MITS4004 Networking: A Detailed Wireshark Analysis of ICMP and IP
VerifiedAdded on 2023/04/24
|21
|3293
|430
Practical Assignment
AI Summary
This assignment delves into the analysis of ICMP and IP protocols using Wireshark, focusing on practical network analysis. The study includes running ping and traceroute commands, capturing packets, and analyzing the captured data to understand network layer information. It covers key aspects such as IP addresses, ICMP packet structures (type, code, checksum, identifier, sequence number), and TTL values. The analysis also identifies potential network delays and explores differences between ICMP request and reply packets. The assignment further investigates IP datagrams, including header length, payload size, fragmentation, and constant/changing fields within the IP header, providing a comprehensive understanding of network communication.

MITS4004 Research Study : Networking
[Student Name]
[University Name]
[Student Name]
[University Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Wireshark Lab: ICMP v6.0........................................................................................................3
ICMP and Ping.......................................................................................................................3
ICMP and Traceroute...........................................................................................................11
Wireshark Lab: IP v6.0............................................................................................................17
Wireshark Lab: ICMP v6.0........................................................................................................3
ICMP and Ping.......................................................................................................................3
ICMP and Traceroute...........................................................................................................11
Wireshark Lab: IP v6.0............................................................................................................17
Wireshark Lab: ICMP v6.0
ICMP and Ping
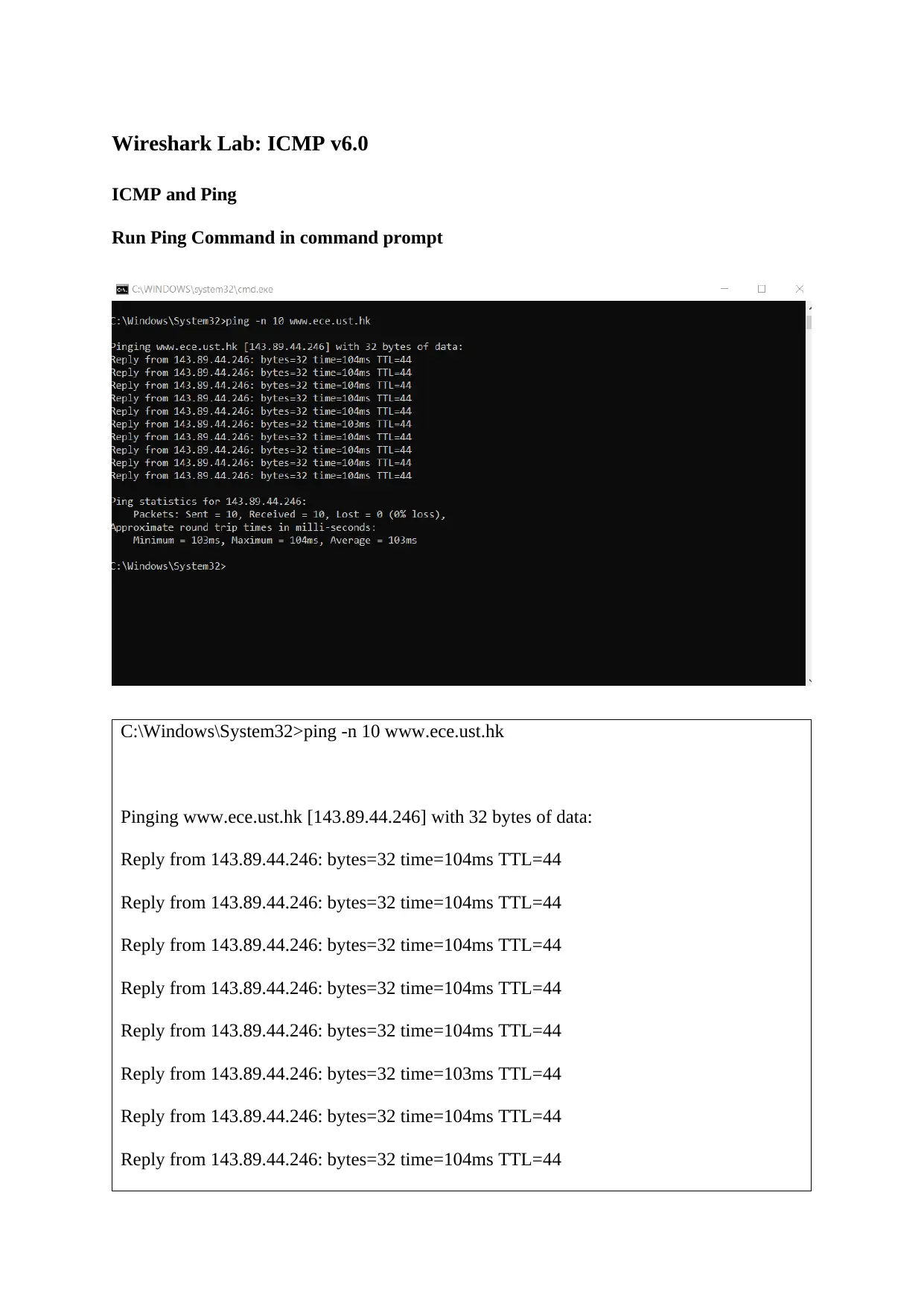
Run Ping Command in command prompt
C:\Windows\System32>ping -n 10 www.ece.ust.hk
Pinging www.ece.ust.hk [143.89.44.246] with 32 bytes of data:
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=103ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
ICMP and Ping
Run Ping Command in command prompt
C:\Windows\System32>ping -n 10 www.ece.ust.hk
Pinging www.ece.ust.hk [143.89.44.246] with 32 bytes of data:
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=103ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Ping statistics for 143.89.44.246:
Packets: Sent = 10, Received = 10, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 103ms, Maximum = 104ms, Average = 103ms
C:\Windows\System32>
Wireshark Packet Capture of Ping Command
Answers
Reply from 143.89.44.246: bytes=32 time=104ms TTL=44
Ping statistics for 143.89.44.246:
Packets: Sent = 10, Received = 10, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 103ms, Maximum = 104ms, Average = 103ms
C:\Windows\System32>
Wireshark Packet Capture of Ping Command
Answers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

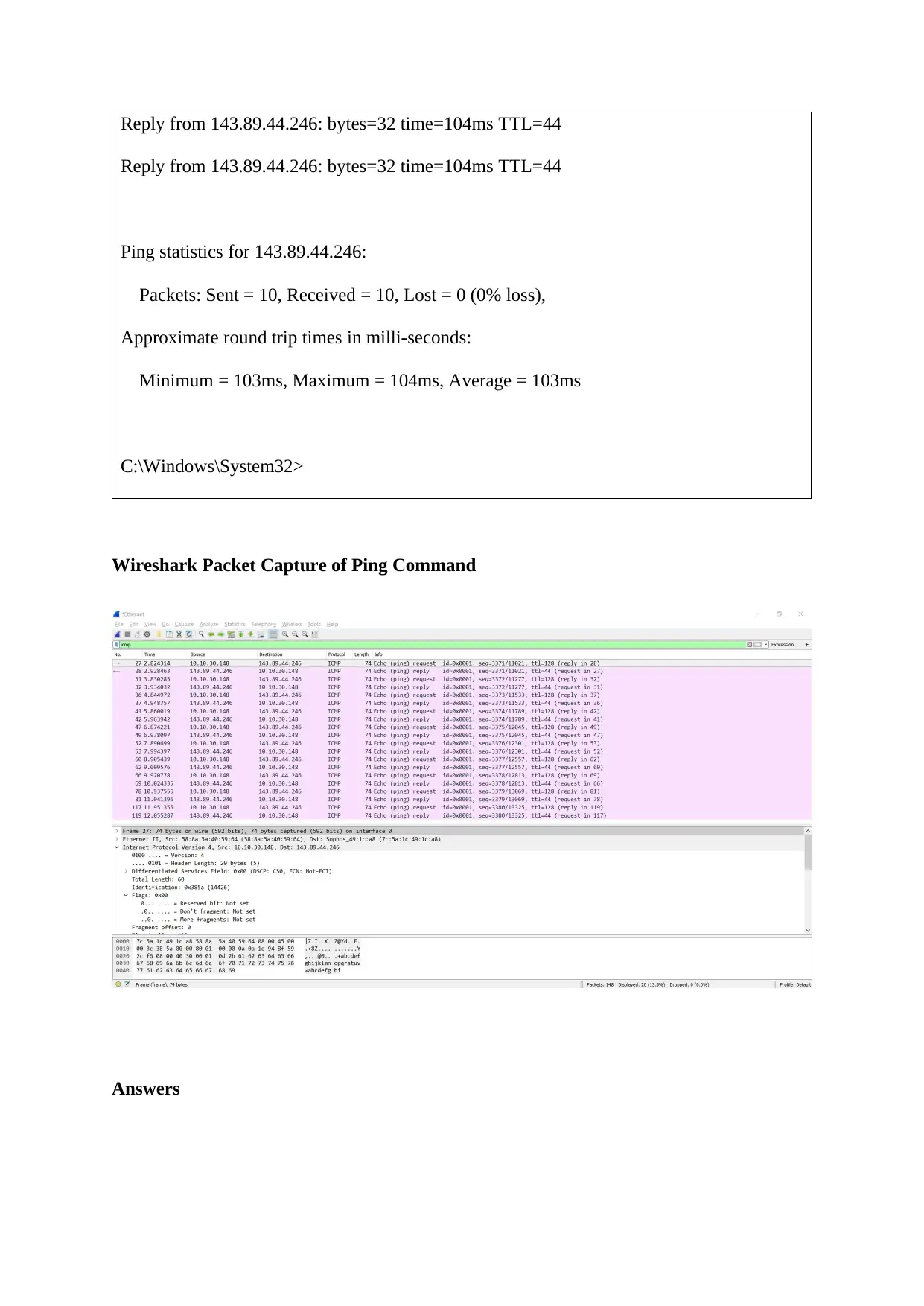
1. IP address of the host is 10.10.30.148. IP address of the destination host is
143.89.44.246
2. ICMP packet communicate network layer information between hosts and routers.
Therefore, ICMP packets does not have the source and destination port number.
3. ICMP packet brief
Frame 27: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) on interface 0
Interface id: 0 (\Device\NPF_{57C7D7B6-27B9-4DA4-A941-901908A75822})
Encapsulation type: Ethernet (1)
Arrival Time: Jan 24, 2019 16:25:54.025442000 India Standard Time
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1548327354.025442000 seconds
[Time delta from previous captured frame: 0.017423000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 2.824314000 seconds]
Frame Number: 27
Frame Length: 74 bytes (592 bits)
Capture Length: 74 bytes (592 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:icmp:data]
[Coloring Rule Name: ICMP]
[Coloring Rule String: icmp || icmpv6]
Ethernet II, Src: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64), Dst: Sophos_49:1c:a8
143.89.44.246
2. ICMP packet communicate network layer information between hosts and routers.
Therefore, ICMP packets does not have the source and destination port number.
3. ICMP packet brief
Frame 27: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) on interface 0
Interface id: 0 (\Device\NPF_{57C7D7B6-27B9-4DA4-A941-901908A75822})
Encapsulation type: Ethernet (1)
Arrival Time: Jan 24, 2019 16:25:54.025442000 India Standard Time
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1548327354.025442000 seconds
[Time delta from previous captured frame: 0.017423000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 2.824314000 seconds]
Frame Number: 27
Frame Length: 74 bytes (592 bits)
Capture Length: 74 bytes (592 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:icmp:data]
[Coloring Rule Name: ICMP]
[Coloring Rule String: icmp || icmpv6]
Ethernet II, Src: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64), Dst: Sophos_49:1c:a8

(7c:5a:1c:49:1c:a8)
Destination: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8)
Address: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64)
Address: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.10.30.148, Dst: 143.89.44.246
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 60
Identification: 0x385a (14426)
Flags: 0x00
0... .... = Reserved bit: Not set
.0.. .... = Don't fragment: Not set
..0. .... = More fragments: Not set
Fragment offset: 0
Time to live: 128
Protocol: ICMP (1)
Destination: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8)
Address: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64)
Address: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.10.30.148, Dst: 143.89.44.246
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 60
Identification: 0x385a (14426)
Flags: 0x00
0... .... = Reserved bit: Not set
.0.. .... = Don't fragment: Not set
..0. .... = More fragments: Not set
Fragment offset: 0
Time to live: 128
Protocol: ICMP (1)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
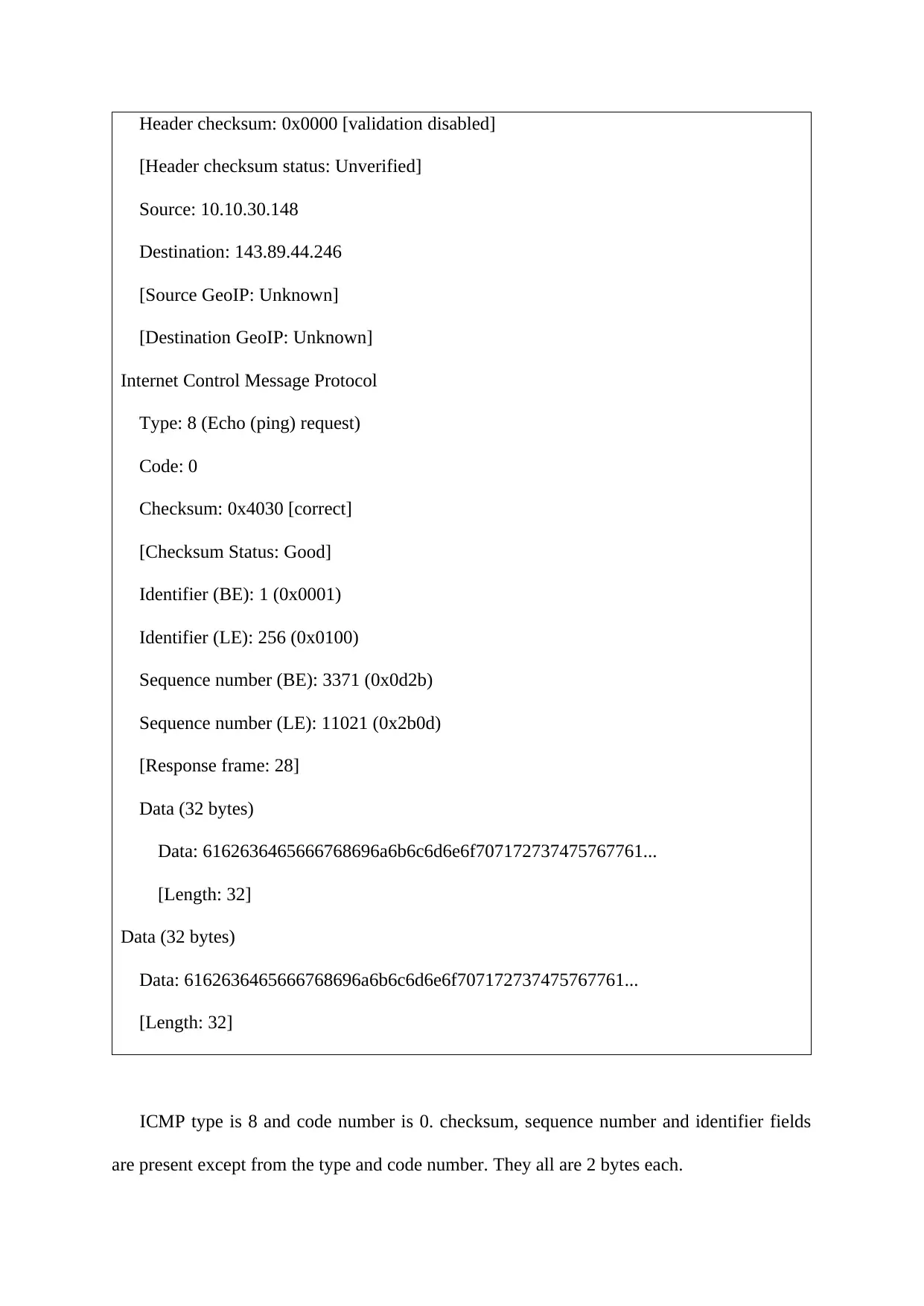
Header checksum: 0x0000 [validation disabled]
[Header checksum status: Unverified]
Source: 10.10.30.148
Destination: 143.89.44.246
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
Internet Control Message Protocol
Type: 8 (Echo (ping) request)
Code: 0
Checksum: 0x4030 [correct]
[Checksum Status: Good]
Identifier (BE): 1 (0x0001)
Identifier (LE): 256 (0x0100)
Sequence number (BE): 3371 (0x0d2b)
Sequence number (LE): 11021 (0x2b0d)
[Response frame: 28]
Data (32 bytes)
Data: 6162636465666768696a6b6c6d6e6f707172737475767761...
[Length: 32]
Data (32 bytes)
Data: 6162636465666768696a6b6c6d6e6f707172737475767761...
[Length: 32]
ICMP type is 8 and code number is 0. checksum, sequence number and identifier fields
are present except from the type and code number. They all are 2 bytes each.
[Header checksum status: Unverified]
Source: 10.10.30.148
Destination: 143.89.44.246
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
Internet Control Message Protocol
Type: 8 (Echo (ping) request)
Code: 0
Checksum: 0x4030 [correct]
[Checksum Status: Good]
Identifier (BE): 1 (0x0001)
Identifier (LE): 256 (0x0100)
Sequence number (BE): 3371 (0x0d2b)
Sequence number (LE): 11021 (0x2b0d)
[Response frame: 28]
Data (32 bytes)
Data: 6162636465666768696a6b6c6d6e6f707172737475767761...
[Length: 32]
Data (32 bytes)
Data: 6162636465666768696a6b6c6d6e6f707172737475767761...
[Length: 32]
ICMP type is 8 and code number is 0. checksum, sequence number and identifier fields
are present except from the type and code number. They all are 2 bytes each.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4. Replay Ping Packets
Frame 28: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) on interface 0
Interface id: 0 (\Device\NPF_{57C7D7B6-27B9-4DA4-A941-901908A75822})
Encapsulation type: Ethernet (1)
Arrival Time: Jan 24, 2019 16:25:54.129591000 India Standard Time
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1548327354.129591000 seconds
[Time delta from previous captured frame: 0.104149000 seconds]
[Time delta from previous displayed frame: 0.104149000 seconds]
[Time since reference or first frame: 2.928463000 seconds]
Frame Number: 28
Frame Length: 74 bytes (592 bits)
Capture Length: 74 bytes (592 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:icmp:data]
[Coloring Rule Name: ICMP]
[Coloring Rule String: icmp || icmpv6]
Ethernet II, Src: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8), Dst: 58:8a:5a:40:59:64
(58:8a:5a:40:59:64)
Destination: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64)
Address: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
Frame 28: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) on interface 0
Interface id: 0 (\Device\NPF_{57C7D7B6-27B9-4DA4-A941-901908A75822})
Encapsulation type: Ethernet (1)
Arrival Time: Jan 24, 2019 16:25:54.129591000 India Standard Time
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1548327354.129591000 seconds
[Time delta from previous captured frame: 0.104149000 seconds]
[Time delta from previous displayed frame: 0.104149000 seconds]
[Time since reference or first frame: 2.928463000 seconds]
Frame Number: 28
Frame Length: 74 bytes (592 bits)
Capture Length: 74 bytes (592 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:icmp:data]
[Coloring Rule Name: ICMP]
[Coloring Rule String: icmp || icmpv6]
Ethernet II, Src: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8), Dst: 58:8a:5a:40:59:64
(58:8a:5a:40:59:64)
Destination: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64)
Address: 58:8a:5a:40:59:64 (58:8a:5a:40:59:64)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)

.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8)
Address: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 143.89.44.246, Dst: 10.10.30.148
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 60
Identification: 0x8bd4 (35796)
Flags: 0x00
0... .... = Reserved bit: Not set
.0.. .... = Don't fragment: Not set
..0. .... = More fragments: Not set
Fragment offset: 0
Time to live: 44
Protocol: ICMP (1)
Header checksum: 0x1e00 [validation disabled]
[Header checksum status: Unverified]
Source: 143.89.44.246
Destination: 10.10.30.148
Source: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8)
Address: Sophos_49:1c:a8 (7c:5a:1c:49:1c:a8)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 143.89.44.246, Dst: 10.10.30.148
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 60
Identification: 0x8bd4 (35796)
Flags: 0x00
0... .... = Reserved bit: Not set
.0.. .... = Don't fragment: Not set
..0. .... = More fragments: Not set
Fragment offset: 0
Time to live: 44
Protocol: ICMP (1)
Header checksum: 0x1e00 [validation disabled]
[Header checksum status: Unverified]
Source: 143.89.44.246
Destination: 10.10.30.148
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
Internet Control Message Protocol
Type: 0 (Echo (ping) reply)
Code: 0
Checksum: 0x4830 [correct]
[Checksum Status: Good]
Identifier (BE): 1 (0x0001)
Identifier (LE): 256 (0x0100)
Sequence number (BE): 3371 (0x0d2b)
Sequence number (LE): 11021 (0x2b0d)
[Request frame: 27]
[Response time: 104.149 ms]
Data (32 bytes)
Data: 6162636465666768696a6b6c6d6e6f707172737475767761...
[Length: 32]
Data (32 bytes)
Data: 6162636465666768696a6b6c6d6e6f707172737475767761...
[Length: 32]
ICMP type is 0 and code number is 0. checksum, sequence number and identifier
fields are present except from the type and code number. They all are 2 bytes each.
[Destination GeoIP: Unknown]
Internet Control Message Protocol
Type: 0 (Echo (ping) reply)
Code: 0
Checksum: 0x4830 [correct]
[Checksum Status: Good]
Identifier (BE): 1 (0x0001)
Identifier (LE): 256 (0x0100)
Sequence number (BE): 3371 (0x0d2b)
Sequence number (LE): 11021 (0x2b0d)
[Request frame: 27]
[Response time: 104.149 ms]
Data (32 bytes)
Data: 6162636465666768696a6b6c6d6e6f707172737475767761...
[Length: 32]
Data (32 bytes)
Data: 6162636465666768696a6b6c6d6e6f707172737475767761...
[Length: 32]
ICMP type is 0 and code number is 0. checksum, sequence number and identifier
fields are present except from the type and code number. They all are 2 bytes each.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
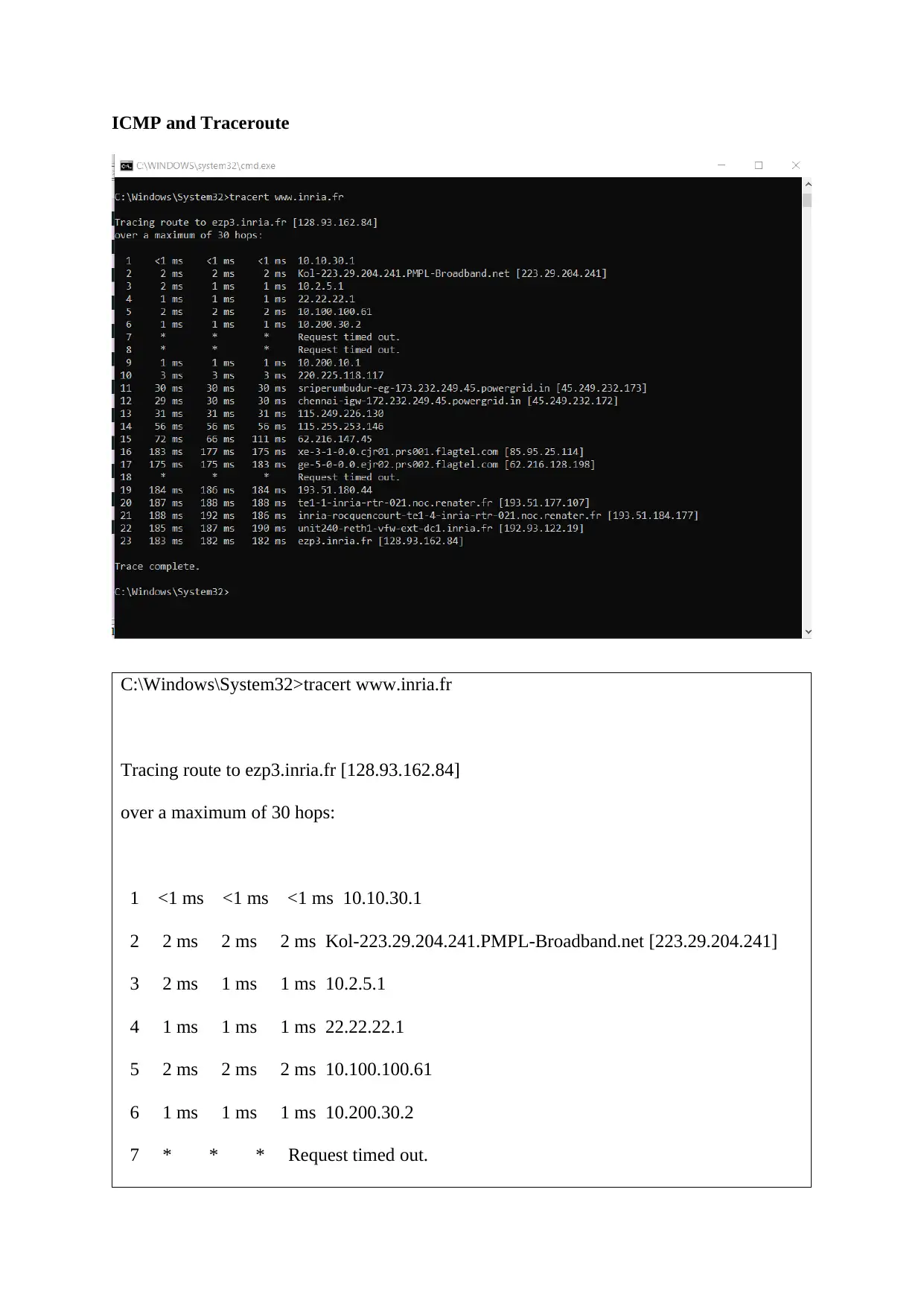
ICMP and Traceroute
C:\Windows\System32>tracert www.inria.fr
Tracing route to ezp3.inria.fr [128.93.162.84]
over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms 10.10.30.1
2 2 ms 2 ms 2 ms Kol-223.29.204.241.PMPL-Broadband.net [223.29.204.241]
3 2 ms 1 ms 1 ms 10.2.5.1
4 1 ms 1 ms 1 ms 22.22.22.1
5 2 ms 2 ms 2 ms 10.100.100.61
6 1 ms 1 ms 1 ms 10.200.30.2
7 * * * Request timed out.
C:\Windows\System32>tracert www.inria.fr
Tracing route to ezp3.inria.fr [128.93.162.84]
over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms 10.10.30.1
2 2 ms 2 ms 2 ms Kol-223.29.204.241.PMPL-Broadband.net [223.29.204.241]
3 2 ms 1 ms 1 ms 10.2.5.1
4 1 ms 1 ms 1 ms 22.22.22.1
5 2 ms 2 ms 2 ms 10.100.100.61
6 1 ms 1 ms 1 ms 10.200.30.2
7 * * * Request timed out.
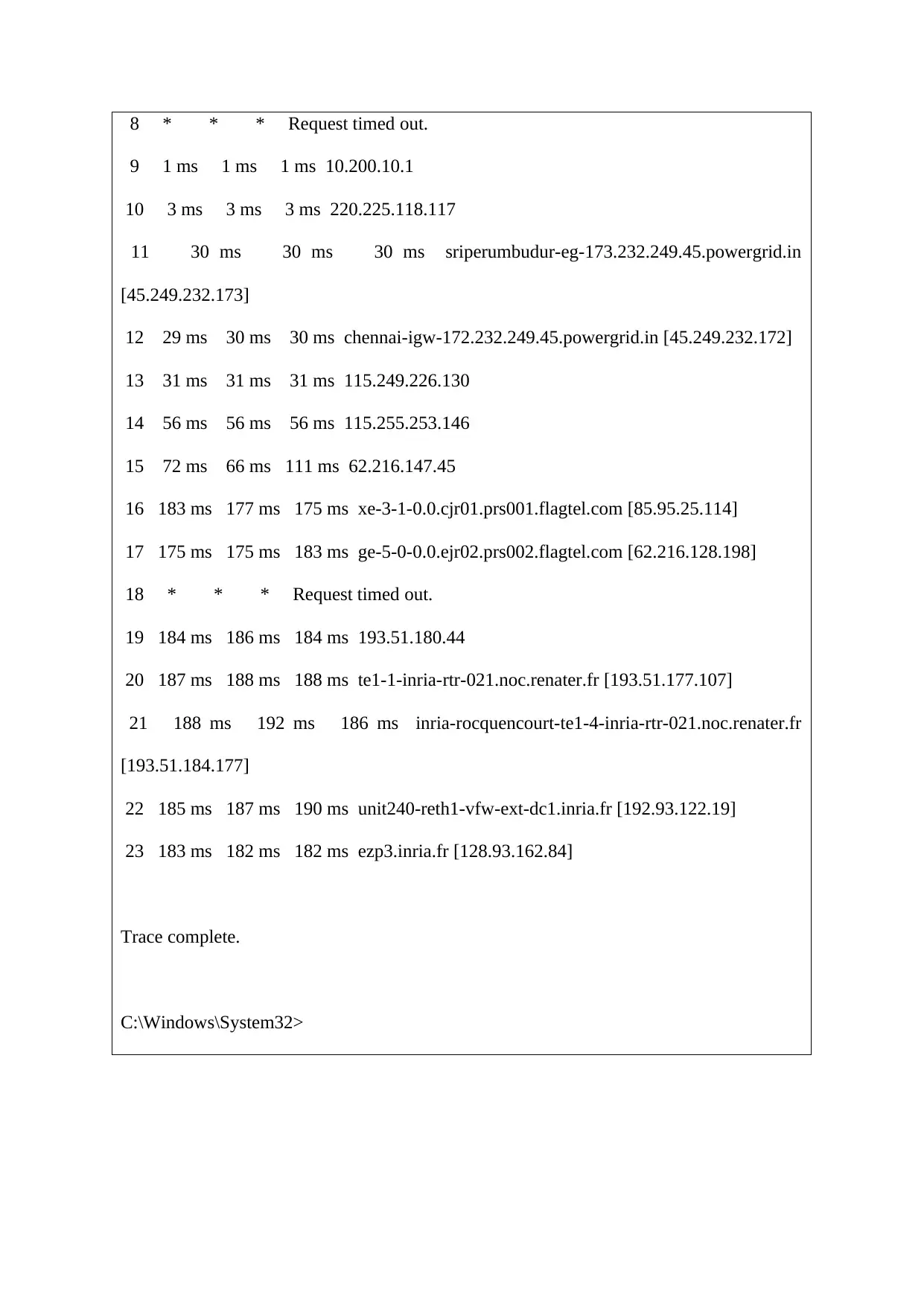
8 * * * Request timed out.
9 1 ms 1 ms 1 ms 10.200.10.1
10 3 ms 3 ms 3 ms 220.225.118.117
11 30 ms 30 ms 30 ms sriperumbudur-eg-173.232.249.45.powergrid.in
[45.249.232.173]
12 29 ms 30 ms 30 ms chennai-igw-172.232.249.45.powergrid.in [45.249.232.172]
13 31 ms 31 ms 31 ms 115.249.226.130
14 56 ms 56 ms 56 ms 115.255.253.146
15 72 ms 66 ms 111 ms 62.216.147.45
16 183 ms 177 ms 175 ms xe-3-1-0.0.cjr01.prs001.flagtel.com [85.95.25.114]
17 175 ms 175 ms 183 ms ge-5-0-0.0.ejr02.prs002.flagtel.com [62.216.128.198]
18 * * * Request timed out.
19 184 ms 186 ms 184 ms 193.51.180.44
20 187 ms 188 ms 188 ms te1-1-inria-rtr-021.noc.renater.fr [193.51.177.107]
21 188 ms 192 ms 186 ms inria-rocquencourt-te1-4-inria-rtr-021.noc.renater.fr
[193.51.184.177]
22 185 ms 187 ms 190 ms unit240-reth1-vfw-ext-dc1.inria.fr [192.93.122.19]
23 183 ms 182 ms 182 ms ezp3.inria.fr [128.93.162.84]
Trace complete.
C:\Windows\System32>
9 1 ms 1 ms 1 ms 10.200.10.1
10 3 ms 3 ms 3 ms 220.225.118.117
11 30 ms 30 ms 30 ms sriperumbudur-eg-173.232.249.45.powergrid.in
[45.249.232.173]
12 29 ms 30 ms 30 ms chennai-igw-172.232.249.45.powergrid.in [45.249.232.172]
13 31 ms 31 ms 31 ms 115.249.226.130
14 56 ms 56 ms 56 ms 115.255.253.146
15 72 ms 66 ms 111 ms 62.216.147.45
16 183 ms 177 ms 175 ms xe-3-1-0.0.cjr01.prs001.flagtel.com [85.95.25.114]
17 175 ms 175 ms 183 ms ge-5-0-0.0.ejr02.prs002.flagtel.com [62.216.128.198]
18 * * * Request timed out.
19 184 ms 186 ms 184 ms 193.51.180.44
20 187 ms 188 ms 188 ms te1-1-inria-rtr-021.noc.renater.fr [193.51.177.107]
21 188 ms 192 ms 186 ms inria-rocquencourt-te1-4-inria-rtr-021.noc.renater.fr
[193.51.184.177]
22 185 ms 187 ms 190 ms unit240-reth1-vfw-ext-dc1.inria.fr [192.93.122.19]
23 183 ms 182 ms 182 ms ezp3.inria.fr [128.93.162.84]
Trace complete.
C:\Windows\System32>
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

