MN503 Internetworking: Primary School Network Design with Guest LAN
VerifiedAdded on 2023/06/11
|9
|1447
|349
Report
AI Summary
This report outlines the design of a computer network for a primary school, accommodating both internal and guest users. The network incorporates an FTP server accessible only to guest users via a separate LAN, while daily users have full network access through another LAN. The design emphasizes security by restricting guest user access to sensitive information. Key components include switches, routers configured for network distribution, and DHCP for IP address assignment. The report also covers subnet creation for guest users, access point considerations, and security configurations to ensure controlled access. The analysis includes project scope, requirements, IP addressing, and network topology, concluding with the importance of proper planning and configuration for a secure and efficient network.

Running head: OVERVIEW OF INTERNETWORKING
Overview of Internetworking
Name of the Student
Name of the University
Author’s Note
Overview of Internetworking
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
OVERVIEW OF INTERNETWORKING
Table of Contents
1. Project Scope:..........................................................................................................................................2
2. Project requirements:..............................................................................................................................2
3. Network Design.......................................................................................................................................3
4. IP Addresses Table...................................................................................................................................3
5. Network Topology Diagram.....................................................................................................................4
5.1. Switch Configuration........................................................................................................................4
5.2. Router Configuration........................................................................................................................5
5.3. DHCP Configuration..........................................................................................................................6
5.4. Access Point......................................................................................................................................6
5.5. Security Configuration......................................................................................................................7
6. Conclusion...............................................................................................................................................7
Bibliography................................................................................................................................................8
OVERVIEW OF INTERNETWORKING
Table of Contents
1. Project Scope:..........................................................................................................................................2
2. Project requirements:..............................................................................................................................2
3. Network Design.......................................................................................................................................3
4. IP Addresses Table...................................................................................................................................3
5. Network Topology Diagram.....................................................................................................................4
5.1. Switch Configuration........................................................................................................................4
5.2. Router Configuration........................................................................................................................5
5.3. DHCP Configuration..........................................................................................................................6
5.4. Access Point......................................................................................................................................6
5.5. Security Configuration......................................................................................................................7
6. Conclusion...............................................................................................................................................7
Bibliography................................................................................................................................................8

2
OVERVIEW OF INTERNETWORKING
1. Project Scope:
In this project scope it generally discusses about the creation of a network which is to be used by a
primary school that is consisting of both internal user as well as guest users. The number of daily user is
around 50 which is more than the number of guest users that is around 10. The main scope of the
mainly includes creation of a restricted network for the guest users where they would be capable of
accessing the FTP server only whereas the daily users would be provided the full access of the system.
Besides this the FTP server would be used by the guest users only for the purpose of getting a limited
amount of access to the network.
2. Project requirements:
The network that is to be created requires the following:
The network shout consist f a FTP server that would be accessed by the guest users only in order
to use certain files or for the purpose of accessing a limited part of the network. For that a
separate LAN would be created which would be only used by the guests.
Besides the LAN for the guest users, another LAN is to be created that would be used by the
daily users in order to get a full access of the network and this LAN would not be used by the
guest user as they would be blocked from using the information that are present in the network
of the daily user.
Besides this some other kinds of servers are also to be included in the network that is to be used
by the users and the guest for the purpose of conducting their various works.
Blocking of the guest users from the actual network would be very much helpful in the process
of securing the sensitive information.
Network components like the switches and routers are also be used which would be mainly
responsible for the distribution of the network and would also be configured accordingly to
provide access to the users and restricted access to the guest users that is only to the FTP
server.
The network would also be consisting a separate subnet for the guest users which would be
associated with making the guest user capable of accessing the FTP server only and not to any
other section of the network from where the guest users would be blocked.
OVERVIEW OF INTERNETWORKING
1. Project Scope:
In this project scope it generally discusses about the creation of a network which is to be used by a
primary school that is consisting of both internal user as well as guest users. The number of daily user is
around 50 which is more than the number of guest users that is around 10. The main scope of the
mainly includes creation of a restricted network for the guest users where they would be capable of
accessing the FTP server only whereas the daily users would be provided the full access of the system.
Besides this the FTP server would be used by the guest users only for the purpose of getting a limited
amount of access to the network.
2. Project requirements:
The network that is to be created requires the following:
The network shout consist f a FTP server that would be accessed by the guest users only in order
to use certain files or for the purpose of accessing a limited part of the network. For that a
separate LAN would be created which would be only used by the guests.
Besides the LAN for the guest users, another LAN is to be created that would be used by the
daily users in order to get a full access of the network and this LAN would not be used by the
guest user as they would be blocked from using the information that are present in the network
of the daily user.
Besides this some other kinds of servers are also to be included in the network that is to be used
by the users and the guest for the purpose of conducting their various works.
Blocking of the guest users from the actual network would be very much helpful in the process
of securing the sensitive information.
Network components like the switches and routers are also be used which would be mainly
responsible for the distribution of the network and would also be configured accordingly to
provide access to the users and restricted access to the guest users that is only to the FTP
server.
The network would also be consisting a separate subnet for the guest users which would be
associated with making the guest user capable of accessing the FTP server only and not to any
other section of the network from where the guest users would be blocked.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
OVERVIEW OF INTERNETWORKING
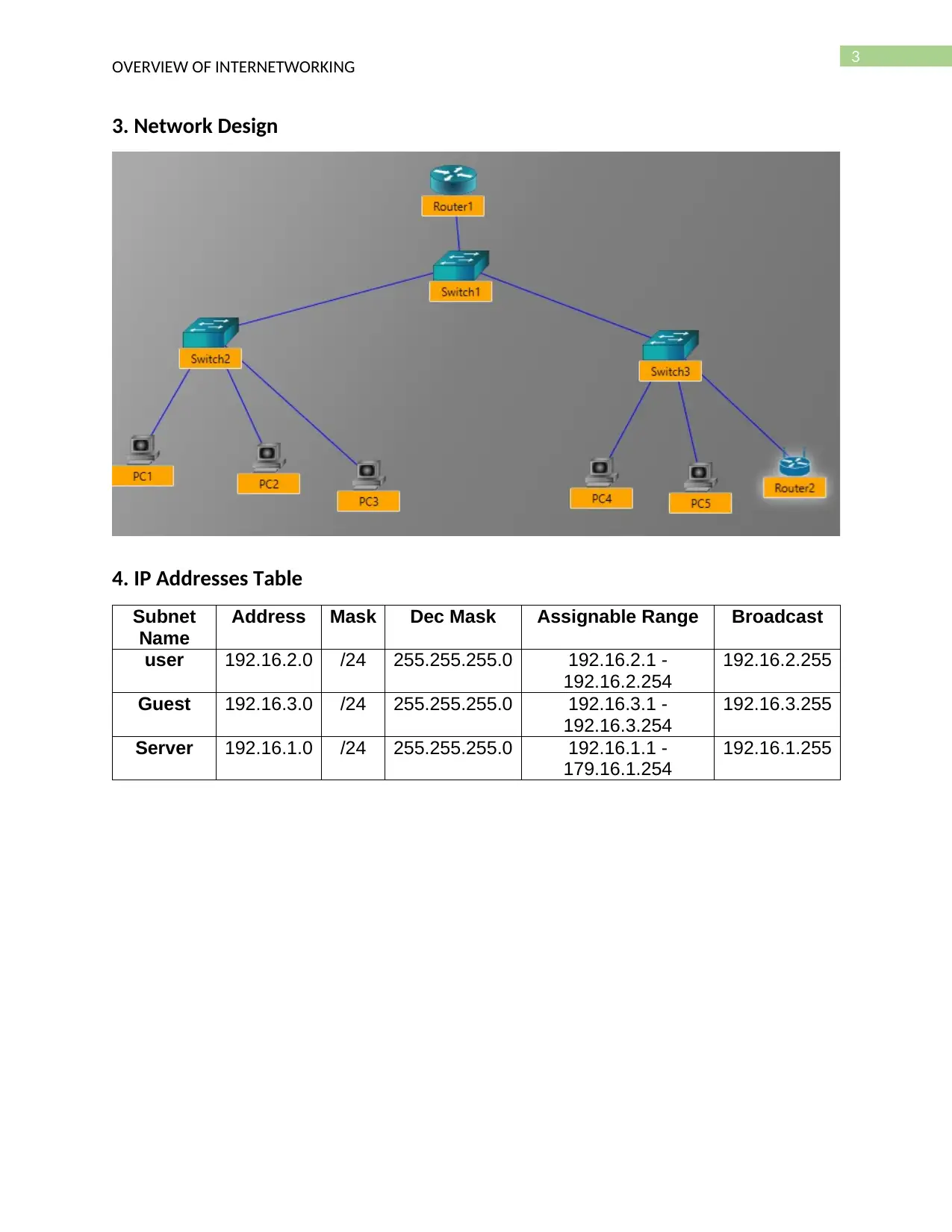
3. Network Design
4. IP Addresses Table
Subnet
Name
Address Mask Dec Mask Assignable Range Broadcast
user 192.16.2.0 /24 255.255.255.0 192.16.2.1 -
192.16.2.254
192.16.2.255
Guest 192.16.3.0 /24 255.255.255.0 192.16.3.1 -
192.16.3.254
192.16.3.255
Server 192.16.1.0 /24 255.255.255.0 192.16.1.1 -
179.16.1.254
192.16.1.255
OVERVIEW OF INTERNETWORKING
3. Network Design
4. IP Addresses Table
Subnet
Name
Address Mask Dec Mask Assignable Range Broadcast
user 192.16.2.0 /24 255.255.255.0 192.16.2.1 -
192.16.2.254
192.16.2.255
Guest 192.16.3.0 /24 255.255.255.0 192.16.3.1 -
192.16.3.254
192.16.3.255
Server 192.16.1.0 /24 255.255.255.0 192.16.1.1 -
179.16.1.254
192.16.1.255
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
OVERVIEW OF INTERNETWORKING
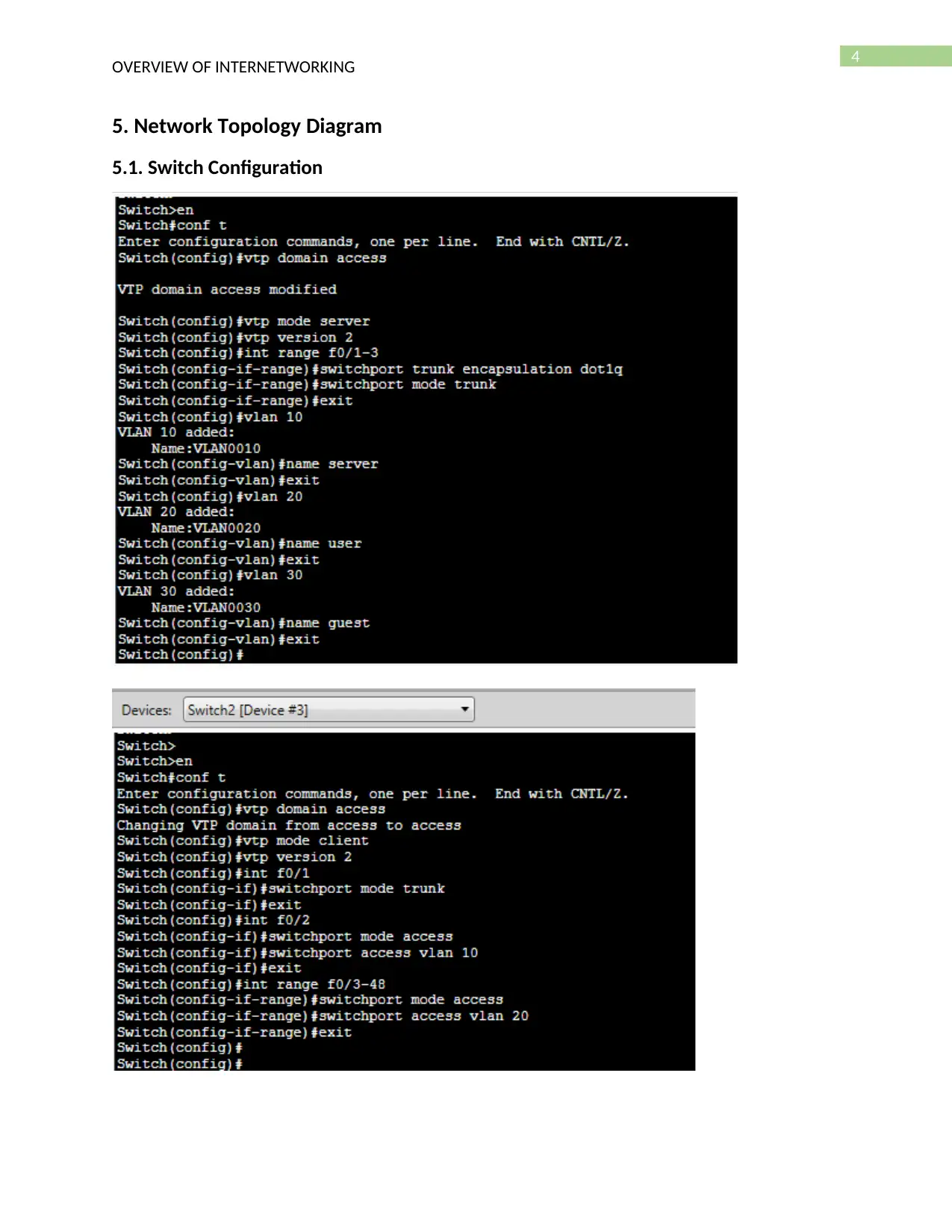
5. Network Topology Diagram
5.1. Switch Configuration
OVERVIEW OF INTERNETWORKING
5. Network Topology Diagram
5.1. Switch Configuration
5
OVERVIEW OF INTERNETWORKING
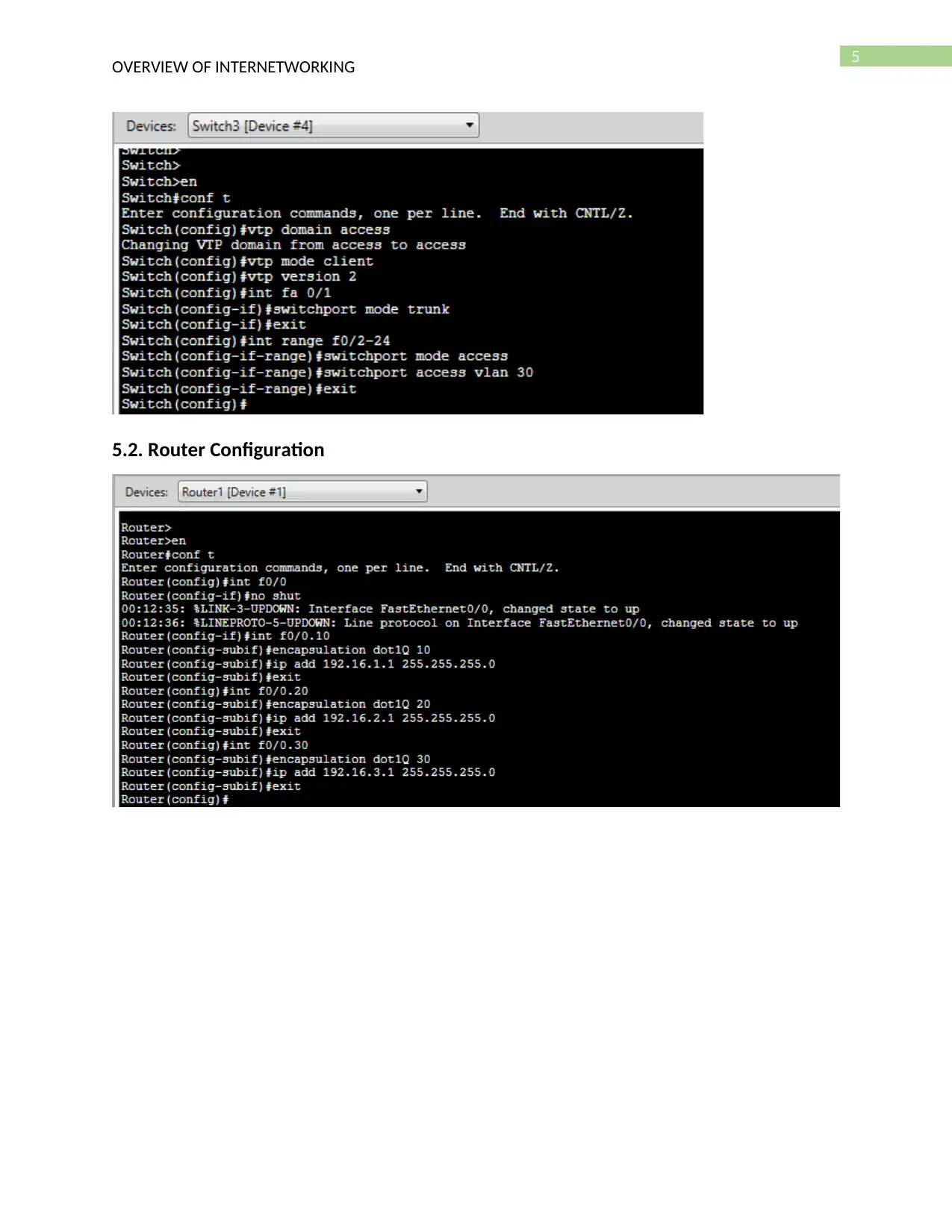
5.2. Router Configuration
OVERVIEW OF INTERNETWORKING
5.2. Router Configuration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
OVERVIEW OF INTERNETWORKING
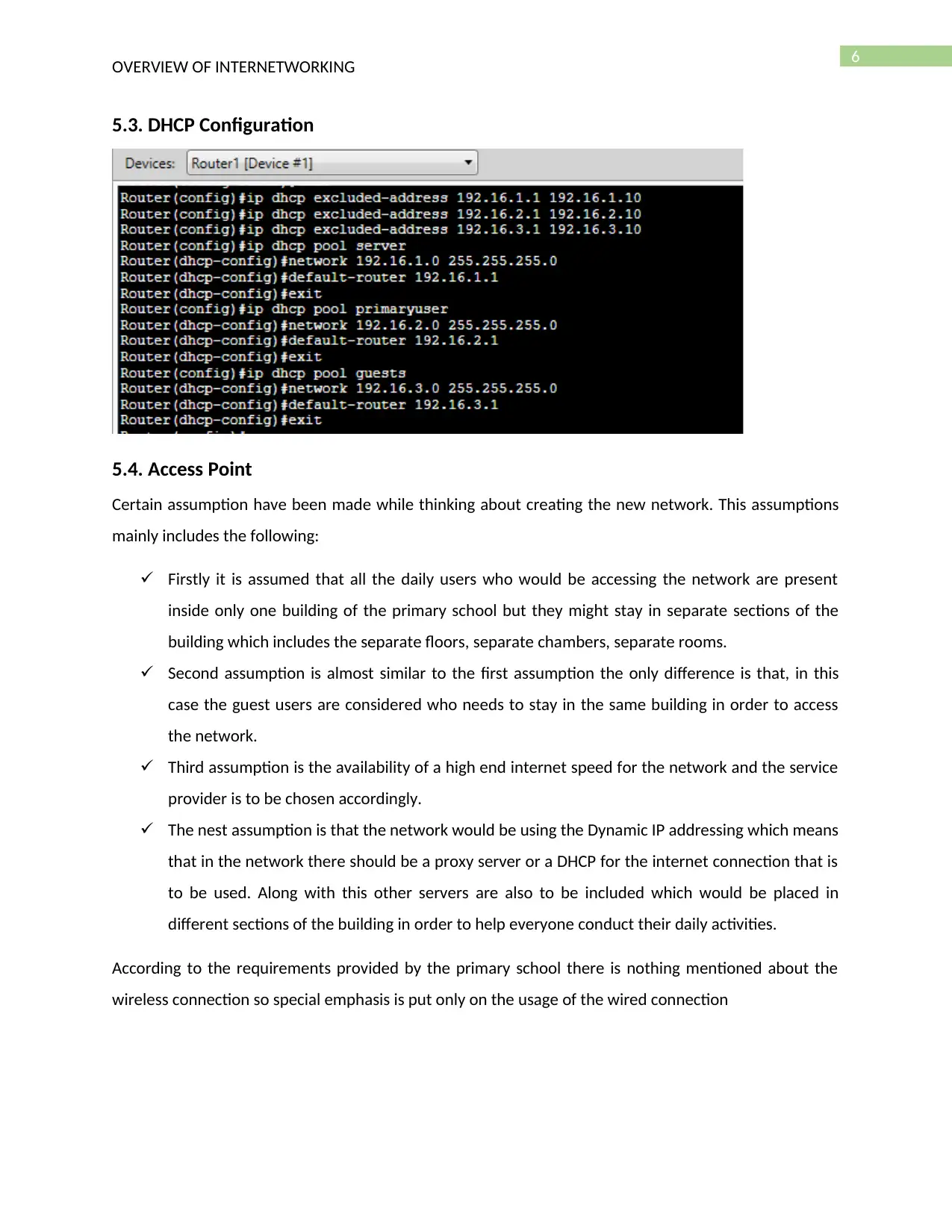
5.3. DHCP Configuration
5.4. Access Point
Certain assumption have been made while thinking about creating the new network. This assumptions
mainly includes the following:
Firstly it is assumed that all the daily users who would be accessing the network are present
inside only one building of the primary school but they might stay in separate sections of the
building which includes the separate floors, separate chambers, separate rooms.
Second assumption is almost similar to the first assumption the only difference is that, in this
case the guest users are considered who needs to stay in the same building in order to access
the network.
Third assumption is the availability of a high end internet speed for the network and the service
provider is to be chosen accordingly.
The nest assumption is that the network would be using the Dynamic IP addressing which means
that in the network there should be a proxy server or a DHCP for the internet connection that is
to be used. Along with this other servers are also to be included which would be placed in
different sections of the building in order to help everyone conduct their daily activities.
According to the requirements provided by the primary school there is nothing mentioned about the
wireless connection so special emphasis is put only on the usage of the wired connection
OVERVIEW OF INTERNETWORKING
5.3. DHCP Configuration
5.4. Access Point
Certain assumption have been made while thinking about creating the new network. This assumptions
mainly includes the following:
Firstly it is assumed that all the daily users who would be accessing the network are present
inside only one building of the primary school but they might stay in separate sections of the
building which includes the separate floors, separate chambers, separate rooms.
Second assumption is almost similar to the first assumption the only difference is that, in this
case the guest users are considered who needs to stay in the same building in order to access
the network.
Third assumption is the availability of a high end internet speed for the network and the service
provider is to be chosen accordingly.
The nest assumption is that the network would be using the Dynamic IP addressing which means
that in the network there should be a proxy server or a DHCP for the internet connection that is
to be used. Along with this other servers are also to be included which would be placed in
different sections of the building in order to help everyone conduct their daily activities.
According to the requirements provided by the primary school there is nothing mentioned about the
wireless connection so special emphasis is put only on the usage of the wired connection
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
OVERVIEW OF INTERNETWORKING
5.5. Security Configuration
6. Conclusion
From the above report it can be conclude the analysis of the scope and the requirement of the project is
essential for the configuration of the primary school network. The identification of the requirement
helps in identifying the network hardware needs and the protocols required for the configuration of the
network. The IP addresses that are required for the configuration of the interfaces of the VLAN and the
Ethernet cards should be listed. The router should be configured with DHCP configuration such that the
PC connected with each of the interface should be automatically assigned with the IP address. The inter-
vlan routing should also be done such that the different users connected in the network should be able
to send and receive data packets in the network. The configuration of the access control list should be
used for meeting the business rules of the school and restricting the guest to communicate with the
primary user vlan.
OVERVIEW OF INTERNETWORKING
5.5. Security Configuration
6. Conclusion
From the above report it can be conclude the analysis of the scope and the requirement of the project is
essential for the configuration of the primary school network. The identification of the requirement
helps in identifying the network hardware needs and the protocols required for the configuration of the
network. The IP addresses that are required for the configuration of the interfaces of the VLAN and the
Ethernet cards should be listed. The router should be configured with DHCP configuration such that the
PC connected with each of the interface should be automatically assigned with the IP address. The inter-
vlan routing should also be done such that the different users connected in the network should be able
to send and receive data packets in the network. The configuration of the access control list should be
used for meeting the business rules of the school and restricting the guest to communicate with the
primary user vlan.

8
OVERVIEW OF INTERNETWORKING
Bibliography
[1]. Atwater, E., Bocovich, C., Hengartner, U. and Goldberg, I. Live Lesson: Netsim: Network
simulation and hacking for high schoolers. In 2017 {USENIX} Workshop on Advances in Security
Education ({ASE} 17). USENIX} Association}., 2017 August.
[2]. Benton, A., Arora, R. and Dredze, M. Learning multiview embeddings of twitter users.
In Proceedings of the 54th Annual Meeting of the Association for Computational Linguistics
(Volume 2: Short Papers) (Vol. 2, pp. 14-19)., 2016.
[3]. Cuppens, F. WirelessHART NetSIM: A WirelessHART SCADA-Based Wireless Sensor Networks
Simulator. In Security of Industrial Control Systems and Cyber Physical Systems: First Workshop,
CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September 21–22, 2015
Revised Selected Papers (Vol. 9588, p. 63). Springer., 2016, June.
[4]. Nayak, P. and Sinha, P. Analysis of Random Way Point and Random Walk Mobility Model for
Reactive Routing Protocols for MANET Using NetSim Simulator. In Artificial Intelligence,
Modelling and Simulation (AIMS), 2015 3rd International Conference on (pp. 427-432). IEEE.,
2015 December.
[5]. Peng, J., Li, H., Wang, Y. and Chen, J. A web tool for measuring gene semantic similarities by
combining Gene Ontology and gene co-function networks. In Proceedings of the 6th ACM
Conference on Bioinformatics, Computational Biology and Health Informatics (pp. 678-679).
ACM., 2015 September.
[6]. Saifuddin, K.M., Ahmed, A.S., Reza, K.F., Alam, S.S. and Rahman, S. Performance analysis of
cognitive radio: Netsim viewpoint. In Electrical Information and Communication Technology
(EICT), 2017 3rd International Conference on (pp. 1-6). IEEE., 2017 December.
[7]. Singh, G. and Singh, H. Performance Evaluation of MANET Routing Protocols using NETSIM. i-
Manager's Journal on Information Technology, 6(1), p.8., 2016.
[8]. Singh, G., Cheema, A.K. and Kapoor, N. Performance Evaluation of Routing Protocol in Internet
of Things using Netsim. International Journal, 8(3)., 2017.
OVERVIEW OF INTERNETWORKING
Bibliography
[1]. Atwater, E., Bocovich, C., Hengartner, U. and Goldberg, I. Live Lesson: Netsim: Network
simulation and hacking for high schoolers. In 2017 {USENIX} Workshop on Advances in Security
Education ({ASE} 17). USENIX} Association}., 2017 August.
[2]. Benton, A., Arora, R. and Dredze, M. Learning multiview embeddings of twitter users.
In Proceedings of the 54th Annual Meeting of the Association for Computational Linguistics
(Volume 2: Short Papers) (Vol. 2, pp. 14-19)., 2016.
[3]. Cuppens, F. WirelessHART NetSIM: A WirelessHART SCADA-Based Wireless Sensor Networks
Simulator. In Security of Industrial Control Systems and Cyber Physical Systems: First Workshop,
CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September 21–22, 2015
Revised Selected Papers (Vol. 9588, p. 63). Springer., 2016, June.
[4]. Nayak, P. and Sinha, P. Analysis of Random Way Point and Random Walk Mobility Model for
Reactive Routing Protocols for MANET Using NetSim Simulator. In Artificial Intelligence,
Modelling and Simulation (AIMS), 2015 3rd International Conference on (pp. 427-432). IEEE.,
2015 December.
[5]. Peng, J., Li, H., Wang, Y. and Chen, J. A web tool for measuring gene semantic similarities by
combining Gene Ontology and gene co-function networks. In Proceedings of the 6th ACM
Conference on Bioinformatics, Computational Biology and Health Informatics (pp. 678-679).
ACM., 2015 September.
[6]. Saifuddin, K.M., Ahmed, A.S., Reza, K.F., Alam, S.S. and Rahman, S. Performance analysis of
cognitive radio: Netsim viewpoint. In Electrical Information and Communication Technology
(EICT), 2017 3rd International Conference on (pp. 1-6). IEEE., 2017 December.
[7]. Singh, G. and Singh, H. Performance Evaluation of MANET Routing Protocols using NETSIM. i-
Manager's Journal on Information Technology, 6(1), p.8., 2016.
[8]. Singh, G., Cheema, A.K. and Kapoor, N. Performance Evaluation of Routing Protocol in Internet
of Things using Netsim. International Journal, 8(3)., 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


