Mobile Application Threat Modeling Report - IT Security Analysis
VerifiedAdded on 2023/03/20
|14
|3127
|21
Report
AI Summary
This report provides a comprehensive analysis of mobile application threat modeling, focusing on the Intune application. It begins by describing the mobile application's architecture, including device-specific features, wireless transmission protocols, and interaction with hardware components. The report then identifies the security needs and requirements, including device management, authentication specifics, and the operating system's security model. A detailed discussion of potential threats and threat agents, along with common methods of attack, is presented. The analysis covers the architecture's design, including network infrastructure, web services, and trust boundaries. The report concludes with a discussion of security controls and best practices, emphasizing the importance of proactive measures like updated encryptions, firewalls, and multi-factor authentication. The overall goal is to provide a secure and protected environment for the mobile application, mitigating potential risks and vulnerabilities.

Mobile Application Threat Modeling
Student’s name
Institution Affiliation(s)
Student’s name
Institution Affiliation(s)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Mobile Application Architecture.....................................................................................................2
Design of the architecture:...........................................................................................................2
Common Hardware components..................................................................................................4
Authentication Specifics..............................................................................................................5
OS stack and security model........................................................................................................5
Requirements for Mobile Application.............................................................................................6
Threats and Threat Agents...............................................................................................................9
Methods of Attack.........................................................................................................................10
Analysis of Mobile Application Threats........................................................................................11
Controls..........................................................................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
1
Mobile Application Architecture.....................................................................................................2
Design of the architecture:...........................................................................................................2
Common Hardware components..................................................................................................4
Authentication Specifics..............................................................................................................5
OS stack and security model........................................................................................................5
Requirements for Mobile Application.............................................................................................6
Threats and Threat Agents...............................................................................................................9
Methods of Attack.........................................................................................................................10
Analysis of Mobile Application Threats........................................................................................11
Controls..........................................................................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
1

Mobile Application Architecture
In today’s work environment, there is the growing reality that executives, managers, and
staff employees are going beyond being stationary in a cubicle. There is a growing culture of
workers to have mobile access to our company’s databases and servers. Staff members from
CEOs to entry levels are now working from remote locations that could be from one to thousands
of miles away from the office or servers (Salazar & Brambilla, 2015). With the fast-pace
increase of mobile applications and the flexibility that mobile devices provide, we are excited to
introduce a product that will simultaneously increase productivity and security for our company.
The product is called Intune, a cloud-based service designed for enterprise mobility
management (EMM) by Microsoft. Intune can be installed on Android, iOS, Windows, and
macOS devices which are accessible through the Play Store (Android) and App Store (iOS). At
the present time, our staff uses both Android and iOS devices with the latest malware protection
installed. Despite the latest virus protection installed on our mobile devices, there is still the
possibility of exploits, theft, and security breaches into our database due to the increased
sophistication of cybercriminals and potential vulnerabilities (Kassas, Abdullah, Yousef, &
Wahba, 2017).
Design of the architecture:
We have a pending agreement with Sprint wireless network that will provide Data, SMS,
and Voice plans at a discount rate to support our Bring Your Own Device (BYOD) policy. The
web service we’re looking into using is Simple Object Access Protocol (SOAP). We prefer this
web service because of its flexibility to work with any application layer protocol (i.e. HTTP,
SMTP, TCP, and UDP); it can perform well in a distributed enterprise environment (Barnett,
Avazpour, Vasa, & Grundy, 2019). The web service for Intune can be located in the Azure
2
In today’s work environment, there is the growing reality that executives, managers, and
staff employees are going beyond being stationary in a cubicle. There is a growing culture of
workers to have mobile access to our company’s databases and servers. Staff members from
CEOs to entry levels are now working from remote locations that could be from one to thousands
of miles away from the office or servers (Salazar & Brambilla, 2015). With the fast-pace
increase of mobile applications and the flexibility that mobile devices provide, we are excited to
introduce a product that will simultaneously increase productivity and security for our company.
The product is called Intune, a cloud-based service designed for enterprise mobility
management (EMM) by Microsoft. Intune can be installed on Android, iOS, Windows, and
macOS devices which are accessible through the Play Store (Android) and App Store (iOS). At
the present time, our staff uses both Android and iOS devices with the latest malware protection
installed. Despite the latest virus protection installed on our mobile devices, there is still the
possibility of exploits, theft, and security breaches into our database due to the increased
sophistication of cybercriminals and potential vulnerabilities (Kassas, Abdullah, Yousef, &
Wahba, 2017).
Design of the architecture:
We have a pending agreement with Sprint wireless network that will provide Data, SMS,
and Voice plans at a discount rate to support our Bring Your Own Device (BYOD) policy. The
web service we’re looking into using is Simple Object Access Protocol (SOAP). We prefer this
web service because of its flexibility to work with any application layer protocol (i.e. HTTP,
SMTP, TCP, and UDP); it can perform well in a distributed enterprise environment (Barnett,
Avazpour, Vasa, & Grundy, 2019). The web service for Intune can be located in the Azure
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

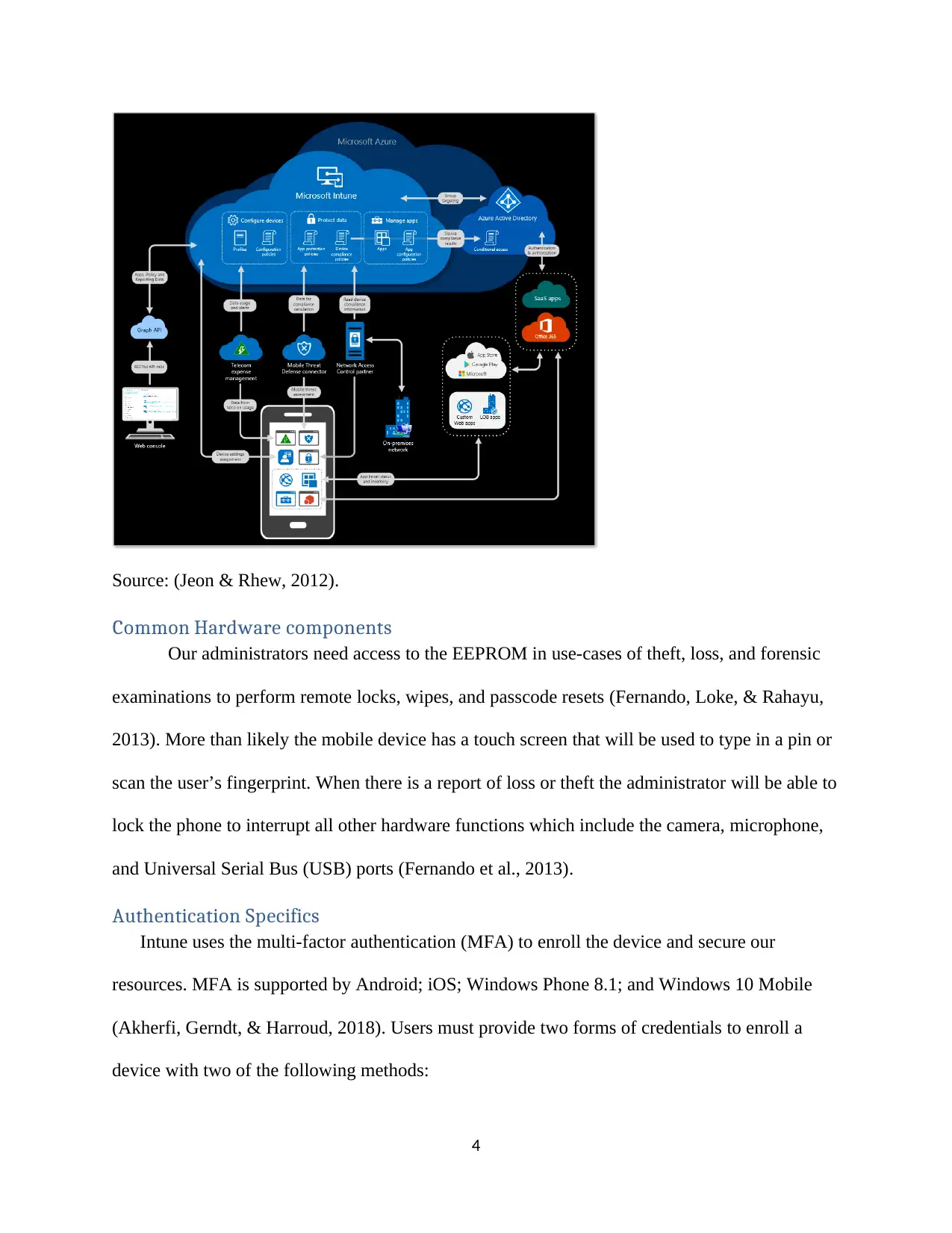
portal. A few of the features of Azure is an integrated console for our EMM and support for most
modern web browsers. Intune integrates most mobile web versions of existing websites.
Intune can be installed via Google Play Store and Apple App Store. The Azure portal will
provide cloud services that support healthcare, retail, financial services, and other large
enterprise work environments. The network protocols will connect via Virtual Private Network
(VPN); this will create a secure “private pipeline” to send and receive data. The wireless
interface to be used is 802.11ac. It provides an improved bandwidth for more flexibility and
backwards compatibility (Volk, Sterle, & Sedlar, 2015). The runtime environment (RTE) will be
operating as a Common Language Runtime (CLR) for Microsoft (Jeon & Rhew, 2012).NET
framework to support different programming languages to achieve a common goal. The OS
platforms supported includes,
a) Apple iOS 10 and later
b) Mac OS X 12.12 and later
c) Android 4.4 and later
d) Android Enterprise (Lollipop 5.0 and later work profile support)
e) Microsoft Win 10 (Home and Enterprise)
f) Microsoft Win 10 Mobile
g) Microsoft Windows 10 IoT Enterprise
3
modern web browsers. Intune integrates most mobile web versions of existing websites.
Intune can be installed via Google Play Store and Apple App Store. The Azure portal will
provide cloud services that support healthcare, retail, financial services, and other large
enterprise work environments. The network protocols will connect via Virtual Private Network
(VPN); this will create a secure “private pipeline” to send and receive data. The wireless
interface to be used is 802.11ac. It provides an improved bandwidth for more flexibility and
backwards compatibility (Volk, Sterle, & Sedlar, 2015). The runtime environment (RTE) will be
operating as a Common Language Runtime (CLR) for Microsoft (Jeon & Rhew, 2012).NET
framework to support different programming languages to achieve a common goal. The OS
platforms supported includes,
a) Apple iOS 10 and later
b) Mac OS X 12.12 and later
c) Android 4.4 and later
d) Android Enterprise (Lollipop 5.0 and later work profile support)
e) Microsoft Win 10 (Home and Enterprise)
f) Microsoft Win 10 Mobile
g) Microsoft Windows 10 IoT Enterprise
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Source: (Jeon & Rhew, 2012).
Common Hardware components
Our administrators need access to the EEPROM in use-cases of theft, loss, and forensic
examinations to perform remote locks, wipes, and passcode resets (Fernando, Loke, & Rahayu,
2013). More than likely the mobile device has a touch screen that will be used to type in a pin or
scan the user’s fingerprint. When there is a report of loss or theft the administrator will be able to
lock the phone to interrupt all other hardware functions which include the camera, microphone,
and Universal Serial Bus (USB) ports (Fernando et al., 2013).
Authentication Specifics
Intune uses the multi-factor authentication (MFA) to enroll the device and secure our
resources. MFA is supported by Android; iOS; Windows Phone 8.1; and Windows 10 Mobile
(Akherfi, Gerndt, & Harroud, 2018). Users must provide two forms of credentials to enroll a
device with two of the following methods:
4
Common Hardware components
Our administrators need access to the EEPROM in use-cases of theft, loss, and forensic
examinations to perform remote locks, wipes, and passcode resets (Fernando, Loke, & Rahayu,
2013). More than likely the mobile device has a touch screen that will be used to type in a pin or
scan the user’s fingerprint. When there is a report of loss or theft the administrator will be able to
lock the phone to interrupt all other hardware functions which include the camera, microphone,
and Universal Serial Bus (USB) ports (Fernando et al., 2013).
Authentication Specifics
Intune uses the multi-factor authentication (MFA) to enroll the device and secure our
resources. MFA is supported by Android; iOS; Windows Phone 8.1; and Windows 10 Mobile
(Akherfi, Gerndt, & Harroud, 2018). Users must provide two forms of credentials to enroll a
device with two of the following methods:
4

a) PIN
b) Trusted mobile device
c) Fingerprint
OS stack and security model
We will exercise a security stack that includes the OS in order to analyze the security
mechanisms of the mobile computing environment. The security stack will be divided into four
layers: Infrastructure, Hardware, OS and the application (Akherfi et al., 2018).
Source: (Akherfi et al., 2018).
The OS can be a pathway for attackers to penetrate due to flawed OS programming of
running applications (Bou & Demerjian, 2017). An example of any vulnerabilities at the
application layer is coding flaws that contribute to improper cryptographic algorithms and
“backdoored” applications. With proper four-layer protection, Intune will protect our on-
premises email and data, protect our Office 365 mail and data, and honour the BYOD policy
(Aldayel & Alnafjan, 2017) However, Intune will limit that access users have to edit documents;
will not be allowed to perform a corporate wipe of corporate data, and isolate personal
information from IT awareness.
5
b) Trusted mobile device
c) Fingerprint
OS stack and security model
We will exercise a security stack that includes the OS in order to analyze the security
mechanisms of the mobile computing environment. The security stack will be divided into four
layers: Infrastructure, Hardware, OS and the application (Akherfi et al., 2018).
Source: (Akherfi et al., 2018).
The OS can be a pathway for attackers to penetrate due to flawed OS programming of
running applications (Bou & Demerjian, 2017). An example of any vulnerabilities at the
application layer is coding flaws that contribute to improper cryptographic algorithms and
“backdoored” applications. With proper four-layer protection, Intune will protect our on-
premises email and data, protect our Office 365 mail and data, and honour the BYOD policy
(Aldayel & Alnafjan, 2017) However, Intune will limit that access users have to edit documents;
will not be allowed to perform a corporate wipe of corporate data, and isolate personal
information from IT awareness.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
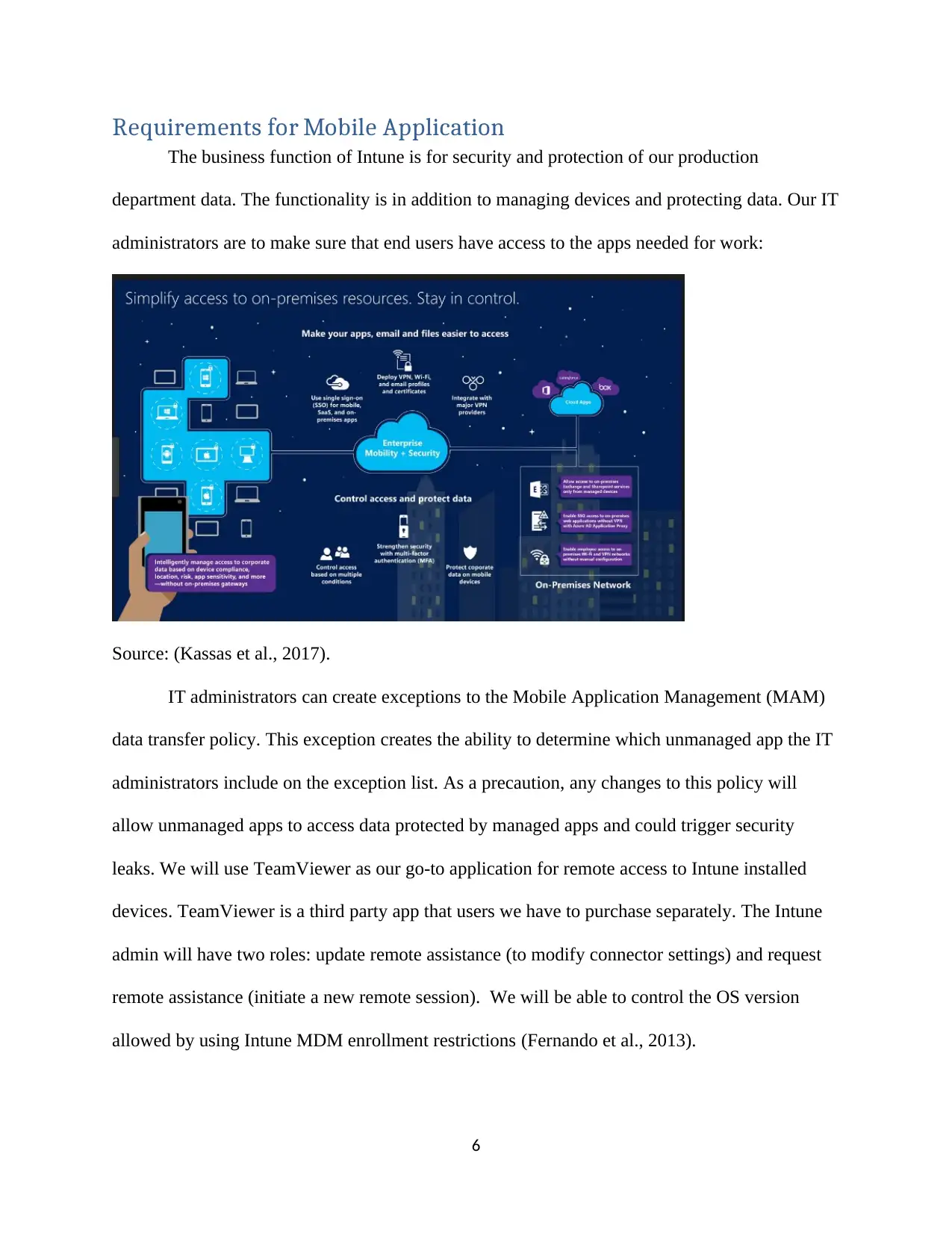
Requirements for Mobile Application
The business function of Intune is for security and protection of our production
department data. The functionality is in addition to managing devices and protecting data. Our IT
administrators are to make sure that end users have access to the apps needed for work:
Source: (Kassas et al., 2017).
IT administrators can create exceptions to the Mobile Application Management (MAM)
data transfer policy. This exception creates the ability to determine which unmanaged app the IT
administrators include on the exception list. As a precaution, any changes to this policy will
allow unmanaged apps to access data protected by managed apps and could trigger security
leaks. We will use TeamViewer as our go-to application for remote access to Intune installed
devices. TeamViewer is a third party app that users we have to purchase separately. The Intune
admin will have two roles: update remote assistance (to modify connector settings) and request
remote assistance (initiate a new remote session). We will be able to control the OS version
allowed by using Intune MDM enrollment restrictions (Fernando et al., 2013).
6
The business function of Intune is for security and protection of our production
department data. The functionality is in addition to managing devices and protecting data. Our IT
administrators are to make sure that end users have access to the apps needed for work:
Source: (Kassas et al., 2017).
IT administrators can create exceptions to the Mobile Application Management (MAM)
data transfer policy. This exception creates the ability to determine which unmanaged app the IT
administrators include on the exception list. As a precaution, any changes to this policy will
allow unmanaged apps to access data protected by managed apps and could trigger security
leaks. We will use TeamViewer as our go-to application for remote access to Intune installed
devices. TeamViewer is a third party app that users we have to purchase separately. The Intune
admin will have two roles: update remote assistance (to modify connector settings) and request
remote assistance (initiate a new remote session). We will be able to control the OS version
allowed by using Intune MDM enrollment restrictions (Fernando et al., 2013).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The Intune application allows IT, administrators, to manage updates and patches on
Windows devices, but other platforms (i.e. Android & iOS) will require end-user participation
for the update process. We will have to educate and encourage staff members that use Android
and iOS devices to upgrade to the latest OS that we approve. Intune uses Microsoft Windows
Azure Active Directory as the cloud service to grant our IT administrators the ability to manage
end-user identities, access rights, and data back-ups (Meneses et al., 2018). Our staff that use
Intune on their mobile devices can know that the personal and company data are both separated,
private, and protected via MDM. Intune has a feature that creates a separate icon on the device
that “houses” all company data Intune portal in Azure allows IT admins to manage only
company data if the employee is terminated or do not want their device to be managed any
longer.
Source: (Akherfi et al., 2018).
Intune uses Microsoft Graph API to apply business logic and access to extract custom
variables; controls access to resources by using permissions; configure controls and policies.
Microsoft Graph API is accessed through the Azure Active Directory. The data on the mobile
device is stored on internal/external memory cards which can cause a threat of exposure by an
attacker if the device is lost or stolen. While the mobile is in data at rest is stores the data in
either internal/external storage yet the device itself is encrypted. If the user power-cycles the
7
Windows devices, but other platforms (i.e. Android & iOS) will require end-user participation
for the update process. We will have to educate and encourage staff members that use Android
and iOS devices to upgrade to the latest OS that we approve. Intune uses Microsoft Windows
Azure Active Directory as the cloud service to grant our IT administrators the ability to manage
end-user identities, access rights, and data back-ups (Meneses et al., 2018). Our staff that use
Intune on their mobile devices can know that the personal and company data are both separated,
private, and protected via MDM. Intune has a feature that creates a separate icon on the device
that “houses” all company data Intune portal in Azure allows IT admins to manage only
company data if the employee is terminated or do not want their device to be managed any
longer.
Source: (Akherfi et al., 2018).
Intune uses Microsoft Graph API to apply business logic and access to extract custom
variables; controls access to resources by using permissions; configure controls and policies.
Microsoft Graph API is accessed through the Azure Active Directory. The data on the mobile
device is stored on internal/external memory cards which can cause a threat of exposure by an
attacker if the device is lost or stolen. While the mobile is in data at rest is stores the data in
either internal/external storage yet the device itself is encrypted. If the user power-cycles the
7

device, they will have to provide a pin or fingerprint to get to their desktop window (Bou &
Demerjian, 2017).
The encryption provides security for data-at-rest and data-in-motion since data is
transmitted via VPN. When IT admins activate functions such as Apple Device Enrollment
Program, Intune then gets the consent for data sharing with appropriate third parties that are
acting as Microsoft agents. For example, allowing access for the unique device identifier
(UDID) being transmitted to a third party can be managed by the device category in Azure
AD. This is necessary to aid customer and technical support and service maintenance (Meneses
et al., 2018). Our IT admins can view some personal data, but our end users will have full control
to change the device’ personal data. There are managed apps provided by our IT/Network
security team that will be accessible once Intune is installed. These apps can interact with a
configuration manager stored in Azure AD. Intune has a feature called Enhanced Jailbreak
Detection once enabled, this triggers a mobile device to check in with Intune more frequently - at
least every 72 hours. The device’s location services are activated, but the location data is not
stored. In the Azure dashboard, you can review to see if the device is compliant within the
Device Compliance Overview section. The reports will show overall device compliance, per-
policy device compliance, pre-setting device compliance, device protection status, and threat
agent status (Meneses et al., 2018).
Threats and Threat Agents
Even though there is the ongoing pursuit in making devices, software, and networks secure
there is still the possibility of vulnerabilities and exploits. Being proactive with system
maintenance and patches is pivotal in protecting against known and the unknown vulnerabilities.
8
Demerjian, 2017).
The encryption provides security for data-at-rest and data-in-motion since data is
transmitted via VPN. When IT admins activate functions such as Apple Device Enrollment
Program, Intune then gets the consent for data sharing with appropriate third parties that are
acting as Microsoft agents. For example, allowing access for the unique device identifier
(UDID) being transmitted to a third party can be managed by the device category in Azure
AD. This is necessary to aid customer and technical support and service maintenance (Meneses
et al., 2018). Our IT admins can view some personal data, but our end users will have full control
to change the device’ personal data. There are managed apps provided by our IT/Network
security team that will be accessible once Intune is installed. These apps can interact with a
configuration manager stored in Azure AD. Intune has a feature called Enhanced Jailbreak
Detection once enabled, this triggers a mobile device to check in with Intune more frequently - at
least every 72 hours. The device’s location services are activated, but the location data is not
stored. In the Azure dashboard, you can review to see if the device is compliant within the
Device Compliance Overview section. The reports will show overall device compliance, per-
policy device compliance, pre-setting device compliance, device protection status, and threat
agent status (Meneses et al., 2018).
Threats and Threat Agents
Even though there is the ongoing pursuit in making devices, software, and networks secure
there is still the possibility of vulnerabilities and exploits. Being proactive with system
maintenance and patches is pivotal in protecting against known and the unknown vulnerabilities.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The following is a breakdown of threats that can possibly cause sabotage (Alsaleh, Alomar, &
Alarifi, 2017).
a) Current and former employees: Former and current employees that has access to our
database that may want to steal information for profit or vengeance. Also the possibility
of the negligence of not keeping up with OS or application updates that has security
patches.
b) Malware: A program that performs the suspicious and unfamiliar activity on the device.
For example, you could be using a social media application and automatically get routed
to take a survey. This could be malware being downloaded to the user’s device without
their knowledge (He, Chan, & Guizani, 2015).
Methods of Attack
One method of attack would be to create false IP, and the hacker can hide their real
location. This method is known as spoofing and its purpose is to trick a non-suspecting user. An
attacker creates IP packets for a specific location, but the source IP field hides the attacker’s
computer and, the computer can be used as a data collector or sniffer by the attacker.
9
Alarifi, 2017).
a) Current and former employees: Former and current employees that has access to our
database that may want to steal information for profit or vengeance. Also the possibility
of the negligence of not keeping up with OS or application updates that has security
patches.
b) Malware: A program that performs the suspicious and unfamiliar activity on the device.
For example, you could be using a social media application and automatically get routed
to take a survey. This could be malware being downloaded to the user’s device without
their knowledge (He, Chan, & Guizani, 2015).
Methods of Attack
One method of attack would be to create false IP, and the hacker can hide their real
location. This method is known as spoofing and its purpose is to trick a non-suspecting user. An
attacker creates IP packets for a specific location, but the source IP field hides the attacker’s
computer and, the computer can be used as a data collector or sniffer by the attacker.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Source: (Volk et al., 2015).
Analysis of Mobile Application Threats
The best practices to ensure a secure network is to have updated encryptions, firewalls,
IDS/IPS, and multi-factor authentications installed on devices and within the network to
minimize the impact of security breaches (Lee et al., 2019). Full-Disk encryption should be
activated on servers containing customer login credentials, PII, and financial records. Developing
security on the network should consist of firewalls, Honeypots, and IDSs to monitor and block
any (and all) suspicious traffic. After using the results of the Wireshark application, we were able
to monitor potentially malicious traffic being discovered:
As in this example above, malformed packets are indicators that an attack is pending. It’s
in the network administrators’ best interest to have alerts activated in Anti-malware and IPS
applications immediately for a consistently secure infrastructure.
Controls
It’s imperative to secure the network and devices - controls will increase a possible
breach-free environment. Educating employees to avoid deceptive emails that are actually
Trojans or Malware attached to the links. Azure AD has a policy that automatically initiates a
10
Analysis of Mobile Application Threats
The best practices to ensure a secure network is to have updated encryptions, firewalls,
IDS/IPS, and multi-factor authentications installed on devices and within the network to
minimize the impact of security breaches (Lee et al., 2019). Full-Disk encryption should be
activated on servers containing customer login credentials, PII, and financial records. Developing
security on the network should consist of firewalls, Honeypots, and IDSs to monitor and block
any (and all) suspicious traffic. After using the results of the Wireshark application, we were able
to monitor potentially malicious traffic being discovered:
As in this example above, malformed packets are indicators that an attack is pending. It’s
in the network administrators’ best interest to have alerts activated in Anti-malware and IPS
applications immediately for a consistently secure infrastructure.
Controls
It’s imperative to secure the network and devices - controls will increase a possible
breach-free environment. Educating employees to avoid deceptive emails that are actually
Trojans or Malware attached to the links. Azure AD has a policy that automatically initiates a
10

password policy that forces users to update their passwords every 90 days will increase a secure
system and minimize attacks. Intune has regularly scheduled OS updates for (multiple platforms)
mobile device can keep the OS current with the latest security patches (Louk, Lim, & Lee, 2014).
Installing antivirus software, Intrusion Prevention Systems (IPS), Intrusion Detection Systems
(IDS) and ad blockers can secure web-based applications and web use on devices.
Conclusion
Understanding the damage (financial and technological) data breaches can do to our
network infrastructure is staggering. It’s imperative to deploy Intune to reinforce an increase in
productivity and ensure we have a secure database. Intune is a valuable asset to invest in for our
corporate structure and the future success of this company. We scheduled a time with the CIO,
IT and network managers to beta test the functionality and reliability of well-known brand
mobile devices in a closed network. Afterwards, we are discussing the cost of the enterprise
package, and SLA then will proceed with the delivery to our production team. We plan to have a
Three-phase deployment of the application, that is, Executives, Managers and Associate
employees.
11
system and minimize attacks. Intune has regularly scheduled OS updates for (multiple platforms)
mobile device can keep the OS current with the latest security patches (Louk, Lim, & Lee, 2014).
Installing antivirus software, Intrusion Prevention Systems (IPS), Intrusion Detection Systems
(IDS) and ad blockers can secure web-based applications and web use on devices.
Conclusion
Understanding the damage (financial and technological) data breaches can do to our
network infrastructure is staggering. It’s imperative to deploy Intune to reinforce an increase in
productivity and ensure we have a secure database. Intune is a valuable asset to invest in for our
corporate structure and the future success of this company. We scheduled a time with the CIO,
IT and network managers to beta test the functionality and reliability of well-known brand
mobile devices in a closed network. Afterwards, we are discussing the cost of the enterprise
package, and SLA then will proceed with the delivery to our production team. We plan to have a
Three-phase deployment of the application, that is, Executives, Managers and Associate
employees.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




