MN502 Network Security: Nessus and Nmap Tools Analysis Report
VerifiedAdded on 2023/06/12
|23
|1463
|224
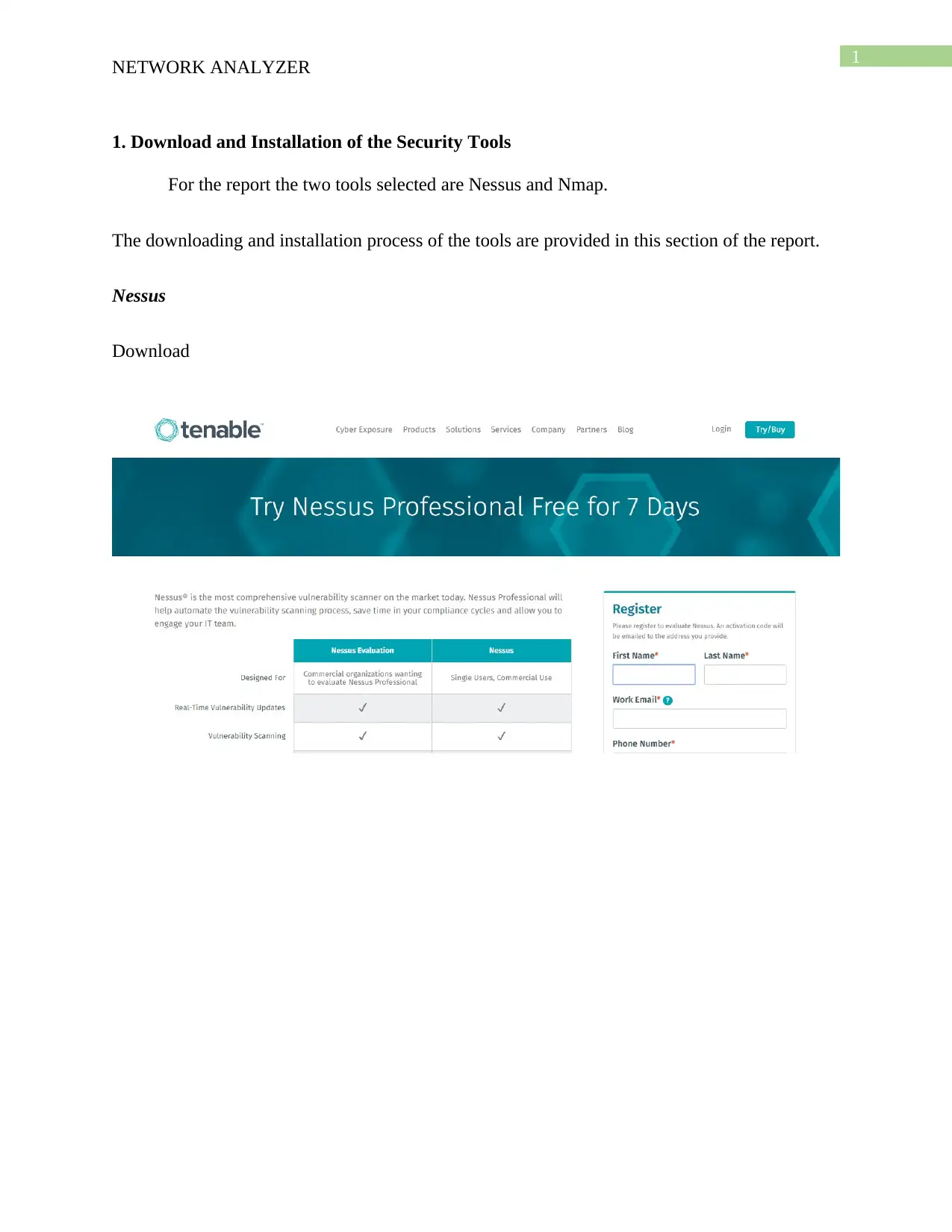
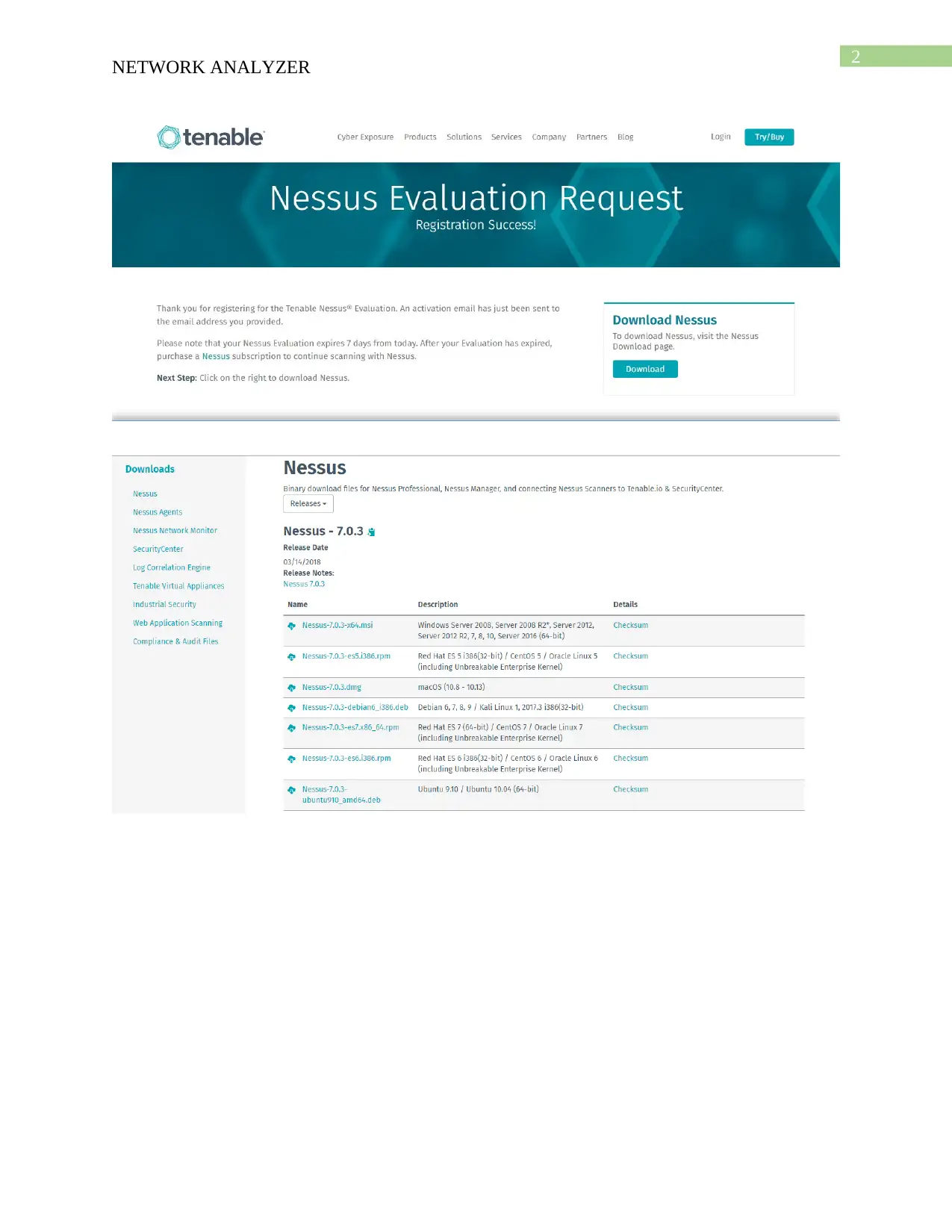
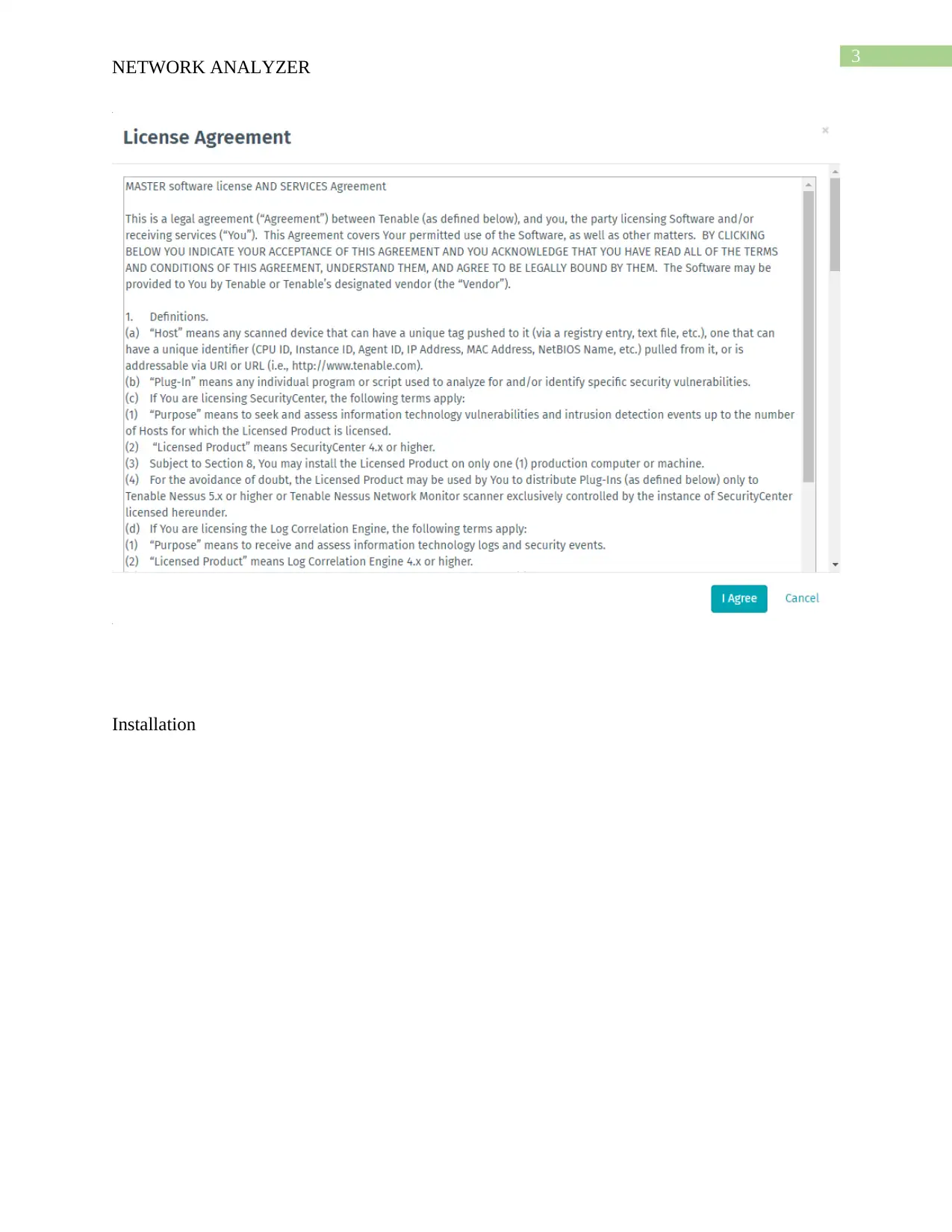
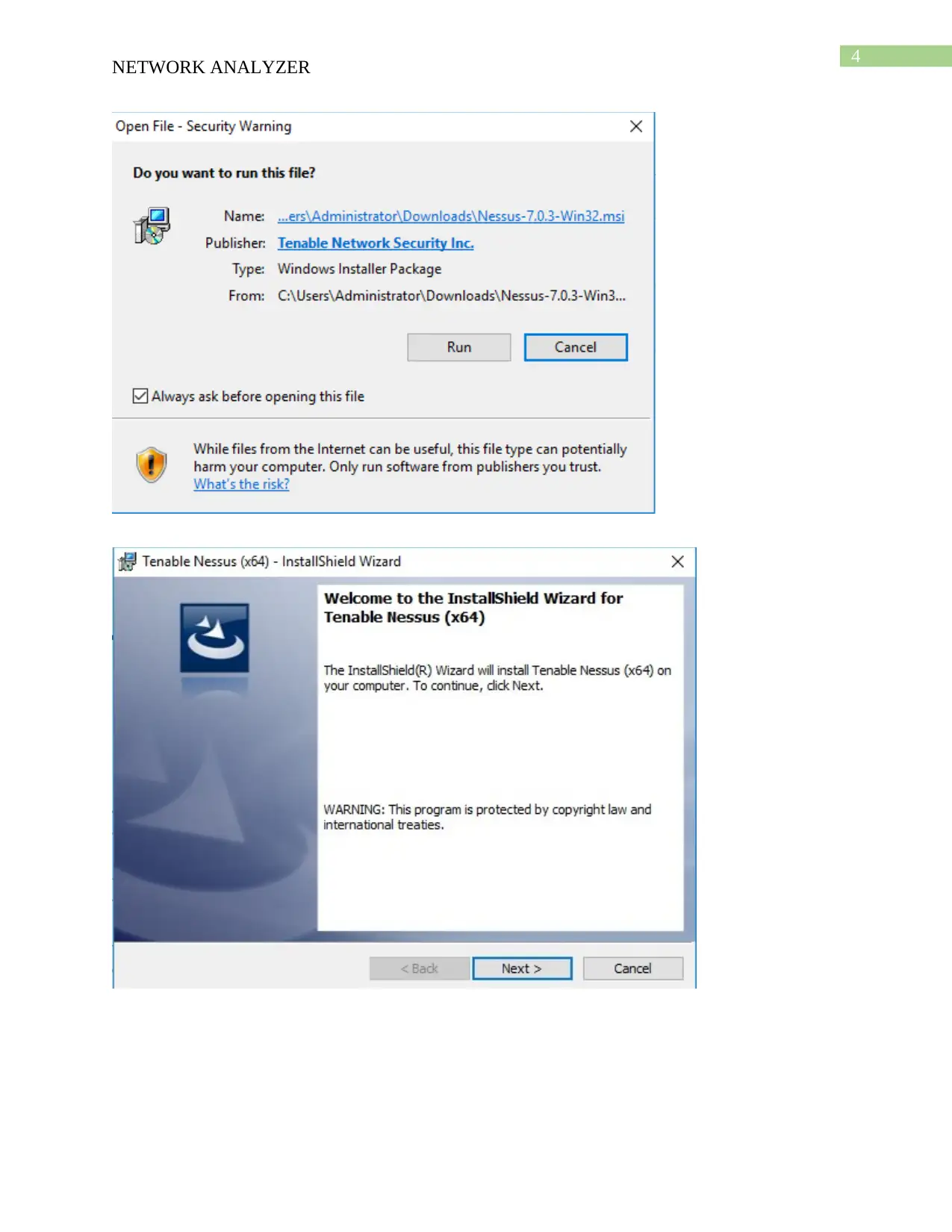
Report
AI Summary
This report provides a detailed analysis of two prominent network security tools, Nessus and Nmap. It covers their download and installation processes, descriptions, and demonstrations of their capabilities. Nessus is highlighted for its vulnerability detection and web scanning options, while Nmap is praised for its network mapping and victim machine identification. The report compares the tools in terms of scanning capabilities, time consumption, and ease of use. A case study involving UVW organization, an educational institute with multiple sites and BYOD policies, is analyzed to determine the most suitable tool, concluding that Nmap is preferable due to its cost-effectiveness and security features. The report also includes a bibliography of relevant sources.
1 out of 23








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)