MN601 Network Project Management Assignment - Safe Network System
VerifiedAdded on 2020/04/07
|14
|2314
|103
Project
AI Summary
This project report outlines the development and implementation of a secure network system for a university, addressing the limitations of email-based data transfer. The project aims to provide a safe and efficient platform for various academic and administrative functions, including study material access, e-library usage, and online assessments. The report details the project's objectives, functional and non-functional requirements, and a comprehensive project plan, including a work breakdown structure, timelines, resource allocation, and cost estimates. It also covers risk management, stakeholder analysis, and communication strategies. Appendices include resource plans, Gantt charts, cost estimates, and a risk matrix. The project concludes with a discussion of ethical considerations, a project deployment plan, and post-project review recommendations, emphasizing the importance of lessons learned for future projects. The project's successful completion is signified by project sign-off from the project manager and sponsor, confirming adherence to the planned scope, timeline, and budget. The project's goal is to overcome the limitations of email for data transfer and provide a more secure and efficient network system.
MN601 Network Project Management
Assignment 2‐
Name of Student
9/22/2017
Assignment 2‐
Name of Student
9/22/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN601 1
Executive Summary
Maintaining the data securely and managing them to transfer at ease to the person which actually needs
it and at the time whenever they require it has become the necessity for any academic institution. There
is much documentation which needs to be maintained and transfer for proper handling of the course
material and its evaluation criteria for the proper marking of the student’s grade and many other such
secret operations which should be regulated through highly secured network system to avoid any data
mishandling. In this report we shall discuss the development of the project plan and other planning
documentations required to be developed for conducting such project. At the end also provide some
conclusion for the execution of the project.
Table of Contents
Introduction.................................................................................................................................................2
Body of Presentation...................................................................................................................................2
Conclusion.................................................................................................................................................10
References.................................................................................................................................................11
Appendices................................................................................................................................................12
Appendix-1: Resource Plan....................................................................................................................12
Appendix-2: Gantt chart........................................................................................................................12
Appendix-3: Cost Estimate....................................................................................................................13
Appendix-4: Risk Matrix.........................................................................................................................14
Executive Summary
Maintaining the data securely and managing them to transfer at ease to the person which actually needs
it and at the time whenever they require it has become the necessity for any academic institution. There
is much documentation which needs to be maintained and transfer for proper handling of the course
material and its evaluation criteria for the proper marking of the student’s grade and many other such
secret operations which should be regulated through highly secured network system to avoid any data
mishandling. In this report we shall discuss the development of the project plan and other planning
documentations required to be developed for conducting such project. At the end also provide some
conclusion for the execution of the project.
Table of Contents
Introduction.................................................................................................................................................2
Body of Presentation...................................................................................................................................2
Conclusion.................................................................................................................................................10
References.................................................................................................................................................11
Appendices................................................................................................................................................12
Appendix-1: Resource Plan....................................................................................................................12
Appendix-2: Gantt chart........................................................................................................................12
Appendix-3: Cost Estimate....................................................................................................................13
Appendix-4: Risk Matrix.........................................................................................................................14

MN601 2
Introduction
For developing a network for the university by using which all the staffs and students shall perform their
basic needs of the institution like getting study material, accessing e-library, doing payment for the
semester, the professor shall distribute the study items, course objectives and access the answer sheets
submitted online or conduct time bound online test to access the student’s capability to stand in some
critical condition and develop them fully for facing the challenges of professional world. So for providing
so many facilities and at the same time maintain the high level security so that nobody can breach the
security level and access other’s data or information a highly secured network system is required to be
developed.
Body of Presentation
Title
Implementation of Safe Network for University
Dates
Start Date: 16th October 2017 Completion Date: 30th October 2018
Project Goal
To develop a safe network system for the university to access all sorts of transactions and overcome the
limitations of using e-mail services.
Project Objective
The objective of this project is to deliver the network within 12 months, where the requirement shall be
finalized in first 3 months and then in 9months we shall develop and implement the network system.
Functional requirement
Registration: professors & students must be requested the enlistment with the framework for
getting the entrance in to the system.
Authentication: while enrolling itself, the secret key might be made a request to put, and from
each future utilization the framework will continue requesting that clients enter subsequent to
Introduction
For developing a network for the university by using which all the staffs and students shall perform their
basic needs of the institution like getting study material, accessing e-library, doing payment for the
semester, the professor shall distribute the study items, course objectives and access the answer sheets
submitted online or conduct time bound online test to access the student’s capability to stand in some
critical condition and develop them fully for facing the challenges of professional world. So for providing
so many facilities and at the same time maintain the high level security so that nobody can breach the
security level and access other’s data or information a highly secured network system is required to be
developed.
Body of Presentation
Title
Implementation of Safe Network for University
Dates
Start Date: 16th October 2017 Completion Date: 30th October 2018
Project Goal
To develop a safe network system for the university to access all sorts of transactions and overcome the
limitations of using e-mail services.
Project Objective
The objective of this project is to deliver the network within 12 months, where the requirement shall be
finalized in first 3 months and then in 9months we shall develop and implement the network system.
Functional requirement
Registration: professors & students must be requested the enlistment with the framework for
getting the entrance in to the system.
Authentication: while enrolling itself, the secret key might be made a request to put, and from
each future utilization the framework will continue requesting that clients enter subsequent to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

MN601 3
putting the set watchword as it were. This id is required to keep any outsider to enter the
framework.
E-notice: the computerized framework must be sufficiently fit to send the subsequent warnings
all alone according to the pre-set criteria and the calendar of assessment submission.
Manage database: the vast database must be reasonable by the framework to store and share
large volume engineering documents.
Accessible: in addition to encourage the professors and students to do their work from their
decision of land a transfer in the framework at whatever point required it must be open from
anyplace.
Uniformity of configurations: the organizations must be orchestrated by its outline and once it is
through the framework need to store them so that these can be picked whenever at whatever
point it is required.
Non-Functional requirement
Secured wall of protection: the framework must give itself a solid divider to keep it away from
any sort of assault.
Access through all hardware system: the framework must be open from any hardware and
working frameworks.
User’s friendly system: the framework must be so much simple and easy to understand that the
professors and students ought to appreciate while doing it.
Team members & Responsibility
Project Manager with all leadership skills and nominal technical knowledge
System Developer strong technical knowledge and passionate to work in team
Administration Member always motivate the team and always inspirational, passionate
to help team
putting the set watchword as it were. This id is required to keep any outsider to enter the
framework.
E-notice: the computerized framework must be sufficiently fit to send the subsequent warnings
all alone according to the pre-set criteria and the calendar of assessment submission.
Manage database: the vast database must be reasonable by the framework to store and share
large volume engineering documents.
Accessible: in addition to encourage the professors and students to do their work from their
decision of land a transfer in the framework at whatever point required it must be open from
anyplace.
Uniformity of configurations: the organizations must be orchestrated by its outline and once it is
through the framework need to store them so that these can be picked whenever at whatever
point it is required.
Non-Functional requirement
Secured wall of protection: the framework must give itself a solid divider to keep it away from
any sort of assault.
Access through all hardware system: the framework must be open from any hardware and
working frameworks.
User’s friendly system: the framework must be so much simple and easy to understand that the
professors and students ought to appreciate while doing it.
Team members & Responsibility
Project Manager with all leadership skills and nominal technical knowledge
System Developer strong technical knowledge and passionate to work in team
Administration Member always motivate the team and always inspirational, passionate
to help team
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MN601 4
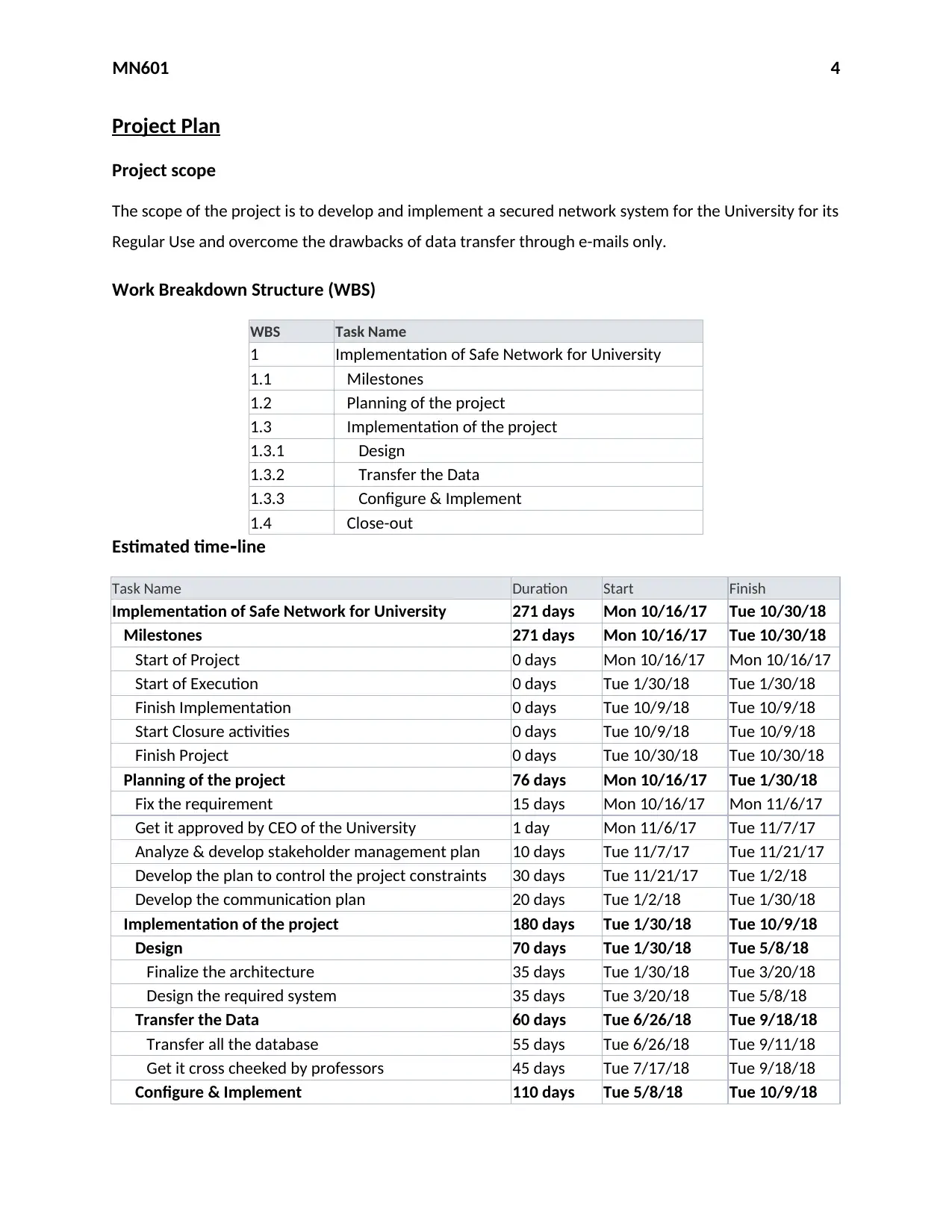
Project Plan
Project scope
The scope of the project is to develop and implement a secured network system for the University for its
Regular Use and overcome the drawbacks of data transfer through e-mails only.
Work Breakdown Structure (WBS)
WBS Task Name
1 Implementation of Safe Network for University
1.1 Milestones
1.2 Planning of the project
1.3 Implementation of the project
1.3.1 Design
1.3.2 Transfer the Data
1.3.3 Configure & Implement
1.4 Close-out
Estimated time line‐
Task Name Duration Start Finish
Implementation of Safe Network for University 271 days Mon 10/16/17 Tue 10/30/18
Milestones 271 days Mon 10/16/17 Tue 10/30/18
Start of Project 0 days Mon 10/16/17 Mon 10/16/17
Start of Execution 0 days Tue 1/30/18 Tue 1/30/18
Finish Implementation 0 days Tue 10/9/18 Tue 10/9/18
Start Closure activities 0 days Tue 10/9/18 Tue 10/9/18
Finish Project 0 days Tue 10/30/18 Tue 10/30/18
Planning of the project 76 days Mon 10/16/17 Tue 1/30/18
Fix the requirement 15 days Mon 10/16/17 Mon 11/6/17
Get it approved by CEO of the University 1 day Mon 11/6/17 Tue 11/7/17
Analyze & develop stakeholder management plan 10 days Tue 11/7/17 Tue 11/21/17
Develop the plan to control the project constraints 30 days Tue 11/21/17 Tue 1/2/18
Develop the communication plan 20 days Tue 1/2/18 Tue 1/30/18
Implementation of the project 180 days Tue 1/30/18 Tue 10/9/18
Design 70 days Tue 1/30/18 Tue 5/8/18
Finalize the architecture 35 days Tue 1/30/18 Tue 3/20/18
Design the required system 35 days Tue 3/20/18 Tue 5/8/18
Transfer the Data 60 days Tue 6/26/18 Tue 9/18/18
Transfer all the database 55 days Tue 6/26/18 Tue 9/11/18
Get it cross cheeked by professors 45 days Tue 7/17/18 Tue 9/18/18
Configure & Implement 110 days Tue 5/8/18 Tue 10/9/18
Project Plan
Project scope
The scope of the project is to develop and implement a secured network system for the University for its
Regular Use and overcome the drawbacks of data transfer through e-mails only.
Work Breakdown Structure (WBS)
WBS Task Name
1 Implementation of Safe Network for University
1.1 Milestones
1.2 Planning of the project
1.3 Implementation of the project
1.3.1 Design
1.3.2 Transfer the Data
1.3.3 Configure & Implement
1.4 Close-out
Estimated time line‐
Task Name Duration Start Finish
Implementation of Safe Network for University 271 days Mon 10/16/17 Tue 10/30/18
Milestones 271 days Mon 10/16/17 Tue 10/30/18
Start of Project 0 days Mon 10/16/17 Mon 10/16/17
Start of Execution 0 days Tue 1/30/18 Tue 1/30/18
Finish Implementation 0 days Tue 10/9/18 Tue 10/9/18
Start Closure activities 0 days Tue 10/9/18 Tue 10/9/18
Finish Project 0 days Tue 10/30/18 Tue 10/30/18
Planning of the project 76 days Mon 10/16/17 Tue 1/30/18
Fix the requirement 15 days Mon 10/16/17 Mon 11/6/17
Get it approved by CEO of the University 1 day Mon 11/6/17 Tue 11/7/17
Analyze & develop stakeholder management plan 10 days Tue 11/7/17 Tue 11/21/17
Develop the plan to control the project constraints 30 days Tue 11/21/17 Tue 1/2/18
Develop the communication plan 20 days Tue 1/2/18 Tue 1/30/18
Implementation of the project 180 days Tue 1/30/18 Tue 10/9/18
Design 70 days Tue 1/30/18 Tue 5/8/18
Finalize the architecture 35 days Tue 1/30/18 Tue 3/20/18
Design the required system 35 days Tue 3/20/18 Tue 5/8/18
Transfer the Data 60 days Tue 6/26/18 Tue 9/18/18
Transfer all the database 55 days Tue 6/26/18 Tue 9/11/18
Get it cross cheeked by professors 45 days Tue 7/17/18 Tue 9/18/18
Configure & Implement 110 days Tue 5/8/18 Tue 10/9/18
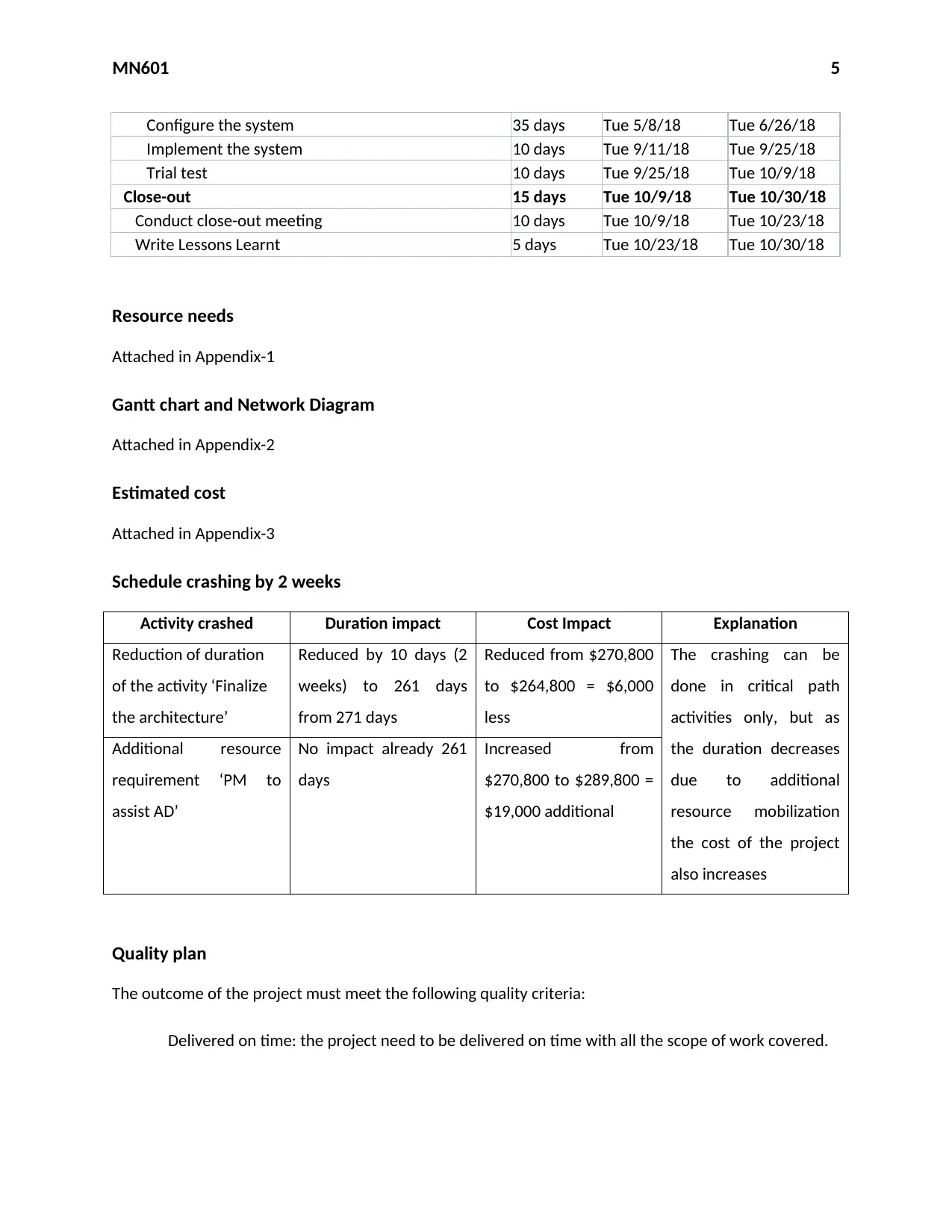
MN601 5
Configure the system 35 days Tue 5/8/18 Tue 6/26/18
Implement the system 10 days Tue 9/11/18 Tue 9/25/18
Trial test 10 days Tue 9/25/18 Tue 10/9/18
Close-out 15 days Tue 10/9/18 Tue 10/30/18
Conduct close-out meeting 10 days Tue 10/9/18 Tue 10/23/18
Write Lessons Learnt 5 days Tue 10/23/18 Tue 10/30/18
Resource needs
Attached in Appendix-1
Gantt chart and Network Diagram
Attached in Appendix-2
Estimated cost
Attached in Appendix-3
Schedule crashing by 2 weeks
Activity crashed Duration impact Cost Impact Explanation
Reduction of duration
of the activity ‘Finalize
the architecture’
Reduced by 10 days (2
weeks) to 261 days
from 271 days
Reduced from $270,800
to $264,800 = $6,000
less
The crashing can be
done in critical path
activities only, but as
the duration decreases
due to additional
resource mobilization
the cost of the project
also increases
Additional resource
requirement ‘PM to
assist AD’
No impact already 261
days
Increased from
$270,800 to $289,800 =
$19,000 additional
Quality plan
The outcome of the project must meet the following quality criteria:
Delivered on time: the project need to be delivered on time with all the scope of work covered.
Configure the system 35 days Tue 5/8/18 Tue 6/26/18
Implement the system 10 days Tue 9/11/18 Tue 9/25/18
Trial test 10 days Tue 9/25/18 Tue 10/9/18
Close-out 15 days Tue 10/9/18 Tue 10/30/18
Conduct close-out meeting 10 days Tue 10/9/18 Tue 10/23/18
Write Lessons Learnt 5 days Tue 10/23/18 Tue 10/30/18
Resource needs
Attached in Appendix-1
Gantt chart and Network Diagram
Attached in Appendix-2
Estimated cost
Attached in Appendix-3
Schedule crashing by 2 weeks
Activity crashed Duration impact Cost Impact Explanation
Reduction of duration
of the activity ‘Finalize
the architecture’
Reduced by 10 days (2
weeks) to 261 days
from 271 days
Reduced from $270,800
to $264,800 = $6,000
less
The crashing can be
done in critical path
activities only, but as
the duration decreases
due to additional
resource mobilization
the cost of the project
also increases
Additional resource
requirement ‘PM to
assist AD’
No impact already 261
days
Increased from
$270,800 to $289,800 =
$19,000 additional
Quality plan
The outcome of the project must meet the following quality criteria:
Delivered on time: the project need to be delivered on time with all the scope of work covered.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
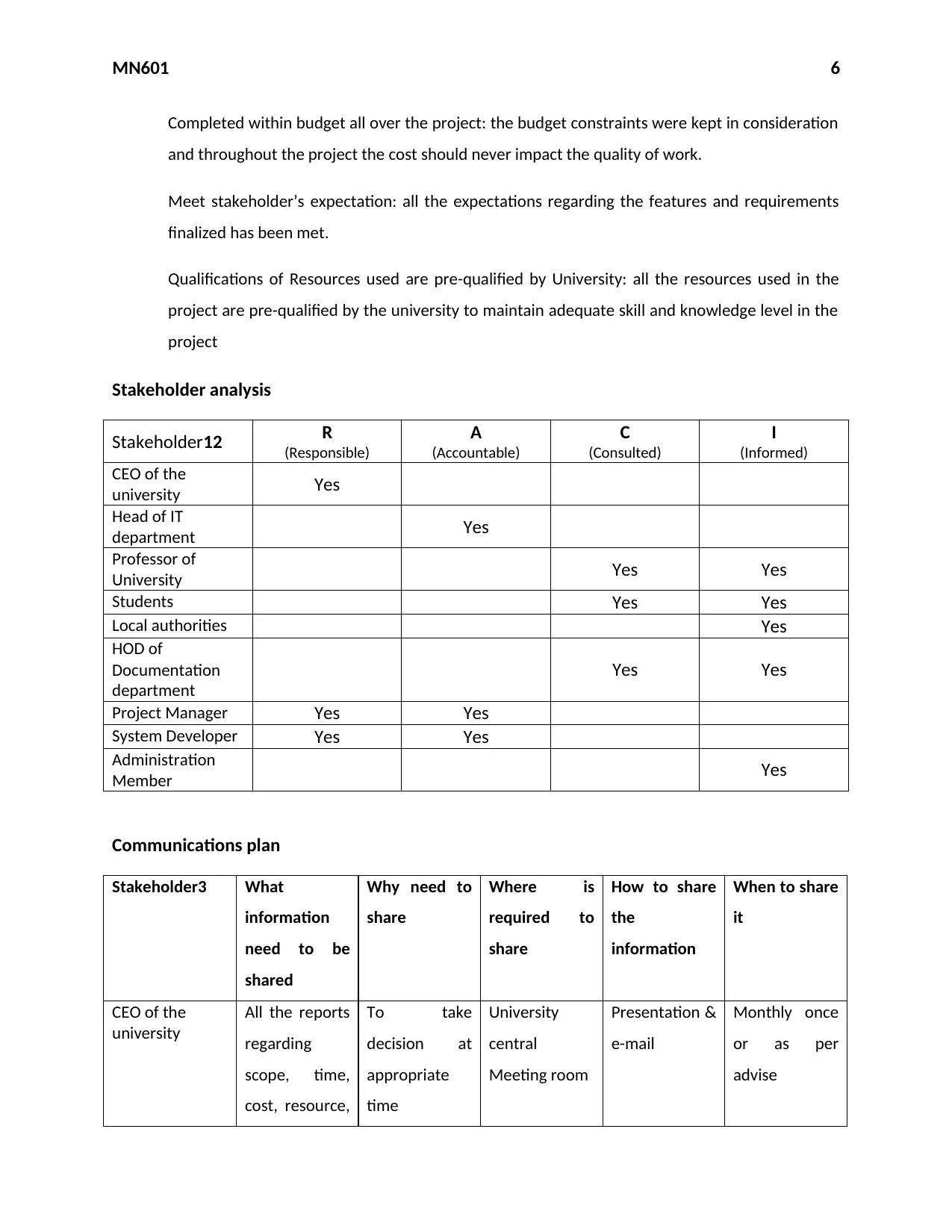
MN601 6
Completed within budget all over the project: the budget constraints were kept in consideration
and throughout the project the cost should never impact the quality of work.
Meet stakeholder’s expectation: all the expectations regarding the features and requirements
finalized has been met.
Qualifications of Resources used are pre-qualified by University: all the resources used in the
project are pre-qualified by the university to maintain adequate skill and knowledge level in the
project
Stakeholder analysis
Stakeholder12 R
(Responsible)
A
(Accountable)
C
(Consulted)
I
(Informed)
CEO of the
university Yes
Head of IT
department Yes
Professor of
University Yes Yes
Students Yes Yes
Local authorities Yes
HOD of
Documentation
department
Yes Yes
Project Manager Yes Yes
System Developer Yes Yes
Administration
Member Yes
Communications plan
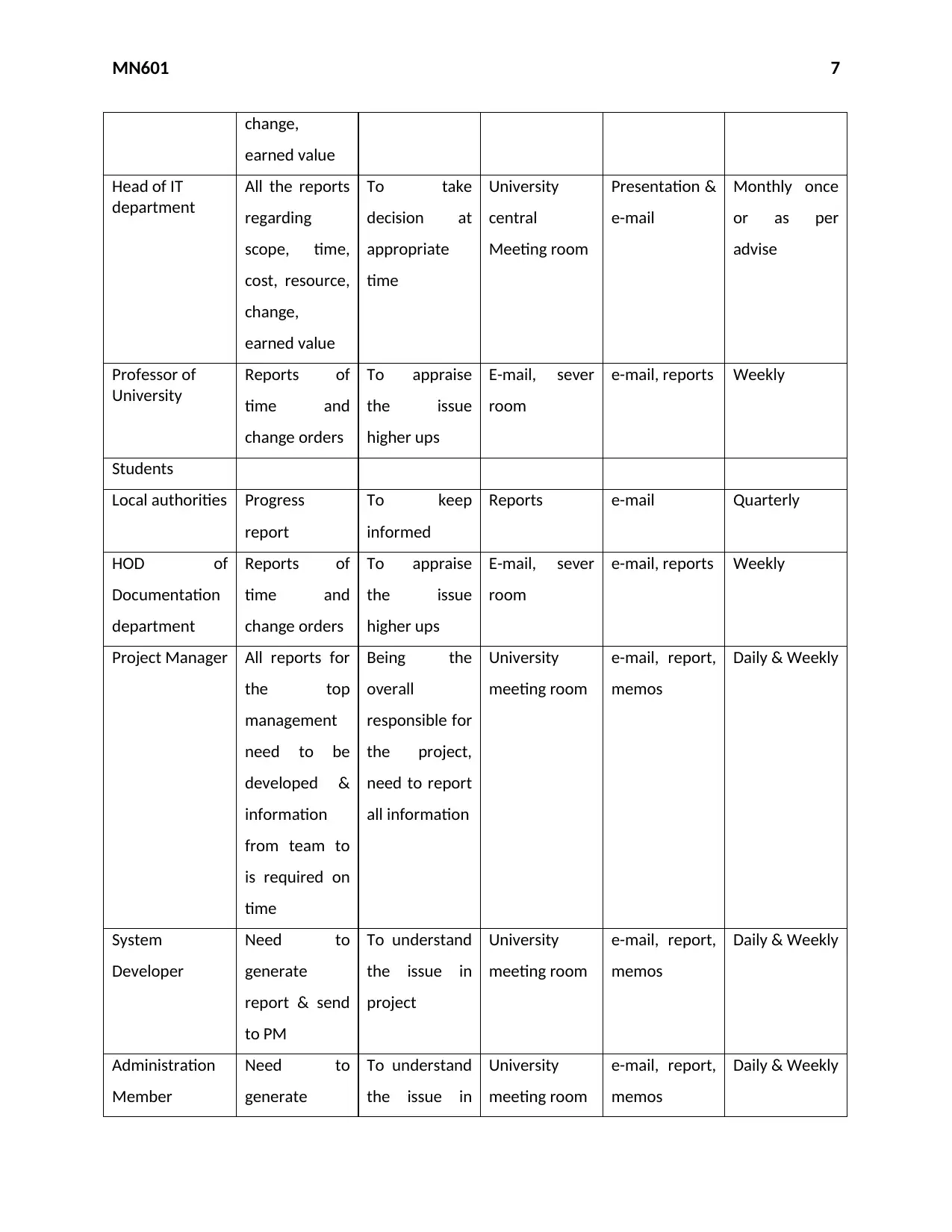
Stakeholder3 What
information
need to be
shared
Why need to
share
Where is
required to
share
How to share
the
information
When to share
it
CEO of the
university
All the reports
regarding
scope, time,
cost, resource,
To take
decision at
appropriate
time
University
central
Meeting room
Presentation &
e-mail
Monthly once
or as per
advise
Completed within budget all over the project: the budget constraints were kept in consideration
and throughout the project the cost should never impact the quality of work.
Meet stakeholder’s expectation: all the expectations regarding the features and requirements
finalized has been met.
Qualifications of Resources used are pre-qualified by University: all the resources used in the
project are pre-qualified by the university to maintain adequate skill and knowledge level in the
project
Stakeholder analysis
Stakeholder12 R
(Responsible)
A
(Accountable)
C
(Consulted)
I
(Informed)
CEO of the
university Yes
Head of IT
department Yes
Professor of
University Yes Yes
Students Yes Yes
Local authorities Yes
HOD of
Documentation
department
Yes Yes
Project Manager Yes Yes
System Developer Yes Yes
Administration
Member Yes
Communications plan
Stakeholder3 What
information
need to be
shared
Why need to
share
Where is
required to
share
How to share
the
information
When to share
it
CEO of the
university
All the reports
regarding
scope, time,
cost, resource,
To take
decision at
appropriate
time
University
central
Meeting room
Presentation &
Monthly once
or as per
advise
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MN601 7
change,
earned value
Head of IT
department
All the reports
regarding
scope, time,
cost, resource,
change,
earned value
To take
decision at
appropriate
time
University
central
Meeting room
Presentation &
e-mail
Monthly once
or as per
advise
Professor of
University
Reports of
time and
change orders
To appraise
the issue
higher ups
E-mail, sever
room
e-mail, reports Weekly
Students
Local authorities Progress
report
To keep
informed
Reports e-mail Quarterly
HOD of
Documentation
department
Reports of
time and
change orders
To appraise
the issue
higher ups
E-mail, sever
room
e-mail, reports Weekly
Project Manager All reports for
the top
management
need to be
developed &
information
from team to
is required on
time
Being the
overall
responsible for
the project,
need to report
all information
University
meeting room
e-mail, report,
memos
Daily & Weekly
System
Developer
Need to
generate
report & send
to PM
To understand
the issue in
project
University
meeting room
e-mail, report,
memos
Daily & Weekly
Administration
Member
Need to
generate
To understand
the issue in
University
meeting room
e-mail, report,
memos
Daily & Weekly
change,
earned value
Head of IT
department
All the reports
regarding
scope, time,
cost, resource,
change,
earned value
To take
decision at
appropriate
time
University
central
Meeting room
Presentation &
Monthly once
or as per
advise
Professor of
University
Reports of
time and
change orders
To appraise
the issue
higher ups
E-mail, sever
room
e-mail, reports Weekly
Students
Local authorities Progress
report
To keep
informed
Reports e-mail Quarterly
HOD of
Documentation
department
Reports of
time and
change orders
To appraise
the issue
higher ups
E-mail, sever
room
e-mail, reports Weekly
Project Manager All reports for
the top
management
need to be
developed &
information
from team to
is required on
time
Being the
overall
responsible for
the project,
need to report
all information
University
meeting room
e-mail, report,
memos
Daily & Weekly
System
Developer
Need to
generate
report & send
to PM
To understand
the issue in
project
University
meeting room
e-mail, report,
memos
Daily & Weekly
Administration
Member
Need to
generate
To understand
the issue in
University
meeting room
e-mail, report,
memos
Daily & Weekly
MN601 8
report & send
to PM
project
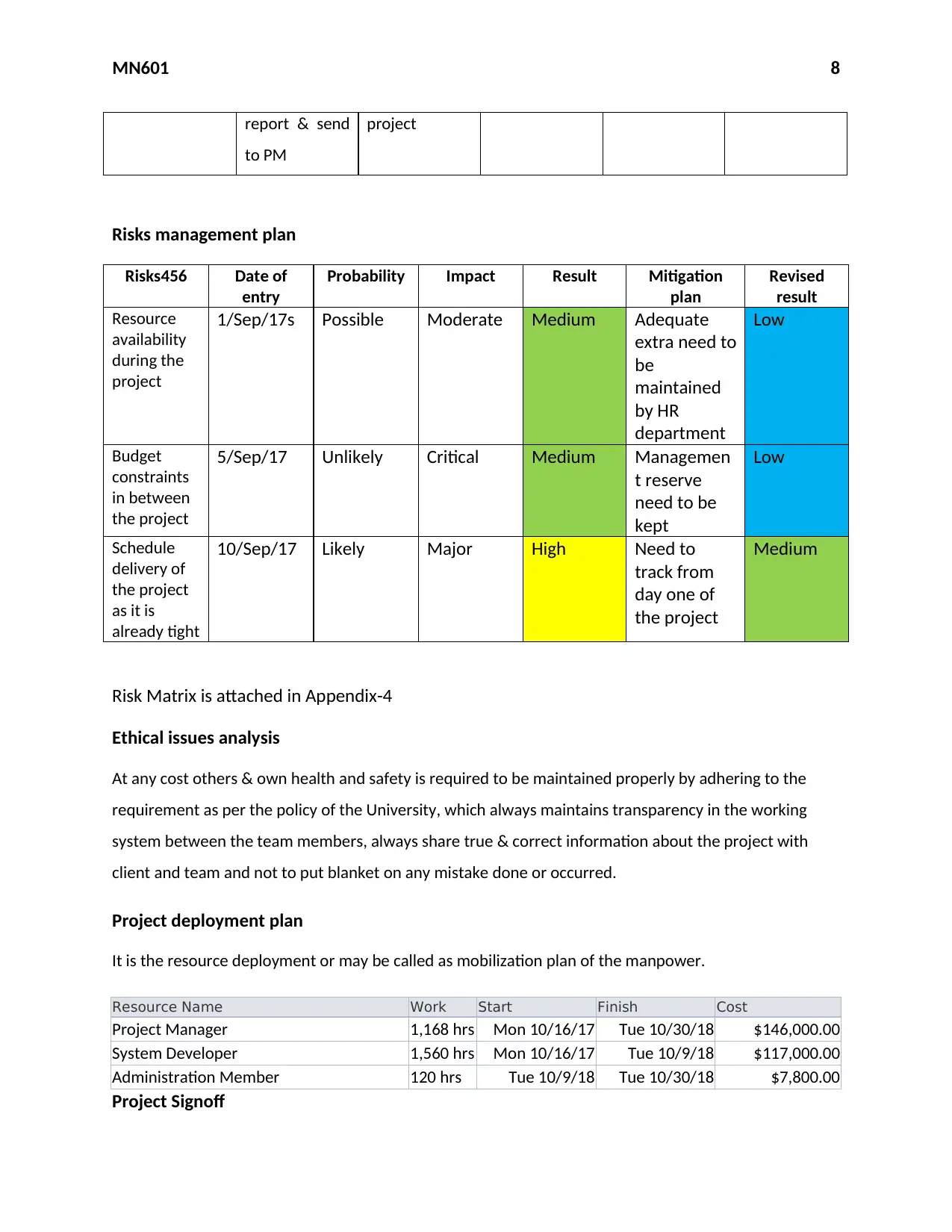
Risks management plan
Risks456 Date of
entry
Probability Impact Result Mitigation
plan
Revised
result
Resource
availability
during the
project
1/Sep/17s Possible Moderate Medium Adequate
extra need to
be
maintained
by HR
department
Low
Budget
constraints
in between
the project
5/Sep/17 Unlikely Critical Medium Managemen
t reserve
need to be
kept
Low
Schedule
delivery of
the project
as it is
already tight
10/Sep/17 Likely Major High Need to
track from
day one of
the project
Medium
Risk Matrix is attached in Appendix-4
Ethical issues analysis
At any cost others & own health and safety is required to be maintained properly by adhering to the
requirement as per the policy of the University, which always maintains transparency in the working
system between the team members, always share true & correct information about the project with
client and team and not to put blanket on any mistake done or occurred.
Project deployment plan
It is the resource deployment or may be called as mobilization plan of the manpower.
Resource Name Work Start Finish Cost
Project Manager 1,168 hrs Mon 10/16/17 Tue 10/30/18 $146,000.00
System Developer 1,560 hrs Mon 10/16/17 Tue 10/9/18 $117,000.00
Administration Member 120 hrs Tue 10/9/18 Tue 10/30/18 $7,800.00
Project Signoff
report & send
to PM
project
Risks management plan
Risks456 Date of
entry
Probability Impact Result Mitigation
plan
Revised
result
Resource
availability
during the
project
1/Sep/17s Possible Moderate Medium Adequate
extra need to
be
maintained
by HR
department
Low
Budget
constraints
in between
the project
5/Sep/17 Unlikely Critical Medium Managemen
t reserve
need to be
kept
Low
Schedule
delivery of
the project
as it is
already tight
10/Sep/17 Likely Major High Need to
track from
day one of
the project
Medium
Risk Matrix is attached in Appendix-4
Ethical issues analysis
At any cost others & own health and safety is required to be maintained properly by adhering to the
requirement as per the policy of the University, which always maintains transparency in the working
system between the team members, always share true & correct information about the project with
client and team and not to put blanket on any mistake done or occurred.
Project deployment plan
It is the resource deployment or may be called as mobilization plan of the manpower.
Resource Name Work Start Finish Cost
Project Manager 1,168 hrs Mon 10/16/17 Tue 10/30/18 $146,000.00
System Developer 1,560 hrs Mon 10/16/17 Tue 10/9/18 $117,000.00
Administration Member 120 hrs Tue 10/9/18 Tue 10/30/18 $7,800.00
Project Signoff
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
MN601 9
7
This is the report which is to sign and confirm the delivery and acceptance of the same.
Project Manager: This is to affirm that our
organization has played out every one of the
exercises according to contract within planned
time and cost. The change asked for has been
raised through legitimate channel. Every one of
the have been reported and given over. Want to
enjoy all that life has to offer for the organization.
_________________________
Signature
Sponsor / Owner: This is to affirm that I got the
framework with in the financial plan and time and
quality benchmarks.
_________________________
Signature
Post project review and recommendations
7
This is the report which is to sign and confirm the delivery and acceptance of the same.
Project Manager: This is to affirm that our
organization has played out every one of the
exercises according to contract within planned
time and cost. The change asked for has been
raised through legitimate channel. Every one of
the have been reported and given over. Want to
enjoy all that life has to offer for the organization.
_________________________
Signature
Sponsor / Owner: This is to affirm that I got the
framework with in the financial plan and time and
quality benchmarks.
_________________________
Signature
Post project review and recommendations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN601 10
Once the project is completed we should not leave the project and site, rather we shall meet at the
University Central Meeting room again with all the key stakeholders present to note the feedback and
lessons learnt. These lessons learnt should be used for developing any such project in future and it will
never repeat the errors done in the project to deliver better quality product in less time and cost.
Conclusion
This is to conclude that the current problem with the data is that the data transfer is only possible within
the college through the use of e-mail service, which always restricts the users to transfer large volume
data. The project will develop a network system which shall connect all colleges of the university to
transfer data as big as possible and other financial transactions shall also be possible without any fear of
cyber-attack. Proper project planning and developing the documents shows the confidence in
developing the project on time. Once so much depth study is done, it helps in execution and assuring
the timely and quality product.
References
x
[1] Mike Miller. (2017) http://study.com. [Online]. http://study.com/academy/lesson/project-
stakeholders-definition-role-identification.html
[2] Fahad Usmani. (2017) PMStudyCircle.com. [Online]. https://pmstudycircle.com/2012/06/identify-
stakeholders-project-management/
[3] Template. (2017) www.template.net. [Online]. https://www.template.net/business/plan-
templates/project-management-communication-plan-template/
[4] Michael Stanleigh. (2017) Risk Management…the What, Why, and How. [Online]. https://bia.ca/risk-
management-the-what-why-and-how/
[5] Adrienne Watt. (2014) opentextbc.ca. [Online].
https://opentextbc.ca/projectmanagement/chapter/chapter-16-risk-management-planning-project-
management/
Once the project is completed we should not leave the project and site, rather we shall meet at the
University Central Meeting room again with all the key stakeholders present to note the feedback and
lessons learnt. These lessons learnt should be used for developing any such project in future and it will
never repeat the errors done in the project to deliver better quality product in less time and cost.
Conclusion
This is to conclude that the current problem with the data is that the data transfer is only possible within
the college through the use of e-mail service, which always restricts the users to transfer large volume
data. The project will develop a network system which shall connect all colleges of the university to
transfer data as big as possible and other financial transactions shall also be possible without any fear of
cyber-attack. Proper project planning and developing the documents shows the confidence in
developing the project on time. Once so much depth study is done, it helps in execution and assuring
the timely and quality product.
References
x
[1] Mike Miller. (2017) http://study.com. [Online]. http://study.com/academy/lesson/project-
stakeholders-definition-role-identification.html
[2] Fahad Usmani. (2017) PMStudyCircle.com. [Online]. https://pmstudycircle.com/2012/06/identify-
stakeholders-project-management/
[3] Template. (2017) www.template.net. [Online]. https://www.template.net/business/plan-
templates/project-management-communication-plan-template/
[4] Michael Stanleigh. (2017) Risk Management…the What, Why, and How. [Online]. https://bia.ca/risk-
management-the-what-why-and-how/
[5] Adrienne Watt. (2014) opentextbc.ca. [Online].
https://opentextbc.ca/projectmanagement/chapter/chapter-16-risk-management-planning-project-
management/
MN601 11
[6] et al. Wiley. (2017) 11.2 Risk Management Process. [Online]. https://pm4id.org/chapter/11-2-risk-
management-process/
[7] Ray Henderson. (2015, July) LinkedIn Corporation. [Online].
https://www.slideshare.net/RayHenderson2/project-signoff
x
Appendices
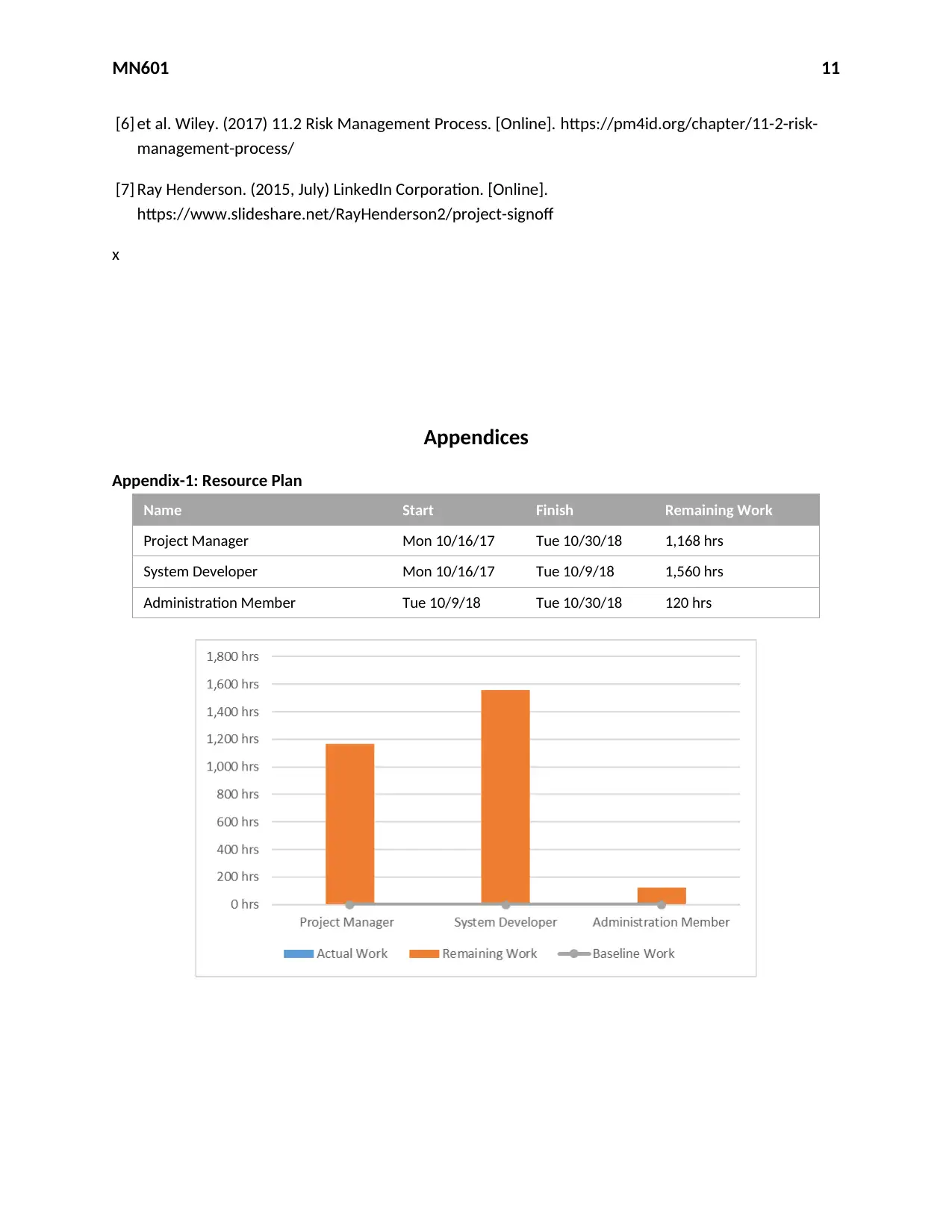
Appendix-1: Resource Plan
Name Start Finish Remaining Work
Project Manager Mon 10/16/17 Tue 10/30/18 1,168 hrs
System Developer Mon 10/16/17 Tue 10/9/18 1,560 hrs
Administration Member Tue 10/9/18 Tue 10/30/18 120 hrs
[6] et al. Wiley. (2017) 11.2 Risk Management Process. [Online]. https://pm4id.org/chapter/11-2-risk-
management-process/
[7] Ray Henderson. (2015, July) LinkedIn Corporation. [Online].
https://www.slideshare.net/RayHenderson2/project-signoff
x
Appendices
Appendix-1: Resource Plan
Name Start Finish Remaining Work
Project Manager Mon 10/16/17 Tue 10/30/18 1,168 hrs
System Developer Mon 10/16/17 Tue 10/9/18 1,560 hrs
Administration Member Tue 10/9/18 Tue 10/30/18 120 hrs
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





