Metadata in Law Enforcement: Collection, Law, and Ethical Concerns
VerifiedAdded on 2023/06/15
|10
|1419
|388
Report
AI Summary
This report explores the increasing importance of metadata in managing information resources, particularly within law enforcement. It classifies metadata types according to NISO standards, detailing descriptive, administrative, structural, and rights management metadata. The report examines the use of metadata in everyday applications like email and web pages, and delves into the legal landscape in the US, focusing on call tapping and potential violations of freedom. Ethical considerations surrounding metadata preservation and privacy risks are also discussed. The report concludes by emphasizing the necessity of a robust metadata system for organized data management, while acknowledging the privacy threats posed by third-party metadata storage, and highlights technologies that weaken metadata collection.

Running head: METADATA
METADATA
Name of the Student
Name of the University
Author Note
METADATA
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1METADATA
Executive Summary
The rapid development of World Wide Web gives huge possibility to access information
always and everywhere. Metadata get more and more important tool in the process of describing
and managing information resources. The researchers discuss the standards connecting to
describing of metadata. Everyone agrees that if anyone wants to manage information than
metadata is the key for it. In this report, the classification of metadata has been discussed with
the law enforcement to collect and protect this type of data.
Executive Summary
The rapid development of World Wide Web gives huge possibility to access information
always and everywhere. Metadata get more and more important tool in the process of describing
and managing information resources. The researchers discuss the standards connecting to
describing of metadata. Everyone agrees that if anyone wants to manage information than
metadata is the key for it. In this report, the classification of metadata has been discussed with
the law enforcement to collect and protect this type of data.

2METADATA
Table of Contents
Introduction......................................................................................................................................3
Classification...................................................................................................................................3
Transportation of metadata in daily life...........................................................................................4
Email............................................................................................................................................4
Web pages....................................................................................................................................5
Law regarding Metadata in US........................................................................................................6
Tapping the calls..........................................................................................................................6
Violation of freedom....................................................................................................................7
Ethical issues...................................................................................................................................7
Conclusion.......................................................................................................................................7
References........................................................................................................................................9
Table of Contents
Introduction......................................................................................................................................3
Classification...................................................................................................................................3
Transportation of metadata in daily life...........................................................................................4
Email............................................................................................................................................4
Web pages....................................................................................................................................5
Law regarding Metadata in US........................................................................................................6
Tapping the calls..........................................................................................................................6
Violation of freedom....................................................................................................................7
Ethical issues...................................................................................................................................7
Conclusion.......................................................................................................................................7
References........................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3METADATA
Introduction
Metadata is a type of data that stores information about other data whether that data is
web pages, video, photography, spreadsheets or content. Metadata give a précis of basic
information about data such as data created, author, file size and data modified of any document.
It can be easier for someone to locate specific files by having the ability to filter through
metadata. Metadata can be created by automated information processing or manually to include
relevant information about specific data. It has been getting very important to implement
metadata in every structured or unstructured data in information technology.
Classification
There generally three types of metadata according to National Information Standards
Organization (NISO).
Descriptive Metadata – it traces a resource for the purpose such as identification and
discovery. It also provides resources after discovering content such as abstract,
keywords and author. This type of metadata drives the ability to search, sort, browse and
filter information.
Administrative metadata – it gives information to deal with a resource such as content
creation time, creation process, type, technical information and accessing privacy.
Rights Management Metadata – it deals with rights, reproduction or other
access requirements, persistent identifiers and methodology.
Preservation Metadata – it holds information required to archive and
protects a resource.
Introduction
Metadata is a type of data that stores information about other data whether that data is
web pages, video, photography, spreadsheets or content. Metadata give a précis of basic
information about data such as data created, author, file size and data modified of any document.
It can be easier for someone to locate specific files by having the ability to filter through
metadata. Metadata can be created by automated information processing or manually to include
relevant information about specific data. It has been getting very important to implement
metadata in every structured or unstructured data in information technology.
Classification
There generally three types of metadata according to National Information Standards
Organization (NISO).
Descriptive Metadata – it traces a resource for the purpose such as identification and
discovery. It also provides resources after discovering content such as abstract,
keywords and author. This type of metadata drives the ability to search, sort, browse and
filter information.
Administrative metadata – it gives information to deal with a resource such as content
creation time, creation process, type, technical information and accessing privacy.
Rights Management Metadata – it deals with rights, reproduction or other
access requirements, persistent identifiers and methodology.
Preservation Metadata – it holds information required to archive and
protects a resource.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4METADATA
Structural metadata – it specifies the intellectual or physical rudiments of a digital contet
such as size, file format, media. It also explains the content’s component and their
relationship as pages, chapters and table of content.
Transportation of metadata in daily life
Email
Figure 1: Metadata in E-mail.
Source: ( Ding et al., 2014)
Every email has several metadata fields concealed in the message heading that is invisible to
mail user. This metadata contains:
Time and Date sent or received.
Subject.
Sender and receiver server name and IP.
Format (text or HTML).
Anti spam software detail.
Structural metadata – it specifies the intellectual or physical rudiments of a digital contet
such as size, file format, media. It also explains the content’s component and their
relationship as pages, chapters and table of content.
Transportation of metadata in daily life
Figure 1: Metadata in E-mail.
Source: ( Ding et al., 2014)
Every email has several metadata fields concealed in the message heading that is invisible to
mail user. This metadata contains:
Time and Date sent or received.
Subject.
Sender and receiver server name and IP.
Format (text or HTML).
Anti spam software detail.
5METADATA
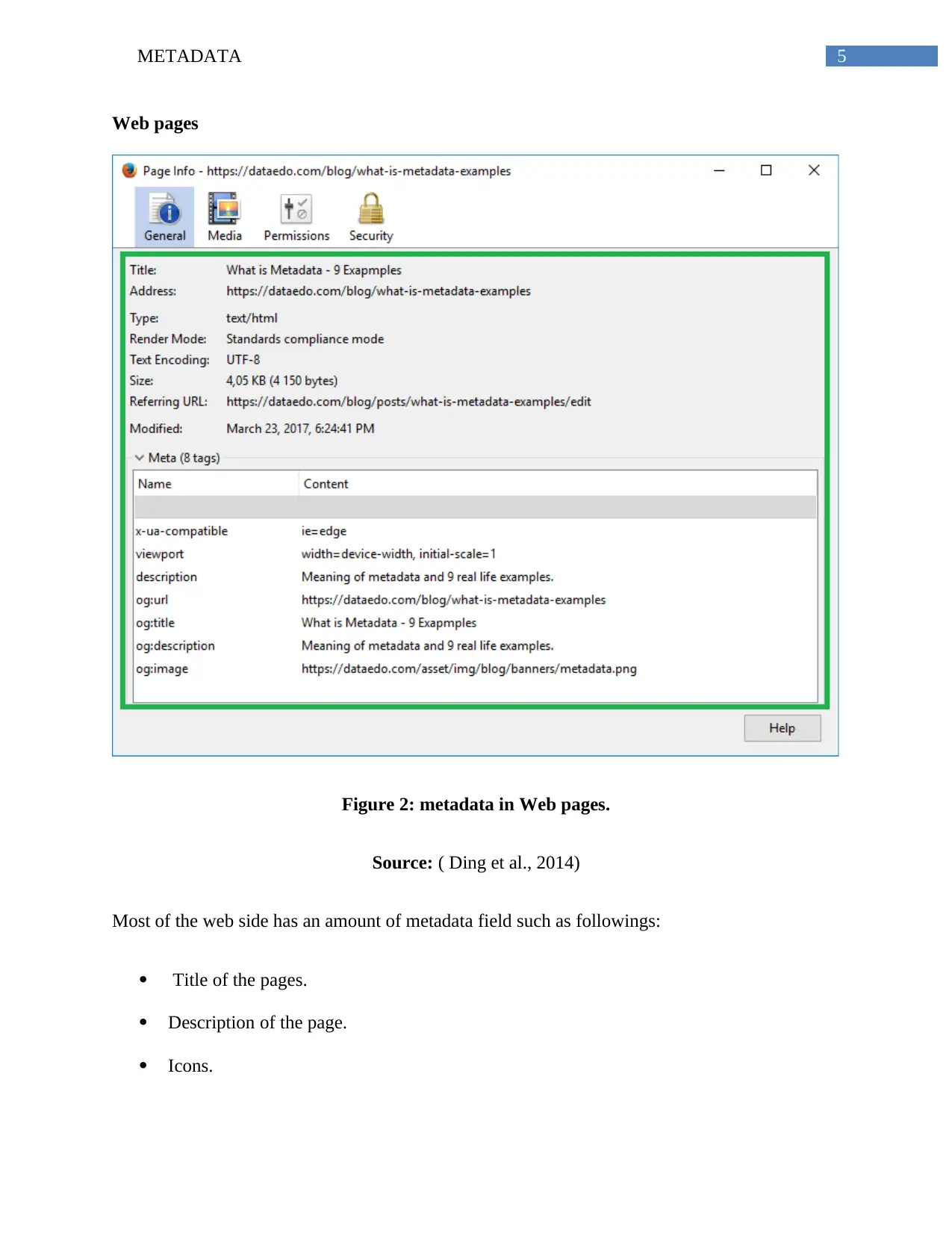
Web pages
Figure 2: metadata in Web pages.
Source: ( Ding et al., 2014)
Most of the web side has an amount of metadata field such as followings:
Title of the pages.
Description of the page.
Icons.
Web pages
Figure 2: metadata in Web pages.
Source: ( Ding et al., 2014)
Most of the web side has an amount of metadata field such as followings:
Title of the pages.
Description of the page.
Icons.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6METADATA
Law regarding Metadata in US
According to the Guardian under Obama management, the phone call records of citizens
in the United States are being stored in bulk despite suspicion of any crime. The Foreign
Intelligence Surveillance Court (FISC) approved the proposal of FBI on April 25 giving the
administration limitless power to gain data of call duration and location data (Ramaswamy &
Feininger, 2017). The order itself does not give the permission to store content of messages or
the private data of any particular Phone though NSA can easily build a comprehensive picture of
communication details such as location, receiver identification and the time by collecting
metadata. To avoid terrorist attack as 9/11 NSA may need encrypted data of all citizens.
Metadata can be stored as data about location of a phone call or email and the time of activity
(Ball, 2018).
Tapping the calls
The NSA has access to metadata over fiber-optic cable with help of secure intelligence
allies such as Britain’s Government Communications Headquarters (Prahlad et al.,
2017).According to the Snowden document Prism is the biggest single supplier of NSA to
collect intellect information. Apple, FaceBook, Google, Yahoo and other internet giants are the
source to collect metadata for this type of downstream program.
NSA main objective is to help America and its ally’s countries around the world though
they snoop on user activity. NSA presumes critical data to American and allied services in other
countries, protecting the countries against cyber attacks (Ball, 2018).
Law regarding Metadata in US
According to the Guardian under Obama management, the phone call records of citizens
in the United States are being stored in bulk despite suspicion of any crime. The Foreign
Intelligence Surveillance Court (FISC) approved the proposal of FBI on April 25 giving the
administration limitless power to gain data of call duration and location data (Ramaswamy &
Feininger, 2017). The order itself does not give the permission to store content of messages or
the private data of any particular Phone though NSA can easily build a comprehensive picture of
communication details such as location, receiver identification and the time by collecting
metadata. To avoid terrorist attack as 9/11 NSA may need encrypted data of all citizens.
Metadata can be stored as data about location of a phone call or email and the time of activity
(Ball, 2018).
Tapping the calls
The NSA has access to metadata over fiber-optic cable with help of secure intelligence
allies such as Britain’s Government Communications Headquarters (Prahlad et al.,
2017).According to the Snowden document Prism is the biggest single supplier of NSA to
collect intellect information. Apple, FaceBook, Google, Yahoo and other internet giants are the
source to collect metadata for this type of downstream program.
NSA main objective is to help America and its ally’s countries around the world though
they snoop on user activity. NSA presumes critical data to American and allied services in other
countries, protecting the countries against cyber attacks (Ball, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7METADATA
Violation of freedom
Only in 2016, national security Agency stores approximately 151 million records of
American’s massages and phone calls despite the approval of USA Freedom Act, which aim to
curb bulk surveillance. It could lead to loss of data privacy but according to Reuters 151 million
records was nothing to compare to the scope of US surveillance. However, many privacy
advocates will be angered for the collection of huge number of data.
Ethical issues
Metadata preservation can elevate complicate ethical issues in term of privacy. The
assumption that Metadata offers a lower risk of violating privacy compared to primary data is
misguided. Satisfactory amount of metadata provides equal opportunities to generate persistent
information about citizens. Assume a mobile carrier’s dataset that have details about date, time
and receiver identity. From these data, someone’s behaviors and activity can be traceable. The
results from accessing metadata can work as similar as accessing primary data like tapping calls.
Privacy is a fundamental human value. Technologies such as Virtual Proxy Network
(VPN), anonymity networks and encrypted communication platforms have been implement as
ways to weaken metadata collection by hiding aspects of communications.
Conclusion
In this report, an attempt is made to find and understand the concepts on which the
metadata standards are based. These concepts include two kinds of objects information sources
or creations, and metadata used in networked surroundings. Metadata has been stored to the third
Violation of freedom
Only in 2016, national security Agency stores approximately 151 million records of
American’s massages and phone calls despite the approval of USA Freedom Act, which aim to
curb bulk surveillance. It could lead to loss of data privacy but according to Reuters 151 million
records was nothing to compare to the scope of US surveillance. However, many privacy
advocates will be angered for the collection of huge number of data.
Ethical issues
Metadata preservation can elevate complicate ethical issues in term of privacy. The
assumption that Metadata offers a lower risk of violating privacy compared to primary data is
misguided. Satisfactory amount of metadata provides equal opportunities to generate persistent
information about citizens. Assume a mobile carrier’s dataset that have details about date, time
and receiver identity. From these data, someone’s behaviors and activity can be traceable. The
results from accessing metadata can work as similar as accessing primary data like tapping calls.
Privacy is a fundamental human value. Technologies such as Virtual Proxy Network
(VPN), anonymity networks and encrypted communication platforms have been implement as
ways to weaken metadata collection by hiding aspects of communications.
Conclusion
In this report, an attempt is made to find and understand the concepts on which the
metadata standards are based. These concepts include two kinds of objects information sources
or creations, and metadata used in networked surroundings. Metadata has been stored to the third

8METADATA
party most of the time without users concern could lead to serious threat. A strong metadata
system will present context for a particular information item can be serving as the spine for well-
organized data management and developed the analysis, use and management of any body of
data. The result will be enhanced utility, comparability and accuracy of secondary and
elementary education data at state, local, and national levels.
party most of the time without users concern could lead to serious threat. A strong metadata
system will present context for a particular information item can be serving as the spine for well-
organized data management and developed the analysis, use and management of any body of
data. The result will be enhanced utility, comparability and accuracy of secondary and
elementary education data at state, local, and national levels.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9METADATA
References
Ball, J. (2018). NSA stores metadata of millions of web users for up to a year, secret files show.
[online]the Guardian. Available at: https://www.theguardian.com/world/2013/sep/30/nsa-
americans-metadata-year-documents [Accessed 6 Feb. 2018].
Ding, L., Finin, T., Joshi, A., Pan, R., Cost, R. S., Peng, Y., ... & Sachs, J. (2014, November).
Swoogle: a search and metadata engine for the semantic web. In Proceedings of the
thirteenth ACM international conference on Information and knowledge
management (pp. 652-659). ACM.
Prahlad, A., Schwartz, J. A., Ngo, D., Brockway, B., & Muller, M. S. (2017). U.S. Patent No.
9,606,994. Washington, DC: U.S. Patent and Trademark Office.
Ramaswamy, A., & Feininger, W. A. (2017). U.S. Patent No. 9,609,034. Washington, DC: U.S.
Patent and Trademark Office. Ramaswamy, A., & Feininger, W. A. (2017). U.S. Patent
No. 9,609,034. Washington, DC: U.S. Patent and Trademark Office.
References
Ball, J. (2018). NSA stores metadata of millions of web users for up to a year, secret files show.
[online]the Guardian. Available at: https://www.theguardian.com/world/2013/sep/30/nsa-
americans-metadata-year-documents [Accessed 6 Feb. 2018].
Ding, L., Finin, T., Joshi, A., Pan, R., Cost, R. S., Peng, Y., ... & Sachs, J. (2014, November).
Swoogle: a search and metadata engine for the semantic web. In Proceedings of the
thirteenth ACM international conference on Information and knowledge
management (pp. 652-659). ACM.
Prahlad, A., Schwartz, J. A., Ngo, D., Brockway, B., & Muller, M. S. (2017). U.S. Patent No.
9,606,994. Washington, DC: U.S. Patent and Trademark Office.
Ramaswamy, A., & Feininger, W. A. (2017). U.S. Patent No. 9,609,034. Washington, DC: U.S.
Patent and Trademark Office. Ramaswamy, A., & Feininger, W. A. (2017). U.S. Patent
No. 9,609,034. Washington, DC: U.S. Patent and Trademark Office.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

