Local Area Network Implementation for Windows Server - MN506 Report
VerifiedAdded on 2023/03/21
|32
|3011
|99
Report
AI Summary
This report details the implementation of a local area network (LAN) designed to support a Windows Server and client environment. It includes a requirement analysis, configuration process description, IP addressing plan, and configuration screenshots. The report covers centralized user authentication, print server configuration, DHCP server configuration, IIS configuration for hosting a website, and file server configuration. It also provides an active directory domain structure diagram. The design prioritizes scalability and security, incorporating subnets for data protection and VLANs for network traffic management. The report concludes with recommendations for maintaining network security and enhancing organizational efficiency through remote access and firewall integration. Desklib provides access to this and similar solved assignments for students.

Local Area Network (LAN) to support Windows Server and Client
Environment
Name of the Student
Name of the University
Author’s Note
Environment
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction...........................................................................................................................................2
Requirement analysis............................................................................................................................2
Configuring process description............................................................................................................3
IP Addressing Plan.............................................................................................................................3
Configuration Screenshots or commands..............................................................................................5
Centralised user authentication........................................................................................................5
Print server configuration..................................................................................................................5
DHCP server configuration...............................................................................................................10
IIS configuration for hosting own website.......................................................................................19
File server configuration..................................................................................................................21
Active Directory Domain Structure Diagram....................................................................................27
Summary.............................................................................................................................................28
Conclusions..........................................................................................................................................29
Bibliography.........................................................................................................................................30
Introduction...........................................................................................................................................2
Requirement analysis............................................................................................................................2
Configuring process description............................................................................................................3
IP Addressing Plan.............................................................................................................................3
Configuration Screenshots or commands..............................................................................................5
Centralised user authentication........................................................................................................5
Print server configuration..................................................................................................................5
DHCP server configuration...............................................................................................................10
IIS configuration for hosting own website.......................................................................................19
File server configuration..................................................................................................................21
Active Directory Domain Structure Diagram....................................................................................27
Summary.............................................................................................................................................28
Conclusions..........................................................................................................................................29
Bibliography.........................................................................................................................................30

Introduction
The report, which is prepared for thinktank, is aimed at providing a detailed implementation guide
for setting up a network for the client side as well as supporting Windows server. This network is
designed on local area network Technology. According to the requirement of the organization, this
Network Support present needs of the organizations while allocating various users. Not only that this
network should be scalable enough so that it provides support to future users whenever there is a
need to allocate more users than the organization presently needs to manage. Analysis has been
made for the existing organizational network to identify the infrastructure so that the network is
designed in an appropriate way while providing the benefits of the network according to the
organizational requirements. All configuration that will be considered for this network has been
discussed in details in this report. Along with those relevant commands that will be considered for
design, the network has also been included in the report and this has been followed by proper
screenshots so that it is easier to review the network configuration as well as the proposed design in
this context.
Requirement analysis
In order to identify the requirements in an appropriate way and define those requirements for the
network design, it is important to involve serious users at a different level based on their roles and
interest in this project. This analysis for the network requirements is essential to identify various
errors that might be associated with the network design. If these errors are not identified during the
planning of the network design it will be difficult to modify the issues during the design
implementation of the network. Requirement gathering and analysis has been done with proper
detailing of various errors that might be relevant in this network design. All the important
stakeholders of this project might be involved in this process so that it is easier to identify sensitive
information what level of protection this information should have and how the organization is
thinking to define access to that information. This information is very essential in designing the
network because this network should support client service, therefore, it is extremely important to
protect the information from illegal access. In this context, separate subnets will be considered for
the network design, as it will help to deny any request to access sensitive data if the user is not
authenticated and does not have the required permission for accessing the data. The IP address that
will be assigned to various clients will be integrated into similar Local area network or LAN.
The report, which is prepared for thinktank, is aimed at providing a detailed implementation guide
for setting up a network for the client side as well as supporting Windows server. This network is
designed on local area network Technology. According to the requirement of the organization, this
Network Support present needs of the organizations while allocating various users. Not only that this
network should be scalable enough so that it provides support to future users whenever there is a
need to allocate more users than the organization presently needs to manage. Analysis has been
made for the existing organizational network to identify the infrastructure so that the network is
designed in an appropriate way while providing the benefits of the network according to the
organizational requirements. All configuration that will be considered for this network has been
discussed in details in this report. Along with those relevant commands that will be considered for
design, the network has also been included in the report and this has been followed by proper
screenshots so that it is easier to review the network configuration as well as the proposed design in
this context.
Requirement analysis
In order to identify the requirements in an appropriate way and define those requirements for the
network design, it is important to involve serious users at a different level based on their roles and
interest in this project. This analysis for the network requirements is essential to identify various
errors that might be associated with the network design. If these errors are not identified during the
planning of the network design it will be difficult to modify the issues during the design
implementation of the network. Requirement gathering and analysis has been done with proper
detailing of various errors that might be relevant in this network design. All the important
stakeholders of this project might be involved in this process so that it is easier to identify sensitive
information what level of protection this information should have and how the organization is
thinking to define access to that information. This information is very essential in designing the
network because this network should support client service, therefore, it is extremely important to
protect the information from illegal access. In this context, separate subnets will be considered for
the network design, as it will help to deny any request to access sensitive data if the user is not
authenticated and does not have the required permission for accessing the data. The IP address that
will be assigned to various clients will be integrated into similar Local area network or LAN.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
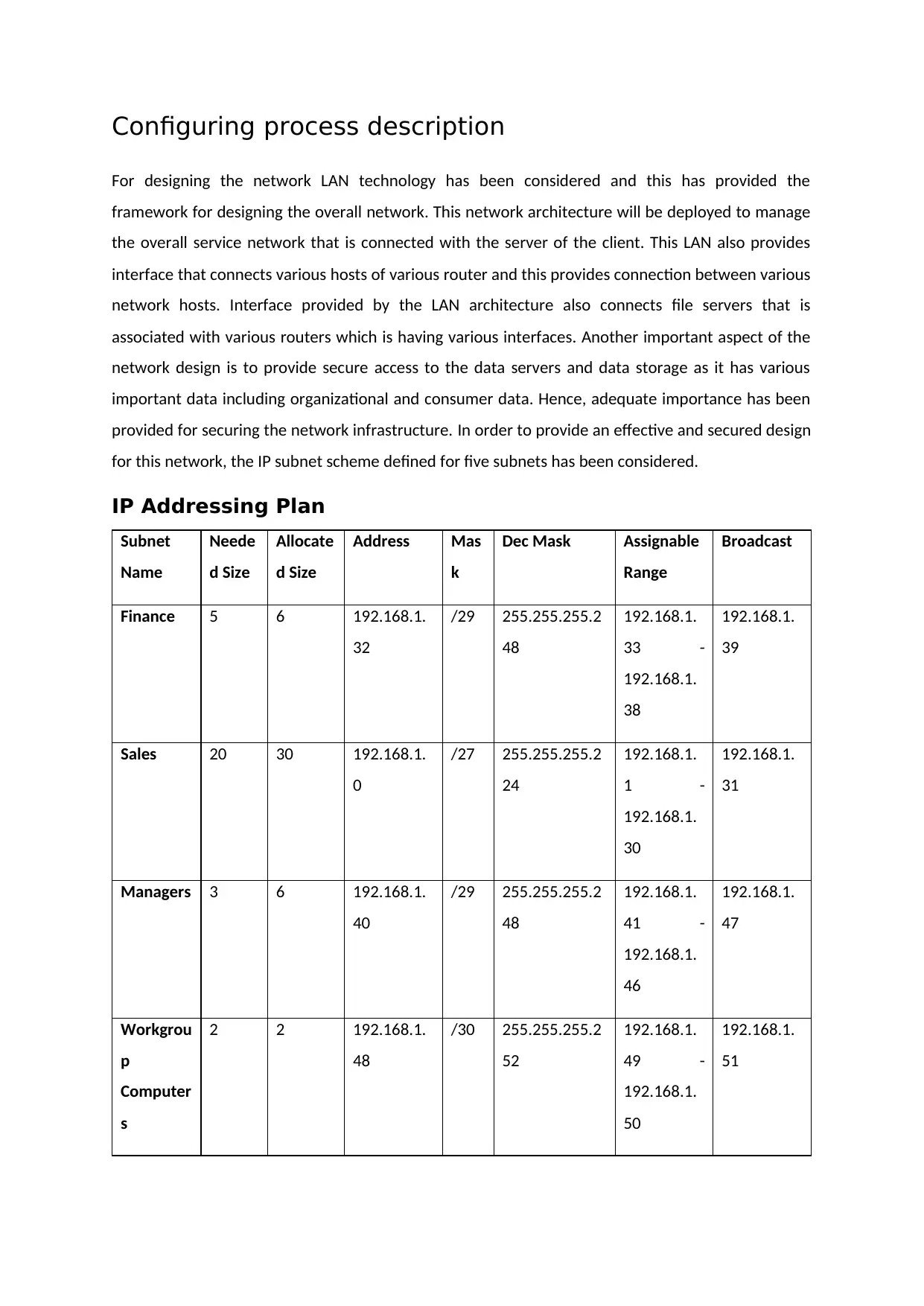
Configuring process description
For designing the network LAN technology has been considered and this has provided the
framework for designing the overall network. This network architecture will be deployed to manage
the overall service network that is connected with the server of the client. This LAN also provides
interface that connects various hosts of various router and this provides connection between various
network hosts. Interface provided by the LAN architecture also connects file servers that is
associated with various routers which is having various interfaces. Another important aspect of the
network design is to provide secure access to the data servers and data storage as it has various
important data including organizational and consumer data. Hence, adequate importance has been
provided for securing the network infrastructure. In order to provide an effective and secured design
for this network, the IP subnet scheme defined for five subnets has been considered.
IP Addressing Plan
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Finance 5 6 192.168.1.
32
/29 255.255.255.2
48
192.168.1.
33 -
192.168.1.
38
192.168.1.
39
Sales 20 30 192.168.1.
0
/27 255.255.255.2
24
192.168.1.
1 -
192.168.1.
30
192.168.1.
31
Managers 3 6 192.168.1.
40
/29 255.255.255.2
48
192.168.1.
41 -
192.168.1.
46
192.168.1.
47
Workgrou
p
Computer
s
2 2 192.168.1.
48
/30 255.255.255.2
52
192.168.1.
49 -
192.168.1.
50
192.168.1.
51
For designing the network LAN technology has been considered and this has provided the
framework for designing the overall network. This network architecture will be deployed to manage
the overall service network that is connected with the server of the client. This LAN also provides
interface that connects various hosts of various router and this provides connection between various
network hosts. Interface provided by the LAN architecture also connects file servers that is
associated with various routers which is having various interfaces. Another important aspect of the
network design is to provide secure access to the data servers and data storage as it has various
important data including organizational and consumer data. Hence, adequate importance has been
provided for securing the network infrastructure. In order to provide an effective and secured design
for this network, the IP subnet scheme defined for five subnets has been considered.
IP Addressing Plan
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Finance 5 6 192.168.1.
32
/29 255.255.255.2
48
192.168.1.
33 -
192.168.1.
38
192.168.1.
39
Sales 20 30 192.168.1.
0
/27 255.255.255.2
24
192.168.1.
1 -
192.168.1.
30
192.168.1.
31
Managers 3 6 192.168.1.
40
/29 255.255.255.2
48
192.168.1.
41 -
192.168.1.
46
192.168.1.
47
Workgrou
p
Computer
s
2 2 192.168.1.
48
/30 255.255.255.2
52
192.168.1.
49 -
192.168.1.
50
192.168.1.
51
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Centralised User Authentication – To ensue authentication for the network and define it for all the
central users of the network, windows server need to be configured with active directory. Domain
service needs to be integrated with other network services. Domain should be properly configured
and proper password should be assigned for every domain name so that it is easier for ensuring
security of various network resources.
Print servers for users – all of the features related to the printing are managed by the network
servers which provides print service. This service is provided by the network manager.
DHCP Configuration – Proper configuration design that is an important requirement for the
Windows Server is done with DHCP service Security group. This security group has been created for
DHCP server and it provides authorization. This is an important requirement for increasing network
security.
Hosting Own Website – Window server provides easy access to host the internal website. Services
like FTP services, WWW could also be implemented as well that is required for the internal website.
Description of OUs, Groups, Users and Access Levels - In order to ensure centralized access control
with accuracy, it is required to install RADIUS. Along with that, certificate of various software needs
to be encrypted with public key encryption technique and this will ensure security of the network.
Here in this context, DHCP service also plays an important role and this needs to be considered as
well. In order to configure various network servers through DHCP service, it is required to design
separate VLAN for all of the departments of the organization and integrate with DHCP service for
enhancing network security through effective control over the network.
File Server configuration –In order to allow various users to send and receive files, it is required to
configure the file servers of the network properly. Sever manager needs to configure file server with
the network and also provide access to network storage so that it is easier to store and receive files
over the network.
central users of the network, windows server need to be configured with active directory. Domain
service needs to be integrated with other network services. Domain should be properly configured
and proper password should be assigned for every domain name so that it is easier for ensuring
security of various network resources.
Print servers for users – all of the features related to the printing are managed by the network
servers which provides print service. This service is provided by the network manager.
DHCP Configuration – Proper configuration design that is an important requirement for the
Windows Server is done with DHCP service Security group. This security group has been created for
DHCP server and it provides authorization. This is an important requirement for increasing network
security.
Hosting Own Website – Window server provides easy access to host the internal website. Services
like FTP services, WWW could also be implemented as well that is required for the internal website.
Description of OUs, Groups, Users and Access Levels - In order to ensure centralized access control
with accuracy, it is required to install RADIUS. Along with that, certificate of various software needs
to be encrypted with public key encryption technique and this will ensure security of the network.
Here in this context, DHCP service also plays an important role and this needs to be considered as
well. In order to configure various network servers through DHCP service, it is required to design
separate VLAN for all of the departments of the organization and integrate with DHCP service for
enhancing network security through effective control over the network.
File Server configuration –In order to allow various users to send and receive files, it is required to
configure the file servers of the network properly. Sever manager needs to configure file server with
the network and also provide access to network storage so that it is easier to store and receive files
over the network.
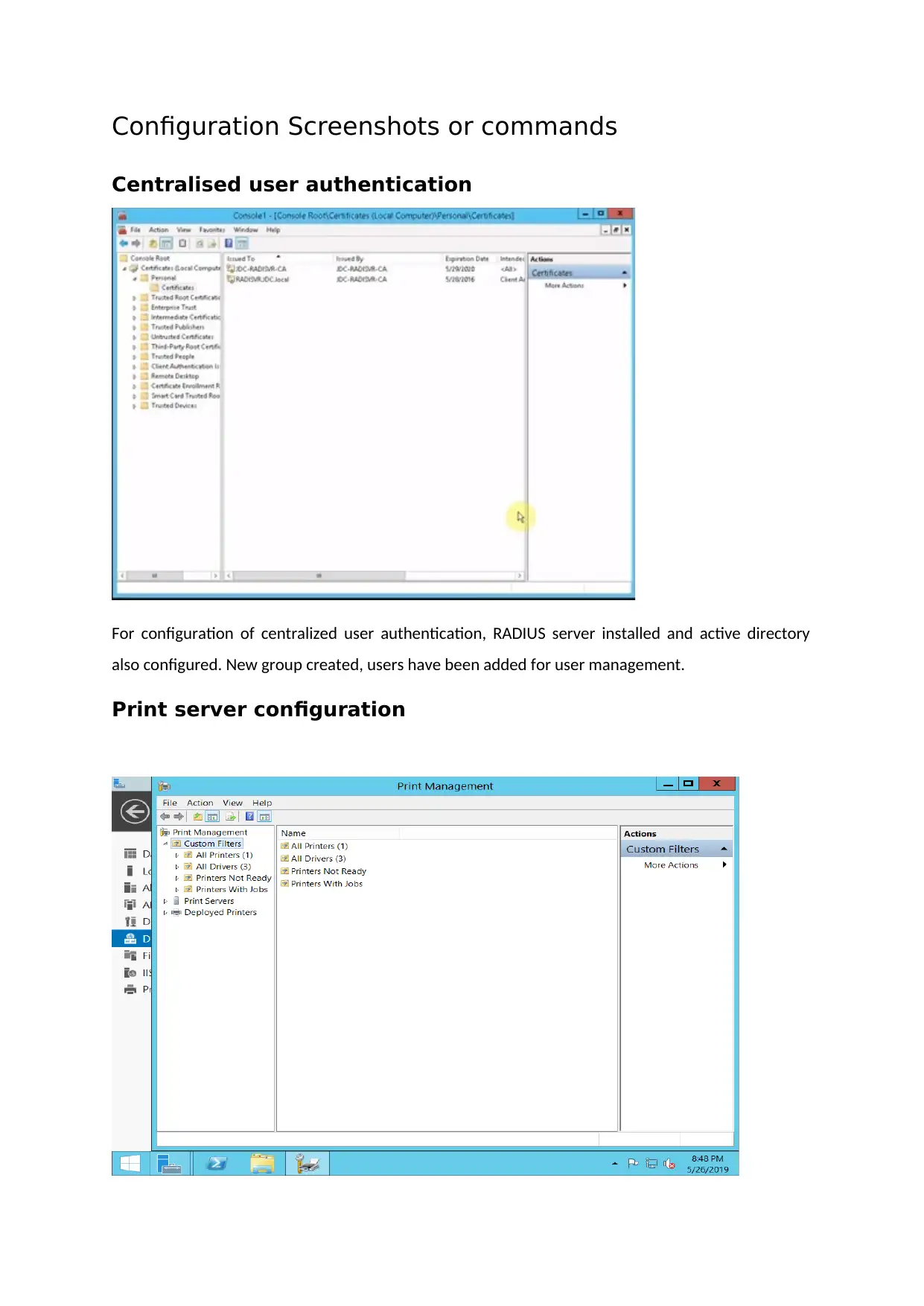
Configuration Screenshots or commands
Centralised user authentication
For configuration of centralized user authentication, RADIUS server installed and active directory
also configured. New group created, users have been added for user management.
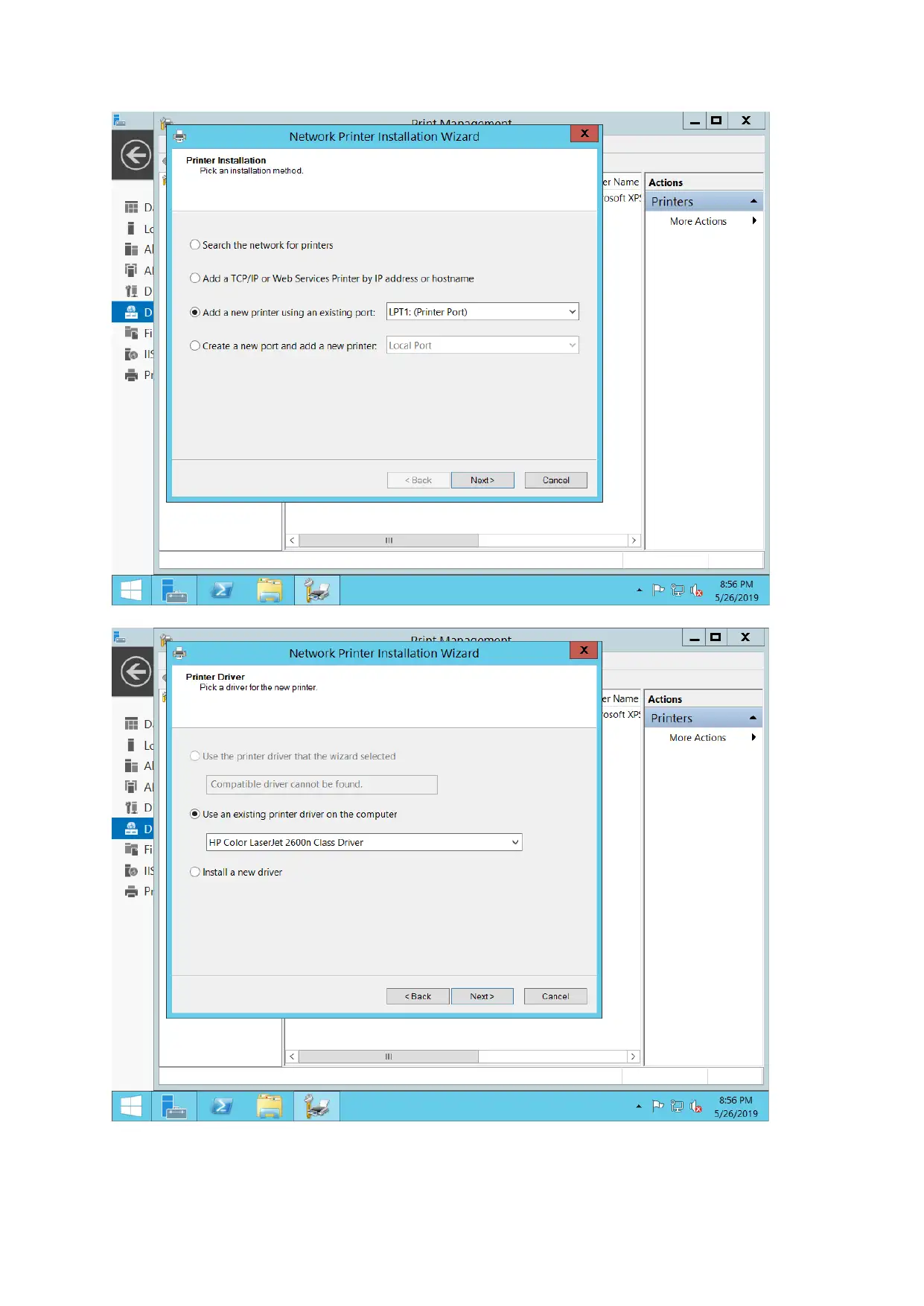
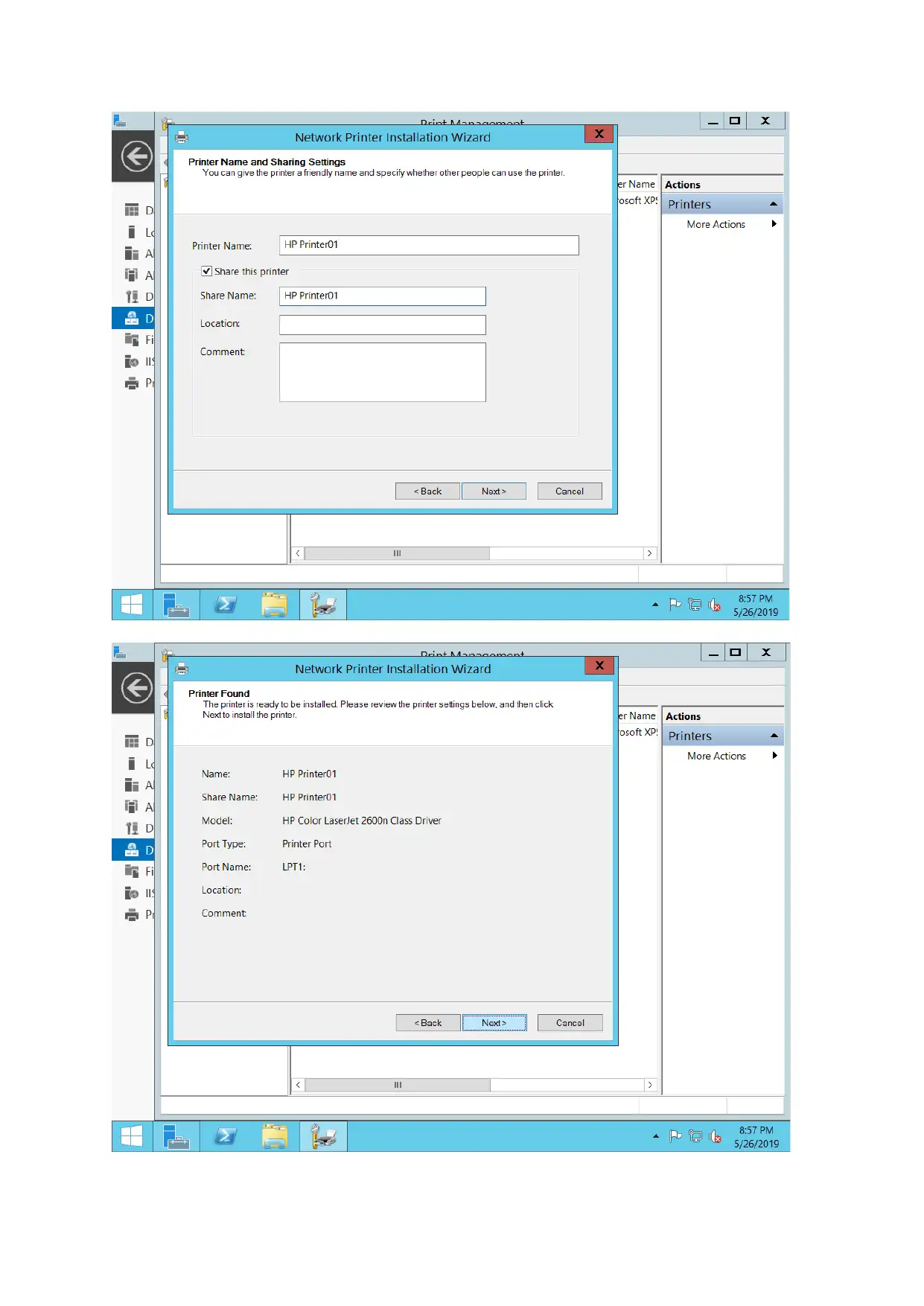
Print server configuration
Centralised user authentication
For configuration of centralized user authentication, RADIUS server installed and active directory
also configured. New group created, users have been added for user management.
Print server configuration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
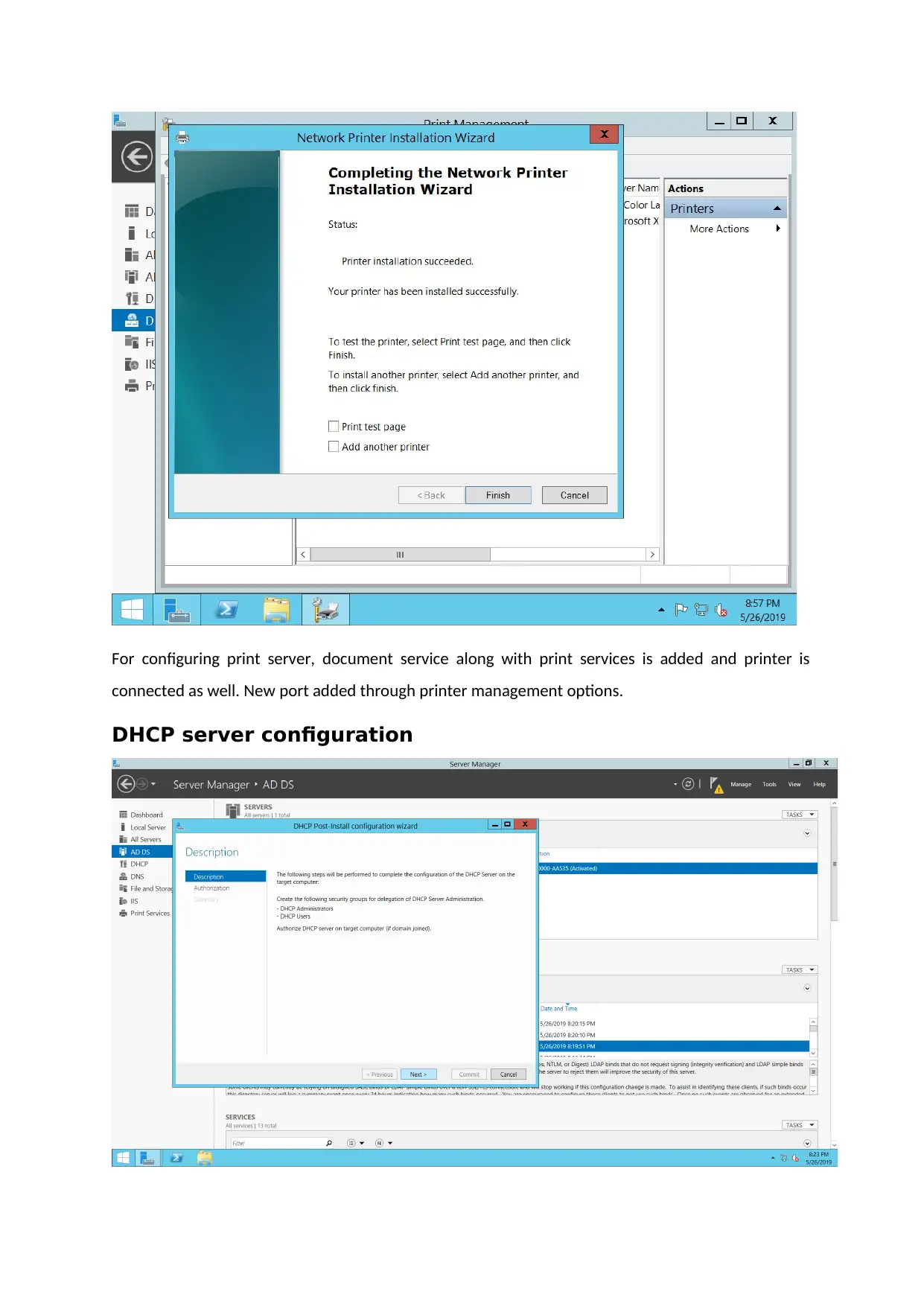
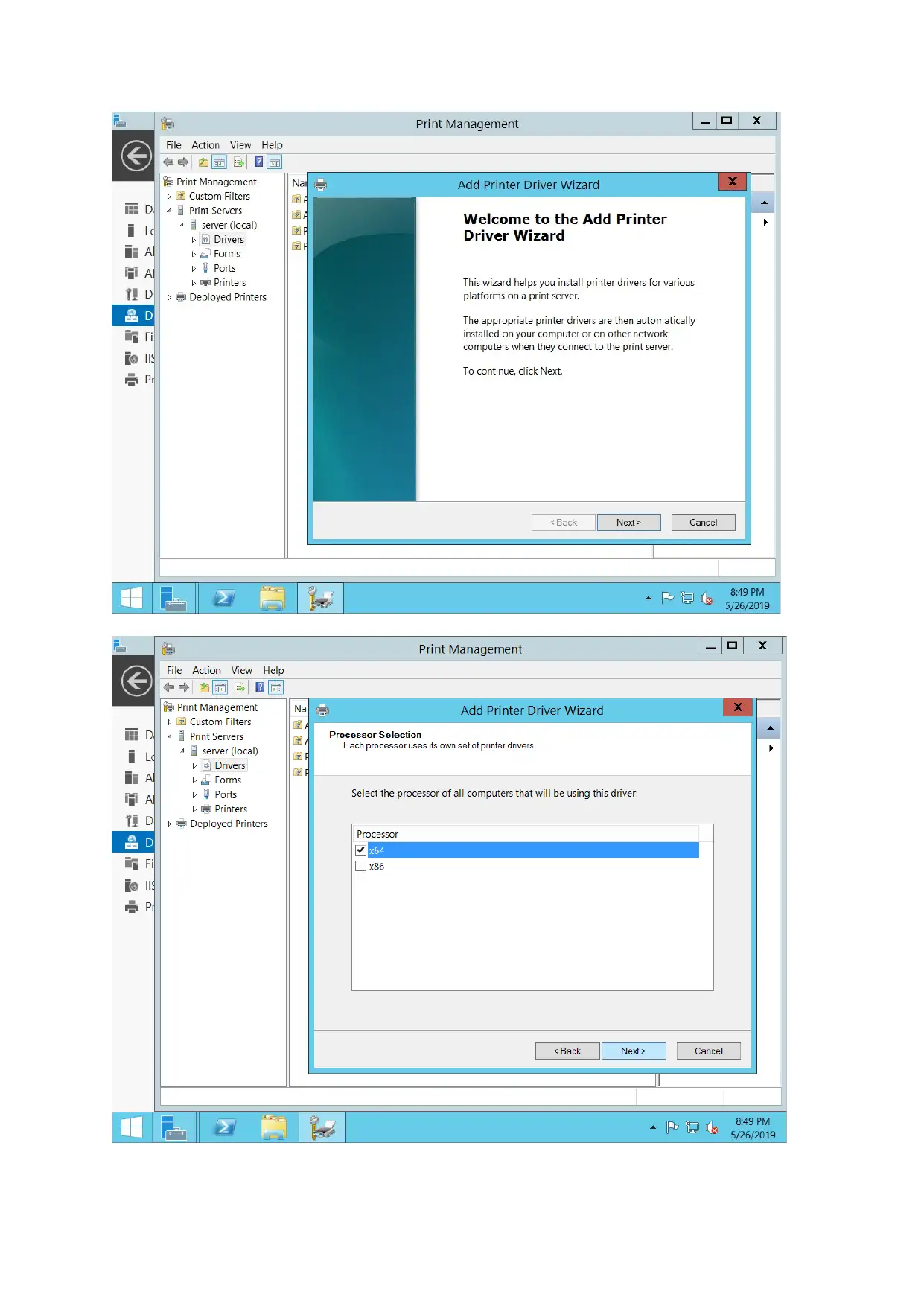
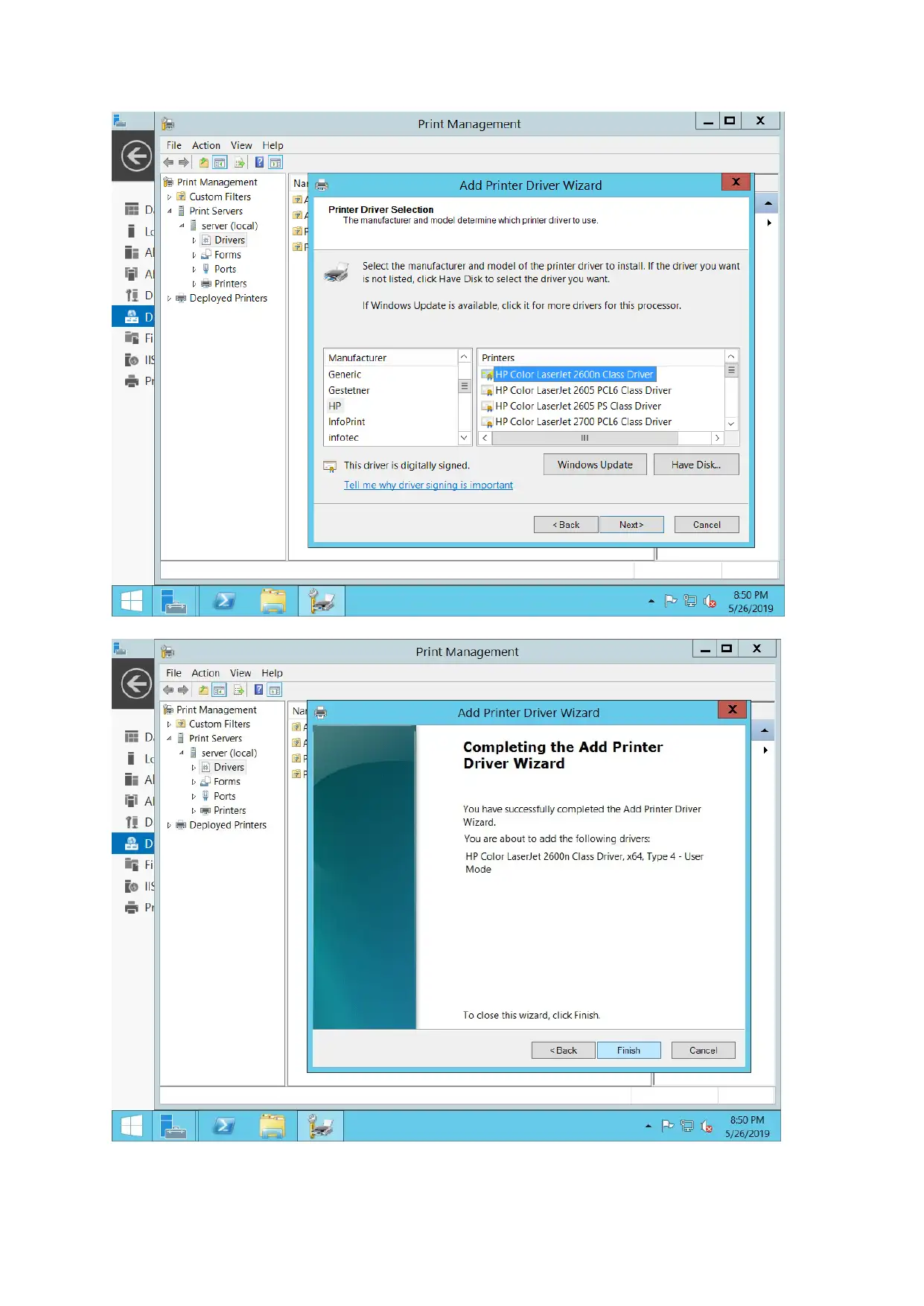
For configuring print server, document service along with print services is added and printer is
connected as well. New port added through printer management options.
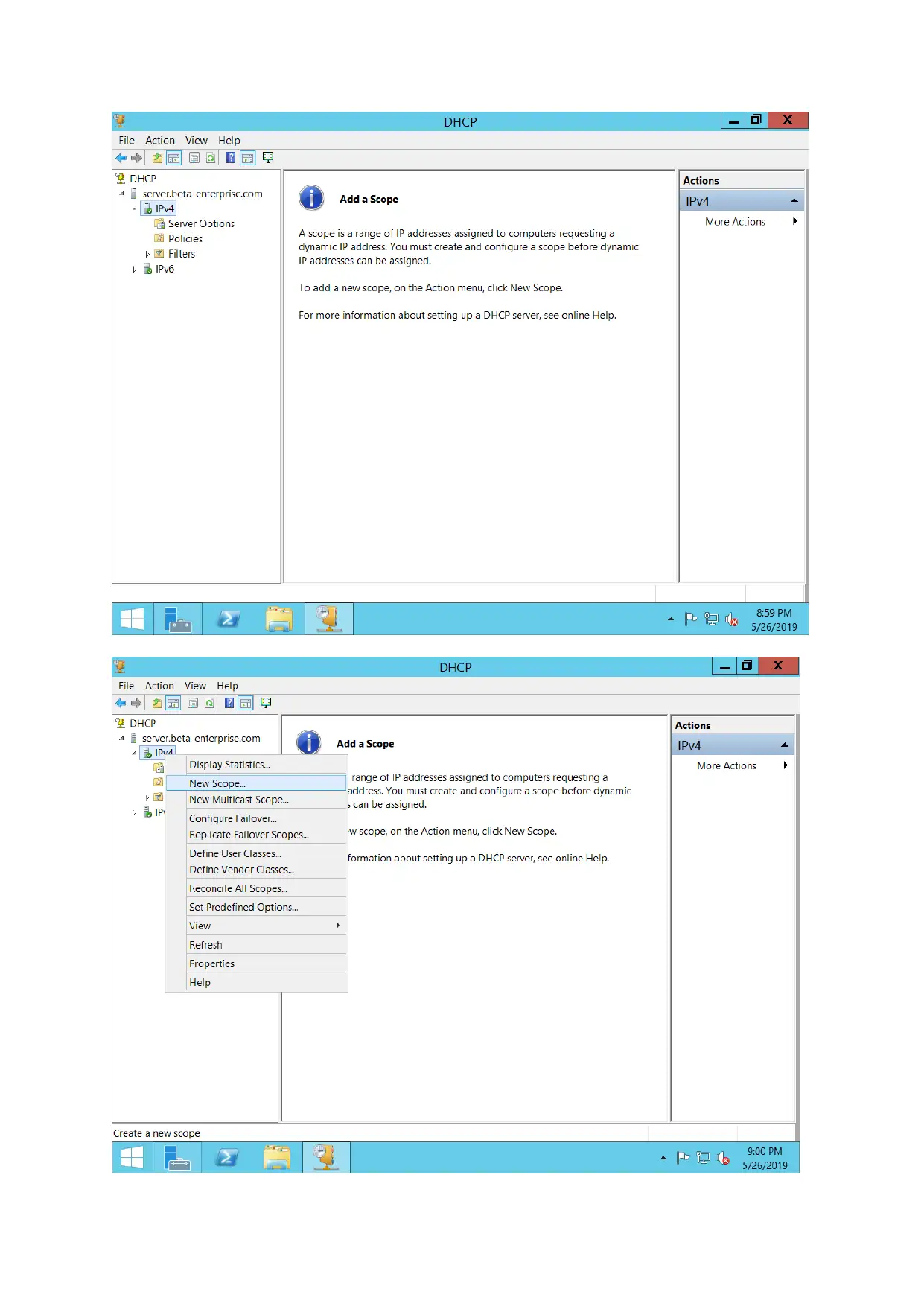
DHCP server configuration
connected as well. New port added through printer management options.
DHCP server configuration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 32
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





