MITS5004 Assignment 1: Phishing Attacks Presentation
VerifiedAdded on 2022/10/04
|11
|653
|328
Presentation
AI Summary
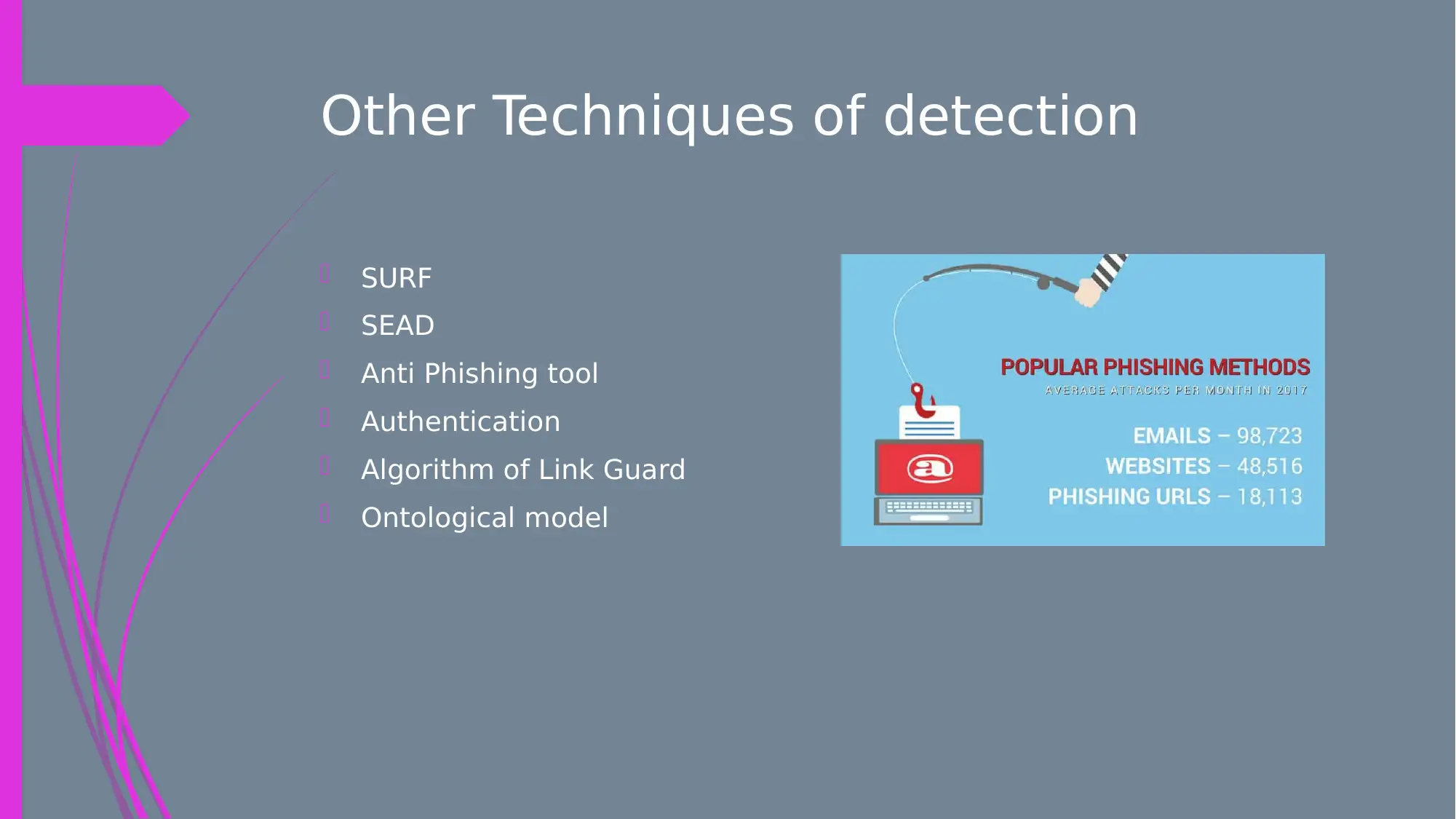
This presentation provides a comprehensive overview of social engineering attacks, focusing specifically on phishing attacks. It explains the manipulation tactics used by attackers to obtain personal information, differentiating between spoofing emails and legitimate communications. The presentation delves into various types of phishing attacks, including spoofing emails, fake accounts, hacking, and Trojan horses, illustrating how attackers exploit system vulnerabilities. Furthermore, it outlines several prevention strategies, such as spoofed email detection using DMARC, fake account detection through awareness, and hacking detection through password security. The presentation also highlights techniques for detecting Trojan horses and emphasizes the importance of caution when downloading files. Various detection methods, including SURF, SEAD, Anti Phishing tools, and authentication algorithms, are also discussed. The conclusion emphasizes the critical need for awareness and knowledge of these attacks to protect against social engineering and phishing threats.
1 out of 11














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)