Business Research Assignment: Mobile Computing Downsides and Solutions
VerifiedAdded on 2020/04/01
|12
|2511
|148
Report
AI Summary
This business research assignment investigates the drawbacks of mobile computing in organizational contexts. The report explores various challenges, including security concerns like VPN vulnerabilities and data breaches, bandwidth limitations affecting communication quality, and potential for data loss. The research employs a mixed-methods approach, combining qualitative data from literature reviews, online sources, and company websites with quantitative data gathered through surveys and interviews with IT managers and system administrators from multinational companies. The study identifies research questions to assess the use of mobile computing applications, experiences with data loss, perceived disadvantages, and current mitigation strategies. The methodology includes stratified sampling to gather data from a sample size of 60 employees across four multinational corporations. The project also details the data analysis process using Microsoft Excel, qualitative research steps, and addresses the research's reliability, validity, and limitations, providing a comprehensive overview of the negative impacts of mobile computing and potential solutions.

Running head: BUSINESS RESEARCH
Business Research
Assignment 2
Name of Student
Name of the University
Author Note
Business Research
Assignment 2
Name of Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
BUSINESS RESEARCH
Introduction
The mobile computing is a diverse field which involves the usage of the mobile
communication, mobile software and the mobile hardware. The communication tools are
inclusive of the “ad-hoc” networks as well as the different infrastructure networks (Dinh, Lee
Niyato & Wang, 2013). There are also different communication technologies such as data
formats, protocols, concrete technologies and others which are increasingly used by the
companies. The different hardware components include the device or the mobile components and
the various mobile software includes the requirements as well as characteristics of the mobile
applications. An increasing number of companies are adopting mobile computing due to their
increased benefits of the technology.
The earlier assignment focused on the advantages of the mobile computing for the
business entities. These kinds of services are aimed at improving the services of the
organizations by accessing the resources with the help of accounting systems. However, there are
several pitfalls of mobile computing, which the earlier literature review failed to address. The
earlier assignment failed to address the various disadvantages of the mobile computing, which
would be done in this assignment. The organizations should not forget the fact that they should
undertake preventive measures so that the negative effects of the technology can be averted.
Project Objective
The objectives of this project are to understand the downfalls of the mobile computing
that are increasingly used by the organizations. It has been observed that a lot of organizations
are facing negative consequences due to the implementation of cloud computing. There are
instances of huge loss of privacy, increase in the stress levels in the global sphere, focus on short
BUSINESS RESEARCH
Introduction
The mobile computing is a diverse field which involves the usage of the mobile
communication, mobile software and the mobile hardware. The communication tools are
inclusive of the “ad-hoc” networks as well as the different infrastructure networks (Dinh, Lee
Niyato & Wang, 2013). There are also different communication technologies such as data
formats, protocols, concrete technologies and others which are increasingly used by the
companies. The different hardware components include the device or the mobile components and
the various mobile software includes the requirements as well as characteristics of the mobile
applications. An increasing number of companies are adopting mobile computing due to their
increased benefits of the technology.
The earlier assignment focused on the advantages of the mobile computing for the
business entities. These kinds of services are aimed at improving the services of the
organizations by accessing the resources with the help of accounting systems. However, there are
several pitfalls of mobile computing, which the earlier literature review failed to address. The
earlier assignment failed to address the various disadvantages of the mobile computing, which
would be done in this assignment. The organizations should not forget the fact that they should
undertake preventive measures so that the negative effects of the technology can be averted.
Project Objective
The objectives of this project are to understand the downfalls of the mobile computing
that are increasingly used by the organizations. It has been observed that a lot of organizations
are facing negative consequences due to the implementation of cloud computing. There are
instances of huge loss of privacy, increase in the stress levels in the global sphere, focus on short

2
BUSINESS RESEARCH
term policies and loss of confidential data. The organizations should take adequate preventive
measures to handle such unfortunate events and hence this research aims to devise some
solutions to handle this issue. The objective of this research is to find the drawbacks of installing
a mobile computing system and suggest suitable ways of addressing the issue.
Project Scope
The scope of the project is to understand the implications of mobile computing and how
it can be tackled in the right manner. A situational study would be conducted in which there
would be more emphasis on the downsides of the mobile computing process. It is important to
create awareness for the digital technologies and their probable risks. This project would help in
better understanding of the organizational roles in averting the negatives of the technological
features such as mobile computing. The study would also strive to provide suitable solutions for
the prevention of such negative instances related to the mobile computing. The positive aspects
of mobile computing are outside the scope of this project.
Literature Review
As opined by Rahimi et al. (2014), the mobile computing is concerned with the transfer
of videos, data, voice and other non-wireless equipment which would aid in the day to day
operational process of the organizations. The infrastructure that is placed for the seamless
integration of the digital communication comprises of the basic idea of the mobile computing.
There are several devices such as bandwidth, protocols, services and portals that are important
for facilitation of the various services. The mobile communication also makes sure that there
would be no collision with the other systems in the same network. Gikas and Grant (2013)
argues that the mobile computing is beneficial to the firms to a large extent. There is an increase
BUSINESS RESEARCH
term policies and loss of confidential data. The organizations should take adequate preventive
measures to handle such unfortunate events and hence this research aims to devise some
solutions to handle this issue. The objective of this research is to find the drawbacks of installing
a mobile computing system and suggest suitable ways of addressing the issue.
Project Scope
The scope of the project is to understand the implications of mobile computing and how
it can be tackled in the right manner. A situational study would be conducted in which there
would be more emphasis on the downsides of the mobile computing process. It is important to
create awareness for the digital technologies and their probable risks. This project would help in
better understanding of the organizational roles in averting the negatives of the technological
features such as mobile computing. The study would also strive to provide suitable solutions for
the prevention of such negative instances related to the mobile computing. The positive aspects
of mobile computing are outside the scope of this project.
Literature Review
As opined by Rahimi et al. (2014), the mobile computing is concerned with the transfer
of videos, data, voice and other non-wireless equipment which would aid in the day to day
operational process of the organizations. The infrastructure that is placed for the seamless
integration of the digital communication comprises of the basic idea of the mobile computing.
There are several devices such as bandwidth, protocols, services and portals that are important
for facilitation of the various services. The mobile communication also makes sure that there
would be no collision with the other systems in the same network. Gikas and Grant (2013)
argues that the mobile computing is beneficial to the firms to a large extent. There is an increase
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
BUSINESS RESEARCH
in the connectivity in the cases of mobile computing. There is also an enhanced social
engagement, which is generated by the increased interaction of the users through the internet.
The companies would be able to enhance their services through the use of digital platforms.
The earlier assignment discussed about the various opportunities presented by mobile
computing. It is expected that the mobile computing help the businesses to expand in a massive
scale. They would also help the employees to stay in touch with each other. The mobile
technologies help in the usage of the data and resources in a particular location. There are also
several impacts of mobile computing on the businesses. There have been new phases in the
communication, which has been highlighted. This kind of computing helps in the integration of
the communicational resources with the various entities of the internet (Luan et al., 2015). There
is also an easy transformation of the organizational information and there is transparent
information flow in the organization. in the discipline of mobile computing, there is an
information flow between the temporal and spatial constraints.
The earlier assignment failed to address the drawbacks of the mobile computing services.
As opined by Hashizume, K., Rosado, D. G., Fernández-Medina and Fernandez (2013), there can
be serious level of security concerns when there is a huge level of uncertainty involved with the
mobile VPNs. There are instances when they are unsafe to use and can be hacked easily by an
intruder. There are instances when a Wifi network is hacked and there are instances of WPA and
WEP security breaches. There are also issues with the online transfer of information. There are
issues with the quality of connectivity, in which there is a significant low coverage in certain
areas. There are still issues with the 3G or 4G connectivity in certain parts of the world, which
makes it an issue. There can be issues with the power consumption in which there is short lives
of the batteries and there is non-availability of the same. This may hamper the mobile computing
BUSINESS RESEARCH
in the connectivity in the cases of mobile computing. There is also an enhanced social
engagement, which is generated by the increased interaction of the users through the internet.
The companies would be able to enhance their services through the use of digital platforms.
The earlier assignment discussed about the various opportunities presented by mobile
computing. It is expected that the mobile computing help the businesses to expand in a massive
scale. They would also help the employees to stay in touch with each other. The mobile
technologies help in the usage of the data and resources in a particular location. There are also
several impacts of mobile computing on the businesses. There have been new phases in the
communication, which has been highlighted. This kind of computing helps in the integration of
the communicational resources with the various entities of the internet (Luan et al., 2015). There
is also an easy transformation of the organizational information and there is transparent
information flow in the organization. in the discipline of mobile computing, there is an
information flow between the temporal and spatial constraints.
The earlier assignment failed to address the drawbacks of the mobile computing services.
As opined by Hashizume, K., Rosado, D. G., Fernández-Medina and Fernandez (2013), there can
be serious level of security concerns when there is a huge level of uncertainty involved with the
mobile VPNs. There are instances when they are unsafe to use and can be hacked easily by an
intruder. There are instances when a Wifi network is hacked and there are instances of WPA and
WEP security breaches. There are also issues with the online transfer of information. There are
issues with the quality of connectivity, in which there is a significant low coverage in certain
areas. There are still issues with the 3G or 4G connectivity in certain parts of the world, which
makes it an issue. There can be issues with the power consumption in which there is short lives
of the batteries and there is non-availability of the same. This may hamper the mobile computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
BUSINESS RESEARCH
effectiveness. When there are no security measures, then the IT system intruded by the outsiders.
The power consumption is concerned with the combination of the compact size devices with
expensive batteries.
As defined by Ahmad, S., Haamid et al. (2016), there are insufficient bandwidths that
are associated with mobile internet access such as GPRS, EDGE and others. The low bandwidths
can cause disruption in the quality of the communication processes. There can also be issues with
transmission interferences (Fernando, Loke & Rahayu, 2013). There can be bad weather, terrain
issue and other problems that may interfere with the reception of signal. There is poor reception
of signals in the areas of remote buildings, tunnels and rural areas. If the business is located in
such locations, then there would be issues in the computing process. This is due to the
insufficient bandwidths in remote locations or improper signals in specific regions of the offices.
Research questions
The research question is important for establishing the validity of the research topic. The
following would be the research questions that would help in establishing research topic-
1) Which of the mobile computing applications are you using in your organization?
2) Have you ever suffered from data loss while using mobile computing applications?
3) What do you think are the possible disadvantages of mobile computing?
4) What are the measures you are undertaking for solving the issues related with mobile
computing?
Research Design and Methodology
The research would be based on the usage of mixed research methods in which there
would be application of both quantitative research and qualitative research. This combination
BUSINESS RESEARCH
effectiveness. When there are no security measures, then the IT system intruded by the outsiders.
The power consumption is concerned with the combination of the compact size devices with
expensive batteries.
As defined by Ahmad, S., Haamid et al. (2016), there are insufficient bandwidths that
are associated with mobile internet access such as GPRS, EDGE and others. The low bandwidths
can cause disruption in the quality of the communication processes. There can also be issues with
transmission interferences (Fernando, Loke & Rahayu, 2013). There can be bad weather, terrain
issue and other problems that may interfere with the reception of signal. There is poor reception
of signals in the areas of remote buildings, tunnels and rural areas. If the business is located in
such locations, then there would be issues in the computing process. This is due to the
insufficient bandwidths in remote locations or improper signals in specific regions of the offices.
Research questions
The research question is important for establishing the validity of the research topic. The
following would be the research questions that would help in establishing research topic-
1) Which of the mobile computing applications are you using in your organization?
2) Have you ever suffered from data loss while using mobile computing applications?
3) What do you think are the possible disadvantages of mobile computing?
4) What are the measures you are undertaking for solving the issues related with mobile
computing?
Research Design and Methodology
The research would be based on the usage of mixed research methods in which there
would be application of both quantitative research and qualitative research. This combination

5
BUSINESS RESEARCH
of the data collection method would be based on variety of approach in which there would better
quality of data that is collected. The improved quality of data would ensure better foundation for
data analysis.
Data Collection Method
The qualitative research is going to be done with the help of various sources such as
online sources, literature study, online journals, company websites, IT publications, IT
associations and others (Merriam & Tisdell, 2015).
The quantitative research would be one with the help of face to face interviews and
digital surveys.
Target participant
The employees from four multinational companies would be selected for the purpose of
this review. The age group of the participants would be 24-48 years of age. The IT managers and
the system administrators would be interviewed from the selected multinational companies.
Sample Size
The sample size would be 60 and there would be stratified sampling. A sample group of
15 employees would be chosen randomly from each of the 4 multinational companies. The total
interviewed candidates would be
Research Location
The research would be done in offline as well as online locations. In the online mode, the
surveys would be sent to the respondents through email. The survey would be uploaded online
and the survey link would be sent to the participants so that they can answer the questionnaire.
BUSINESS RESEARCH
of the data collection method would be based on variety of approach in which there would better
quality of data that is collected. The improved quality of data would ensure better foundation for
data analysis.
Data Collection Method
The qualitative research is going to be done with the help of various sources such as
online sources, literature study, online journals, company websites, IT publications, IT
associations and others (Merriam & Tisdell, 2015).
The quantitative research would be one with the help of face to face interviews and
digital surveys.
Target participant
The employees from four multinational companies would be selected for the purpose of
this review. The age group of the participants would be 24-48 years of age. The IT managers and
the system administrators would be interviewed from the selected multinational companies.
Sample Size
The sample size would be 60 and there would be stratified sampling. A sample group of
15 employees would be chosen randomly from each of the 4 multinational companies. The total
interviewed candidates would be
Research Location
The research would be done in offline as well as online locations. In the online mode, the
surveys would be sent to the respondents through email. The survey would be uploaded online
and the survey link would be sent to the participants so that they can answer the questionnaire.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
BUSINESS RESEARCH
The offline research would be carried out by interviewing the employees of the multinational
organizations.
Data Analysis
The data collection for the primary data would be done through the help of Microsoft
Excel (Anderson, Sweeney & Williams, 2014). The data analysis would be performed and
represented through different illustrations such as charts, tables, pie-charts and scatter diagrams.
The qualitative research would be conducted through the use of critical observation as well as
different analytical techniques.
Process of qualitative research
The qualitative research was done with the help of certain steps, which are outlined
below-
The first step was the identification of the research problem in which it was identified
that downfalls of mobile computing needs to be measured.
The next step was the review of the appropriate literature review regarding the
disadvantages of mobile computing.
The next step involved the specification of the research purpose
The next step was followed by the data collection process from the various online sources
The data collection step was followed by the analysis of the collected data so that
necessary conclusions can be deducted.
Reliability and Validity
BUSINESS RESEARCH
The offline research would be carried out by interviewing the employees of the multinational
organizations.
Data Analysis
The data collection for the primary data would be done through the help of Microsoft
Excel (Anderson, Sweeney & Williams, 2014). The data analysis would be performed and
represented through different illustrations such as charts, tables, pie-charts and scatter diagrams.
The qualitative research would be conducted through the use of critical observation as well as
different analytical techniques.
Process of qualitative research
The qualitative research was done with the help of certain steps, which are outlined
below-
The first step was the identification of the research problem in which it was identified
that downfalls of mobile computing needs to be measured.
The next step was the review of the appropriate literature review regarding the
disadvantages of mobile computing.
The next step involved the specification of the research purpose
The next step was followed by the data collection process from the various online sources
The data collection step was followed by the analysis of the collected data so that
necessary conclusions can be deducted.
Reliability and Validity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
BUSINESS RESEARCH
The data collected is a fairly reliable one This is because of the fact that this kind of
research gives fairly same value whenever it is being repeated. This research is also a valid one
since it precisely measures the variable it wishes to measure. The downfalls of the mobile
computing can be effectively measured with this research.
Research Limitations
There are various limitations of the research which would occur once the research
commences. There are situations when there was lack of reliable data for the purpose of
quantitative research and this would make the survey ineffective. There are also chances of lack
of suitable employees from the IT managers from which relevant data can be sourced. There can
be excessive delay in project completion.
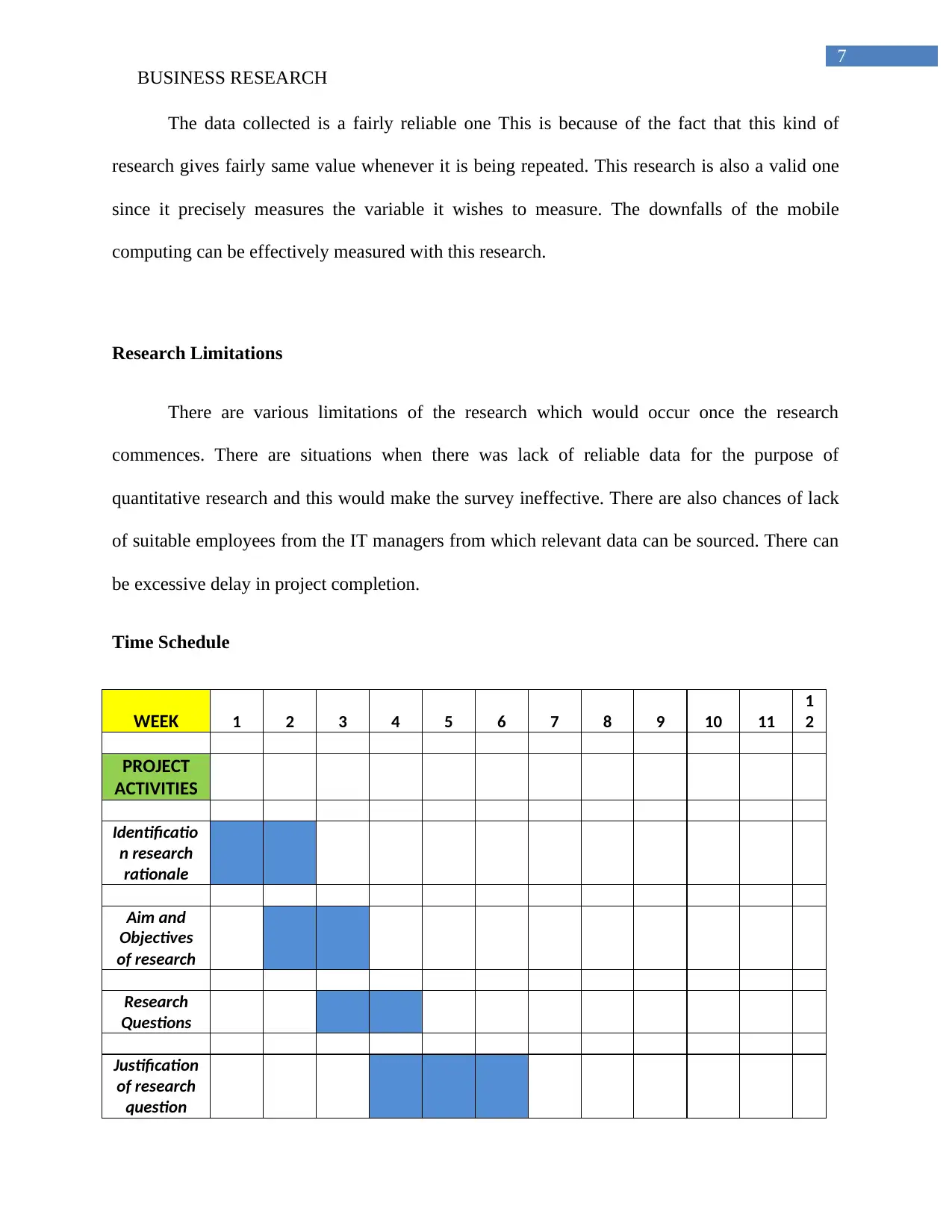
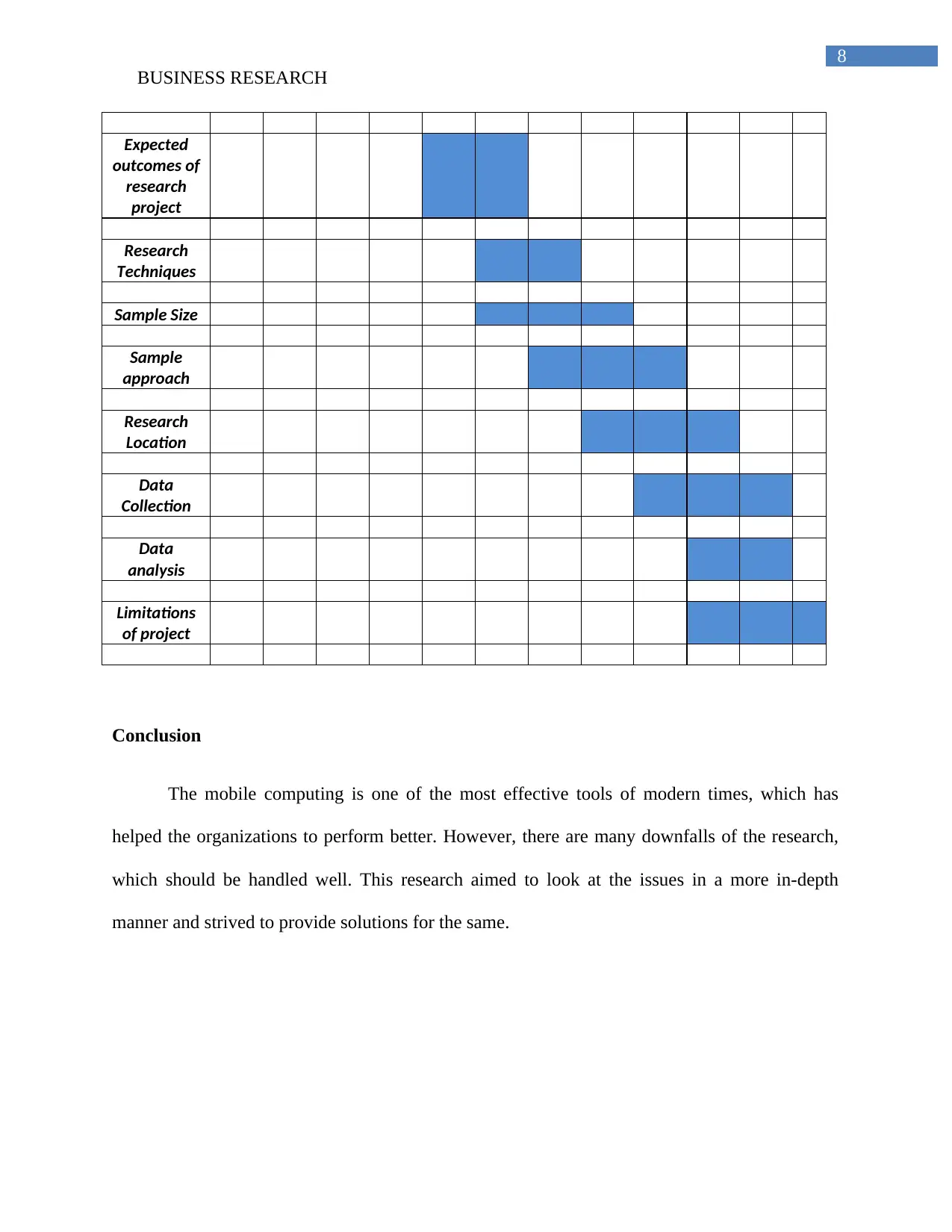
Time Schedule
WEEK 1 2 3 4 5 6 7 8 9 10 11
1
2
PROJECT
ACTIVITIES
Identificatio
n research
rationale
Aim and
Objectives
of research
Research
Questions
Justification
of research
question
BUSINESS RESEARCH
The data collected is a fairly reliable one This is because of the fact that this kind of
research gives fairly same value whenever it is being repeated. This research is also a valid one
since it precisely measures the variable it wishes to measure. The downfalls of the mobile
computing can be effectively measured with this research.
Research Limitations
There are various limitations of the research which would occur once the research
commences. There are situations when there was lack of reliable data for the purpose of
quantitative research and this would make the survey ineffective. There are also chances of lack
of suitable employees from the IT managers from which relevant data can be sourced. There can
be excessive delay in project completion.
Time Schedule
WEEK 1 2 3 4 5 6 7 8 9 10 11
1
2
PROJECT
ACTIVITIES
Identificatio
n research
rationale
Aim and
Objectives
of research
Research
Questions
Justification
of research
question
8
BUSINESS RESEARCH
Expected
outcomes of
research
project
Research
Techniques
Sample Size
Sample
approach
Research
Location
Data
Collection
Data
analysis
Limitations
of project
Conclusion
The mobile computing is one of the most effective tools of modern times, which has
helped the organizations to perform better. However, there are many downfalls of the research,
which should be handled well. This research aimed to look at the issues in a more in-depth
manner and strived to provide solutions for the same.
BUSINESS RESEARCH
Expected
outcomes of
research
project
Research
Techniques
Sample Size
Sample
approach
Research
Location
Data
Collection
Data
analysis
Limitations
of project
Conclusion
The mobile computing is one of the most effective tools of modern times, which has
helped the organizations to perform better. However, there are many downfalls of the research,
which should be handled well. This research aimed to look at the issues in a more in-depth
manner and strived to provide solutions for the same.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
BUSINESS RESEARCH
References
Ahmad, S., Haamid, A. L., Qazi, Z. A., Zhou, Z., Benson, T., & Qazi, I. A. (2016, November). A
view from the other side: Understanding mobile phone characteristics in the developing
world. In Proceedings of the 2016 ACM on Internet Measurement Conference (pp. 319-
325). ACM.
Anderson, D., Sweeney, D., & Williams, T. (2014). Modern business statistics with Microsoft
Excel. Nelson Education.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing:
architecture, applications, and approaches. Wireless communications and mobile
computing, 13(18), 1587-1611.
Fernando, N., Loke, S. W., & Rahayu, W. (2013). Mobile cloud computing: A survey. Future
generation computer systems, 29(1), 84-106.
Gikas, J., & Grant, M. M. (2013). Mobile computing devices in higher education: Student
perspectives on learning with cellphones, smartphones & social media. The Internet and
Higher Education, 19, 18-26.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An analysis of
security issues for cloud computing. Journal of Internet Services and Applications, 4(1),
5.
Luan, T. H., Gao, L., Li, Z., Xiang, Y., Wei, G., & Sun, L. (2015). Fog computing: Focusing on
mobile users at the edge. arXiv preprint arXiv:1502.01815.
BUSINESS RESEARCH
References
Ahmad, S., Haamid, A. L., Qazi, Z. A., Zhou, Z., Benson, T., & Qazi, I. A. (2016, November). A
view from the other side: Understanding mobile phone characteristics in the developing
world. In Proceedings of the 2016 ACM on Internet Measurement Conference (pp. 319-
325). ACM.
Anderson, D., Sweeney, D., & Williams, T. (2014). Modern business statistics with Microsoft
Excel. Nelson Education.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing:
architecture, applications, and approaches. Wireless communications and mobile
computing, 13(18), 1587-1611.
Fernando, N., Loke, S. W., & Rahayu, W. (2013). Mobile cloud computing: A survey. Future
generation computer systems, 29(1), 84-106.
Gikas, J., & Grant, M. M. (2013). Mobile computing devices in higher education: Student
perspectives on learning with cellphones, smartphones & social media. The Internet and
Higher Education, 19, 18-26.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An analysis of
security issues for cloud computing. Journal of Internet Services and Applications, 4(1),
5.
Luan, T. H., Gao, L., Li, Z., Xiang, Y., Wei, G., & Sun, L. (2015). Fog computing: Focusing on
mobile users at the edge. arXiv preprint arXiv:1502.01815.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
BUSINESS RESEARCH
Merriam, S. B., & Tisdell, E. J. (2015). Qualitative research: A guide to design and
implementation. John Wiley & Sons.
Rahimi, M. R., Ren, J., Liu, C. H., Vasilakos, A. V., & Venkatasubramanian, N. (2014). Mobile
cloud computing: A survey, state of art and future directions. Mobile Networks and
Applications, 19(2), 133-143.
BUSINESS RESEARCH
Merriam, S. B., & Tisdell, E. J. (2015). Qualitative research: A guide to design and
implementation. John Wiley & Sons.
Rahimi, M. R., Ren, J., Liu, C. H., Vasilakos, A. V., & Venkatasubramanian, N. (2014). Mobile
cloud computing: A survey, state of art and future directions. Mobile Networks and
Applications, 19(2), 133-143.

11
BUSINESS RESEARCH
Research Questionnaire
1. What is your take on the issue of mobile computing?
2. What do you think about the IT security in your organizations?
3. Why you feel that it is important for your organization to implement adequate security
measures for mobile computing?
4. At present, what are the threats faced by your organization concerning mobile
computing?
5. Are you afraid of the loss of your confidential data over the digital platform?
6. What are you doing to prevent your files from getting hacked by a third-party offender?
7. How much budget your organization allocates for IT security every year?
8. Do you think it is adequate for protecting the mobile computing services? If no, why?
BUSINESS RESEARCH
Research Questionnaire
1. What is your take on the issue of mobile computing?
2. What do you think about the IT security in your organizations?
3. Why you feel that it is important for your organization to implement adequate security
measures for mobile computing?
4. At present, what are the threats faced by your organization concerning mobile
computing?
5. Are you afraid of the loss of your confidential data over the digital platform?
6. What are you doing to prevent your files from getting hacked by a third-party offender?
7. How much budget your organization allocates for IT security every year?
8. Do you think it is adequate for protecting the mobile computing services? If no, why?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





