Digital Forensics Case Study Report: Analysis of Financial Fraud Case
VerifiedAdded on 2023/01/16
|23
|3253
|98
Report
AI Summary
This report details a digital forensics case study focused on a financial fraud investigation. The study utilizes forensic tools like EnCase, Autopsy, and TrID to analyze a suspect's computer system. The investigation involves keyword searches, timeline analysis, and signature analysis to uncover evidence of communication and potential wrongdoing. The case revolves around a company employee, Monika, suspected of offering proprietary information to a competitor. The report outlines the steps taken to acquire and analyze the evidence, including the use of various software to image the hard drive, recover deleted files, and examine email communications. Findings include temporary internet files containing incriminating messages and emails exchanged between the suspect and a competitor. The report provides a detailed account of the investigation process, methodologies and tools used in the digital forensic analysis, and the evidence uncovered. The student has provided this report to Desklib for educational purposes, a platform which offers AI based study tools and resources for students.
4-10-2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Abstract................................................................................................................................1
Introduction..........................................................................................................................1
Case Study Summary...........................................................................................................2
Computer and Forensic Tool Statistics................................................................................2
Investigation........................................................................................................................2
Conclusion and Future Work.............................................................................................21
Abstract
This report conducted during the assignment. The assignment we will work on a case
study, we will work digital case study software, that help gather evidence and deliver
facts .Any questions or concerns pertaining to the acquisition of the evidence can be
found in his/her report.
Introduction
In this project we will work on forensic tools . These tools are Autospy and TrID for
case analysis. In this report we work on case study of a company financial fraud The
report kicks off with a brief description of what this technique of digital forensics is all
about and why is it required in modern data-centric and digital era. Further, it other
evidences could be used to inspect and examine a reported wrongdoing.
Abstract................................................................................................................................1
Introduction..........................................................................................................................1
Case Study Summary...........................................................................................................2
Computer and Forensic Tool Statistics................................................................................2
Investigation........................................................................................................................2
Conclusion and Future Work.............................................................................................21
Abstract
This report conducted during the assignment. The assignment we will work on a case
study, we will work digital case study software, that help gather evidence and deliver
facts .Any questions or concerns pertaining to the acquisition of the evidence can be
found in his/her report.
Introduction
In this project we will work on forensic tools . These tools are Autospy and TrID for
case analysis. In this report we work on case study of a company financial fraud The
report kicks off with a brief description of what this technique of digital forensics is all
about and why is it required in modern data-centric and digital era. Further, it other
evidences could be used to inspect and examine a reported wrongdoing.

Case Study Summary
Mcme Industries’ Monika is being investigated under the fear that he may be offering
proprietary company information to a competitor in exchange for a job.
Computer and Forensic Tool Statistics
The computer was removed from its position in MCME Industries at 4/4/19 9:29:03 PM
where it was carted out to a nearby secure forensics facility. Once settled at the forensics
lab the hard drive was imaged to begin the research and testing. The image of the hard
drive was tested using the program EnCase Forensic Edition Version 4.17b by Guidance
Software. This program has been proven in the court of law to provide valid and accurate
results when scanning and analyzing a system. We use TrID and autopsy software for
forensic digital analysis
Investigation
The following was the procedure that I took to extract what data I found to be relevant to
the case.
I created a new case called Case Study. I added to this case the already captured image
file (C:\forensicsfile\winlabencase.image) by going to File Add Device, clicking
sessions, and clicking on add evidence file.
With the case loaded I immediately set the time zone by right clicking on the image
Modify Time Zone. From the following screen I selected the time zone that I was
working in. This is done to adjust the evidence to all correlate in the same time zone.
Mcme Industries’ Monika is being investigated under the fear that he may be offering
proprietary company information to a competitor in exchange for a job.
Computer and Forensic Tool Statistics
The computer was removed from its position in MCME Industries at 4/4/19 9:29:03 PM
where it was carted out to a nearby secure forensics facility. Once settled at the forensics
lab the hard drive was imaged to begin the research and testing. The image of the hard
drive was tested using the program EnCase Forensic Edition Version 4.17b by Guidance
Software. This program has been proven in the court of law to provide valid and accurate
results when scanning and analyzing a system. We use TrID and autopsy software for
forensic digital analysis
Investigation
The following was the procedure that I took to extract what data I found to be relevant to
the case.
I created a new case called Case Study. I added to this case the already captured image
file (C:\forensicsfile\winlabencase.image) by going to File Add Device, clicking
sessions, and clicking on add evidence file.
With the case loaded I immediately set the time zone by right clicking on the image
Modify Time Zone. From the following screen I selected the time zone that I was
working in. This is done to adjust the evidence to all correlate in the same time zone.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The next step was to recover any hidden or deleted folders on the system. Doing this step
now would allow my searches to be more complete in the future and determine if there
were any actions taken to hide or destroy evidence. In order to do this I right clicked on
the image Recover Folders.
I ran a script next to determine the specifications about the computer because I had not
been the one to create the image from the suspect machine. The script comes preloaded
into EnCase V4. I went to View Scripts and selected the Initialize Case script which
prompted me to enter information of the investigator and person conducting the
examination. Once the information was entered the script asks where I would like the
data saved. I chose to add it to the bookmark section under the folder Encase Computer
Analysis Report. I also needed to check which information I would want present. I
chose to display the Windows version and registration, time zone settings, network
information, user information, and last shutdown time. The report generated can be
found on the following page. The important information pulled from the report is that the
machine is running a FAT16 file system with Windows 10. The total capacity of the
partition is only 22MB. Now that this information has been discovered I can begin my
investigation. For this case study we use Autopsy software . The autopsy software uses
two images for compare ; these are store before and after case study. The step are given
bellow
Autopsy software is provide gui interface .
Data Carving techniques.
now would allow my searches to be more complete in the future and determine if there
were any actions taken to hide or destroy evidence. In order to do this I right clicked on
the image Recover Folders.
I ran a script next to determine the specifications about the computer because I had not
been the one to create the image from the suspect machine. The script comes preloaded
into EnCase V4. I went to View Scripts and selected the Initialize Case script which
prompted me to enter information of the investigator and person conducting the
examination. Once the information was entered the script asks where I would like the
data saved. I chose to add it to the bookmark section under the folder Encase Computer
Analysis Report. I also needed to check which information I would want present. I
chose to display the Windows version and registration, time zone settings, network
information, user information, and last shutdown time. The report generated can be
found on the following page. The important information pulled from the report is that the
machine is running a FAT16 file system with Windows 10. The total capacity of the
partition is only 22MB. Now that this information has been discovered I can begin my
investigation. For this case study we use Autopsy software . The autopsy software uses
two images for compare ; these are store before and after case study. The step are given
bellow
Autopsy software is provide gui interface .
Data Carving techniques.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
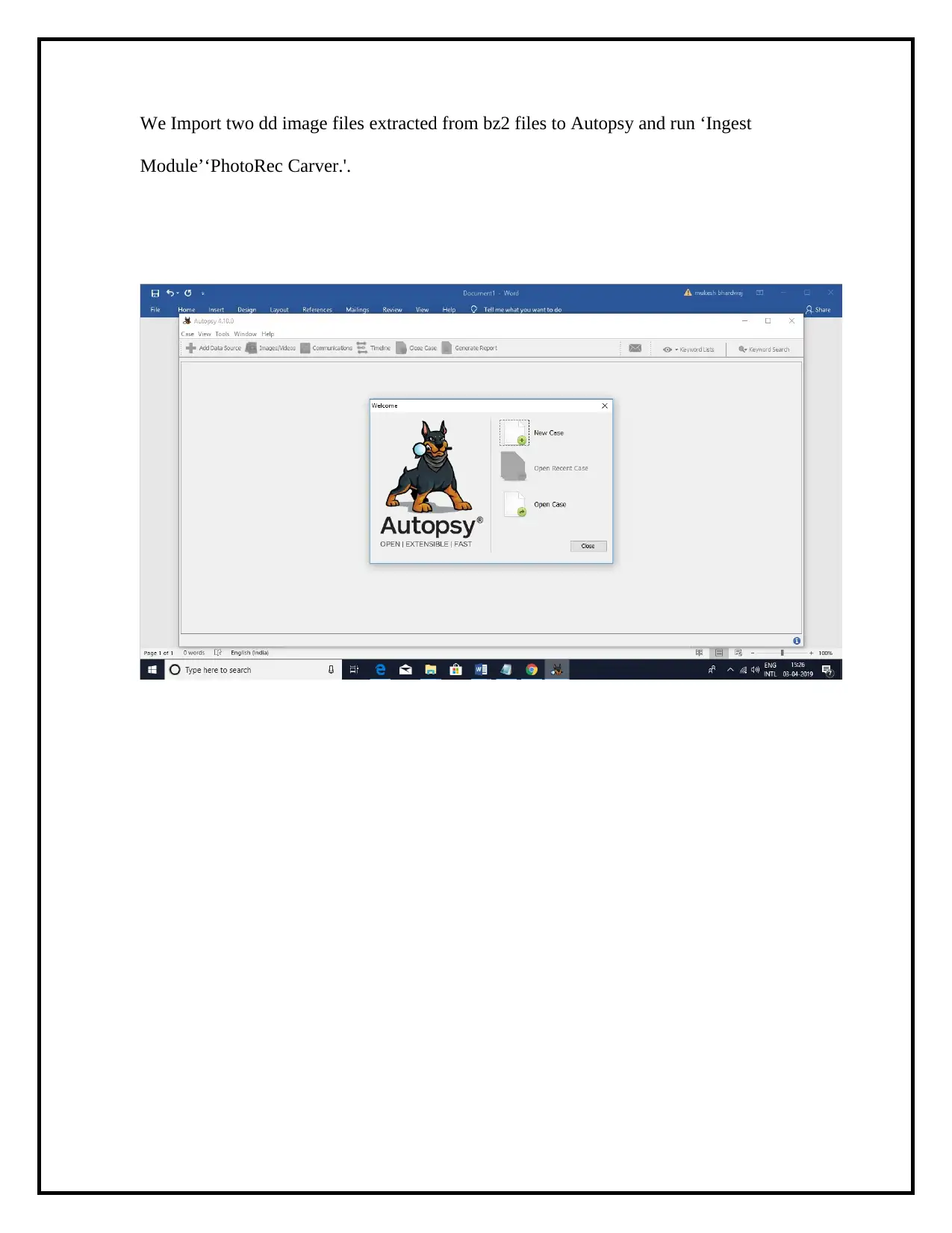
We Import two dd image files extracted from bz2 files to Autopsy and run ‘Ingest
Module’‘PhotoRec Carver.'.
Module’‘PhotoRec Carver.'.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
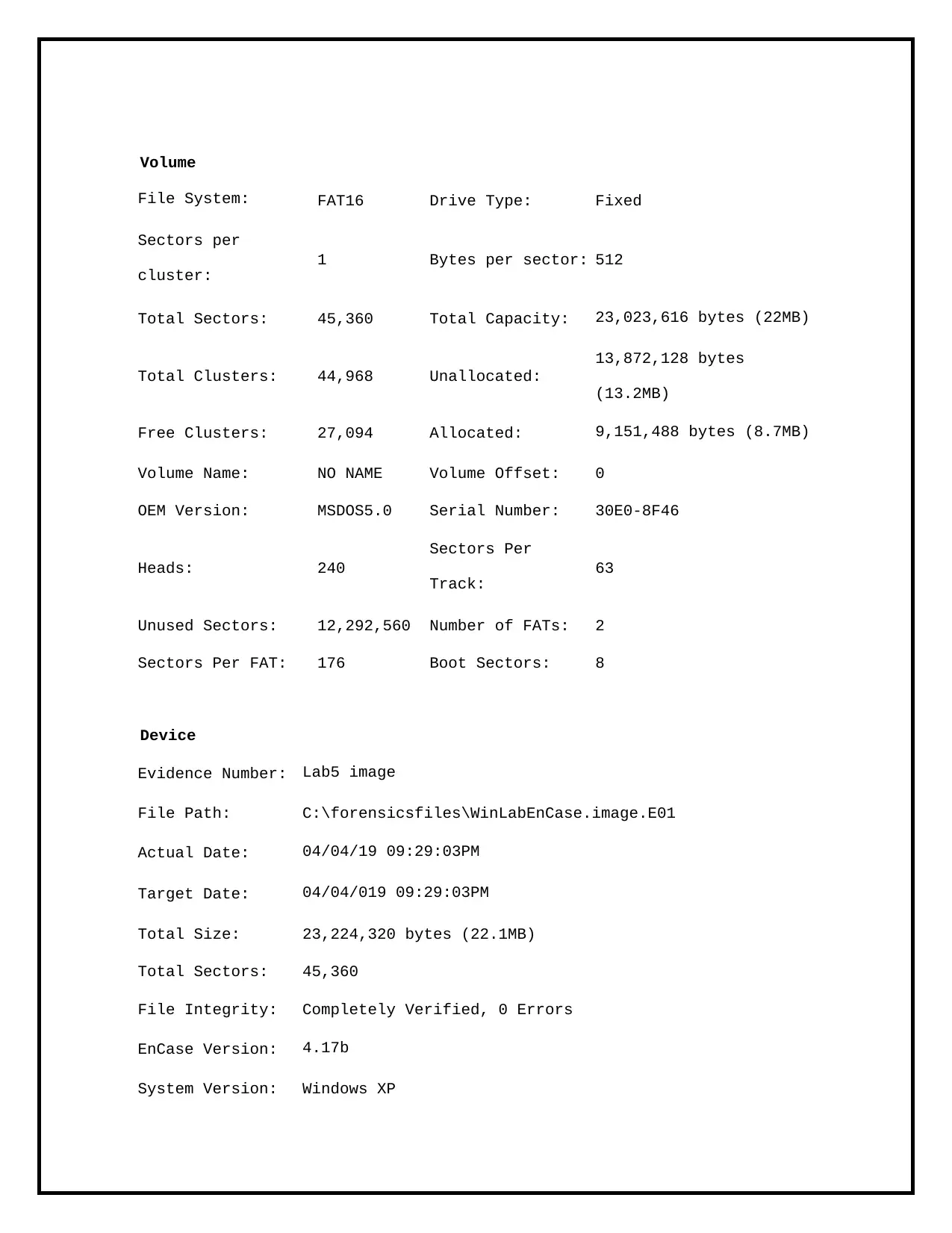
Volume
File System: FAT16 Drive Type: Fixed
Sectors per
cluster:
1 Bytes per sector: 512
Total Sectors: 45,360 Total Capacity: 23,023,616 bytes (22MB)
Total Clusters: 44,968 Unallocated:
13,872,128 bytes
(13.2MB)
Free Clusters: 27,094 Allocated: 9,151,488 bytes (8.7MB)
Volume Name: NO NAME Volume Offset: 0
OEM Version: MSDOS5.0 Serial Number: 30E0-8F46
Heads: 240
Sectors Per
Track:
63
Unused Sectors: 12,292,560 Number of FATs: 2
Sectors Per FAT: 176 Boot Sectors: 8
Device
Evidence Number: Lab5 image
File Path: C:\forensicsfiles\WinLabEnCase.image.E01
Actual Date: 04/04/19 09:29:03PM
Target Date: 04/04/019 09:29:03PM
Total Size: 23,224,320 bytes (22.1MB)
Total Sectors: 45,360
File Integrity: Completely Verified, 0 Errors
EnCase Version: 4.17b
System Version: Windows XP
File System: FAT16 Drive Type: Fixed
Sectors per
cluster:
1 Bytes per sector: 512
Total Sectors: 45,360 Total Capacity: 23,023,616 bytes (22MB)
Total Clusters: 44,968 Unallocated:
13,872,128 bytes
(13.2MB)
Free Clusters: 27,094 Allocated: 9,151,488 bytes (8.7MB)
Volume Name: NO NAME Volume Offset: 0
OEM Version: MSDOS5.0 Serial Number: 30E0-8F46
Heads: 240
Sectors Per
Track:
63
Unused Sectors: 12,292,560 Number of FATs: 2
Sectors Per FAT: 176 Boot Sectors: 8
Device
Evidence Number: Lab5 image
File Path: C:\forensicsfiles\WinLabEnCase.image.E01
Actual Date: 04/04/19 09:29:03PM
Target Date: 04/04/019 09:29:03PM
Total Size: 23,224,320 bytes (22.1MB)
Total Sectors: 45,360
File Integrity: Completely Verified, 0 Errors
EnCase Version: 4.17b
System Version: Windows XP

Acquisition Hash: F70C5FFF082E526A368E2C0A13ABB093
Verify Hash: F70C5FFF082E526A368E2C0A13ABB093
Daylight Saving Time settings
Hour Day of Week Week of month (5=last) Month
Daylight start 2 Sunday 1 4
Standard start 2 Sunday 5 10
Time Zone Settings (minutes)
Time Zone Bias: 300
Daylight Bias: -60
Standard Bias: 0
Time Zone: (GMT-05:00) Eastern Time (US & Canada)
My first task was to compile a list of keywords that I would need to search the file system
for. Knowing what words to start searching on could help me eliminate loads of
irrelevant data. The list contained the following: MCME Industries (MCME and
MCME Industry as different variations as well), Shalin, Anjali, and promotion. With
this list in hand I created a keyword list by clicking on View Keywords. I right
clicked Keywords Add New Folder. I named the folder Monika Keywords. Once the
folder was created I can right click the Monika Keywords folder Insert Keyword List.
The list box gets stored with the keywords previously mentioned. The new keywords
were then selected and a search was performed by going to Search at the top. The search
Verify Hash: F70C5FFF082E526A368E2C0A13ABB093
Daylight Saving Time settings
Hour Day of Week Week of month (5=last) Month
Daylight start 2 Sunday 1 4
Standard start 2 Sunday 5 10
Time Zone Settings (minutes)
Time Zone Bias: 300
Daylight Bias: -60
Standard Bias: 0
Time Zone: (GMT-05:00) Eastern Time (US & Canada)
My first task was to compile a list of keywords that I would need to search the file system
for. Knowing what words to start searching on could help me eliminate loads of
irrelevant data. The list contained the following: MCME Industries (MCME and
MCME Industry as different variations as well), Shalin, Anjali, and promotion. With
this list in hand I created a keyword list by clicking on View Keywords. I right
clicked Keywords Add New Folder. I named the folder Monika Keywords. Once the
folder was created I can right click the Monika Keywords folder Insert Keyword List.
The list box gets stored with the keywords previously mentioned. The new keywords
were then selected and a search was performed by going to Search at the top. The search
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
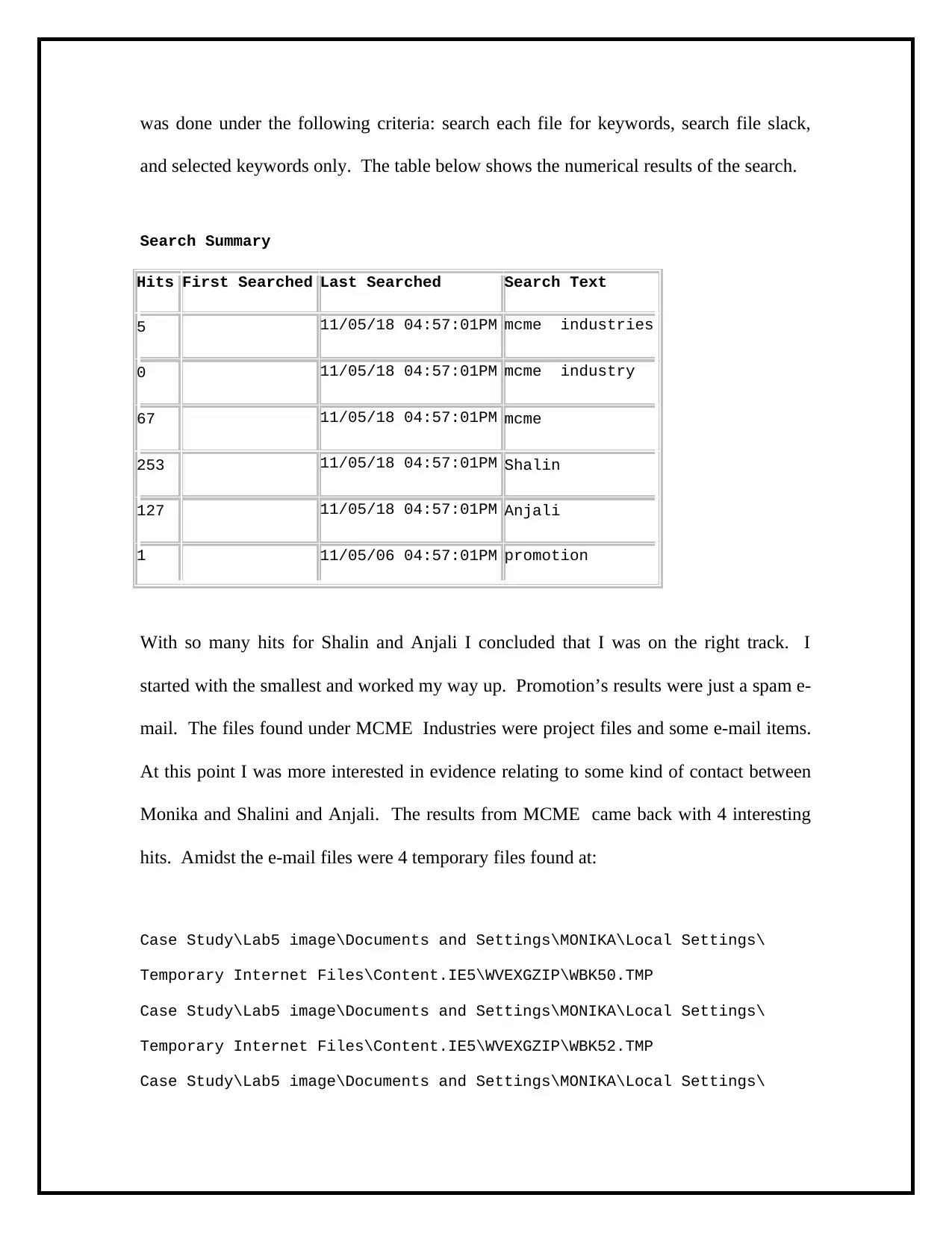
was done under the following criteria: search each file for keywords, search file slack,
and selected keywords only. The table below shows the numerical results of the search.
Search Summary
Hits First Searched Last Searched Search Text
5 11/05/18 04:57:01PM mcme industries
0 11/05/18 04:57:01PM mcme industry
67 11/05/18 04:57:01PM mcme
253 11/05/18 04:57:01PM Shalin
127 11/05/18 04:57:01PM Anjali
1 11/05/06 04:57:01PM promotion
With so many hits for Shalin and Anjali I concluded that I was on the right track. I
started with the smallest and worked my way up. Promotion’s results were just a spam e-
mail. The files found under MCME Industries were project files and some e-mail items.
At this point I was more interested in evidence relating to some kind of contact between
Monika and Shalini and Anjali. The results from MCME came back with 4 interesting
hits. Amidst the e-mail files were 4 temporary files found at:
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Temporary Internet Files\Content.IE5\WVEXGZIP\WBK50.TMP
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Temporary Internet Files\Content.IE5\WVEXGZIP\WBK52.TMP
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
and selected keywords only. The table below shows the numerical results of the search.
Search Summary
Hits First Searched Last Searched Search Text
5 11/05/18 04:57:01PM mcme industries
0 11/05/18 04:57:01PM mcme industry
67 11/05/18 04:57:01PM mcme
253 11/05/18 04:57:01PM Shalin
127 11/05/18 04:57:01PM Anjali
1 11/05/06 04:57:01PM promotion
With so many hits for Shalin and Anjali I concluded that I was on the right track. I
started with the smallest and worked my way up. Promotion’s results were just a spam e-
mail. The files found under MCME Industries were project files and some e-mail items.
At this point I was more interested in evidence relating to some kind of contact between
Monika and Shalini and Anjali. The results from MCME came back with 4 interesting
hits. Amidst the e-mail files were 4 temporary files found at:
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Temporary Internet Files\Content.IE5\WVEXGZIP\WBK50.TMP
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Temporary Internet Files\Content.IE5\WVEXGZIP\WBK52.TMP
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Temporary Internet Files\Content.IE5\WVEXGZIP\WBK54.TMP
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Temporary Internet Files\Content.IE5\WVEXGZIP\WBK56.TMP
These files all contained the message: “I’d like to offer you some material from my
company in exchange for a position in your company.” – Monika@mcme .com. These
files grabbed my attention so I made sure to take down the access times (all last accessed
on 3/9/04 around 11:38 AM). I took note by book marking the four files by selecting
them and right clicking Bookmark Files. I created a new folder called TMP Files
(MCME ) and the four were imported there for further consideration later. Anjali’s
results were next shuffled through but they were mostly HTML files that Monika must
have been visiting. The bulk of the hits came from Shalin. They were a mix of web files
including data and content. The web files came from the Shalin website where the
company’s about and contact pages were visited. Also mixed in were a few e-mails to a
Anjali@Shalin.com. I selected a few files which I saved to bookmarks in the DBX Files
(Shalin) folder. Two e-mails in particular stood out that contained information that
seemed to relate to this case. The following below is where the files can be located.
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Application Data\Identities\{E893F19B-C77A-4082-9435-87534CCECF93}\
Microsoft\Outlook Express\Deleted Items.dbx
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Application Data\Identities\{E893F19B-C77A-4082-9435-87534CCECF93}\
Microsoft\Outlook Express\Sent Items.dbx
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Temporary Internet Files\Content.IE5\WVEXGZIP\WBK56.TMP
These files all contained the message: “I’d like to offer you some material from my
company in exchange for a position in your company.” – Monika@mcme .com. These
files grabbed my attention so I made sure to take down the access times (all last accessed
on 3/9/04 around 11:38 AM). I took note by book marking the four files by selecting
them and right clicking Bookmark Files. I created a new folder called TMP Files
(MCME ) and the four were imported there for further consideration later. Anjali’s
results were next shuffled through but they were mostly HTML files that Monika must
have been visiting. The bulk of the hits came from Shalin. They were a mix of web files
including data and content. The web files came from the Shalin website where the
company’s about and contact pages were visited. Also mixed in were a few e-mails to a
Anjali@Shalin.com. I selected a few files which I saved to bookmarks in the DBX Files
(Shalin) folder. Two e-mails in particular stood out that contained information that
seemed to relate to this case. The following below is where the files can be located.
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Application Data\Identities\{E893F19B-C77A-4082-9435-87534CCECF93}\
Microsoft\Outlook Express\Deleted Items.dbx
Case Study\Lab5 image\Documents and Settings\MONIKA\Local Settings\
Application Data\Identities\{E893F19B-C77A-4082-9435-87534CCECF93}\
Microsoft\Outlook Express\Sent Items.dbx

The e-mails were both from Monika@mcme .com to Anjali@Shalin.com. The following
are the content of the two e-mails.
"Monika" <Monika@mcme .com>
To: "Anjali@Shalin.com"
Subject: A Proposition
Date: Fri, 23 Jan 2019 12:06:52 -0500
I'd like to offer you some material from my company in exchange for a
position in your company.
Monika
Monika@mcme .com
From: "Monika" <Monika@mcme .com>
To: "Anjali@Shalin.com"
Subject: My Proposition
Date: Fri, 01 Jul 2018 10:04:39 -0500
It's been a week since I sent you my proposal. Have you had a chance to
consider it?
Pat
are the content of the two e-mails.
"Monika" <Monika@mcme .com>
To: "Anjali@Shalin.com"
Subject: A Proposition
Date: Fri, 23 Jan 2019 12:06:52 -0500
I'd like to offer you some material from my company in exchange for a
position in your company.
Monika
Monika@mcme .com
From: "Monika" <Monika@mcme .com>
To: "Anjali@Shalin.com"
Subject: My Proposition
Date: Fri, 01 Jul 2018 10:04:39 -0500
It's been a week since I sent you my proposal. Have you had a chance to
consider it?
Pat
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




