MITS5004 IT Security: A Critical Analysis of Nmap and Metasploit
VerifiedAdded on 2024/05/15
|20
|2496
|156
Report
AI Summary
This report provides a critical analysis of two prominent IT security tools: Nmap and Metasploit. Nmap, a network security tool, is examined for its scanning capabilities, host discovery, operating system detection, and quick traceroute features, with a focus on its installation, usage, scalability, performance, availability, and reporting. Metasploit, a penetration testing framework, is explored for its exploit development, vulnerability assessment, and pen-testing automation features, including screen capturing, information gathering, database support, and automation capabilities. The analysis covers installation, command-line interface, scalability, performance, availability, and reporting functionalities of both tools, highlighting their strengths and weaknesses in various security-related tasks. This assignment solution is available on Desklib, a platform offering study tools and resources for students.

Contents
Introduction......................................................................................................................................3
Security tools...................................................................................................................................4
Nmap............................................................................................................................................4
Overview..................................................................................................................................4
Installation and launching........................................................................................................4
Features....................................................................................................................................5
Analysis...................................................................................................................................5
Metasploit....................................................................................................................................9
Overview:................................................................................................................................9
Installation and launching........................................................................................................9
Features..................................................................................................................................10
Analysis.................................................................................................................................14
Conclusion:....................................................................................................................................19
References......................................................................................................................................20
Introduction......................................................................................................................................3
Security tools...................................................................................................................................4
Nmap............................................................................................................................................4
Overview..................................................................................................................................4
Installation and launching........................................................................................................4
Features....................................................................................................................................5
Analysis...................................................................................................................................5
Metasploit....................................................................................................................................9
Overview:................................................................................................................................9
Installation and launching........................................................................................................9
Features..................................................................................................................................10
Analysis.................................................................................................................................14
Conclusion:....................................................................................................................................19
References......................................................................................................................................20
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

List of figures
Figure 1 Nmap installation commands............................................................................................4
Figure 2 Nmap installation..............................................................................................................5
Figure 3 Nmap GUI 1......................................................................................................................6
Figure 4 Nmap GUI 2......................................................................................................................7
Figure 5 Metasploit installation.......................................................................................................9
Figure 6 Metasploit installation completion..................................................................................10
Figure 7 Show encoders.................................................................................................................11
Figure 8 Database backend help....................................................................................................12
Figure 9 Database backend............................................................................................................13
Figure 10 Metasploit working.......................................................................................................14
Figure 11 Metasploit Framework console.....................................................................................15
Figure 12 Show exploits command...............................................................................................15
Figure 13 Show auxiliary command..............................................................................................16
Figure 14 Show payload command...............................................................................................16
Figure 15 show options command.................................................................................................16
Figure 16 shows the advance option command.............................................................................17
Figure 17 Metasploit Pro GUI.......................................................................................................18
Figure 18 Report customization.....................................................................................................18
Figure 1 Nmap installation commands............................................................................................4
Figure 2 Nmap installation..............................................................................................................5
Figure 3 Nmap GUI 1......................................................................................................................6
Figure 4 Nmap GUI 2......................................................................................................................7
Figure 5 Metasploit installation.......................................................................................................9
Figure 6 Metasploit installation completion..................................................................................10
Figure 7 Show encoders.................................................................................................................11
Figure 8 Database backend help....................................................................................................12
Figure 9 Database backend............................................................................................................13
Figure 10 Metasploit working.......................................................................................................14
Figure 11 Metasploit Framework console.....................................................................................15
Figure 12 Show exploits command...............................................................................................15
Figure 13 Show auxiliary command..............................................................................................16
Figure 14 Show payload command...............................................................................................16
Figure 15 show options command.................................................................................................16
Figure 16 shows the advance option command.............................................................................17
Figure 17 Metasploit Pro GUI.......................................................................................................18
Figure 18 Report customization.....................................................................................................18

Introduction
The assignment is based on information technology security. This report is based on the analysis
of the tool that is being used in security. The selected tools for this report are Nmap and
Metasploit framework. The report has distinct sections. These sections will first cover the
demonstration of these tools along with the installation procedure in Linux. This is followed by
listing four features of each of these tools. Then net section will cover the analysis of the tool in
different aspects. To support the description and analysis screenshots will be used.
The assignment is based on information technology security. This report is based on the analysis
of the tool that is being used in security. The selected tools for this report are Nmap and
Metasploit framework. The report has distinct sections. These sections will first cover the
demonstration of these tools along with the installation procedure in Linux. This is followed by
listing four features of each of these tools. Then net section will cover the analysis of the tool in
different aspects. To support the description and analysis screenshots will be used.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Security tools
Nmap
Overview
Nmap is a tool for network security. This tool is able to perform various security-related
activities major related to scanning. This is helpful for the administrators to find out the services
and hosts on the network in order to prepare a network map. This is an open-source and free tool.
This provides a scan for running services and open ports, operating systems, firewall, etc. Nmap
refers to network mapper [5].
Installation and launching
In order to use the Nmap tool for the Linux distribution, GUI is required to be installed.
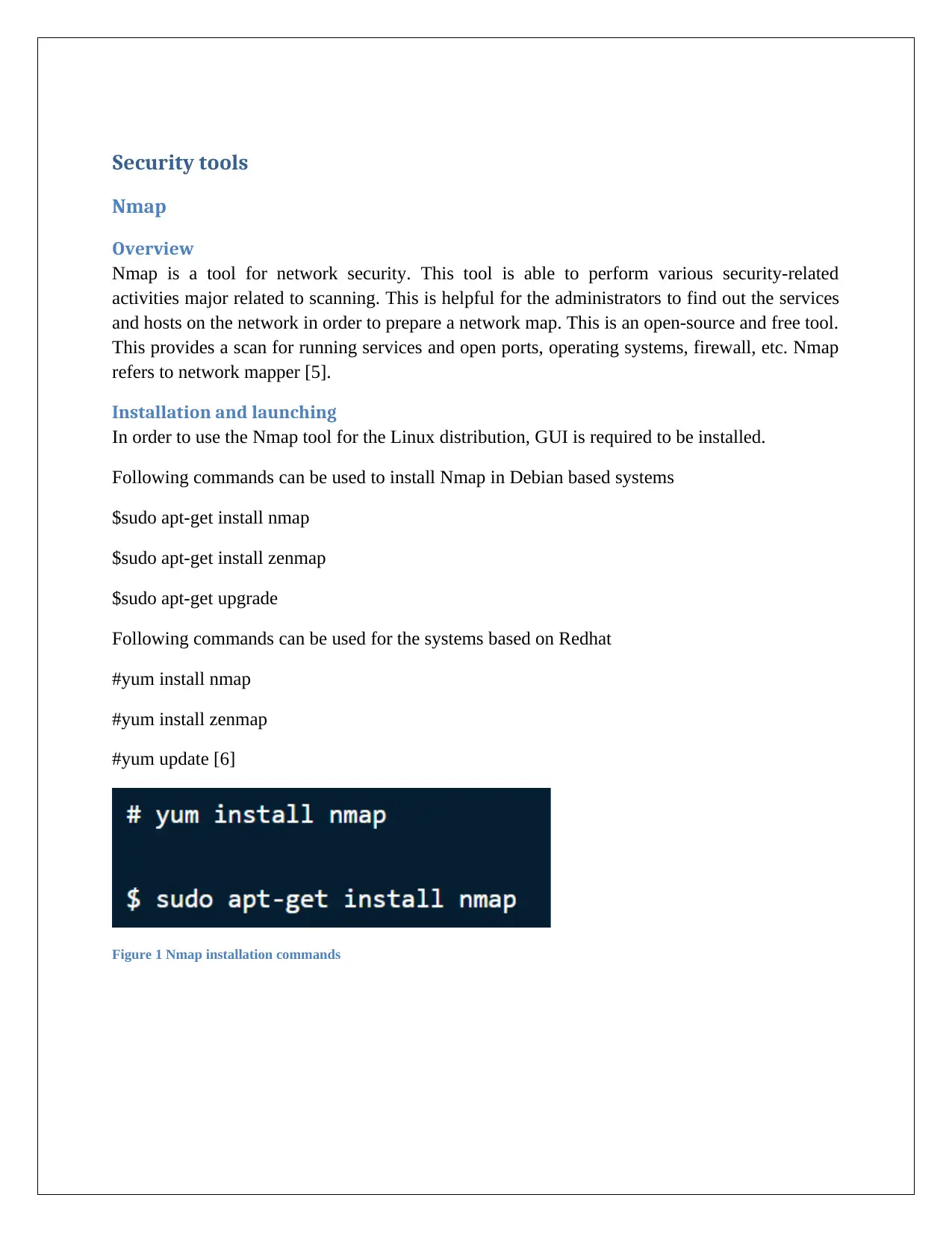
Following commands can be used to install Nmap in Debian based systems
$sudo apt-get install nmap
$sudo apt-get install zenmap
$sudo apt-get upgrade
Following commands can be used for the systems based on Redhat
#yum install nmap
#yum install zenmap
#yum update [6]
Figure 1 Nmap installation commands
Nmap
Overview
Nmap is a tool for network security. This tool is able to perform various security-related
activities major related to scanning. This is helpful for the administrators to find out the services
and hosts on the network in order to prepare a network map. This is an open-source and free tool.
This provides a scan for running services and open ports, operating systems, firewall, etc. Nmap
refers to network mapper [5].
Installation and launching
In order to use the Nmap tool for the Linux distribution, GUI is required to be installed.
Following commands can be used to install Nmap in Debian based systems
$sudo apt-get install nmap
$sudo apt-get install zenmap
$sudo apt-get upgrade
Following commands can be used for the systems based on Redhat
#yum install nmap
#yum install zenmap
#yum update [6]
Figure 1 Nmap installation commands
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Figure 2 Nmap installation
Features
The features of the tools include:
1. Ping Scan: This is helpful in host discovery by detecting the online devices and computers
on the network with the help of ACK or SYN packet. Option –sP is used for this.
2. Detection of operating system and information of network: This feature is used to the get
information about the running service or a port that is open. This information also consists of
a version number and name of the product. Option –sV is used for the detection of version
and option –A supports fingerprinting of OS and detection of version.
3. Quick traceroute: Nmap is able to trace the path of hop to every host in the network also it
can perform ping scan in which scanning of a port is disabled.
--traceroute option is used for the tracing and –sN is used for ping scan.
4. Quick scan: The Nmap tool provides advance and quick scanning. This is able to detect the
version and service information of the open ports, also detect the OS. This faster scanning
scans less port. –O option is used for the operating system detection. – V option is used to
enable the verbosity. –p option is used to scan all the ports from 1 to 65535. The number and
range of ports can be modified according to the user requirement [4].
Analysis
Use: Nmap tool provides a user-friendly interface as the tool also has a Graphical user interface.
Also in command line, options are easy to remember like –O is for operating system, -p is for
Features
The features of the tools include:
1. Ping Scan: This is helpful in host discovery by detecting the online devices and computers
on the network with the help of ACK or SYN packet. Option –sP is used for this.
2. Detection of operating system and information of network: This feature is used to the get
information about the running service or a port that is open. This information also consists of
a version number and name of the product. Option –sV is used for the detection of version
and option –A supports fingerprinting of OS and detection of version.
3. Quick traceroute: Nmap is able to trace the path of hop to every host in the network also it
can perform ping scan in which scanning of a port is disabled.
--traceroute option is used for the tracing and –sN is used for ping scan.
4. Quick scan: The Nmap tool provides advance and quick scanning. This is able to detect the
version and service information of the open ports, also detect the OS. This faster scanning
scans less port. –O option is used for the operating system detection. – V option is used to
enable the verbosity. –p option is used to scan all the ports from 1 to 65535. The number and
range of ports can be modified according to the user requirement [4].
Analysis
Use: Nmap tool provides a user-friendly interface as the tool also has a Graphical user interface.
Also in command line, options are easy to remember like –O is for operating system, -p is for
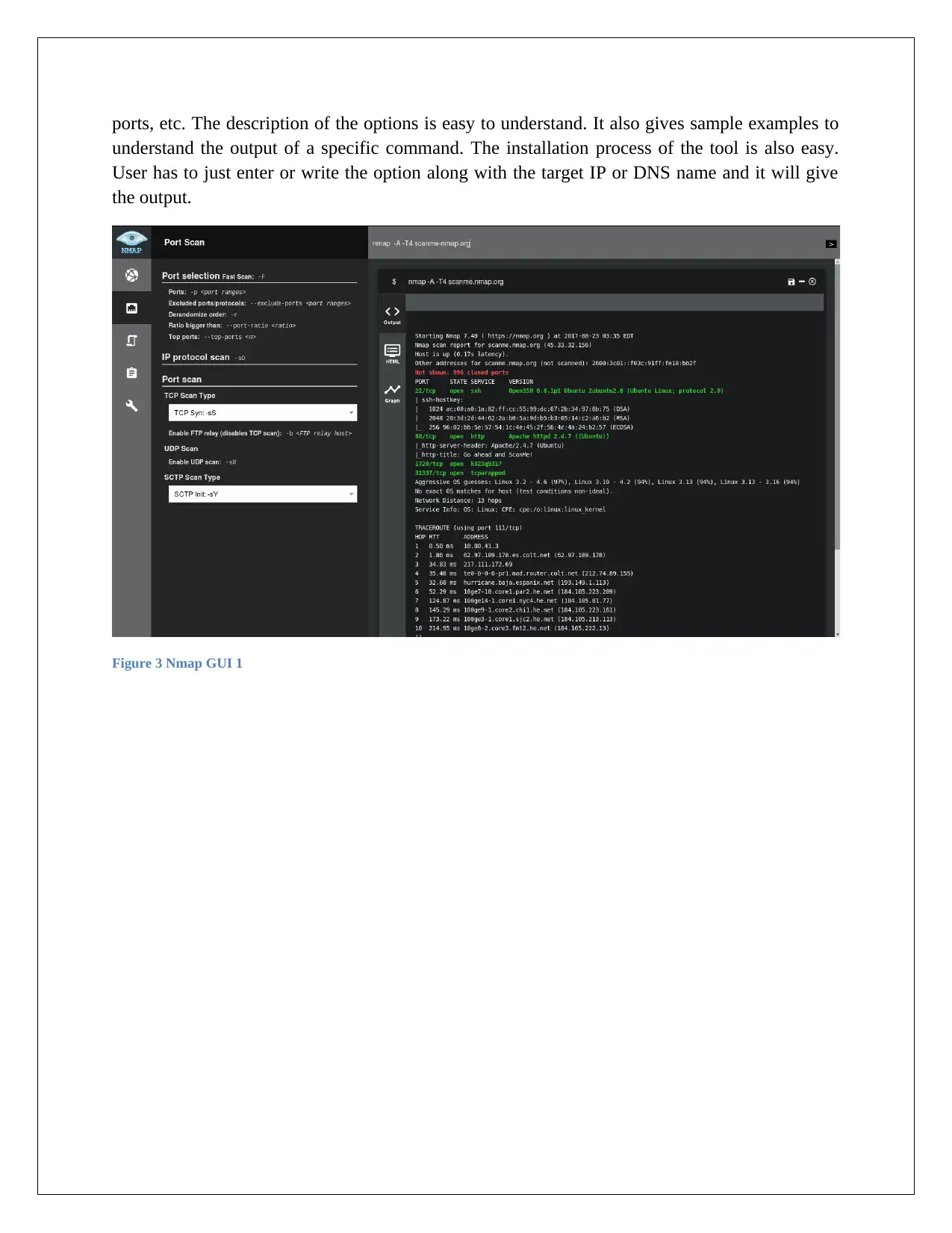
ports, etc. The description of the options is easy to understand. It also gives sample examples to
understand the output of a specific command. The installation process of the tool is also easy.
User has to just enter or write the option along with the target IP or DNS name and it will give
the output.
Figure 3 Nmap GUI 1
understand the output of a specific command. The installation process of the tool is also easy.
User has to just enter or write the option along with the target IP or DNS name and it will give
the output.
Figure 3 Nmap GUI 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
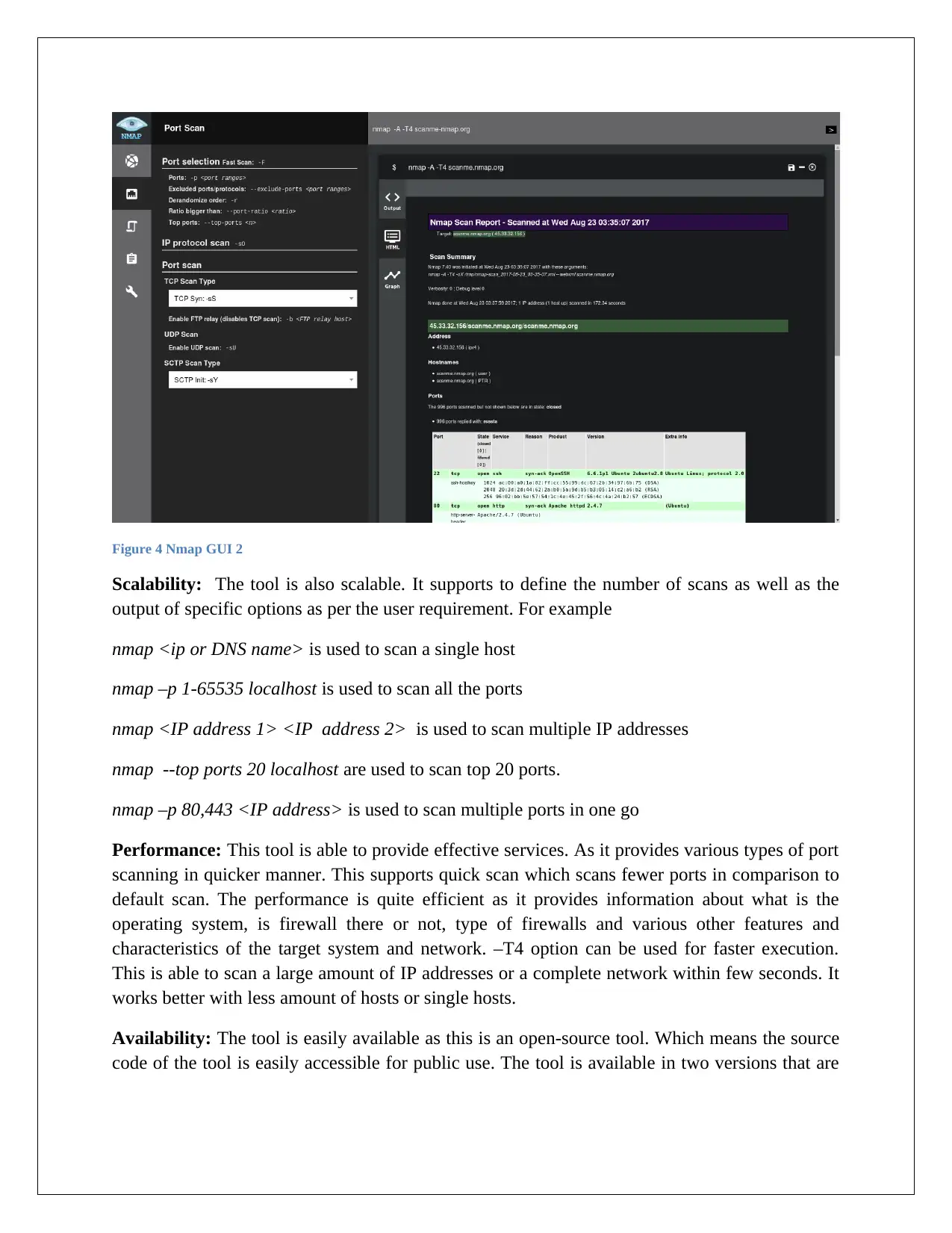
Figure 4 Nmap GUI 2
Scalability: The tool is also scalable. It supports to define the number of scans as well as the
output of specific options as per the user requirement. For example
nmap <ip or DNS name> is used to scan a single host
nmap –p 1-65535 localhost is used to scan all the ports
nmap <IP address 1> <IP address 2> is used to scan multiple IP addresses
nmap --top ports 20 localhost are used to scan top 20 ports.
nmap –p 80,443 <IP address> is used to scan multiple ports in one go
Performance: This tool is able to provide effective services. As it provides various types of port
scanning in quicker manner. This supports quick scan which scans fewer ports in comparison to
default scan. The performance is quite efficient as it provides information about what is the
operating system, is firewall there or not, type of firewalls and various other features and
characteristics of the target system and network. –T4 option can be used for faster execution.
This is able to scan a large amount of IP addresses or a complete network within few seconds. It
works better with less amount of hosts or single hosts.
Availability: The tool is easily available as this is an open-source tool. Which means the source
code of the tool is easily accessible for public use. The tool is available in two versions that are
Scalability: The tool is also scalable. It supports to define the number of scans as well as the
output of specific options as per the user requirement. For example
nmap <ip or DNS name> is used to scan a single host
nmap –p 1-65535 localhost is used to scan all the ports
nmap <IP address 1> <IP address 2> is used to scan multiple IP addresses
nmap --top ports 20 localhost are used to scan top 20 ports.
nmap –p 80,443 <IP address> is used to scan multiple ports in one go
Performance: This tool is able to provide effective services. As it provides various types of port
scanning in quicker manner. This supports quick scan which scans fewer ports in comparison to
default scan. The performance is quite efficient as it provides information about what is the
operating system, is firewall there or not, type of firewalls and various other features and
characteristics of the target system and network. –T4 option can be used for faster execution.
This is able to scan a large amount of IP addresses or a complete network within few seconds. It
works better with less amount of hosts or single hosts.
Availability: The tool is easily available as this is an open-source tool. Which means the source
code of the tool is easily accessible for public use. The tool is available in two versions that are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

command line and graphical user interface. The tool is available in Kali Linux (inbuilt) and also
supports different version of LINUX and UNIX. It is also available for the Windows platform.
Analytics and reporting: Nmap tool allows the user to save the output of the scan in a file for
future reference. This allows saving the report in different formats. To save the output in normal
format use following command:
nmap 192.168.1.1 > result.txt
nmap –oX result.xml 192.168.1.1
As per the requirements, user can select from agreeable, XML or normal output. By using this
option output will be saved in an understandable and structured way. Also, this supports the –
help option which will provide an overview of the options supported in Nmap [1].
supports different version of LINUX and UNIX. It is also available for the Windows platform.
Analytics and reporting: Nmap tool allows the user to save the output of the scan in a file for
future reference. This allows saving the report in different formats. To save the output in normal
format use following command:
nmap 192.168.1.1 > result.txt
nmap –oX result.xml 192.168.1.1
As per the requirements, user can select from agreeable, XML or normal output. By using this
option output will be saved in an understandable and structured way. Also, this supports the –
help option which will provide an overview of the options supported in Nmap [1].
Metasploit
Overview:
This tool is helpful in penetration testing. The tool allows the user to test, write and execute the
code for exploit. The framework includes a set of tools which provide support for testing of
security-related vulnerabilities, enumeration of networks, execution of attacks and detection of
evading. Thus, it supports development of exploits as well as pen-testing.
Installation and launching
To install the Metasploit framework on the Linux system following commands are used:
$ wget http://downloads.metasploit.com/datrelaeses/metasploit -latest-Linux-installer.run
After this, use the following command to change the permissions of the file
chmod +x /path/to/Metasploit-latest-Linux-x64-installer.run
Following command is used for the launching of the installer
sudo /path/to/metasploit-latest-linux-x64-installer.run
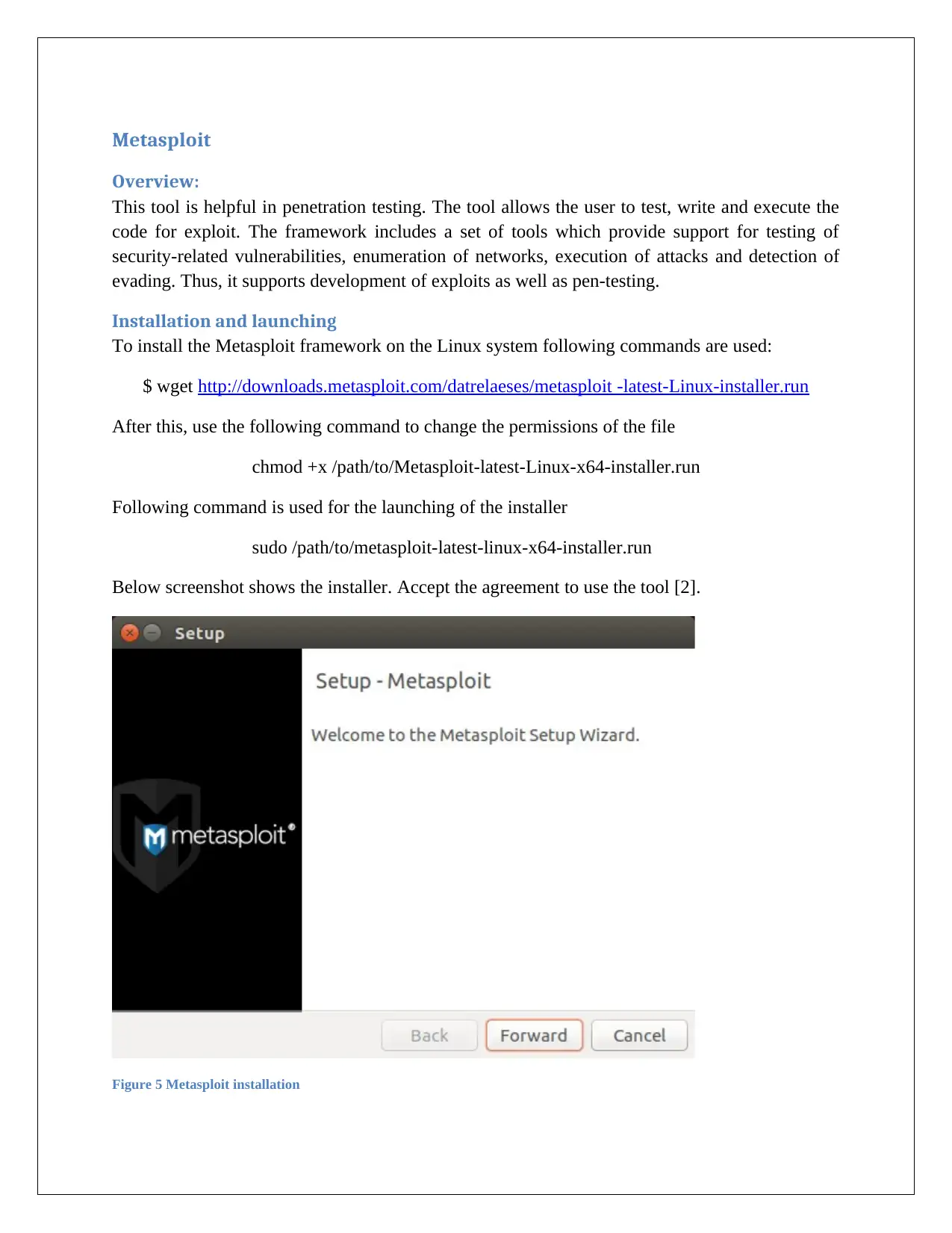
Below screenshot shows the installer. Accept the agreement to use the tool [2].
Figure 5 Metasploit installation
Overview:
This tool is helpful in penetration testing. The tool allows the user to test, write and execute the
code for exploit. The framework includes a set of tools which provide support for testing of
security-related vulnerabilities, enumeration of networks, execution of attacks and detection of
evading. Thus, it supports development of exploits as well as pen-testing.
Installation and launching
To install the Metasploit framework on the Linux system following commands are used:
$ wget http://downloads.metasploit.com/datrelaeses/metasploit -latest-Linux-installer.run
After this, use the following command to change the permissions of the file
chmod +x /path/to/Metasploit-latest-Linux-x64-installer.run
Following command is used for the launching of the installer
sudo /path/to/metasploit-latest-linux-x64-installer.run
Below screenshot shows the installer. Accept the agreement to use the tool [2].
Figure 5 Metasploit installation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
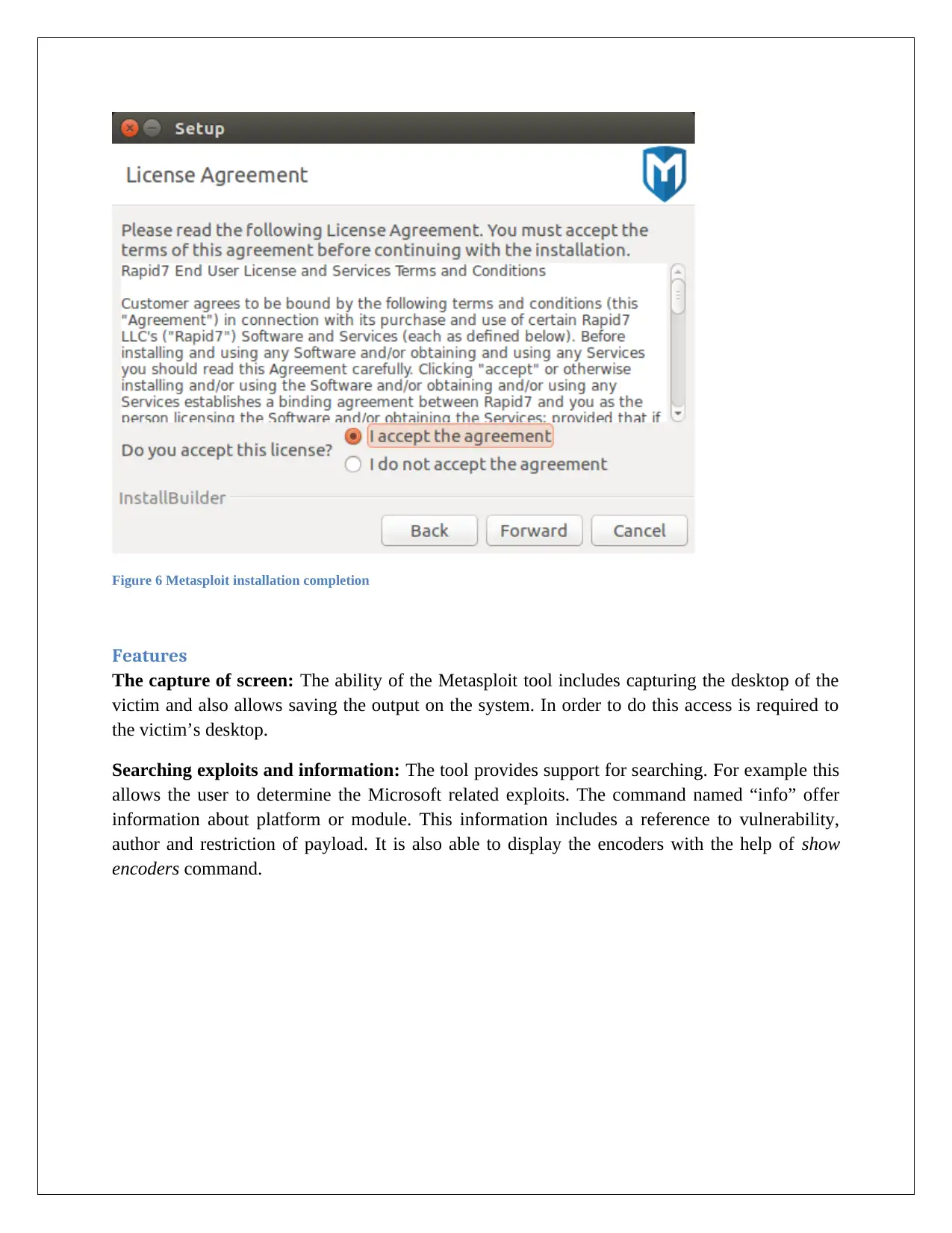
Figure 6 Metasploit installation completion
Features
The capture of screen: The ability of the Metasploit tool includes capturing the desktop of the
victim and also allows saving the output on the system. In order to do this access is required to
the victim’s desktop.
Searching exploits and information: The tool provides support for searching. For example this
allows the user to determine the Microsoft related exploits. The command named “info” offer
information about platform or module. This information includes a reference to vulnerability,
author and restriction of payload. It is also able to display the encoders with the help of show
encoders command.
Features
The capture of screen: The ability of the Metasploit tool includes capturing the desktop of the
victim and also allows saving the output on the system. In order to do this access is required to
the victim’s desktop.
Searching exploits and information: The tool provides support for searching. For example this
allows the user to determine the Microsoft related exploits. The command named “info” offer
information about platform or module. This information includes a reference to vulnerability,
author and restriction of payload. It is also able to display the encoders with the help of show
encoders command.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
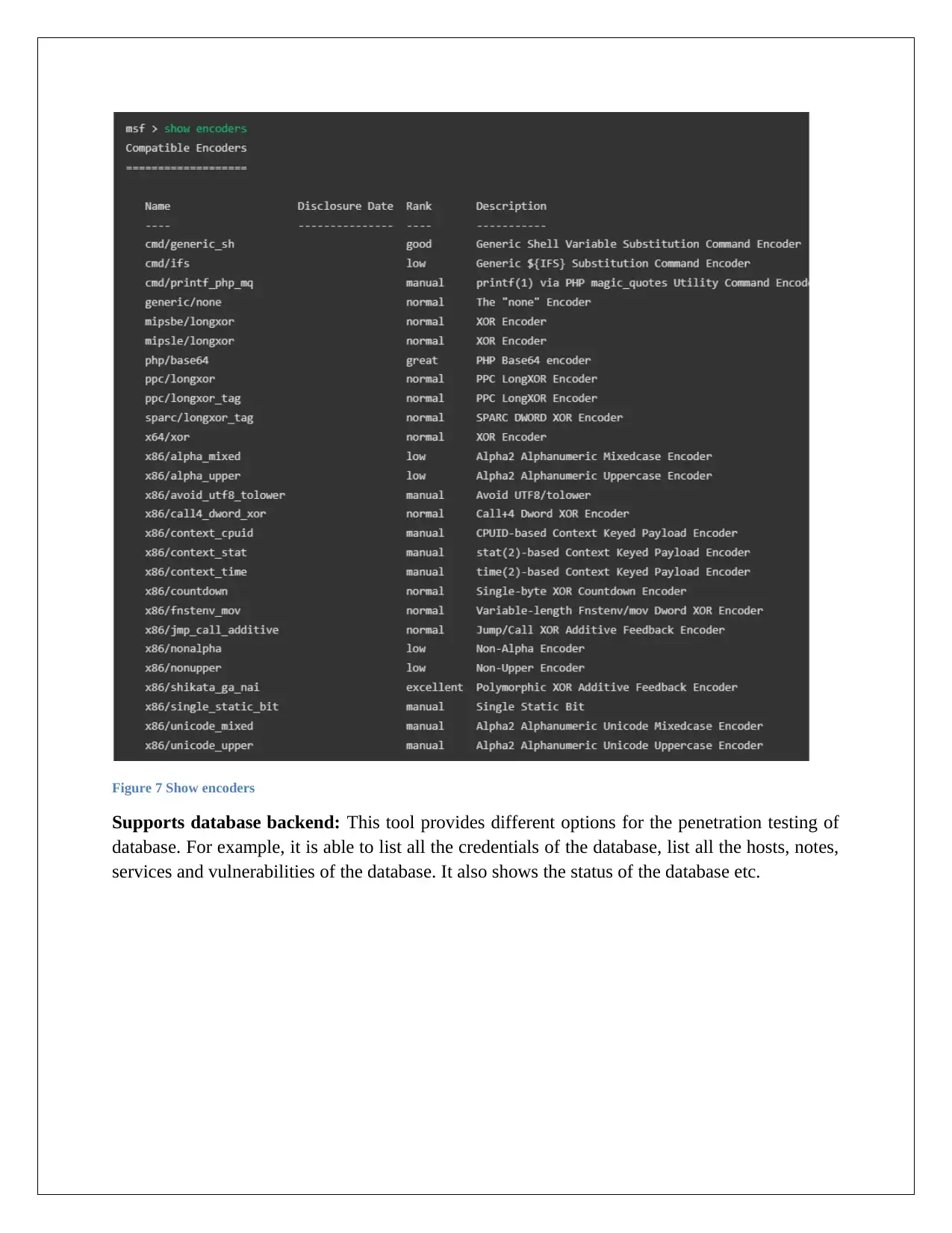
Figure 7 Show encoders
Supports database backend: This tool provides different options for the penetration testing of
database. For example, it is able to list all the credentials of the database, list all the hosts, notes,
services and vulnerabilities of the database. It also shows the status of the database etc.
Supports database backend: This tool provides different options for the penetration testing of
database. For example, it is able to list all the credentials of the database, list all the hosts, notes,
services and vulnerabilities of the database. It also shows the status of the database etc.
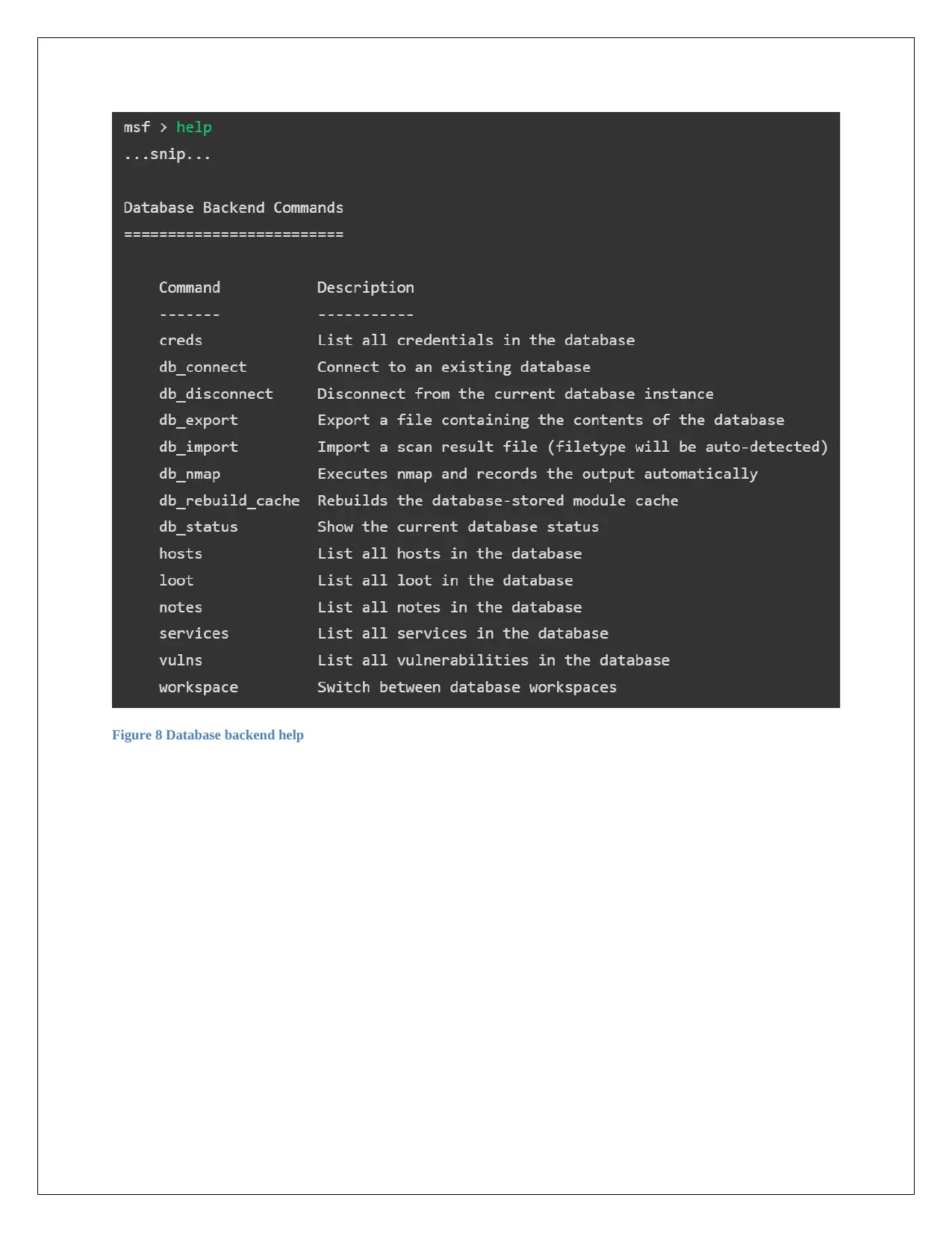
Figure 8 Database backend help
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



