MITS 5004 IT Security: Metasploit Framework Analysis Report
VerifiedAdded on 2023/03/20
|9
|1857
|31
Report
AI Summary
This report provides an introduction to the Metasploit Framework, an open-source tool created in 2003 for penetration testing and vulnerability assessment. It details the different types of Metasploit (Pro, Community, and Framework), highlighting the features available within the framework, such as Meterpreter, PassiveX Payloads, and Win32 DLL Injection Payloads. The report categorizes exploits into active and passive types and explores techniques like information gathering (port scanning, MSSQL hunting, service identification, password sniffing, and SNMP sweeping) and vulnerability scanning. An experiment is described where Metasploit is used to gather emails from a public site. The report concludes by emphasizing the tool's power and the importance of ethical usage and provides references to related works. This assignment was completed for MITS 5004 IT Security at the Victorian Institute of Technology.

METASPLOIT
Introduction
Metasploit framework was created in 2003 by H.D Moore. It’s an open source framework and
can be used by anyone. The best thing about Metasploit is that it is a framework, and anyone can
build their own tools to use for a specific function. There are three types of Metasploit
frameworks. Metasploit Pro, Metasploit Community and Metasploit framework. Metasploit
community and framework are open source and are available for free while Metasploit Pro you
must pay to fully access it after the 14-day trial period. Metasploit is used to run attacks on other
systems and to exploit the vulnerability of systems and hack into them. Mostly it is used by
hackers to test the strength of a system (Dalziel, 2019). The Metasploit framework has two types
of interfaces: the console interface and the GUI interface. Both these interfaces can perform the
same tasks and it depends on the user preference. Metasploit framework can be used in windows
environment, Linux environment and Mac OS environment. You can find the downloadable files
on their website. For kali Linux, the Metasploit framework comes already installed. In this report
we are going to concentrate on the kali Linux Metasploit framework.
Features of Metasploit Framework
Metasploit has various features that assist the user in finding vulnerabilities to the system. Some
of the features of Metasploit framework include
The Meterpreter
This is a payload which contains various functions which can change and can also be increased
when a system is ran. This feature gives you an interface which is a basic shell and gives you
access to increase the features and possibly make new ones.
PassiveX Payloads
This feature targets the ActiveX controls. It manipulates the registry of the targeted system and
this in turn causes the processes that have been compromised to launch Internet explores with a
URL that points back to the framework. A web server is started by the framework and the
request is then acknowledged which in turn starts a web page which loads the Active x control
that has been exploited. The compromised component then registers, downloads and executes the
ActiveX.
Introduction
Metasploit framework was created in 2003 by H.D Moore. It’s an open source framework and
can be used by anyone. The best thing about Metasploit is that it is a framework, and anyone can
build their own tools to use for a specific function. There are three types of Metasploit
frameworks. Metasploit Pro, Metasploit Community and Metasploit framework. Metasploit
community and framework are open source and are available for free while Metasploit Pro you
must pay to fully access it after the 14-day trial period. Metasploit is used to run attacks on other
systems and to exploit the vulnerability of systems and hack into them. Mostly it is used by
hackers to test the strength of a system (Dalziel, 2019). The Metasploit framework has two types
of interfaces: the console interface and the GUI interface. Both these interfaces can perform the
same tasks and it depends on the user preference. Metasploit framework can be used in windows
environment, Linux environment and Mac OS environment. You can find the downloadable files
on their website. For kali Linux, the Metasploit framework comes already installed. In this report
we are going to concentrate on the kali Linux Metasploit framework.
Features of Metasploit Framework
Metasploit has various features that assist the user in finding vulnerabilities to the system. Some
of the features of Metasploit framework include
The Meterpreter
This is a payload which contains various functions which can change and can also be increased
when a system is ran. This feature gives you an interface which is a basic shell and gives you
access to increase the features and possibly make new ones.
PassiveX Payloads
This feature targets the ActiveX controls. It manipulates the registry of the targeted system and
this in turn causes the processes that have been compromised to launch Internet explores with a
URL that points back to the framework. A web server is started by the framework and the
request is then acknowledged which in turn starts a web page which loads the Active x control
that has been exploited. The compromised component then registers, downloads and executes the
ActiveX.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Chainable Proxies
This feature makes use of the TCP proxies. Before an exploit can be carried out using this
feature, an environment variable must be set up first. After that the server is configured using the
host and port format. This server can be used to test whether a system is secure or not. You can
use multiple server configuration until you find the system weakness.
Win32 UploadExec Payloads
This feature exploits the weaknesses that are in the windows operating system. It takes advantage
of the fact that windows does not have a powerful command line. This feature enables users to
exploit a Windows system. It is very powerful in that it can allow the hacker to upload and
execute the tool they are used to wit ease across the payload socket connection. Also, it can be
used with other scripting languages such as perl.exe or combined with a self-extracting rootkit
hence making it one of the features that’s powerful in Metasploit.
Win32 DLL Injection Payloads
This feature enables a hacker to customize their own DLL and use it to exploit other systems.
The DLL is inserted to the memory of the target system and is usually combined with a Win32
exploit. When this is done the DLL will export a function known as init which will now be the
access point to which the processes can be exploited by the new thread.
VNC Server DLL Injection
This feature allows the hacker to gain access to the other systems desktop by using the win32
exploit. Once the DLL is inserted into one of the processes of the target system, it is started as a
new thread. Once the thread has been started, it listens to the requests made by the VNC client.
The framework then gathers information that is sent through the VNC client and after acquiring
all the needed information, it will attempt to gain full access to the target computers desktop.
Techniques used by Metasploit to exploit vulnerabilities of information systems
Exploits that are used in the Metasploit framework have been categorized into two. Active
exploits and passive exploits. Active exploits will compromise a particular target and exploit the
target until the process is completed then it terminates the process. On the other hand, A passive
exploit will wait until the hosts are identified then compromise them as they connect
(Kerner,2019).
Some of the techniques used include
This feature makes use of the TCP proxies. Before an exploit can be carried out using this
feature, an environment variable must be set up first. After that the server is configured using the
host and port format. This server can be used to test whether a system is secure or not. You can
use multiple server configuration until you find the system weakness.
Win32 UploadExec Payloads
This feature exploits the weaknesses that are in the windows operating system. It takes advantage
of the fact that windows does not have a powerful command line. This feature enables users to
exploit a Windows system. It is very powerful in that it can allow the hacker to upload and
execute the tool they are used to wit ease across the payload socket connection. Also, it can be
used with other scripting languages such as perl.exe or combined with a self-extracting rootkit
hence making it one of the features that’s powerful in Metasploit.
Win32 DLL Injection Payloads
This feature enables a hacker to customize their own DLL and use it to exploit other systems.
The DLL is inserted to the memory of the target system and is usually combined with a Win32
exploit. When this is done the DLL will export a function known as init which will now be the
access point to which the processes can be exploited by the new thread.
VNC Server DLL Injection
This feature allows the hacker to gain access to the other systems desktop by using the win32
exploit. Once the DLL is inserted into one of the processes of the target system, it is started as a
new thread. Once the thread has been started, it listens to the requests made by the VNC client.
The framework then gathers information that is sent through the VNC client and after acquiring
all the needed information, it will attempt to gain full access to the target computers desktop.
Techniques used by Metasploit to exploit vulnerabilities of information systems
Exploits that are used in the Metasploit framework have been categorized into two. Active
exploits and passive exploits. Active exploits will compromise a particular target and exploit the
target until the process is completed then it terminates the process. On the other hand, A passive
exploit will wait until the hosts are identified then compromise them as they connect
(Kerner,2019).
Some of the techniques used include

Information gathering
For a hack to be successful adequate information needs to be gathered for that system to
adequately understand the system. There are various types of methods for gathering information
and these methods include
a) Port scanning. This gathers information on a network through the ports. Port scanning
can either be done on the whole network or just a particular target. It is effective
especially when some systems are behind s firewall.
b) Hunting for MSSQL. Installations of MSSQL nature are targeted using this information
gathering technique. This can be achieved by the use of UDP foot printing.
c) Service Identification Metasploit also includes a large variety of scanners for various
services, often helping you determine potentially vulnerable running services
d) Password Sniffing, The Metasploit framework has a variety of password sniffing tools
which can be used to acquire the passwords of different users. An example of a password
sniffing tool is the dsniff. This tool supports various protocols such as IMAP
e) SNMP sweeping. This includes sweeping of different systems so as to acquire more
information about them. An example is finding a cisco device and downloading its
configurations. After that is done, the hacker can replace the configuration by replacing it
with his own malicious configuration and uploading it to that device
Vulnerability Scanning with Metasploit
This involves scanning and identifying a vulnerable system before exploiting it. The scanning is
based on a certain range of IP addresses and this helps the attacker to identify which type of
attack to use (Maynor, 2011). This method has its advantages and disadvantages, but the results
obtained are often high when using this method.
a) SMB login check. This method connects to different targets and identifies whether different
combinations of password and usernames can compromise the targets.
b) VNC Authentication. This tool scans a given IP address range and tries to locate systems har
are running VNC server. If it finds a VNC server, it will check if it has a password that has
been configured to it or not. If the password has not been configured, it makes it easy for the
hacker to gain access to the system.
For a hack to be successful adequate information needs to be gathered for that system to
adequately understand the system. There are various types of methods for gathering information
and these methods include
a) Port scanning. This gathers information on a network through the ports. Port scanning
can either be done on the whole network or just a particular target. It is effective
especially when some systems are behind s firewall.
b) Hunting for MSSQL. Installations of MSSQL nature are targeted using this information
gathering technique. This can be achieved by the use of UDP foot printing.
c) Service Identification Metasploit also includes a large variety of scanners for various
services, often helping you determine potentially vulnerable running services
d) Password Sniffing, The Metasploit framework has a variety of password sniffing tools
which can be used to acquire the passwords of different users. An example of a password
sniffing tool is the dsniff. This tool supports various protocols such as IMAP
e) SNMP sweeping. This includes sweeping of different systems so as to acquire more
information about them. An example is finding a cisco device and downloading its
configurations. After that is done, the hacker can replace the configuration by replacing it
with his own malicious configuration and uploading it to that device
Vulnerability Scanning with Metasploit
This involves scanning and identifying a vulnerable system before exploiting it. The scanning is
based on a certain range of IP addresses and this helps the attacker to identify which type of
attack to use (Maynor, 2011). This method has its advantages and disadvantages, but the results
obtained are often high when using this method.
a) SMB login check. This method connects to different targets and identifies whether different
combinations of password and usernames can compromise the targets.
b) VNC Authentication. This tool scans a given IP address range and tries to locate systems har
are running VNC server. If it finds a VNC server, it will check if it has a password that has
been configured to it or not. If the password has not been configured, it makes it easy for the
hacker to gain access to the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
c) WMAP Web Scanner. This tool enables a hacker to scan a web application using the
Metasploit framework. This is a really good tool especially if you want to find a vulnerability
in a web application.
Experiment using Metasploit Framework
I used Metasploit Framework to gather emails of people from public sites.
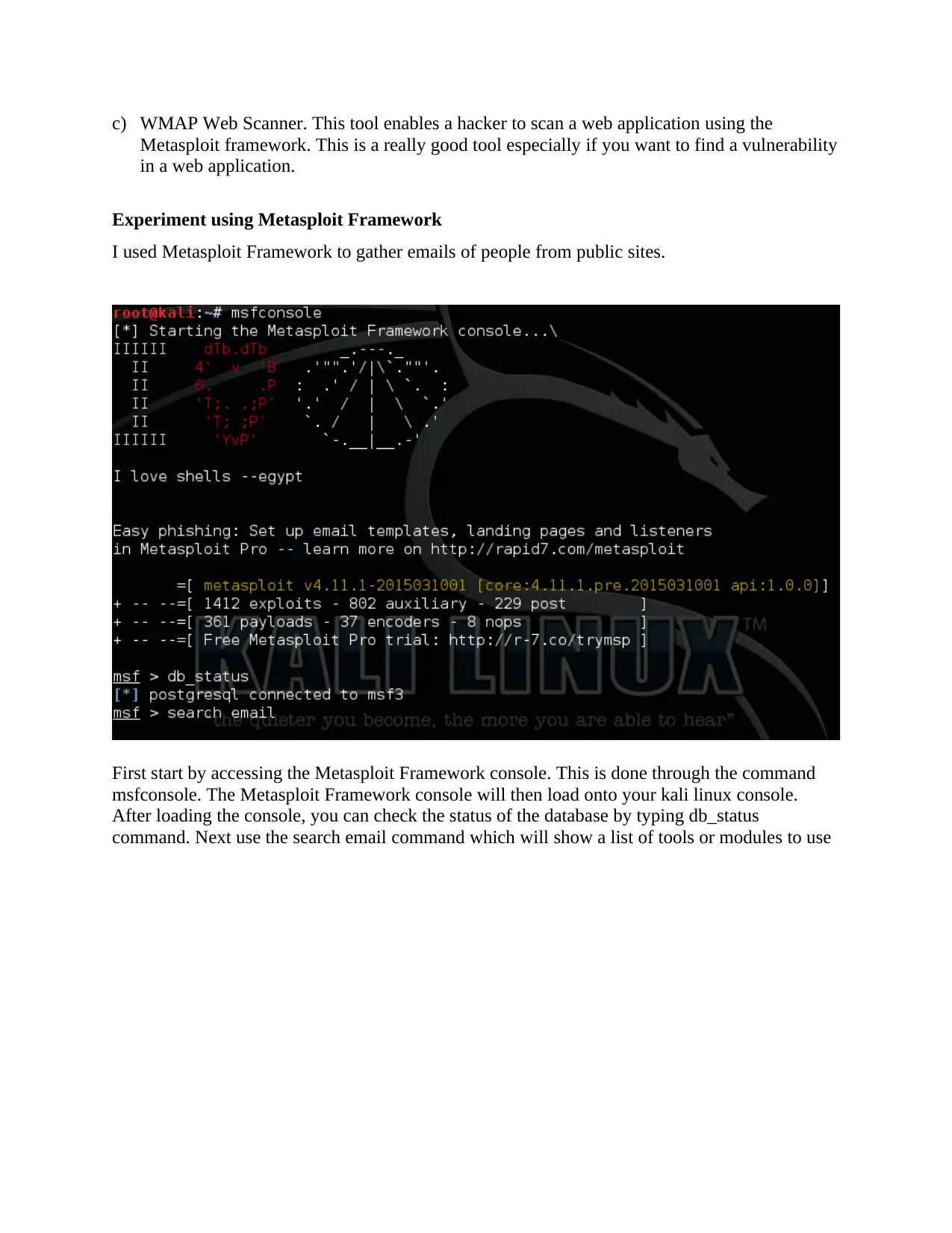
First start by accessing the Metasploit Framework console. This is done through the command
msfconsole. The Metasploit Framework console will then load onto your kali linux console.
After loading the console, you can check the status of the database by typing db_status
command. Next use the search email command which will show a list of tools or modules to use
Metasploit framework. This is a really good tool especially if you want to find a vulnerability
in a web application.
Experiment using Metasploit Framework
I used Metasploit Framework to gather emails of people from public sites.
First start by accessing the Metasploit Framework console. This is done through the command
msfconsole. The Metasploit Framework console will then load onto your kali linux console.
After loading the console, you can check the status of the database by typing db_status
command. Next use the search email command which will show a list of tools or modules to use
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
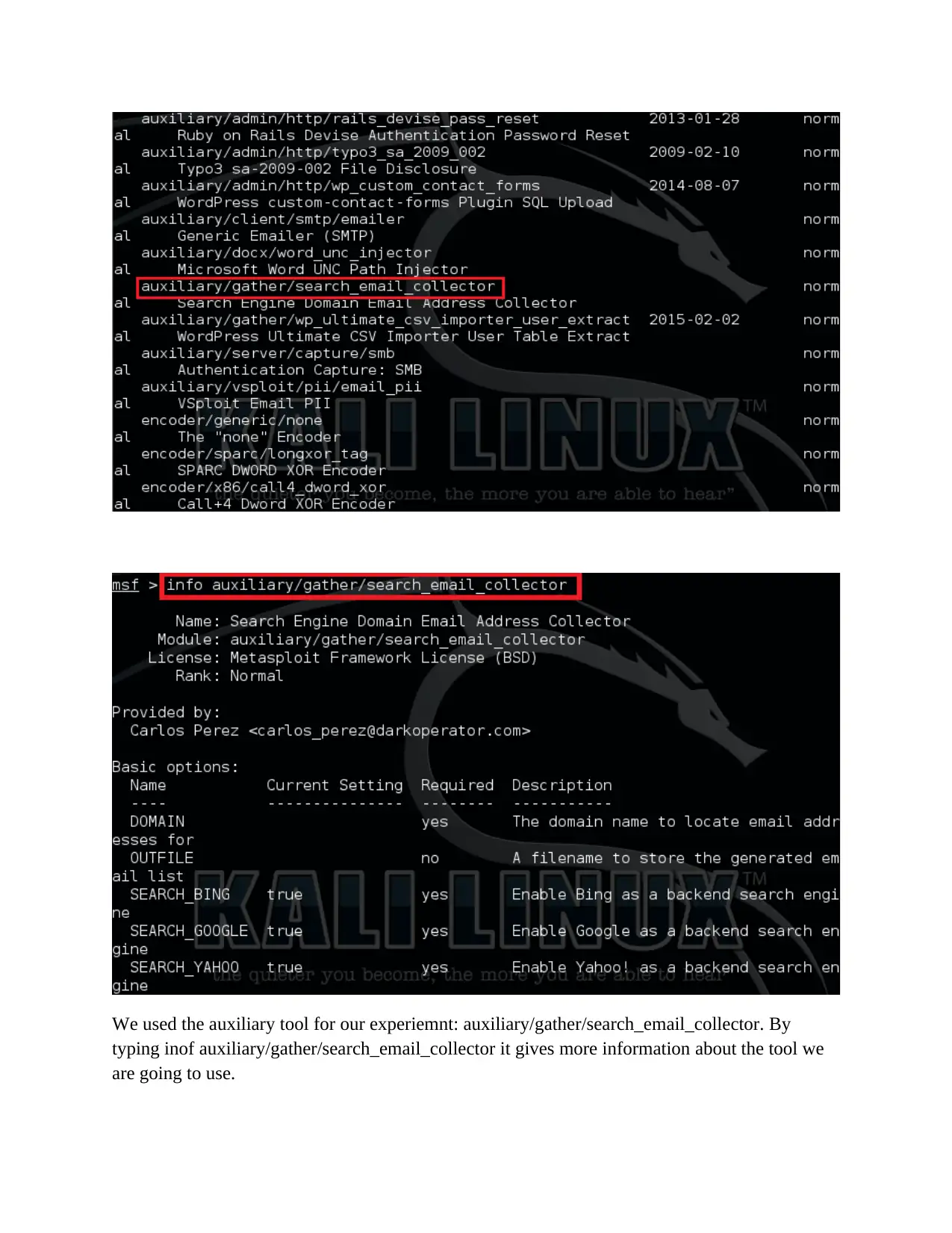
We used the auxiliary tool for our experiemnt: auxiliary/gather/search_email_collector. By
typing inof auxiliary/gather/search_email_collector it gives more information about the tool we
are going to use.
typing inof auxiliary/gather/search_email_collector it gives more information about the tool we
are going to use.
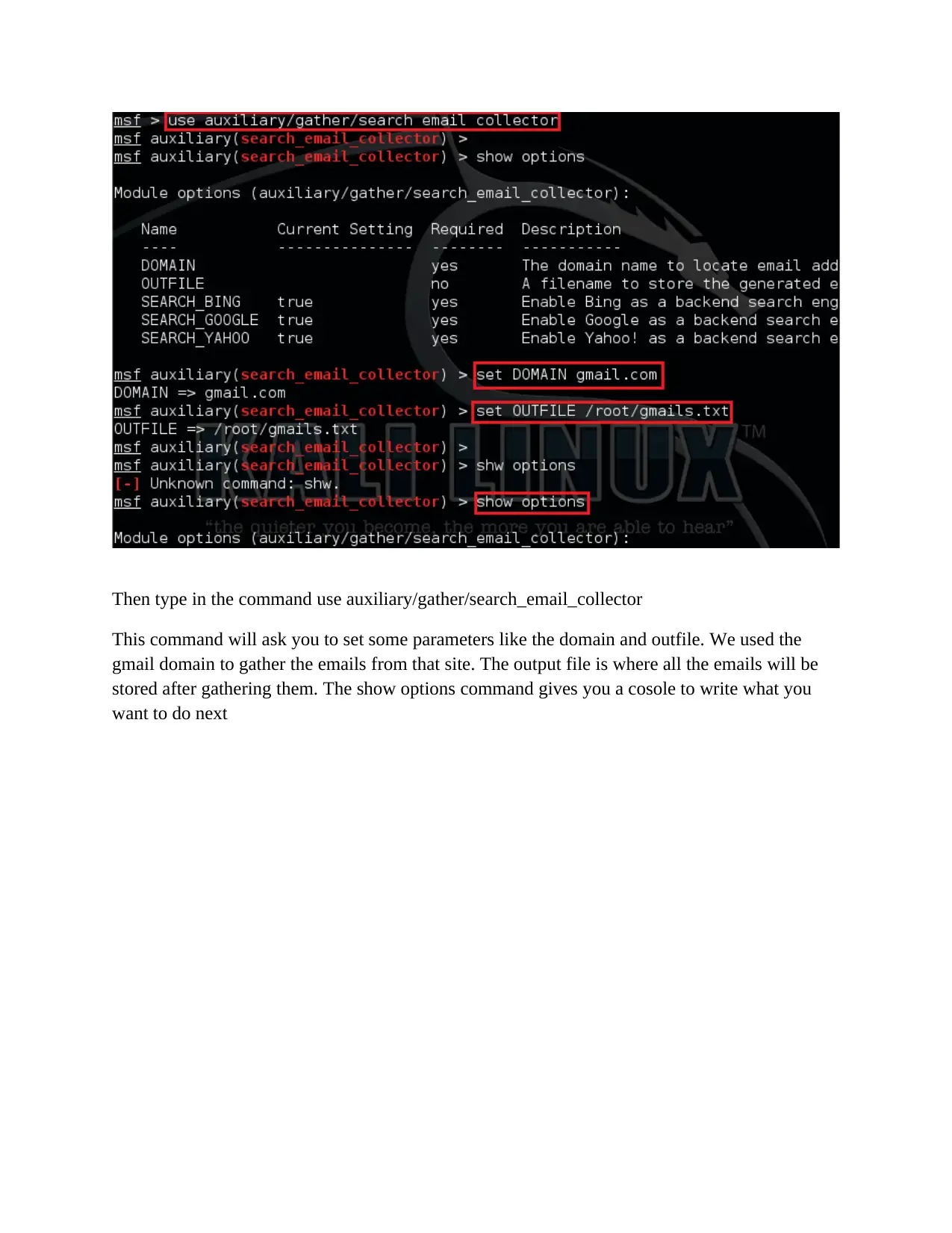
Then type in the command use auxiliary/gather/search_email_collector
This command will ask you to set some parameters like the domain and outfile. We used the
gmail domain to gather the emails from that site. The output file is where all the emails will be
stored after gathering them. The show options command gives you a cosole to write what you
want to do next
This command will ask you to set some parameters like the domain and outfile. We used the
gmail domain to gather the emails from that site. The output file is where all the emails will be
stored after gathering them. The show options command gives you a cosole to write what you
want to do next
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
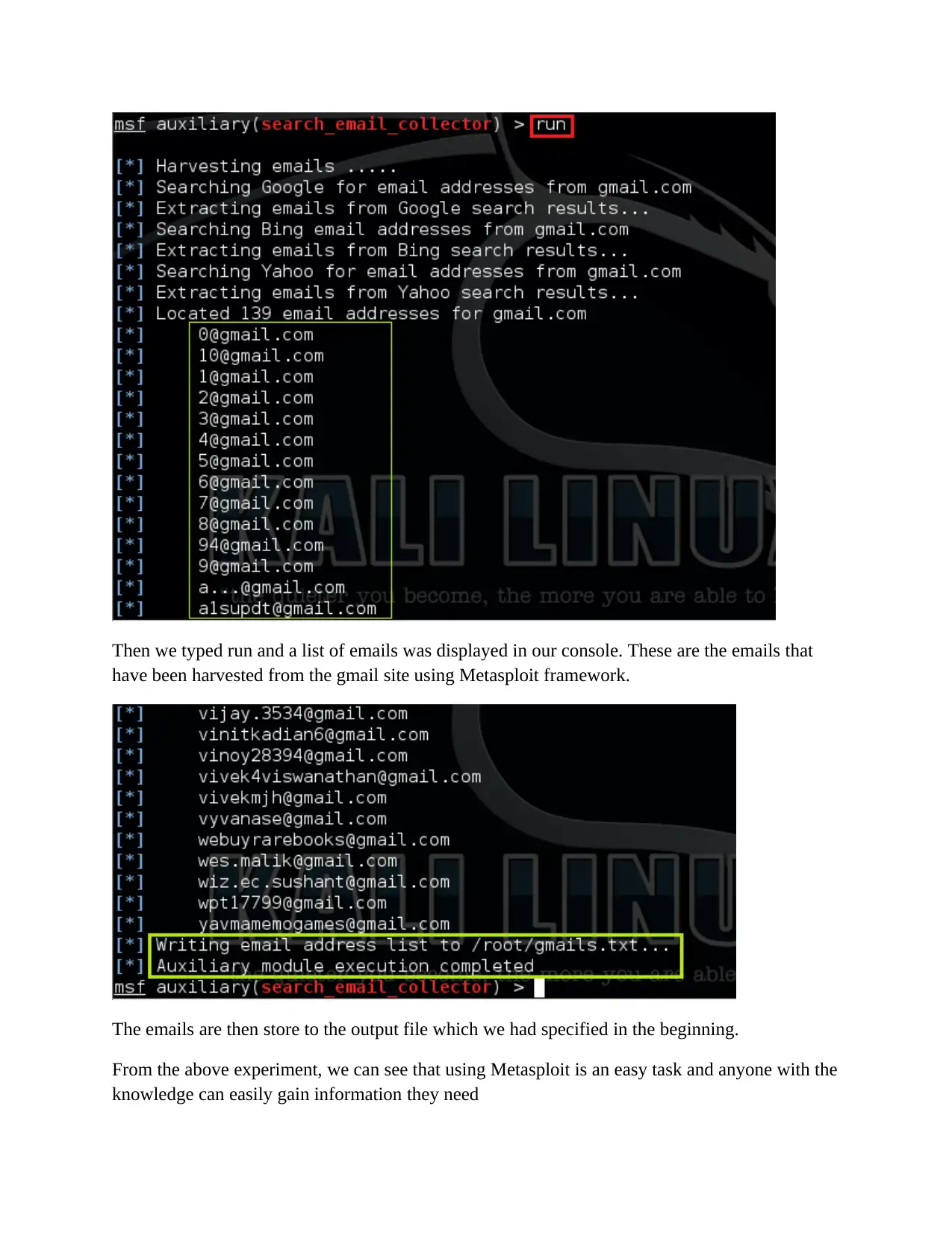
Then we typed run and a list of emails was displayed in our console. These are the emails that
have been harvested from the gmail site using Metasploit framework.
The emails are then store to the output file which we had specified in the beginning.
From the above experiment, we can see that using Metasploit is an easy task and anyone with the
knowledge can easily gain information they need
have been harvested from the gmail site using Metasploit framework.
The emails are then store to the output file which we had specified in the beginning.
From the above experiment, we can see that using Metasploit is an easy task and anyone with the
knowledge can easily gain information they need
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
Metasploit Framework is a powerful tool for penetration testing. When used properly it can be
able to assist security administrator to patch up the weaknesses in their systems and make them
even more secure. When used wrongly Metasploit Framework has the ability exploit system
vulnerabilities hence can result in data loss or data being stolen. Therefore, we should always act
within the law so as to ensure that we can make the world a better place by ensuring that we
report the system vulnerabilities and also by ensuring that the vulnerabilities and corrected and
the systems are secure.
References
Bort, J. (2019). Open source hacker tool, Metasploit, gains new features. Retrieved from
https://www.networkworld.com/article/2230523/open-source-hacker-tool--metasploit--gains-new-
features.html
Dalziel, H. (2019). Metasploit For Complete Beginners & N00bs (Basic Commands). Retrieved from
https://www.concise-courses.com/metasploit-for-beginners/
Gupta, H., & Kumar, R. (2015, September). Protection against penetration attacks using Metasploit. In
2015 4th International Conference on Reliability, Infocom Technologies and Optimization (ICRITO)(Trends
and Future Directions) (pp. 1-4). IEEE.
Holik, F., Horalek, J., Marik, O., Neradova, S., & Zitta, S. (2014, November). Effective penetration testing
with Metasploit framework and methodologies. In 2014 IEEE 15th International Symposium on
Computational Intelligence and Informatics (CINTI) (pp. 237-242). IEEE.
Kennedy, D., O'gorman, J., Kearns, D., & Aharoni, M. (2011). Metasploit: the penetration tester's guide.
No Starch Press.
Metasploit Framework is a powerful tool for penetration testing. When used properly it can be
able to assist security administrator to patch up the weaknesses in their systems and make them
even more secure. When used wrongly Metasploit Framework has the ability exploit system
vulnerabilities hence can result in data loss or data being stolen. Therefore, we should always act
within the law so as to ensure that we can make the world a better place by ensuring that we
report the system vulnerabilities and also by ensuring that the vulnerabilities and corrected and
the systems are secure.
References
Bort, J. (2019). Open source hacker tool, Metasploit, gains new features. Retrieved from
https://www.networkworld.com/article/2230523/open-source-hacker-tool--metasploit--gains-new-
features.html
Dalziel, H. (2019). Metasploit For Complete Beginners & N00bs (Basic Commands). Retrieved from
https://www.concise-courses.com/metasploit-for-beginners/
Gupta, H., & Kumar, R. (2015, September). Protection against penetration attacks using Metasploit. In
2015 4th International Conference on Reliability, Infocom Technologies and Optimization (ICRITO)(Trends
and Future Directions) (pp. 1-4). IEEE.
Holik, F., Horalek, J., Marik, O., Neradova, S., & Zitta, S. (2014, November). Effective penetration testing
with Metasploit framework and methodologies. In 2014 IEEE 15th International Symposium on
Computational Intelligence and Informatics (CINTI) (pp. 237-242). IEEE.
Kennedy, D., O'gorman, J., Kearns, D., & Aharoni, M. (2011). Metasploit: the penetration tester's guide.
No Starch Press.

Maynor, D. (2011). Metasploit toolkit for penetration testing, exploit development, and vulnerability
research. Elsevier.
Kerner S. (2019) Open-Source Metasploit Framework 5.0 Improves Security Testing. (2019). Retrieved
from https://www.eweek.com/security/open-source-metasploit-framework-5.0-improves-security-
testing
What is Metasploit? Webopedia Definition. (2019). Retrieved from
https://www.webopedia.com/TERM/M/Metasploit.html
research. Elsevier.
Kerner S. (2019) Open-Source Metasploit Framework 5.0 Improves Security Testing. (2019). Retrieved
from https://www.eweek.com/security/open-source-metasploit-framework-5.0-improves-security-
testing
What is Metasploit? Webopedia Definition. (2019). Retrieved from
https://www.webopedia.com/TERM/M/Metasploit.html
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




