Exploring Security Challenges in Merging Internet of Things Networks
VerifiedAdded on 2024/05/31
|12
|2468
|371
Report
AI Summary
This report provides a comprehensive literature review of the Internet of Things (IoT), focusing on its characteristics compared to traditional networks and its applications in smart homes, enterprises, and industries. It critically analyzes current and future security issues in IoT, such as unauthorized access to RFID, sensor node security breaches, and cloud computing abuse. Furthermore, it discusses countermeasures and mitigation techniques, including secure web interfaces, sufficient authorization, secure network services, encryption techniques, and privacy concerns. The report highlights the importance of addressing these security challenges to ensure the safe and effective implementation of IoT technologies.

SECURITY CHALLENGES IN MERGING NETWORKS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Literature Review of IOT..........................................................................................................................2
I. Introduction to IOT...............................................................................................................................2
II. Characteristics of IOT to Traditional Network (include IOT devices)....................................................3
III. Three areas of application of IOT........................................................................................................5
2. Analyse critically, three current and future security issues in IOT and its countermeasures...................7
I. Analyse three security issues in IOT......................................................................................................7
II. Countermeasures and Mitigation techniques and tools used for security issues................................9
References.................................................................................................................................................11
List of figure
Figure 1 Characteristics of IOT.....................................................................................................................3
Figure 2 Smart Homes.................................................................................................................................4
Figure 3 Smart Enterprise...........................................................................................................................5
Figure 4 Smart Industry...............................................................................................................................5
1. Literature Review of IOT..........................................................................................................................2
I. Introduction to IOT...............................................................................................................................2
II. Characteristics of IOT to Traditional Network (include IOT devices)....................................................3
III. Three areas of application of IOT........................................................................................................5
2. Analyse critically, three current and future security issues in IOT and its countermeasures...................7
I. Analyse three security issues in IOT......................................................................................................7
II. Countermeasures and Mitigation techniques and tools used for security issues................................9
References.................................................................................................................................................11
List of figure
Figure 1 Characteristics of IOT.....................................................................................................................3
Figure 2 Smart Homes.................................................................................................................................4
Figure 3 Smart Enterprise...........................................................................................................................5
Figure 4 Smart Industry...............................................................................................................................5

1. Literature Review of IOT
I. Introduction to IOT
IoT (Internet of Things) is the ecosystem in which devices are connected to the internet and
the other devices so long as it has an on/off switch. It is a giant network in which things and
people are connected in such a manner as to collect data about the environment and share
it. The objects that are connected can be anything and can be of any shape and size. For
example, a gate, a microwave that cooks your food automatically, a football, self-driving
cars, wearable fitness devices etc.
These devices have built-in sensors within them which are connected to an Internet of
Things platform. This platform integrates the data that is collected from different devices
and apply analytics to pass the important information to the applications which are built
with the purpose to serve a specific need. These IOT platforms are made so powerful that
they can infer which information is important and needed to be kept and which are to be
ignored. This information detects patterns, potential problems and can be used to make
suggestions and recommendations. This information can help make smart business decisions
and may help to grow faster [3].
Example of IOT:
Example 1: Imagine a situation where you need to reach your workplace at 9:30. For this,
you need to wake up at 8’O clock in the morning. You set your alarm clock to ring an alarm
at 8:00 am. Now, it happened that the bus you take for work has been canceled and will be
before time and it is raining cats and dogs. In this, situation, your normal alarm clock will ring
at 8’O clock but if your alarm clock is synced to IOT platform it will calculate the time your
bus will reach the station, calculate the speed of the bus in this heavy rain and will ring
before time so that you reach office on time [1].
Example 2: You are going to a resort where you visit frequently. You have already registered
yourself with your mobile number and email id. The gates of the resort are embedded with
sensors. Now when you with your device enter the resort, the sensors of the gate will detect
it’s you and will send you a message saying “Welcome To Our Resort”.
IOT connects devices beyond the standard devices like laptops and desktops.
I. Introduction to IOT
IoT (Internet of Things) is the ecosystem in which devices are connected to the internet and
the other devices so long as it has an on/off switch. It is a giant network in which things and
people are connected in such a manner as to collect data about the environment and share
it. The objects that are connected can be anything and can be of any shape and size. For
example, a gate, a microwave that cooks your food automatically, a football, self-driving
cars, wearable fitness devices etc.
These devices have built-in sensors within them which are connected to an Internet of
Things platform. This platform integrates the data that is collected from different devices
and apply analytics to pass the important information to the applications which are built
with the purpose to serve a specific need. These IOT platforms are made so powerful that
they can infer which information is important and needed to be kept and which are to be
ignored. This information detects patterns, potential problems and can be used to make
suggestions and recommendations. This information can help make smart business decisions
and may help to grow faster [3].
Example of IOT:
Example 1: Imagine a situation where you need to reach your workplace at 9:30. For this,
you need to wake up at 8’O clock in the morning. You set your alarm clock to ring an alarm
at 8:00 am. Now, it happened that the bus you take for work has been canceled and will be
before time and it is raining cats and dogs. In this, situation, your normal alarm clock will ring
at 8’O clock but if your alarm clock is synced to IOT platform it will calculate the time your
bus will reach the station, calculate the speed of the bus in this heavy rain and will ring
before time so that you reach office on time [1].
Example 2: You are going to a resort where you visit frequently. You have already registered
yourself with your mobile number and email id. The gates of the resort are embedded with
sensors. Now when you with your device enter the resort, the sensors of the gate will detect
it’s you and will send you a message saying “Welcome To Our Resort”.
IOT connects devices beyond the standard devices like laptops and desktops.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

II. Characteristics of IOT to Traditional Network (include
IoT devices)
There are seven key characteristics of IoT:
a) Connectivity – All the devices embedded with RFID, needs to be connected to the
internet. Connectivity is very important as this is the only way things in IOT
environment can exchange the valuable data.
b) Things – Things can be anything and can be of any shape and size like a door, a
football etc. These things can be tagged using RFID, which provides them with a
unique identification number. They can be tagged actively as well as passively.
c) Data – This is the first step towards action and intelligence. Data is collected from
the sensors that are embedded inside the objects. This data is analysed to take a
certain course of action [7].
d) Intelligence – This is the foundation of the IOT. Artificial Intelligence which senses
and analyses the data according to the function is one such thing that makes IOT an
advanced and easy to use technology.
e) Ecosystem – This contains all the aspects and characteristics of IoT as seen from the
perspective of other technologies and communities.
f) Action – It is based on the decision made by intelligence. This action can be manual
as well as automatic.
g) Communication – All the devices are well connected so that the communication
between the devices can take place to exchange the data [9].
Figure 1 Characteristics of IOT
IoT devices)
There are seven key characteristics of IoT:
a) Connectivity – All the devices embedded with RFID, needs to be connected to the
internet. Connectivity is very important as this is the only way things in IOT
environment can exchange the valuable data.
b) Things – Things can be anything and can be of any shape and size like a door, a
football etc. These things can be tagged using RFID, which provides them with a
unique identification number. They can be tagged actively as well as passively.
c) Data – This is the first step towards action and intelligence. Data is collected from
the sensors that are embedded inside the objects. This data is analysed to take a
certain course of action [7].
d) Intelligence – This is the foundation of the IOT. Artificial Intelligence which senses
and analyses the data according to the function is one such thing that makes IOT an
advanced and easy to use technology.
e) Ecosystem – This contains all the aspects and characteristics of IoT as seen from the
perspective of other technologies and communities.
f) Action – It is based on the decision made by intelligence. This action can be manual
as well as automatic.
g) Communication – All the devices are well connected so that the communication
between the devices can take place to exchange the data [9].
Figure 1 Characteristics of IOT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IOT Devices:
Amazon Dash Button – It is the collection of buttons that directly order some
commonly used household products from Amazon.com.
August Doorbell Cam – Using this device, you can converse with people at your door
just using your smartphone.
Amazon Echo – This is a speaker that can listen to the users and respond to their
commands. Example: Play music, Answer the call, order the pizza etc. [6]
Amazon Dash Button – It is the collection of buttons that directly order some
commonly used household products from Amazon.com.
August Doorbell Cam – Using this device, you can converse with people at your door
just using your smartphone.
Amazon Echo – This is a speaker that can listen to the users and respond to their
commands. Example: Play music, Answer the call, order the pizza etc. [6]
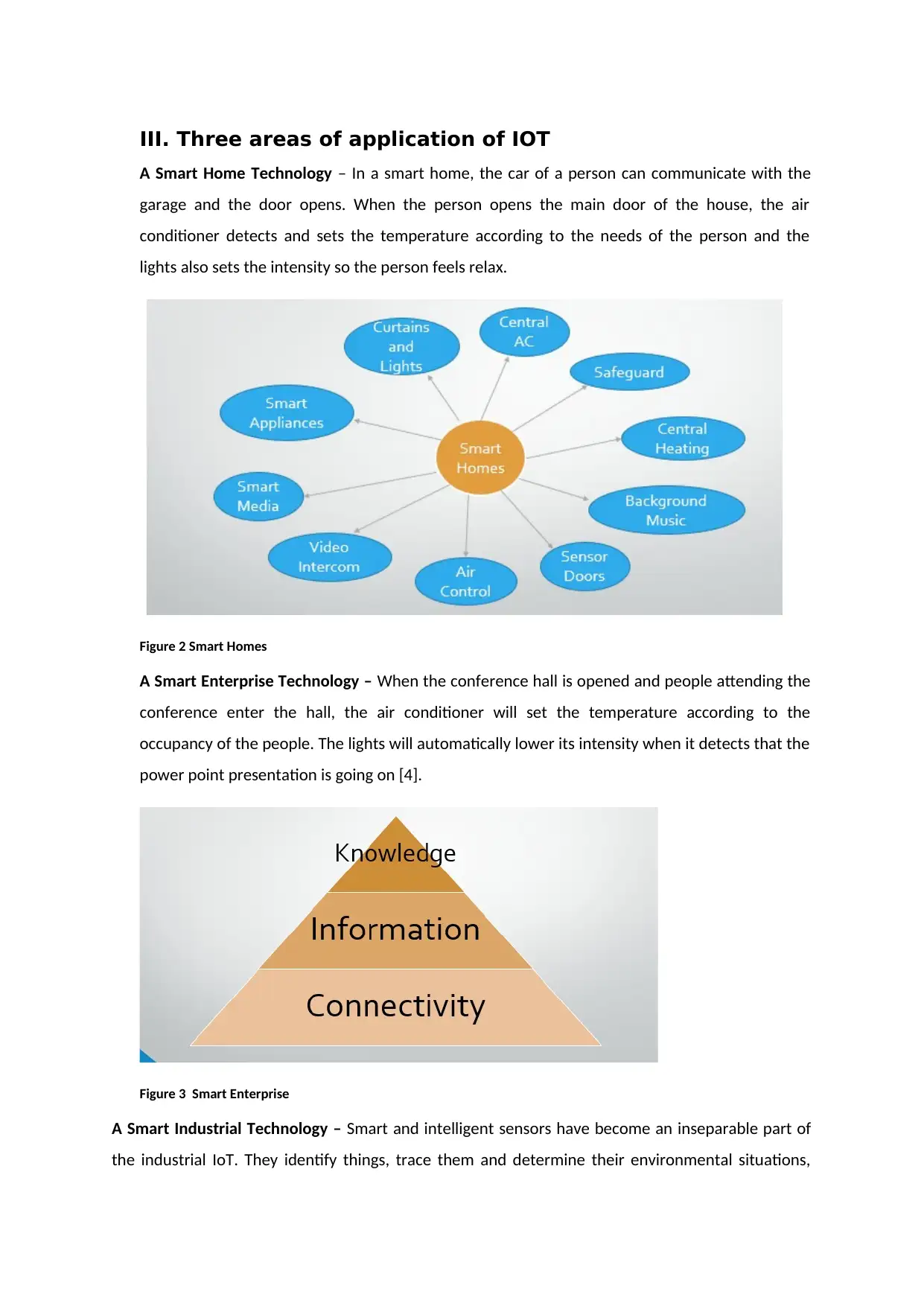
III. Three areas of application of IOT
A Smart Home Technology – In a smart home, the car of a person can communicate with the
garage and the door opens. When the person opens the main door of the house, the air
conditioner detects and sets the temperature according to the needs of the person and the
lights also sets the intensity so the person feels relax.
Figure 2 Smart Homes
A Smart Enterprise Technology – When the conference hall is opened and people attending the
conference enter the hall, the air conditioner will set the temperature according to the
occupancy of the people. The lights will automatically lower its intensity when it detects that the
power point presentation is going on [4].
Figure 3 Smart Enterprise
A Smart Industrial Technology – Smart and intelligent sensors have become an inseparable part of
the industrial IoT. They identify things, trace them and determine their environmental situations,
A Smart Home Technology – In a smart home, the car of a person can communicate with the
garage and the door opens. When the person opens the main door of the house, the air
conditioner detects and sets the temperature according to the needs of the person and the
lights also sets the intensity so the person feels relax.
Figure 2 Smart Homes
A Smart Enterprise Technology – When the conference hall is opened and people attending the
conference enter the hall, the air conditioner will set the temperature according to the
occupancy of the people. The lights will automatically lower its intensity when it detects that the
power point presentation is going on [4].
Figure 3 Smart Enterprise
A Smart Industrial Technology – Smart and intelligent sensors have become an inseparable part of
the industrial IoT. They identify things, trace them and determine their environmental situations,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
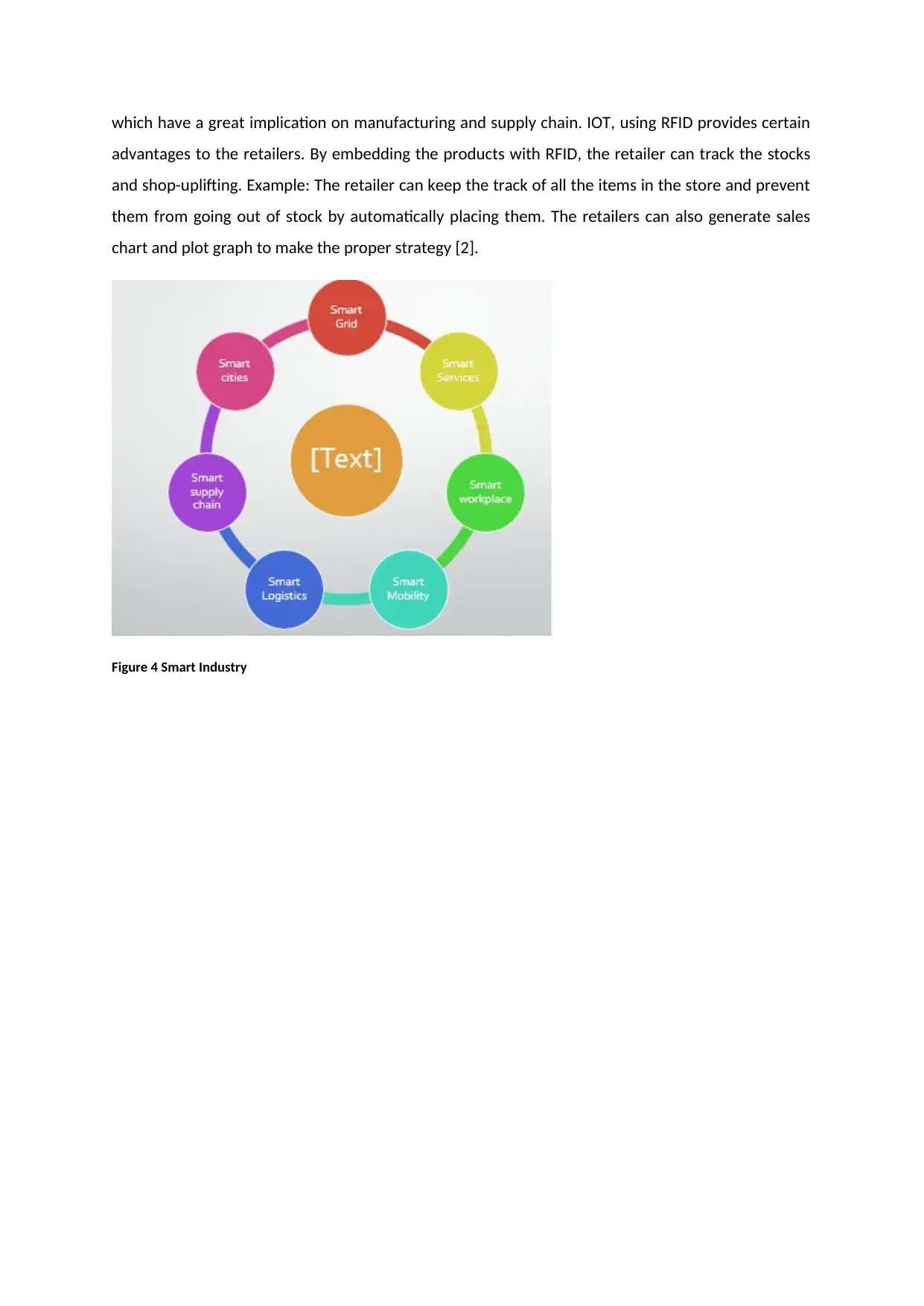
which have a great implication on manufacturing and supply chain. IOT, using RFID provides certain
advantages to the retailers. By embedding the products with RFID, the retailer can track the stocks
and shop-uplifting. Example: The retailer can keep the track of all the items in the store and prevent
them from going out of stock by automatically placing them. The retailers can also generate sales
chart and plot graph to make the proper strategy [2].
Figure 4 Smart Industry
advantages to the retailers. By embedding the products with RFID, the retailer can track the stocks
and shop-uplifting. Example: The retailer can keep the track of all the items in the store and prevent
them from going out of stock by automatically placing them. The retailers can also generate sales
chart and plot graph to make the proper strategy [2].
Figure 4 Smart Industry
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. Analyse critically, three current and future security
issues in IOT and its countermeasures.
I. Analyse three security issues in IOT
IOT is implemented to make our lives easier but it needs proper security as it makes
everything and person locatable. IoT have a durable infrastructure of security. Some of the
security issues in IOT are:
Unauthorized Access to RFID – It makes the objects uniquely identifiable. Its small size and
low cost make it a perfect platform to integrate with any object. It is a trans-receiver
microchip which is very similar to an adhesive sticker. These are of two types: Active and
Passive. Whether they are active or passive depends upon the application type that are
using. Active tags contain a battery which is attached to them because it required always
active whereas the passive tags to covert in active tags when it required triggered. One of
the major issues of IOT is unauthorized access to active and passive tags which can leak any
confidential information about a user. These tags cannot be only read but can also be
damaged & modified. Some threats are given as RFID Virus, Side Channel Attack and Speed
Pass hack [9].
Sensor Node security Breach – Wireless sensor networks (WSNs) are highly exposed to
many attack types because of sensor nodes which are the part of bi-directional network
sensor. Other than just trans-mission of data, achieve the data which is also possible. Some
of the attacks on sensor nodes are:
a) Jamming – Jamming blocks the whole network by disturbing the frequencies of the
sensor nodes [8].
b) Tampering – In this kind of attack, data of node could be easily read or modified by the
intruder to generate the controllable node.
c) Sybil – It rights to take multiple pseudonymous identities to the nodes that are giving
big influence.
d) Flooding – It is a kind of DOS attack, which is caused by a large amount of traffic. It
results in memory exhaustion.
Cloud Computing Abuse – It is a huge network of servers which share data between one
another. The resources shared between these servers can face a lot of attacks like Man in
the Middle Attack. These cloud platforms require very tight security. Some possible threats
to cloud platform are:
issues in IOT and its countermeasures.
I. Analyse three security issues in IOT
IOT is implemented to make our lives easier but it needs proper security as it makes
everything and person locatable. IoT have a durable infrastructure of security. Some of the
security issues in IOT are:
Unauthorized Access to RFID – It makes the objects uniquely identifiable. Its small size and
low cost make it a perfect platform to integrate with any object. It is a trans-receiver
microchip which is very similar to an adhesive sticker. These are of two types: Active and
Passive. Whether they are active or passive depends upon the application type that are
using. Active tags contain a battery which is attached to them because it required always
active whereas the passive tags to covert in active tags when it required triggered. One of
the major issues of IOT is unauthorized access to active and passive tags which can leak any
confidential information about a user. These tags cannot be only read but can also be
damaged & modified. Some threats are given as RFID Virus, Side Channel Attack and Speed
Pass hack [9].
Sensor Node security Breach – Wireless sensor networks (WSNs) are highly exposed to
many attack types because of sensor nodes which are the part of bi-directional network
sensor. Other than just trans-mission of data, achieve the data which is also possible. Some
of the attacks on sensor nodes are:
a) Jamming – Jamming blocks the whole network by disturbing the frequencies of the
sensor nodes [8].
b) Tampering – In this kind of attack, data of node could be easily read or modified by the
intruder to generate the controllable node.
c) Sybil – It rights to take multiple pseudonymous identities to the nodes that are giving
big influence.
d) Flooding – It is a kind of DOS attack, which is caused by a large amount of traffic. It
results in memory exhaustion.
Cloud Computing Abuse – It is a huge network of servers which share data between one
another. The resources shared between these servers can face a lot of attacks like Man in
the Middle Attack. These cloud platforms require very tight security. Some possible threats
to cloud platform are:

a) Malicious Insider – In this threat, some person from the inside of the network is
involved in manipulating the data.
b) Data Loss -In this kind of attack, any unauthorized customer who can delete or alter the
exist data.
c) Man in the Middle Attack – It is a kind of Hijacked Account in which the hacker can
alter or divert the messages which are exchanged between two events.
d) Cloud Computing – The attacks on a cloud platform can be used in monstrous ways. In
this kind of attack, the intruder can upload malicious software on the server like botnet
[5].
involved in manipulating the data.
b) Data Loss -In this kind of attack, any unauthorized customer who can delete or alter the
exist data.
c) Man in the Middle Attack – It is a kind of Hijacked Account in which the hacker can
alter or divert the messages which are exchanged between two events.
d) Cloud Computing – The attacks on a cloud platform can be used in monstrous ways. In
this kind of attack, the intruder can upload malicious software on the server like botnet
[5].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

II. Countermeasures and Mitigation techniques and tools
used for security issues
1. Insecure Web Interface: The web interface allows a user to interact with the device. Any
unauthorized access can cause harm to the data interchanged. The issues related to web
interface are Account Enumeration, SQL-injection, Cross-site Scripting etc. The
countermeasures for these issues are:
Password recovery mechanism should be robust.
Not allowing the weak passwords.
Ensuring the change of default password [4].
Making sure that the credentials are never exposed to anyone.
2. Insufficient Authorization: It includes ineffective mechanisms to authenticate the IOT
interface and poor authorization technique which can lead to higher access to some people
than needed. The countermeasures to avoid these issues are:
Sensitive features require re-authentication
Password recovery mechanisms must be secure.
Granular Access Control is in place
Always generating a strong password.
3. Insecure Network Services: It relates to the vulnerabilities in the network which connects
IOT devices. These might get exposed to intruders and leakage of data is possible. It includes
threats like Buffer Flow and Dos.
To overcome these issues the countermeasures are;
Making only necessary ports available and that ports are not exposed to DoS attacks.
Ensuring that services are protected from buffer flow and fuzzing attacks.
4. Lack of Encrypting Techniques: This deals with the exchange of data with an IoT device in an
unencrypted form. Security vulnerabilities that can lead to these issues are poorly
implemented SSL and exchange of unencrypted data via internet or local network.
Countermeasures to mitigate such issues are:
Data should be encrypted using protocols such as SSL/TLS.
Ensuring that data encryption standard techniques are used to protect data while
SSL and TLS are not available [5].
5. Privacy Concerns: It means a collection of personal data without any security measures to
protect this data. Automated tools can look up for certain patterns of personal data.
Countermeasures to avoid this issue are:
Collecting only critical data that is used by the function
used for security issues
1. Insecure Web Interface: The web interface allows a user to interact with the device. Any
unauthorized access can cause harm to the data interchanged. The issues related to web
interface are Account Enumeration, SQL-injection, Cross-site Scripting etc. The
countermeasures for these issues are:
Password recovery mechanism should be robust.
Not allowing the weak passwords.
Ensuring the change of default password [4].
Making sure that the credentials are never exposed to anyone.
2. Insufficient Authorization: It includes ineffective mechanisms to authenticate the IOT
interface and poor authorization technique which can lead to higher access to some people
than needed. The countermeasures to avoid these issues are:
Sensitive features require re-authentication
Password recovery mechanisms must be secure.
Granular Access Control is in place
Always generating a strong password.
3. Insecure Network Services: It relates to the vulnerabilities in the network which connects
IOT devices. These might get exposed to intruders and leakage of data is possible. It includes
threats like Buffer Flow and Dos.
To overcome these issues the countermeasures are;
Making only necessary ports available and that ports are not exposed to DoS attacks.
Ensuring that services are protected from buffer flow and fuzzing attacks.
4. Lack of Encrypting Techniques: This deals with the exchange of data with an IoT device in an
unencrypted form. Security vulnerabilities that can lead to these issues are poorly
implemented SSL and exchange of unencrypted data via internet or local network.
Countermeasures to mitigate such issues are:
Data should be encrypted using protocols such as SSL/TLS.
Ensuring that data encryption standard techniques are used to protect data while
SSL and TLS are not available [5].
5. Privacy Concerns: It means a collection of personal data without any security measures to
protect this data. Automated tools can look up for certain patterns of personal data.
Countermeasures to avoid this issue are:
Collecting only critical data that is used by the function
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The data that is collected is of less sensitive nature
The data collected should be properly encrypted.
Only authorized people have access to this collected data [1].
The data collected should be properly encrypted.
Only authorized people have access to this collected data [1].

References
[1] Abbasi, Bushra Zaheer, and Munam Ali Shah. "Fog computing: Security issues, solutions, and
robust practices." Automation and Computing (ICAC), 2017 23rd International Conference
on. IEEE, (2017).
[2] Bazm, Mohammad-Mahdi, et al. "Side Channels in the Cloud: Isolation Challenges, Attacks,
and Countermeasures." (2017).
[3] Cai, Hongming, et al. "IoT-based big data storage systems in cloud computing: perspectives
and challenges." IEEE Internet of Things Journal 4.1 (2017): 75-87.
[4] Kalkan, Kubra, and Sherali Zeadally. "Securing Internet of Things (IoT) with Software Defined
Networking (SDN)." IEEE Communications Magazine (2017).
[5] Kelly, Sean Dieter Tebje, Nagender Kumar Suryadevara, and Subhas Chandra
Mukhopadhyay. "Towards the implementation of IoT for environmental condition
monitoring in homes." IEEE Sensors Journal 13.10 (2013): 3846-3853.
[6] Kim, Jun Young, et al. "Automated Analysis of Secure Internet of Things
Protocols." Proceedings of the 33rd Annual Computer Security Applications Conference. ACM,
(2017).
[7] Mai, Xuan Phu, et al. "Modeling Security and Privacy Requirements: a Use Case-Driven
Approach." Information and Software Technology (2018).
[8] Sadeghi, Abbas, et al. "Vulnerability and Security Risk Assessment of a Thermal Power Plant
Using SVA Technique." Journal of Integrated Security Science 1.1 (2017).
[9] Sindre, Guttorm, and Andreas L. Opdahl. "Eliciting security requirements with misuse
cases." Requirements engineering10.1 (2005): 34-44.
[1] Abbasi, Bushra Zaheer, and Munam Ali Shah. "Fog computing: Security issues, solutions, and
robust practices." Automation and Computing (ICAC), 2017 23rd International Conference
on. IEEE, (2017).
[2] Bazm, Mohammad-Mahdi, et al. "Side Channels in the Cloud: Isolation Challenges, Attacks,
and Countermeasures." (2017).
[3] Cai, Hongming, et al. "IoT-based big data storage systems in cloud computing: perspectives
and challenges." IEEE Internet of Things Journal 4.1 (2017): 75-87.
[4] Kalkan, Kubra, and Sherali Zeadally. "Securing Internet of Things (IoT) with Software Defined
Networking (SDN)." IEEE Communications Magazine (2017).
[5] Kelly, Sean Dieter Tebje, Nagender Kumar Suryadevara, and Subhas Chandra
Mukhopadhyay. "Towards the implementation of IoT for environmental condition
monitoring in homes." IEEE Sensors Journal 13.10 (2013): 3846-3853.
[6] Kim, Jun Young, et al. "Automated Analysis of Secure Internet of Things
Protocols." Proceedings of the 33rd Annual Computer Security Applications Conference. ACM,
(2017).
[7] Mai, Xuan Phu, et al. "Modeling Security and Privacy Requirements: a Use Case-Driven
Approach." Information and Software Technology (2018).
[8] Sadeghi, Abbas, et al. "Vulnerability and Security Risk Assessment of a Thermal Power Plant
Using SVA Technique." Journal of Integrated Security Science 1.1 (2017).
[9] Sindre, Guttorm, and Andreas L. Opdahl. "Eliciting security requirements with misuse
cases." Requirements engineering10.1 (2005): 34-44.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

