MN613 Computer Forensics T2 2018: Validating Data Recovery Tools
VerifiedAdded on 2023/06/07
|14
|1404
|192
Case Study
AI Summary
This case study presents a digital forensics investigation involving data recovery from a USB drive, employing tools such as ProDiscover and WinHex. The study details the process of data acquisition, where a scientific image of the USB drive is created using ProDiscover to preserve the original evidence. Subsequently, data recovery techniques are applied to retrieve deleted files, including documents and images. The analysis phase involves using WinHex to examine the recovered data, identify hidden files, and validate the integrity of the recovered information through hashing and hexadecimal editing. A second case study briefly discusses duplicating a 2GB drive at a crime scene, emphasizing data acquisition methods and best practices for forensic imaging. The document concludes with references to relevant literature in the field of digital forensics. Desklib provides access to this and other solved assignments to aid students in their studies.

0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Case Study I: Create and Delete Files on USB Drive........................................................................................2
1. Data Acquisition.........................................................................................................................................2
2. Data Recovery.............................................................................................................................................3
3. Data Analysis..............................................................................................................................................5
4. Data Validation.........................................................................................................................................10
2. Case Study II: Investing a Case......................................................................................................................11
References..............................................................................................................................................................12
1. Case Study I: Create and Delete Files on USB Drive........................................................................................2
1. Data Acquisition.........................................................................................................................................2
2. Data Recovery.............................................................................................................................................3
3. Data Analysis..............................................................................................................................................5
4. Data Validation.........................................................................................................................................10
2. Case Study II: Investing a Case......................................................................................................................11
References..............................................................................................................................................................12
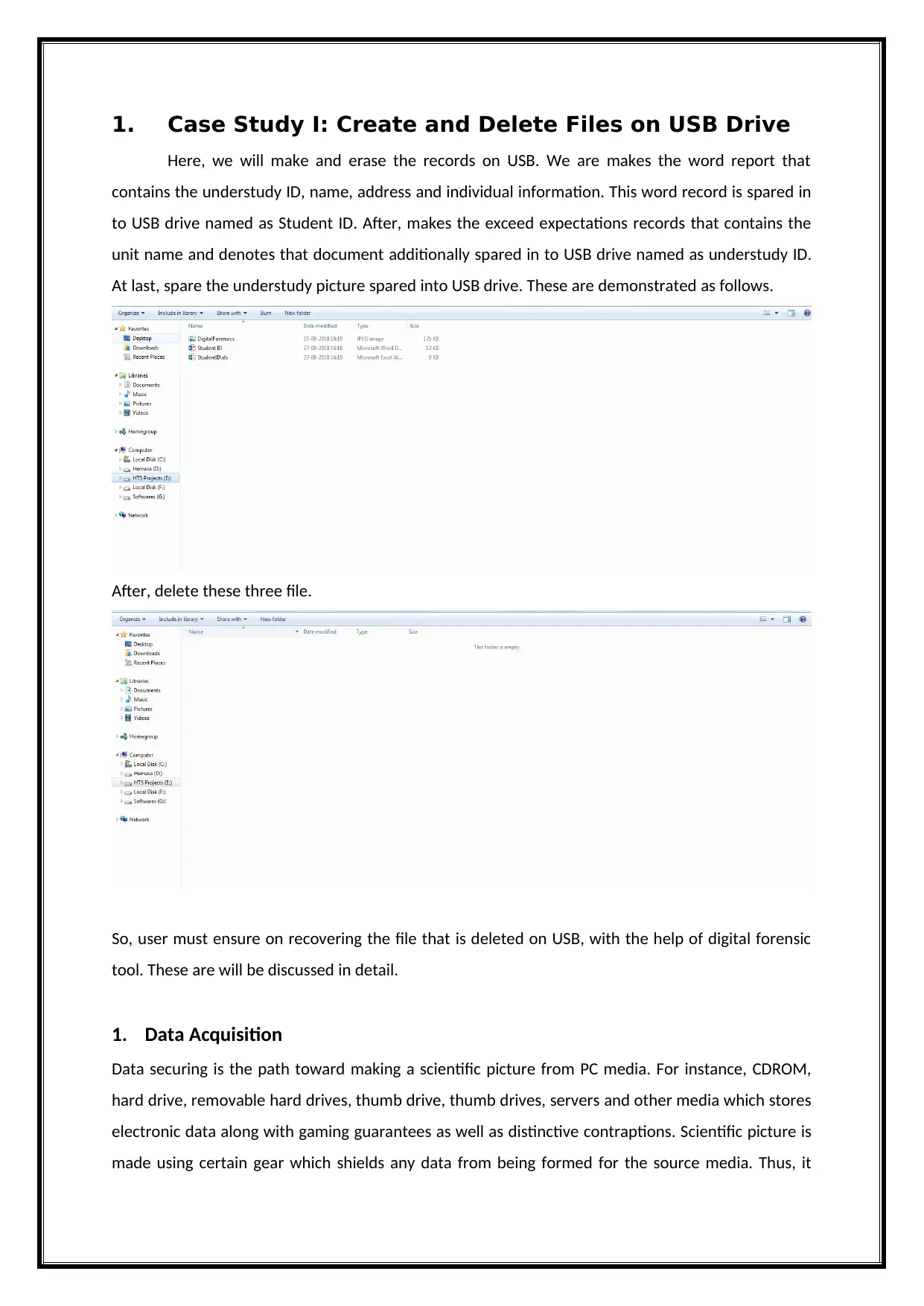
1. Case Study I: Create and Delete Files on USB Drive
Here, we will make and erase the records on USB. We are makes the word report that
contains the understudy ID, name, address and individual information. This word record is spared in
to USB drive named as Student ID. After, makes the exceed expectations records that contains the
unit name and denotes that document additionally spared in to USB drive named as understudy ID.
At last, spare the understudy picture spared into USB drive. These are demonstrated as follows.
After, delete these three file.
So, user must ensure on recovering the file that is deleted on USB, with the help of digital forensic
tool. These are will be discussed in detail.
1. Data Acquisition
Data securing is the path toward making a scientific picture from PC media. For instance, CDROM,
hard drive, removable hard drives, thumb drive, thumb drives, servers and other media which stores
electronic data along with gaming guarantees as well as distinctive contraptions. Scientific picture is
made using certain gear which shields any data from being formed for the source media. Thus, it
Here, we will make and erase the records on USB. We are makes the word report that
contains the understudy ID, name, address and individual information. This word record is spared in
to USB drive named as Student ID. After, makes the exceed expectations records that contains the
unit name and denotes that document additionally spared in to USB drive named as understudy ID.
At last, spare the understudy picture spared into USB drive. These are demonstrated as follows.
After, delete these three file.
So, user must ensure on recovering the file that is deleted on USB, with the help of digital forensic
tool. These are will be discussed in detail.
1. Data Acquisition
Data securing is the path toward making a scientific picture from PC media. For instance, CDROM,
hard drive, removable hard drives, thumb drive, thumb drives, servers and other media which stores
electronic data along with gaming guarantees as well as distinctive contraptions. Scientific picture is
made using certain gear which shields any data from being formed for the source media. Thus, it
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

remains consummate. Criminological picture, not the primary media, is used by the legal analyst for
leading examination. The data getting process fuses the record of each serial number and distinctive
markings using a propelled camera. Measurable picture is affirmed against the first to ensure the
criminological picture is a right duplicate of the primary media. To do data securing by utilizing the
star find fundamental device. The prodiscover legal sciences device is most intense PC security
instrument that used to empower the criminology agent to decide the every one of the data on the
PC framework while ensuring the proof and making the evidentiary quality reports. This device has
different highlights and advantages, for example,
It makes the bit stream duplicate of circle to be dissected to protect the first
confirmation.
It effectively look through the whole circle and records including the PC data streams
which is utilized for finish plate scientific investigation [1].
It keep up the multi instrument similarity by composing and perusing the pictures.
It inspect the PC document to give the data uprightness.
It additionally analyse the all record frameworks for most extreme adaptability.
It used the Perl contents to mechanize the examination undertakings.
It personality the record makers to separates the EXIF data from JPEG documents.
It enhances the similarity and precision via robotized the report age in XML design.
It intended to NIST plate imaging instrument to guarantee the high calibre.
It bolster for VM product to run a caught pictures.
2. Data Recovery
Open Pro discover basic Tool.
leading examination. The data getting process fuses the record of each serial number and distinctive
markings using a propelled camera. Measurable picture is affirmed against the first to ensure the
criminological picture is a right duplicate of the primary media. To do data securing by utilizing the
star find fundamental device. The prodiscover legal sciences device is most intense PC security
instrument that used to empower the criminology agent to decide the every one of the data on the
PC framework while ensuring the proof and making the evidentiary quality reports. This device has
different highlights and advantages, for example,
It makes the bit stream duplicate of circle to be dissected to protect the first
confirmation.
It effectively look through the whole circle and records including the PC data streams
which is utilized for finish plate scientific investigation [1].
It keep up the multi instrument similarity by composing and perusing the pictures.
It inspect the PC document to give the data uprightness.
It additionally analyse the all record frameworks for most extreme adaptability.
It used the Perl contents to mechanize the examination undertakings.
It personality the record makers to separates the EXIF data from JPEG documents.
It enhances the similarity and precision via robotized the report age in XML design.
It intended to NIST plate imaging instrument to guarantee the high calibre.
It bolster for VM product to run a caught pictures.
2. Data Recovery
Open Pro discover basic Tool.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
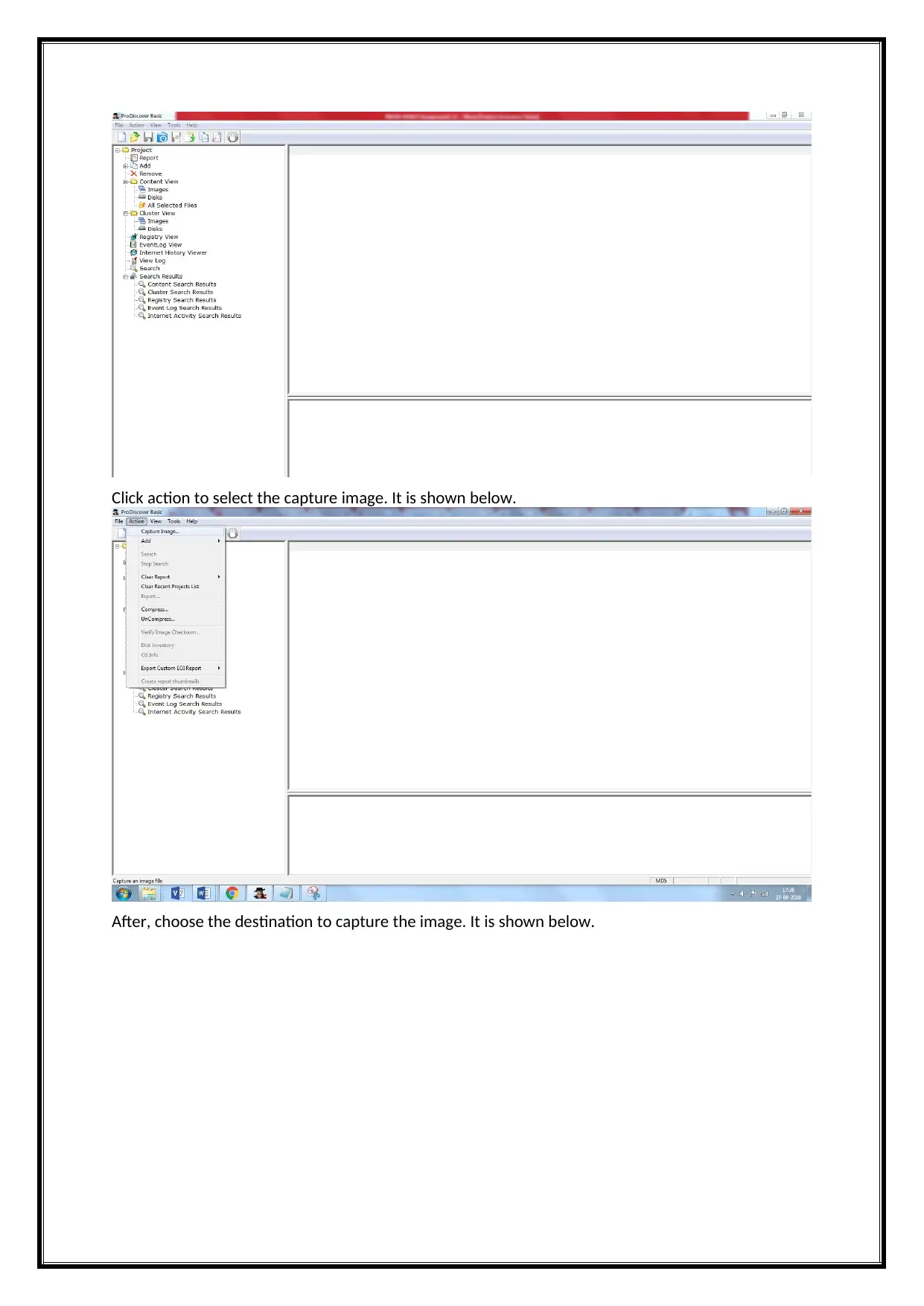
Click action to select the capture image. It is shown below.
After, choose the destination to capture the image. It is shown below.
After, choose the destination to capture the image. It is shown below.
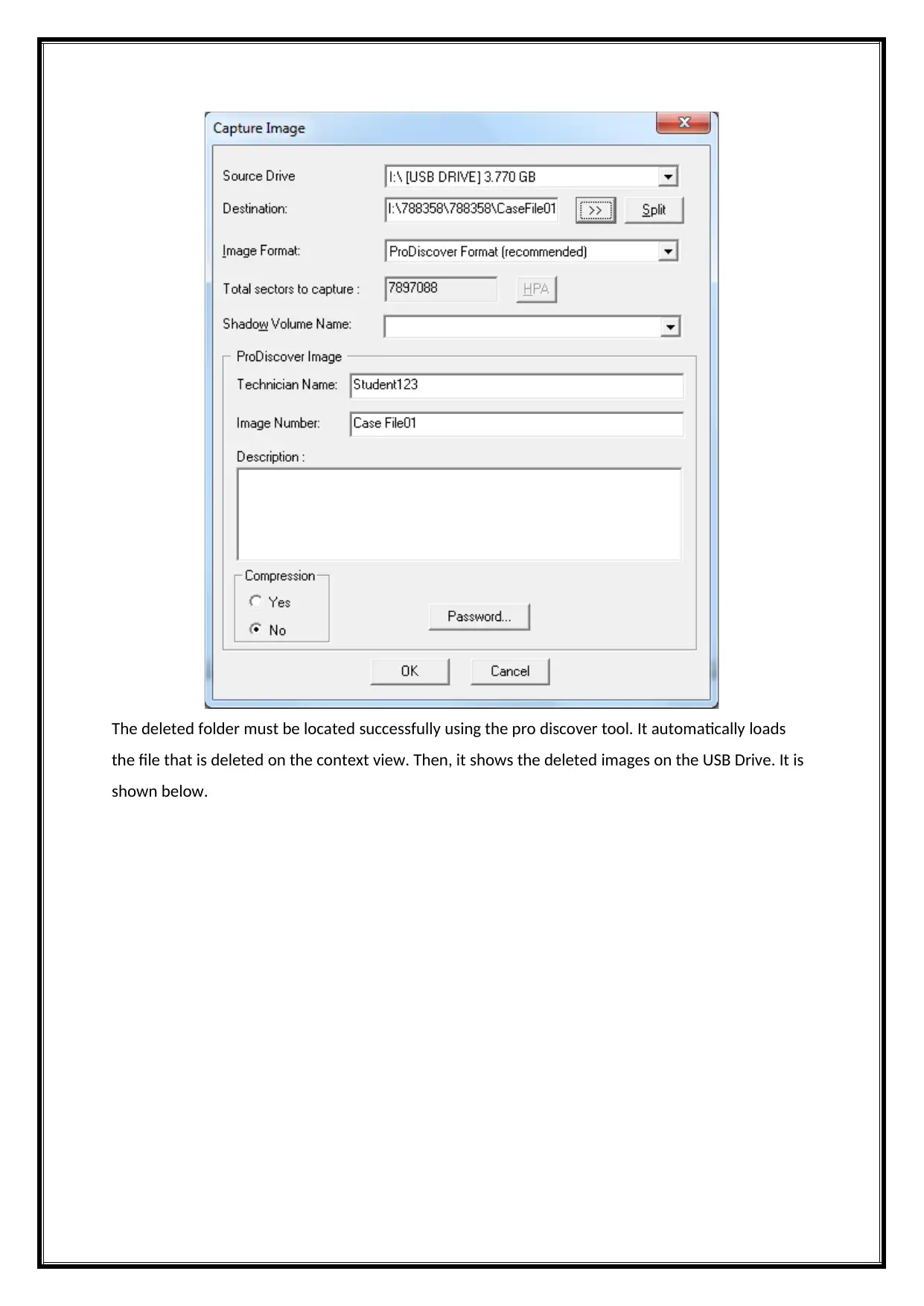
The deleted folder must be located successfully using the pro discover tool. It automatically loads
the file that is deleted on the context view. Then, it shows the deleted images on the USB Drive. It is
shown below.
the file that is deleted on the context view. Then, it shows the deleted images on the USB Drive. It is
shown below.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
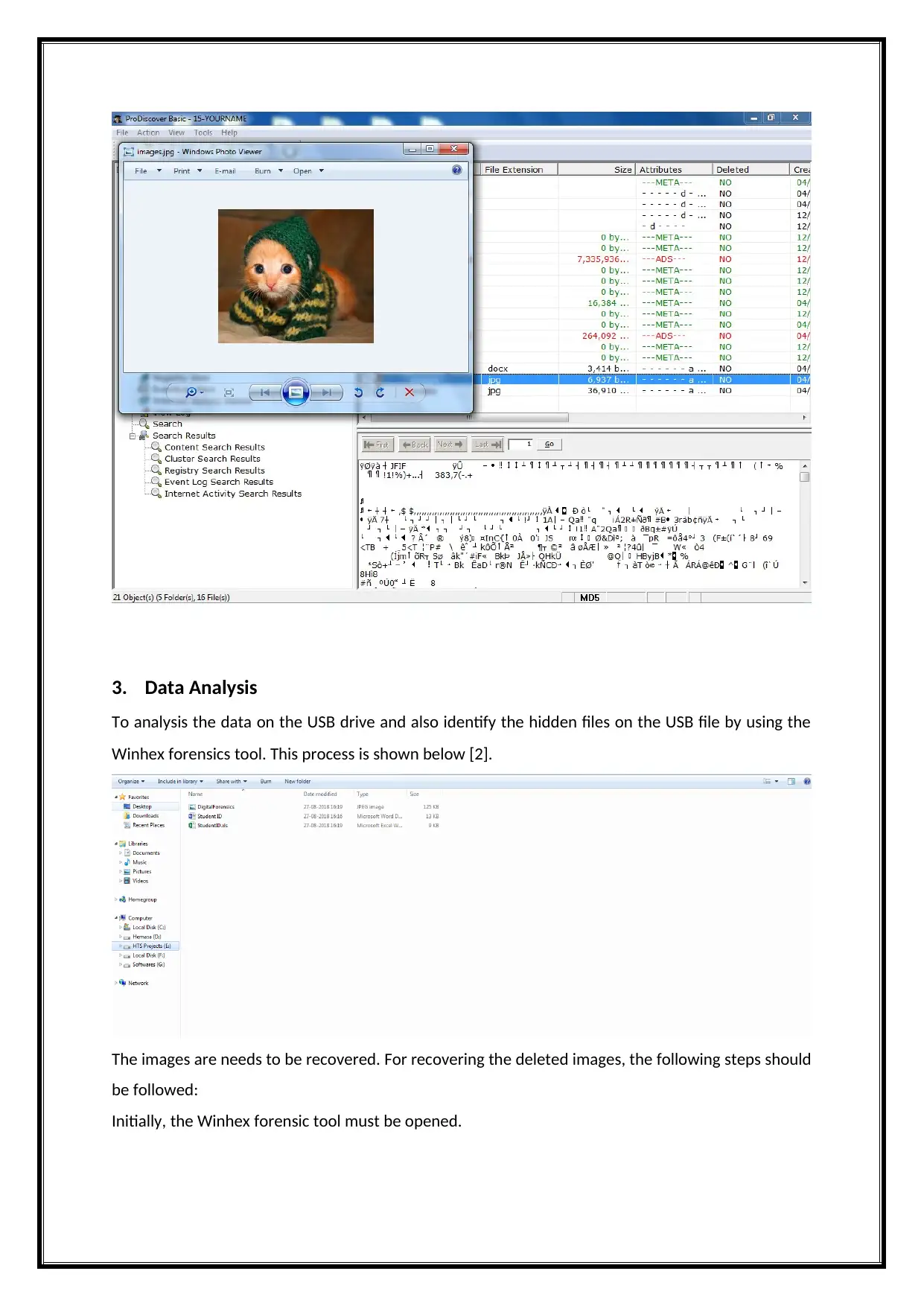
3. Data Analysis
To analysis the data on the USB drive and also identify the hidden files on the USB file by using the
Winhex forensics tool. This process is shown below [2].
The images are needs to be recovered. For recovering the deleted images, the following steps should
be followed:
Initially, the Winhex forensic tool must be opened.
To analysis the data on the USB drive and also identify the hidden files on the USB file by using the
Winhex forensics tool. This process is shown below [2].
The images are needs to be recovered. For recovering the deleted images, the following steps should
be followed:
Initially, the Winhex forensic tool must be opened.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
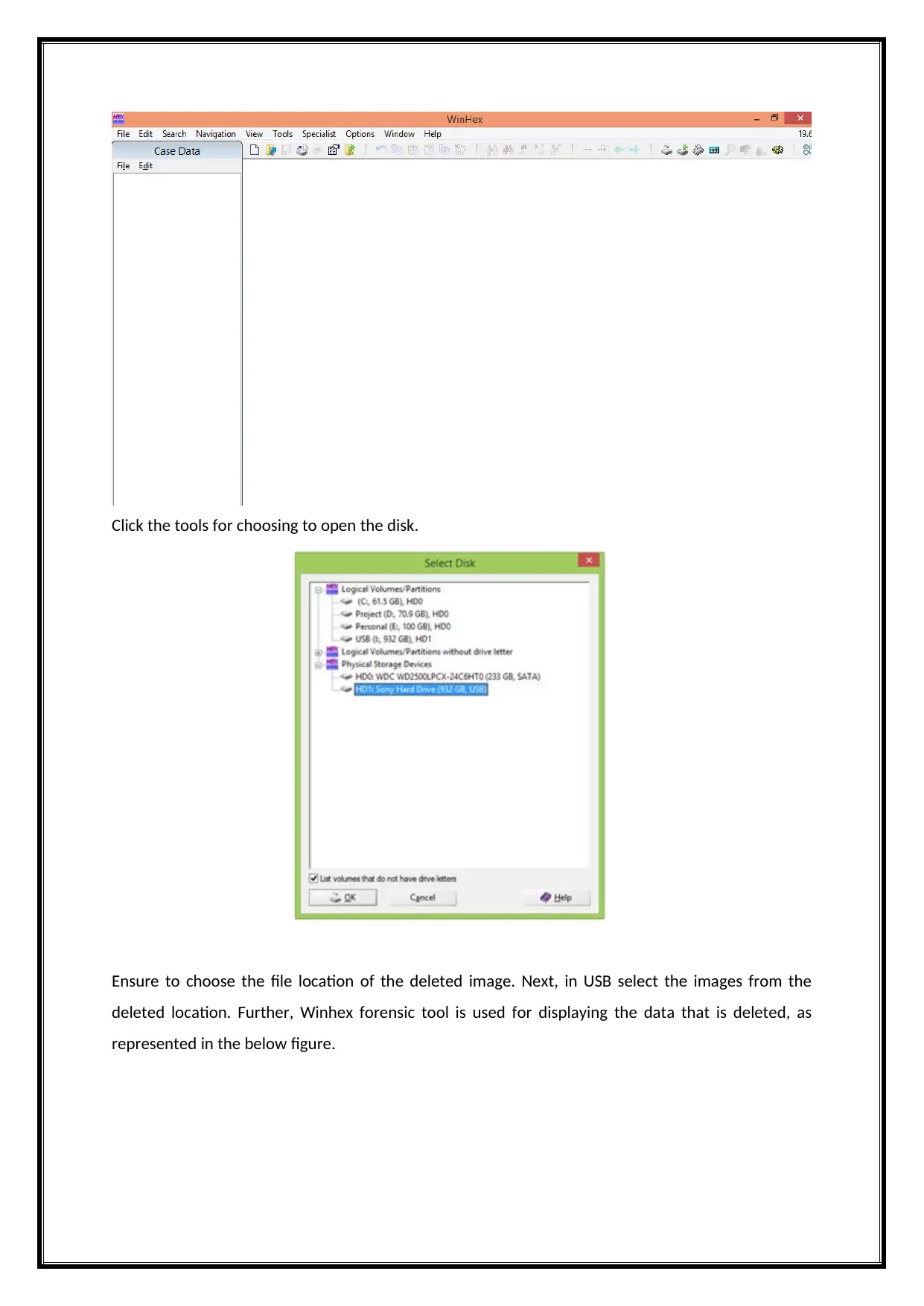
Click the tools for choosing to open the disk.
Ensure to choose the file location of the deleted image. Next, in USB select the images from the
deleted location. Further, Winhex forensic tool is used for displaying the data that is deleted, as
represented in the below figure.
Ensure to choose the file location of the deleted image. Next, in USB select the images from the
deleted location. Further, Winhex forensic tool is used for displaying the data that is deleted, as
represented in the below figure.
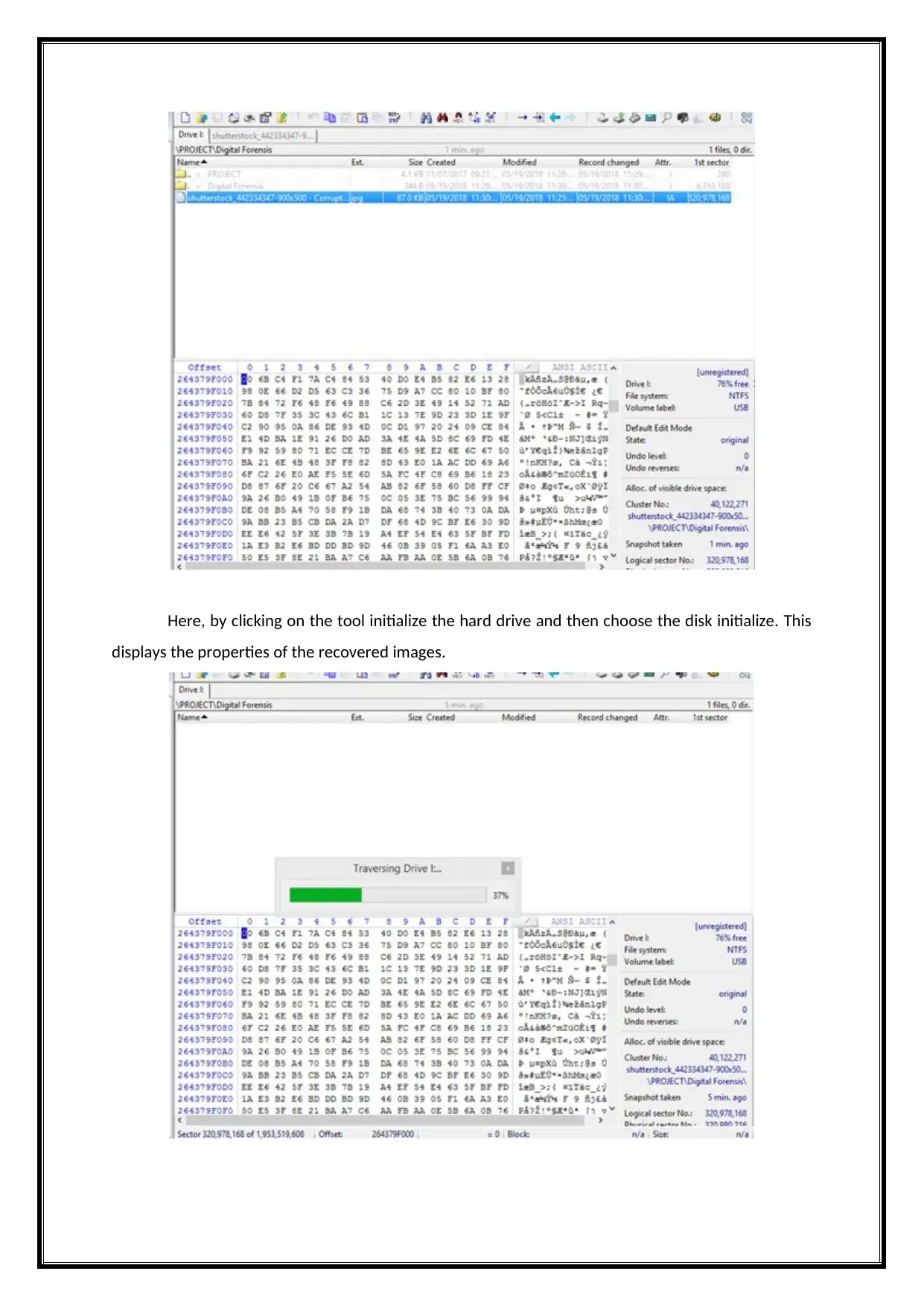
Here, by clicking on the tool initialize the hard drive and then choose the disk initialize. This
displays the properties of the recovered images.
displays the properties of the recovered images.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
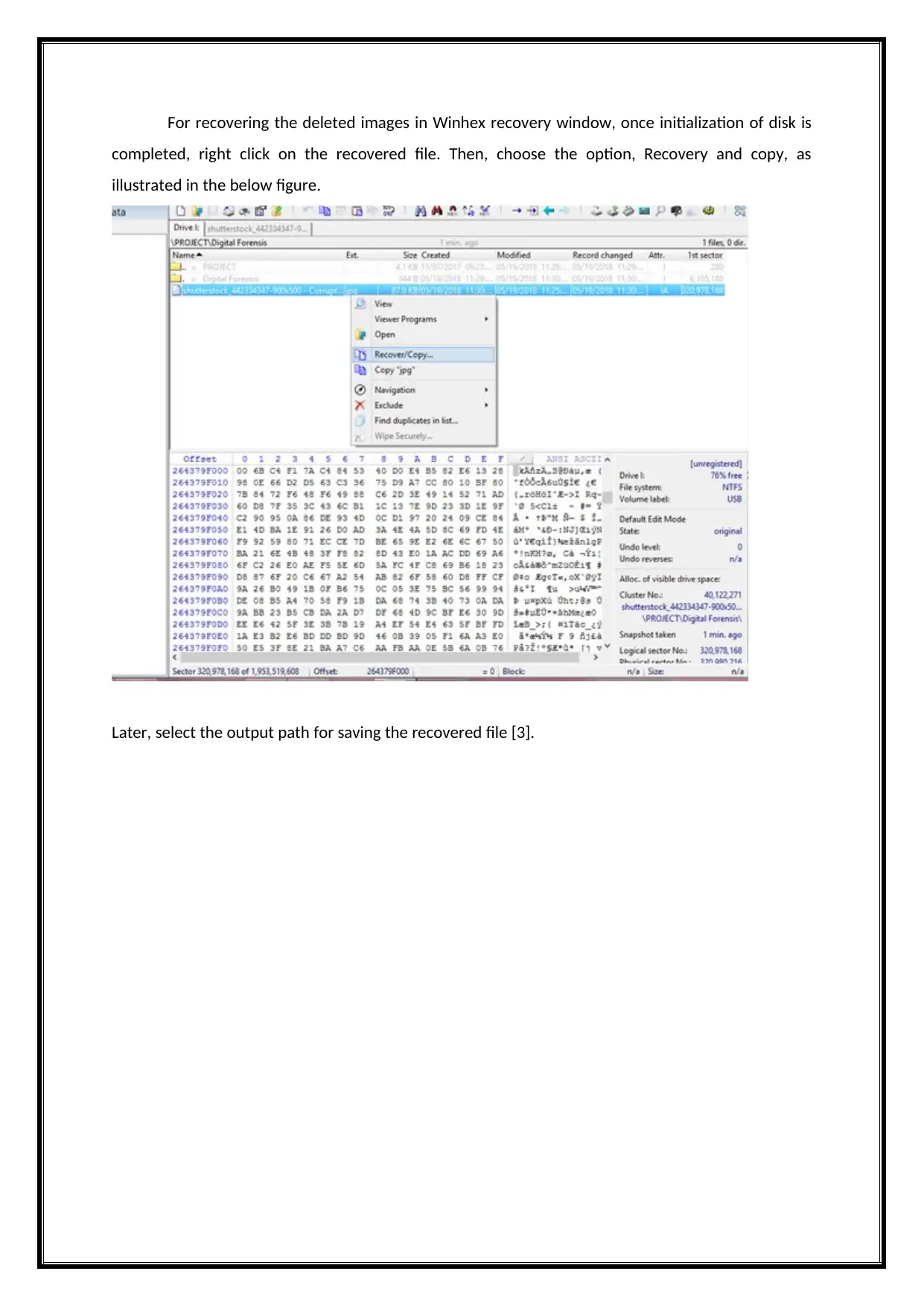
For recovering the deleted images in Winhex recovery window, once initialization of disk is
completed, right click on the recovered file. Then, choose the option, Recovery and copy, as
illustrated in the below figure.
Later, select the output path for saving the recovered file [3].
completed, right click on the recovered file. Then, choose the option, Recovery and copy, as
illustrated in the below figure.
Later, select the output path for saving the recovered file [3].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
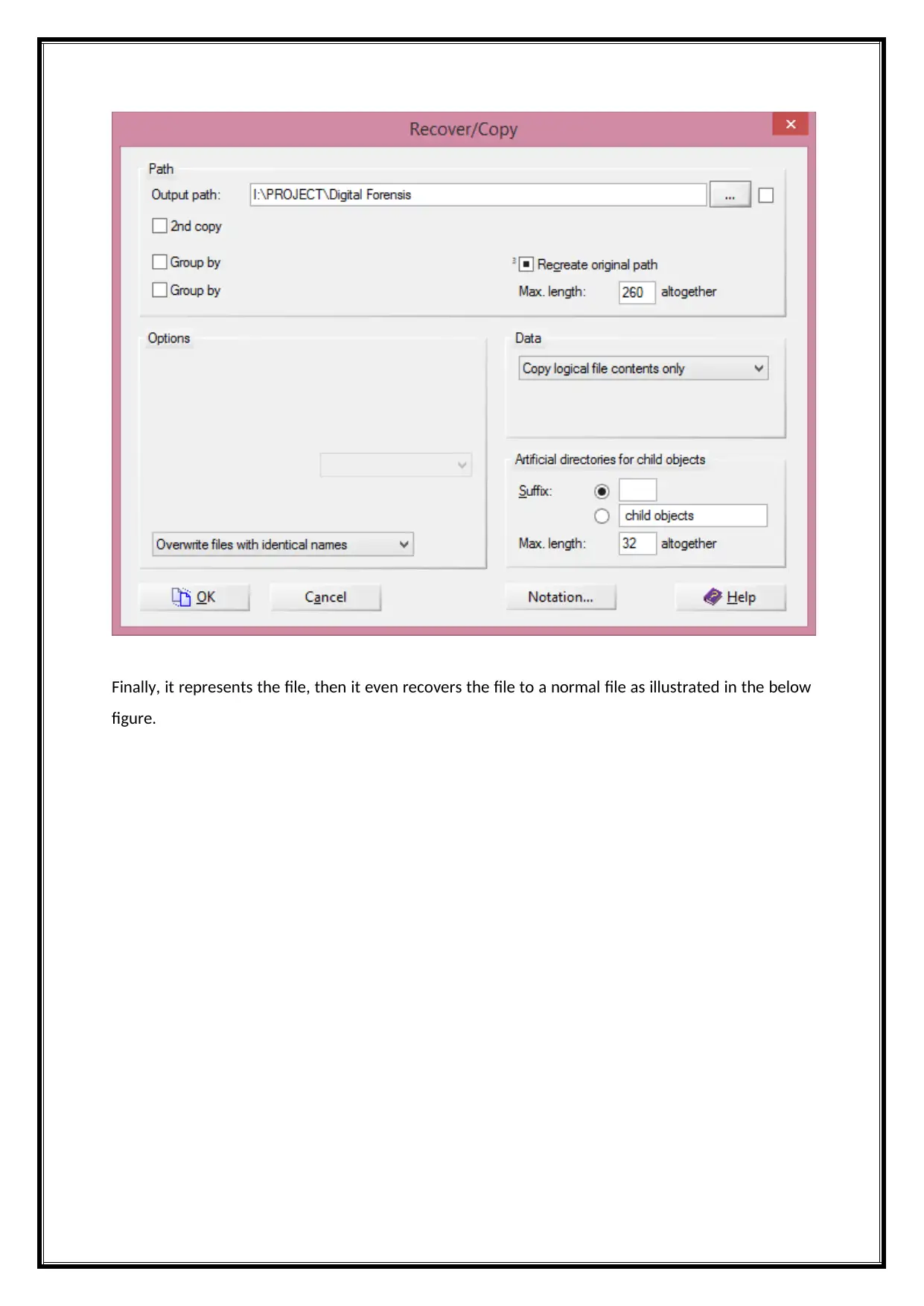
Finally, it represents the file, then it even recovers the file to a normal file as illustrated in the below
figure.
figure.
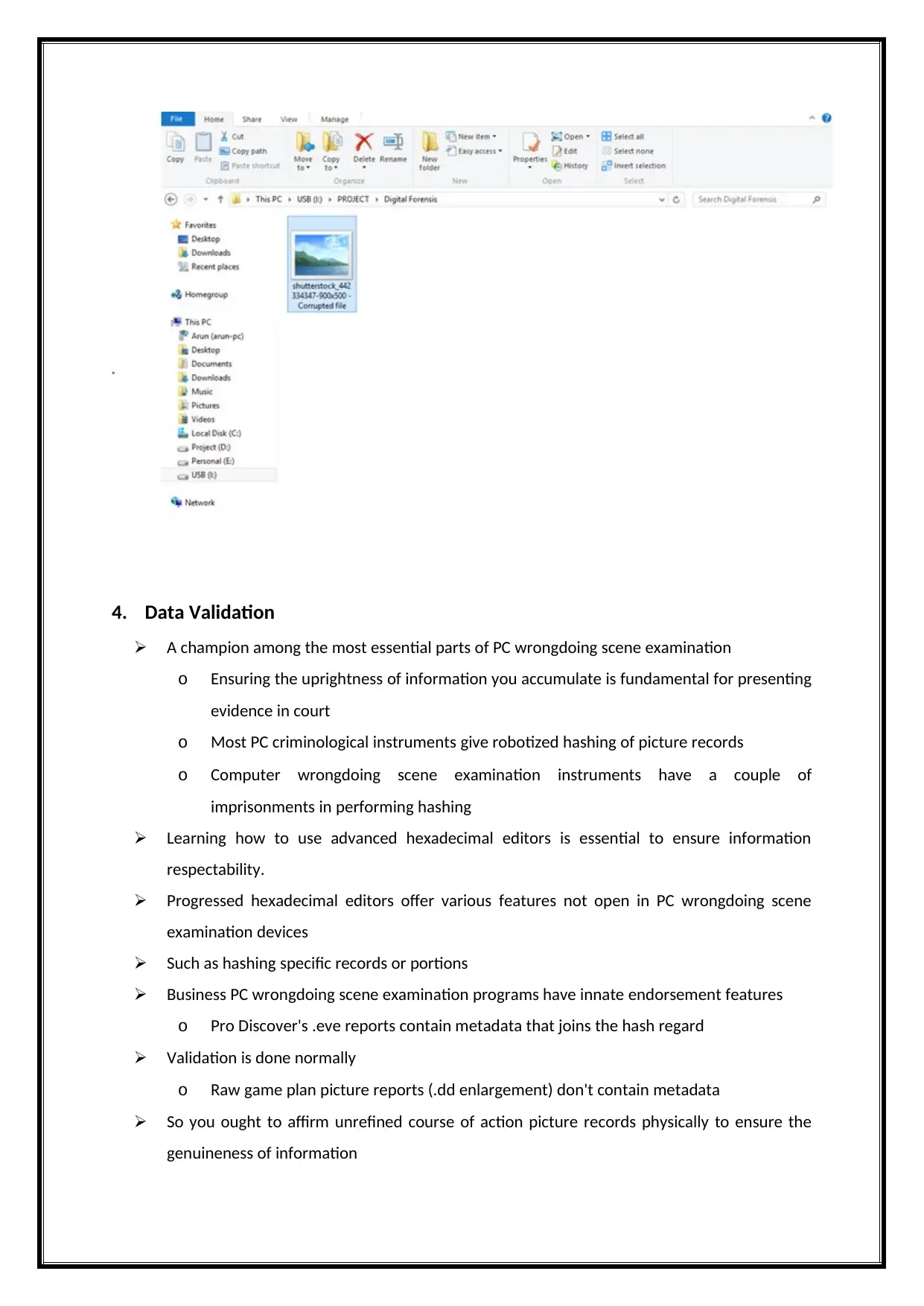
4. Data Validation
A champion among the most essential parts of PC wrongdoing scene examination
o Ensuring the uprightness of information you accumulate is fundamental for presenting
evidence in court
o Most PC criminological instruments give robotized hashing of picture records
o Computer wrongdoing scene examination instruments have a couple of
imprisonments in performing hashing
Learning how to use advanced hexadecimal editors is essential to ensure information
respectability.
Progressed hexadecimal editors offer various features not open in PC wrongdoing scene
examination devices
Such as hashing specific records or portions
Business PC wrongdoing scene examination programs have innate endorsement features
o Pro Discover's .eve reports contain metadata that joins the hash regard
Validation is done normally
o Raw game plan picture reports (.dd enlargement) don't contain metadata
So you ought to affirm unrefined course of action picture records physically to ensure the
genuineness of information
A champion among the most essential parts of PC wrongdoing scene examination
o Ensuring the uprightness of information you accumulate is fundamental for presenting
evidence in court
o Most PC criminological instruments give robotized hashing of picture records
o Computer wrongdoing scene examination instruments have a couple of
imprisonments in performing hashing
Learning how to use advanced hexadecimal editors is essential to ensure information
respectability.
Progressed hexadecimal editors offer various features not open in PC wrongdoing scene
examination devices
Such as hashing specific records or portions
Business PC wrongdoing scene examination programs have innate endorsement features
o Pro Discover's .eve reports contain metadata that joins the hash regard
Validation is done normally
o Raw game plan picture reports (.dd enlargement) don't contain metadata
So you ought to affirm unrefined course of action picture records physically to ensure the
genuineness of information
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



