Analysis of Management Information Systems and Business Applications
VerifiedAdded on 2020/10/22
|17
|5139
|399
Homework Assignment
AI Summary
This assignment provides a comprehensive analysis of Management Information Systems (MIS). It starts with an illustration of a Decision Support System (DSS) and its application at the management level, followed by an analysis of the relationship between MIS components, identifying true and false statements. The assignment recommends different types of information systems for organizations, including Transaction Processing Systems (TPS), DSS, and MIS. It also explores the characteristics and drawbacks of cloud computing, defining databases and comparing DBMS with flat files, and highlighting the importance of data mining tools. Furthermore, the assignment offers suggestions for improving the efficiency of a sandwich shop's business processes and outlines the primary components of a comprehensive CRM system. It also covers e-policies for business protection and authentication technologies for restricting unauthorized access. Finally, the assignment includes new information system trends, the relationship of the Internet and the World Wide Web, the impact of information systems on businesses, challenges and opportunities due to globalization, business objectives of information systems, application of Porter’s Five Forces, and UPS’s embracement of sustainable technologies.

Management
Information System
Information System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Table of Contents
PART A...........................................................................................................................................3
Q-1 a). Voyage' related illustration and type of Information system represented by this and
also describe at which level of organisation, this IS is used........................................................3
b). Analyse the relationship represented between the components below and also identify the
statement true or false in account of such relationship................................................................4
Q-2 Different types of Information system recommended in an organisation............................4
Q-3 a). Characteristics of Cloud computing................................................................................5
b). Drawbacks of Cloud computing with example......................................................................6
Q-4 a). Definition of Database and also describe that DBMS are better system as compared to
Flat files.......................................................................................................................................6
b). Importance of Data mining tool and also determine the situation in the company where this
tool is used...................................................................................................................................7
Q-5 a). Suggestions for Sandwich shop business process to improve the efficiency of a local
business shop...............................................................................................................................7
b). Primary components of comprehensive CRM System...........................................................8
Question-6....................................................................................................................................8
a). E-policies to protect the business............................................................................................8
b). Provide the use of Authentication technologies that restrict the access of unauthorised users
in organisational system...............................................................................................................8
PART B............................................................................................................................................1
1. New information system trends...............................................................................................1
Relationship of Internet and the World Wide Web with other technology components of
information systems.....................................................................................................................1
2. Impact of information systems on businesses operations with their products or services.......1
3. Challenges and opportunities due to globalization in the flattened world...............................3
4. Business objectives of information-systems............................................................................4
5. Apply Porter’s Five Forces analytical framework to UPS.......................................................4
6. UPS embracement of sustainable technologies.......................................................................6
REFERENCES................................................................................................................................7
PART A...........................................................................................................................................3
Q-1 a). Voyage' related illustration and type of Information system represented by this and
also describe at which level of organisation, this IS is used........................................................3
b). Analyse the relationship represented between the components below and also identify the
statement true or false in account of such relationship................................................................4
Q-2 Different types of Information system recommended in an organisation............................4
Q-3 a). Characteristics of Cloud computing................................................................................5
b). Drawbacks of Cloud computing with example......................................................................6
Q-4 a). Definition of Database and also describe that DBMS are better system as compared to
Flat files.......................................................................................................................................6
b). Importance of Data mining tool and also determine the situation in the company where this
tool is used...................................................................................................................................7
Q-5 a). Suggestions for Sandwich shop business process to improve the efficiency of a local
business shop...............................................................................................................................7
b). Primary components of comprehensive CRM System...........................................................8
Question-6....................................................................................................................................8
a). E-policies to protect the business............................................................................................8
b). Provide the use of Authentication technologies that restrict the access of unauthorised users
in organisational system...............................................................................................................8
PART B............................................................................................................................................1
1. New information system trends...............................................................................................1
Relationship of Internet and the World Wide Web with other technology components of
information systems.....................................................................................................................1
2. Impact of information systems on businesses operations with their products or services.......1
3. Challenges and opportunities due to globalization in the flattened world...............................3
4. Business objectives of information-systems............................................................................4
5. Apply Porter’s Five Forces analytical framework to UPS.......................................................4
6. UPS embracement of sustainable technologies.......................................................................6
REFERENCES................................................................................................................................7
PART A
Q-1 a). Voyage' related illustration and type of Information system represented by this and also
describe at which level of organisation, this IS is used.
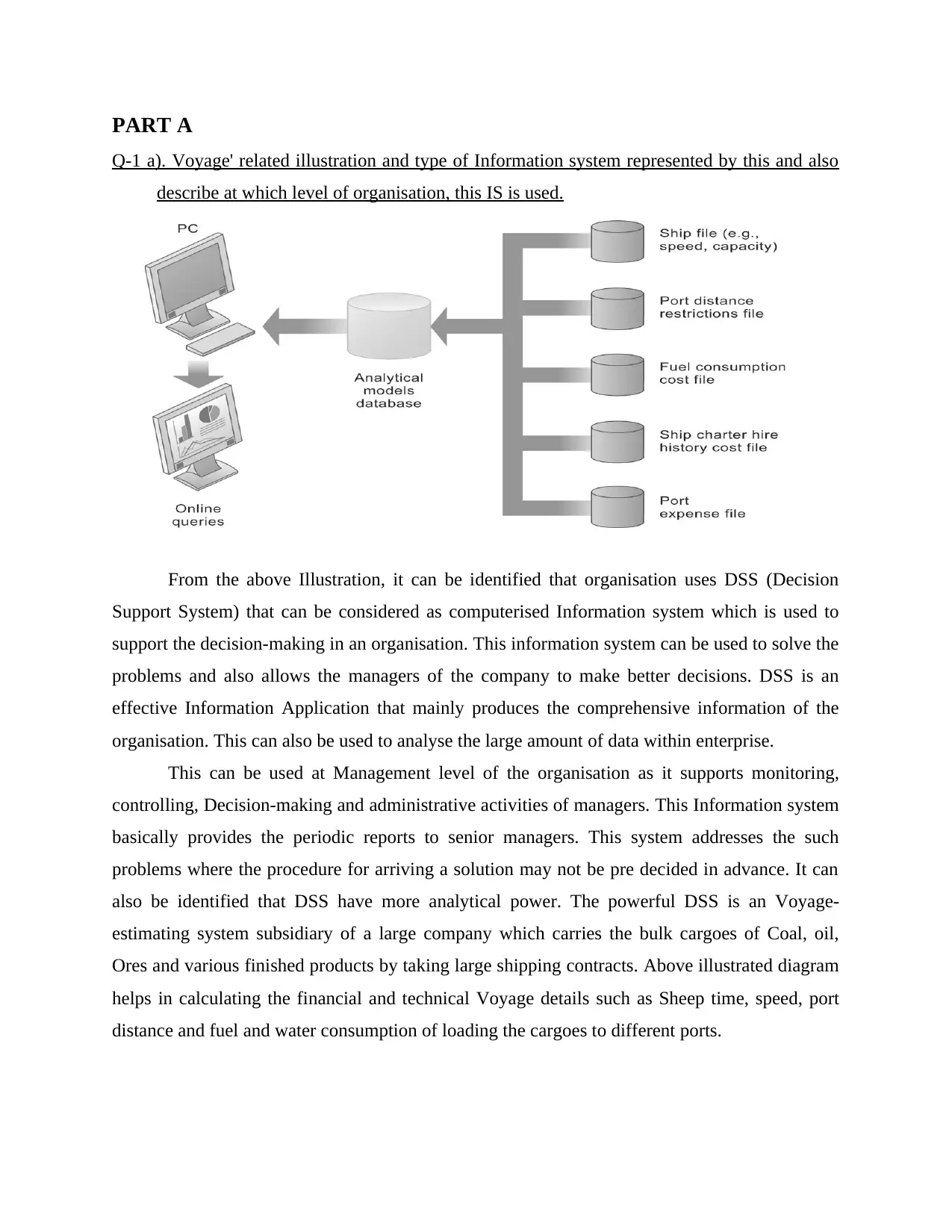
From the above Illustration, it can be identified that organisation uses DSS (Decision
Support System) that can be considered as computerised Information system which is used to
support the decision-making in an organisation. This information system can be used to solve the
problems and also allows the managers of the company to make better decisions. DSS is an
effective Information Application that mainly produces the comprehensive information of the
organisation. This can also be used to analyse the large amount of data within enterprise.
This can be used at Management level of the organisation as it supports monitoring,
controlling, Decision-making and administrative activities of managers. This Information system
basically provides the periodic reports to senior managers. This system addresses the such
problems where the procedure for arriving a solution may not be pre decided in advance. It can
also be identified that DSS have more analytical power. The powerful DSS is an Voyage-
estimating system subsidiary of a large company which carries the bulk cargoes of Coal, oil,
Ores and various finished products by taking large shipping contracts. Above illustrated diagram
helps in calculating the financial and technical Voyage details such as Sheep time, speed, port
distance and fuel and water consumption of loading the cargoes to different ports.
Q-1 a). Voyage' related illustration and type of Information system represented by this and also
describe at which level of organisation, this IS is used.
From the above Illustration, it can be identified that organisation uses DSS (Decision
Support System) that can be considered as computerised Information system which is used to
support the decision-making in an organisation. This information system can be used to solve the
problems and also allows the managers of the company to make better decisions. DSS is an
effective Information Application that mainly produces the comprehensive information of the
organisation. This can also be used to analyse the large amount of data within enterprise.
This can be used at Management level of the organisation as it supports monitoring,
controlling, Decision-making and administrative activities of managers. This Information system
basically provides the periodic reports to senior managers. This system addresses the such
problems where the procedure for arriving a solution may not be pre decided in advance. It can
also be identified that DSS have more analytical power. The powerful DSS is an Voyage-
estimating system subsidiary of a large company which carries the bulk cargoes of Coal, oil,
Ores and various finished products by taking large shipping contracts. Above illustrated diagram
helps in calculating the financial and technical Voyage details such as Sheep time, speed, port
distance and fuel and water consumption of loading the cargoes to different ports.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
b). Analyse the relationship represented between the components below and also identify the
statement true or false in account of such relationship.
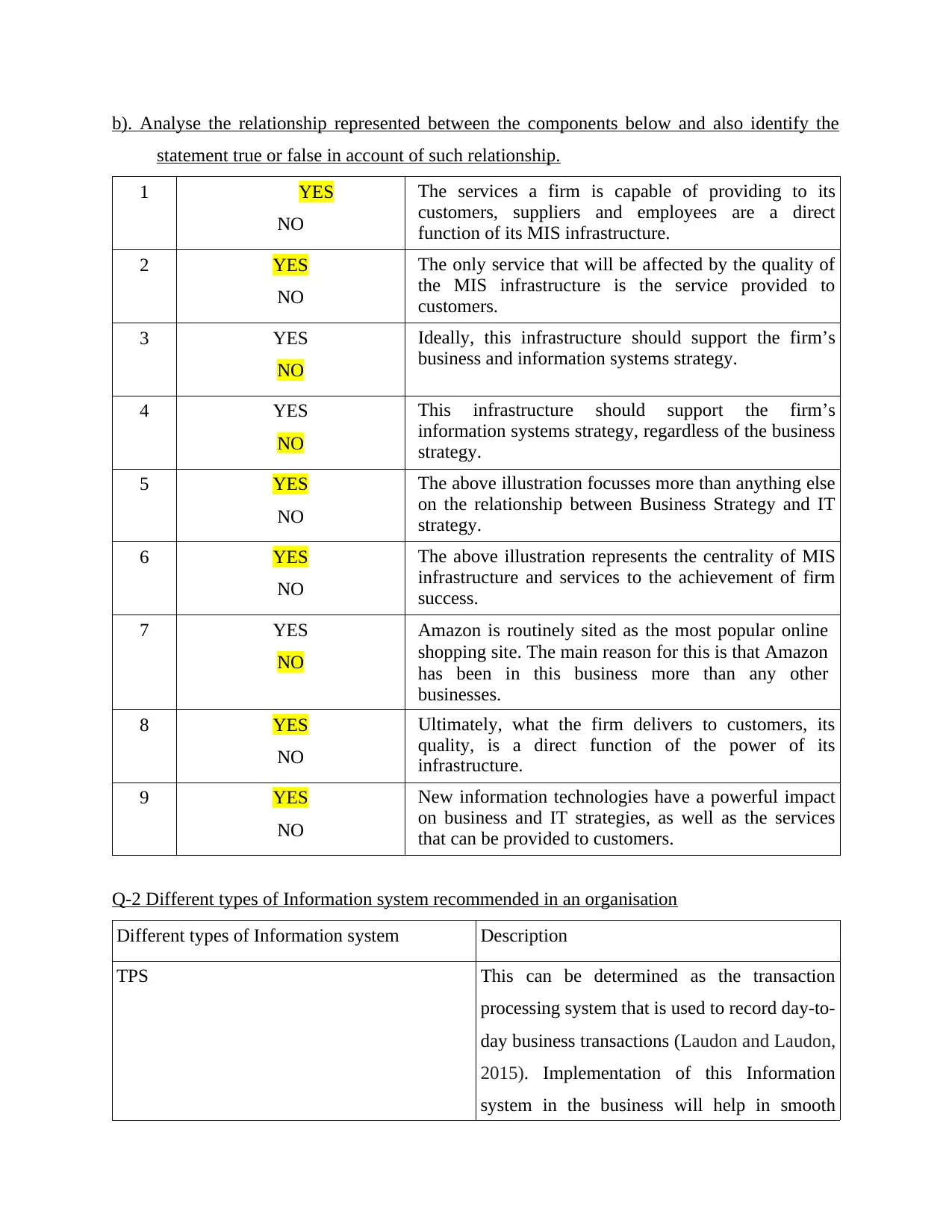
1 YES
NO
The services a firm is capable of providing to its
customers, suppliers and employees are a direct
function of its MIS infrastructure.
2 YES
NO
The only service that will be affected by the quality of
the MIS infrastructure is the service provided to
customers.
3 YES
NO
Ideally, this infrastructure should support the firm’s
business and information systems strategy.
4 YES
NO
This infrastructure should support the firm’s
information systems strategy, regardless of the business
strategy.
5 YES
NO
The above illustration focusses more than anything else
on the relationship between Business Strategy and IT
strategy.
6 YES
NO
The above illustration represents the centrality of MIS
infrastructure and services to the achievement of firm
success.
7 YES
NO
Amazon is routinely sited as the most popular online
shopping site. The main reason for this is that Amazon
has been in this business more than any other
businesses.
8 YES
NO
Ultimately, what the firm delivers to customers, its
quality, is a direct function of the power of its
infrastructure.
9 YES
NO
New information technologies have a powerful impact
on business and IT strategies, as well as the services
that can be provided to customers.
Q-2 Different types of Information system recommended in an organisation
Different types of Information system Description
TPS This can be determined as the transaction
processing system that is used to record day-to-
day business transactions (Laudon and Laudon,
2015). Implementation of this Information
system in the business will help in smooth
statement true or false in account of such relationship.
1 YES
NO
The services a firm is capable of providing to its
customers, suppliers and employees are a direct
function of its MIS infrastructure.
2 YES
NO
The only service that will be affected by the quality of
the MIS infrastructure is the service provided to
customers.
3 YES
NO
Ideally, this infrastructure should support the firm’s
business and information systems strategy.
4 YES
NO
This infrastructure should support the firm’s
information systems strategy, regardless of the business
strategy.
5 YES
NO
The above illustration focusses more than anything else
on the relationship between Business Strategy and IT
strategy.
6 YES
NO
The above illustration represents the centrality of MIS
infrastructure and services to the achievement of firm
success.
7 YES
NO
Amazon is routinely sited as the most popular online
shopping site. The main reason for this is that Amazon
has been in this business more than any other
businesses.
8 YES
NO
Ultimately, what the firm delivers to customers, its
quality, is a direct function of the power of its
infrastructure.
9 YES
NO
New information technologies have a powerful impact
on business and IT strategies, as well as the services
that can be provided to customers.
Q-2 Different types of Information system recommended in an organisation
Different types of Information system Description
TPS This can be determined as the transaction
processing system that is used to record day-to-
day business transactions (Laudon and Laudon,
2015). Implementation of this Information
system in the business will help in smooth
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
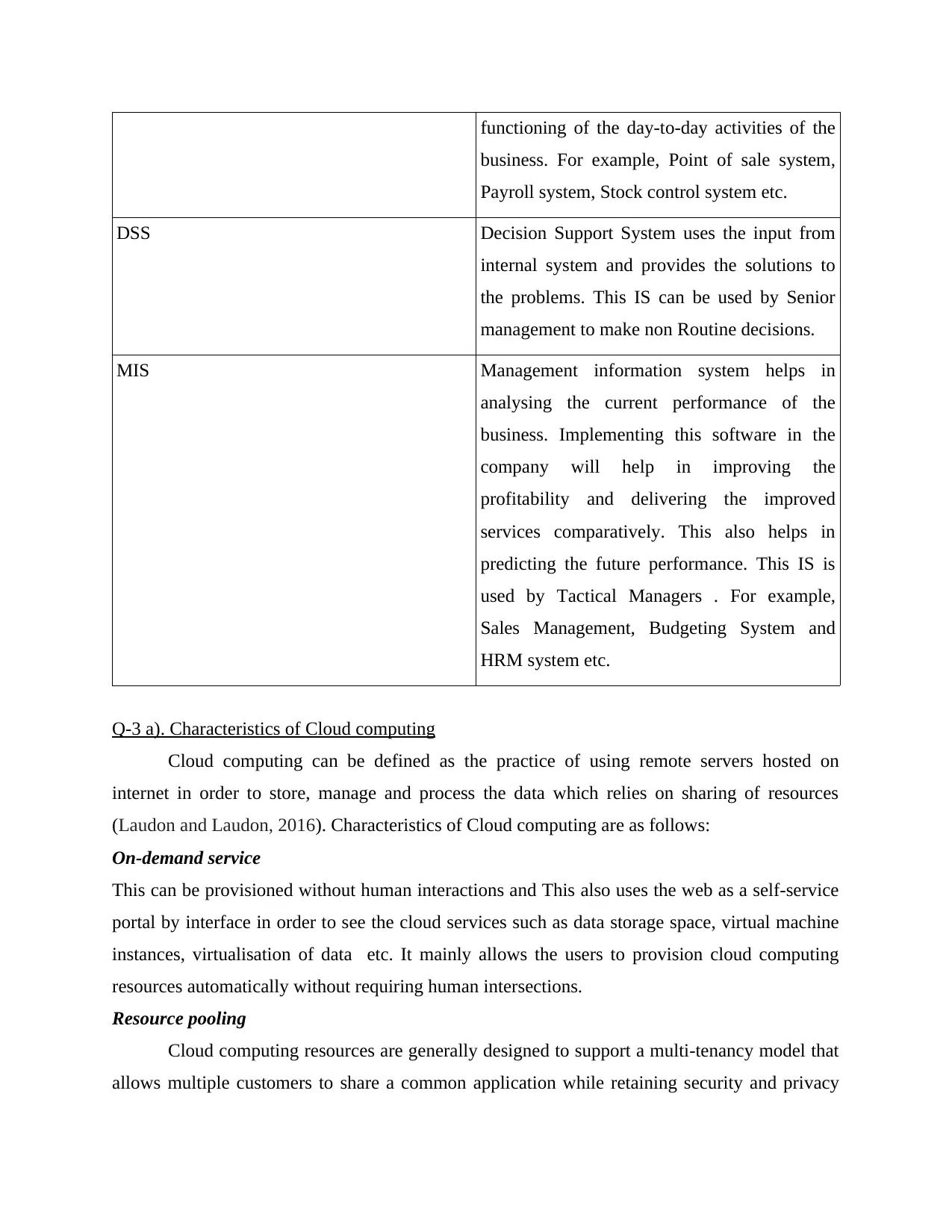
functioning of the day-to-day activities of the
business. For example, Point of sale system,
Payroll system, Stock control system etc.
DSS Decision Support System uses the input from
internal system and provides the solutions to
the problems. This IS can be used by Senior
management to make non Routine decisions.
MIS Management information system helps in
analysing the current performance of the
business. Implementing this software in the
company will help in improving the
profitability and delivering the improved
services comparatively. This also helps in
predicting the future performance. This IS is
used by Tactical Managers . For example,
Sales Management, Budgeting System and
HRM system etc.
Q-3 a). Characteristics of Cloud computing
Cloud computing can be defined as the practice of using remote servers hosted on
internet in order to store, manage and process the data which relies on sharing of resources
(Laudon and Laudon, 2016). Characteristics of Cloud computing are as follows:
On-demand service
This can be provisioned without human interactions and This also uses the web as a self-service
portal by interface in order to see the cloud services such as data storage space, virtual machine
instances, virtualisation of data etc. It mainly allows the users to provision cloud computing
resources automatically without requiring human intersections.
Resource pooling
Cloud computing resources are generally designed to support a multi-tenancy model that
allows multiple customers to share a common application while retaining security and privacy
business. For example, Point of sale system,
Payroll system, Stock control system etc.
DSS Decision Support System uses the input from
internal system and provides the solutions to
the problems. This IS can be used by Senior
management to make non Routine decisions.
MIS Management information system helps in
analysing the current performance of the
business. Implementing this software in the
company will help in improving the
profitability and delivering the improved
services comparatively. This also helps in
predicting the future performance. This IS is
used by Tactical Managers . For example,
Sales Management, Budgeting System and
HRM system etc.
Q-3 a). Characteristics of Cloud computing
Cloud computing can be defined as the practice of using remote servers hosted on
internet in order to store, manage and process the data which relies on sharing of resources
(Laudon and Laudon, 2016). Characteristics of Cloud computing are as follows:
On-demand service
This can be provisioned without human interactions and This also uses the web as a self-service
portal by interface in order to see the cloud services such as data storage space, virtual machine
instances, virtualisation of data etc. It mainly allows the users to provision cloud computing
resources automatically without requiring human intersections.
Resource pooling
Cloud computing resources are generally designed to support a multi-tenancy model that
allows multiple customers to share a common application while retaining security and privacy

over the data and information. Resource pooling basically provides the services to multiple
clients through the common physical infrastructure on the same economy of scale.
Broad network access
This computing resources are generally available over the network and this can be
accessed by diverse platform of customers (Lee, Kao and Yang, 2014). Cloud computing
consists of two very important aspects such as Bandwidth and latency. These aspects are linked
with the quality of services on the network.
Rapid elasticity
Elasticity can be determined as the landmark of cloud computing as this has the ability to
quickly provision the resources on the cloud. With the cloud computing scalability, there is a less
capital expenditure on the cloud customer side. As usage of the cloud data, capacity and cost can
be scaled up or down. Just-in-time services are required in order to either provision the resources
and or less.
b). Drawbacks of Cloud computing with example
The convenience and accessibility of the cloud derives many business organisations to
adopt the cloud computing technology in order to perform efficient business operations (Link,
And et.al., SCIENCELOGIC Inc, 2017). As it provides easy accessibility so risk of insecure
interfaces, data loses and theft of the account credentials increases which involves various
drawbacks such as:
Denial of services
This can be considered as one of the biggest threat involved in providing the cloud
services in this technological world. This technology makes it easier for attackers to flood the
network connection with large number of requests simultaneously. This may result in denial of
services which can be determined as a intended attack of the attacker which is mainly meant to
shutdown the network or machine which leads to inaccessibility of data from the users.
Loss of Data
As the internet connection provides easy accessibility of large amount of database then it
may be responsible for the loss of the data or destruction of the large amount of data altogether.
There are many reputable cloud services that offers the protection and security to the loss of the
data.
clients through the common physical infrastructure on the same economy of scale.
Broad network access
This computing resources are generally available over the network and this can be
accessed by diverse platform of customers (Lee, Kao and Yang, 2014). Cloud computing
consists of two very important aspects such as Bandwidth and latency. These aspects are linked
with the quality of services on the network.
Rapid elasticity
Elasticity can be determined as the landmark of cloud computing as this has the ability to
quickly provision the resources on the cloud. With the cloud computing scalability, there is a less
capital expenditure on the cloud customer side. As usage of the cloud data, capacity and cost can
be scaled up or down. Just-in-time services are required in order to either provision the resources
and or less.
b). Drawbacks of Cloud computing with example
The convenience and accessibility of the cloud derives many business organisations to
adopt the cloud computing technology in order to perform efficient business operations (Link,
And et.al., SCIENCELOGIC Inc, 2017). As it provides easy accessibility so risk of insecure
interfaces, data loses and theft of the account credentials increases which involves various
drawbacks such as:
Denial of services
This can be considered as one of the biggest threat involved in providing the cloud
services in this technological world. This technology makes it easier for attackers to flood the
network connection with large number of requests simultaneously. This may result in denial of
services which can be determined as a intended attack of the attacker which is mainly meant to
shutdown the network or machine which leads to inaccessibility of data from the users.
Loss of Data
As the internet connection provides easy accessibility of large amount of database then it
may be responsible for the loss of the data or destruction of the large amount of data altogether.
There are many reputable cloud services that offers the protection and security to the loss of the
data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

For instance, Denial of services is a security attack that causes a large amount of
destruction to data base and this may attempt to prevent the legitimate user to access services.
Attacker access the confidential data and it may bay be used and manipulated for the wrong
intention.
Q-4 a). Definition of Database and also describe that DBMS are better system as compared to
Flat files
Database can be termed as a organised collection of the data which is stored
electronically on the computer systems. DBMS can be helped in easily access, manage and
update the data in row and column format(Naser and Al Shobaki, 2016). Flat file database used
to store the data in a single table structure. These are typically plain text files that stores one
record per line with the record field denoted by white space or delimiters such as commas or
tabs. Although, DBMS is better then flat file system in every aspects of database. Such benefits
can be described as
DBMS consists of the structured database which can be easily accessible and more
efficient then flat file system as it stores the data in files which consumes lot of time to
manipulate the data.
Flat file stores the data in a single directory on the other hand, DBMS is better as it stores
the data in an organised manner which is as efficient as the more data is added to it.
DBMS is a more user friendly as compared to flat file system.
b). Importance of Data mining tool and also determine the situation in the company where this
tool is used.
Data mining can be determined as the set of methodology that is used in analysing the
data from various perspectives that are used for summarising and grouping the data (Perrier and
Barnes, 2018). This technique is basically used for abstraction of a specific data from the large
amount of database. Various data mining tools are available such as Weka, Rapid miner,
DataMelt, KEEL etc. Data mining tool is used to identify the required data from the collection of
huge amount of database and conversion of this data in meaningful information which can be
used further. Importance of data mining tool are as follows:
Rapid Miner: This is the leading predictive analytical technique that is helping the enterprises in
Business process. This tool is also compatible with weak scripts which can be used for business
or commercial application, research and education.
destruction to data base and this may attempt to prevent the legitimate user to access services.
Attacker access the confidential data and it may bay be used and manipulated for the wrong
intention.
Q-4 a). Definition of Database and also describe that DBMS are better system as compared to
Flat files
Database can be termed as a organised collection of the data which is stored
electronically on the computer systems. DBMS can be helped in easily access, manage and
update the data in row and column format(Naser and Al Shobaki, 2016). Flat file database used
to store the data in a single table structure. These are typically plain text files that stores one
record per line with the record field denoted by white space or delimiters such as commas or
tabs. Although, DBMS is better then flat file system in every aspects of database. Such benefits
can be described as
DBMS consists of the structured database which can be easily accessible and more
efficient then flat file system as it stores the data in files which consumes lot of time to
manipulate the data.
Flat file stores the data in a single directory on the other hand, DBMS is better as it stores
the data in an organised manner which is as efficient as the more data is added to it.
DBMS is a more user friendly as compared to flat file system.
b). Importance of Data mining tool and also determine the situation in the company where this
tool is used.
Data mining can be determined as the set of methodology that is used in analysing the
data from various perspectives that are used for summarising and grouping the data (Perrier and
Barnes, 2018). This technique is basically used for abstraction of a specific data from the large
amount of database. Various data mining tools are available such as Weka, Rapid miner,
DataMelt, KEEL etc. Data mining tool is used to identify the required data from the collection of
huge amount of database and conversion of this data in meaningful information which can be
used further. Importance of data mining tool are as follows:
Rapid Miner: This is the leading predictive analytical technique that is helping the enterprises in
Business process. This tool is also compatible with weak scripts which can be used for business
or commercial application, research and education.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Weka: This is a Java based free and open source software which can be used on Linux, Mac, OS
X and Windows. It packages tools for pre processing classification, regression, clustering,
association rules and visualisation.
Data Melt: This tool does much more than just Data Mining. This tool offers various
computational platforms such as Statistics, numericals, symbolic computations and scientific
visualisation etc.
Q-5 a). Suggestions for Sandwich shop business process to improve the efficiency of a local
business shop
Consumers are mostly aware of their choices these days so managers need to implement
the best Information System that ensures most suitable demanded product at the right time, right
place and right price. Efficiency of the sandwich shop can be improved by adopting a systematic
approach can be helpful in increasing the operational efficiency of the business. Suggestions for
improving the efficiency of the sandwich shop are as follows:
Automatic reordering and payment method helps in automatically taking the orders of
customers which saves the time and human efficiency (Sassen, 2016). Managers should
implement contract management software to improve the efficiency as it helps in
estimating the clear budget of resources required at sandwich shop.
In order to perform Streamlined scheduling, Managers need to focus on the standardised
material in order to achieve the effective production. Use of Scheduling app will helps in
improving the efficiency and also reduce the time invested on scheduling the business
activities.
Optimise the Ordering area Owners of the Sandwich shop should also need to develop
a business process plan in order to perform the efficient operations.
Three business process of sandwich shop includes the following three steps:
Take order and payments
Make sandwich and wrap it
Handover to customer
All the above process can be better coordinated by employing the use of information
system in the business and this ultimately supports efficient operations of the sandwich shop.
b). Primary components of comprehensive CRM System
Primary components of the Customer Relationship Management can be identified below:
X and Windows. It packages tools for pre processing classification, regression, clustering,
association rules and visualisation.
Data Melt: This tool does much more than just Data Mining. This tool offers various
computational platforms such as Statistics, numericals, symbolic computations and scientific
visualisation etc.
Q-5 a). Suggestions for Sandwich shop business process to improve the efficiency of a local
business shop
Consumers are mostly aware of their choices these days so managers need to implement
the best Information System that ensures most suitable demanded product at the right time, right
place and right price. Efficiency of the sandwich shop can be improved by adopting a systematic
approach can be helpful in increasing the operational efficiency of the business. Suggestions for
improving the efficiency of the sandwich shop are as follows:
Automatic reordering and payment method helps in automatically taking the orders of
customers which saves the time and human efficiency (Sassen, 2016). Managers should
implement contract management software to improve the efficiency as it helps in
estimating the clear budget of resources required at sandwich shop.
In order to perform Streamlined scheduling, Managers need to focus on the standardised
material in order to achieve the effective production. Use of Scheduling app will helps in
improving the efficiency and also reduce the time invested on scheduling the business
activities.
Optimise the Ordering area Owners of the Sandwich shop should also need to develop
a business process plan in order to perform the efficient operations.
Three business process of sandwich shop includes the following three steps:
Take order and payments
Make sandwich and wrap it
Handover to customer
All the above process can be better coordinated by employing the use of information
system in the business and this ultimately supports efficient operations of the sandwich shop.
b). Primary components of comprehensive CRM System
Primary components of the Customer Relationship Management can be identified below:

Lead management: This is referred as keeping the track of the sales as well as their distribution.
Most of the sales industries are benefited by This components of CRM (Speed, 2016). It involves
the customised design of forms, finalising the mailing lists, efficient management of campaigns.
Human Resource Management: This involves the correct and effective use of human efforts
and skills at a specific situation of the business.
Customer service: Customer relationship Management emphasizes on collecting the
information and data from the customers which helps in delivering the services which satisfies
the loyal customers of the company.
Q-6 a). E-policies to protect the business
Encryption policy: This helps in operating the data and information by encrypting it into the
other formats (Stair and Reynolds, 2013). This policy helps in encrypting the user password by
applying different encryption methods and this is most secured way to protect the data and
information.
password Management policy: This helps in managing the strong passwords as manageable as
possible. As employee password is the first line to defence the data and protect the confidential
information from unauthorised users.
Data access policy: This policy helps in providing access to only those people who are
authenticated to access such data. Other wise all the extracted data will be displayed to
unauthorised users.
b). Provide the use of Authentication technologies that restrict the access of unauthorised users in
organisational system
Authentication is a process which provides the accessibility to the users in order to use
the data and information of the company. This can be considered as the first step in access
control. It provides three factors that restricts the accessibility of the database from unauthorised
users. This includes the following factors:
1. Something you know: This can be determined as the passwords, so identification occus at
the time when user professes an identity. This factor helps in identifying the
authentication by the correct user name and password of the user.
2. Something you have: This factor helps in identifying the authenticated user by the
evidence such as smart cards etc. this authenticate the identity of the user by identifying
Most of the sales industries are benefited by This components of CRM (Speed, 2016). It involves
the customised design of forms, finalising the mailing lists, efficient management of campaigns.
Human Resource Management: This involves the correct and effective use of human efforts
and skills at a specific situation of the business.
Customer service: Customer relationship Management emphasizes on collecting the
information and data from the customers which helps in delivering the services which satisfies
the loyal customers of the company.
Q-6 a). E-policies to protect the business
Encryption policy: This helps in operating the data and information by encrypting it into the
other formats (Stair and Reynolds, 2013). This policy helps in encrypting the user password by
applying different encryption methods and this is most secured way to protect the data and
information.
password Management policy: This helps in managing the strong passwords as manageable as
possible. As employee password is the first line to defence the data and protect the confidential
information from unauthorised users.
Data access policy: This policy helps in providing access to only those people who are
authenticated to access such data. Other wise all the extracted data will be displayed to
unauthorised users.
b). Provide the use of Authentication technologies that restrict the access of unauthorised users in
organisational system
Authentication is a process which provides the accessibility to the users in order to use
the data and information of the company. This can be considered as the first step in access
control. It provides three factors that restricts the accessibility of the database from unauthorised
users. This includes the following factors:
1. Something you know: This can be determined as the passwords, so identification occus at
the time when user professes an identity. This factor helps in identifying the
authentication by the correct user name and password of the user.
2. Something you have: This factor helps in identifying the authenticated user by the
evidence such as smart cards etc. this authenticate the identity of the user by identifying
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the cards as well as matching the password kept at server (Components of Customer
Relationship Management, 2018).
3. Something you are: This is termed as the Biometric method which provides the
authentication with the help of accessing the fingerprints of the person. These also
includes various methods such as retina of an eye, face etc. this helps in recognising the
identity of the user.
PART B
1. New information system trends
The three major information system trends that have brought revolutionary changes for
proper dissemination of data and information to conduct businesses are the following:
Use of mobile phones platforms: This has assisted in improvising the communication
channels, both direct and indirect channels (Vayena and et.al., 2015). For e.g. apple
itunes, customer service management etc.
Software-as-a-service: It is popularly known as SaaS. This is one of the software
distribution models that has given platform to the users to connect over the internet. For
e.g. calendaring, email, office tools etc. Cloud Computing: This supports in presentation of any type of information in a concise
and coherent manner. It leads to procuring, storing and analysing the data at widest scale
through multiple platforms such as email messages, sensors, social media etc.
Relationship of Internet and the World Wide Web with other technology components of
information systems
In this regard, the information systems act as the third party provider who lays the
foundation of applications to the hosts via use of internet and World wide web. These two tools
have accelerated the development of the networking and its related concepts in the most
profound manner. E-commerce have gain benefits by applying different components such as
software, hardware etc. of such information-systems at both individual and organizational levels
(Lee, Kao and Yang,2014). Moreover, it paved the path of collaboration and giving services to
the customers whoa re sitting at their homes, offices and can explore varieties of things. This has
also helped in the virtual sharing of resources for gaining competitive advantages in the global
markets.
Relationship Management, 2018).
3. Something you are: This is termed as the Biometric method which provides the
authentication with the help of accessing the fingerprints of the person. These also
includes various methods such as retina of an eye, face etc. this helps in recognising the
identity of the user.
PART B
1. New information system trends
The three major information system trends that have brought revolutionary changes for
proper dissemination of data and information to conduct businesses are the following:
Use of mobile phones platforms: This has assisted in improvising the communication
channels, both direct and indirect channels (Vayena and et.al., 2015). For e.g. apple
itunes, customer service management etc.
Software-as-a-service: It is popularly known as SaaS. This is one of the software
distribution models that has given platform to the users to connect over the internet. For
e.g. calendaring, email, office tools etc. Cloud Computing: This supports in presentation of any type of information in a concise
and coherent manner. It leads to procuring, storing and analysing the data at widest scale
through multiple platforms such as email messages, sensors, social media etc.
Relationship of Internet and the World Wide Web with other technology components of
information systems
In this regard, the information systems act as the third party provider who lays the
foundation of applications to the hosts via use of internet and World wide web. These two tools
have accelerated the development of the networking and its related concepts in the most
profound manner. E-commerce have gain benefits by applying different components such as
software, hardware etc. of such information-systems at both individual and organizational levels
(Lee, Kao and Yang,2014). Moreover, it paved the path of collaboration and giving services to
the customers whoa re sitting at their homes, offices and can explore varieties of things. This has
also helped in the virtual sharing of resources for gaining competitive advantages in the global
markets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. Impact of information systems on businesses operations with their products or services
Information systems have drastically put the changes in how businesses are operating
these days. Customers are easily getting access to the product or service in convenient and proper
manner. Such information systems have reaped advantages and benefits that transformed the
operational practices of organizations. These are as follows:
1. It minimizes the time consumption by cutting down the costing on organizing sessions,
meeting, discussions along with unnecessary travelling. This helps in checking the
validity and reliability parameters attached with the production/marketing/packaging and
many more functional units.
2. Use of wireless technological tools and techniques through websites, mobile applications
etc. which gives instant information regarding the product and connect with consumers
from any geographical location of the world.
3. This provides a connecting link between the space and time shifting by making the
management flexible and efficiency. Example Wal-Mart’s RetailLink system for
effective arrangement of replenishment system.
4. Promotion and advertising have become cost effective since digital marketing has
reduced the hiring of PR, putting up the billboards, spending on print media tactics etc .
5. It reduced the decision making strategies by incorporating the accuracy factor and made
the running of operational practices smoothly (Eason, 2014). Herby, the production
department is linked management of resources on schedule.
6. For instance: Verizon's web based digital dashboard gives real time data for overcoming
challenges such as complaints of employees' or customers', performance of networking
etc.
7. This mainly deals with the customer services and forms a transparent and clear platform
to attain the productivity and profitability in appropriate order.
Information systems have drastically put the changes in how businesses are operating
these days. Customers are easily getting access to the product or service in convenient and proper
manner. Such information systems have reaped advantages and benefits that transformed the
operational practices of organizations. These are as follows:
1. It minimizes the time consumption by cutting down the costing on organizing sessions,
meeting, discussions along with unnecessary travelling. This helps in checking the
validity and reliability parameters attached with the production/marketing/packaging and
many more functional units.
2. Use of wireless technological tools and techniques through websites, mobile applications
etc. which gives instant information regarding the product and connect with consumers
from any geographical location of the world.
3. This provides a connecting link between the space and time shifting by making the
management flexible and efficiency. Example Wal-Mart’s RetailLink system for
effective arrangement of replenishment system.
4. Promotion and advertising have become cost effective since digital marketing has
reduced the hiring of PR, putting up the billboards, spending on print media tactics etc .
5. It reduced the decision making strategies by incorporating the accuracy factor and made
the running of operational practices smoothly (Eason, 2014). Herby, the production
department is linked management of resources on schedule.
6. For instance: Verizon's web based digital dashboard gives real time data for overcoming
challenges such as complaints of employees' or customers', performance of networking
etc.
7. This mainly deals with the customer services and forms a transparent and clear platform
to attain the productivity and profitability in appropriate order.
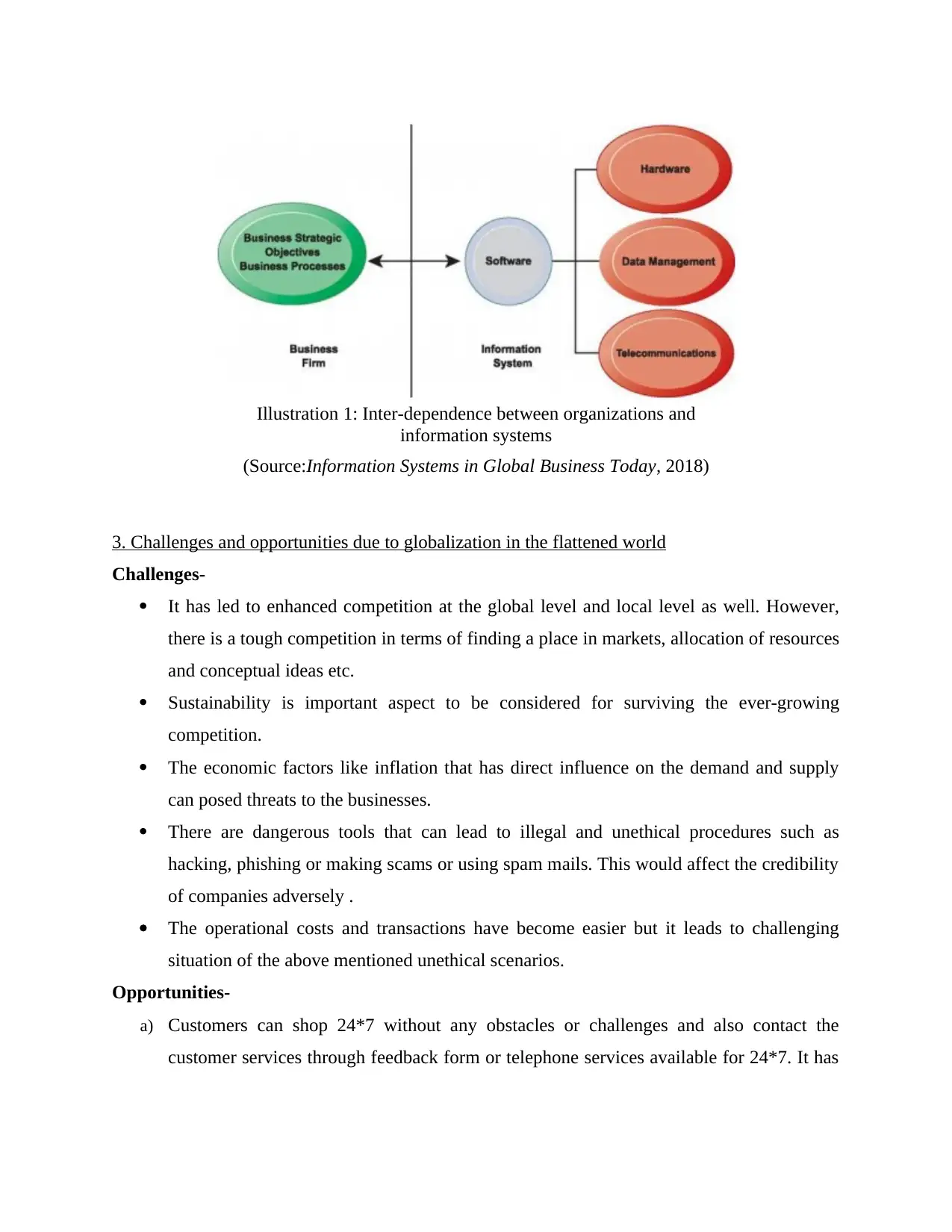
3. Challenges and opportunities due to globalization in the flattened world
Challenges-
It has led to enhanced competition at the global level and local level as well. However,
there is a tough competition in terms of finding a place in markets, allocation of resources
and conceptual ideas etc.
Sustainability is important aspect to be considered for surviving the ever-growing
competition.
The economic factors like inflation that has direct influence on the demand and supply
can posed threats to the businesses.
There are dangerous tools that can lead to illegal and unethical procedures such as
hacking, phishing or making scams or using spam mails. This would affect the credibility
of companies adversely .
The operational costs and transactions have become easier but it leads to challenging
situation of the above mentioned unethical scenarios.
Opportunities-
a) Customers can shop 24*7 without any obstacles or challenges and also contact the
customer services through feedback form or telephone services available for 24*7. It has
Illustration 1: Inter-dependence between organizations and
information systems
(Source:Information Systems in Global Business Today, 2018)
Challenges-
It has led to enhanced competition at the global level and local level as well. However,
there is a tough competition in terms of finding a place in markets, allocation of resources
and conceptual ideas etc.
Sustainability is important aspect to be considered for surviving the ever-growing
competition.
The economic factors like inflation that has direct influence on the demand and supply
can posed threats to the businesses.
There are dangerous tools that can lead to illegal and unethical procedures such as
hacking, phishing or making scams or using spam mails. This would affect the credibility
of companies adversely .
The operational costs and transactions have become easier but it leads to challenging
situation of the above mentioned unethical scenarios.
Opportunities-
a) Customers can shop 24*7 without any obstacles or challenges and also contact the
customer services through feedback form or telephone services available for 24*7. It has
Illustration 1: Inter-dependence between organizations and
information systems
(Source:Information Systems in Global Business Today, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





