MITS5003 Wireless Networks & Communication: Term Paper Solution 2019S2
VerifiedAdded on 2022/10/06
|14
|821
|24
Homework Assignment
AI Summary
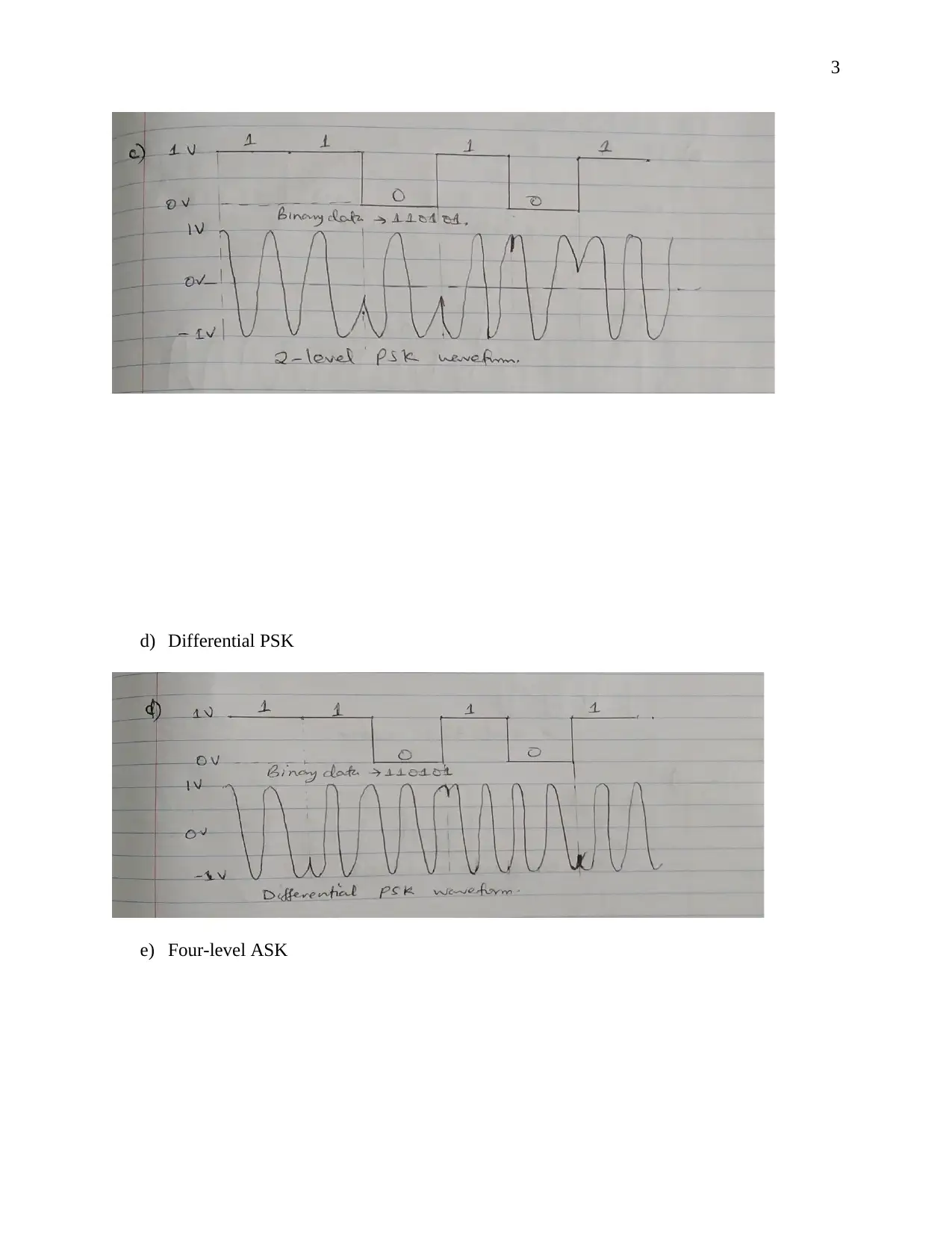
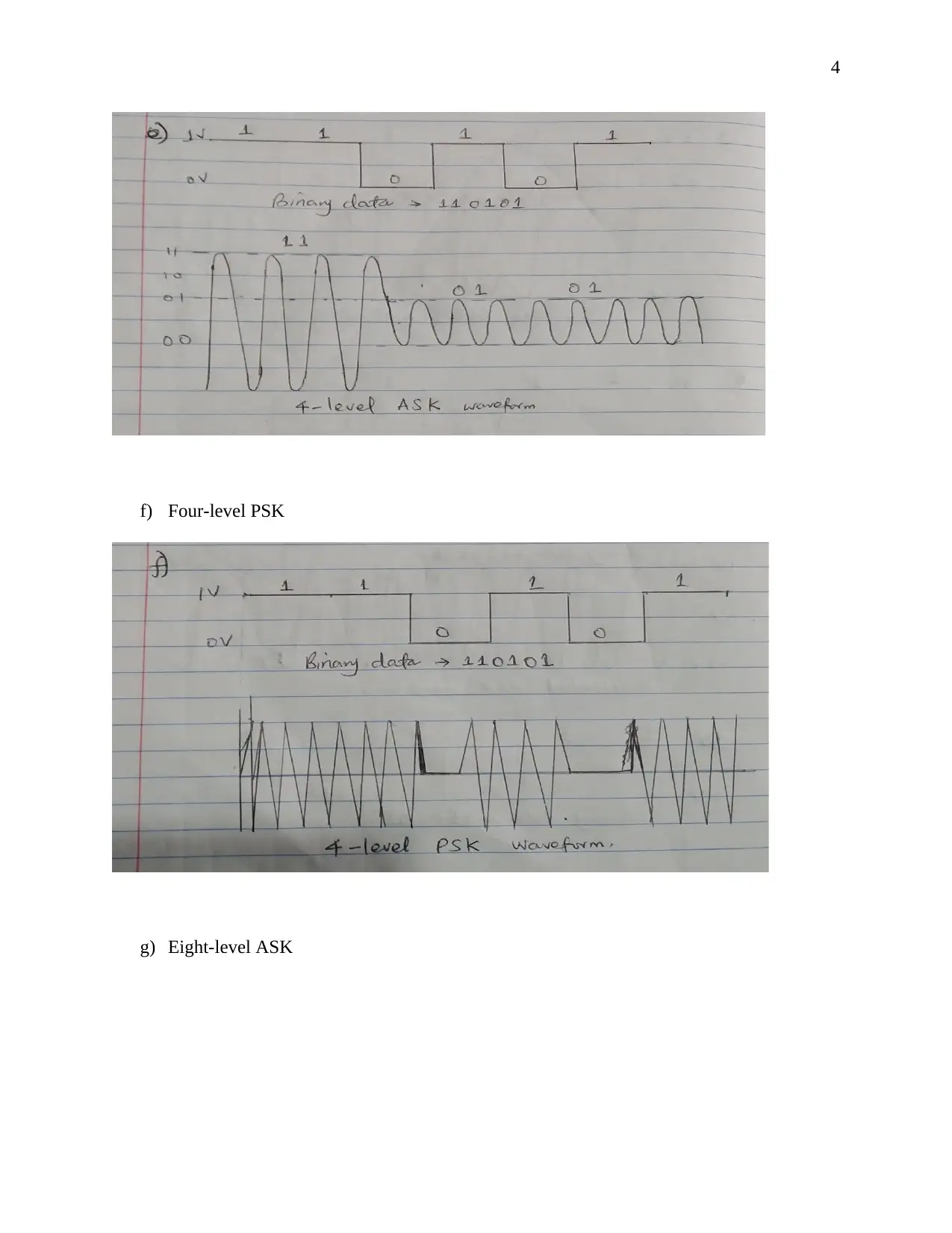
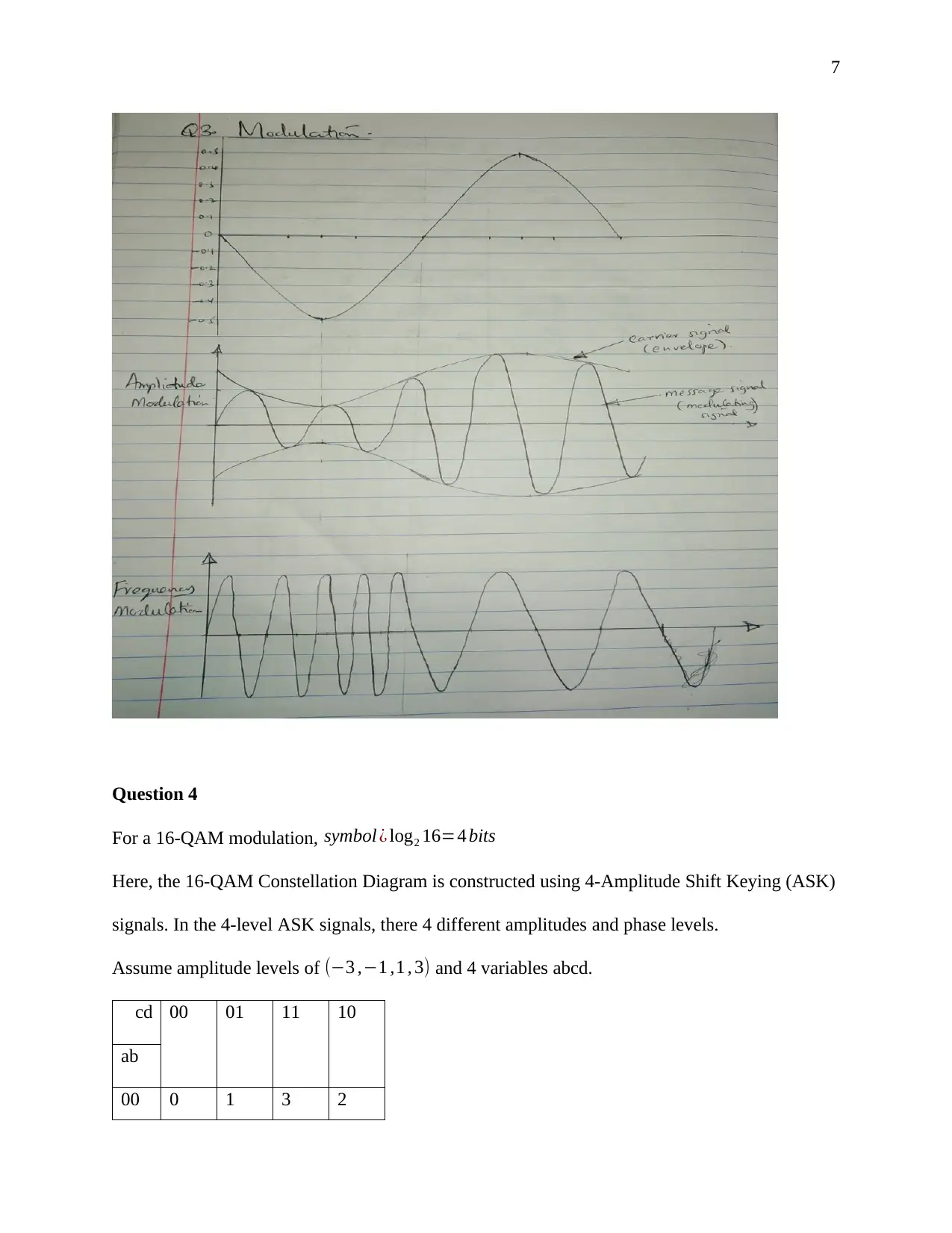
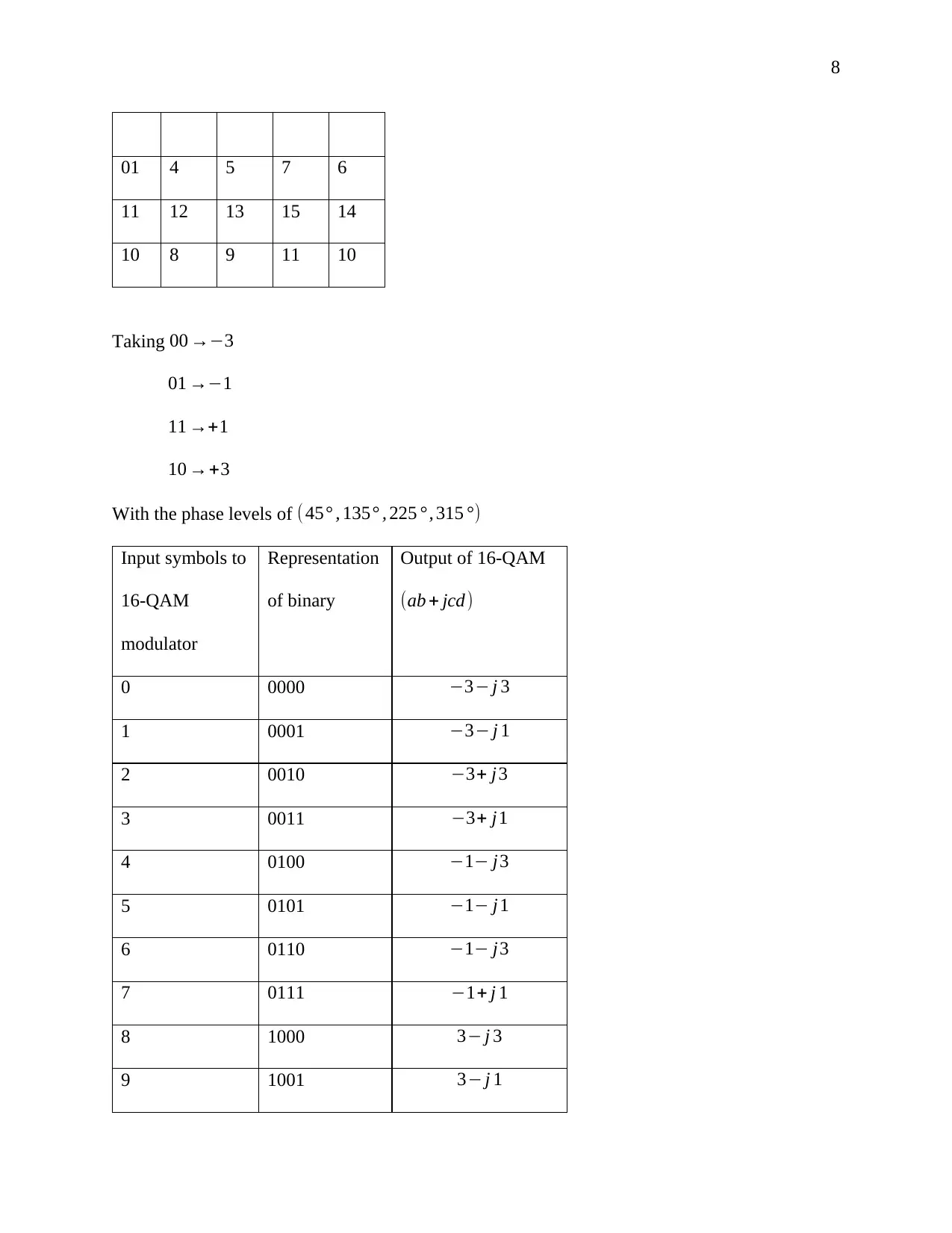
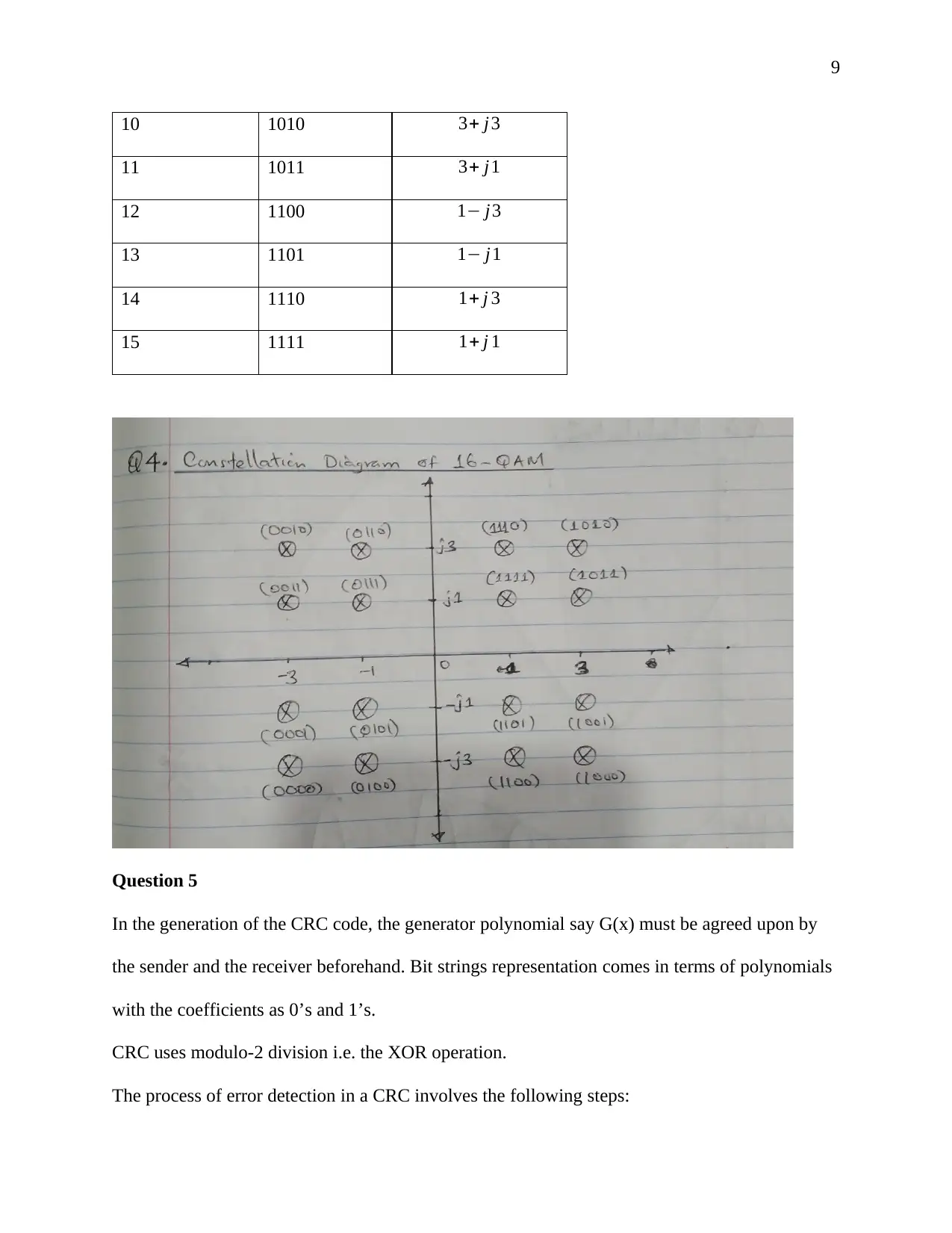
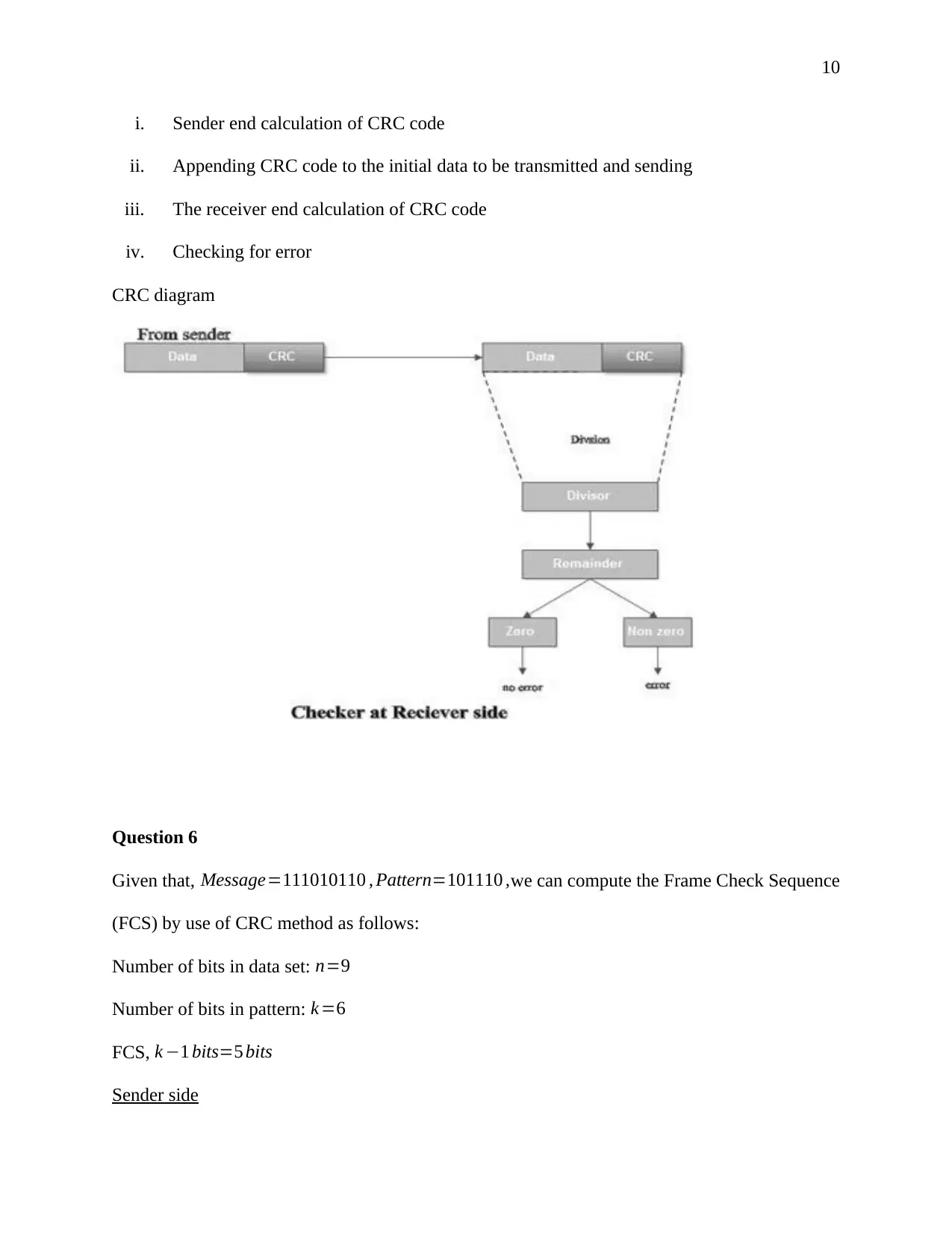
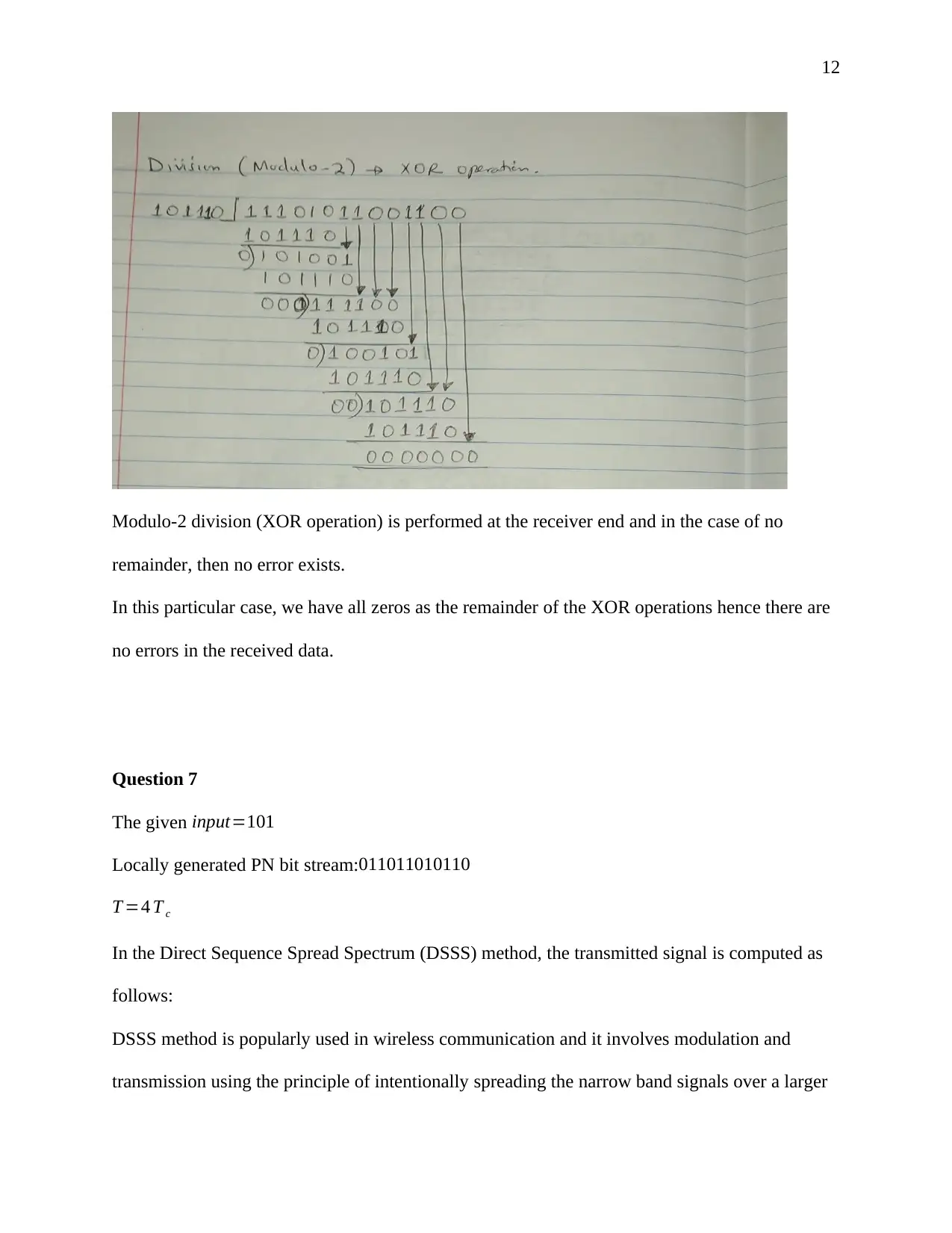
This document presents a comprehensive solution to a term paper assignment on wireless networks and communication. The assignment covers various topics, including the conversion of binary data to analog waveforms using different modulation techniques like ASK, FSK, PSK, and QAM. It includes calculations related to signal elements and frequencies. The solution also delves into Cyclic Redundancy Check (CRC) code generation and error detection, explaining the process with sender and receiver-end calculations and diagrams. Furthermore, the assignment addresses Direct Sequence Spread Spectrum (DSSS) and its application in wireless communication, including the use of XOR operations. Finally, the solution discusses the advantages of hexagonal cell structures in cellular networks, comparing them to square and circle-shaped cells in terms of coverage and performance. This assignment is designed to provide a complete understanding of key concepts in wireless communication and network design.
1 out of 14











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)