MN503 Overview of Internetworking: Network Design for Primary School
VerifiedAdded on 2023/06/11
|9
|1328
|153
Report
AI Summary
This report outlines the design of a network for a primary school, incorporating a separate guest network with restricted access. The project scope includes creating a basic LAN for 50 internal users and a separate LAN for approximately 10 guest users, utilizing an FTP server to limit guest access to specific files. The network design incorporates routers and switches configured to differentiate access levels, ensuring full access for internal users while restricting guest users. The report includes an IP address table, network topology diagram, switch and router configurations, DHCP configuration, and guidelines for access point and server configurations. Security configurations are also addressed, with the core switch configured with access control lists to prevent guest network access to the school's local area network. The design adheres to user-centric principles, dividing the network into core, access, and distribution layers to meet the organization's needs.

Running head: OVERVIEW OF INTERNETWORKING
Assignment 2
Primary School Network Design with Guest Network
Name of the Student
Name of the University
Author’s Note
Assignment 2
Primary School Network Design with Guest Network
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
OVERVIEW OF INTERNETWORKING
Table of Contents
Project scope...............................................................................................................................................2
Project Requirement...................................................................................................................................2
Network Design...........................................................................................................................................3
IP address Table...........................................................................................................................................3
Network Topology Diagram.........................................................................................................................3
Switch Configuration...............................................................................................................................3
Router Configuration...............................................................................................................................5
DHCP Configuration.................................................................................................................................6
Access Point, Server configuration Guidelines.........................................................................................6
Security Configurations...........................................................................................................................7
Conclusion...................................................................................................................................................7
Bibliography................................................................................................................................................8
OVERVIEW OF INTERNETWORKING
Table of Contents
Project scope...............................................................................................................................................2
Project Requirement...................................................................................................................................2
Network Design...........................................................................................................................................3
IP address Table...........................................................................................................................................3
Network Topology Diagram.........................................................................................................................3
Switch Configuration...............................................................................................................................3
Router Configuration...............................................................................................................................5
DHCP Configuration.................................................................................................................................6
Access Point, Server configuration Guidelines.........................................................................................6
Security Configurations...........................................................................................................................7
Conclusion...................................................................................................................................................7
Bibliography................................................................................................................................................8

2
OVERVIEW OF INTERNETWORKING
Project scope
The primary school can be considered as a is a small organization has faced the need of a network which
is to be used by the internal users which is around 50 and guest user which is not more than 10. The
network would be created with an aim that the 50 users would be using the whole network whereas the
separate network would be created that would be used by the 10 users that would be consisting of
some specific details. The separate section would be created which used by the guest user for the
purpose of downloading specific files and the LAN network that would be created for the daily users
would totally remain separated. The network would be using the FTP server which would be associated
with creating the separation between the daily user and the guest user.
Project Requirement
The network has certain requirements and this would be mainly including the following components:
Creation of a basic LAN network which would be used by the daily 50 users
Besides the LAN network for the daily user a separate LAN network is also to be created for the
guest users which would be consisting of a limited access.
The network would be consisting of a FTP server which would associated with restricting eth
guest user’s form accessing the original network. Only a limited access would be provided to the
gest users.
The network would be consisting of various network components that mainly includes the
routers and the switches which are to be configured so as to limit the guest users and to provide
full access to the daily users.
OVERVIEW OF INTERNETWORKING
Project scope
The primary school can be considered as a is a small organization has faced the need of a network which
is to be used by the internal users which is around 50 and guest user which is not more than 10. The
network would be created with an aim that the 50 users would be using the whole network whereas the
separate network would be created that would be used by the 10 users that would be consisting of
some specific details. The separate section would be created which used by the guest user for the
purpose of downloading specific files and the LAN network that would be created for the daily users
would totally remain separated. The network would be using the FTP server which would be associated
with creating the separation between the daily user and the guest user.
Project Requirement
The network has certain requirements and this would be mainly including the following components:
Creation of a basic LAN network which would be used by the daily 50 users
Besides the LAN network for the daily user a separate LAN network is also to be created for the
guest users which would be consisting of a limited access.
The network would be consisting of a FTP server which would associated with restricting eth
guest user’s form accessing the original network. Only a limited access would be provided to the
gest users.
The network would be consisting of various network components that mainly includes the
routers and the switches which are to be configured so as to limit the guest users and to provide
full access to the daily users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
OVERVIEW OF INTERNETWORKING
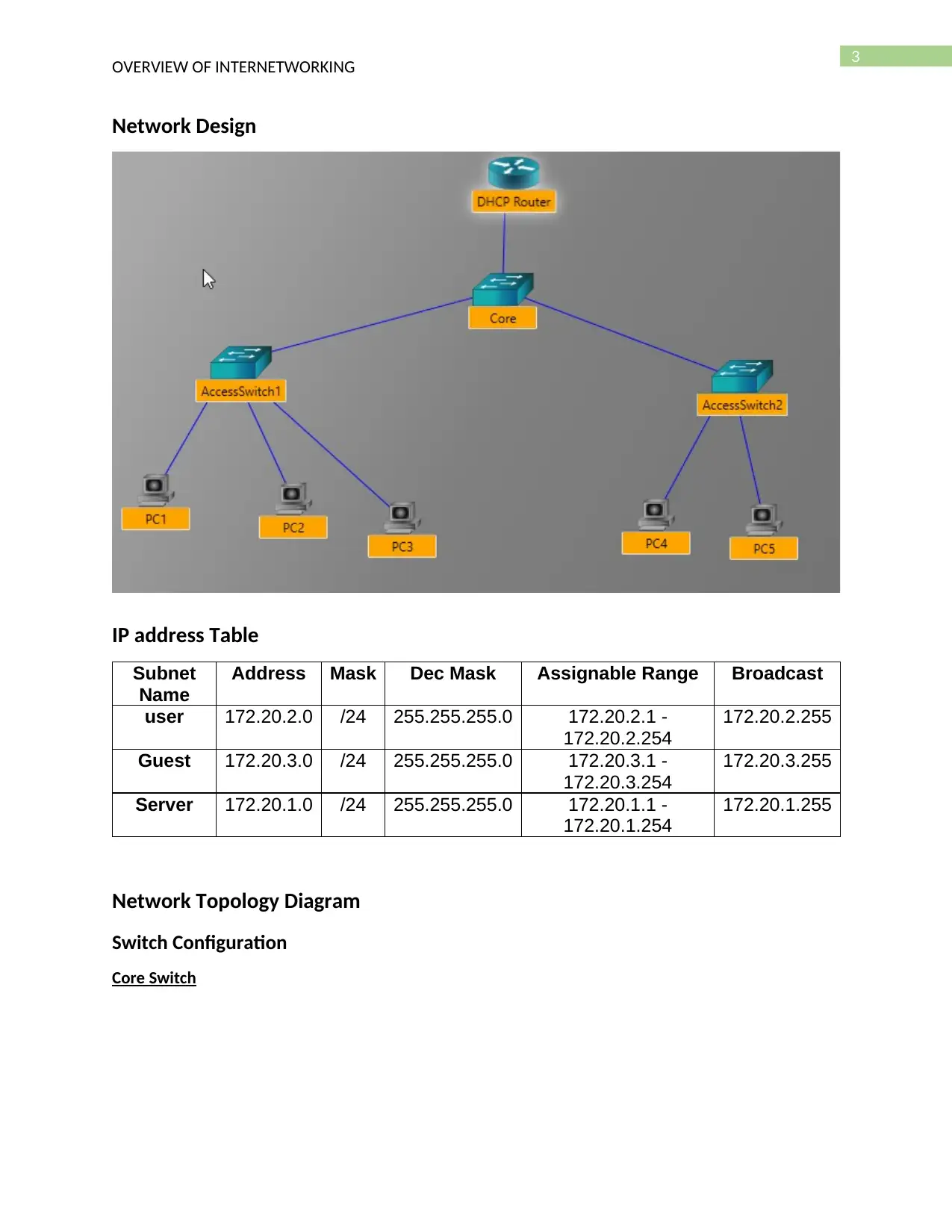
Network Design
IP address Table
Subnet
Name
Address Mask Dec Mask Assignable Range Broadcast
user 172.20.2.0 /24 255.255.255.0 172.20.2.1 -
172.20.2.254
172.20.2.255
Guest 172.20.3.0 /24 255.255.255.0 172.20.3.1 -
172.20.3.254
172.20.3.255
Server 172.20.1.0 /24 255.255.255.0 172.20.1.1 -
172.20.1.254
172.20.1.255
Network Topology Diagram
Switch Configuration
Core Switch
OVERVIEW OF INTERNETWORKING
Network Design
IP address Table
Subnet
Name
Address Mask Dec Mask Assignable Range Broadcast
user 172.20.2.0 /24 255.255.255.0 172.20.2.1 -
172.20.2.254
172.20.2.255
Guest 172.20.3.0 /24 255.255.255.0 172.20.3.1 -
172.20.3.254
172.20.3.255
Server 172.20.1.0 /24 255.255.255.0 172.20.1.1 -
172.20.1.254
172.20.1.255
Network Topology Diagram
Switch Configuration
Core Switch
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
OVERVIEW OF INTERNETWORKING
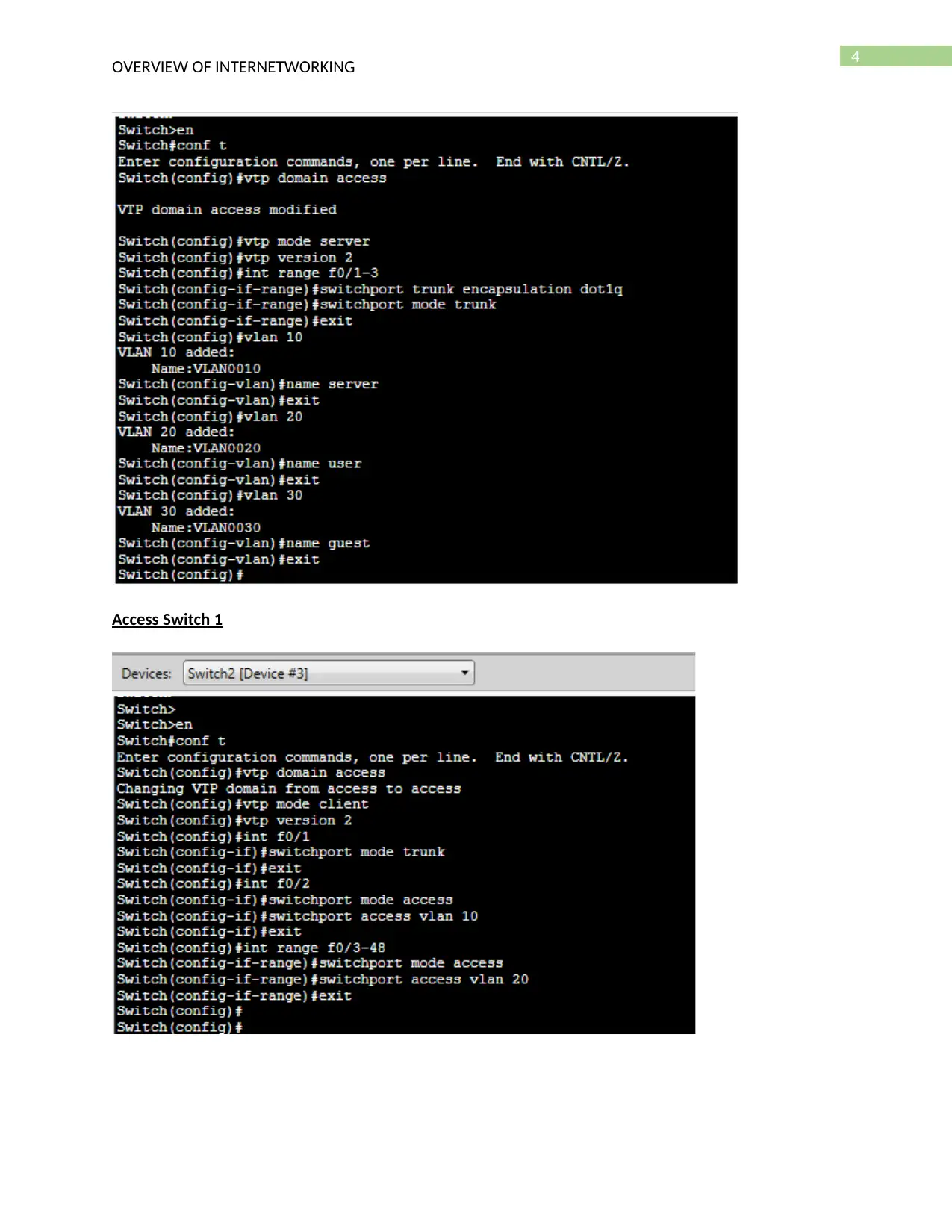
Access Switch 1
OVERVIEW OF INTERNETWORKING
Access Switch 1
5
OVERVIEW OF INTERNETWORKING
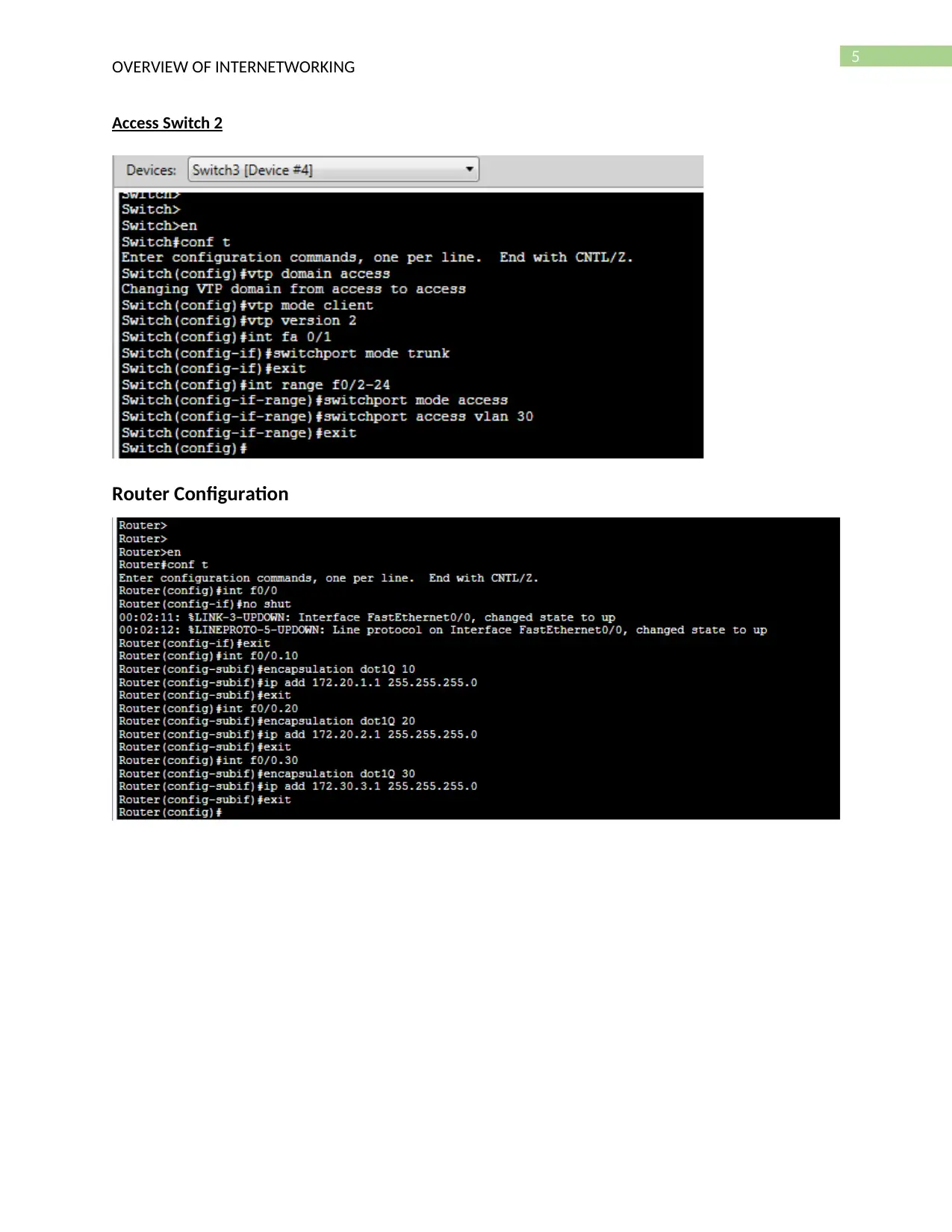
Access Switch 2
Router Configuration
OVERVIEW OF INTERNETWORKING
Access Switch 2
Router Configuration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
OVERVIEW OF INTERNETWORKING
DHCP Configuration
Access Point, Server configuration Guidelines
The problem guideline has been associated with stating the fact that the network would be designed in
such a way that there is a presence of separate subnet that is to be used by the guest users in an easy
way in order to access the FTP server only. When the design is to be made certain assumptions are to be
made and this assumptions mainly includes the following:
All the users that is the 50 daily user and the 10 guest user should be staying in the same
building of the primary school.
Despite of staying in the same building the user might be staying in different sections of the
building like different rooms, or different chambers or in different floor.
Besides this is also to be assumed that the network would be associated with the usage of the
high end internet connection which is to be provided by the internet service provider which is to
be selected by the organization. Due to this reason it is very much essential to select the
appropriate service provider.
The new network that is to be created should be associated with the usage of the Dynamic IP
addressing. Which means that in the network there should exists proxy server or a DHCP or
Dynamic Hybrid Configuration Protocol for the users along with the internet connection that is
to be used by the network. Besides this various servers should also be present in the various
sections of the building.
Along with this in the problem statement there is nothing mentioned about the wireless LAN,
and due to this reason the implementation of the new network no focus is put upon the wireless
connections and there is only an need of having a focus upon the wired connections only.
OVERVIEW OF INTERNETWORKING
DHCP Configuration
Access Point, Server configuration Guidelines
The problem guideline has been associated with stating the fact that the network would be designed in
such a way that there is a presence of separate subnet that is to be used by the guest users in an easy
way in order to access the FTP server only. When the design is to be made certain assumptions are to be
made and this assumptions mainly includes the following:
All the users that is the 50 daily user and the 10 guest user should be staying in the same
building of the primary school.
Despite of staying in the same building the user might be staying in different sections of the
building like different rooms, or different chambers or in different floor.
Besides this is also to be assumed that the network would be associated with the usage of the
high end internet connection which is to be provided by the internet service provider which is to
be selected by the organization. Due to this reason it is very much essential to select the
appropriate service provider.
The new network that is to be created should be associated with the usage of the Dynamic IP
addressing. Which means that in the network there should exists proxy server or a DHCP or
Dynamic Hybrid Configuration Protocol for the users along with the internet connection that is
to be used by the network. Besides this various servers should also be present in the various
sections of the building.
Along with this in the problem statement there is nothing mentioned about the wireless LAN,
and due to this reason the implementation of the new network no focus is put upon the wireless
connections and there is only an need of having a focus upon the wired connections only.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
OVERVIEW OF INTERNETWORKING
This implementation of the new network would be configured according to the needs of the
organization.
Security Configurations
Conclusion
The report is prepared for a primary school for designing its network with a guest network, for designing
the network solution the main requirement of the school is analyzed and the IP subnet plan is created
according to it. Different subnet and different VLAN is used for the guest, the school LAN and the server
network such that the guests can be blocked from accessing the PCs connected in the local area network
of the school. The report consists of the project scope, and the project requirement used for the
identification of the network device that are essential for the development of the network framework.
The IP addressing table is created by dividing the network into three subnets and the configuration
commands used or the configuration of the switch, router and the PC are attached with the report. The
design of the network is created following the human factors and the user centric design concepts and
dividing the network design into three layers such as core, access and distribution. For securing the
network the core switch is configured with access control list such that the guest network can be
blocked to access the PC connected in the vlan 20.
OVERVIEW OF INTERNETWORKING
This implementation of the new network would be configured according to the needs of the
organization.
Security Configurations
Conclusion
The report is prepared for a primary school for designing its network with a guest network, for designing
the network solution the main requirement of the school is analyzed and the IP subnet plan is created
according to it. Different subnet and different VLAN is used for the guest, the school LAN and the server
network such that the guests can be blocked from accessing the PCs connected in the local area network
of the school. The report consists of the project scope, and the project requirement used for the
identification of the network device that are essential for the development of the network framework.
The IP addressing table is created by dividing the network into three subnets and the configuration
commands used or the configuration of the switch, router and the PC are attached with the report. The
design of the network is created following the human factors and the user centric design concepts and
dividing the network design into three layers such as core, access and distribution. For securing the
network the core switch is configured with access control list such that the guest network can be
blocked to access the PC connected in the vlan 20.

8
OVERVIEW OF INTERNETWORKING
Bibliography
[1]. Bartram, A., El-Bizri, N. and Gittens, D. Introduction. In Recto Verso: Redefining the
Sketchbook (pp. 23-32). Routledge., 2016.
[2]. Ding, Z., Zhong, C., Ng, D.W.K., Peng, M., Suraweera, H.A., Schober, R. and Poor, H.V. Application
of smart antenna technologies in simultaneous wireless information and power transfer. IEEE
Communications Magazine, 53(4), pp.86-93., 2015.
[3]. Huh, J.H., Otgonchimeg, S. and Seo, K. Advanced metering infrastructure design and test bed
experiment using intelligent agents: focusing on the PLC network base technology for Smart Grid
system. The Journal of Supercomputing, 72(5), pp.1862-1877., 2016.
[4]. Jurado, F. and Rodriguez, P. Sentiment Analysis in monitoring software development processes:
An exploratory case study on GitHub's project issues. Journal of Systems and Software, 104,
pp.82-89., 2015.
[5]. Marchetti, M., Pierazzi, F., Colajanni, M. and Guido, A. Analysis of high volumes of network
traffic for Advanced Persistent Threat detection. Computer Networks, 109, pp.127-141., 2016.
[6]. McCormack, K.P. and Johnson, W.C. Supply chain networks and business process orientation:
advanced strategies and best practices. CRC Press., 2016.
[7]. Sandhu, R., Gill, H.K. and Sood, S.K. Smart monitoring and controlling of Pandemic Influenza A
(H1N1) using Social Network Analysis and cloud computing. Journal of Computational
Science, 12, pp.11-22., 2016.
[8]. Simmons, J.M. Optical network design and planning. Springer., 2014.
OVERVIEW OF INTERNETWORKING
Bibliography
[1]. Bartram, A., El-Bizri, N. and Gittens, D. Introduction. In Recto Verso: Redefining the
Sketchbook (pp. 23-32). Routledge., 2016.
[2]. Ding, Z., Zhong, C., Ng, D.W.K., Peng, M., Suraweera, H.A., Schober, R. and Poor, H.V. Application
of smart antenna technologies in simultaneous wireless information and power transfer. IEEE
Communications Magazine, 53(4), pp.86-93., 2015.
[3]. Huh, J.H., Otgonchimeg, S. and Seo, K. Advanced metering infrastructure design and test bed
experiment using intelligent agents: focusing on the PLC network base technology for Smart Grid
system. The Journal of Supercomputing, 72(5), pp.1862-1877., 2016.
[4]. Jurado, F. and Rodriguez, P. Sentiment Analysis in monitoring software development processes:
An exploratory case study on GitHub's project issues. Journal of Systems and Software, 104,
pp.82-89., 2015.
[5]. Marchetti, M., Pierazzi, F., Colajanni, M. and Guido, A. Analysis of high volumes of network
traffic for Advanced Persistent Threat detection. Computer Networks, 109, pp.127-141., 2016.
[6]. McCormack, K.P. and Johnson, W.C. Supply chain networks and business process orientation:
advanced strategies and best practices. CRC Press., 2016.
[7]. Sandhu, R., Gill, H.K. and Sood, S.K. Smart monitoring and controlling of Pandemic Influenza A
(H1N1) using Social Network Analysis and cloud computing. Journal of Computational
Science, 12, pp.11-22., 2016.
[8]. Simmons, J.M. Optical network design and planning. Springer., 2014.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



