MN610 Virtual Private Networks: Designing a VPN for SME Organizations
VerifiedAdded on 2023/06/04
|12
|552
|89
Report
AI Summary
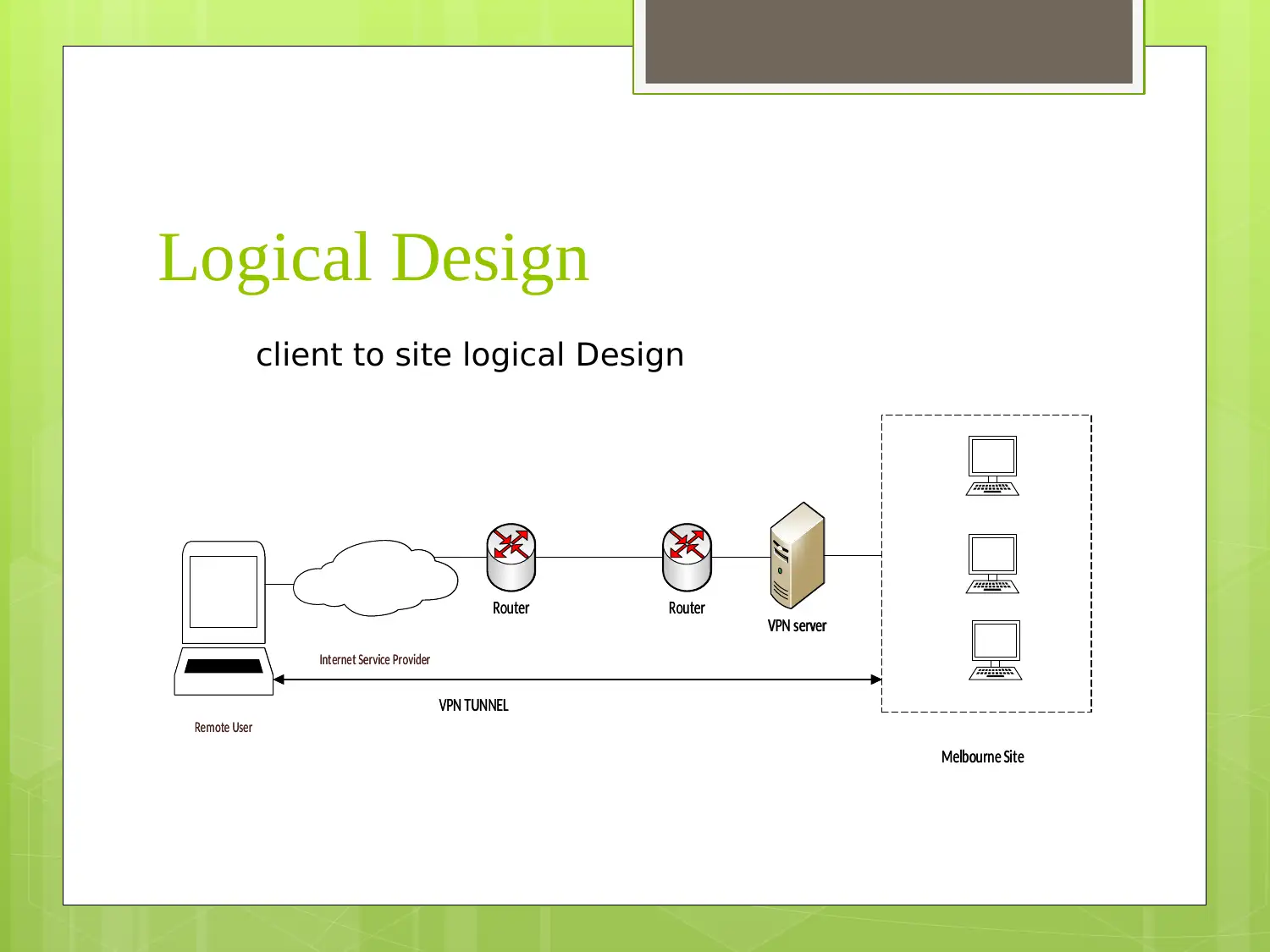
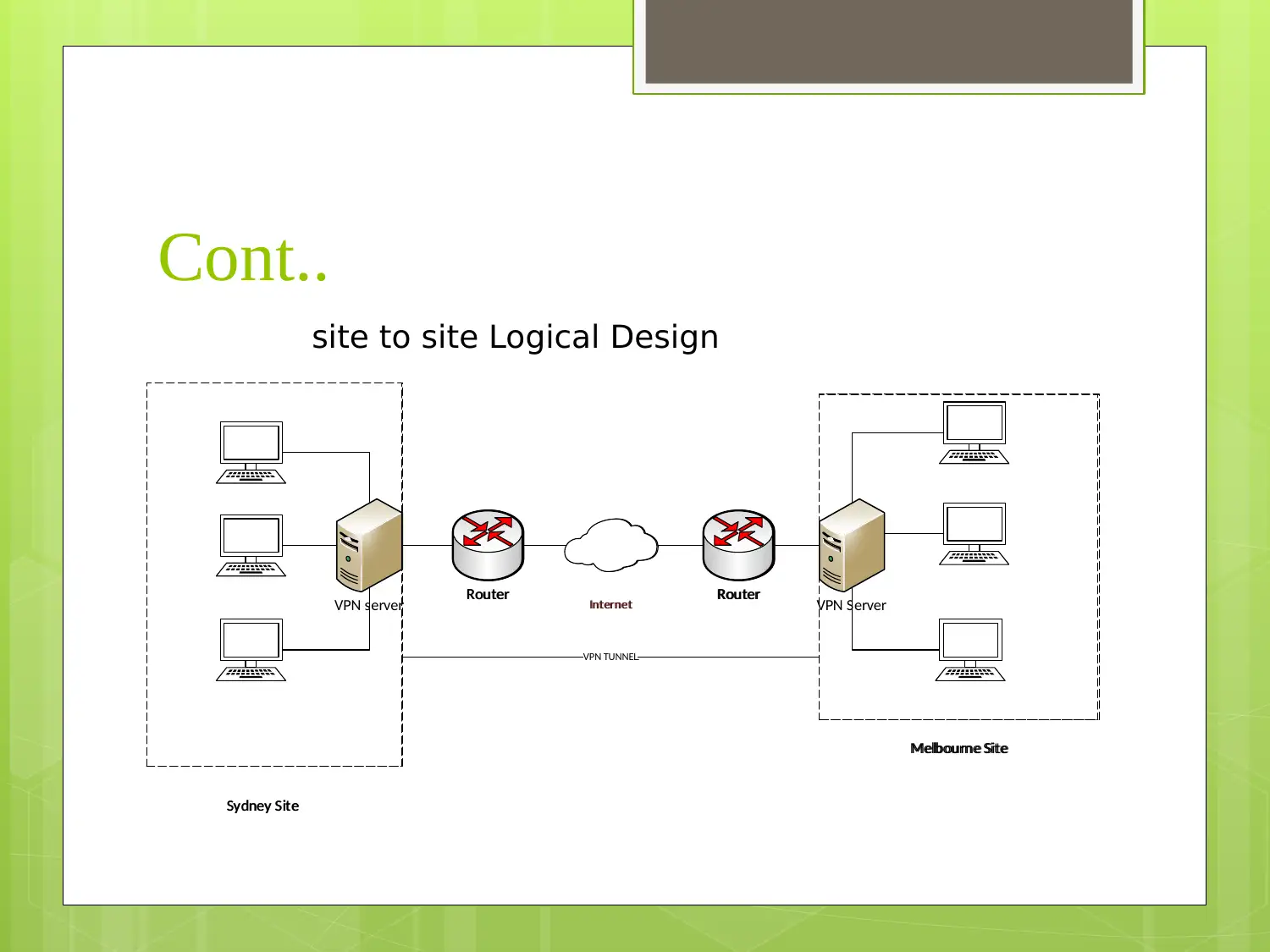
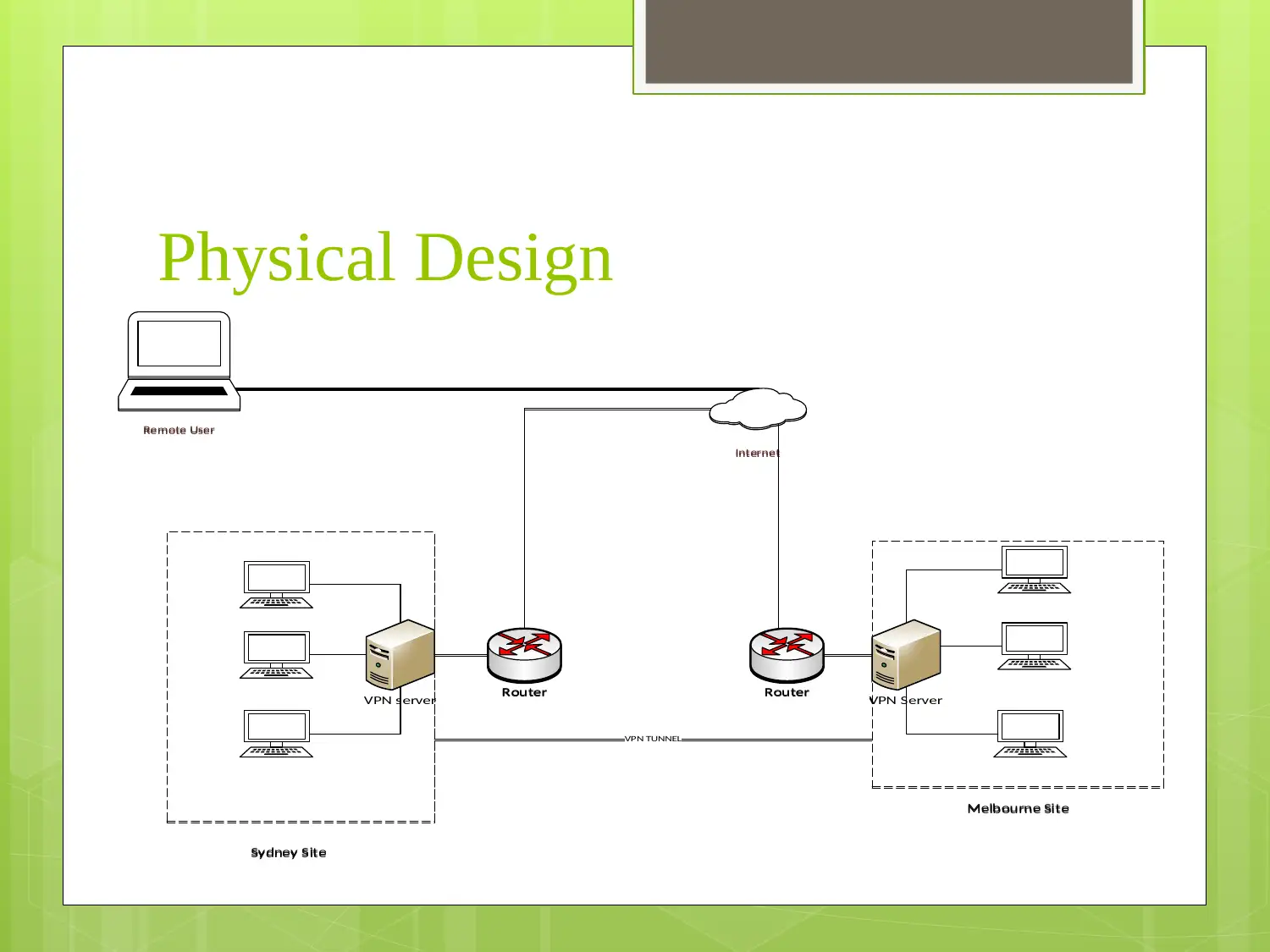
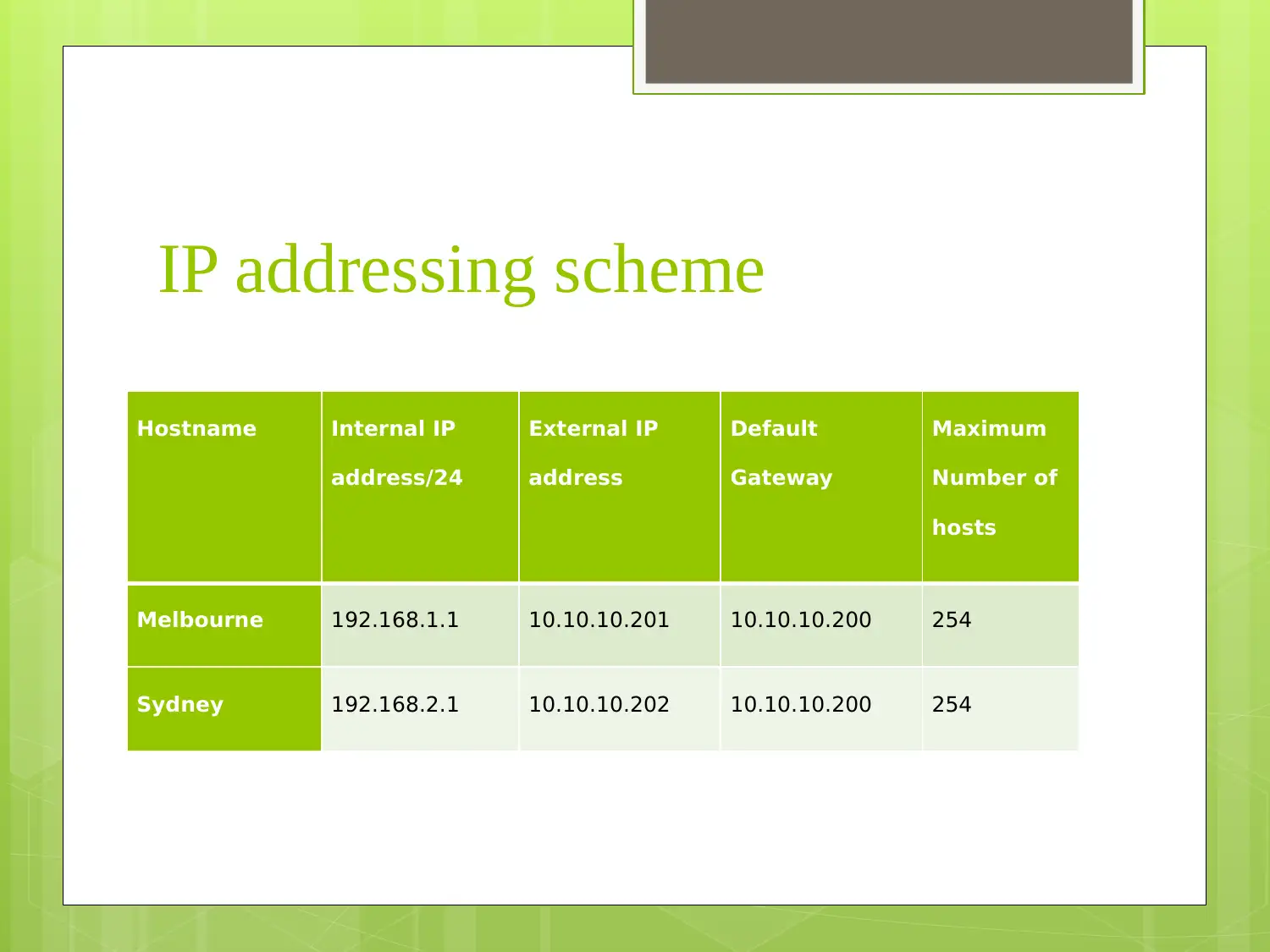
This report presents a comprehensive VPN network design for small to medium-sized enterprises (SMEs), outlining a phased approach to implementation with a focus on client-to-site and site-to-site VPN technologies. It details the requirements, logical and physical designs, managed VPN technology topology, and an IP addressing scheme. Furthermore, the report emphasizes security features and policies, including the use of firewalls and IPsec, and provides a six-step VPN service implementation process encompassing assessment, design, testing, implementation, training, and project management. The design aims to provide reliable, secure, and scalable communication solutions for SME organizations.
1 out of 12















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)