MN692 Capstone: Network Intrusion Detection System with SNORT Report
VerifiedAdded on 2023/06/11
|51
|9826
|455
Report
AI Summary
This report presents a detailed study and implementation of a Network Intrusion Detection System (NIDS) using Snort. It covers the project's design, including a literature review, objectives, and detailed design aspects such as weekly activities, roles and responsibilities, Gantt chart, and project methodology. The report further delves into the implementation phase, discussing software and hardware requirements, research on malware attacks, and the installation and configuration of Snort. Testing, troubleshooting, and results, including ping scan results and verification of Snort intrusion detection, are thoroughly documented. A discussion and analysis section interprets the findings, concluding with insights into the effectiveness of the implemented NIDS. The project aims to successfully detect malware and inform the system about malicious traffic using various tools, contributing to enhanced network security.

MN692 Capstone Project
Network intrusion detection system
Final Report
Student Names
Student IDs
School of IT and Engineering
Trimester x 201x
Network intrusion detection system
Final Report
Student Names
Student IDs
School of IT and Engineering
Trimester x 201x
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN692 Capstone Project Report Page 2 of 51
Table of Contents
Acknowledgment.......................................................................................................................3
1 Abstract..............................................................................................................................4
2 Glossary and Abbreviations...............................................................................................6
1. Introduction........................................................................................................................7
2. Project Detailed Design......................................................................................................8
2.1 Literature Review......................................................................................................12
2.2 Objectives of the Project...........................................................................................12
2.3 Detailed Design.........................................................................................................13
2.3.1 Design and implementation.....................................................................................13
2.3.2 Table of weekly Activities for MN692...................................................................14
2.3.3 Roles& Responsibilities of each team member......................................................15
2.3.4 Gantt Chart..............................................................................................................18
2.3.5 Project methodology...............................................................................................26
Figure 14: Block diagram of NIDS..................................................................................27
3 Project Implementation and Evaluation...........................................................................27
3.1 Implementation..........................................................................................................27
3.1.1 Software Requirements......................................................................................28
3.1.2 Hardware Requirements.....................................................................................29
3.1.3 Research graphs of malware attacks..................................................................29
3.1.4 Installing Snort...................................................................................................30
3.2 Testing and troubleshooting......................................................................................32
3.3 Results.......................................................................................................................38
Ping scan results that are stored in snort log............................................................................41
Verification of snort intrusion..................................................................................................42
3.4 Discussion and analysis.............................................................................................42
3 Conclusion........................................................................................................................51
References................................................................................................................................52
Network Intrusion Detection System Using SNORT
Table of Contents
Acknowledgment.......................................................................................................................3
1 Abstract..............................................................................................................................4
2 Glossary and Abbreviations...............................................................................................6
1. Introduction........................................................................................................................7
2. Project Detailed Design......................................................................................................8
2.1 Literature Review......................................................................................................12
2.2 Objectives of the Project...........................................................................................12
2.3 Detailed Design.........................................................................................................13
2.3.1 Design and implementation.....................................................................................13
2.3.2 Table of weekly Activities for MN692...................................................................14
2.3.3 Roles& Responsibilities of each team member......................................................15
2.3.4 Gantt Chart..............................................................................................................18
2.3.5 Project methodology...............................................................................................26
Figure 14: Block diagram of NIDS..................................................................................27
3 Project Implementation and Evaluation...........................................................................27
3.1 Implementation..........................................................................................................27
3.1.1 Software Requirements......................................................................................28
3.1.2 Hardware Requirements.....................................................................................29
3.1.3 Research graphs of malware attacks..................................................................29
3.1.4 Installing Snort...................................................................................................30
3.2 Testing and troubleshooting......................................................................................32
3.3 Results.......................................................................................................................38
Ping scan results that are stored in snort log............................................................................41
Verification of snort intrusion..................................................................................................42
3.4 Discussion and analysis.............................................................................................42
3 Conclusion........................................................................................................................51
References................................................................................................................................52
Network Intrusion Detection System Using SNORT

MN692 Capstone Project Report Page 3 of 51
Acknowledgment
We like to express our gratitude to our respected A/Prof Savitri Bevinakoppa and our
supervisor, lecturer Dr. Ammar Alazab. Most significantly to our industry client Dr. Robert
Layton who provided the best guidance throughout our project on Network Intrusion
Detection System, Which aided to execute the project successfully without any hurdles, by
neutralizing and detecting the attacks on the system with different techniques.
We are thankful to our mentors.
Signatures of students:
Network Intrusion Detection System Using SNORT
Acknowledgment
We like to express our gratitude to our respected A/Prof Savitri Bevinakoppa and our
supervisor, lecturer Dr. Ammar Alazab. Most significantly to our industry client Dr. Robert
Layton who provided the best guidance throughout our project on Network Intrusion
Detection System, Which aided to execute the project successfully without any hurdles, by
neutralizing and detecting the attacks on the system with different techniques.
We are thankful to our mentors.
Signatures of students:
Network Intrusion Detection System Using SNORT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

MN692 Capstone Project Report Page 4 of 51
1 Abstract
The Internet and computer networks are increasingly exposed to security threats.
When there are new types of attacks that occur constantly, the development of flexible and
adaptive security-oriented approaches is a serious problem. In this context, a network based
on anomaly intrusion detection methods are a valuable technology for protecting target
systems and networks against malicious activities. Intrusion detection systems (IDS) are
based on the belief that the behaviour of an attacker will be markedly different from that of a
legitimate user and that many unauthorized actions can be detected [1]. Typically, IDS uses
statistical anomalies and abuse patterns based on rules to detect intrusions. A number of IDS
prototypes were developed in several institutions and some of them were also deployed on an
experimental basis. However, despite the variety of such methods security tools that include
the detection of anomalies functionality is just beginning to emerge, and a number of
important problems remain unsolved. In this process, the system tries to neutralize the attacks
that are being happened. IDS are being installed in the network rather than being installed in
individual hosts to provide security to the system. Using signature and anomaly-based
detection the attacks are being detected and stopped. Snort is the major IDS tool which
detects the attack successfully by installing and configuring it in a network. The system
provides a continuous response to the intrusions that happen [2].
The intention of the project is to implement a NIDS successfully in detecting the
malware and inform the system about the incoming malicious traffic using different tools.
Network Intrusion Detection System Using SNORT
1 Abstract
The Internet and computer networks are increasingly exposed to security threats.
When there are new types of attacks that occur constantly, the development of flexible and
adaptive security-oriented approaches is a serious problem. In this context, a network based
on anomaly intrusion detection methods are a valuable technology for protecting target
systems and networks against malicious activities. Intrusion detection systems (IDS) are
based on the belief that the behaviour of an attacker will be markedly different from that of a
legitimate user and that many unauthorized actions can be detected [1]. Typically, IDS uses
statistical anomalies and abuse patterns based on rules to detect intrusions. A number of IDS
prototypes were developed in several institutions and some of them were also deployed on an
experimental basis. However, despite the variety of such methods security tools that include
the detection of anomalies functionality is just beginning to emerge, and a number of
important problems remain unsolved. In this process, the system tries to neutralize the attacks
that are being happened. IDS are being installed in the network rather than being installed in
individual hosts to provide security to the system. Using signature and anomaly-based
detection the attacks are being detected and stopped. Snort is the major IDS tool which
detects the attack successfully by installing and configuring it in a network. The system
provides a continuous response to the intrusions that happen [2].
The intention of the project is to implement a NIDS successfully in detecting the
malware and inform the system about the incoming malicious traffic using different tools.
Network Intrusion Detection System Using SNORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN692 Capstone Project Report Page 5 of 51
2 Glossary and Abbreviations
NIDS: Network Intrusion Detection System
IDS: Intrusion Detection System
DDoS: Distributed Denial of Service
SVM: Support Vector Machine
STP: Spanning Tree Protocol
WEKA: Waikato environment for knowledge and analysis
QP: Quadratic programming
SMO: Sequential minimal optimization
NIDS: Network intrusion detection system
Network Intrusion Detection System Using SNORT
2 Glossary and Abbreviations
NIDS: Network Intrusion Detection System
IDS: Intrusion Detection System
DDoS: Distributed Denial of Service
SVM: Support Vector Machine
STP: Spanning Tree Protocol
WEKA: Waikato environment for knowledge and analysis
QP: Quadratic programming
SMO: Sequential minimal optimization
NIDS: Network intrusion detection system
Network Intrusion Detection System Using SNORT

MN692 Capstone Project Report Page 6 of 51
1. Introduction
Intrusion Detection Systems are security tools that, like other measures such as
antivirus software, firewalls, and access control schemes, are intended to strengthen the
security of information and communication systems. Over the years, several IDS approaches
have been proposed in literature since the creation of this technology, two highly relevant
works in this direction reddening [3].
An intrusion detection system (IDS) can be considered an application which is
associated with monitoring a network or systems for detecting various kinds of malicious
activity or policy violations. Various malicious activities or violations are typically reported
either to the administrator or are generally collected centrally by making use of a security
information and event management (SIEM) system. The SIEM system is associated with
combining the outputs from multiple sources, which is followed by the usage of the alarm
filtering techniques in order to distinguish the various type of malicious activity from the
alarms that are false.
There exist several types of IDS, and this scopes from a single computer to a
widespread network. The most common Type of IDS includes the “network intrusion
detection systems” (NIDS) and “host-based intrusion detection systems” (HIDS). The system
which is associated with monitoring the important operating system files can be considered as
an example of a HIDS, whereas a system which is associated with the analysing the network
traffic which is incoming can be considered as an example of a NIDS. The IDS can be
classified according to the detection approach that is used amongst which the most well-
known variants include the signature-based detection or recognizing the bad patterns, such as
malware and anomaly-based detection or the detecting deviations from a model of "good"
traffic, which often relies on machine learning. Some IDS have the ability to respond to
Network Intrusion Detection System Using SNORT
1. Introduction
Intrusion Detection Systems are security tools that, like other measures such as
antivirus software, firewalls, and access control schemes, are intended to strengthen the
security of information and communication systems. Over the years, several IDS approaches
have been proposed in literature since the creation of this technology, two highly relevant
works in this direction reddening [3].
An intrusion detection system (IDS) can be considered an application which is
associated with monitoring a network or systems for detecting various kinds of malicious
activity or policy violations. Various malicious activities or violations are typically reported
either to the administrator or are generally collected centrally by making use of a security
information and event management (SIEM) system. The SIEM system is associated with
combining the outputs from multiple sources, which is followed by the usage of the alarm
filtering techniques in order to distinguish the various type of malicious activity from the
alarms that are false.
There exist several types of IDS, and this scopes from a single computer to a
widespread network. The most common Type of IDS includes the “network intrusion
detection systems” (NIDS) and “host-based intrusion detection systems” (HIDS). The system
which is associated with monitoring the important operating system files can be considered as
an example of a HIDS, whereas a system which is associated with the analysing the network
traffic which is incoming can be considered as an example of a NIDS. The IDS can be
classified according to the detection approach that is used amongst which the most well-
known variants include the signature-based detection or recognizing the bad patterns, such as
malware and anomaly-based detection or the detecting deviations from a model of "good"
traffic, which often relies on machine learning. Some IDS have the ability to respond to
Network Intrusion Detection System Using SNORT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

MN692 Capstone Project Report Page 7 of 51
detected intrusions. Systems with response capabilities are typically referred to as an
intrusion prevention system.
Network intrusion detection systems (NIDS) has been placed at a strategic point or
points inside a network for the purpose of monitoring the traffic that is generally towards or
from all devices connected with the network. This is generally associated with performing an
analysis of the traffic that is passing on the entire subnet, which is followed by matching of
the traffic which is generally passed on the subnets to the library of known attacks. After the
identification of the attack or abnormal behaviour is done, then an alert is sent to the
administrator. (An example of a NIDS would be installing it on the subnet where firewalls are
located in order to see if someone is trying to break into the firewall. Ideally one would scan
all inbound and outbound traffic, however doing so might create a bottleneck that would
impair the overall speed of the network.).Some of the common tools used for simulating
network intrusion detection systems mainly includes the OPNET and Net Sim. This type of
Systems is also capable of comparing signatures for similar packets in order to link and drop
the harmful detected packets that are consisting of a signature matching with the records in
the NIDS. When the classification of the design of NIDS is done according to the system
interactivity property, then it can be concluded that there are two types and this mainly
includes the 5fon-line and off-line NIDS, which are often referred to as inline and tap mode,
respectively. On-line NIDS is associated with dealing with the network on a real-time basis.
This is also associated with analysing the Ethernet packets along with the application of some
rules in order to decide if it is an attack or not. Off-line NIDS are associated with dealing
with the stored data, which is initially associated with the passing of it through some
processes in order to decide if it is an attack or not.
Network Intrusion Detection System Using SNORT
detected intrusions. Systems with response capabilities are typically referred to as an
intrusion prevention system.
Network intrusion detection systems (NIDS) has been placed at a strategic point or
points inside a network for the purpose of monitoring the traffic that is generally towards or
from all devices connected with the network. This is generally associated with performing an
analysis of the traffic that is passing on the entire subnet, which is followed by matching of
the traffic which is generally passed on the subnets to the library of known attacks. After the
identification of the attack or abnormal behaviour is done, then an alert is sent to the
administrator. (An example of a NIDS would be installing it on the subnet where firewalls are
located in order to see if someone is trying to break into the firewall. Ideally one would scan
all inbound and outbound traffic, however doing so might create a bottleneck that would
impair the overall speed of the network.).Some of the common tools used for simulating
network intrusion detection systems mainly includes the OPNET and Net Sim. This type of
Systems is also capable of comparing signatures for similar packets in order to link and drop
the harmful detected packets that are consisting of a signature matching with the records in
the NIDS. When the classification of the design of NIDS is done according to the system
interactivity property, then it can be concluded that there are two types and this mainly
includes the 5fon-line and off-line NIDS, which are often referred to as inline and tap mode,
respectively. On-line NIDS is associated with dealing with the network on a real-time basis.
This is also associated with analysing the Ethernet packets along with the application of some
rules in order to decide if it is an attack or not. Off-line NIDS are associated with dealing
with the stored data, which is initially associated with the passing of it through some
processes in order to decide if it is an attack or not.
Network Intrusion Detection System Using SNORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN692 Capstone Project Report Page 8 of 51
2. Project Detailed Design
NIDS monitors the traffic that is headed towards the main system using applications.
It can be used either software or hardware based. It creates alert to the admin when the
attacker tries to enter the system. NIDS detects different kinds of attacks that try to enter into
the main system. There are several applications used in order to detect network intrusions,
snort is one of the major tools which is used to detect the intrusions and alert it regularly. As
these tools are open source and easy to install on any network which is cost-efficient. Snort is
mainly based on the rules which are stored in a file name called local. Rules which can be
customized according to the user requirements. It reads the customized rules and applies it to
the captured data.
There exists various kind of techniques in the literature for detecting the behaviours
related to intrusion. In recent times, intrusion detection has been associated with receiving a
lot of interest amongst the researchers and this has mainly happened due to the wide
application of this for preserving the security within a network. Here, we present some of the
techniques used for intrusion detection.
S. F. Owens and R. R. Levaryhas been associated with stating the fact that the
intruder detection systems have been commonly created by making use of the expert system
technology. However, the Intrusion Detection System (IDS) researchers have been associated
with biasing which is generally related to the construction of the systems which are generally
difficult to handle, along with lacking in insightful user interfaces, besides this, they are also
very inconvenient for usage with real-life circumstances. The adaptive expert system
proposed by them has been associated with the utilizing of fuzzy sets in order to detect the
attacks. Besides this, the implementation of the expert system can be considered as
comparatively easy while using it with computer system networks which have the capability
of getting adjusted to nature or to the degree of the threat. Experiments with Clips have been
Network Intrusion Detection System Using SNORT
2. Project Detailed Design
NIDS monitors the traffic that is headed towards the main system using applications.
It can be used either software or hardware based. It creates alert to the admin when the
attacker tries to enter the system. NIDS detects different kinds of attacks that try to enter into
the main system. There are several applications used in order to detect network intrusions,
snort is one of the major tools which is used to detect the intrusions and alert it regularly. As
these tools are open source and easy to install on any network which is cost-efficient. Snort is
mainly based on the rules which are stored in a file name called local. Rules which can be
customized according to the user requirements. It reads the customized rules and applies it to
the captured data.
There exists various kind of techniques in the literature for detecting the behaviours
related to intrusion. In recent times, intrusion detection has been associated with receiving a
lot of interest amongst the researchers and this has mainly happened due to the wide
application of this for preserving the security within a network. Here, we present some of the
techniques used for intrusion detection.
S. F. Owens and R. R. Levaryhas been associated with stating the fact that the
intruder detection systems have been commonly created by making use of the expert system
technology. However, the Intrusion Detection System (IDS) researchers have been associated
with biasing which is generally related to the construction of the systems which are generally
difficult to handle, along with lacking in insightful user interfaces, besides this, they are also
very inconvenient for usage with real-life circumstances. The adaptive expert system
proposed by them has been associated with the utilizing of fuzzy sets in order to detect the
attacks. Besides this, the implementation of the expert system can be considered as
comparatively easy while using it with computer system networks which have the capability
of getting adjusted to nature or to the degree of the threat. Experiments with Clips have been
Network Intrusion Detection System Using SNORT

MN692 Capstone Project Report Page 9 of 51
used have been used for the purpose of proving the adjustment capability of the system. A
researcher Alok Sharma did the usage of text processing on system call sequences technique
for only intrusion detection. To have a host-based intrusion detection kernel based
comparison measurement is used. K-nearest neighbour is used for processing to check if it’s
normal or abnormal classification [11] in 1998-DARPA has assessed the proposed method
and compared with present methods for operation.
B. Shanmugam and NorbikBashah Idris have been related to proposing a progressive
fuzzy and data mining approaches which were built upon the hybrid model in which both the
misuse and along with anomaly malware attack. The goals of this researchers mainly
included the decreasing of the quantity of data that is generally kept for the purpose of
processing and also for the purpose of improving the detection rate of the existing IDS by
making use of the attribute assortment process and data mining method. An improved Kuok
fuzzy data mining algorithm or a modified version of APRIORI algorithm is generally used
for the purpose of utilizing and also for the purpose of implementing fuzzy rules which have
been associated with enabling the generation of if-then rules that are associated with showing
the best possible way to process the attack.
To test and benchmark the efficiency of any model use DARPS 1999 dataset which
include the live results of the working networking environment.)
O. A. Adebayo has presented a method that uses Fuzzy-Bayesian to detect real-time
network anomaly attack for discovering malicious activity against a computer network. They
have established the effectiveness of the method by describing the framework. The overall
performance of the intrusion detection system (IDS) based on Bayes has been improved by a
combination of fuzzy with the Bayesian classifier. In addition, by the experiment carried out
on KDD 1999 IDS data set, the practicability of the method has been verified. Abadeh, M.S.,
and Habibi, J. has proposed a method to develop fuzzy classification rules for intrusion
Network Intrusion Detection System Using SNORT
used have been used for the purpose of proving the adjustment capability of the system. A
researcher Alok Sharma did the usage of text processing on system call sequences technique
for only intrusion detection. To have a host-based intrusion detection kernel based
comparison measurement is used. K-nearest neighbour is used for processing to check if it’s
normal or abnormal classification [11] in 1998-DARPA has assessed the proposed method
and compared with present methods for operation.
B. Shanmugam and NorbikBashah Idris have been related to proposing a progressive
fuzzy and data mining approaches which were built upon the hybrid model in which both the
misuse and along with anomaly malware attack. The goals of this researchers mainly
included the decreasing of the quantity of data that is generally kept for the purpose of
processing and also for the purpose of improving the detection rate of the existing IDS by
making use of the attribute assortment process and data mining method. An improved Kuok
fuzzy data mining algorithm or a modified version of APRIORI algorithm is generally used
for the purpose of utilizing and also for the purpose of implementing fuzzy rules which have
been associated with enabling the generation of if-then rules that are associated with showing
the best possible way to process the attack.
To test and benchmark the efficiency of any model use DARPS 1999 dataset which
include the live results of the working networking environment.)
O. A. Adebayo has presented a method that uses Fuzzy-Bayesian to detect real-time
network anomaly attack for discovering malicious activity against a computer network. They
have established the effectiveness of the method by describing the framework. The overall
performance of the intrusion detection system (IDS) based on Bayes has been improved by a
combination of fuzzy with the Bayesian classifier. In addition, by the experiment carried out
on KDD 1999 IDS data set, the practicability of the method has been verified. Abadeh, M.S.,
and Habibi, J. has proposed a method to develop fuzzy classification rules for intrusion
Network Intrusion Detection System Using SNORT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

MN692 Capstone Project Report Page 10 of 51
detection use in computer networks. The method of fuzzy rule base system design has been
based on the iterative rule learning approach (IRL). Using the evolutionary algorithm to
optimize one fuzzy classifier rule at a time, the fuzzy rule base has been created in an
incremental fashion. Intrusion detection problem has been used as a high-dimensional
classification problem to analyse the functioning of the final fuzzy classification system.
Results have demonstrated that the fuzzy rules generated by the proposed algorithm can be
utilized to build a reliable intrusion detection system [13].
Network Intrusion Detection Systems (NIDS) generally consists of a network
appliance (or sensor) along with a Network Interface Card (NIC) which is generally
responsible for operating in the promiscuous mode along with working in a separate
management interface. Placing of the IDS is done in association with the network segment or
boundary along with the monitoring of all traffic present in that segment. Network intrusion
detection system (NIDS) can be considered as an independent platform which is associated
with identifying the various intrusions by examining the traffic in the network along with
monitoring of multiple hosts. Network intrusion detection systems are associated with
gaining access to the network traffic by creating a connection with the network hub.
Additionally, the network switches are also configured for mirroring the ports, or for the
network tap. Along with this in a NIDS, the sensors are generally present at the choke points
of the network which are to be monitored, often in the demilitarized zone (DMZ) or at
network borders. The Sensors are associated with capturing all the network traffic along with
analysing the content of individual packets for the traffics which are malicious in nature.
Network Intrusion Detection System Using SNORT
detection use in computer networks. The method of fuzzy rule base system design has been
based on the iterative rule learning approach (IRL). Using the evolutionary algorithm to
optimize one fuzzy classifier rule at a time, the fuzzy rule base has been created in an
incremental fashion. Intrusion detection problem has been used as a high-dimensional
classification problem to analyse the functioning of the final fuzzy classification system.
Results have demonstrated that the fuzzy rules generated by the proposed algorithm can be
utilized to build a reliable intrusion detection system [13].
Network Intrusion Detection Systems (NIDS) generally consists of a network
appliance (or sensor) along with a Network Interface Card (NIC) which is generally
responsible for operating in the promiscuous mode along with working in a separate
management interface. Placing of the IDS is done in association with the network segment or
boundary along with the monitoring of all traffic present in that segment. Network intrusion
detection system (NIDS) can be considered as an independent platform which is associated
with identifying the various intrusions by examining the traffic in the network along with
monitoring of multiple hosts. Network intrusion detection systems are associated with
gaining access to the network traffic by creating a connection with the network hub.
Additionally, the network switches are also configured for mirroring the ports, or for the
network tap. Along with this in a NIDS, the sensors are generally present at the choke points
of the network which are to be monitored, often in the demilitarized zone (DMZ) or at
network borders. The Sensors are associated with capturing all the network traffic along with
analysing the content of individual packets for the traffics which are malicious in nature.
Network Intrusion Detection System Using SNORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
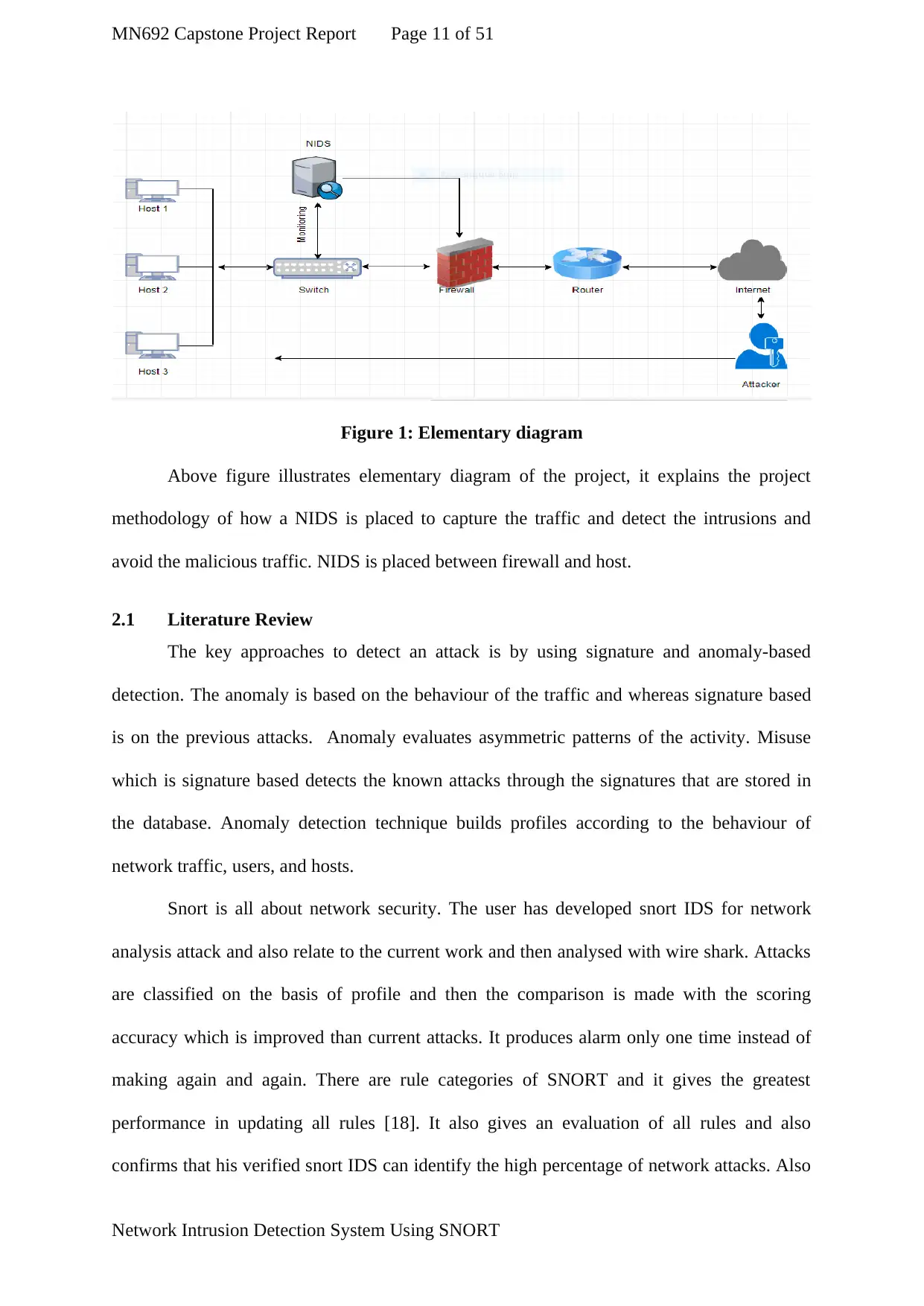
MN692 Capstone Project Report Page 11 of 51
Figure 1: Elementary diagram
Above figure illustrates elementary diagram of the project, it explains the project
methodology of how a NIDS is placed to capture the traffic and detect the intrusions and
avoid the malicious traffic. NIDS is placed between firewall and host.
2.1 Literature Review
The key approaches to detect an attack is by using signature and anomaly-based
detection. The anomaly is based on the behaviour of the traffic and whereas signature based
is on the previous attacks. Anomaly evaluates asymmetric patterns of the activity. Misuse
which is signature based detects the known attacks through the signatures that are stored in
the database. Anomaly detection technique builds profiles according to the behaviour of
network traffic, users, and hosts.
Snort is all about network security. The user has developed snort IDS for network
analysis attack and also relate to the current work and then analysed with wire shark. Attacks
are classified on the basis of profile and then the comparison is made with the scoring
accuracy which is improved than current attacks. It produces alarm only one time instead of
making again and again. There are rule categories of SNORT and it gives the greatest
performance in updating all rules [18]. It also gives an evaluation of all rules and also
confirms that his verified snort IDS can identify the high percentage of network attacks. Also
Network Intrusion Detection System Using SNORT
Figure 1: Elementary diagram
Above figure illustrates elementary diagram of the project, it explains the project
methodology of how a NIDS is placed to capture the traffic and detect the intrusions and
avoid the malicious traffic. NIDS is placed between firewall and host.
2.1 Literature Review
The key approaches to detect an attack is by using signature and anomaly-based
detection. The anomaly is based on the behaviour of the traffic and whereas signature based
is on the previous attacks. Anomaly evaluates asymmetric patterns of the activity. Misuse
which is signature based detects the known attacks through the signatures that are stored in
the database. Anomaly detection technique builds profiles according to the behaviour of
network traffic, users, and hosts.
Snort is all about network security. The user has developed snort IDS for network
analysis attack and also relate to the current work and then analysed with wire shark. Attacks
are classified on the basis of profile and then the comparison is made with the scoring
accuracy which is improved than current attacks. It produces alarm only one time instead of
making again and again. There are rule categories of SNORT and it gives the greatest
performance in updating all rules [18]. It also gives an evaluation of all rules and also
confirms that his verified snort IDS can identify the high percentage of network attacks. Also
Network Intrusion Detection System Using SNORT

MN692 Capstone Project Report Page 12 of 51
clear that users must update their snort rules frequently. As a future work, we can say that if
we identify other types of network attacks like teardrop attack, DoS, DDoS and data
alteration with existing method than there could be further room for the research
2.2 Objectives of the Project
The project's goal is to find a way to escape the most vicious intruders. This can be
done by implementing NIDS, which needs to be updated according to the present situation.
These can be done by analysing the packets that are captured by using techniques such as
identification, vulnerability and risk calculation. Our project, therefore, aims to preserve the
concept and its function of the system for detecting and preventing network intrusion and
network security by analysing incoming and outgoing traffic. Predefining set of rules in our
operating firewall this helps the firewall to build in identifying different types of attacks. The
main objective is to identify the threat and protect the sensitive data from the intruder. NIDS
is programmed to differentiate between valuable data with help of identification strings.
Capture, analyse and deliver report using signature and anomaly-based detection
system.
To implement NIDS that can detect any irregular network traffic in the network by
analysing the header file, port no and address.
Storing all the details of the attacks that are being happened before for the usage of
signature-based detection technique.
Create a system which helps to detect security threats in a network.
Launch a new system in a network to decrease the attacks.
A network-based IDS scanner secures the whole network by detecting the missing
packets, open ports and security breach.
Network Intrusion Detection System Using SNORT
clear that users must update their snort rules frequently. As a future work, we can say that if
we identify other types of network attacks like teardrop attack, DoS, DDoS and data
alteration with existing method than there could be further room for the research
2.2 Objectives of the Project
The project's goal is to find a way to escape the most vicious intruders. This can be
done by implementing NIDS, which needs to be updated according to the present situation.
These can be done by analysing the packets that are captured by using techniques such as
identification, vulnerability and risk calculation. Our project, therefore, aims to preserve the
concept and its function of the system for detecting and preventing network intrusion and
network security by analysing incoming and outgoing traffic. Predefining set of rules in our
operating firewall this helps the firewall to build in identifying different types of attacks. The
main objective is to identify the threat and protect the sensitive data from the intruder. NIDS
is programmed to differentiate between valuable data with help of identification strings.
Capture, analyse and deliver report using signature and anomaly-based detection
system.
To implement NIDS that can detect any irregular network traffic in the network by
analysing the header file, port no and address.
Storing all the details of the attacks that are being happened before for the usage of
signature-based detection technique.
Create a system which helps to detect security threats in a network.
Launch a new system in a network to decrease the attacks.
A network-based IDS scanner secures the whole network by detecting the missing
packets, open ports and security breach.
Network Intrusion Detection System Using SNORT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 51
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




