MN624: Digital Forensics Assignment on Data Acquisition Methods
VerifiedAdded on 2022/09/13
|10
|1033
|15
Report
AI Summary
This report, prepared for the MN624 Digital Forensics course, delves into the crucial aspects of digital investigations. It begins by highlighting the increasing significance of digital forensics in addressing cybercrime, emphasizing the importance of data acquisition, preservation, and analysis. The report then explores the ProDiscover forensic tool, detailing its capabilities in disk capture, analysis, and investigation without altering original data. The core of the report focuses on data acquisition, identifying it as a vital step in collecting crime-related data and ensuring data integrity. Two key data acquisition methods, generating sparse copies and disk image data acquisition, are explained. Furthermore, the report discusses data preservation methods such as drive imaging, hash values, and chain of custody. These methods are essential for maintaining the integrity and admissibility of digital evidence. The report provides a comprehensive overview of digital forensics techniques and tools, offering valuable insights into the investigation process.

Running head: MN624
MN624
Name of the Student
Name of the University
Author Note
MN624
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN624 1
Table of Contents
Digital clues:..............................................................................................................................2
Prodiscover forensics tool:.........................................................................................................2
Data acquisition in digital forensics:..........................................................................................3
Data preservation methods in digital forensics:.........................................................................3
Explain two data acquisition methods for digital forensics:......................................................4
References:.................................................................................................................................5
Table of Contents
Digital clues:..............................................................................................................................2
Prodiscover forensics tool:.........................................................................................................2
Data acquisition in digital forensics:..........................................................................................3
Data preservation methods in digital forensics:.........................................................................3
Explain two data acquisition methods for digital forensics:......................................................4
References:.................................................................................................................................5

2MN624
Digital clues:
Considering the rapid growth of technology it is identified that the significance of
cyber-crime is increasing day by day where it is very essential to identify the reason behind
these types of threats as well as the strategies to cover come from these identified digital
threats.
Digital forensic is such practice by which the law enforcement professionals
investigates any incident of cyber-crime. While analyzing the operation of Digital forensic it
is noticed that the primary reason behind the application of digital forensic is to get a detailed
idea about the occurred incidence by gathering required data. In order to get the detailed idea
about the incident the collected data will be analyzed and followed by the analysis useful
information will be extracted which will help the professionals for investment [1].
While analyzing the procedure of digital forensic it is noticed that digital forensic
practice includes the steps of identification of the crime, collection and preserving the
collected data, analysis of the collected data and preparing a report of the targeted crime.
Prodiscover forensics tool:
ProDiscover forensic tool is one of the most effective tool that is used to assist the digital
forensic professionals. Followed by these identification it is noticed among other digital
forensic tools this is one of the most effective tools as this holds the capabilities of capture
the targeted disk as well as to analyze that tool effectively. Considering these aspects it in
noticed that this tool has several effective features which includes the followings-
Captures the disk.
Analyses the disk.
Create the records from the investigation.
Digital clues:
Considering the rapid growth of technology it is identified that the significance of
cyber-crime is increasing day by day where it is very essential to identify the reason behind
these types of threats as well as the strategies to cover come from these identified digital
threats.
Digital forensic is such practice by which the law enforcement professionals
investigates any incident of cyber-crime. While analyzing the operation of Digital forensic it
is noticed that the primary reason behind the application of digital forensic is to get a detailed
idea about the occurred incidence by gathering required data. In order to get the detailed idea
about the incident the collected data will be analyzed and followed by the analysis useful
information will be extracted which will help the professionals for investment [1].
While analyzing the procedure of digital forensic it is noticed that digital forensic
practice includes the steps of identification of the crime, collection and preserving the
collected data, analysis of the collected data and preparing a report of the targeted crime.
Prodiscover forensics tool:
ProDiscover forensic tool is one of the most effective tool that is used to assist the digital
forensic professionals. Followed by these identification it is noticed among other digital
forensic tools this is one of the most effective tools as this holds the capabilities of capture
the targeted disk as well as to analyze that tool effectively. Considering these aspects it in
noticed that this tool has several effective features which includes the followings-
Captures the disk.
Analyses the disk.
Create the records from the investigation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3MN624
Effectively investigates the data by not impacting the original data present in the
targeted disk [2].
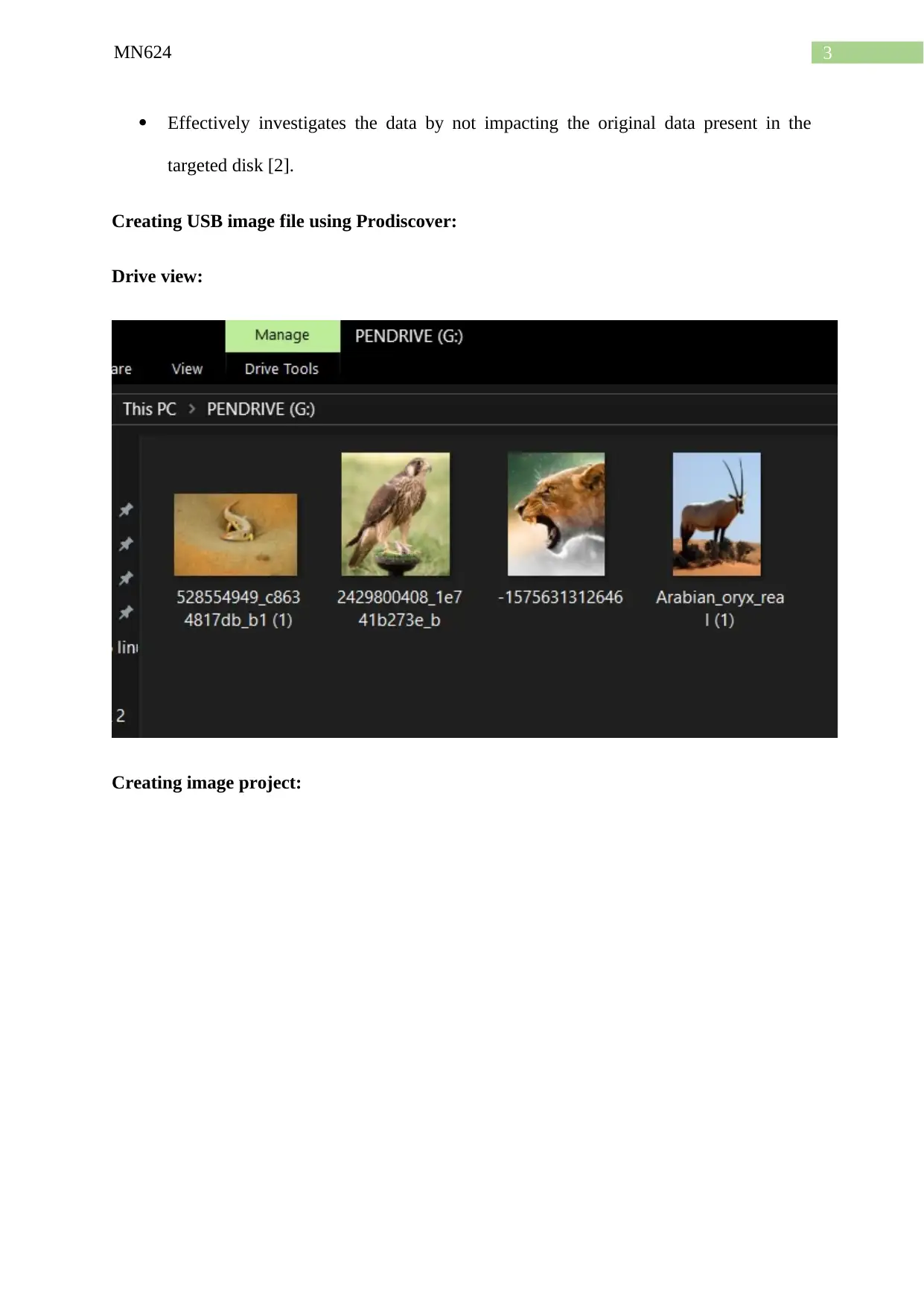
Creating USB image file using Prodiscover:
Drive view:
Creating image project:
Effectively investigates the data by not impacting the original data present in the
targeted disk [2].
Creating USB image file using Prodiscover:
Drive view:
Creating image project:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4MN624
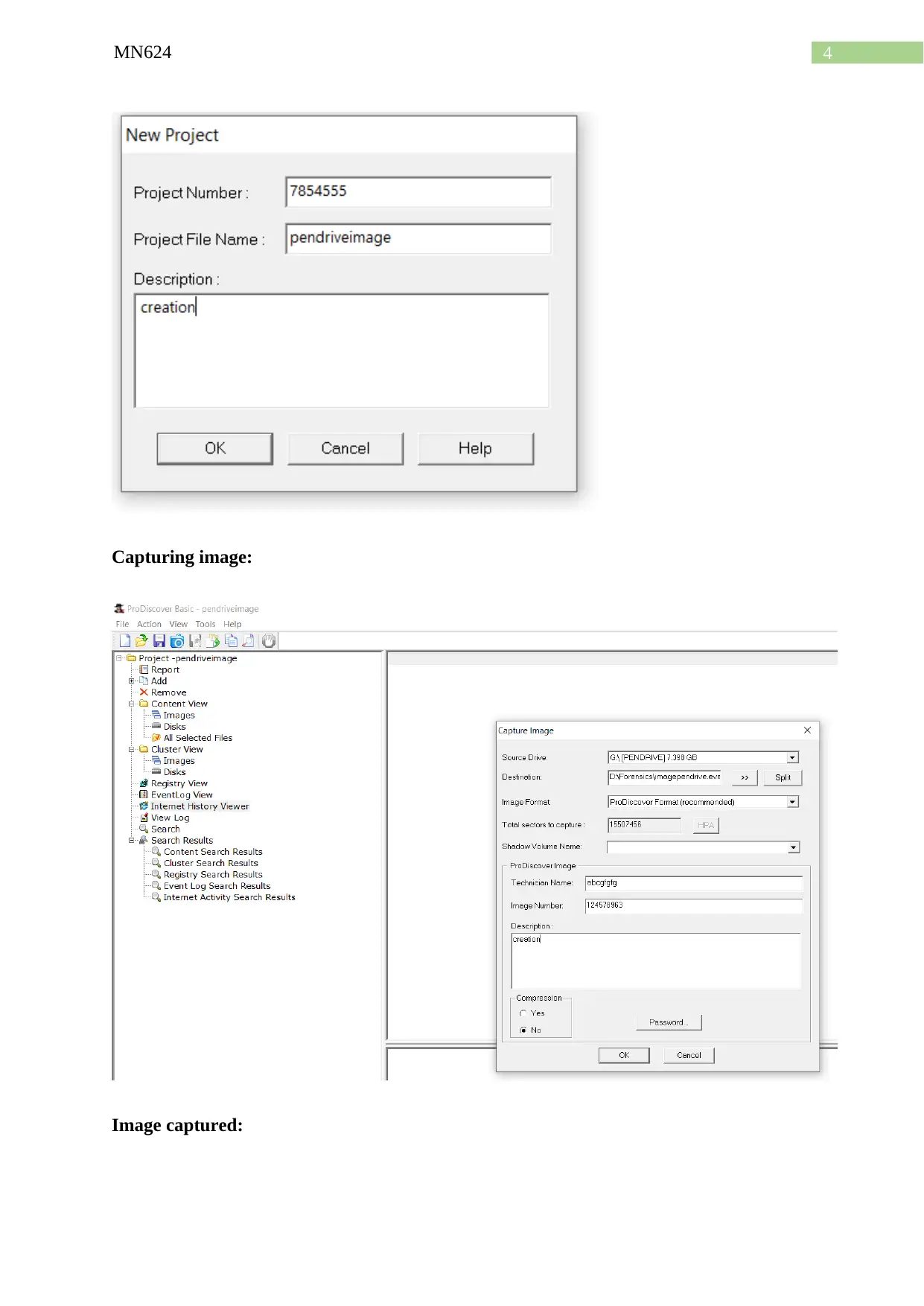
Capturing image:
Image captured:
Capturing image:
Image captured:
5MN624
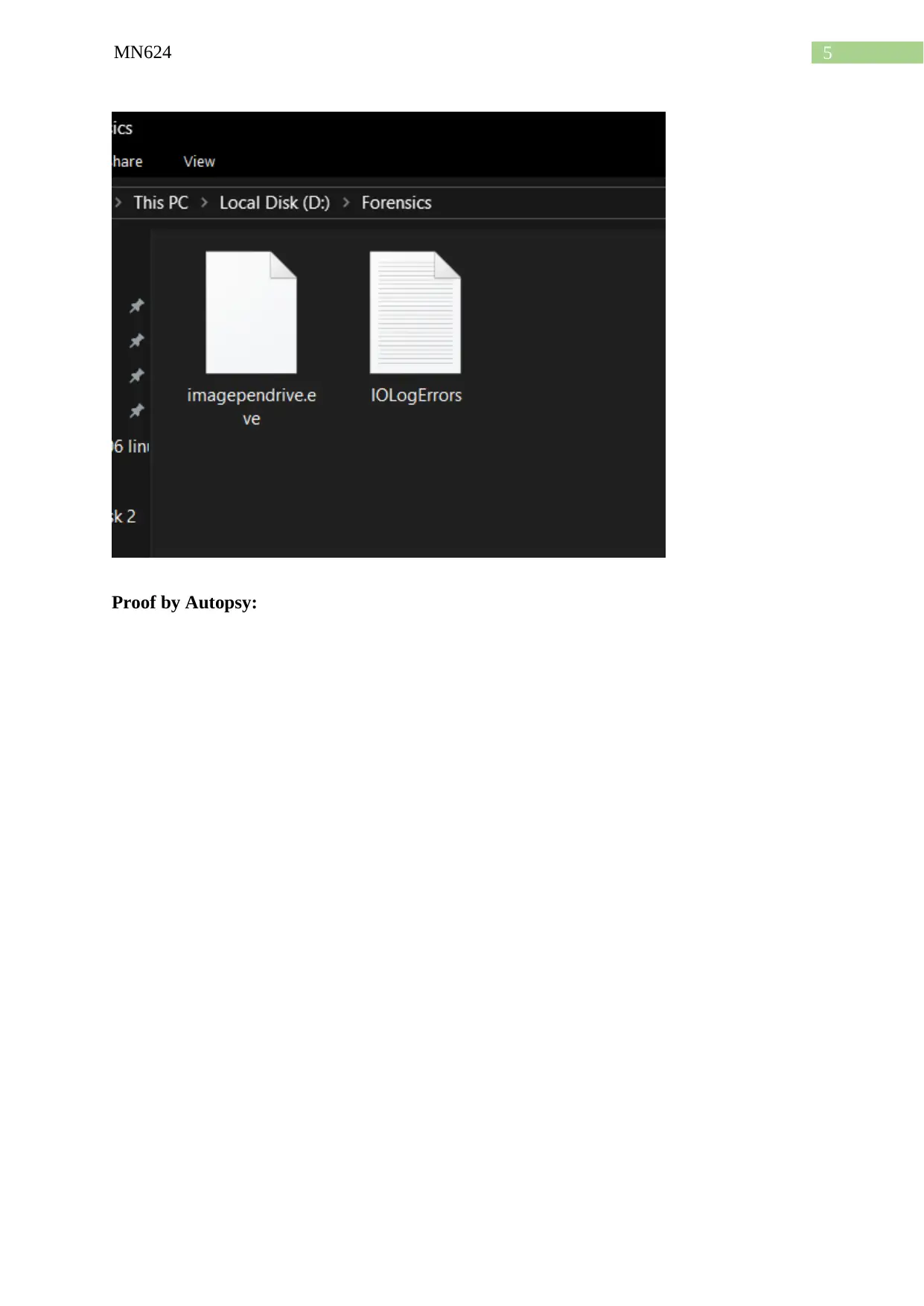
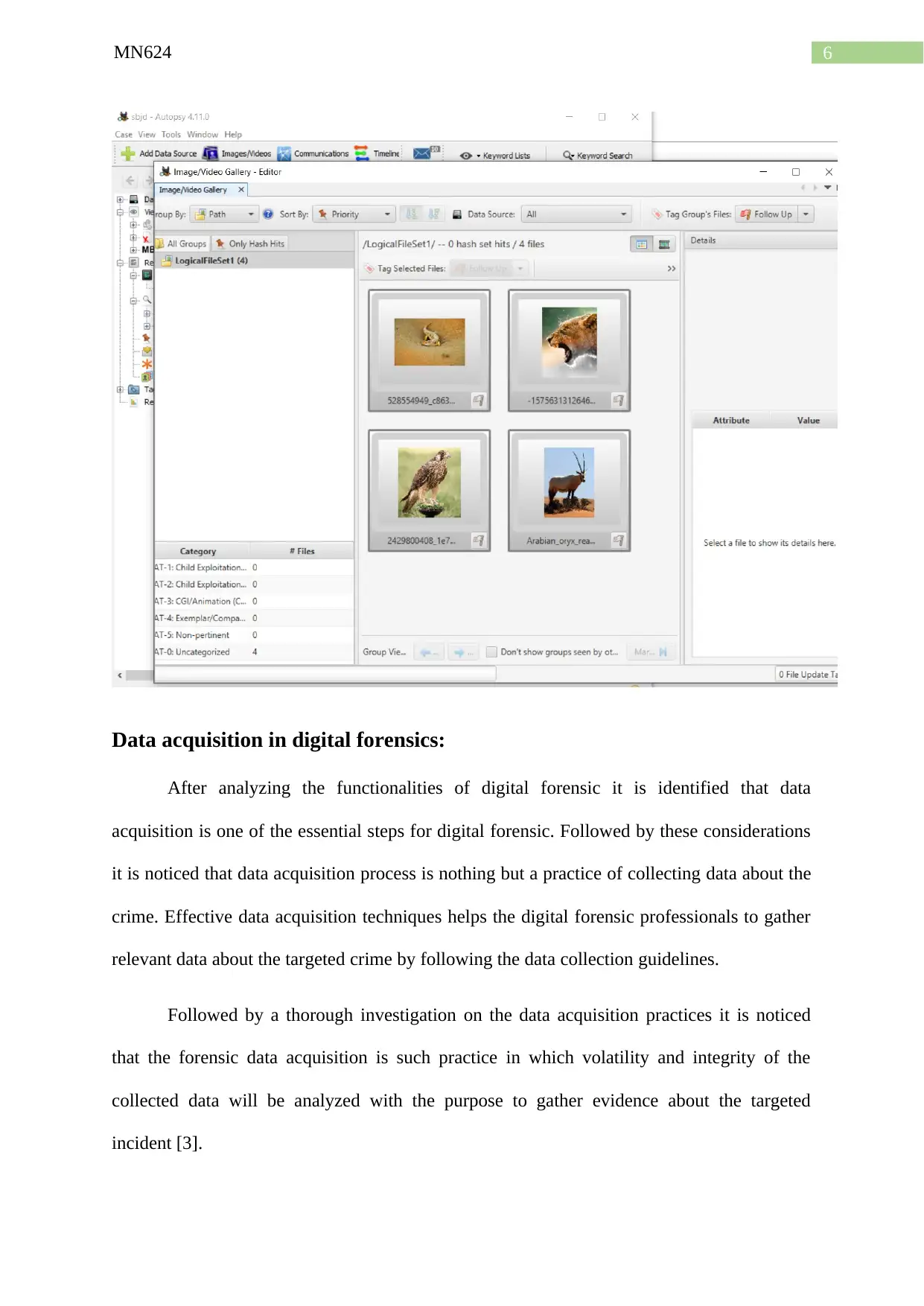
Proof by Autopsy:
Proof by Autopsy:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6MN624
Data acquisition in digital forensics:
After analyzing the functionalities of digital forensic it is identified that data
acquisition is one of the essential steps for digital forensic. Followed by these considerations
it is noticed that data acquisition process is nothing but a practice of collecting data about the
crime. Effective data acquisition techniques helps the digital forensic professionals to gather
relevant data about the targeted crime by following the data collection guidelines.
Followed by a thorough investigation on the data acquisition practices it is noticed
that the forensic data acquisition is such practice in which volatility and integrity of the
collected data will be analyzed with the purpose to gather evidence about the targeted
incident [3].
Data acquisition in digital forensics:
After analyzing the functionalities of digital forensic it is identified that data
acquisition is one of the essential steps for digital forensic. Followed by these considerations
it is noticed that data acquisition process is nothing but a practice of collecting data about the
crime. Effective data acquisition techniques helps the digital forensic professionals to gather
relevant data about the targeted crime by following the data collection guidelines.
Followed by a thorough investigation on the data acquisition practices it is noticed
that the forensic data acquisition is such practice in which volatility and integrity of the
collected data will be analyzed with the purpose to gather evidence about the targeted
incident [3].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MN624
Data acquisition technique of digital forensic also helps to protect the digital evidence
by copying the actual data into a duplicate folder in order to retain the gathered data
whenever it is required, this process reduces the threat of data loss and improves data
integrity.
Data preservation methods in digital forensics:
Followed by a thorough investigation on the application of digital forensic it is
noticed that data preservation is one of the most effective functionality of digital forensic
since, by using this process the examiner will be able to collect and store the digital evidence.
Considering these aspects it is noticed that drive imaging, hash value as well as chain of
custody are the three effective data preservation method which helps to enhance the
effectiveness of digital forensic.
Drive Imaging- is such practice in which the digital evidences are stored in a form of a
duplicate file which helps to retain the data easily when required [4].
Hash value- data preservation technique is also one of the effective process of storing the
data by using the cryptographic hash values such as SHA-1, MD5. One of the primary
objective of using this method is that hash values are very easy to represent and acquiesce
into the court of law.
Chain of Custody- is also one of the effective data preservation process in which the
examiner investigates the data and store them into the form of hand paper which consists of
all of the transmission details of those data.
Explain two data acquisition methods for digital forensics:
After completion of the above discussion it is noticed that digital forensic requires
effective data acquisition methods which will help to collect the digital evidence. Considering
Data acquisition technique of digital forensic also helps to protect the digital evidence
by copying the actual data into a duplicate folder in order to retain the gathered data
whenever it is required, this process reduces the threat of data loss and improves data
integrity.
Data preservation methods in digital forensics:
Followed by a thorough investigation on the application of digital forensic it is
noticed that data preservation is one of the most effective functionality of digital forensic
since, by using this process the examiner will be able to collect and store the digital evidence.
Considering these aspects it is noticed that drive imaging, hash value as well as chain of
custody are the three effective data preservation method which helps to enhance the
effectiveness of digital forensic.
Drive Imaging- is such practice in which the digital evidences are stored in a form of a
duplicate file which helps to retain the data easily when required [4].
Hash value- data preservation technique is also one of the effective process of storing the
data by using the cryptographic hash values such as SHA-1, MD5. One of the primary
objective of using this method is that hash values are very easy to represent and acquiesce
into the court of law.
Chain of Custody- is also one of the effective data preservation process in which the
examiner investigates the data and store them into the form of hand paper which consists of
all of the transmission details of those data.
Explain two data acquisition methods for digital forensics:
After completion of the above discussion it is noticed that digital forensic requires
effective data acquisition methods which will help to collect the digital evidence. Considering

8MN624
these aspect two methods has been identified which includes the generation of sparse copy
and image data acquisition.
Generating sparse copy from digital folder is one of the effective data acquisition method
which is also capable to gathering the erased data as well.
Generation of disk data file acquisition is also one of the effective data acquisition process
in which the examiner will be able to copy the actual data and store it in different folder for
further use.
these aspect two methods has been identified which includes the generation of sparse copy
and image data acquisition.
Generating sparse copy from digital folder is one of the effective data acquisition method
which is also capable to gathering the erased data as well.
Generation of disk data file acquisition is also one of the effective data acquisition process
in which the examiner will be able to copy the actual data and store it in different folder for
further use.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9MN624
References:
[1] G.H. Carlton and G.C. Kessler 2018. Disconnects of Specialized Mobile Digital Forensics
within the Generalized Field of Digital Forensic Science. International Journal of
Interdisciplinary Telecommunications and Networking (IJITN), 10(3), pp.62-65.
[2] L. Chen, H. Takabi and N.A. Le-Khac 2019. Security, Privacy, and Digital Forensics in
the Cloud. John Wiley & Sons.
[3] K. Conlan, I. Baggili and F. Breitinger 2016. Anti-forensics: Furthering digital forensic
science through a new extended, granular taxonomy. Digital investigation, 18, pp.S66-S75.
[4] S.C. Sathe and N.M. Dongre 2018, January. Data acquisition techniques in mobile
forensics. In 2018 2nd International Conference on Inventive Systems and Control
(ICISC) (pp. 280-286). IEEE.
References:
[1] G.H. Carlton and G.C. Kessler 2018. Disconnects of Specialized Mobile Digital Forensics
within the Generalized Field of Digital Forensic Science. International Journal of
Interdisciplinary Telecommunications and Networking (IJITN), 10(3), pp.62-65.
[2] L. Chen, H. Takabi and N.A. Le-Khac 2019. Security, Privacy, and Digital Forensics in
the Cloud. John Wiley & Sons.
[3] K. Conlan, I. Baggili and F. Breitinger 2016. Anti-forensics: Furthering digital forensic
science through a new extended, granular taxonomy. Digital investigation, 18, pp.S66-S75.
[4] S.C. Sathe and N.M. Dongre 2018, January. Data acquisition techniques in mobile
forensics. In 2018 2nd International Conference on Inventive Systems and Control
(ICISC) (pp. 280-286). IEEE.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





