MITS5003 Wireless Networks: Encoding, Multiplexing, Error Control
VerifiedAdded on 2023/06/10
|14
|2004
|421
Homework Assignment
AI Summary
This assignment solution delves into various aspects of wireless communication, starting with encoding techniques like Bipolar AMI, Manchester, and Pseudo-ternary encoding, and their application in encoding a robot's status string. It further explains ASK, FSK, and PSK encoding methods. The solution includes a calculation of CRC for error detection using a polynomial divisor. Flow control techniques like Stop and Wait, and Sliding Window, along with error control methods such as error detection and vertical redundancy check are discussed. The assignment also covers multiplexing techniques including TDM, FDM, and CDMA, contrasting them with OFDM and its application in 4G and WiMAX. Finally, it addresses Wi-Fi network design, BSS, ESS, throughput calculation, IEEE standards, and security strategies. Desklib is your go-to resource for more solved assignments and study materials.

WIRELESS COMMUNICATION
By Name
Course
Instructor
Institution
Location
Date
By Name
Course
Instructor
Institution
Location
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Part I: Encoding and error control
a) Calculate the data rate required for robot to remote controller communication
Data rate= number of bits sent/ second
Total number of bits send = 16
Time= 2seconds
16/2
8mbs
b) Explain 3 types of suitable encoding techniques could be used to encode the status
string.
i. Bipolar AMI encoding: a no line signal represent a zero and a one is represented
by positives and negatives. In this technique, there is no loss of synchronization
with a long string ones (Maeda, 2014)
ii. Manchester encoding: there is a transition at the middle of one bit. low to high
represent a one while high to low shows a zero. The transition serves as a clock
and data. This encoding is used in 10Mbps Ethernet (Amiri & Ali, 2013)
iii. Pseudo-ternary encoding: One is represented by the absence of a line signal. An
alternating negative and positive indicates zero. There is no loss of
synchronization with a long string of zeros.
c)
i. Write the status string in binary for this instance
Convert all the parameters to a binary
5m/s = 0101
48cm = 110000
Motor functionality = 1111
75%= 0.11
Combine all the binary to form one string
a) Calculate the data rate required for robot to remote controller communication
Data rate= number of bits sent/ second
Total number of bits send = 16
Time= 2seconds
16/2
8mbs
b) Explain 3 types of suitable encoding techniques could be used to encode the status
string.
i. Bipolar AMI encoding: a no line signal represent a zero and a one is represented
by positives and negatives. In this technique, there is no loss of synchronization
with a long string ones (Maeda, 2014)
ii. Manchester encoding: there is a transition at the middle of one bit. low to high
represent a one while high to low shows a zero. The transition serves as a clock
and data. This encoding is used in 10Mbps Ethernet (Amiri & Ali, 2013)
iii. Pseudo-ternary encoding: One is represented by the absence of a line signal. An
alternating negative and positive indicates zero. There is no loss of
synchronization with a long string of zeros.
c)
i. Write the status string in binary for this instance
Convert all the parameters to a binary
5m/s = 0101
48cm = 110000
Motor functionality = 1111
75%= 0.11
Combine all the binary to form one string
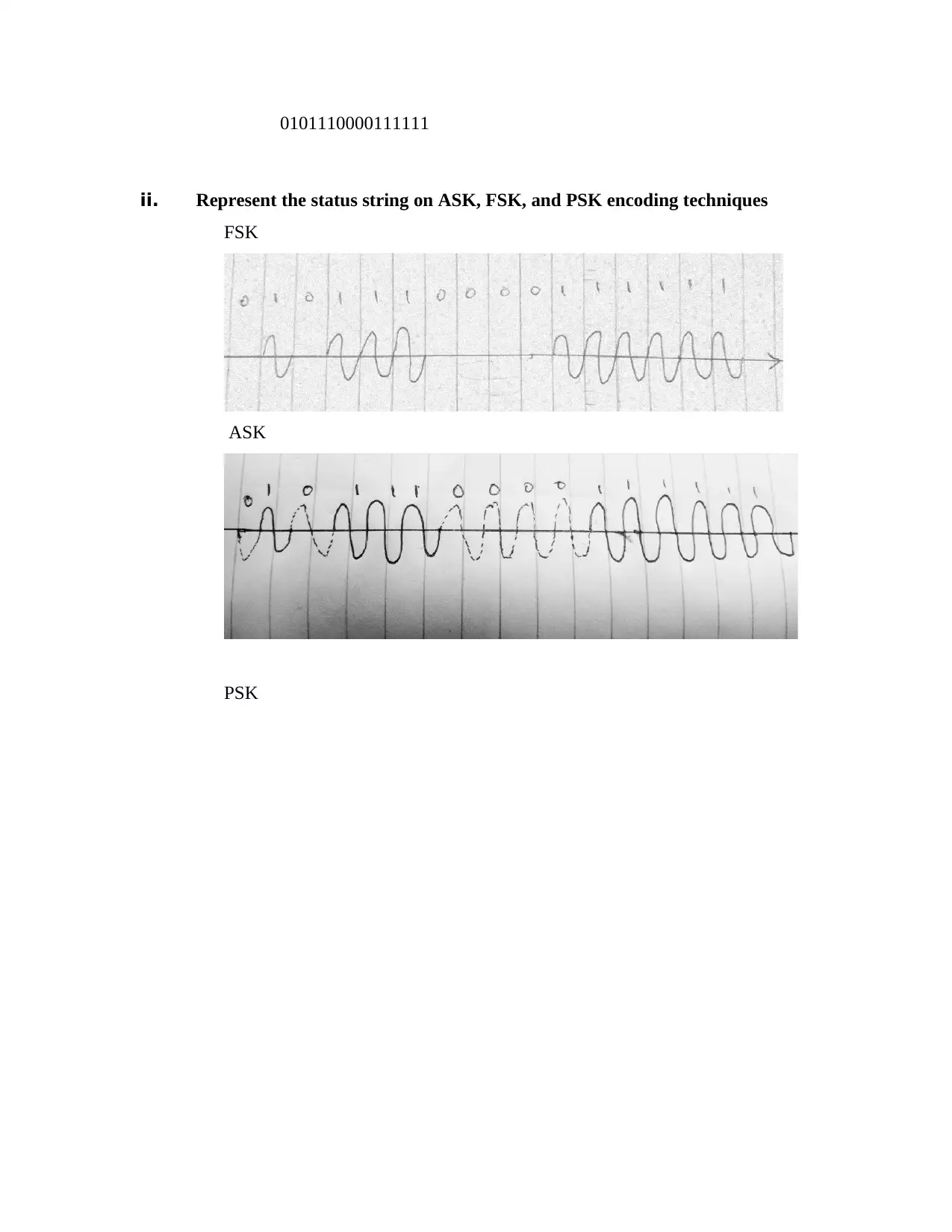
0101110000111111
ii. Represent the status string on ASK, FSK, and PSK encoding techniques
FSK
ASK
PSK
ii. Represent the status string on ASK, FSK, and PSK encoding techniques
FSK
ASK
PSK
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
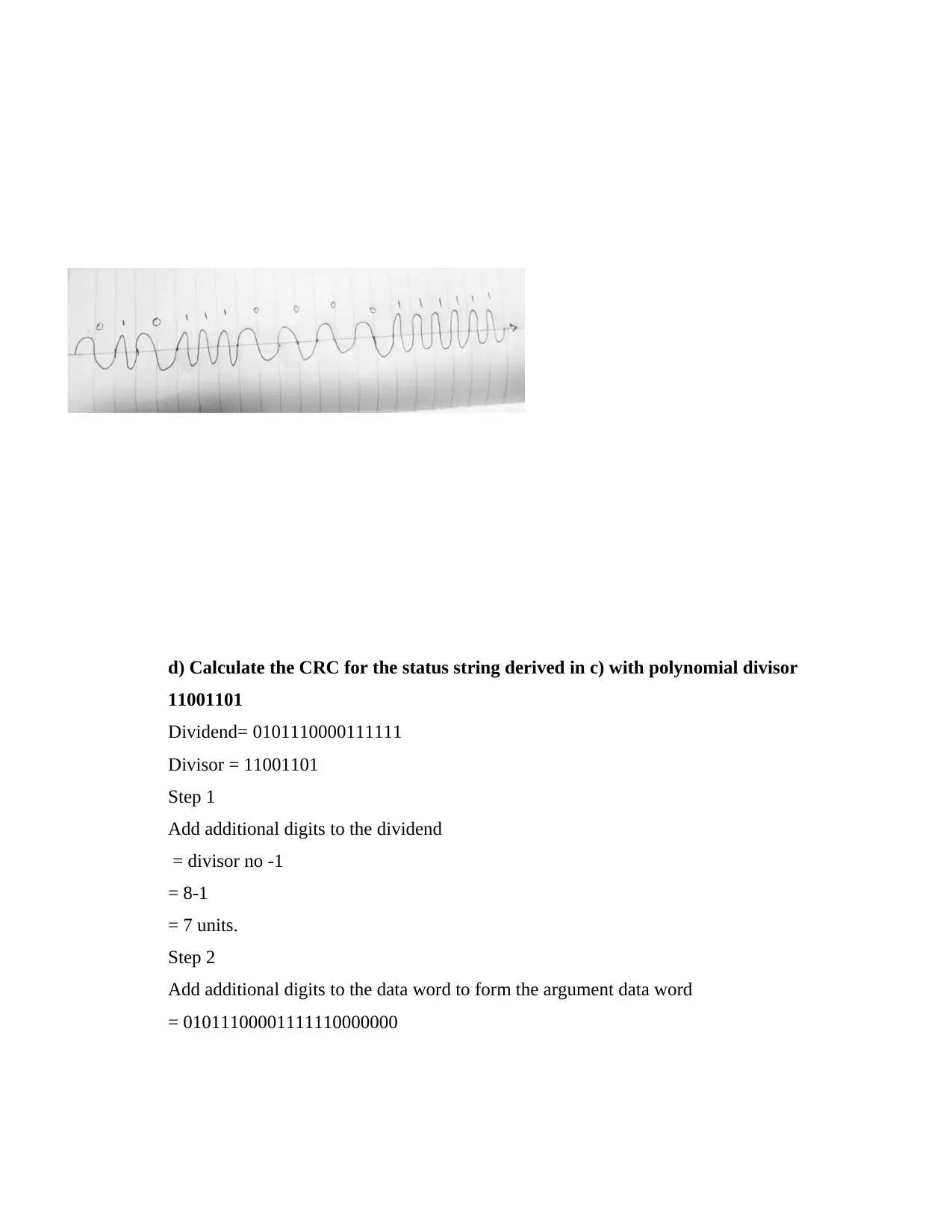
d) Calculate the CRC for the status string derived in c) with polynomial divisor
11001101
Dividend= 0101110000111111
Divisor = 11001101
Step 1
Add additional digits to the dividend
= divisor no -1
= 8-1
= 7 units.
Step 2
Add additional digits to the data word to form the argument data word
= 01011100001111110000000
11001101
Dividend= 0101110000111111
Divisor = 11001101
Step 1
Add additional digits to the dividend
= divisor no -1
= 8-1
= 7 units.
Step 2
Add additional digits to the data word to form the argument data word
= 01011100001111110000000
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
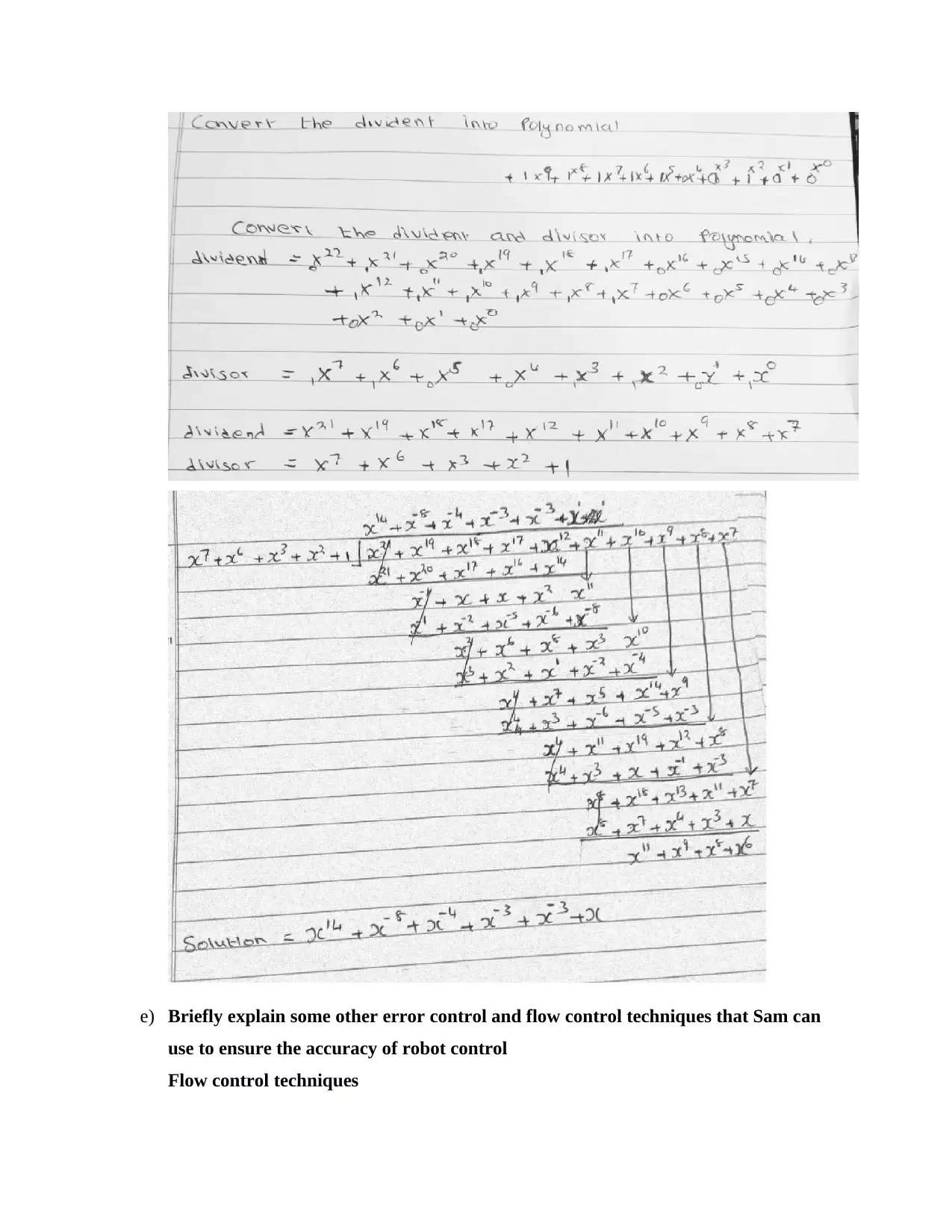
e) Briefly explain some other error control and flow control techniques that Sam can
use to ensure the accuracy of robot control
Flow control techniques
use to ensure the accuracy of robot control
Flow control techniques

1. Stop and wait control
When a frame is sent the sender wait for an acknowledgment. When the acknowledgment
s received then the next frame is sent.. the process continues till the end of the
transmission. In this techniques, the receiver indicates when its ready to receive data in
each frame(Gomez, Demirkol, & Paradells, 2011).
2. Sliding window flow control
Both the receiver and the sender have a window frame. Frames are numbered according
to the sliding window. Many frames from the sender as many as the window can hold are
sent. the receiver when it has received enough frames sends an acknowledgment all frame
slide. Once the acknowledgment is sent, the receiver indicates the number of next frames
it expects to receive(Zhang, Zhang, Ma, & Kan, 2010).
Error control techniques
1. Error detection: it uses the redundancy concept that is adding extra-bits to detect
errors at the destination. when the checking function performs the error detection
action on the stream of the bit, the data portion is either accepted or rejected.
2. Vertical redundancy check: this technique a parity bit which is called a redundant
bit is appended to every unit of data. This makes the number of the 1’s together
with the redundant bit become even. If the bits are already even the parity nit
added is a 0 (Wu & Sutardja, 2011)
Part II: Multiplexing and multiple access
a) Explain TDM, FDM and CDMA multiplexing techniques with suitable diagrams
1. TDM
is it a method for transmitting and receiving an independent signal over a path. It allows sync of
switches on each end of transmitting line. method of transmitting and also receiving an
independent signal over a path of the signal by synchronizing switches at each end of the
transmission line. It is used when the bit rate(Yazdani, 2008)
When a frame is sent the sender wait for an acknowledgment. When the acknowledgment
s received then the next frame is sent.. the process continues till the end of the
transmission. In this techniques, the receiver indicates when its ready to receive data in
each frame(Gomez, Demirkol, & Paradells, 2011).
2. Sliding window flow control
Both the receiver and the sender have a window frame. Frames are numbered according
to the sliding window. Many frames from the sender as many as the window can hold are
sent. the receiver when it has received enough frames sends an acknowledgment all frame
slide. Once the acknowledgment is sent, the receiver indicates the number of next frames
it expects to receive(Zhang, Zhang, Ma, & Kan, 2010).
Error control techniques
1. Error detection: it uses the redundancy concept that is adding extra-bits to detect
errors at the destination. when the checking function performs the error detection
action on the stream of the bit, the data portion is either accepted or rejected.
2. Vertical redundancy check: this technique a parity bit which is called a redundant
bit is appended to every unit of data. This makes the number of the 1’s together
with the redundant bit become even. If the bits are already even the parity nit
added is a 0 (Wu & Sutardja, 2011)
Part II: Multiplexing and multiple access
a) Explain TDM, FDM and CDMA multiplexing techniques with suitable diagrams
1. TDM
is it a method for transmitting and receiving an independent signal over a path. It allows sync of
switches on each end of transmitting line. method of transmitting and also receiving an
independent signal over a path of the signal by synchronizing switches at each end of the
transmission line. It is used when the bit rate(Yazdani, 2008)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
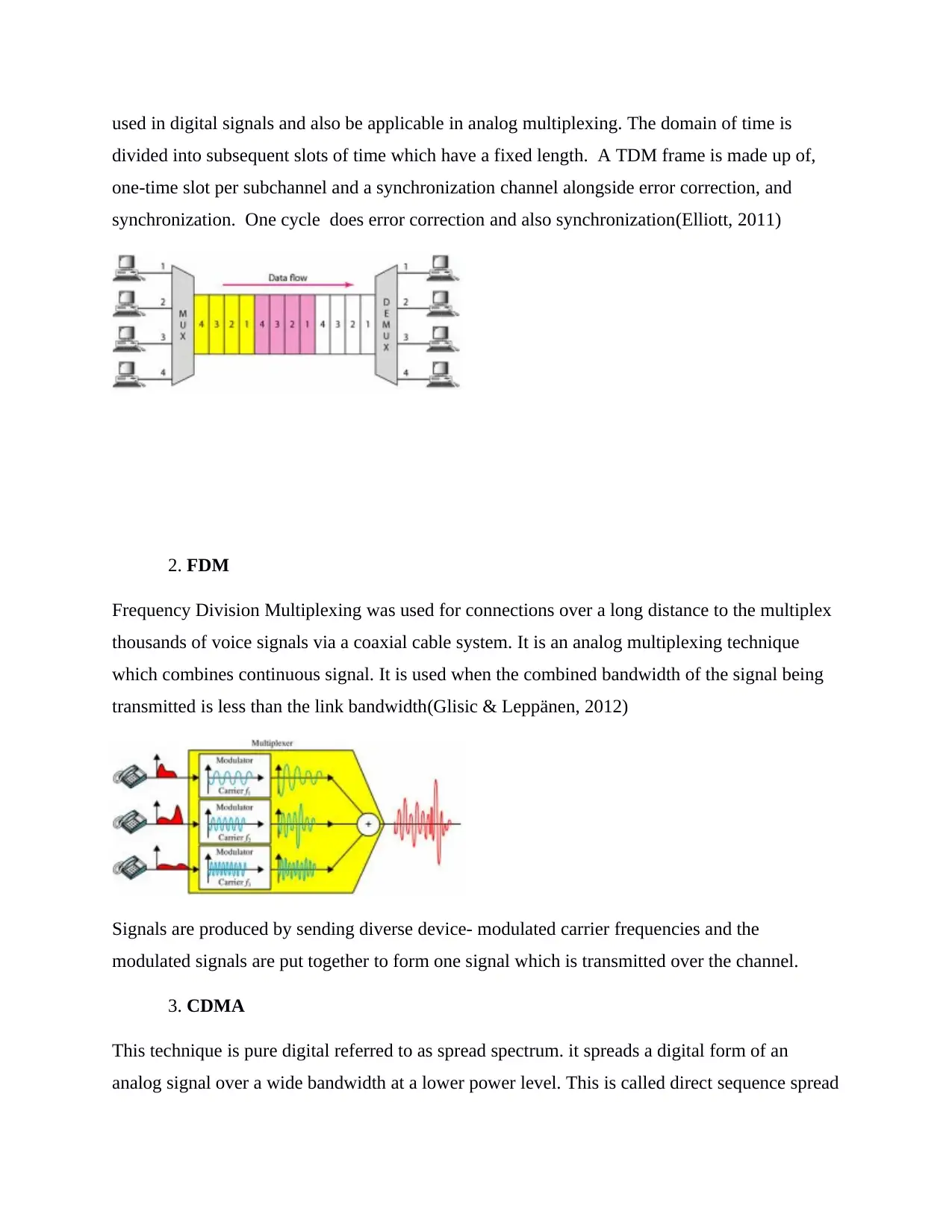
used in digital signals and also be applicable in analog multiplexing. The domain of time is
divided into subsequent slots of time which have a fixed length. A TDM frame is made up of,
one-time slot per subchannel and a synchronization channel alongside error correction, and
synchronization. One cycle does error correction and also synchronization(Elliott, 2011)
2. FDM
Frequency Division Multiplexing was used for connections over a long distance to the multiplex
thousands of voice signals via a coaxial cable system. It is an analog multiplexing technique
which combines continuous signal. It is used when the combined bandwidth of the signal being
transmitted is less than the link bandwidth(Glisic & Leppänen, 2012)
Signals are produced by sending diverse device- modulated carrier frequencies and the
modulated signals are put together to form one signal which is transmitted over the channel.
3. CDMA
This technique is pure digital referred to as spread spectrum. it spreads a digital form of an
analog signal over a wide bandwidth at a lower power level. This is called direct sequence spread
divided into subsequent slots of time which have a fixed length. A TDM frame is made up of,
one-time slot per subchannel and a synchronization channel alongside error correction, and
synchronization. One cycle does error correction and also synchronization(Elliott, 2011)
2. FDM
Frequency Division Multiplexing was used for connections over a long distance to the multiplex
thousands of voice signals via a coaxial cable system. It is an analog multiplexing technique
which combines continuous signal. It is used when the combined bandwidth of the signal being
transmitted is less than the link bandwidth(Glisic & Leppänen, 2012)
Signals are produced by sending diverse device- modulated carrier frequencies and the
modulated signals are put together to form one signal which is transmitted over the channel.
3. CDMA
This technique is pure digital referred to as spread spectrum. it spreads a digital form of an
analog signal over a wide bandwidth at a lower power level. This is called direct sequence spread
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
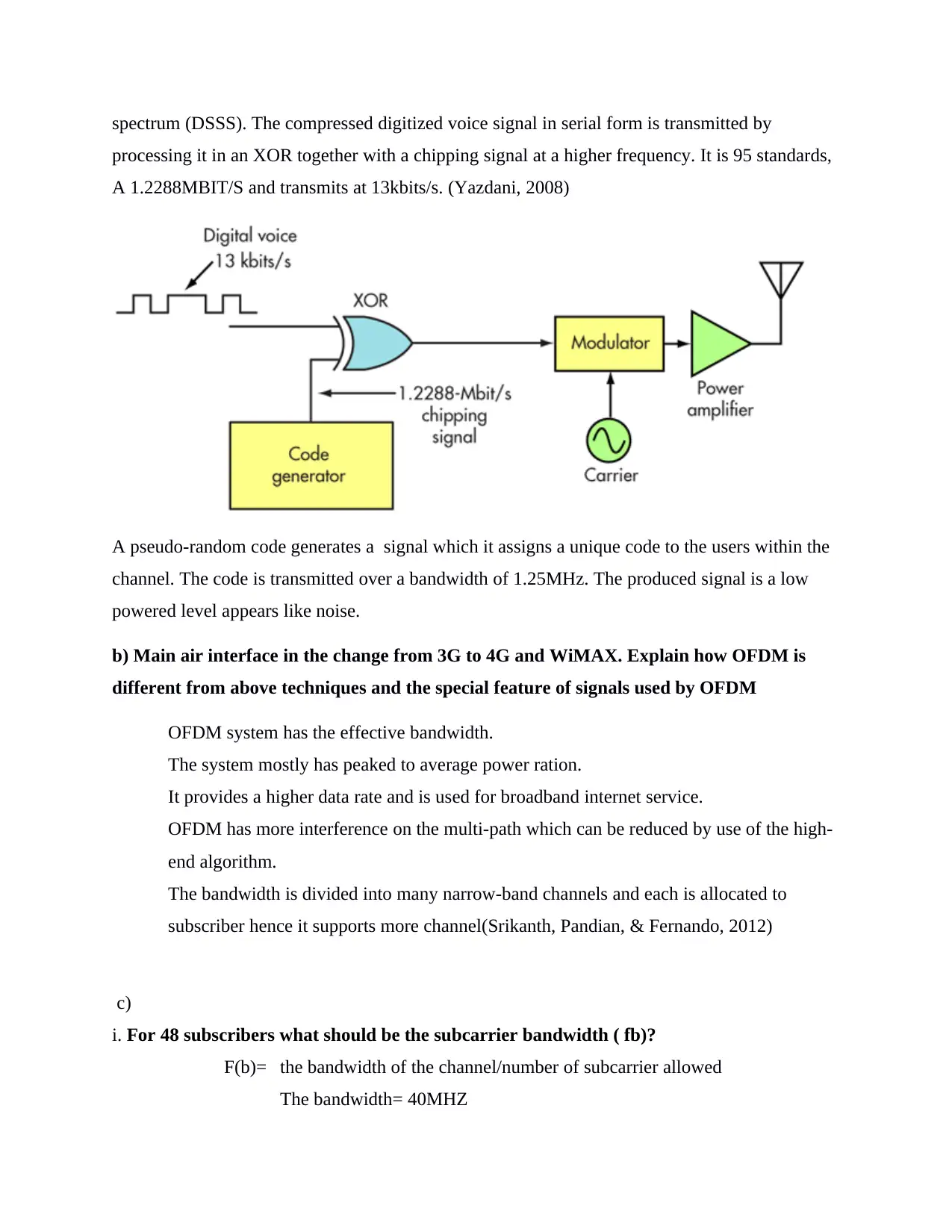
spectrum (DSSS). The compressed digitized voice signal in serial form is transmitted by
processing it in an XOR together with a chipping signal at a higher frequency. It is 95 standards,
A 1.2288MBIT/S and transmits at 13kbits/s. (Yazdani, 2008)
A pseudo-random code generates a signal which it assigns a unique code to the users within the
channel. The code is transmitted over a bandwidth of 1.25MHz. The produced signal is a low
powered level appears like noise.
b) Main air interface in the change from 3G to 4G and WiMAX. Explain how OFDM is
different from above techniques and the special feature of signals used by OFDM
OFDM system has the effective bandwidth.
The system mostly has peaked to average power ration.
It provides a higher data rate and is used for broadband internet service.
OFDM has more interference on the multi-path which can be reduced by use of the high-
end algorithm.
The bandwidth is divided into many narrow-band channels and each is allocated to
subscriber hence it supports more channel(Srikanth, Pandian, & Fernando, 2012)
c)
i. For 48 subscribers what should be the subcarrier bandwidth ( fb)?
F(b)= the bandwidth of the channel/number of subcarrier allowed
The bandwidth= 40MHZ
processing it in an XOR together with a chipping signal at a higher frequency. It is 95 standards,
A 1.2288MBIT/S and transmits at 13kbits/s. (Yazdani, 2008)
A pseudo-random code generates a signal which it assigns a unique code to the users within the
channel. The code is transmitted over a bandwidth of 1.25MHz. The produced signal is a low
powered level appears like noise.
b) Main air interface in the change from 3G to 4G and WiMAX. Explain how OFDM is
different from above techniques and the special feature of signals used by OFDM
OFDM system has the effective bandwidth.
The system mostly has peaked to average power ration.
It provides a higher data rate and is used for broadband internet service.
OFDM has more interference on the multi-path which can be reduced by use of the high-
end algorithm.
The bandwidth is divided into many narrow-band channels and each is allocated to
subscriber hence it supports more channel(Srikanth, Pandian, & Fernando, 2012)
c)
i. For 48 subscribers what should be the subcarrier bandwidth ( fb)?
F(b)= the bandwidth of the channel/number of subcarrier allowed
The bandwidth= 40MHZ

sub carriers=128
F(b) =40MHZ/128 subcarrier
=0.3125MHz
=312.5KHZ
ii. Propose a suitable subcarrier bit time of T to achieve orthogonality
Bit time = 1/fb
Fb = (312.5khz)
=1s/312.5Khz
Bit time = 0.0032 microsecond
iii. Explain how OFDM overcomes the issue of inter-symbol interference
The OFDM solve the problem of inter-symbol interference by modulating the data in the
frequency domain over the short sub-carriers and this make the OFDM long enough, it is longer
than the delay spread. To avoid inter OFDM symbol interference a cyclic prefix of appropriate
length chosen.
Part III: Wi-Fi
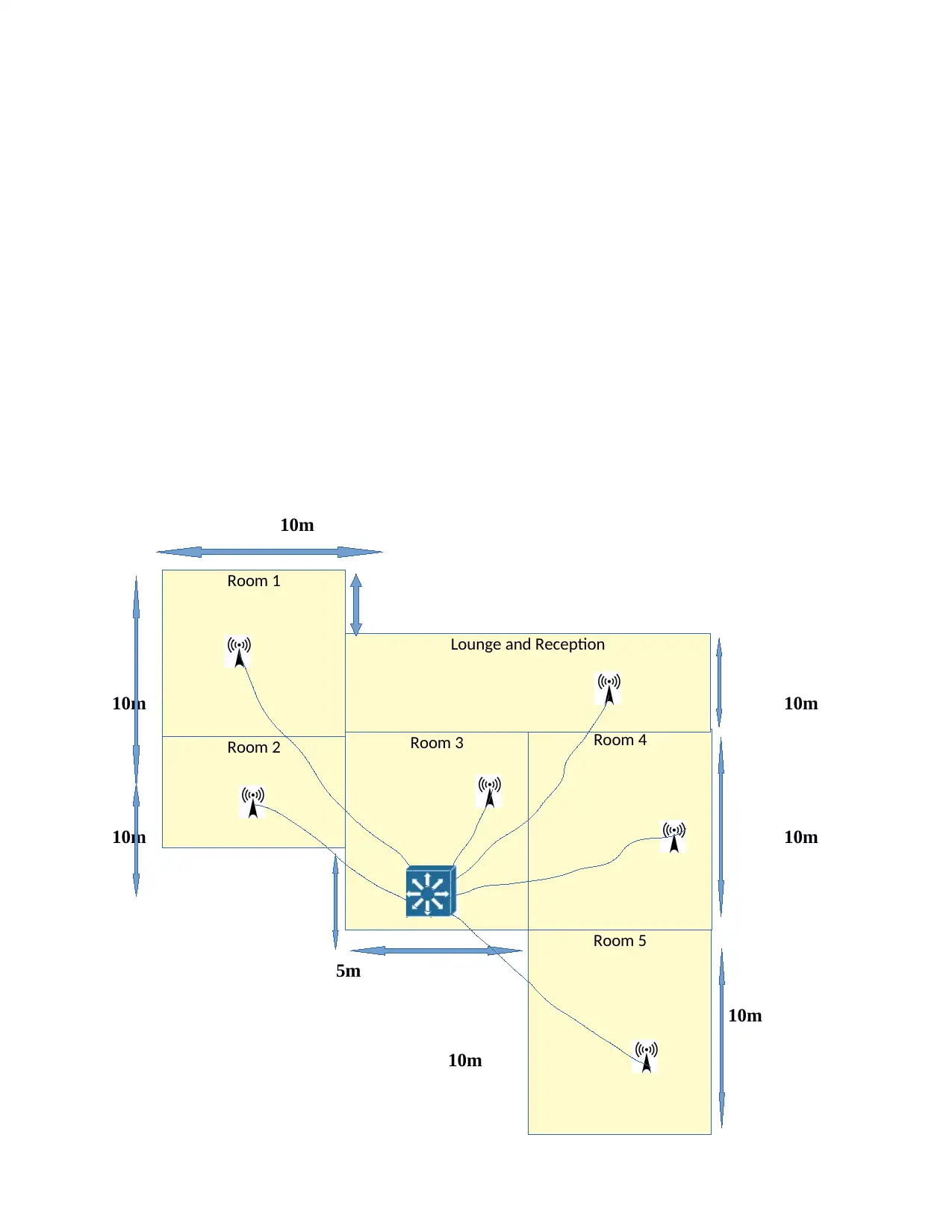
a) Design the network specifying the locations of access points and distributions system
showing the backbone network.
\
F(b) =40MHZ/128 subcarrier
=0.3125MHz
=312.5KHZ
ii. Propose a suitable subcarrier bit time of T to achieve orthogonality
Bit time = 1/fb
Fb = (312.5khz)
=1s/312.5Khz
Bit time = 0.0032 microsecond
iii. Explain how OFDM overcomes the issue of inter-symbol interference
The OFDM solve the problem of inter-symbol interference by modulating the data in the
frequency domain over the short sub-carriers and this make the OFDM long enough, it is longer
than the delay spread. To avoid inter OFDM symbol interference a cyclic prefix of appropriate
length chosen.
Part III: Wi-Fi
a) Design the network specifying the locations of access points and distributions system
showing the backbone network.
\
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10m
10m 10m
10m 10m
5m
10m
10m
Room 1
Room 2 Room 3 Room 4
Room 5
Lounge and Reception
10m 10m
10m 10m
5m
10m
10m
Room 1
Room 2 Room 3 Room 4
Room 5
Lounge and Reception
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10m
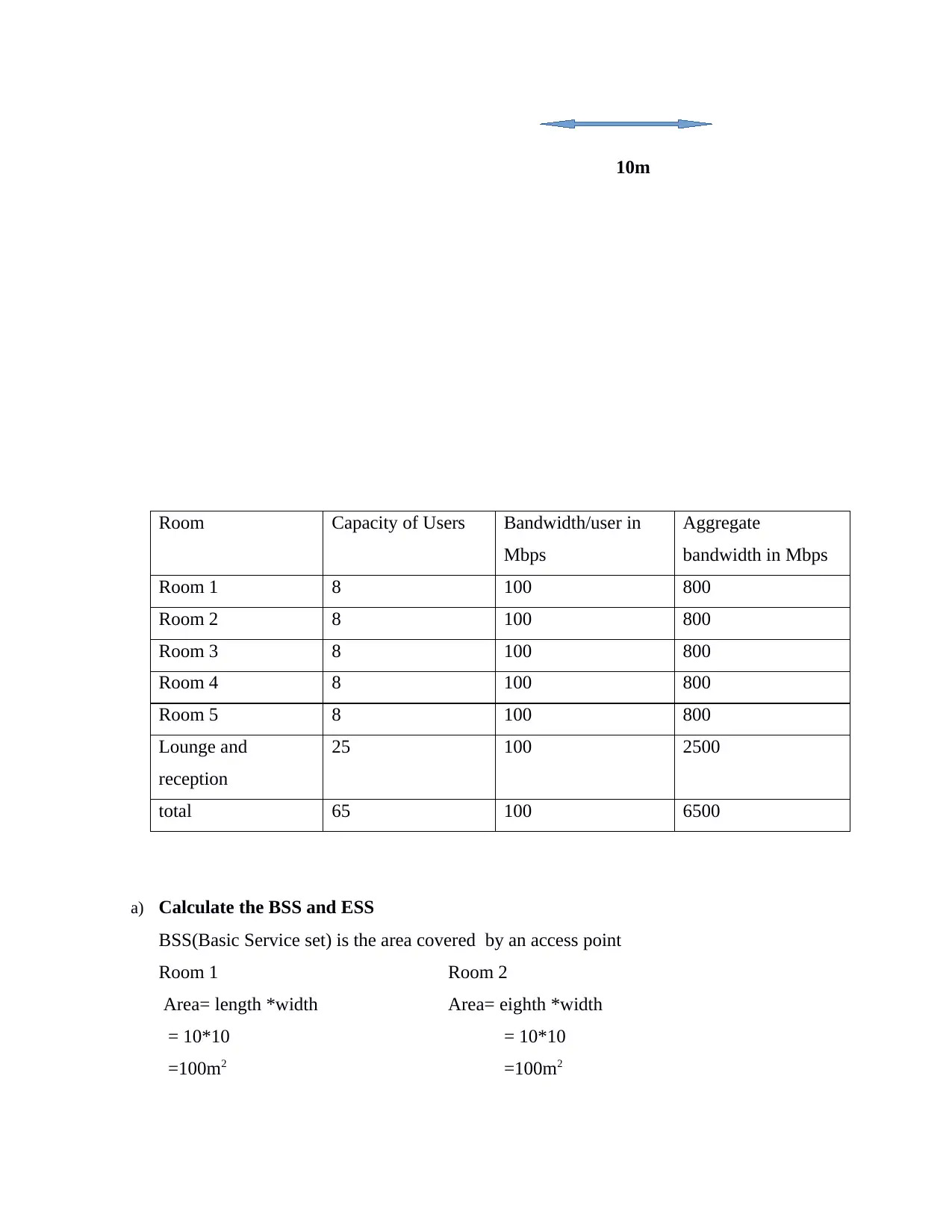
Room Capacity of Users Bandwidth/user in
Mbps
Aggregate
bandwidth in Mbps
Room 1 8 100 800
Room 2 8 100 800
Room 3 8 100 800
Room 4 8 100 800
Room 5 8 100 800
Lounge and
reception
25 100 2500
total 65 100 6500
a) Calculate the BSS and ESS
BSS(Basic Service set) is the area covered by an access point
Room 1 Room 2
Area= length *width Area= eighth *width
= 10*10 = 10*10
=100m2 =100m2
Room Capacity of Users Bandwidth/user in
Mbps
Aggregate
bandwidth in Mbps
Room 1 8 100 800
Room 2 8 100 800
Room 3 8 100 800
Room 4 8 100 800
Room 5 8 100 800
Lounge and
reception
25 100 2500
total 65 100 6500
a) Calculate the BSS and ESS
BSS(Basic Service set) is the area covered by an access point
Room 1 Room 2
Area= length *width Area= eighth *width
= 10*10 = 10*10
=100m2 =100m2

Room 3 Room 4
Area= length *width Area= length *width
= 10*10 = 10*10
=100m2 =100m2
Room 5 lounge and reception
Area= length *width Area= length *width
= 10*10 = 20*10
=100m2 =100m2
ESS is the total area of the covered by the various BSS
ESS=(Room1 +room2+Room3+Room4+Room5+Lounge)
= 100+100+100+100+100+200
=700m2
b) Calculate the throughput for the DS.
The actual data passing through the network/ second
For each room throughput= 8*100mbps
The rooms through put = 5*800mbps
Lounge and reception throughput = 25*100mbps
Lounge +rooms = 2500+4000
= 6500mbps
c) Recommend a suitable IEEE Substandard for the network and give a reason for your
choice.
IEEE 802.11ac. this substandard is the next generation for WIFI. It will give three times
faster connection that the substandard IEEE 802.11b/n. this WIFI standard allows for use
of multiple users. It offers fast surfing, smooth video streaming and less buffering (Ong et
al., 2011).
Area= length *width Area= length *width
= 10*10 = 10*10
=100m2 =100m2
Room 5 lounge and reception
Area= length *width Area= length *width
= 10*10 = 20*10
=100m2 =100m2
ESS is the total area of the covered by the various BSS
ESS=(Room1 +room2+Room3+Room4+Room5+Lounge)
= 100+100+100+100+100+200
=700m2
b) Calculate the throughput for the DS.
The actual data passing through the network/ second
For each room throughput= 8*100mbps
The rooms through put = 5*800mbps
Lounge and reception throughput = 25*100mbps
Lounge +rooms = 2500+4000
= 6500mbps
c) Recommend a suitable IEEE Substandard for the network and give a reason for your
choice.
IEEE 802.11ac. this substandard is the next generation for WIFI. It will give three times
faster connection that the substandard IEEE 802.11b/n. this WIFI standard allows for use
of multiple users. It offers fast surfing, smooth video streaming and less buffering (Ong et
al., 2011).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



