System Engineering for Managers: Digital Migration Security Report
VerifiedAdded on 2020/02/19
|8
|2090
|53
Report
AI Summary
This report provides a detailed analysis of the security challenges associated with digital transformation, a critical process for modern businesses. It identifies the key problem areas, with a specific focus on security risks, which organizations report as their biggest obstacle. The report examines both internal and external security threats, including data theft, hacking, data loss, and accidental data deletion. It delves into current trends in mitigating these security problems, emphasizing the importance of effective planning, robust security policies, and the acquisition of appropriate hardware and software. The report underscores the need for education, strong security measures, network monitoring, and the use of consultants to ensure a secure digital migration. The conclusion highlights the significance of proactive security measures to safeguard data and maintain operational continuity during and after digital transformation.

SYSTEM ENGINEERING FOR MANAGERS
Name
Date
Name
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
This paper identifies the theme of digital migration, of which the major problem is the issue of
security, and discussed them using the rich picture model. Security risks and threats is reported by
55% of organizations as the biggest challenge to digital migration. Security challenges are external
and internal and the different tends in resolving the issue is discussed in this paper
This paper identifies the theme of digital migration, of which the major problem is the issue of
security, and discussed them using the rich picture model. Security risks and threats is reported by
55% of organizations as the biggest challenge to digital migration. Security challenges are external
and internal and the different tends in resolving the issue is discussed in this paper

Table of Contents
Abstract.................................................................................................................................................2
Introduction..........................................................................................................................................3
The Problem of Security in Digital Transformation.............................................................................3
Current trends in mitigating/ managing security problems in digital migration..................................5
Conclusion............................................................................................................................................6
References Used...................................................................................................................................7
Abstract.................................................................................................................................................2
Introduction..........................................................................................................................................3
The Problem of Security in Digital Transformation.............................................................................3
Current trends in mitigating/ managing security problems in digital migration..................................5
Conclusion............................................................................................................................................6
References Used...................................................................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
businesses and organizations have been compelled to adapt to changes in technology and the
business environment in order adapt, improve its processes and systems, serve customers better, and
reduce optimize costs. This is necessitated by a business environment that has become increasingly
competitive where firms must adapt or go bust. One of the ways in which organizations adapt and
change is through digital transformation ('i-Scoop', 2015). Digital transformation entails the
transformation of the organizational activities within a business where the competencies, processes,
and models as well as activities are profoundly transformed in order to leverage the opportunities
and changes afforded by a combination of digital technologies and their impact that are sped-up
across the organization and the society in general in a manner that is prioritized and strategic,
bearing in mind present and future shifts (Mazzone, 2014), . While digital transformation has
several benefits for a business, it has some challenges and problems, and among the most common
and profound ones is security problems, for instance when migrating to the cloud. This paper
discusses security woes as a major problem in the digital transformation theme, using the rich
picture model.
The Problem of Security in Digital Transformation
According to DeNisco (2017), research indicates that more than half (55%) of firms allude to
security being their biggest challenge with respect to digital transformation. Yet digital
transformation is almost an obligation for most businesses. The causal loop diagram below
illustrates how security is a challenge in digital transformation;
businesses and organizations have been compelled to adapt to changes in technology and the
business environment in order adapt, improve its processes and systems, serve customers better, and
reduce optimize costs. This is necessitated by a business environment that has become increasingly
competitive where firms must adapt or go bust. One of the ways in which organizations adapt and
change is through digital transformation ('i-Scoop', 2015). Digital transformation entails the
transformation of the organizational activities within a business where the competencies, processes,
and models as well as activities are profoundly transformed in order to leverage the opportunities
and changes afforded by a combination of digital technologies and their impact that are sped-up
across the organization and the society in general in a manner that is prioritized and strategic,
bearing in mind present and future shifts (Mazzone, 2014), . While digital transformation has
several benefits for a business, it has some challenges and problems, and among the most common
and profound ones is security problems, for instance when migrating to the cloud. This paper
discusses security woes as a major problem in the digital transformation theme, using the rich
picture model.
The Problem of Security in Digital Transformation
According to DeNisco (2017), research indicates that more than half (55%) of firms allude to
security being their biggest challenge with respect to digital transformation. Yet digital
transformation is almost an obligation for most businesses. The causal loop diagram below
illustrates how security is a challenge in digital transformation;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
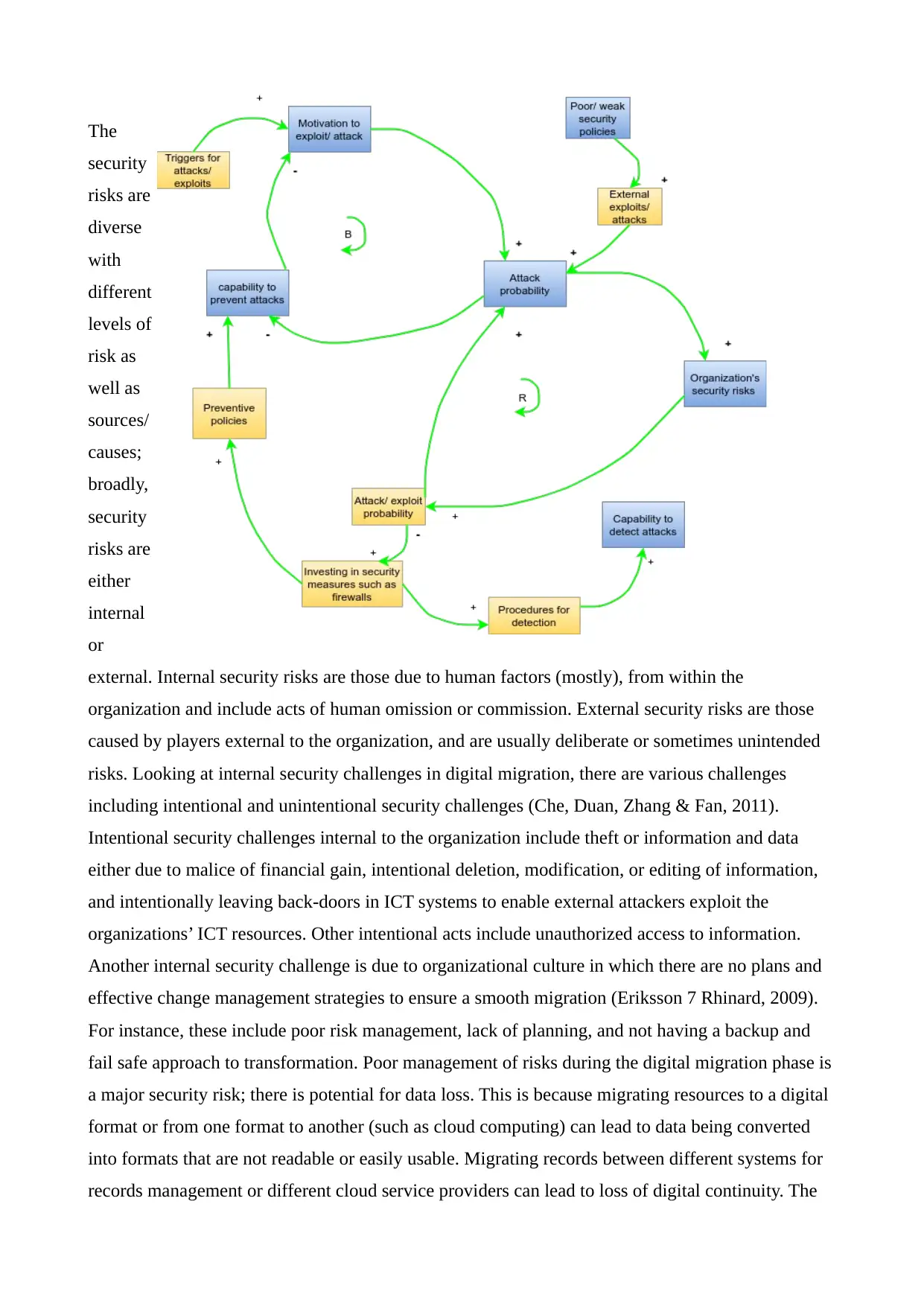
The
security
risks are
diverse
with
different
levels of
risk as
well as
sources/
causes;
broadly,
security
risks are
either
internal
or
external. Internal security risks are those due to human factors (mostly), from within the
organization and include acts of human omission or commission. External security risks are those
caused by players external to the organization, and are usually deliberate or sometimes unintended
risks. Looking at internal security challenges in digital migration, there are various challenges
including intentional and unintentional security challenges (Che, Duan, Zhang & Fan, 2011).
Intentional security challenges internal to the organization include theft or information and data
either due to malice of financial gain, intentional deletion, modification, or editing of information,
and intentionally leaving back-doors in ICT systems to enable external attackers exploit the
organizations’ ICT resources. Other intentional acts include unauthorized access to information.
Another internal security challenge is due to organizational culture in which there are no plans and
effective change management strategies to ensure a smooth migration (Eriksson 7 Rhinard, 2009).
For instance, these include poor risk management, lack of planning, and not having a backup and
fail safe approach to transformation. Poor management of risks during the digital migration phase is
a major security risk; there is potential for data loss. This is because migrating resources to a digital
format or from one format to another (such as cloud computing) can lead to data being converted
into formats that are not readable or easily usable. Migrating records between different systems for
records management or different cloud service providers can lead to loss of digital continuity. The
security
risks are
diverse
with
different
levels of
risk as
well as
sources/
causes;
broadly,
security
risks are
either
internal
or
external. Internal security risks are those due to human factors (mostly), from within the
organization and include acts of human omission or commission. External security risks are those
caused by players external to the organization, and are usually deliberate or sometimes unintended
risks. Looking at internal security challenges in digital migration, there are various challenges
including intentional and unintentional security challenges (Che, Duan, Zhang & Fan, 2011).
Intentional security challenges internal to the organization include theft or information and data
either due to malice of financial gain, intentional deletion, modification, or editing of information,
and intentionally leaving back-doors in ICT systems to enable external attackers exploit the
organizations’ ICT resources. Other intentional acts include unauthorized access to information.
Another internal security challenge is due to organizational culture in which there are no plans and
effective change management strategies to ensure a smooth migration (Eriksson 7 Rhinard, 2009).
For instance, these include poor risk management, lack of planning, and not having a backup and
fail safe approach to transformation. Poor management of risks during the digital migration phase is
a major security risk; there is potential for data loss. This is because migrating resources to a digital
format or from one format to another (such as cloud computing) can lead to data being converted
into formats that are not readable or easily usable. Migrating records between different systems for
records management or different cloud service providers can lead to loss of digital continuity. The

initial reason to migrate data or migrate to a digital platform such as the cloud could be achieve data
security; however, this is fraught with risks that must carefully be managed. There is also a risk of
migration time as it can take weeks or even months, if the data volumes are too large. Failure to
properly backup to have a copy of that data, on the assumption that the migration will be successful
and take a short time will adversely affect operations. This is because the organization will not be
able to access and/ or use the data during the period of migration, resulting in downtime, severely
affecting operations. Compatibility is also a significant security risk during migration as files are at
risk of being corrupted and rendered unusable when applications are incompatible, especially
between different cloud service providers (Aleem & Sprott 2013), (Barateiro, Antunes, Freitas &
Borbinha, 2010). Unintentional internal security challenges include accidental deletion,
modification, or editing of data by staff, such as information resident on company servers or cloud
information. Another unintentional risk includes using applications that do not serve the purposes
of the organization are are ill-suited for the company’s digital migration objectives. This extends to
using cloud service providers without understanding the impact of such a move with regard to data
security, accessibility, and data loss. External security threats to digital migration include malicious
attacks to data or company systems; when companies migrate or are migrating to a digital
environment, they seldom have the right security experience. As such, systems are designed without
requisite security measures including backups, using antimalware software, and implementing
firewalls. Another security risk is the concept of employees coming to work with their own devices;
if they have machines infected with malware, these will automatically be installed into the
organizations’ network and cause adverse effects such as data deletion, data theft, or denial of
access as in ransomware attacks. In modern times, digital migration has often entailed cloud
computing where organizations use applications that can be accessed on the go. These applications
are implemented with single sign on (SSO) features, that amplify threats in terms of being hacked/
compromised or accidental mistakes that result in hackers gaining access to organization ICT
resources, including those at the cloud. Organizations also face challenges from malicious cyber
attacks, that include denial of service (DoS) and distributed denial of service attacks (DdoS),
spamming, malware, and data/ identity theft. Further, external security risks in digital migration
relate to service and application/ software providers, such as using cloud providers without alternate
geographically distributed backups and data centers, so that a disaster on their data center can lead
to an organization loosing its data. Other security risks are due to the complexity of data and device
ownership, for instance cloud computing and devices that read credit cards; the organization owns
the data, but another firm owns the devices that read and process payments, while the information
belongs to the customer. Cloud services entail the organization handing over its data and with it,
total control over its data and other ICT resources to third parties. The organization can use more
security; however, this is fraught with risks that must carefully be managed. There is also a risk of
migration time as it can take weeks or even months, if the data volumes are too large. Failure to
properly backup to have a copy of that data, on the assumption that the migration will be successful
and take a short time will adversely affect operations. This is because the organization will not be
able to access and/ or use the data during the period of migration, resulting in downtime, severely
affecting operations. Compatibility is also a significant security risk during migration as files are at
risk of being corrupted and rendered unusable when applications are incompatible, especially
between different cloud service providers (Aleem & Sprott 2013), (Barateiro, Antunes, Freitas &
Borbinha, 2010). Unintentional internal security challenges include accidental deletion,
modification, or editing of data by staff, such as information resident on company servers or cloud
information. Another unintentional risk includes using applications that do not serve the purposes
of the organization are are ill-suited for the company’s digital migration objectives. This extends to
using cloud service providers without understanding the impact of such a move with regard to data
security, accessibility, and data loss. External security threats to digital migration include malicious
attacks to data or company systems; when companies migrate or are migrating to a digital
environment, they seldom have the right security experience. As such, systems are designed without
requisite security measures including backups, using antimalware software, and implementing
firewalls. Another security risk is the concept of employees coming to work with their own devices;
if they have machines infected with malware, these will automatically be installed into the
organizations’ network and cause adverse effects such as data deletion, data theft, or denial of
access as in ransomware attacks. In modern times, digital migration has often entailed cloud
computing where organizations use applications that can be accessed on the go. These applications
are implemented with single sign on (SSO) features, that amplify threats in terms of being hacked/
compromised or accidental mistakes that result in hackers gaining access to organization ICT
resources, including those at the cloud. Organizations also face challenges from malicious cyber
attacks, that include denial of service (DoS) and distributed denial of service attacks (DdoS),
spamming, malware, and data/ identity theft. Further, external security risks in digital migration
relate to service and application/ software providers, such as using cloud providers without alternate
geographically distributed backups and data centers, so that a disaster on their data center can lead
to an organization loosing its data. Other security risks are due to the complexity of data and device
ownership, for instance cloud computing and devices that read credit cards; the organization owns
the data, but another firm owns the devices that read and process payments, while the information
belongs to the customer. Cloud services entail the organization handing over its data and with it,
total control over its data and other ICT resources to third parties. The organization can use more
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

than a single cloud services provider, which multiplies the risk in the event that the data is breached.
However, using multiple service providers for cloud security is a ‘double edged sword’ since it
provides an additional security feature in terms of backups. A breach at any level will adversely
impact the entire ecosystem (Tassev, 2017)
Current trends in mitigating/ managing security problems in digital migration
The first step is to ensure digital migration planning and management that is effective in which the
organization sensitizes the migration plan, involving all employees. Internal risks can be mitigated
through education and sensitization as well as implementing strong security measures to protect
data, including data encryption, strong and controlled access and authentication, implementing and
updating firewalls, antimalware software, and firmware, and securing network access points
including routers. Network access points such as routers, especially wireless routers, are easy
targets for cyber exploitation if security measures are not undertaken. These should be encrypted,
with encrypted passwords and the firmware updated to ‘harden’ network security. Given the high
risk of internal threats, data access should be limited and strong, possibly two step authentication
used to regulate and restrict access. For cloud migration, firms must ensure the service providers
have security measures including data encryption and geographically dispersed data center backups,
in addition to virtual backups (Barateiro, Antunes, Freitas & Borbinha, 2010). Organizations must
also employ the services of consultants to ensure the software, applications, and hardware to be
acquired are suitable for the purposes of the organizations. External threats can be neutralized using
network monitoring tools to detect malicious activity. Further, strong and tested APIs should be
used to improve security on the network edge (Islam, Fenz, Weippl & Mouratidis, 2017). Mitigation
measures during migration include hiring consultants or data management (and recovery) firms to
manage the migration, starting with creating a copy/ backup of all the data/ ICT resources,
including with virtualization to ensue availability during migration and provide a backup in case of
data loss/ corruption.
Conclusion
Digital migration is a common practice among organizations but which has its problems, a major
one being security challenges. Security problems in digital migration can be internal or external and
either intentional (such as data theft, hacking and data loss) or unintentional (such as mistaken data
deletion and lost encryption keys). Mitigation measures include effective planning in digital
migration, implementing strong policies and measures, and acquiring hardware and software
resources that suit the needs of the organization.
However, using multiple service providers for cloud security is a ‘double edged sword’ since it
provides an additional security feature in terms of backups. A breach at any level will adversely
impact the entire ecosystem (Tassev, 2017)
Current trends in mitigating/ managing security problems in digital migration
The first step is to ensure digital migration planning and management that is effective in which the
organization sensitizes the migration plan, involving all employees. Internal risks can be mitigated
through education and sensitization as well as implementing strong security measures to protect
data, including data encryption, strong and controlled access and authentication, implementing and
updating firewalls, antimalware software, and firmware, and securing network access points
including routers. Network access points such as routers, especially wireless routers, are easy
targets for cyber exploitation if security measures are not undertaken. These should be encrypted,
with encrypted passwords and the firmware updated to ‘harden’ network security. Given the high
risk of internal threats, data access should be limited and strong, possibly two step authentication
used to regulate and restrict access. For cloud migration, firms must ensure the service providers
have security measures including data encryption and geographically dispersed data center backups,
in addition to virtual backups (Barateiro, Antunes, Freitas & Borbinha, 2010). Organizations must
also employ the services of consultants to ensure the software, applications, and hardware to be
acquired are suitable for the purposes of the organizations. External threats can be neutralized using
network monitoring tools to detect malicious activity. Further, strong and tested APIs should be
used to improve security on the network edge (Islam, Fenz, Weippl & Mouratidis, 2017). Mitigation
measures during migration include hiring consultants or data management (and recovery) firms to
manage the migration, starting with creating a copy/ backup of all the data/ ICT resources,
including with virtualization to ensue availability during migration and provide a backup in case of
data loss/ corruption.
Conclusion
Digital migration is a common practice among organizations but which has its problems, a major
one being security challenges. Security problems in digital migration can be internal or external and
either intentional (such as data theft, hacking and data loss) or unintentional (such as mistaken data
deletion and lost encryption keys). Mitigation measures include effective planning in digital
migration, implementing strong policies and measures, and acquiring hardware and software
resources that suit the needs of the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References Used
Aleem, A., & Sprott, C. (2013). Let me in the cloud: analysis of the benefit and risk assessment of
cloud platform. JOURNAL OF FINANCIAL CRIME. 20, 6-24.
Barateiro, J., Antunes, G., Freitas, F., & Borbinha, J. (2010). Designing Digital Preservation
Solutions: A Risk Management-Based Approach. International Journal Of Digital Curation, 5(1), 4-
17. http://dx.doi.org/10.2218/ijdc.v5i1.140
Che, J., Duan, Y., Zhang, T., & Fan, J. (2011). Study on the Security Models and Strategies of Cloud
Computing. Procedia Engineering. 23, 586-593.
DeNisco, A. (2017). Report: 55% of companies say security is biggest digital transformation
challenge. TechRepublic. Retrieved 2 September 2017, from
http://www.techrepublic.com/article/report-55-of-companies-say-security-is-biggest-digital-
transformation-challenge/
Eriksson, J., & Rhinard, M. (2009). The Internal-External Security Nexus: Notes on an Emerging
Research Agenda. Cooperation And Conflict. 44, 243-267.
Islam, S., Fenz, S., Weippl, E., & Mouratidis, H. (2017). A Risk Management Framework for Cloud
Migration Decision Support. Journal of Risk and Financial Management. 10, 10.
'i-Scoop'. (2015). Digital transformation: online guide to digital transformation. i-SCOOP.
Retrieved 2 September 2017, from https://www.i-scoop.eu/digital-transformation/
Mazzone, D. (2014). Digital or death: digital transformation - the only choice for business to
survive, smash or conquer. [s.l.], Smashbox Consulting.
Tassev, S. (2017). Migrating to a digitised environment? Consider the security risk | IT News Africa
– Africa's Technology News Leader. Itnewsafrica.com. Retrieved 2 September 2017, from
http://www.itnewsafrica.com/2017/08/migrating-to-a-digitised-environment-consider-the-security-
risk/
Aleem, A., & Sprott, C. (2013). Let me in the cloud: analysis of the benefit and risk assessment of
cloud platform. JOURNAL OF FINANCIAL CRIME. 20, 6-24.
Barateiro, J., Antunes, G., Freitas, F., & Borbinha, J. (2010). Designing Digital Preservation
Solutions: A Risk Management-Based Approach. International Journal Of Digital Curation, 5(1), 4-
17. http://dx.doi.org/10.2218/ijdc.v5i1.140
Che, J., Duan, Y., Zhang, T., & Fan, J. (2011). Study on the Security Models and Strategies of Cloud
Computing. Procedia Engineering. 23, 586-593.
DeNisco, A. (2017). Report: 55% of companies say security is biggest digital transformation
challenge. TechRepublic. Retrieved 2 September 2017, from
http://www.techrepublic.com/article/report-55-of-companies-say-security-is-biggest-digital-
transformation-challenge/
Eriksson, J., & Rhinard, M. (2009). The Internal-External Security Nexus: Notes on an Emerging
Research Agenda. Cooperation And Conflict. 44, 243-267.
Islam, S., Fenz, S., Weippl, E., & Mouratidis, H. (2017). A Risk Management Framework for Cloud
Migration Decision Support. Journal of Risk and Financial Management. 10, 10.
'i-Scoop'. (2015). Digital transformation: online guide to digital transformation. i-SCOOP.
Retrieved 2 September 2017, from https://www.i-scoop.eu/digital-transformation/
Mazzone, D. (2014). Digital or death: digital transformation - the only choice for business to
survive, smash or conquer. [s.l.], Smashbox Consulting.
Tassev, S. (2017). Migrating to a digitised environment? Consider the security risk | IT News Africa
– Africa's Technology News Leader. Itnewsafrica.com. Retrieved 2 September 2017, from
http://www.itnewsafrica.com/2017/08/migrating-to-a-digitised-environment-consider-the-security-
risk/
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




