MITS5003 Wireless Networks Assignment: Encoding, Error, Multiplexing
VerifiedAdded on 2023/06/10
|11
|1888
|405
Homework Assignment
AI Summary
This assignment solution covers various aspects of wireless networks, including encoding techniques like ASK, FSK, and PSK, error control methods such as Hamming code and flow control protocols like Simplex Stop-and-Wait and Sliding Window. It also delves into multiplexing techniques, including TDM, FDM, and CDMA, with a focus on Time-Division Multiplexing (TDM) and its synchronous and asynchronous variations. The solution further discusses OFDM features and how it overcomes inter-symbol interference (ISI). Finally, it addresses network design, including access point locations, distribution systems, BSS and ESS sizes, throughput calculation, suitable IEEE standards, and network security measures.

Assignment
Name:
Subject
Date Of Submission
Name:
Subject
Date Of Submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

PART I
a)
Total Bits = 4 + 6 + 4 + 2 = 16bits
Time = 2s
According to Blaufer,
Bits (b) = rate (r) * time (t)
16 bits = r * 2s
r = 16 bits/2s
Data rate r = 8bits/s
b) encoding techniques .
Amplitude shift keying (ASK): digital data i can be defined as a variation of
amplitudes in the a carrier wave . Two unlike amplitudes of transporter signal signify
'0' or '1' (Sanghi). A unique pattern of binary digits that represent digital data are
allocated to each of the finite number of amplitudes is used. Every bid encoded equal
number of amplitudes
Frequency shift keying (FSK): different digits are defined by a change in frequency,
while the amplitude of the carrier remains the same . Two unlike occurrences
approaching carrier frequency represent '0' ,''1'.
Phase shift keying (PSK): This phase is changed to show data signals. The state of a
bit is determined relative to that of the bit preceding it, in accordance with data being
transmitted. (Sanghi).
c)
i) The status string in binary
Acceleration - 5m/s2 = 0101
Ultrasound – 48cm = 0.48m = 0.01111
Motors – full = 1111
Battery – 75% = 10
Status signal: 0101 0.01111 1111 10
ii) Status string on ASK, FSK, PSK
64 3 6F 64 65 20 41 53 43 49 49
d) =10001111001101
a)
Total Bits = 4 + 6 + 4 + 2 = 16bits
Time = 2s
According to Blaufer,
Bits (b) = rate (r) * time (t)
16 bits = r * 2s
r = 16 bits/2s
Data rate r = 8bits/s
b) encoding techniques .
Amplitude shift keying (ASK): digital data i can be defined as a variation of
amplitudes in the a carrier wave . Two unlike amplitudes of transporter signal signify
'0' or '1' (Sanghi). A unique pattern of binary digits that represent digital data are
allocated to each of the finite number of amplitudes is used. Every bid encoded equal
number of amplitudes
Frequency shift keying (FSK): different digits are defined by a change in frequency,
while the amplitude of the carrier remains the same . Two unlike occurrences
approaching carrier frequency represent '0' ,''1'.
Phase shift keying (PSK): This phase is changed to show data signals. The state of a
bit is determined relative to that of the bit preceding it, in accordance with data being
transmitted. (Sanghi).
c)
i) The status string in binary
Acceleration - 5m/s2 = 0101
Ultrasound – 48cm = 0.48m = 0.01111
Motors – full = 1111
Battery – 75% = 10
Status signal: 0101 0.01111 1111 10
ii) Status string on ASK, FSK, PSK
64 3 6F 64 65 20 41 53 43 49 49
d) =10001111001101

e)Error and Flow Control
Error Control:
Hamming Code
It is a method that utilizes redundant bits which are included with the original data. The bits
are ordered in a manner to allow for detection of a corrupt bit since unlike indecent bits yield
different fault results. Once identified, the receiver reverses its value and corrects the error.
Flow Control:
A Simplex Stop-and-Wait Protocol
The Sender sends data and waits for the response from Receiver.
If the Channel has errors there will be no acknowledgement from the receiver because it did
not receive the correct data. This will disable the sender from sending the next data hence the
communication will end.
Sliding Window Protocol
Here, both communicating parties use buffer of the same size, eliminating the necessity to
wait for the sender to transmit the next data, it just sends one after the other without having to
wait of the receiver’s acknowledgment.
Error Control:
Hamming Code
It is a method that utilizes redundant bits which are included with the original data. The bits
are ordered in a manner to allow for detection of a corrupt bit since unlike indecent bits yield
different fault results. Once identified, the receiver reverses its value and corrects the error.
Flow Control:
A Simplex Stop-and-Wait Protocol
The Sender sends data and waits for the response from Receiver.
If the Channel has errors there will be no acknowledgement from the receiver because it did
not receive the correct data. This will disable the sender from sending the next data hence the
communication will end.
Sliding Window Protocol
Here, both communicating parties use buffer of the same size, eliminating the necessity to
wait for the sender to transmit the next data, it just sends one after the other without having to
wait of the receiver’s acknowledgment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
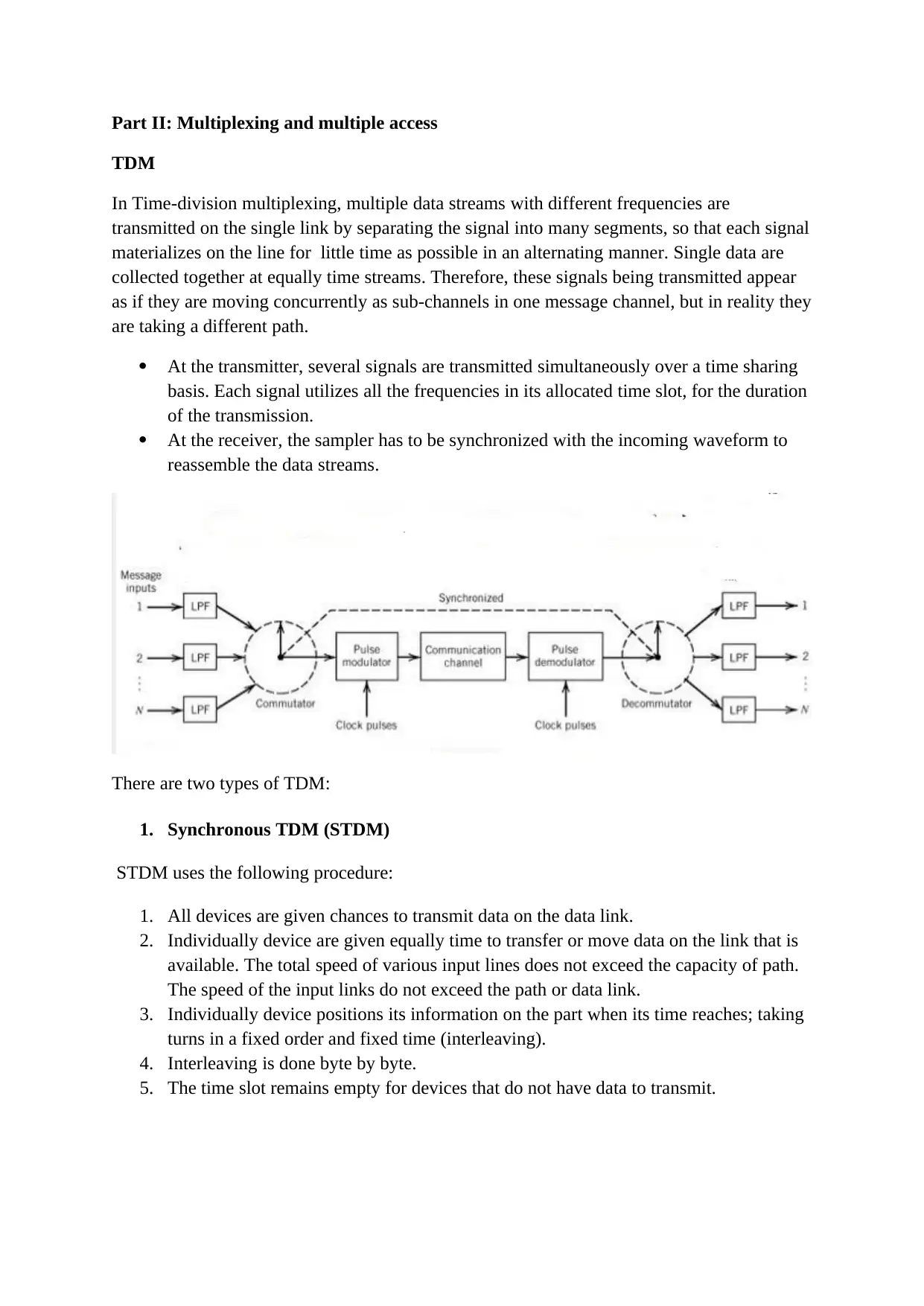
Part II: Multiplexing and multiple access
TDM
In Time-division multiplexing, multiple data streams with different frequencies are
transmitted on the single link by separating the signal into many segments, so that each signal
materializes on the line for little time as possible in an alternating manner. Single data are
collected together at equally time streams. Therefore, these signals being transmitted appear
as if they are moving concurrently as sub-channels in one message channel, but in reality they
are taking a different path.
At the transmitter, several signals are transmitted simultaneously over a time sharing
basis. Each signal utilizes all the frequencies in its allocated time slot, for the duration
of the transmission.
At the receiver, the sampler has to be synchronized with the incoming waveform to
reassemble the data streams.
There are two types of TDM:
1. Synchronous TDM (STDM)
STDM uses the following procedure:
1. All devices are given chances to transmit data on the data link.
2. Individually device are given equally time to transfer or move data on the link that is
available. The total speed of various input lines does not exceed the capacity of path.
The speed of the input links do not exceed the path or data link.
3. Individually device positions its information on the part when its time reaches; taking
turns in a fixed order and fixed time (interleaving).
4. Interleaving is done byte by byte.
5. The time slot remains empty for devices that do not have data to transmit.
TDM
In Time-division multiplexing, multiple data streams with different frequencies are
transmitted on the single link by separating the signal into many segments, so that each signal
materializes on the line for little time as possible in an alternating manner. Single data are
collected together at equally time streams. Therefore, these signals being transmitted appear
as if they are moving concurrently as sub-channels in one message channel, but in reality they
are taking a different path.
At the transmitter, several signals are transmitted simultaneously over a time sharing
basis. Each signal utilizes all the frequencies in its allocated time slot, for the duration
of the transmission.
At the receiver, the sampler has to be synchronized with the incoming waveform to
reassemble the data streams.
There are two types of TDM:
1. Synchronous TDM (STDM)
STDM uses the following procedure:
1. All devices are given chances to transmit data on the data link.
2. Individually device are given equally time to transfer or move data on the link that is
available. The total speed of various input lines does not exceed the capacity of path.
The speed of the input links do not exceed the path or data link.
3. Individually device positions its information on the part when its time reaches; taking
turns in a fixed order and fixed time (interleaving).
4. Interleaving is done byte by byte.
5. The time slot remains empty for devices that do not have data to transmit.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
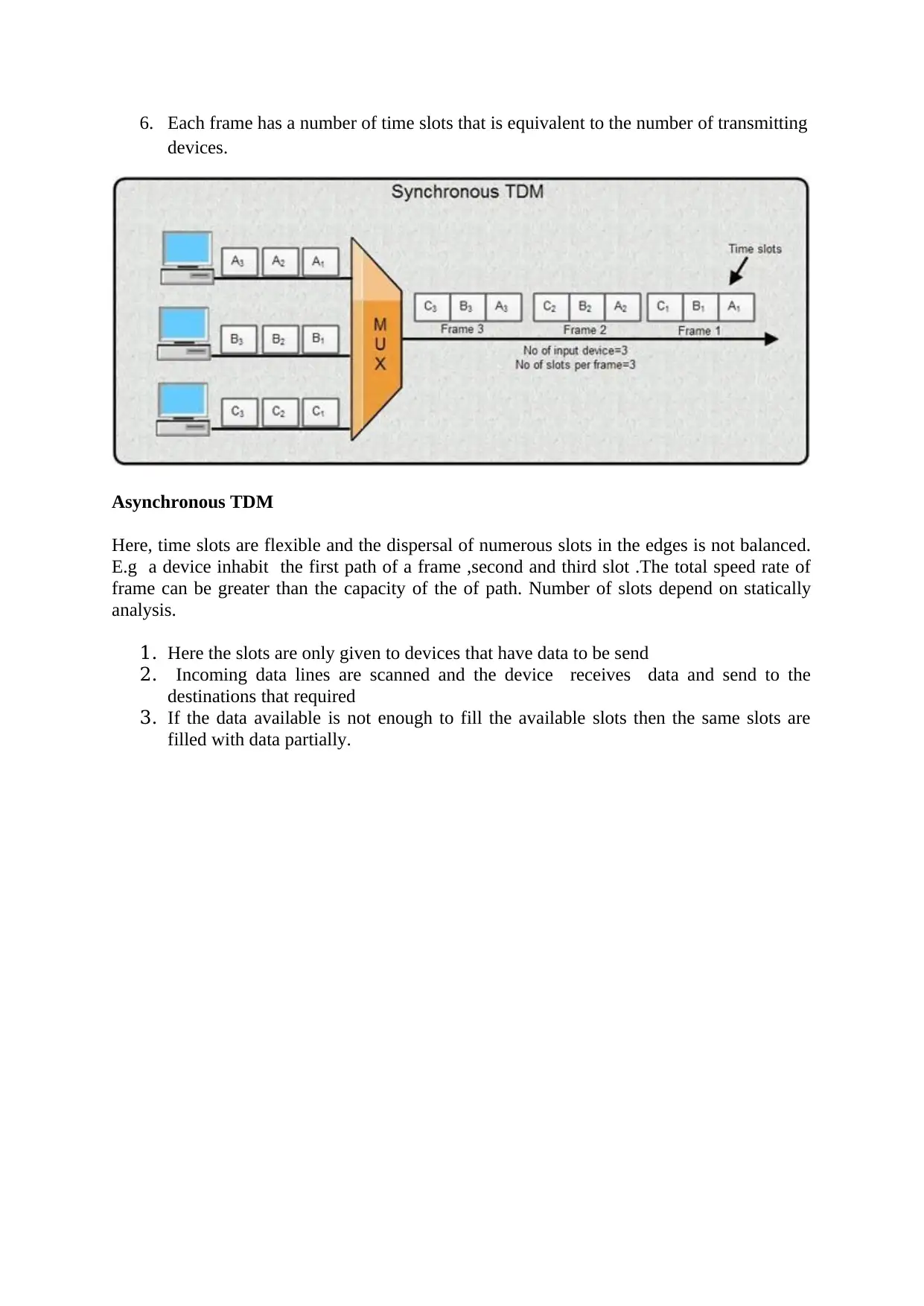
6. Each frame has a number of time slots that is equivalent to the number of transmitting
devices.
Asynchronous TDM
Here, time slots are flexible and the dispersal of numerous slots in the edges is not balanced.
E.g a device inhabit the first path of a frame ,second and third slot .The total speed rate of
frame can be greater than the capacity of the of path. Number of slots depend on statically
analysis.
1. Here the slots are only given to devices that have data to be send
2. Incoming data lines are scanned and the device receives data and send to the
destinations that required
3. If the data available is not enough to fill the available slots then the same slots are
filled with data partially.
devices.
Asynchronous TDM
Here, time slots are flexible and the dispersal of numerous slots in the edges is not balanced.
E.g a device inhabit the first path of a frame ,second and third slot .The total speed rate of
frame can be greater than the capacity of the of path. Number of slots depend on statically
analysis.
1. Here the slots are only given to devices that have data to be send
2. Incoming data lines are scanned and the device receives data and send to the
destinations that required
3. If the data available is not enough to fill the available slots then the same slots are
filled with data partially.
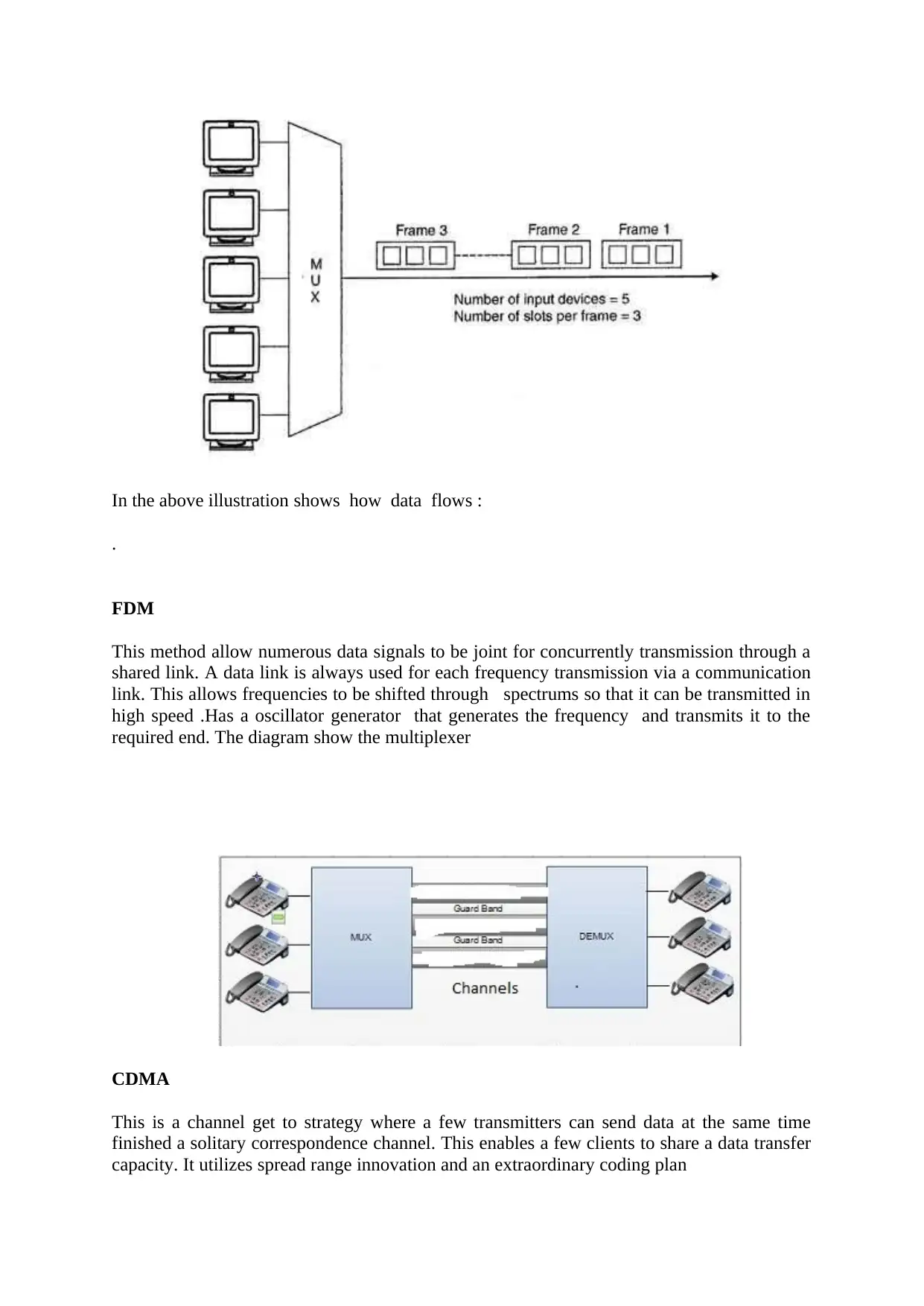
In the above illustration shows how data flows :
.
FDM
This method allow numerous data signals to be joint for concurrently transmission through a
shared link. A data link is always used for each frequency transmission via a communication
link. This allows frequencies to be shifted through spectrums so that it can be transmitted in
high speed .Has a oscillator generator that generates the frequency and transmits it to the
required end. The diagram show the multiplexer
CDMA
This is a channel get to strategy where a few transmitters can send data at the same time
finished a solitary correspondence channel. This enables a few clients to share a data transfer
capacity. It utilizes spread range innovation and an extraordinary coding plan
.
FDM
This method allow numerous data signals to be joint for concurrently transmission through a
shared link. A data link is always used for each frequency transmission via a communication
link. This allows frequencies to be shifted through spectrums so that it can be transmitted in
high speed .Has a oscillator generator that generates the frequency and transmits it to the
required end. The diagram show the multiplexer
CDMA
This is a channel get to strategy where a few transmitters can send data at the same time
finished a solitary correspondence channel. This enables a few clients to share a data transfer
capacity. It utilizes spread range innovation and an extraordinary coding plan
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
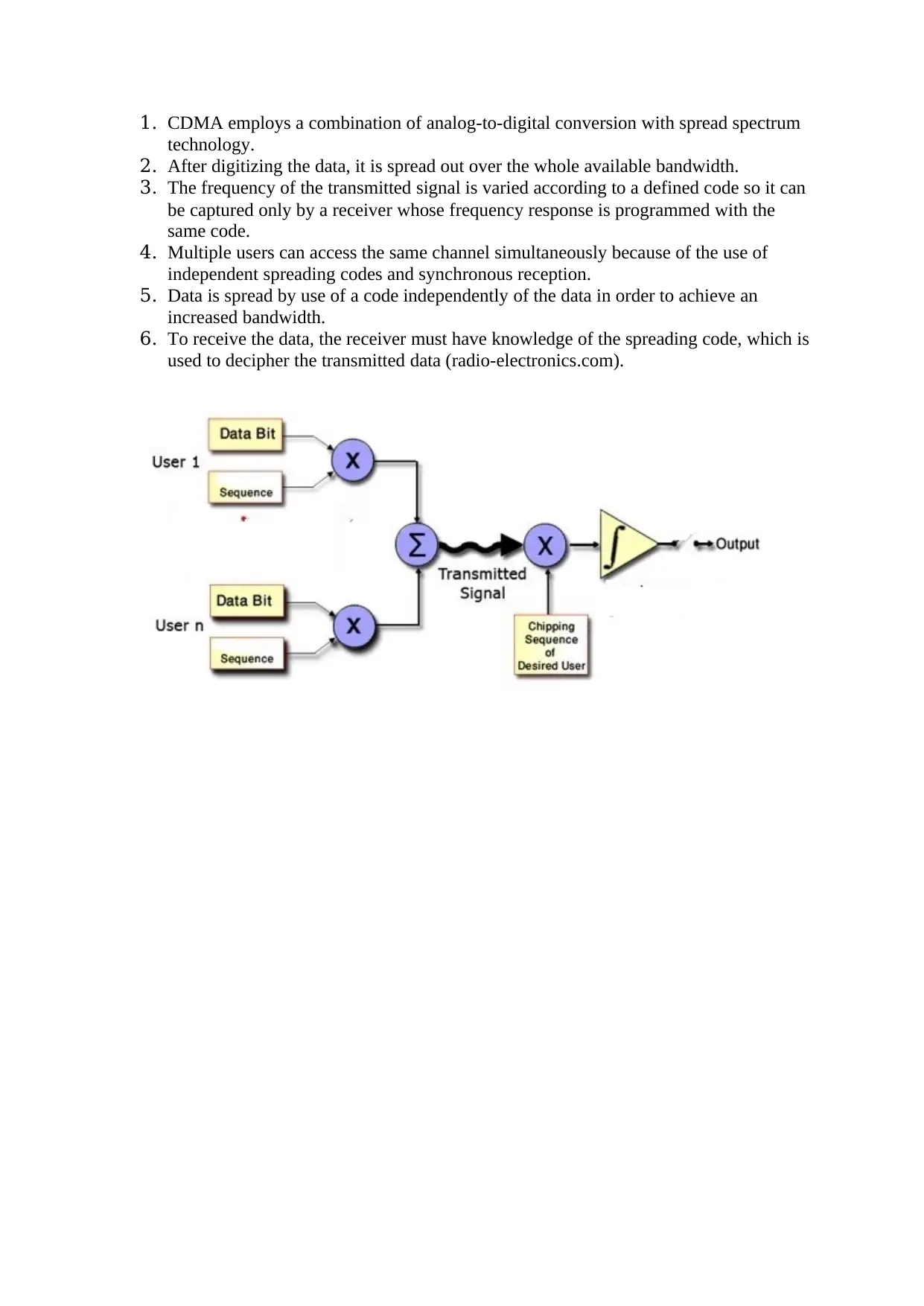
1. CDMA employs a combination of analog-to-digital conversion with spread spectrum
technology.
2. After digitizing the data, it is spread out over the whole available bandwidth.
3. The frequency of the transmitted signal is varied according to a defined code so it can
be captured only by a receiver whose frequency response is programmed with the
same code.
4. Multiple users can access the same channel simultaneously because of the use of
independent spreading codes and synchronous reception.
5. Data is spread by use of a code independently of the data in order to achieve an
increased bandwidth.
6. To receive the data, the receiver must have knowledge of the spreading code, which is
used to decipher the transmitted data (radio-electronics.com).
technology.
2. After digitizing the data, it is spread out over the whole available bandwidth.
3. The frequency of the transmitted signal is varied according to a defined code so it can
be captured only by a receiver whose frequency response is programmed with the
same code.
4. Multiple users can access the same channel simultaneously because of the use of
independent spreading codes and synchronous reception.
5. Data is spread by use of a code independently of the data in order to achieve an
increased bandwidth.
6. To receive the data, the receiver must have knowledge of the spreading code, which is
used to decipher the transmitted data (radio-electronics.com).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

b) OFDM
Features of OFDM
Source data is processed to rectify coding for correcting errors, interleave and map
bits onto symbols.
Adding a recurring prefix to the frame to be sent helps maintain Orthogonality during
channel transmission.
The cyclic prefix can be a means of detecting the start of each frame.
Demodulation of the signals is done using FFT.
Channel equalization is estimated using a training sequence or pilot symbols at
allocated sub-carriers.
c)
i) For 48 subscribers what should be the subcarrier bandwidth ( fb ) ?
According to a Rohde and Schwarz whitepaper on 802.11 ac, the subcarrier bandwidths will
be as follows:
For a 40MHz transmission, maximum number of subscribers will be 128 transmitting signals
from -58 to -2 and 2 to 58MHz.
ii) Suitable subcarrier bit time for orthogonality
orthogonality requires that the sub-carrier spacing is:
Where Tu seconds is symbol duration and k is a positive integer, equal to 1.
Therefore, with 48 sub-carriers, the total passband bandwidth will be
B ≈ 48·Δf (Hz).
iii) Explain how OFDM overcomes the issue of inter symbol interference (ISI)
Frequency Domain Equalization
The fading distortion in the channel causes ISI in a OFDM demodulator and compensating
for it introduces the problem of noise enhancement. Frequency domain equalization process
inserts frequency domain pilot symbols in each frame.
Time Domain Windowing
Windowing a signal to be transmitted by multiplying with a suitable function works to
diminish the interference by causing the spectrum of the signal wave form to be more
concentrated, then same window is used receiver-side to reconstruct the original signal. The
window functions need to satisfy the Nyquists vestigial symmetry criterion for ISI to be
eliminated.
Pulse Shaping
A frequency offset causes loss of orthogonality due to the spectral null not coinciding to the
peak of the individual carriers and as it increases the ISI power increases too. Pulse shaping
reduces the side lobes in order to maintain orthogonality.
Features of OFDM
Source data is processed to rectify coding for correcting errors, interleave and map
bits onto symbols.
Adding a recurring prefix to the frame to be sent helps maintain Orthogonality during
channel transmission.
The cyclic prefix can be a means of detecting the start of each frame.
Demodulation of the signals is done using FFT.
Channel equalization is estimated using a training sequence or pilot symbols at
allocated sub-carriers.
c)
i) For 48 subscribers what should be the subcarrier bandwidth ( fb ) ?
According to a Rohde and Schwarz whitepaper on 802.11 ac, the subcarrier bandwidths will
be as follows:
For a 40MHz transmission, maximum number of subscribers will be 128 transmitting signals
from -58 to -2 and 2 to 58MHz.
ii) Suitable subcarrier bit time for orthogonality
orthogonality requires that the sub-carrier spacing is:
Where Tu seconds is symbol duration and k is a positive integer, equal to 1.
Therefore, with 48 sub-carriers, the total passband bandwidth will be
B ≈ 48·Δf (Hz).
iii) Explain how OFDM overcomes the issue of inter symbol interference (ISI)
Frequency Domain Equalization
The fading distortion in the channel causes ISI in a OFDM demodulator and compensating
for it introduces the problem of noise enhancement. Frequency domain equalization process
inserts frequency domain pilot symbols in each frame.
Time Domain Windowing
Windowing a signal to be transmitted by multiplying with a suitable function works to
diminish the interference by causing the spectrum of the signal wave form to be more
concentrated, then same window is used receiver-side to reconstruct the original signal. The
window functions need to satisfy the Nyquists vestigial symmetry criterion for ISI to be
eliminated.
Pulse Shaping
A frequency offset causes loss of orthogonality due to the spectral null not coinciding to the
peak of the individual carriers and as it increases the ISI power increases too. Pulse shaping
reduces the side lobes in order to maintain orthogonality.
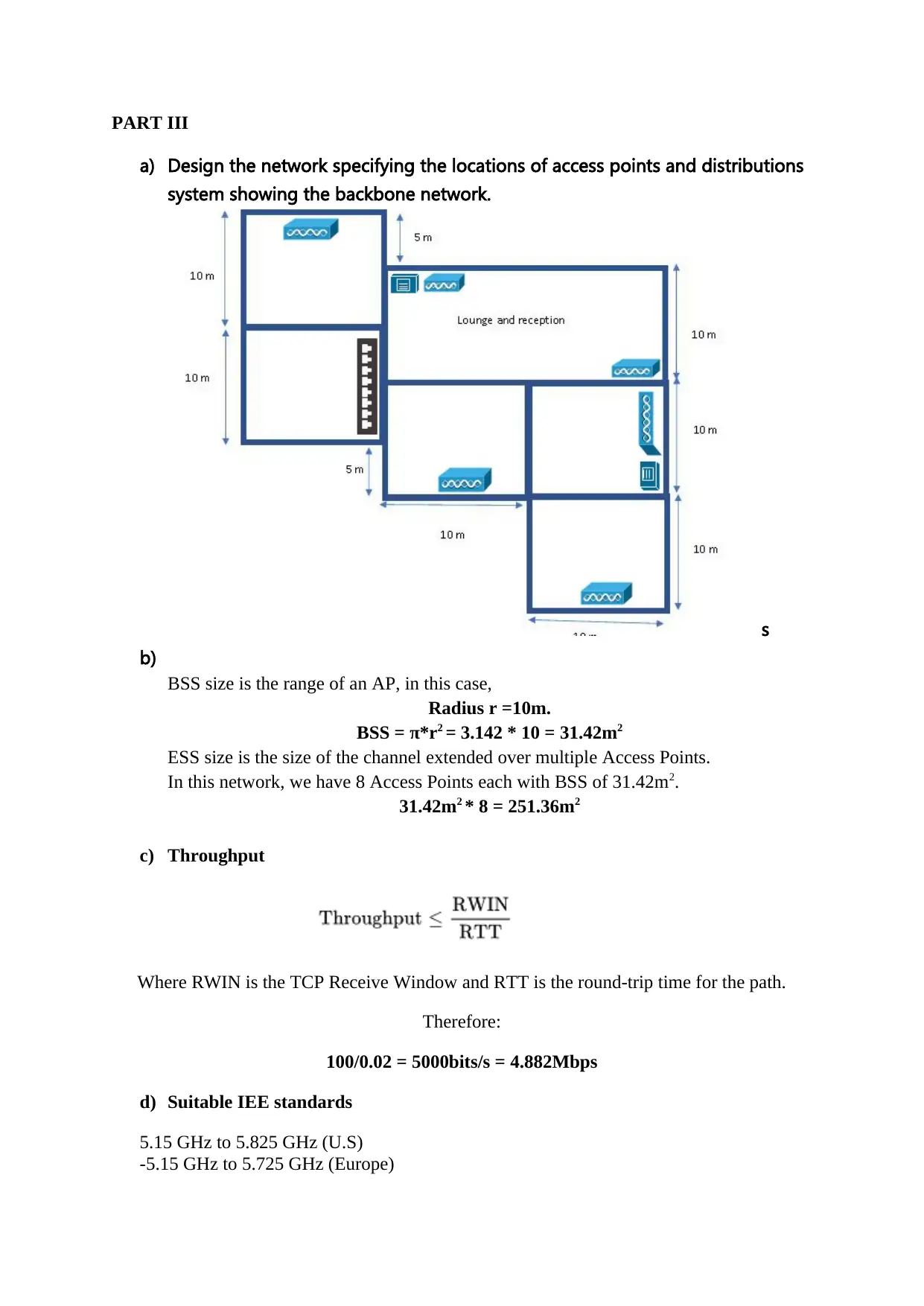
PART III
a) Design the network specifying the locations of access points and distributions
system showing the backbone network.
s
b)
BSS size is the range of an AP, in this case,
Radius r =10m.
BSS = π*r2 = 3.142 * 10 = 31.42m2
ESS size is the size of the channel extended over multiple Access Points.
In this network, we have 8 Access Points each with BSS of 31.42m2.
31.42m2 * 8 = 251.36m2
c) Throughput
Where RWIN is the TCP Receive Window and RTT is the round-trip time for the path.
Therefore:
100/0.02 = 5000bits/s = 4.882Mbps
d) Suitable IEE standards
5.15 GHz to 5.825 GHz (U.S)
-5.15 GHz to 5.725 GHz (Europe)
a) Design the network specifying the locations of access points and distributions
system showing the backbone network.
s
b)
BSS size is the range of an AP, in this case,
Radius r =10m.
BSS = π*r2 = 3.142 * 10 = 31.42m2
ESS size is the size of the channel extended over multiple Access Points.
In this network, we have 8 Access Points each with BSS of 31.42m2.
31.42m2 * 8 = 251.36m2
c) Throughput
Where RWIN is the TCP Receive Window and RTT is the round-trip time for the path.
Therefore:
100/0.02 = 5000bits/s = 4.882Mbps
d) Suitable IEE standards
5.15 GHz to 5.825 GHz (U.S)
-5.15 GHz to 5.725 GHz (Europe)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

e) Securing the network
Enable logging
Switch on logging of devices and network activity
Login credentials
Change login credentials from the factory default to a new username and a complex password
made up of letters, numbers and symbols
Firmware update
Regularly check for, and install firmware updates for the routers, as well as software an
driver updates for the workstations.
Encryption
Enable Access Point Encryption such as WPA or WPA2 to protect data sent over that
network
Physical security
Aps devices should be kept in locked cabinets to avoid being interfered with.
Secure the 802.1X client settings
This prevents attacks on the server.
Enable logging
Switch on logging of devices and network activity
Login credentials
Change login credentials from the factory default to a new username and a complex password
made up of letters, numbers and symbols
Firmware update
Regularly check for, and install firmware updates for the routers, as well as software an
driver updates for the workstations.
Encryption
Enable Access Point Encryption such as WPA or WPA2 to protect data sent over that
network
Physical security
Aps devices should be kept in locked cabinets to avoid being interfered with.
Secure the 802.1X client settings
This prevents attacks on the server.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Bibliography
Cheng, H., & Li, X. (2010). Partial encryption of compressed images and videos. IEEE Transactions
on signal processing, 48(8), 2439-2451.
Nosratinia, A., Hunter, T. E., & Hedayat, A. (2004). Cooperative communication in wireless
networks. IEEE communications Magazine, 42(10), 74-80.
Lueng, K. T., Dao, S., & Shek, E. (2009). U.S. Patent No. 7,483,693. Washington, DC: U.S. Patent
and Trademark Office.
Lee, H. Y., Chang, R. C., Huang, L. Y., & Chiang, M. L. (2010). U.S. Patent No. 6,657,981.
Washington, DC: U.S. Patent and Trademark Office.
Cheng, H., & Li, X. (2010). Partial encryption of compressed images and videos. IEEE Transactions
on signal processing, 48(8), 2439-2451.
Nosratinia, A., Hunter, T. E., & Hedayat, A. (2004). Cooperative communication in wireless
networks. IEEE communications Magazine, 42(10), 74-80.
Lueng, K. T., Dao, S., & Shek, E. (2009). U.S. Patent No. 7,483,693. Washington, DC: U.S. Patent
and Trademark Office.
Lee, H. Y., Chang, R. C., Huang, L. Y., & Chiang, M. L. (2010). U.S. Patent No. 6,657,981.
Washington, DC: U.S. Patent and Trademark Office.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



