Countering Side Channel Attacks in Smart Home Applications
VerifiedAdded on 2022/11/13
|8
|3781
|311
Report
AI Summary
This report presents a novel method for countering snooping-based side channel attacks in smart home environments, crucial in the era of the Internet of Things (IoT). The study addresses the vulnerability of smart home applications to privacy breaches through side channel attacks, where adversaries exploit radio frequency signals to infer user activities. The proposed method utilizes logistic regression to add noise to transmitted data sequences, adapting to network status to protect resident privacy. This approach offers advantages such as low energy consumption, reduced latency, and strong adaptability compared to existing solutions. The report details the method's implementation, incorporating variables like traffic state, time, and send density to determine the need for fake messages. It also reviews related work, including models like ConstRate and FitProbRate, while emphasizing the importance of balancing privacy, energy consumption, and latency in wireless sensor networks. The report concludes by highlighting the effectiveness of the proposed method in enhancing privacy protection in smart home environments.

A Method for Countering Snooping-Based Side
Channel Attacks in Smart Home Applications
Jingsha He,Qi Xiao(&) , and Muhammad Salman Pathan
School of Software Engineering,Beijing Engineering Research Center for IoT
Software and Systems, Beijing University of Technology, Beijing 100124, China
jhe@bjut.edu.cn, xqnssa@emails.bjut.edu.cn,
muhammad.salman@nu.edu.pk
Abstract.In recent years, with the rapid development of the Internet of Things
(IoT),the information technology has been widely used in smarthome appli-
cations.On the other hand,smarthome technology closely related to people’s
privacy,which is notmuch considered by smarthome vendors,making the
privacy protection of smarthome a hotresearch topic.Traditionalencryption
methods can ensure the security of the transmission process,butit can hardly
resistthe side channelattacks.Adversaries can analyze the radio frequency
signals of wireless sensors and timestamp series to acquire the Activity of Daily
Living (ADL). The most simple and efficient way to counter side channel attacks
is to add noise into the transmitted data sequence. In this paper, we propose an
improved method based on Logistic Regression (LR), which can be adapted to
network status to protect the privacy of residents in smart home environments.
Compared with other similar approaches, our method has the advantage of low
energy consumption, low latency, strong adaptability and good effect of privacy
protection.
Keywords:Smart homeSide channel attackPrivacy Logistic Regression
1 Introduction
Smarthome is one of the importantbranches of the Internetof Things (IoT) which
relies on wireless sensors to sense and collectactivity and status information.These
sensors can sense particularphenomena,convertthe sensed information into data,
process the data and then transmit the data onto a sink node for further analysi
example, the measurement of temperature, humidity, luminosity, noise levels, p
etc., can provide useful data to interpret a physical activity in space and time in
determine the activity of a person and thus can contribute in detecting unusual
tions and emergency cases [2].The sensed data contains much private information of
the resident, however, while the societal concerns of smart home technology ev
in relation to the privacy and security of the citizen appear to be still at an embr
stage [3]. The acquired ADLs can help to improve the quality of life, but it can al
exposed to the attacker,therefore,the issue ofprivacy protection in smarthome
environments has become one of the most challenging issues.
© ICST Institute for Computer Sciences,Social Informatics and Telecommunications Engineering 2018
Q. Chen et al.(Eds.): ChinaCom 2016,Part I,LNICST 209,pp.200–207,2018.
DOI: 10.1007/978-3-319-66625-9_20
Channel Attacks in Smart Home Applications
Jingsha He,Qi Xiao(&) , and Muhammad Salman Pathan
School of Software Engineering,Beijing Engineering Research Center for IoT
Software and Systems, Beijing University of Technology, Beijing 100124, China
jhe@bjut.edu.cn, xqnssa@emails.bjut.edu.cn,
muhammad.salman@nu.edu.pk
Abstract.In recent years, with the rapid development of the Internet of Things
(IoT),the information technology has been widely used in smarthome appli-
cations.On the other hand,smarthome technology closely related to people’s
privacy,which is notmuch considered by smarthome vendors,making the
privacy protection of smarthome a hotresearch topic.Traditionalencryption
methods can ensure the security of the transmission process,butit can hardly
resistthe side channelattacks.Adversaries can analyze the radio frequency
signals of wireless sensors and timestamp series to acquire the Activity of Daily
Living (ADL). The most simple and efficient way to counter side channel attacks
is to add noise into the transmitted data sequence. In this paper, we propose an
improved method based on Logistic Regression (LR), which can be adapted to
network status to protect the privacy of residents in smart home environments.
Compared with other similar approaches, our method has the advantage of low
energy consumption, low latency, strong adaptability and good effect of privacy
protection.
Keywords:Smart homeSide channel attackPrivacy Logistic Regression
1 Introduction
Smarthome is one of the importantbranches of the Internetof Things (IoT) which
relies on wireless sensors to sense and collectactivity and status information.These
sensors can sense particularphenomena,convertthe sensed information into data,
process the data and then transmit the data onto a sink node for further analysi
example, the measurement of temperature, humidity, luminosity, noise levels, p
etc., can provide useful data to interpret a physical activity in space and time in
determine the activity of a person and thus can contribute in detecting unusual
tions and emergency cases [2].The sensed data contains much private information of
the resident, however, while the societal concerns of smart home technology ev
in relation to the privacy and security of the citizen appear to be still at an embr
stage [3]. The acquired ADLs can help to improve the quality of life, but it can al
exposed to the attacker,therefore,the issue ofprivacy protection in smarthome
environments has become one of the most challenging issues.
© ICST Institute for Computer Sciences,Social Informatics and Telecommunications Engineering 2018
Q. Chen et al.(Eds.): ChinaCom 2016,Part I,LNICST 209,pp.200–207,2018.
DOI: 10.1007/978-3-319-66625-9_20
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Compared to other wireless sensor networks, the type and number of sens
smarthome are similarto generalhomes.And mostsensorsare operated in the
event-triggered mode,where sensor data is transmitted only when a relevant eve
detected. We can image that when an event occurs, the transmission will be
immediately.While data encryption algorithms can only ensure the security ofthe
sensor data during the transmission,however the radio frequency of the transmissio
can be revealed to the adversary who has the ability to listen to the global tra
state. The adversary can use a side channel attack method to analyze the tra
sequence and can acquire the ADLs ofthe resident.For example,FingerprintAnd
Timing-based Snooping (FATS) attacks only need the timestamp and the fing
each radio message, where a fingerprint is a set of features of an RF waveform
unique to a particular transmitter [4].The mostsimple and effective method to resist
side channel attacks is to add fake message onto the transmission sequence
adversary unable to distinguish between fake and real messages. However, d
limitations of the communication bandwidth,battery energy and computing power of
wireless sensor nodes,the amount of fake data should be added as low as possibl
There has been an extensive study ofthe approaches to protectthe privacy of
residents in a smarthome environment.These solutions are mainly based on a fixed
frequency orprobability models,thus having the majordrawbacks like delaying in
reporting the realevents untilthe nextscheduled transmission.For smarthome sce-
narios, such delay of reporting real sensed data can cause the degradation of
of service (QoS) in many applications [5].Some of the applications like intelligent
sensing, the delay can generally not be tolerated, where the states of the sen
be received in a realtimely fashion for making the corresponding responses.As the
delay problem isconcerned,Park etal. proposed an improved method based on
behavioral semantics. But the method heavily depends on the accuracy of pre
the prediction ofthe nextactivity providesan inaccurate answer,the added fake
messages will not be enough to affect the statistical analysis. In this paper, w
an improved method to resist the side channel attacks based on logistic regre
can be adapted to the network state.Thatis, when the traffic is heavy and no ADL
happens, the frequency of adding fake data should be automatically reduced
real event occurs,right time will be chosen to add noise to protect the real event
The rest of this paper is organized as follows. In Sect.2, we review some existing
solutions. In Sect.3, we describe our method in detail. In Sect.4, we will compare our
method to some othersolutions.In Sect.5, we have given the conclusion ofthis
approach.
2 Related Work
The ConstRate (Sending packets at a fixed frequency) model, all the sensor n
the packets according to the same transmission intervals.Thus,the realevents must
send the packets until the next transmission. So the method can achieve the
work to resistthe static analysis attack.Obviously,the ConstRate modelhas a con-
genital deficiency: the delay depends on the transmission interval which is ha
interval.Also it is difficultto determine an appropriate transmission intervalin the
A Method for Countering Snooping-Based Side Channel Attacks201
smarthome are similarto generalhomes.And mostsensorsare operated in the
event-triggered mode,where sensor data is transmitted only when a relevant eve
detected. We can image that when an event occurs, the transmission will be
immediately.While data encryption algorithms can only ensure the security ofthe
sensor data during the transmission,however the radio frequency of the transmissio
can be revealed to the adversary who has the ability to listen to the global tra
state. The adversary can use a side channel attack method to analyze the tra
sequence and can acquire the ADLs ofthe resident.For example,FingerprintAnd
Timing-based Snooping (FATS) attacks only need the timestamp and the fing
each radio message, where a fingerprint is a set of features of an RF waveform
unique to a particular transmitter [4].The mostsimple and effective method to resist
side channel attacks is to add fake message onto the transmission sequence
adversary unable to distinguish between fake and real messages. However, d
limitations of the communication bandwidth,battery energy and computing power of
wireless sensor nodes,the amount of fake data should be added as low as possibl
There has been an extensive study ofthe approaches to protectthe privacy of
residents in a smarthome environment.These solutions are mainly based on a fixed
frequency orprobability models,thus having the majordrawbacks like delaying in
reporting the realevents untilthe nextscheduled transmission.For smarthome sce-
narios, such delay of reporting real sensed data can cause the degradation of
of service (QoS) in many applications [5].Some of the applications like intelligent
sensing, the delay can generally not be tolerated, where the states of the sen
be received in a realtimely fashion for making the corresponding responses.As the
delay problem isconcerned,Park etal. proposed an improved method based on
behavioral semantics. But the method heavily depends on the accuracy of pre
the prediction ofthe nextactivity providesan inaccurate answer,the added fake
messages will not be enough to affect the statistical analysis. In this paper, w
an improved method to resist the side channel attacks based on logistic regre
can be adapted to the network state.Thatis, when the traffic is heavy and no ADL
happens, the frequency of adding fake data should be automatically reduced
real event occurs,right time will be chosen to add noise to protect the real event
The rest of this paper is organized as follows. In Sect.2, we review some existing
solutions. In Sect.3, we describe our method in detail. In Sect.4, we will compare our
method to some othersolutions.In Sect.5, we have given the conclusion ofthis
approach.
2 Related Work
The ConstRate (Sending packets at a fixed frequency) model, all the sensor n
the packets according to the same transmission intervals.Thus,the realevents must
send the packets until the next transmission. So the method can achieve the
work to resistthe static analysis attack.Obviously,the ConstRate modelhas a con-
genital deficiency: the delay depends on the transmission interval which is ha
interval.Also it is difficultto determine an appropriate transmission intervalin the
A Method for Countering Snooping-Based Side Channel Attacks201

ConstRate Model.The delay will vary with the time interval.When the time interval
increases,the delay time willalso increase.And the amountof fake messages and
additional energy consumption will be increased significantly.
Shao et al. proposed the FitProbRate model that aims to improve the deficien
ConstRate model. The core idea is to make the intervals follow the specific prob
distribution.When a realeventoccurred,the algorithm willstartlooking for a mini-
mum interval which obey the distribution of index distribution to send. When the
event is sparse, the FitProbRate model will get a good performance, and compar
the ConstRate modelthe delay willbe reduced.On the contrary,the realeventtrig-
gered frequently,the delay will bigger than other models.
Park etal. proposed a modelwhich based on adding severalfake packets to the
transmission sequence [6].The modeladds fake packets lie on the events thatwill
happen in the future.The first step is to forecast the activity through the status of th
sensor nodes and then the fake messages will be generated according to the pre
Even an attacker has the ability to listen to the transmission of all the sensors, it
only predict the wrong ADLs. However, the shortcoming of the model is that the
depends on the answer of the prediction. If the prediction model gives a wrong f
the fake packets will pall on the protection of the ADLs. Obviously, the stability o
model is lower than these two models mentioned above.
The purpose of adding fake packets to the transmission sequence is to make
attacker can’t pick out the fake packets from all the RF radios. For the top two m
above, the interval of all the packets is obey to the same distribution. It is assum
the attackerhave the ability to listen to the RF radio ofthe whole wireless sensor
network.And make the modeleffectively,the transmission sequence musthave the
significant confidence to make sure that the adversary couldn’t determine the re
is contained in which intervals [7]. That is, if the transmission sequence which co
the fake packets in sending real messages has the sufficient randomness, the ad
cannot recognize the fake data from the real messages, and the ADLs of the res
will be protected. In our method, we have made enough randomness between fa
real data to ensure the attacker couldn’t recognize the fake messages. As for th
traffic is concerned,the more closerto the sink node,the largerdata is needed to
forward.If all the sensors send the packets follow the same distribution,the sensor
node near the sink node will be too heavy to forward packets. Therefore, it is ne
to make the sensor node sends fake data packets adaptively according to the ne
status.
Considering the particularity of the wireless sensor network and the sensitivit
the smarthome,it is importantto think overthe privacy,energy consumption and
latency of the WSN while designing the noisy based privacy protection models. F
effect of privacy protection, the noise data should not be recognized, but also m
correctrecognition rate of the behavior low enough.In other words,either the iden-
tification of the behavior should be wrong, or can’t recognize the true behavior.
energy consumption,it cannotbe a good privacy protection model,if the implemen-
tation of the modelgreatly reduces the lifetime of the WSN.We should consider the
average of traffic load to prolong the lifetime of the sensor network. Latency is t
indicator of the QoS. If the latency is too long, it can lose the meaning of intellige
As for the delay, a good model should make the delay as small as possible. Espe
202 J. He et al.
increases,the delay time willalso increase.And the amountof fake messages and
additional energy consumption will be increased significantly.
Shao et al. proposed the FitProbRate model that aims to improve the deficien
ConstRate model. The core idea is to make the intervals follow the specific prob
distribution.When a realeventoccurred,the algorithm willstartlooking for a mini-
mum interval which obey the distribution of index distribution to send. When the
event is sparse, the FitProbRate model will get a good performance, and compar
the ConstRate modelthe delay willbe reduced.On the contrary,the realeventtrig-
gered frequently,the delay will bigger than other models.
Park etal. proposed a modelwhich based on adding severalfake packets to the
transmission sequence [6].The modeladds fake packets lie on the events thatwill
happen in the future.The first step is to forecast the activity through the status of th
sensor nodes and then the fake messages will be generated according to the pre
Even an attacker has the ability to listen to the transmission of all the sensors, it
only predict the wrong ADLs. However, the shortcoming of the model is that the
depends on the answer of the prediction. If the prediction model gives a wrong f
the fake packets will pall on the protection of the ADLs. Obviously, the stability o
model is lower than these two models mentioned above.
The purpose of adding fake packets to the transmission sequence is to make
attacker can’t pick out the fake packets from all the RF radios. For the top two m
above, the interval of all the packets is obey to the same distribution. It is assum
the attackerhave the ability to listen to the RF radio ofthe whole wireless sensor
network.And make the modeleffectively,the transmission sequence musthave the
significant confidence to make sure that the adversary couldn’t determine the re
is contained in which intervals [7]. That is, if the transmission sequence which co
the fake packets in sending real messages has the sufficient randomness, the ad
cannot recognize the fake data from the real messages, and the ADLs of the res
will be protected. In our method, we have made enough randomness between fa
real data to ensure the attacker couldn’t recognize the fake messages. As for th
traffic is concerned,the more closerto the sink node,the largerdata is needed to
forward.If all the sensors send the packets follow the same distribution,the sensor
node near the sink node will be too heavy to forward packets. Therefore, it is ne
to make the sensor node sends fake data packets adaptively according to the ne
status.
Considering the particularity of the wireless sensor network and the sensitivit
the smarthome,it is importantto think overthe privacy,energy consumption and
latency of the WSN while designing the noisy based privacy protection models. F
effect of privacy protection, the noise data should not be recognized, but also m
correctrecognition rate of the behavior low enough.In other words,either the iden-
tification of the behavior should be wrong, or can’t recognize the true behavior.
energy consumption,it cannotbe a good privacy protection model,if the implemen-
tation of the modelgreatly reduces the lifetime of the WSN.We should consider the
average of traffic load to prolong the lifetime of the sensor network. Latency is t
indicator of the QoS. If the latency is too long, it can lose the meaning of intellige
As for the delay, a good model should make the delay as small as possible. Espe
202 J. He et al.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

in the automatic adjudication environment,the sink node use the long delayed mes-
sages is meaningless.
3 Proposed Method
In this section, we have introduced our method. The logistic regression will be
judge whetherthe fake messages should be sentor not,and named as hypothesis
function. At first, the sensor node will acquire the current state, and normaliz
by a simple process. Then, input the processed data to the hypothesis functio
whetherto send the fake message.For each sensornode,the parametersof the
hypothesis function will be different. And the different parameter will be train
sink node through supervised learning.
At the very beginning of our method. All of the sensor nodes in the sensor
will send fake messages with a fixed time-window. The detailed procedure is
in Fig.1. The sensor node needs three variables to plug into the hypothesis fu
determine whether the fake data should be sent or not. These three variables
state, time and send density, represented by x1, x2, x3. We collected the traffic state and
send density in the period of the block time.We presentthe real-time transmission
times as TT, which consists of the send times of themselves and the forwardin
from other sensor nodes. And we use TT to divide by TrMax to represent the c
traffic situation, where the TrMax is the max transmission times of all the sen
in the block time. In order to unify the time, we map the current timestamp to
of [0,24], and presents as x2. As for the send density, we use the Send Times (ST) t
divided by BlockMax to represent the send density, where the BlockMax is the
interval divided by time-window. When these three parameters are collected,
could be calculated by the hypothesis function.If the ANS is greater than 0.5,fake
Fig. 1. Sensor node checks for sending fake messages
A Method for Countering Snooping-Based Side Channel Attacks203
sages is meaningless.
3 Proposed Method
In this section, we have introduced our method. The logistic regression will be
judge whetherthe fake messages should be sentor not,and named as hypothesis
function. At first, the sensor node will acquire the current state, and normaliz
by a simple process. Then, input the processed data to the hypothesis functio
whetherto send the fake message.For each sensornode,the parametersof the
hypothesis function will be different. And the different parameter will be train
sink node through supervised learning.
At the very beginning of our method. All of the sensor nodes in the sensor
will send fake messages with a fixed time-window. The detailed procedure is
in Fig.1. The sensor node needs three variables to plug into the hypothesis fu
determine whether the fake data should be sent or not. These three variables
state, time and send density, represented by x1, x2, x3. We collected the traffic state and
send density in the period of the block time.We presentthe real-time transmission
times as TT, which consists of the send times of themselves and the forwardin
from other sensor nodes. And we use TT to divide by TrMax to represent the c
traffic situation, where the TrMax is the max transmission times of all the sen
in the block time. In order to unify the time, we map the current timestamp to
of [0,24], and presents as x2. As for the send density, we use the Send Times (ST) t
divided by BlockMax to represent the send density, where the BlockMax is the
interval divided by time-window. When these three parameters are collected,
could be calculated by the hypothesis function.If the ANS is greater than 0.5,fake
Fig. 1. Sensor node checks for sending fake messages
A Method for Countering Snooping-Based Side Channel Attacks203
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

massage should be sentaftera random time interval.Otherwise the algorithm will
judge whether to send the messages at long intervals, if so, the time-window wo
increased.Once the real data is sent,the time-window will be recovered again.
Figure 2 Shows the detail of the learning algorithm. Each sensor node has its
different parameters, the learning algorithm will deal with all the data and calcu
for each sensor node respectively.As for each dataset from different sensor nodes are
concerned.Before the learning algorithm,the received data should be labeled.The
main purpose of labels is to mark the fake data, labeled with 1 indicates that fak
should be sent, labeled with 0 indicates that the fake data should not be sent. A
learning algorithm, Firstly, we calculate the cost by using the square difference m
just as the J(h) in the Algorithm 2, the m in J(h) is the number of training samples
then the gradient descent algorithm is used to find the h that makes the J(h) obt
global minimum [9]. When the learning algorithm is completed, the h should be
out to the sensor node and should be plugged into the hypothesis function.
4 Evaluation
In this section, we will first introduce the method and settings of the experiment
then will do the experiment to compare the effect of privacy protection and dela
the ConstRate Model and FitProbRate Model. We have used the public dataset re
to accurate activity recognition in a Home Setting [8] for our experiment.
In order to evaluate the effects of the privacy,we studied the side channelattack
method in a smart home. The common step of the side channel attack is to clust
sensor data to the reasoning for the number of rooms in the home. The purpose
FitProbRate model and ConstRate model are to disturb the attacker to cluster th
to a wrong classification. In our experiment we use the cluster accuracy to evalu
protection model[5]. If the clustering accuracy is approximate to 1,the clustering
results will equal to the number of rooms and the sensor distribution is the same
Fig. 2. Sink node training sensor data
204 J. He et al.
judge whether to send the messages at long intervals, if so, the time-window wo
increased.Once the real data is sent,the time-window will be recovered again.
Figure 2 Shows the detail of the learning algorithm. Each sensor node has its
different parameters, the learning algorithm will deal with all the data and calcu
for each sensor node respectively.As for each dataset from different sensor nodes are
concerned.Before the learning algorithm,the received data should be labeled.The
main purpose of labels is to mark the fake data, labeled with 1 indicates that fak
should be sent, labeled with 0 indicates that the fake data should not be sent. A
learning algorithm, Firstly, we calculate the cost by using the square difference m
just as the J(h) in the Algorithm 2, the m in J(h) is the number of training samples
then the gradient descent algorithm is used to find the h that makes the J(h) obt
global minimum [9]. When the learning algorithm is completed, the h should be
out to the sensor node and should be plugged into the hypothesis function.
4 Evaluation
In this section, we will first introduce the method and settings of the experiment
then will do the experiment to compare the effect of privacy protection and dela
the ConstRate Model and FitProbRate Model. We have used the public dataset re
to accurate activity recognition in a Home Setting [8] for our experiment.
In order to evaluate the effects of the privacy,we studied the side channelattack
method in a smart home. The common step of the side channel attack is to clust
sensor data to the reasoning for the number of rooms in the home. The purpose
FitProbRate model and ConstRate model are to disturb the attacker to cluster th
to a wrong classification. In our experiment we use the cluster accuracy to evalu
protection model[5]. If the clustering accuracy is approximate to 1,the clustering
results will equal to the number of rooms and the sensor distribution is the same
Fig. 2. Sink node training sensor data
204 J. He et al.
clustering results. In contrast, if the clustering results are completely inconsis
the actualroom distribution,the ADL willbe perfectly protected.Consequently,the
lowerthe clusteraccuracy willbe, the bettereffectof privacy protection willbe
achieved. In addition,the Ratio is calculated by the number of fake messages div
by the number of real messages.
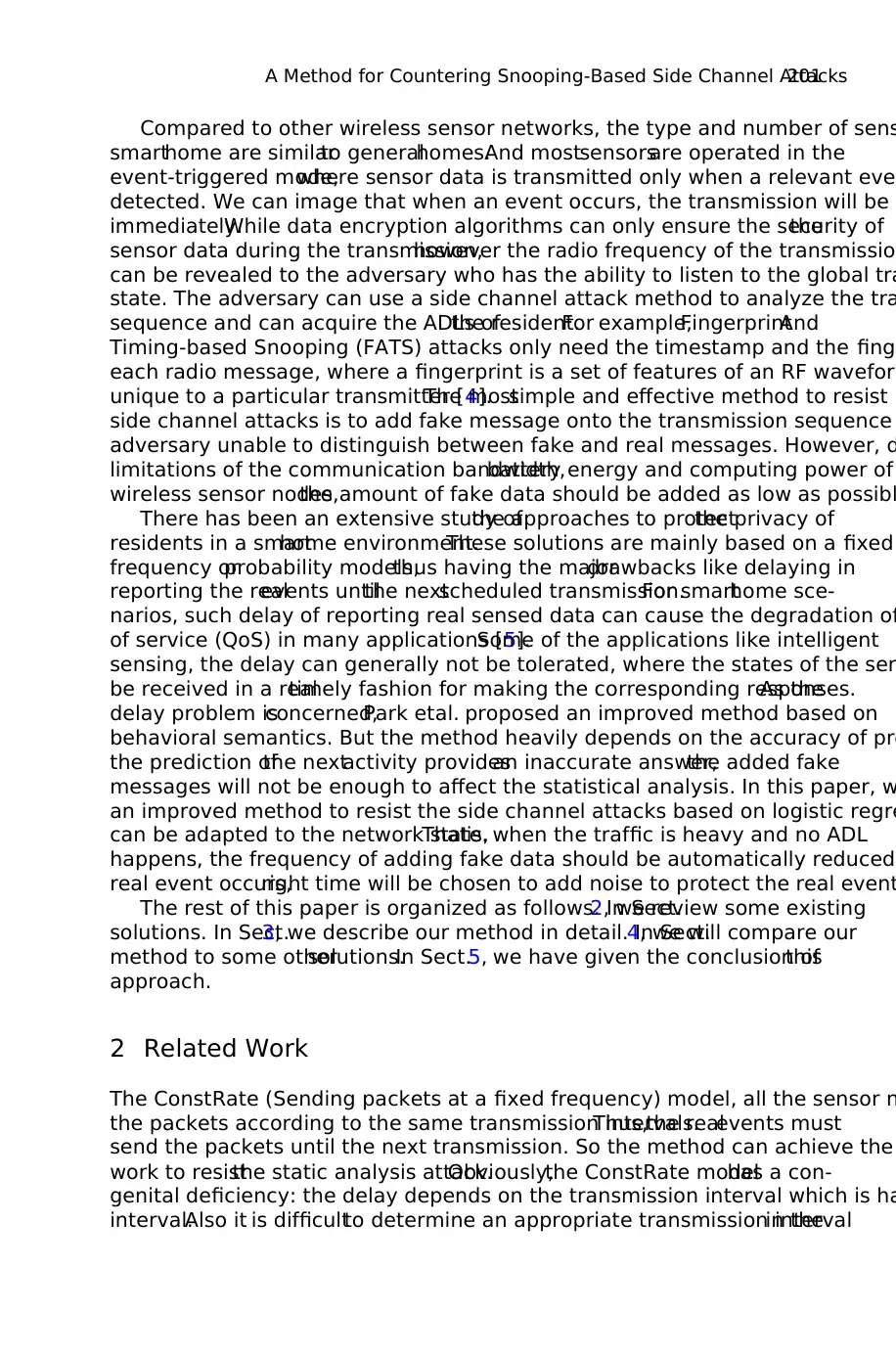
As shown in Fig.3, with the incensement of the Ratio,the clustering accuracy of
these three model decreased gradually. The clustering accuracy of the ConstR
maintained at a low level.Our method and the FitProbRate model are affected by
Ratio,because when the Ratio is increased,the clustering accuracy is declined,And
when the ratio is in the range of (5,15),the clustering accuracy between our metho
and FitProbRate modelhas a wide margin,and the FitProbRate modelhas a good
performance than ourmethod.When the amountof fake messages is low,the Fit-
ProbRate model has been well-distributed than our method. So our method is
accuracy than the FitProbRate modelin terms of clustering accuracy in the range of
(5,15).When the Ratio is greater than 15,the gap between our method and FitPro-
bRate model is very small. Also, we have ensured that when the clustering ac
lower than 0.4,the side channel attack will be hard to analyze the ADL.
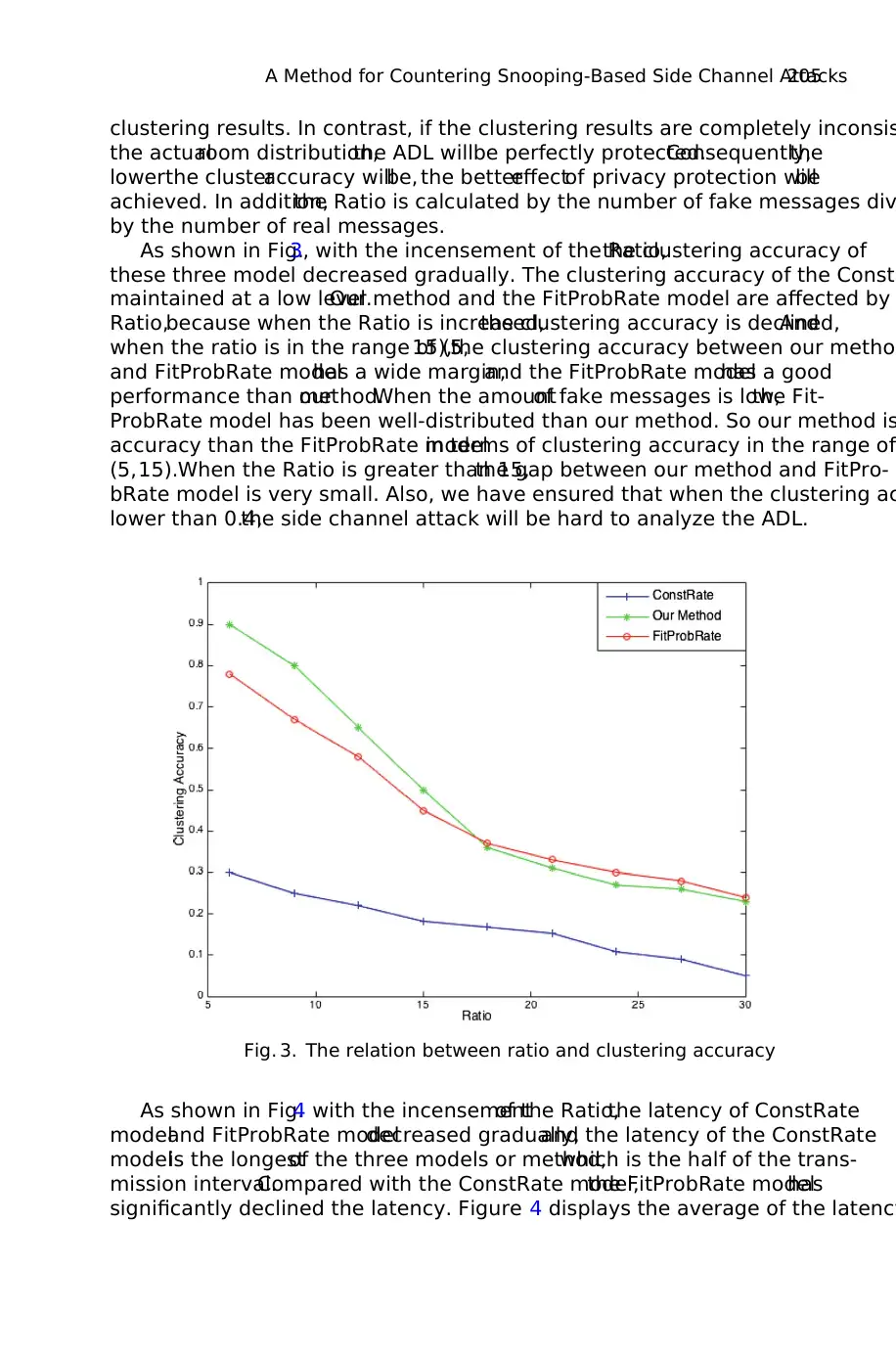
As shown in Fig.4 with the incensementof the Ratio,the latency of ConstRate
modeland FitProbRate modeldecreased gradually,and the latency of the ConstRate
modelis the longestof the three models or method,which is the half of the trans-
mission interval.Compared with the ConstRate model,the FitProbRate modelhas
significantly declined the latency. Figure 4 displays the average of the latency
Fig. 3. The relation between ratio and clustering accuracy
A Method for Countering Snooping-Based Side Channel Attacks205
the actualroom distribution,the ADL willbe perfectly protected.Consequently,the
lowerthe clusteraccuracy willbe, the bettereffectof privacy protection willbe
achieved. In addition,the Ratio is calculated by the number of fake messages div
by the number of real messages.
As shown in Fig.3, with the incensement of the Ratio,the clustering accuracy of
these three model decreased gradually. The clustering accuracy of the ConstR
maintained at a low level.Our method and the FitProbRate model are affected by
Ratio,because when the Ratio is increased,the clustering accuracy is declined,And
when the ratio is in the range of (5,15),the clustering accuracy between our metho
and FitProbRate modelhas a wide margin,and the FitProbRate modelhas a good
performance than ourmethod.When the amountof fake messages is low,the Fit-
ProbRate model has been well-distributed than our method. So our method is
accuracy than the FitProbRate modelin terms of clustering accuracy in the range of
(5,15).When the Ratio is greater than 15,the gap between our method and FitPro-
bRate model is very small. Also, we have ensured that when the clustering ac
lower than 0.4,the side channel attack will be hard to analyze the ADL.
As shown in Fig.4 with the incensementof the Ratio,the latency of ConstRate
modeland FitProbRate modeldecreased gradually,and the latency of the ConstRate
modelis the longestof the three models or method,which is the half of the trans-
mission interval.Compared with the ConstRate model,the FitProbRate modelhas
significantly declined the latency. Figure 4 displays the average of the latency
Fig. 3. The relation between ratio and clustering accuracy
A Method for Countering Snooping-Based Side Channel Attacks205
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
three model,the latency of the FitProbRate model related to the density of the tran
mission, when the transmission frequency of the real event is raised up, the late
be increased. On the contrary, when the transmission is sparse, the latency time
declined.Consequently,the latency of the FitProbRate modelis affected by the fre-
quency of the real events.
5 Conclusion and Future Work
In this paper,we have proposed a new method to resistthe side channelattack.
Compared with other models, our method has the advantage of adaptive networ
low latency and low power consumption.In the contextof the smarthome environ-
ment, when the user goes to work and when comes back to home from work or
go to sleep etc., these are likely to be the scope of privacy protection. The attac
infer these living habits through analyzing the density of the transmission seque
the future, we plan to make our method fit the daily routines to the popular rout
almost people. Even if the attacker gains the daily routines, also cannot distingu
routines of the particular prey. In a word, the privacy plays an essential role in th
home,we should pay more attention to the privacy protection in smart home.
Acknowledgement.The work in this paperhas been supported by Beijing NaturalScience
Foundation (4142008),National Nature Science Foundation of China (61272500) and Nationa
High-tech R&D Program (863 Program) (2015AA017204).
Fig. 4. The relation between ratio and latency
206 J. He et al.
mission, when the transmission frequency of the real event is raised up, the late
be increased. On the contrary, when the transmission is sparse, the latency time
declined.Consequently,the latency of the FitProbRate modelis affected by the fre-
quency of the real events.
5 Conclusion and Future Work
In this paper,we have proposed a new method to resistthe side channelattack.
Compared with other models, our method has the advantage of adaptive networ
low latency and low power consumption.In the contextof the smarthome environ-
ment, when the user goes to work and when comes back to home from work or
go to sleep etc., these are likely to be the scope of privacy protection. The attac
infer these living habits through analyzing the density of the transmission seque
the future, we plan to make our method fit the daily routines to the popular rout
almost people. Even if the attacker gains the daily routines, also cannot distingu
routines of the particular prey. In a word, the privacy plays an essential role in th
home,we should pay more attention to the privacy protection in smart home.
Acknowledgement.The work in this paperhas been supported by Beijing NaturalScience
Foundation (4142008),National Nature Science Foundation of China (61272500) and Nationa
High-tech R&D Program (863 Program) (2015AA017204).
Fig. 4. The relation between ratio and latency
206 J. He et al.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
1. Theoharidou, M., Tsalis, N., Gritzalis, D.: Smart Home Solutions: Privacy Issues. Han
of Smart Homes,Health Care and Well-Being,pp.1–14.Springer,Cham (2014)
2. Alami,A., Benhlima,L., Bah,S.: An overview of privacy preserving techniques in smart
home wireless sensornetworks.In: 10th InternationalConference on IntelligentSystems:
Theories and Applications,pp.1–4.IEEE Press,Rabat (2015)
3. Sanchez,I., Satta,R., Fovino,I.N., Baldini,G.: Privacy leakages in smarthome wireless
technologies. In: International Carnahan Conference on Security Technology, pp. 1
Press,Rome (2014)
4. Srinivasan,V., Stankovic,J., Whitehouse,K.: Protecting yourdaily in-homeactivity
information from a wireless snooping attack.In: InternationalConference on Ubiquitous
Computing,pp.202–211.ACM Press,Seoul (2008)
5. Park, H., Park, T., Sang, H.S.: A comparative study of privacy protection methods fo
home environments.Int.J. Smart Home 7,1–12 (2013)
6. Park, H., Basaran, C., Park, T., Son, S.H.: Energy-efficient privacy protection for sma
environments using behavioral semantics.J. Sens.14,16235–16257 (2014)
7. Yang,Y., Shao,M., Zhu,S., Cao,G.: Towards statistically strong source anonymity for
sensornetworks.In: 27th Conferenceon ComputerCommunications.pp. 51–55.
IEEE INFOCOM,Phoenix (2008)
8. Van Kasteren,T., Noulas,A., Englebienne,G.: Accurate activity recognition in a home
setting.In: International Conference on Ubiquitous Computing,pp.1–9.ACM Press,Seoul
(2008)
9. Song, Y., Cai, Q., Nie, F., Zhang, C.: Semi-supervised additive logistic regression: a
descent solution.J. Tsinghua Sci.Technol.12,638–646 (2007)
A Method for Countering Snooping-Based Side Channel Attacks207
1. Theoharidou, M., Tsalis, N., Gritzalis, D.: Smart Home Solutions: Privacy Issues. Han
of Smart Homes,Health Care and Well-Being,pp.1–14.Springer,Cham (2014)
2. Alami,A., Benhlima,L., Bah,S.: An overview of privacy preserving techniques in smart
home wireless sensornetworks.In: 10th InternationalConference on IntelligentSystems:
Theories and Applications,pp.1–4.IEEE Press,Rabat (2015)
3. Sanchez,I., Satta,R., Fovino,I.N., Baldini,G.: Privacy leakages in smarthome wireless
technologies. In: International Carnahan Conference on Security Technology, pp. 1
Press,Rome (2014)
4. Srinivasan,V., Stankovic,J., Whitehouse,K.: Protecting yourdaily in-homeactivity
information from a wireless snooping attack.In: InternationalConference on Ubiquitous
Computing,pp.202–211.ACM Press,Seoul (2008)
5. Park, H., Park, T., Sang, H.S.: A comparative study of privacy protection methods fo
home environments.Int.J. Smart Home 7,1–12 (2013)
6. Park, H., Basaran, C., Park, T., Son, S.H.: Energy-efficient privacy protection for sma
environments using behavioral semantics.J. Sens.14,16235–16257 (2014)
7. Yang,Y., Shao,M., Zhu,S., Cao,G.: Towards statistically strong source anonymity for
sensornetworks.In: 27th Conferenceon ComputerCommunications.pp. 51–55.
IEEE INFOCOM,Phoenix (2008)
8. Van Kasteren,T., Noulas,A., Englebienne,G.: Accurate activity recognition in a home
setting.In: International Conference on Ubiquitous Computing,pp.1–9.ACM Press,Seoul
(2008)
9. Song, Y., Cai, Q., Nie, F., Zhang, C.: Semi-supervised additive logistic regression: a
descent solution.J. Tsinghua Sci.Technol.12,638–646 (2007)
A Method for Countering Snooping-Based Side Channel Attacks207
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



