MITS5004 IT Security: Analyzing the Sony PlayStation Outage & WannaCry
VerifiedAdded on 2023/04/22
|16
|3404
|318
Report
AI Summary
This report delves into two significant IT security incidents: the WannaCry ransomware attack of 2017 and the 2011 Sony PlayStation Network outage. The WannaCry analysis covers the problem's origin, propagation, and potential solutions like vulnerability management, data backups, and endpoint monitoring. It highlights the importance of security awareness training and isolating critical systems. The report also addresses asynchronous I/O issues in memory protection schemes. The Sony PlayStation Network outage section examines the causes, impact on users, and the organization's response, emphasizing the need for robust security measures and timely communication. The document provides a comprehensive overview of these incidents, offering valuable lessons for IT security professionals and students. Desklib provides access to similar solved assignments and study resources.

Running head: It SECURITY
It SECURITY
Name of the Student
Name of the University
Author Note:
It SECURITY
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1It SECURITY
Table of Contents
Part A...................................................................................................................................2
Q.1...................................................................................................................................2
Introduction..................................................................................................................2
Discussion....................................................................................................................2
Conclusion...................................................................................................................5
References....................................................................................................................6
Q.2...................................................................................................................................7
Part B...................................................................................................................................8
Introduction..........................................................................................................................8
Discussion............................................................................................................................8
Problem Encountered.......................................................................................................8
Affect and How................................................................................................................9
Method of attack............................................................................................................10
Preventive Measures......................................................................................................11
Conclusion.........................................................................................................................11
References..........................................................................................................................12
Table of Contents
Part A...................................................................................................................................2
Q.1...................................................................................................................................2
Introduction..................................................................................................................2
Discussion....................................................................................................................2
Conclusion...................................................................................................................5
References....................................................................................................................6
Q.2...................................................................................................................................7
Part B...................................................................................................................................8
Introduction..........................................................................................................................8
Discussion............................................................................................................................8
Problem Encountered.......................................................................................................8
Affect and How................................................................................................................9
Method of attack............................................................................................................10
Preventive Measures......................................................................................................11
Conclusion.........................................................................................................................11
References..........................................................................................................................12

2It SECURITY
Part A
Q.1
Introduction
Digitization in the domain of technology is all about improving the life of various system
user. Digitization has ultimately decreased the number of crimes along documentation of large
number of works [5]. It mainly aims to create a huge number of issues related to personal and
vital information of individuals. There is large number of thefts and cyber-attacks like malware,
spam, Trojan and many more. The main goal of ransomware virus in a system then it can easily
infect and encrypt files of different standards [3]. Ransomware is nothing but a demand which is
paid by the user for getting access to the important files. WannaCry Ransomware Attack 2017 is
nothing but the worst kind of attack.
The upcoming pages of the report mainly tends to highlight encountered problem,
method of occurrence and last possible solution. WannaCry Ransomware is a kind of malicious
attack which can block access of a user to its files or even system. It is all about hosting large
number of files for entire devices before making use of encryption until and unless a ransom is
paid to the hacker.
Discussion
Problem Encountered
WannaCry Ransomware attack 2017 is considered to be as one of the largest kind of
attack. As per [2], India was on the list from this particular cyber attack, Madhya Pradesh was
one of the worst affect regions in the world to date. Organization FedEx, Nissan and railway of
Part A
Q.1
Introduction
Digitization in the domain of technology is all about improving the life of various system
user. Digitization has ultimately decreased the number of crimes along documentation of large
number of works [5]. It mainly aims to create a huge number of issues related to personal and
vital information of individuals. There is large number of thefts and cyber-attacks like malware,
spam, Trojan and many more. The main goal of ransomware virus in a system then it can easily
infect and encrypt files of different standards [3]. Ransomware is nothing but a demand which is
paid by the user for getting access to the important files. WannaCry Ransomware Attack 2017 is
nothing but the worst kind of attack.
The upcoming pages of the report mainly tends to highlight encountered problem,
method of occurrence and last possible solution. WannaCry Ransomware is a kind of malicious
attack which can block access of a user to its files or even system. It is all about hosting large
number of files for entire devices before making use of encryption until and unless a ransom is
paid to the hacker.
Discussion
Problem Encountered
WannaCry Ransomware attack 2017 is considered to be as one of the largest kind of
attack. As per [2], India was on the list from this particular cyber attack, Madhya Pradesh was
one of the worst affect regions in the world to date. Organization FedEx, Nissan and railway of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3It SECURITY
Germany and interior industry. It focuses on analyzing some of the telecommunication
organization like mega for telephonic which is based in Spain. Around 16 NHS based
organization which are based in UK are badly affected [4]. Some of UK based system are badly
affect by malware and large number of Chinese student were badly hit by this ransomware.
Fig 1: Ransomware Attack
Source: [6]
How and Why did it occur
The above diagram highlights the Working mechanism of WannaCry Ransomware
Attack. WannaCry is all about locking all the current data in the computer system of different
users [1]. It mainly leaves two files for instructing users that is what user is taken next step for
decrypting the program. The hacker of this WannaCry attack demands the total payment in the
form of bitcoin. There are many instances where the file can be easily deleted. Ransomware
virus can overwrite the content of any file by opening any file, irrespective of the content. The
Germany and interior industry. It focuses on analyzing some of the telecommunication
organization like mega for telephonic which is based in Spain. Around 16 NHS based
organization which are based in UK are badly affected [4]. Some of UK based system are badly
affect by malware and large number of Chinese student were badly hit by this ransomware.
Fig 1: Ransomware Attack
Source: [6]
How and Why did it occur
The above diagram highlights the Working mechanism of WannaCry Ransomware
Attack. WannaCry is all about locking all the current data in the computer system of different
users [1]. It mainly leaves two files for instructing users that is what user is taken next step for
decrypting the program. The hacker of this WannaCry attack demands the total payment in the
form of bitcoin. There are many instances where the file can be easily deleted. Ransomware
virus can overwrite the content of any file by opening any file, irrespective of the content. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
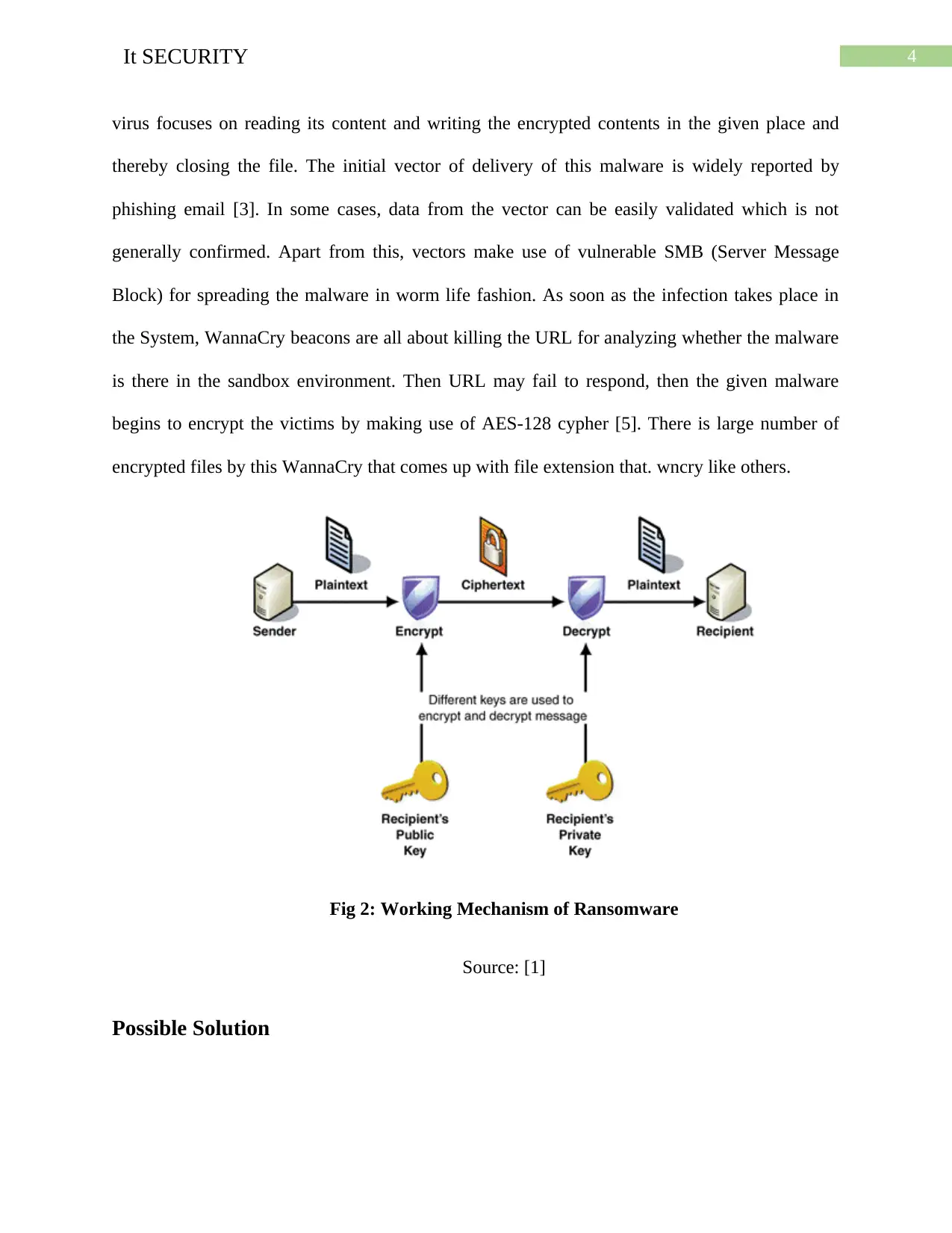
4It SECURITY
virus focuses on reading its content and writing the encrypted contents in the given place and
thereby closing the file. The initial vector of delivery of this malware is widely reported by
phishing email [3]. In some cases, data from the vector can be easily validated which is not
generally confirmed. Apart from this, vectors make use of vulnerable SMB (Server Message
Block) for spreading the malware in worm life fashion. As soon as the infection takes place in
the System, WannaCry beacons are all about killing the URL for analyzing whether the malware
is there in the sandbox environment. Then URL may fail to respond, then the given malware
begins to encrypt the victims by making use of AES-128 cypher [5]. There is large number of
encrypted files by this WannaCry that comes up with file extension that. wncry like others.
Fig 2: Working Mechanism of Ransomware
Source: [1]
Possible Solution
virus focuses on reading its content and writing the encrypted contents in the given place and
thereby closing the file. The initial vector of delivery of this malware is widely reported by
phishing email [3]. In some cases, data from the vector can be easily validated which is not
generally confirmed. Apart from this, vectors make use of vulnerable SMB (Server Message
Block) for spreading the malware in worm life fashion. As soon as the infection takes place in
the System, WannaCry beacons are all about killing the URL for analyzing whether the malware
is there in the sandbox environment. Then URL may fail to respond, then the given malware
begins to encrypt the victims by making use of AES-128 cypher [5]. There is large number of
encrypted files by this WannaCry that comes up with file extension that. wncry like others.
Fig 2: Working Mechanism of Ransomware
Source: [1]
Possible Solution

5It SECURITY
Various organization can easily overcome the risk by taking account large number of
aspect like
Organization should focus on vulnerability management which is inclusive of patch
management and vulnerability scanning [2]. It considered being robust and mature kind
of enterprise level program.
Organization should maintain backups which will store the critical data and speed of data
generation [4]. A proper alignment should be done concerning timeline and procedure for
restoring the backups. It is mainly aligned with the business continuity plan (BCP).
Various firms need to implement end point monitoring providing visibility into malicious
behaviour. It mainly tends to occur at a different level.
A proper verification needs to be done concerning security awareness training program
for maintaining effectiveness against this ransomware attack [6]. It is mainly updated on
a regular basis on understanding the present cyber threat environment.
A confirmation needs to be done concerning critical system which is not unnecessarily
connected or accessible from Internet.
Conclusion
It can be concluded that the report tend to provide an analysis and making aware of
ransomware, its effect and some of its preventive measures. The fact has been concluded that
WannaCry 2017 attack was most terrifying one. The main source of the ransomware virus is
through phishing mail advertisement. It is a website which contains a malicious program. The
only recommendation for this attack is back up of the data on a regular basis.
Various organization can easily overcome the risk by taking account large number of
aspect like
Organization should focus on vulnerability management which is inclusive of patch
management and vulnerability scanning [2]. It considered being robust and mature kind
of enterprise level program.
Organization should maintain backups which will store the critical data and speed of data
generation [4]. A proper alignment should be done concerning timeline and procedure for
restoring the backups. It is mainly aligned with the business continuity plan (BCP).
Various firms need to implement end point monitoring providing visibility into malicious
behaviour. It mainly tends to occur at a different level.
A proper verification needs to be done concerning security awareness training program
for maintaining effectiveness against this ransomware attack [6]. It is mainly updated on
a regular basis on understanding the present cyber threat environment.
A confirmation needs to be done concerning critical system which is not unnecessarily
connected or accessible from Internet.
Conclusion
It can be concluded that the report tend to provide an analysis and making aware of
ransomware, its effect and some of its preventive measures. The fact has been concluded that
WannaCry 2017 attack was most terrifying one. The main source of the ransomware virus is
through phishing mail advertisement. It is a website which contains a malicious program. The
only recommendation for this attack is back up of the data on a regular basis.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6It SECURITY
References
[1] Q. Chen, and R.A. Bridges. Automated Behavioral Analysis of Malware a Case Study of
WannaCry Ransomware. arXiv preprint arXiv:1709.08753, 2017.
[2] S.K, Sahi. A Study of WannaCry Ransomware Attack. International Journal of Engineering
Research in Computer Science and Engineering, 4(9), pp.5-7, 2017.
[3] G., Martin, S., Ghafur, J., Kinross, C, Hankin. and A. Darzi. WannaCry—a year on, 2018.
[4] M., Alam, S., Bhattacharya, D., Mukhopadhyay and A., Chattopadhyay. RAPPER:
Ransomware Prevention via Performance Counters. arXiv preprint arXiv:1802.03909, 2018.
[5] A., Zimba, L., Simukonda and M., Chishimba. Demystifying Ransomware Attacks: Reverse
Engineering and Dynamic Malware Analysis of WannaCry for Network and Information
Security. Zambia ICT Journal, 1(1), pp.35-40, 2017.
[6] D.,Lisiak-Felicka, P. Nowak, and M. Szmit. SELECTED ASPECTS OF INFORMATION
SECURITY MANAGEMENT IN ENTITIES PERFORMING MEDICAL ACTIVITY.
In Economic and Social Development (Book of Proceedings), 34th International Scientific
Conference on Economic and Social(Vol. 20, No. 3, p. 51) , 2018.
References
[1] Q. Chen, and R.A. Bridges. Automated Behavioral Analysis of Malware a Case Study of
WannaCry Ransomware. arXiv preprint arXiv:1709.08753, 2017.
[2] S.K, Sahi. A Study of WannaCry Ransomware Attack. International Journal of Engineering
Research in Computer Science and Engineering, 4(9), pp.5-7, 2017.
[3] G., Martin, S., Ghafur, J., Kinross, C, Hankin. and A. Darzi. WannaCry—a year on, 2018.
[4] M., Alam, S., Bhattacharya, D., Mukhopadhyay and A., Chattopadhyay. RAPPER:
Ransomware Prevention via Performance Counters. arXiv preprint arXiv:1802.03909, 2018.
[5] A., Zimba, L., Simukonda and M., Chishimba. Demystifying Ransomware Attacks: Reverse
Engineering and Dynamic Malware Analysis of WannaCry for Network and Information
Security. Zambia ICT Journal, 1(1), pp.35-40, 2017.
[6] D.,Lisiak-Felicka, P. Nowak, and M. Szmit. SELECTED ASPECTS OF INFORMATION
SECURITY MANAGEMENT IN ENTITIES PERFORMING MEDICAL ACTIVITY.
In Economic and Social Development (Book of Proceedings), 34th International Scientific
Conference on Economic and Social(Vol. 20, No. 3, p. 51) , 2018.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7It SECURITY
Q.2
Fence register provides the ability for relocating. It is needed for separating two users
with a start address which is defined as base address that has been provided. All the required
programs are in the specific area which is offset from the base address. A user can make use of
address in the space which can exceed beyond the limit [4]. It is done on the upper bound which
is a restriction given to user from entering in the given area. Upper bound register is sometimes
named as bound register. It is required for providing separation and integrity of given data to
scheme for base/bound register which is important for implementation. A pair of register that is
base/ bound aims in providing lower and upper limit to some of the areas to the user. It can easily
can protect a given single user from another kind of available user. Paging aims divide the
program into equal sizes, pages and lastly memory into required time frame [1]. By the help of
this page table name and related memory address is a generally stored in the page table. Making
use of page and offset value, different kind of address can be easily accessed.
The biggest advantage of operating system is the fence register which comes up with the
ability to relocate [4]. It is an important characteristic for understanding the multiuser
environment. With the help of one or more user, no one can have an understanding where the
program will execute. Relocated register aims to solving problem by giving base or even the
starting address. All the given addresses are provided inside the program which is offset in the
base address. The given programs are mainly offset in the base or even starting address. A
variable or fence register is also known as base register. In the case of Fence register aims to
provide lower bound not the upper bound. An upper bound can be considered to be useful in the
given space by analyzing the given forbidden areas. To tackle these issues, a second register is
often added [1]. The second register is often termed like a bound register which is provided in
Q.2
Fence register provides the ability for relocating. It is needed for separating two users
with a start address which is defined as base address that has been provided. All the required
programs are in the specific area which is offset from the base address. A user can make use of
address in the space which can exceed beyond the limit [4]. It is done on the upper bound which
is a restriction given to user from entering in the given area. Upper bound register is sometimes
named as bound register. It is required for providing separation and integrity of given data to
scheme for base/bound register which is important for implementation. A pair of register that is
base/ bound aims in providing lower and upper limit to some of the areas to the user. It can easily
can protect a given single user from another kind of available user. Paging aims divide the
program into equal sizes, pages and lastly memory into required time frame [1]. By the help of
this page table name and related memory address is a generally stored in the page table. Making
use of page and offset value, different kind of address can be easily accessed.
The biggest advantage of operating system is the fence register which comes up with the
ability to relocate [4]. It is an important characteristic for understanding the multiuser
environment. With the help of one or more user, no one can have an understanding where the
program will execute. Relocated register aims to solving problem by giving base or even the
starting address. All the given addresses are provided inside the program which is offset in the
base address. The given programs are mainly offset in the base or even starting address. A
variable or fence register is also known as base register. In the case of Fence register aims to
provide lower bound not the upper bound. An upper bound can be considered to be useful in the
given space by analyzing the given forbidden areas. To tackle these issues, a second register is
often added [1]. The second register is often termed like a bound register which is provided in

8It SECURITY
the upper limit. Each of the given diagrams is forced above the given base address which is
added to address limit. This particular technique is used for protecting a given program address
which can be changed by any of modification by another given user. As the given execution
changes from one given program to another, then the operating system should aim to makes
changes concerning content of the base and bound register. It is mainly required for
understanding the true space for that particular use r[3]. Any kind of change is the given part is
defined as preparation of a given context switch. Making use of pair in base/ bound can help a
register in protecting the users from outside.
the upper limit. Each of the given diagrams is forced above the given base address which is
added to address limit. This particular technique is used for protecting a given program address
which can be changed by any of modification by another given user. As the given execution
changes from one given program to another, then the operating system should aim to makes
changes concerning content of the base and bound register. It is mainly required for
understanding the true space for that particular use r[3]. Any kind of change is the given part is
defined as preparation of a given context switch. Making use of pair in base/ bound can help a
register in protecting the users from outside.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9It SECURITY
References
[1] D., Jeong, Y, Lee and J.S, Kim. Boosting Quasi-Asynchronous I/O for Better Responsiveness
in Mobile Devices. In FAST (pp. 191-202) , 2015, February.
[2] P., Harrington. Diagnosing Parallel, I/O Bottlenecks in HPC Applications. In International
Conference for High Performance Computing, Networking, Storage and Analysis (SCI7), ACM
Student Research Competition (SRC), 2017
[3] S. Kim, H. Kim, J, Lee and J, Jeong. Enlightening the I/O Path: A Holistic Approach for
Application Performance. In FAST (pp. 345-358), 2017, February.
[4] W., Zwart, K.D., Flach, B., Rudraraju, T.M., Abdel-Fatah, O., Gojis, S., Canisius, D.Moore ,
E., Nevedomskaya, M.,Opdam, M. Droog, and I. Hofland, SRC3 phosphorylation at serine 543
is a positive independent prognostic factor in ER-positive breast cancer. Clinical Cancer
Research, 22(2), pp.479-491, 2016.
References
[1] D., Jeong, Y, Lee and J.S, Kim. Boosting Quasi-Asynchronous I/O for Better Responsiveness
in Mobile Devices. In FAST (pp. 191-202) , 2015, February.
[2] P., Harrington. Diagnosing Parallel, I/O Bottlenecks in HPC Applications. In International
Conference for High Performance Computing, Networking, Storage and Analysis (SCI7), ACM
Student Research Competition (SRC), 2017
[3] S. Kim, H. Kim, J, Lee and J, Jeong. Enlightening the I/O Path: A Holistic Approach for
Application Performance. In FAST (pp. 345-358), 2017, February.
[4] W., Zwart, K.D., Flach, B., Rudraraju, T.M., Abdel-Fatah, O., Gojis, S., Canisius, D.Moore ,
E., Nevedomskaya, M.,Opdam, M. Droog, and I. Hofland, SRC3 phosphorylation at serine 543
is a positive independent prognostic factor in ER-positive breast cancer. Clinical Cancer
Research, 22(2), pp.479-491, 2016.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10It SECURITY
Part B
Introduction
On 28 April, 2011 Sony shares has come down by more than 5% at Tokyo Stock
Exchange [5]. The organization was encountering huge number of issues in the present period in
the current its gaming division. Hackers have invaded the Network of Sony PlayStation have
roughly invaded two weeks earlier in the period between 17 April 2011 and 19 April 2011 [4].
In the coming pages of the report, an idea has been provided concerning problem
encountered in Sony. After that, the effects of Sony been been provided in details. Mode of this
particular attack has been provided in brief. The report ends with a list of preventive step for this
kind of attack in near future.
Discussion
Problem Encountered
Sony failed to understand the main source of intrusion until and initial discovery of the
attack [1]. The organization does information related to breach in the given period. General
public tends to put question on the slow response on Sony and lack internal security system.
Sony was in the plan of bringing back the network to online platform. It does not make any kind
of confirmation concerning information which can be illegally used by hackers [4]. Blogs were
there about the fact that how organization can respond to changes in the upcoming days. It is
considered to be a dreadful incident till date.
Part B
Introduction
On 28 April, 2011 Sony shares has come down by more than 5% at Tokyo Stock
Exchange [5]. The organization was encountering huge number of issues in the present period in
the current its gaming division. Hackers have invaded the Network of Sony PlayStation have
roughly invaded two weeks earlier in the period between 17 April 2011 and 19 April 2011 [4].
In the coming pages of the report, an idea has been provided concerning problem
encountered in Sony. After that, the effects of Sony been been provided in details. Mode of this
particular attack has been provided in brief. The report ends with a list of preventive step for this
kind of attack in near future.
Discussion
Problem Encountered
Sony failed to understand the main source of intrusion until and initial discovery of the
attack [1]. The organization does information related to breach in the given period. General
public tends to put question on the slow response on Sony and lack internal security system.
Sony was in the plan of bringing back the network to online platform. It does not make any kind
of confirmation concerning information which can be illegally used by hackers [4]. Blogs were
there about the fact that how organization can respond to changes in the upcoming days. It is
considered to be a dreadful incident till date.

11It SECURITY
On 21 April, 2011 just one day later Sony PlayStation was taken down, the director of
Corporate Communication and Marketing issues related to messages were given to the Customer
of Sony on their official PlayStation blog. At the time of investing the main cause of Network
outage, the people want to make an alert for full day or even before. The organization may fail to
get services for competing for backup and running [5]. Consumer provided a wide range of
option and gamer were given thought about inability for playing game or even watching movies
and television shows. In various comment posted by user on PlayStation Blog and Huffington
post, there were large number of users for understanding their outage [7]. It focuses on
understanding the frustration of their inability for playing games which they were waiting for
more.
Affect and How
On this day of attack, Sony along its representative kept their whole gaming community
up to date which can become clear. On 21st and 22nd April, certain number of messages were
posted on the PlayStation Blog. It mainly notified large number of users who believed the fact
that outage was mainly due a result of any external intrusion [8]. Sony was planning to bring
both PlayStation and Qriocity) back to online mode. The main effort of this organization was all
about resolving large number of matters like building large number of system for the network
infrastructure. It was considered to be time-consuming which is required for providing any given
system with additional kind of security measures. The goodwill from the community mainly
tends to evaporate in few minutes. There was large number of people that have different number
of communities in the given time. There is large number of people who tend to provide support
to Sony [4]. A large number of users have reacted for understanding who felt that they had been
betrayed by Sony. This is because their credit card information has been stolen by some hackers.
On 21 April, 2011 just one day later Sony PlayStation was taken down, the director of
Corporate Communication and Marketing issues related to messages were given to the Customer
of Sony on their official PlayStation blog. At the time of investing the main cause of Network
outage, the people want to make an alert for full day or even before. The organization may fail to
get services for competing for backup and running [5]. Consumer provided a wide range of
option and gamer were given thought about inability for playing game or even watching movies
and television shows. In various comment posted by user on PlayStation Blog and Huffington
post, there were large number of users for understanding their outage [7]. It focuses on
understanding the frustration of their inability for playing games which they were waiting for
more.
Affect and How
On this day of attack, Sony along its representative kept their whole gaming community
up to date which can become clear. On 21st and 22nd April, certain number of messages were
posted on the PlayStation Blog. It mainly notified large number of users who believed the fact
that outage was mainly due a result of any external intrusion [8]. Sony was planning to bring
both PlayStation and Qriocity) back to online mode. The main effort of this organization was all
about resolving large number of matters like building large number of system for the network
infrastructure. It was considered to be time-consuming which is required for providing any given
system with additional kind of security measures. The goodwill from the community mainly
tends to evaporate in few minutes. There was large number of people that have different number
of communities in the given time. There is large number of people who tend to provide support
to Sony [4]. A large number of users have reacted for understanding who felt that they had been
betrayed by Sony. This is because their credit card information has been stolen by some hackers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





