prevention of denial of service
attack.

11MEMCRASHED VULNERABILITY
In order to disable the UDP in the system the users can specify by - - listen 127.0.0.1
so that only the local host can listen and – U 0 for disabling the UDP completely.
From the system administrator end memcached servers can be firewalled from the
internet. The command nc can be used to test whether the servers can be accessed from the
UDP.
Future importance and effectiveness of memcached:
It has been seen that the memcrashed vulnerability has remained for a long time.
However, certain steps were not taken as this vulnerability was not exploited. However, it has
been seen that memcache has been used for the initialization of the threats through the
memcrashed (Balzacq & Cavelty, 2016). This vulnerability is considered as one of the
biggest denial of service attacks that has affected many organizations along with Github.
At present the organizations are becoming concerned about this kind of security
threats. It can be assumed that the use of the internet and the dependency over the cyber space
will be increasing in future. In this situation, the use of memcache will be increased. The use
of memcache and UDP will enhance the probability of the memcrashed attack. In order to
prevent this the IP spoofing is needed to be controlled (Lu, Shankar & Panda, 2017). Apart
from that the orgnaizations have to take care of maintaing the firewall and controlling the
network traffics in the organization network.
The users are needed to be aware about the effects of the memcrashed attacks and
they should follow the basic rules like disabling the UDP for the prevention of attacks.
It has been assumed by the experts that there are 17,000 memcrashed severs those are
capable of memcrashed attacks. It can be expected that this type of attack can occur at large
scale in future (Hyder & Lung, 2018). However, there are kill switch invented to disable for
the memcrashed attack but there has questions about their effectiveness.
In order to disable the UDP in the system the users can specify by - - listen 127.0.0.1
so that only the local host can listen and – U 0 for disabling the UDP completely.
From the system administrator end memcached servers can be firewalled from the
internet. The command nc can be used to test whether the servers can be accessed from the
UDP.
Future importance and effectiveness of memcached:
It has been seen that the memcrashed vulnerability has remained for a long time.
However, certain steps were not taken as this vulnerability was not exploited. However, it has
been seen that memcache has been used for the initialization of the threats through the
memcrashed (Balzacq & Cavelty, 2016). This vulnerability is considered as one of the
biggest denial of service attacks that has affected many organizations along with Github.
At present the organizations are becoming concerned about this kind of security
threats. It can be assumed that the use of the internet and the dependency over the cyber space
will be increasing in future. In this situation, the use of memcache will be increased. The use
of memcache and UDP will enhance the probability of the memcrashed attack. In order to
prevent this the IP spoofing is needed to be controlled (Lu, Shankar & Panda, 2017). Apart
from that the orgnaizations have to take care of maintaing the firewall and controlling the
network traffics in the organization network.
The users are needed to be aware about the effects of the memcrashed attacks and
they should follow the basic rules like disabling the UDP for the prevention of attacks.
It has been assumed by the experts that there are 17,000 memcrashed severs those are
capable of memcrashed attacks. It can be expected that this type of attack can occur at large
scale in future (Hyder & Lung, 2018). However, there are kill switch invented to disable for
the memcrashed attack but there has questions about their effectiveness.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




