Mobile Application Project: Coffee Shop App Development and Analysis
VerifiedAdded on 2019/10/18
|9
|1792
|224
Project
AI Summary
This project outlines the development of a mobile application for a coffee shop, detailing critical attributes like user experience, device compatibility, and security. It presents a comprehensive project plan with milestones, work breakdown structures, and a defect detection workflow model. Reporting criteria are defined, alongside a communication plan for stakeholders. The project includes calculations for cost and schedule variances, and a maintenance phase strategy. A risk register identifies potential issues such as misalignment with user needs, unsustainable user growth, and security breaches. The project leverages earned value reporting and binary tracking algorithms for efficient maintenance and incorporates references to project management resources. This assignment provides a complete overview of mobile application development, integrating planning, execution, and risk management.
Mobile application project
19
19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Critical attributes of the mobile application development project.............................................2
Project plan summary of milestones..........................................................................................2
Work breakdown structure.........................................................................................................4
Defect detection workflow model..............................................................................................4
Reporting criteria.......................................................................................................................5
Communication plan..................................................................................................................5
Calculations................................................................................................................................6
Maintenance phase.....................................................................................................................7
Risk register...............................................................................................................................7
References..................................................................................................................................8
1
Critical attributes of the mobile application development project.............................................2
Project plan summary of milestones..........................................................................................2
Work breakdown structure.........................................................................................................4
Defect detection workflow model..............................................................................................4
Reporting criteria.......................................................................................................................5
Communication plan..................................................................................................................5
Calculations................................................................................................................................6
Maintenance phase.....................................................................................................................7
Risk register...............................................................................................................................7
References..................................................................................................................................8
1
Critical attributes of the mobile application development project
There are various attributes in the mobile application development for the coffeemaker
organization that are critical for the successful use of the mobile application for the company.
They are
User experience- the user experience is one of the most important factors contributing
to the success of mobile devices in a specific scenario. The information presented in
the various users must differ based on their requirements. For example, the user
might only want to know the direction to the closest coffee shop or order their drink
online before reaching the store or they might just want to browse the menu. The user
interface needs to make these functions integrated based on the consumer needs to be
successful.
Device compatibility- there is a range of mobile devices with different screen
resolutions and aspect rations which needs to be considered while developing mobile
software. Moreover, the ability of handling data of the devices also differs. This
makes the compatibility of the app for all users a major attribute for success. Thus,
using seamless experience for the user using different devices is a priority.
Security- data security is one of the major concerns that need to be included in the
application for it to be successful as current smartphones are sued for storing personal
and financial information. The various functions like location detection and internet
connectivity is also a threat as this can be exploited making this attribute an essential
aspect of the software. area
Analytic- the mobile application can offer the business additional insight into the
customers and the purchasing behaviours in addition to increasing the ease of availing
the services of their coffee shop. This is a huge advantage for the company as
analytics and big data are major aids in decision-making for any company.
Project plan summary of milestones
The project plan consists of several progressive milestones that help define the process flow
and the work packages to be conducted in the project. Thus, the project plan can be divided
into several interdependent activities contributing to the goals of the project which in this
2
There are various attributes in the mobile application development for the coffeemaker
organization that are critical for the successful use of the mobile application for the company.
They are
User experience- the user experience is one of the most important factors contributing
to the success of mobile devices in a specific scenario. The information presented in
the various users must differ based on their requirements. For example, the user
might only want to know the direction to the closest coffee shop or order their drink
online before reaching the store or they might just want to browse the menu. The user
interface needs to make these functions integrated based on the consumer needs to be
successful.
Device compatibility- there is a range of mobile devices with different screen
resolutions and aspect rations which needs to be considered while developing mobile
software. Moreover, the ability of handling data of the devices also differs. This
makes the compatibility of the app for all users a major attribute for success. Thus,
using seamless experience for the user using different devices is a priority.
Security- data security is one of the major concerns that need to be included in the
application for it to be successful as current smartphones are sued for storing personal
and financial information. The various functions like location detection and internet
connectivity is also a threat as this can be exploited making this attribute an essential
aspect of the software. area
Analytic- the mobile application can offer the business additional insight into the
customers and the purchasing behaviours in addition to increasing the ease of availing
the services of their coffee shop. This is a huge advantage for the company as
analytics and big data are major aids in decision-making for any company.
Project plan summary of milestones
The project plan consists of several progressive milestones that help define the process flow
and the work packages to be conducted in the project. Thus, the project plan can be divided
into several interdependent activities contributing to the goals of the project which in this
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

case, happens to be the establishment of a mobile application for a coffee shop chain. The
tasks or milestone or the project is listed below
Researching and prototyping the user flows for the specific type of application
Development of the UI design and wireframe for the application
Application functionality development
Beta version development and testing
Conducting user acceptance test
Gain software quality assurance (SQA) certifications
Release the application to the public through app stores for various platforms
3
tasks or milestone or the project is listed below
Researching and prototyping the user flows for the specific type of application
Development of the UI design and wireframe for the application
Application functionality development
Beta version development and testing
Conducting user acceptance test
Gain software quality assurance (SQA) certifications
Release the application to the public through app stores for various platforms
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Work breakdown structure
Defect detection workflow model
The defect detection workflow model is based on understanding the usage patterns of the
users and test the application from the end-user perspective. The test cases are developed first
after designing using the technique of decision tables for the mobile app. The different user
types are used in the workflow w analysis for the software and both positive and negative
tests are conducted. This helps determine the expected workflow for the various users which
can then be used to compare the real workflow and the logs of the actual workflows can be
used for the comparison and detection of the defects.
4
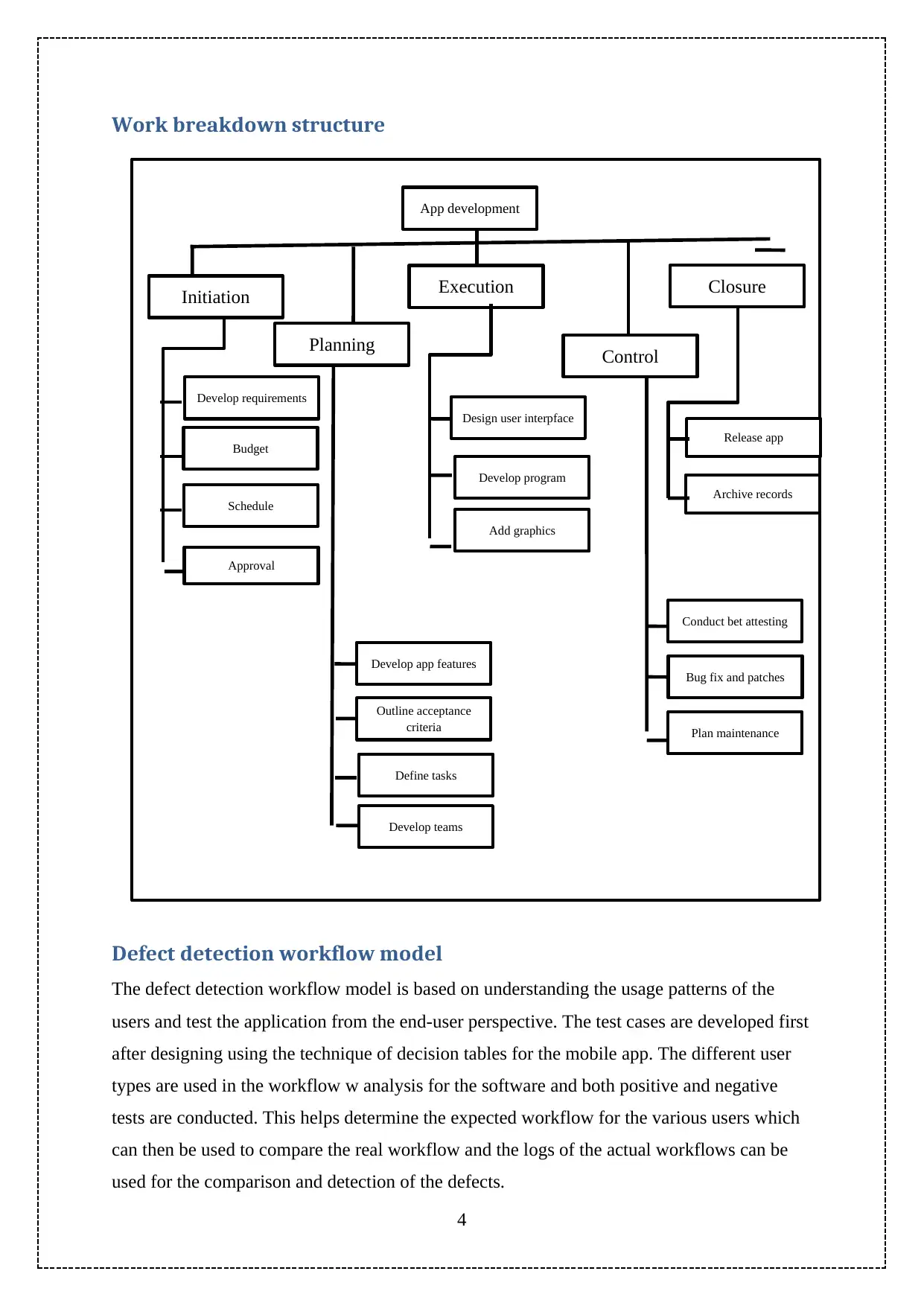
App development
Initiation
Planning
Execution
Control
Closure
Budget
Develop requirements
Schedule
Approval
Develop app features
Outline acceptance
criteria
Define tasks
Develop teams
Design user interpface
Develop program
Add graphics
Conduct bet attesting
Plan maintenance
Bug fix and patches
Release app
Archive records
Defect detection workflow model
The defect detection workflow model is based on understanding the usage patterns of the
users and test the application from the end-user perspective. The test cases are developed first
after designing using the technique of decision tables for the mobile app. The different user
types are used in the workflow w analysis for the software and both positive and negative
tests are conducted. This helps determine the expected workflow for the various users which
can then be used to compare the real workflow and the logs of the actual workflows can be
used for the comparison and detection of the defects.
4
App development
Initiation
Planning
Execution
Control
Closure
Budget
Develop requirements
Schedule
Approval
Develop app features
Outline acceptance
criteria
Define tasks
Develop teams
Design user interpface
Develop program
Add graphics
Conduct bet attesting
Plan maintenance
Bug fix and patches
Release app
Archive records

Reporting criteria
The defect detection workflow specifies the identified defects based on the actual workflow
and their deviation from the test cases workflow. However, the reporting of the deviation in
the workflow is not necessarily essential for the reporting. The error reporting for the defect
cases identified by the user and testing should be based on the severity and reproducibility of
the bug causing the error. The first aspects that need to be considered in the error reporting
are the user test case whether the cause of the error has been identified. If the cause of the
error has been identified, then the reporting priority will be based on a predetermined scale of
the impact of the deviation of the user experience and the functionalities of the app. The
reporting should also be specific in identifying the error and its cause along with the scenario
for the occurrence.
However, for the errors for which the cause cannot be identified readily the activity log of the
program prior to the error has to be sent along with the report so that the cause can be
determined. However, if the cause of the error is determined to be user error or device
limitation then the reporting should be forfeited in favour of the error message to the user
identifying the cause of the failure or instruction for avoiding future occurrence of the errors.
Communication plan
The sponsor - the coffeemaker organization- the sponsor needs any information regarding the
change in the time, scope or cost of the project and the technical information should be easily
understandable form non-technical perspective. Thus, periodic progress reporting with
minimal technical details should be used for the sponsor. Any resource requirements needing
approval also needs to be Cleary quantifiable in the reports.
The end user - the consumers of the app need not be reported until the final stage of making
the software available for the populace. This should include the various compatibility
specifications and a list of features for the end users.
The project manager- the project manager needs periodic reports about the progress and an
immediate report any deviation from the project plan. The reports need contain all aspects of
technical information and the detailed description of the task and the exact progress level for
the various tasks.
5
The defect detection workflow specifies the identified defects based on the actual workflow
and their deviation from the test cases workflow. However, the reporting of the deviation in
the workflow is not necessarily essential for the reporting. The error reporting for the defect
cases identified by the user and testing should be based on the severity and reproducibility of
the bug causing the error. The first aspects that need to be considered in the error reporting
are the user test case whether the cause of the error has been identified. If the cause of the
error has been identified, then the reporting priority will be based on a predetermined scale of
the impact of the deviation of the user experience and the functionalities of the app. The
reporting should also be specific in identifying the error and its cause along with the scenario
for the occurrence.
However, for the errors for which the cause cannot be identified readily the activity log of the
program prior to the error has to be sent along with the report so that the cause can be
determined. However, if the cause of the error is determined to be user error or device
limitation then the reporting should be forfeited in favour of the error message to the user
identifying the cause of the failure or instruction for avoiding future occurrence of the errors.
Communication plan
The sponsor - the coffeemaker organization- the sponsor needs any information regarding the
change in the time, scope or cost of the project and the technical information should be easily
understandable form non-technical perspective. Thus, periodic progress reporting with
minimal technical details should be used for the sponsor. Any resource requirements needing
approval also needs to be Cleary quantifiable in the reports.
The end user - the consumers of the app need not be reported until the final stage of making
the software available for the populace. This should include the various compatibility
specifications and a list of features for the end users.
The project manager- the project manager needs periodic reports about the progress and an
immediate report any deviation from the project plan. The reports need contain all aspects of
technical information and the detailed description of the task and the exact progress level for
the various tasks.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
The development team- the development team needs to be made aware of the progress by
other teams in the project through periodic meeting and needs to be notified of any change
requirements for the app being developed.
Graphic design and testing- they only need to be made aware of any change requirements
pertinent to their specific aspect of the operations and can be easily done through the periodic
scheduled and unscheduled meetings.
Calculations
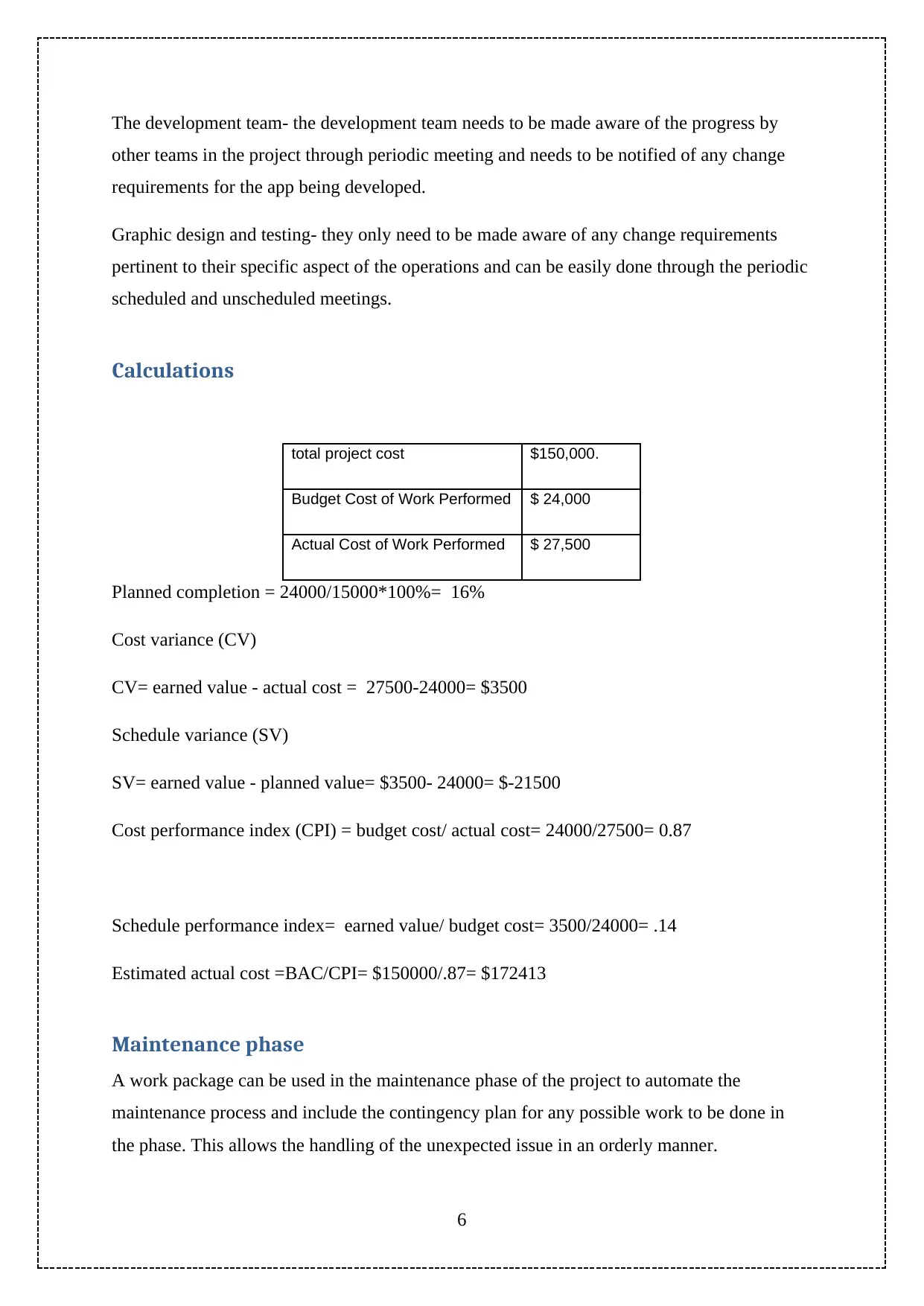
total project cost $150,000.
Budget Cost of Work Performed $ 24,000
Actual Cost of Work Performed $ 27,500
Planned completion = 24000/15000*100%= 16%
Cost variance (CV)
CV= earned value - actual cost = 27500-24000= $3500
Schedule variance (SV)
SV= earned value - planned value= $3500- 24000= $-21500
Cost performance index (CPI) = budget cost/ actual cost= 24000/27500= 0.87
Schedule performance index= earned value/ budget cost= 3500/24000= .14
Estimated actual cost =BAC/CPI= $150000/.87= $172413
Maintenance phase
A work package can be used in the maintenance phase of the project to automate the
maintenance process and include the contingency plan for any possible work to be done in
the phase. This allows the handling of the unexpected issue in an orderly manner.
6
other teams in the project through periodic meeting and needs to be notified of any change
requirements for the app being developed.
Graphic design and testing- they only need to be made aware of any change requirements
pertinent to their specific aspect of the operations and can be easily done through the periodic
scheduled and unscheduled meetings.
Calculations
total project cost $150,000.
Budget Cost of Work Performed $ 24,000
Actual Cost of Work Performed $ 27,500
Planned completion = 24000/15000*100%= 16%
Cost variance (CV)
CV= earned value - actual cost = 27500-24000= $3500
Schedule variance (SV)
SV= earned value - planned value= $3500- 24000= $-21500
Cost performance index (CPI) = budget cost/ actual cost= 24000/27500= 0.87
Schedule performance index= earned value/ budget cost= 3500/24000= .14
Estimated actual cost =BAC/CPI= $150000/.87= $172413
Maintenance phase
A work package can be used in the maintenance phase of the project to automate the
maintenance process and include the contingency plan for any possible work to be done in
the phase. This allows the handling of the unexpected issue in an orderly manner.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Binary tracking algorithms allow for the tracking of the various operators of the program and
allow the maintenance team to track any anomaly to its source cause which can be used to
address the issue more efficiently.
Earned valued reporting can be used for the comparison of the estimated value to the actual
one where the discrepancies can be used for making decisions regarding the formulation of
the mitigation actions like patching.
Risk register
Misalignment with user needs- the risk of misinterpreting the user needs is a serious risk for
mobile applications development. Thus, the user needs to need to be understood before
deciding on the feature for the app. The risk management technique to be applied in this case
is to reject the risk and make the necessary change to the app specifications to make it more
acceptable to the end-users.
Including unnecessary features- this risk is called goal plating which can incur extra time and
expense that is not translated into the project outcome. This increases the possibility of other
risk s like reliability issues. The response to the risk is to prevention and monitor for future
occurrence in the planning and designing phase.
Unsustainable user growth- this is a serious risk that is based on the scalability of the app
which can crash and decrease in the response time and accuracy because of the higher
number of users. The response to this is to prevention as this can affect all of the future stages
of the project.
Security breach- this is another risk possible risk affecting the user experience and company
reputation this can be addressed through monitoring and risk mitigation measures that are
updated based on the current information.
Platform compatibility issues or stability- there are many aspects of the platform
compatibility that can cause a possible risk event or more specifically crash of the app. This
can be caused by various factors like the browser incompatibility, incorrect memory usage,
and fatal production bugs. The risk response technique used in this case should be monitor
and prevent through bug fix and testing which can address the issue successfully.
7
allow the maintenance team to track any anomaly to its source cause which can be used to
address the issue more efficiently.
Earned valued reporting can be used for the comparison of the estimated value to the actual
one where the discrepancies can be used for making decisions regarding the formulation of
the mitigation actions like patching.
Risk register
Misalignment with user needs- the risk of misinterpreting the user needs is a serious risk for
mobile applications development. Thus, the user needs to need to be understood before
deciding on the feature for the app. The risk management technique to be applied in this case
is to reject the risk and make the necessary change to the app specifications to make it more
acceptable to the end-users.
Including unnecessary features- this risk is called goal plating which can incur extra time and
expense that is not translated into the project outcome. This increases the possibility of other
risk s like reliability issues. The response to the risk is to prevention and monitor for future
occurrence in the planning and designing phase.
Unsustainable user growth- this is a serious risk that is based on the scalability of the app
which can crash and decrease in the response time and accuracy because of the higher
number of users. The response to this is to prevention as this can affect all of the future stages
of the project.
Security breach- this is another risk possible risk affecting the user experience and company
reputation this can be addressed through monitoring and risk mitigation measures that are
updated based on the current information.
Platform compatibility issues or stability- there are many aspects of the platform
compatibility that can cause a possible risk event or more specifically crash of the app. This
can be caused by various factors like the browser incompatibility, incorrect memory usage,
and fatal production bugs. The risk response technique used in this case should be monitor
and prevent through bug fix and testing which can address the issue successfully.
7

References
Kerzner, H., & Kerzner, H. R. (2017). Project management: a systems approach to planning,
scheduling, and controlling. John Wiley & Sons.
Fleming, Q. W., & Koppelman, J. M. (2016, December). Earned value project management.
Project Management Institute.
Heagney, J. (2016). Fundamentals of project management. Amacom.
Harrison, F., & Lock, D. (2017). Advanced project management: a structured approach.
Routledge.
Schwalbe, K. (2015). Information technology project management. Cengage Learning.
8
Kerzner, H., & Kerzner, H. R. (2017). Project management: a systems approach to planning,
scheduling, and controlling. John Wiley & Sons.
Fleming, Q. W., & Koppelman, J. M. (2016, December). Earned value project management.
Project Management Institute.
Heagney, J. (2016). Fundamentals of project management. Amacom.
Harrison, F., & Lock, D. (2017). Advanced project management: a structured approach.
Routledge.
Schwalbe, K. (2015). Information technology project management. Cengage Learning.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





