MITS5003 Wireless Networks & Communication Assignment 2 Solution
VerifiedAdded on 2022/08/24
|11
|1047
|26
Homework Assignment
AI Summary
This assignment solution for MITS5003 Wireless Networks and Communication addresses several key concepts in wireless communication. It begins by exploring handoff strategies, including the impact of delay and signal strength considerations. The solution then delves into Cyclic Redundancy Check (CRC) error detection, detailing the process and methods involved. Further, the assignment calculates traffic intensity for multiple users and analyzes cell division techniques in cellular networks, explaining hexagonal cell structures and cell splitting. The solution also includes references to relevant research papers.
1
A) .
b) .
A) .
b) .
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
c) .
d) .
d) .
e) .
f) .
f) .
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
g) .
2
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
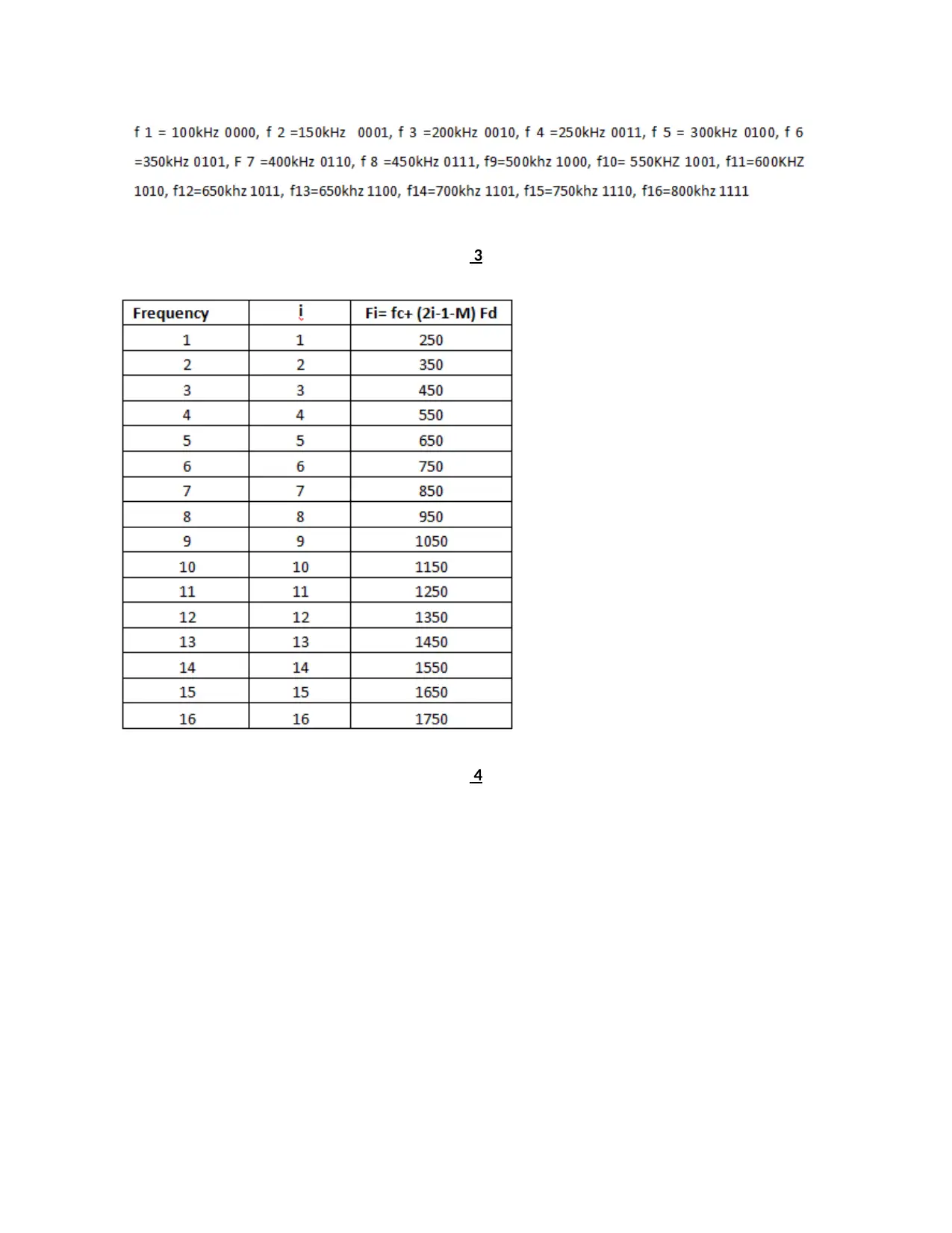
3
4
4
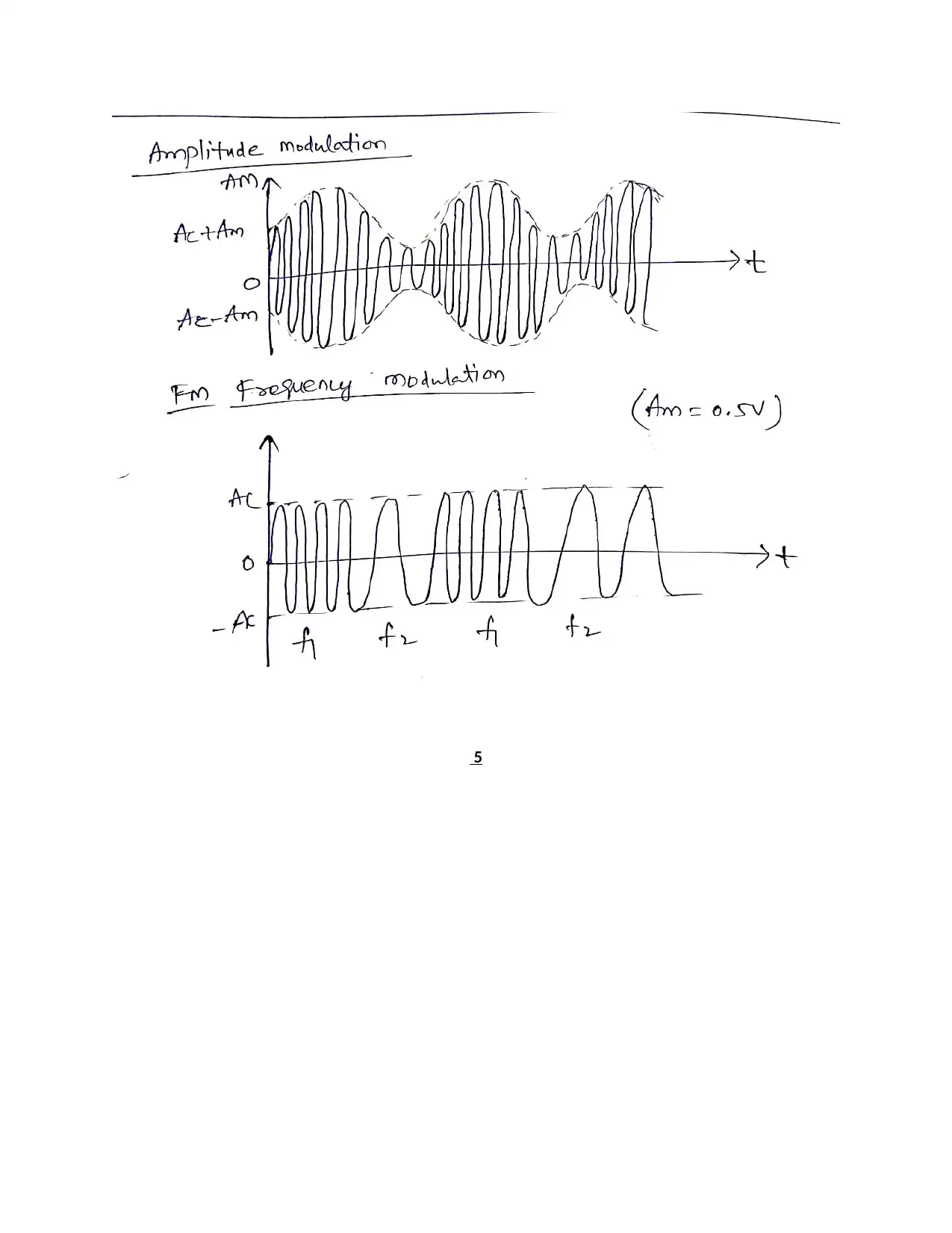
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
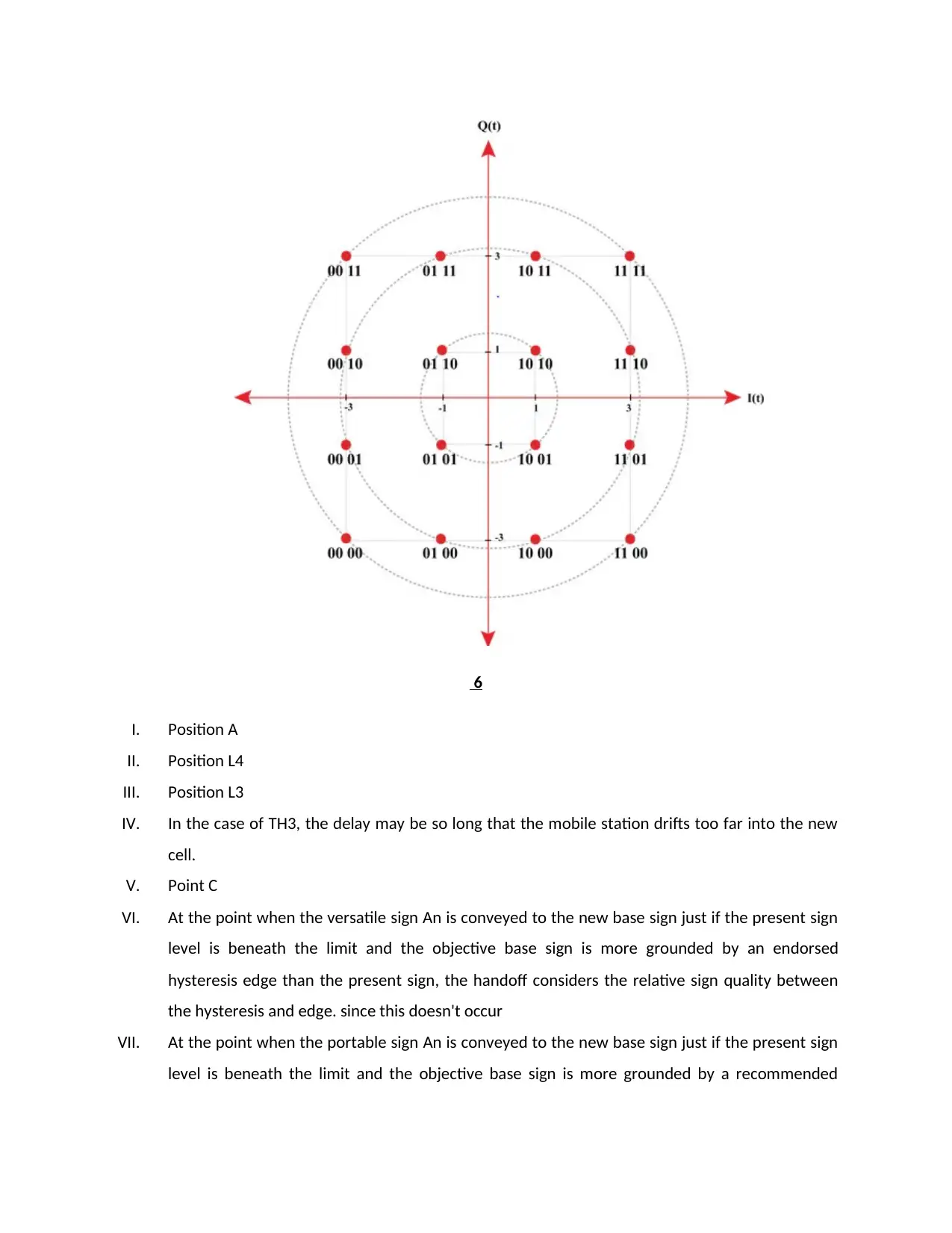
6
I. Position A
II. Position L4
III. Position L3
IV. In the case of TH3, the delay may be so long that the mobile station drifts too far into the new
cell.
V. Point C
VI. At the point when the versatile sign An is conveyed to the new base sign just if the present sign
level is beneath the limit and the objective base sign is more grounded by an endorsed
hysteresis edge than the present sign, the handoff considers the relative sign quality between
the hysteresis and edge. since this doesn't occur
VII. At the point when the portable sign An is conveyed to the new base sign just if the present sign
level is beneath the limit and the objective base sign is more grounded by a recommended
I. Position A
II. Position L4
III. Position L3
IV. In the case of TH3, the delay may be so long that the mobile station drifts too far into the new
cell.
V. Point C
VI. At the point when the versatile sign An is conveyed to the new base sign just if the present sign
level is beneath the limit and the objective base sign is more grounded by an endorsed
hysteresis edge than the present sign, the handoff considers the relative sign quality between
the hysteresis and edge. since this doesn't occur
VII. At the point when the portable sign An is conveyed to the new base sign just if the present sign
level is beneath the limit and the objective base sign is more grounded by a recommended
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
hysteresis edge than the present sign, the handoff considers the relative sign quality between
the hysteresis and edge. since this doesn't occur
VIII. Point L1
7
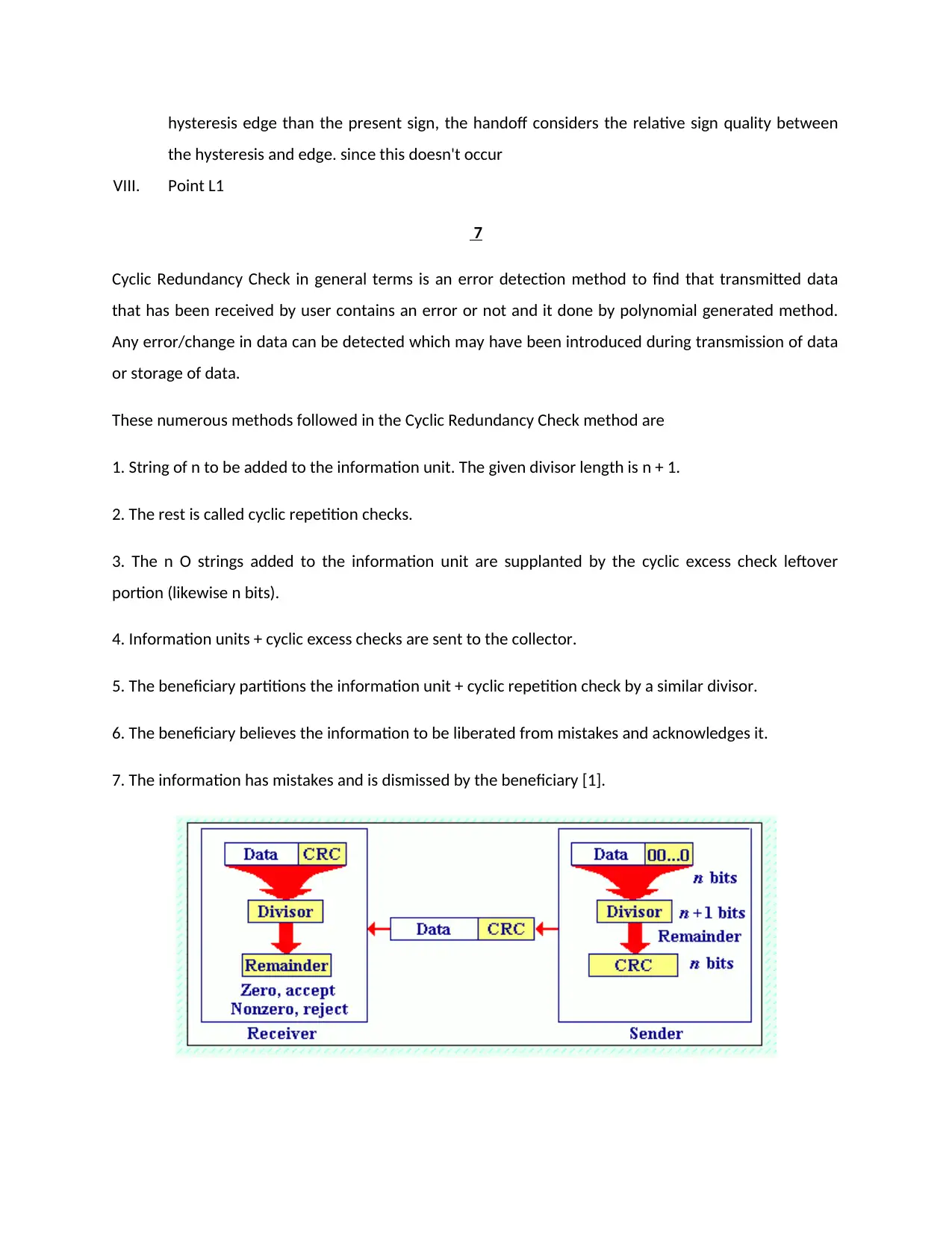
Cyclic Redundancy Check in general terms is an error detection method to find that transmitted data
that has been received by user contains an error or not and it done by polynomial generated method.
Any error/change in data can be detected which may have been introduced during transmission of data
or storage of data.
These numerous methods followed in the Cyclic Redundancy Check method are
1. String of n to be added to the information unit. The given divisor length is n + 1.
2. The rest is called cyclic repetition checks.
3. The n O strings added to the information unit are supplanted by the cyclic excess check leftover
portion (likewise n bits).
4. Information units + cyclic excess checks are sent to the collector.
5. The beneficiary partitions the information unit + cyclic repetition check by a similar divisor.
6. The beneficiary believes the information to be liberated from mistakes and acknowledges it.
7. The information has mistakes and is dismissed by the beneficiary [1].
the hysteresis and edge. since this doesn't occur
VIII. Point L1
7
Cyclic Redundancy Check in general terms is an error detection method to find that transmitted data
that has been received by user contains an error or not and it done by polynomial generated method.
Any error/change in data can be detected which may have been introduced during transmission of data
or storage of data.
These numerous methods followed in the Cyclic Redundancy Check method are
1. String of n to be added to the information unit. The given divisor length is n + 1.
2. The rest is called cyclic repetition checks.
3. The n O strings added to the information unit are supplanted by the cyclic excess check leftover
portion (likewise n bits).
4. Information units + cyclic excess checks are sent to the collector.
5. The beneficiary partitions the information unit + cyclic repetition check by a similar divisor.
6. The beneficiary believes the information to be liberated from mistakes and acknowledges it.
7. The information has mistakes and is dismissed by the beneficiary [1].

The n-bit Cyclic Redundancy Check obtained in organizes 2 replaces the O included at the completion of
the data unit. Recipient the entire string 1 is treated as a unit, Cyclic Redundancy Check segment by a
comparative divisor that was used to find the remainder of. If the string lands without botch, the Cyclic
Redundancy Check checker delivers the remaining zeros just as the data unit passes. If the string is
changed during the move, the division conveys a nonzero remaining segment just as the data unit
doesn't pass.
8
I. Total occupied time =
II. Total number of calls =
III. Time occupied per call for U1 =
Time occupied per call for U2 =
Time occupied per call for U3 =
Time occupied per call for U4 =
Time occupied per call for U5 =
Mean time occupied per call =
IV. Calls per min for U1 =
Calls per min for U2 =
Calls per min for U3 =
Calls per min for U4 =
Calls per min for U5 =
Mean time occupied per call =
V. Traffic intensity per user A:
the data unit. Recipient the entire string 1 is treated as a unit, Cyclic Redundancy Check segment by a
comparative divisor that was used to find the remainder of. If the string lands without botch, the Cyclic
Redundancy Check checker delivers the remaining zeros just as the data unit passes. If the string is
changed during the move, the division conveys a nonzero remaining segment just as the data unit
doesn't pass.
8
I. Total occupied time =
II. Total number of calls =
III. Time occupied per call for U1 =
Time occupied per call for U2 =
Time occupied per call for U3 =
Time occupied per call for U4 =
Time occupied per call for U5 =
Mean time occupied per call =
IV. Calls per min for U1 =
Calls per min for U2 =
Calls per min for U3 =
Calls per min for U4 =
Calls per min for U5 =
Mean time occupied per call =
V. Traffic intensity per user A:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

A = average call request rate * average holding time
Total traffic intensity = traffic intensity per user * number of users
Total traffic intensity for U1 =
Total traffic intensity for U2 =
Total traffic intensity for U3 =
Total traffic intensity for U4 =
Total traffic intensity for U5 =
Total traffic intensity for U1, U2, U3, U4 as well as U5 is 51.99 Erlangs
9
A geographic zone or a phone the executive’s zone is separated into little hexagonal regions called cell-
based units in a phone structure. These cells stretch out across bigger topographical regions. The
hexagonal cell shape is more finished than the cell condition of a square or triangle in a cell structure.
This is to cover the whole zone without covering it. This implies the whole geographic zone can be
secured without openings [2].
Reusing and cell partition are two fundamental thoughts for cell frameworks. Parting a cell is a method
for separating a bigger, filled cell into littler cells. Every cell has its very own base station with the
intensity of the transmitter and the tallness of the get wire. As traffic in the zone builds, enormous cells
are partitioned into littler cells with the goal that frequencies can be reused. Parting cells expands
framework limit. This likewise expands the accessibility of the quantity of extra channels per unit
administration territory. There are two kinds of cell divisions: A tireless cell division plans everything
before it is really executed in another part cell. The allocated recurrence, transmitter power, traffic load,
and so forth are considered previously [2].
Executing dynamic cell parting is a troublesome undertaking. Dynamic cell parting follows committed
range and traffic load use.
The state of hexagonal cells is desirable over the state of squares or triangles:
Total traffic intensity = traffic intensity per user * number of users
Total traffic intensity for U1 =
Total traffic intensity for U2 =
Total traffic intensity for U3 =
Total traffic intensity for U4 =
Total traffic intensity for U5 =
Total traffic intensity for U1, U2, U3, U4 as well as U5 is 51.99 Erlangs
9
A geographic zone or a phone the executive’s zone is separated into little hexagonal regions called cell-
based units in a phone structure. These cells stretch out across bigger topographical regions. The
hexagonal cell shape is more finished than the cell condition of a square or triangle in a cell structure.
This is to cover the whole zone without covering it. This implies the whole geographic zone can be
secured without openings [2].
Reusing and cell partition are two fundamental thoughts for cell frameworks. Parting a cell is a method
for separating a bigger, filled cell into littler cells. Every cell has its very own base station with the
intensity of the transmitter and the tallness of the get wire. As traffic in the zone builds, enormous cells
are partitioned into littler cells with the goal that frequencies can be reused. Parting cells expands
framework limit. This likewise expands the accessibility of the quantity of extra channels per unit
administration territory. There are two kinds of cell divisions: A tireless cell division plans everything
before it is really executed in another part cell. The allocated recurrence, transmitter power, traffic load,
and so forth are considered previously [2].
Executing dynamic cell parting is a troublesome undertaking. Dynamic cell parting follows committed
range and traffic load use.
The state of hexagonal cells is desirable over the state of squares or triangles:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Because hexagonal cells have a bigger territory than squares or triangles, fewer cells are utilized
to cover explicit geographic areas.
The state of the hexagonal cell is fundamentally the same as the roundabout radiation design
(utilized in the present unidirectional receiving wires) of the base station (that is, the
transmitter). Roundabout cell shapes are not utilized when actualized in light of the fact that
there is a hole between them [2].
References
[1] C. Leung, "Evaluation of the undetected error probability of single parity-check product codes", IEEE
Trans. Commun., vol. COM-31, pp. 250-253, Feb. 2014.
[2] T. Kasami, T. Klove, S. Lin, "Linear block codes for error detection", IEEE Trans. Inform. Theory, vol. IT-
29, pp. 131-136, Jan. 2013.
to cover explicit geographic areas.
The state of the hexagonal cell is fundamentally the same as the roundabout radiation design
(utilized in the present unidirectional receiving wires) of the base station (that is, the
transmitter). Roundabout cell shapes are not utilized when actualized in light of the fact that
there is a hole between them [2].
References
[1] C. Leung, "Evaluation of the undetected error probability of single parity-check product codes", IEEE
Trans. Commun., vol. COM-31, pp. 250-253, Feb. 2014.
[2] T. Kasami, T. Klove, S. Lin, "Linear block codes for error detection", IEEE Trans. Inform. Theory, vol. IT-
29, pp. 131-136, Jan. 2013.
1 out of 11
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.