Security in Mobile Computing: Literature Review and Proposed Research
VerifiedAdded on 2023/01/18
|25
|5600
|67
Report
AI Summary
This report presents a literature review on the topic of security in mobile computing. The student researcher has explored various articles and research papers to understand the security challenges and threats within the mobile computing sector. The report begins with a broad scan of keywords like 'mobile security', 'MDM', and 'BYOD', and then narrows down to focus on specific articles, summarizing key findings and identifying critical issues. The report also discusses the evolution of technologies like fog computing, mobile cloud computing, and mobile edge computing and their associated security considerations. The student highlights the need for enhanced security measures, especially in the context of BYOD policies and the increasing use of personal devices for accessing organizational data. Finally, the report includes a proposed research section that aims to address the identified gaps and contribute to the advancement of mobile computing security.

Running head: SECURITY IN MOBILE COMPUTING
Security in Mobile Computing
Name of the Student
Student ID
Author’s note
Security in Mobile Computing
Name of the Student
Student ID
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY IN MOBILE COMPUTING
Abstract
The discussion in this report is mainly based over focusing over the works of various authors and
their related articles. The research is based on the topic of security in the platform of mobile
computing. In the recent times, there have been major topics of security breaches that have
occurred within the area of mobile computing. In this article, we have researched over these
article in order to understand about the various aspects of security within the mobile computing
sector and thus understand about the various kind of steps, which could be approached in order
to mitigate the chances of problems within the sector. All the associated sectors that could be
prone to such kind of attacks have also been discussed in this part of the report. Thus this
research would be helpful in understanding about the needs of security aspects that could be
enforced within the mobile computing platform.
Abstract
The discussion in this report is mainly based over focusing over the works of various authors and
their related articles. The research is based on the topic of security in the platform of mobile
computing. In the recent times, there have been major topics of security breaches that have
occurred within the area of mobile computing. In this article, we have researched over these
article in order to understand about the various aspects of security within the mobile computing
sector and thus understand about the various kind of steps, which could be approached in order
to mitigate the chances of problems within the sector. All the associated sectors that could be
prone to such kind of attacks have also been discussed in this part of the report. Thus this
research would be helpful in understanding about the needs of security aspects that could be
enforced within the mobile computing platform.

2SECURITY IN MOBILE COMPUTING
Table of Contents
1. Literature Review – Broad Scan and Reading.............................................................................3
1.1 Round 1..................................................................................................................................3
1.1.1 Search Keyword..............................................................................................................3
1.1.2 Result..............................................................................................................................3
1.2 Round 2..................................................................................................................................6
1.2.1 Search Keyword..............................................................................................................6
1.2.2 Result..............................................................................................................................6
1.3 Round 3................................................................................................................................10
1.3.1 Search Keyword............................................................................................................10
1.3.2 Result............................................................................................................................10
2. Literature Review – Focused Reading.......................................................................................13
2.1 Detail Reading of Article 1..................................................................................................13
2.2 Detail Reading of Article 2..................................................................................................15
2.3 Detail Reading of Article 3..................................................................................................17
2.4 Detail Reading of Article 4..................................................................................................19
3. Proposed Research.....................................................................................................................21
References......................................................................................................................................23
Table of Contents
1. Literature Review – Broad Scan and Reading.............................................................................3
1.1 Round 1..................................................................................................................................3
1.1.1 Search Keyword..............................................................................................................3
1.1.2 Result..............................................................................................................................3
1.2 Round 2..................................................................................................................................6
1.2.1 Search Keyword..............................................................................................................6
1.2.2 Result..............................................................................................................................6
1.3 Round 3................................................................................................................................10
1.3.1 Search Keyword............................................................................................................10
1.3.2 Result............................................................................................................................10
2. Literature Review – Focused Reading.......................................................................................13
2.1 Detail Reading of Article 1..................................................................................................13
2.2 Detail Reading of Article 2..................................................................................................15
2.3 Detail Reading of Article 3..................................................................................................17
2.4 Detail Reading of Article 4..................................................................................................19
3. Proposed Research.....................................................................................................................21
References......................................................................................................................................23
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3SECURITY IN MOBILE COMPUTING
1. Literature Review – Broad Scan and Reading
1.1 Round 1
1.1.1 Search Keyword
I was researching over the factors that lead to the security issues in mobile computing.
There were a lot of research that was conducted in choosing the proper keywords and would lead
to the issues that were arising in the field of mobile computing.
Keyword Source/research database Number of results
Mobile security, MDM, Mobile Botnets,
MAM, BYOD
Google Scholar 3,180,000
1.1.2 Result
Title Author Journal/conference Year
BYOD: Current State
and Security
Challenges
Meisam Eslahi,
Maryam Var Naseri,
H. Hashim, N.M.
Tahir, Ezril Hisham
Mat Saad
IEEE Symposium on Computer
Applications and Industrial
Electronics (ISCAIE)
2014, April
Security of self-
organizing networks:
MANET, WSN,
WMN, VANET
Pathan, Al-Sakib
Khan
CRC press 2016
Mobile malware
security challeges and
cloud-based detection
Penning, Nicholas,
Michael Hoffman,
Jason Nikolai, and
Yong Wang
International Conference on
Collaboration Technologies
and Systems (CTS)
2014
Mobile app
recommendations
with security and
privacy awareness
Zhu, Hengshu, Hui
Xiong, Yong Ge, and
Enhong Chen
In Proceedings of the 20th
ACM SIGKDD international
conference on Knowledge
discovery and data mining
2014
Privacy and security
in mobile health
apps: a review and
recommendations
Martínez-Pérez,
Borja, Isabel De La
Torre-Díez, and
Miguel López-
Coronado
Journal of medical systems 2015
1. Literature Review – Broad Scan and Reading
1.1 Round 1
1.1.1 Search Keyword
I was researching over the factors that lead to the security issues in mobile computing.
There were a lot of research that was conducted in choosing the proper keywords and would lead
to the issues that were arising in the field of mobile computing.
Keyword Source/research database Number of results
Mobile security, MDM, Mobile Botnets,
MAM, BYOD
Google Scholar 3,180,000
1.1.2 Result
Title Author Journal/conference Year
BYOD: Current State
and Security
Challenges
Meisam Eslahi,
Maryam Var Naseri,
H. Hashim, N.M.
Tahir, Ezril Hisham
Mat Saad
IEEE Symposium on Computer
Applications and Industrial
Electronics (ISCAIE)
2014, April
Security of self-
organizing networks:
MANET, WSN,
WMN, VANET
Pathan, Al-Sakib
Khan
CRC press 2016
Mobile malware
security challeges and
cloud-based detection
Penning, Nicholas,
Michael Hoffman,
Jason Nikolai, and
Yong Wang
International Conference on
Collaboration Technologies
and Systems (CTS)
2014
Mobile app
recommendations
with security and
privacy awareness
Zhu, Hengshu, Hui
Xiong, Yong Ge, and
Enhong Chen
In Proceedings of the 20th
ACM SIGKDD international
conference on Knowledge
discovery and data mining
2014
Privacy and security
in mobile health
apps: a review and
recommendations
Martínez-Pérez,
Borja, Isabel De La
Torre-Díez, and
Miguel López-
Coronado
Journal of medical systems 2015
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SECURITY IN MOBILE COMPUTING
Software-defined
mobile networks
security Mobile
Networks and
Applications
Chen, Min, Yongfeng
Qian, Shiwen Mao,
Wan Tang, and
Ximin Yang
Mobile Networks and
Applications
2016
Exploring the far side
of mobile health:
information security
and privacy of mobile
health apps on iOS
and Android
Dehling, Tobias,
Fangjian Gao,
Stephan Schneider,
and Ali Sunyaev
JMIR mHealth and uHealth 2015
Security and privacy
in mobile
crowdsourcing
networks: challenges
and opportunities
Yang, Kan, Kuan
Zhang, Ju Ren, and
Xuemin Shen
IEEE communications
magazine
2015
Security
enhancements for
mobile ad hoc
networks with trust
management using
uncertain reasoning
Wei, Zhexiong,
Helen Tang, F.
Richard Yu, Maoyu
Wang, and Peter
Mason
IEEE Transactions on
Vehicular Technology
2014
Mobile device
security
considerations for
small-and medium-
sized enterprise
business mobility
A. Harris, Mark, and
Karen P. Patten
Information Management &
Computer Security
2014
The untapped
potential of trusted
execution
environments on
mobile devices
Ekberg, Jan-Erik,
Kari Kostiainen, and
N. Asokan
IEEE Security & Privacy 2014
Always connected,
but are smart mobile
users getting more
security savvy? A
survey of smart
mobile device users.
Imgraben, James,
Alewyn Engelbrecht,
and Kim-Kwang
Raymond Choo
Behaviour & Information
Technology
2014
Mobile security Kravets, Alla G., In Joint Conference on 2014
Software-defined
mobile networks
security Mobile
Networks and
Applications
Chen, Min, Yongfeng
Qian, Shiwen Mao,
Wan Tang, and
Ximin Yang
Mobile Networks and
Applications
2016
Exploring the far side
of mobile health:
information security
and privacy of mobile
health apps on iOS
and Android
Dehling, Tobias,
Fangjian Gao,
Stephan Schneider,
and Ali Sunyaev
JMIR mHealth and uHealth 2015
Security and privacy
in mobile
crowdsourcing
networks: challenges
and opportunities
Yang, Kan, Kuan
Zhang, Ju Ren, and
Xuemin Shen
IEEE communications
magazine
2015
Security
enhancements for
mobile ad hoc
networks with trust
management using
uncertain reasoning
Wei, Zhexiong,
Helen Tang, F.
Richard Yu, Maoyu
Wang, and Peter
Mason
IEEE Transactions on
Vehicular Technology
2014
Mobile device
security
considerations for
small-and medium-
sized enterprise
business mobility
A. Harris, Mark, and
Karen P. Patten
Information Management &
Computer Security
2014
The untapped
potential of trusted
execution
environments on
mobile devices
Ekberg, Jan-Erik,
Kari Kostiainen, and
N. Asokan
IEEE Security & Privacy 2014
Always connected,
but are smart mobile
users getting more
security savvy? A
survey of smart
mobile device users.
Imgraben, James,
Alewyn Engelbrecht,
and Kim-Kwang
Raymond Choo
Behaviour & Information
Technology
2014
Mobile security Kravets, Alla G., In Joint Conference on 2014
5SECURITY IN MOBILE COMPUTING
solution for enterprise
network
Ngoc Duong Bui, and
Mohammed Al-
Ashval
Knowledge-Based Software
Engineering
Mobile security
testing approaches
and challenges
Wang, Yong, and
Yazan Alshboul
First Conference on Mobile
and Secure Services
(MOBISECSERV)
2015
Security threats to
mobile multimedia
applications: Camera-
based attacks on
mobile phones.
Wu, Longfei,
Xiaojiang Du, and
Xinwen Fu
IEEE Communications
Magazine
2014
Outsourcing mobile
security in the cloud
Hurel, Gaëtan, Rémi
Badonnel,
Abdelkader Lahmadi,
and Olivier Festor
IFIP International Conference
on Autonomous Infrastructure,
Management and Security
2014
Security and privacy
in mobile social
networks: challenges
and solutions
Liang, Xiaohui, Kuan
Zhang, Xuemin Shen,
and Xiaodong Lin
IEEE Wireless
Communications
2014
A mean field game
theoretic approach for
security
enhancements in
mobile ad hoc
networks
Wang, Yanwei, F.
Richard Yu, Helen
Tang, and Minyi
Huang
IEEE transactions on wireless
communications
2014
Handbook of Mobile
Radio Networks
Tabbane, Sami Artech House Mobile
Communications Library
2014
Security and privacy
challenges in mobile
cloud computing:
Survey and way
ahead
Mollah, Muhammad
Baqer, Md Abul
Kalam Azad, and
Athanasios Vasilakos
Journal of Network and
Computer Applications
2017
Review and Summary – After conducting a review over the search results based on the
keywords, I could find that the mobile devices are not fully protected as compared to the
computer devices and computer networks. In case of mobile based devices, the users pay a little
attention towards the security updates that are provided to an application. During the initial
solution for enterprise
network
Ngoc Duong Bui, and
Mohammed Al-
Ashval
Knowledge-Based Software
Engineering
Mobile security
testing approaches
and challenges
Wang, Yong, and
Yazan Alshboul
First Conference on Mobile
and Secure Services
(MOBISECSERV)
2015
Security threats to
mobile multimedia
applications: Camera-
based attacks on
mobile phones.
Wu, Longfei,
Xiaojiang Du, and
Xinwen Fu
IEEE Communications
Magazine
2014
Outsourcing mobile
security in the cloud
Hurel, Gaëtan, Rémi
Badonnel,
Abdelkader Lahmadi,
and Olivier Festor
IFIP International Conference
on Autonomous Infrastructure,
Management and Security
2014
Security and privacy
in mobile social
networks: challenges
and solutions
Liang, Xiaohui, Kuan
Zhang, Xuemin Shen,
and Xiaodong Lin
IEEE Wireless
Communications
2014
A mean field game
theoretic approach for
security
enhancements in
mobile ad hoc
networks
Wang, Yanwei, F.
Richard Yu, Helen
Tang, and Minyi
Huang
IEEE transactions on wireless
communications
2014
Handbook of Mobile
Radio Networks
Tabbane, Sami Artech House Mobile
Communications Library
2014
Security and privacy
challenges in mobile
cloud computing:
Survey and way
ahead
Mollah, Muhammad
Baqer, Md Abul
Kalam Azad, and
Athanasios Vasilakos
Journal of Network and
Computer Applications
2017
Review and Summary – After conducting a review over the search results based on the
keywords, I could find that the mobile devices are not fully protected as compared to the
computer devices and computer networks. In case of mobile based devices, the users pay a little
attention towards the security updates that are provided to an application. During the initial
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SECURITY IN MOBILE COMPUTING
search over the keywords within the article, it was also found that the security of mobile devices
has become a critical issue in BYOD. In certain cases, employees are more concerned to make
use of their personal devices to access the data and systems within an organisation. Hence, this
article discusses about the critical aspects in relation to security in mobile computing technology.
1.2 Round 2
1.2.1 Search Keyword
Keyword Source/research database Number of results
Privacy, Security, Fog computing,
Mobile cloud computing, Mobile edge
computing.
Google Scholar 1,260,000
1.2.2 Result
Title Author Journal/conference Year
Mobile edge computing, fog
et al.: A survey and analysis
of security threats and
challenges
Roman, Rodrigo, Javier
Lopez, and Masahiro
Mambo
Future Generation
Computer Systems
2018
The fog computing
paradigm: Scenarios and
security issues
Stojmenovic, Ivan, and
Sheng Wen
Federated Conference
on Computer Science
and Information
Systems
2014
Finding your way in the
fog: Towards a
comprehensive definition of
fog computing
Vaquero, Luis M., and Luis
Rodero-Merino
ACM SIGCOMM
Computer
Communication
Review
2014
Fog computing: A platform
for internet of things and
analytics
Bonomi, Flavio, Rodolfo
Milito, Preethi Natarajan,
and Jiang Zhu
In Big data and
internet of things: A
roadmap for smart
environments
2014
Heterogeneity in mobile
cloud computing: taxonomy
and open challenges
Sanaei, Zohreh, Saeid
Abolfazli, Abdullah Gani,
and Rajkumar Buyya
IEEE
Communications
Surveys & Tutorials
2014
Decentralized computation Chen, Xu IEEE Transactions on 2015
search over the keywords within the article, it was also found that the security of mobile devices
has become a critical issue in BYOD. In certain cases, employees are more concerned to make
use of their personal devices to access the data and systems within an organisation. Hence, this
article discusses about the critical aspects in relation to security in mobile computing technology.
1.2 Round 2
1.2.1 Search Keyword
Keyword Source/research database Number of results
Privacy, Security, Fog computing,
Mobile cloud computing, Mobile edge
computing.
Google Scholar 1,260,000
1.2.2 Result
Title Author Journal/conference Year
Mobile edge computing, fog
et al.: A survey and analysis
of security threats and
challenges
Roman, Rodrigo, Javier
Lopez, and Masahiro
Mambo
Future Generation
Computer Systems
2018
The fog computing
paradigm: Scenarios and
security issues
Stojmenovic, Ivan, and
Sheng Wen
Federated Conference
on Computer Science
and Information
Systems
2014
Finding your way in the
fog: Towards a
comprehensive definition of
fog computing
Vaquero, Luis M., and Luis
Rodero-Merino
ACM SIGCOMM
Computer
Communication
Review
2014
Fog computing: A platform
for internet of things and
analytics
Bonomi, Flavio, Rodolfo
Milito, Preethi Natarajan,
and Jiang Zhu
In Big data and
internet of things: A
roadmap for smart
environments
2014
Heterogeneity in mobile
cloud computing: taxonomy
and open challenges
Sanaei, Zohreh, Saeid
Abolfazli, Abdullah Gani,
and Rajkumar Buyya
IEEE
Communications
Surveys & Tutorials
2014
Decentralized computation Chen, Xu IEEE Transactions on 2015
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
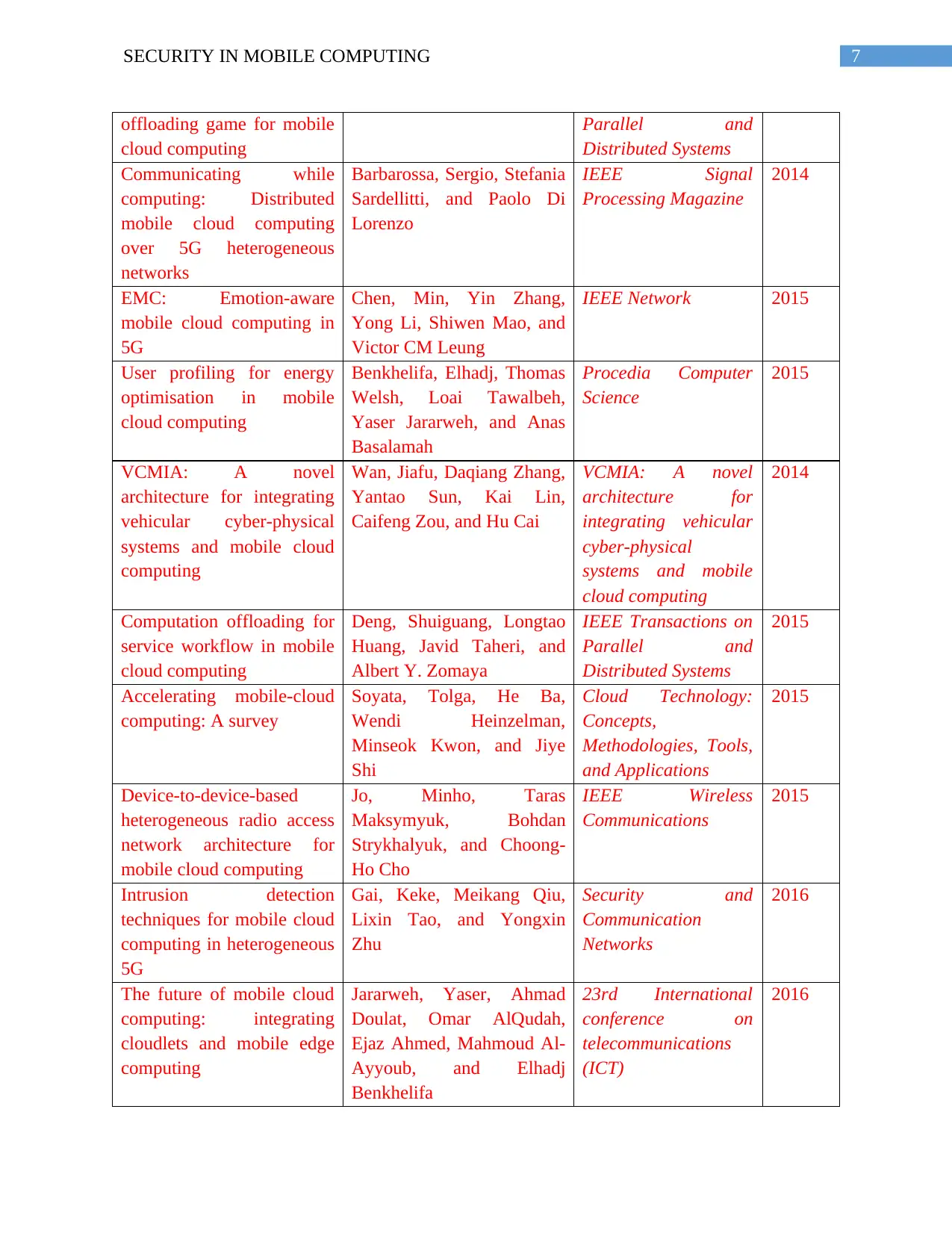
7SECURITY IN MOBILE COMPUTING
offloading game for mobile
cloud computing
Parallel and
Distributed Systems
Communicating while
computing: Distributed
mobile cloud computing
over 5G heterogeneous
networks
Barbarossa, Sergio, Stefania
Sardellitti, and Paolo Di
Lorenzo
IEEE Signal
Processing Magazine
2014
EMC: Emotion-aware
mobile cloud computing in
5G
Chen, Min, Yin Zhang,
Yong Li, Shiwen Mao, and
Victor CM Leung
IEEE Network 2015
User profiling for energy
optimisation in mobile
cloud computing
Benkhelifa, Elhadj, Thomas
Welsh, Loai Tawalbeh,
Yaser Jararweh, and Anas
Basalamah
Procedia Computer
Science
2015
VCMIA: A novel
architecture for integrating
vehicular cyber-physical
systems and mobile cloud
computing
Wan, Jiafu, Daqiang Zhang,
Yantao Sun, Kai Lin,
Caifeng Zou, and Hu Cai
VCMIA: A novel
architecture for
integrating vehicular
cyber-physical
systems and mobile
cloud computing
2014
Computation offloading for
service workflow in mobile
cloud computing
Deng, Shuiguang, Longtao
Huang, Javid Taheri, and
Albert Y. Zomaya
IEEE Transactions on
Parallel and
Distributed Systems
2015
Accelerating mobile-cloud
computing: A survey
Soyata, Tolga, He Ba,
Wendi Heinzelman,
Minseok Kwon, and Jiye
Shi
Cloud Technology:
Concepts,
Methodologies, Tools,
and Applications
2015
Device-to-device-based
heterogeneous radio access
network architecture for
mobile cloud computing
Jo, Minho, Taras
Maksymyuk, Bohdan
Strykhalyuk, and Choong-
Ho Cho
IEEE Wireless
Communications
2015
Intrusion detection
techniques for mobile cloud
computing in heterogeneous
5G
Gai, Keke, Meikang Qiu,
Lixin Tao, and Yongxin
Zhu
Security and
Communication
Networks
2016
The future of mobile cloud
computing: integrating
cloudlets and mobile edge
computing
Jararweh, Yaser, Ahmad
Doulat, Omar AlQudah,
Ejaz Ahmed, Mahmoud Al-
Ayyoub, and Elhadj
Benkhelifa
23rd International
conference on
telecommunications
(ICT)
2016
offloading game for mobile
cloud computing
Parallel and
Distributed Systems
Communicating while
computing: Distributed
mobile cloud computing
over 5G heterogeneous
networks
Barbarossa, Sergio, Stefania
Sardellitti, and Paolo Di
Lorenzo
IEEE Signal
Processing Magazine
2014
EMC: Emotion-aware
mobile cloud computing in
5G
Chen, Min, Yin Zhang,
Yong Li, Shiwen Mao, and
Victor CM Leung
IEEE Network 2015
User profiling for energy
optimisation in mobile
cloud computing
Benkhelifa, Elhadj, Thomas
Welsh, Loai Tawalbeh,
Yaser Jararweh, and Anas
Basalamah
Procedia Computer
Science
2015
VCMIA: A novel
architecture for integrating
vehicular cyber-physical
systems and mobile cloud
computing
Wan, Jiafu, Daqiang Zhang,
Yantao Sun, Kai Lin,
Caifeng Zou, and Hu Cai
VCMIA: A novel
architecture for
integrating vehicular
cyber-physical
systems and mobile
cloud computing
2014
Computation offloading for
service workflow in mobile
cloud computing
Deng, Shuiguang, Longtao
Huang, Javid Taheri, and
Albert Y. Zomaya
IEEE Transactions on
Parallel and
Distributed Systems
2015
Accelerating mobile-cloud
computing: A survey
Soyata, Tolga, He Ba,
Wendi Heinzelman,
Minseok Kwon, and Jiye
Shi
Cloud Technology:
Concepts,
Methodologies, Tools,
and Applications
2015
Device-to-device-based
heterogeneous radio access
network architecture for
mobile cloud computing
Jo, Minho, Taras
Maksymyuk, Bohdan
Strykhalyuk, and Choong-
Ho Cho
IEEE Wireless
Communications
2015
Intrusion detection
techniques for mobile cloud
computing in heterogeneous
5G
Gai, Keke, Meikang Qiu,
Lixin Tao, and Yongxin
Zhu
Security and
Communication
Networks
2016
The future of mobile cloud
computing: integrating
cloudlets and mobile edge
computing
Jararweh, Yaser, Ahmad
Doulat, Omar AlQudah,
Ejaz Ahmed, Mahmoud Al-
Ayyoub, and Elhadj
Benkhelifa
23rd International
conference on
telecommunications
(ICT)
2016
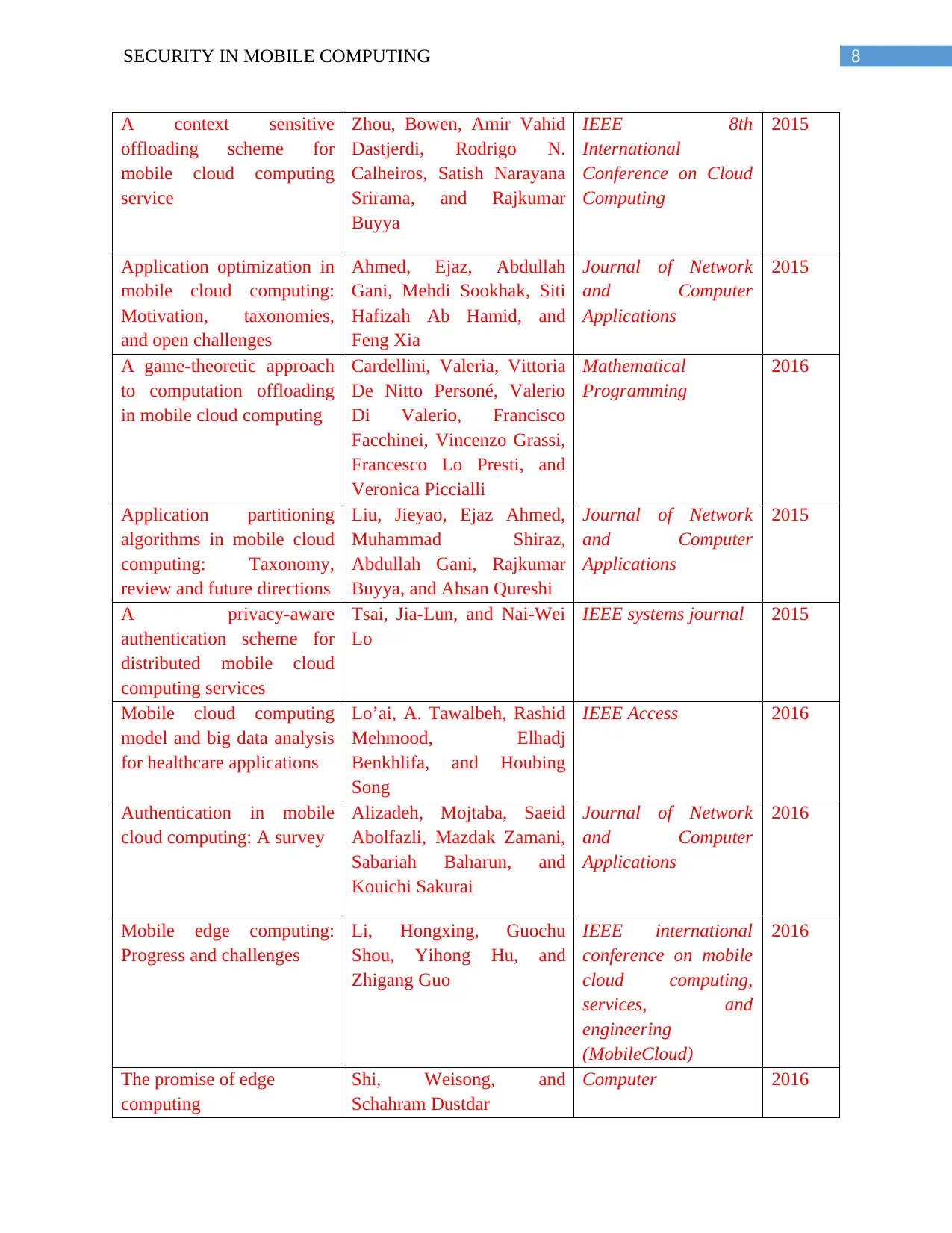
8SECURITY IN MOBILE COMPUTING
A context sensitive
offloading scheme for
mobile cloud computing
service
Zhou, Bowen, Amir Vahid
Dastjerdi, Rodrigo N.
Calheiros, Satish Narayana
Srirama, and Rajkumar
Buyya
IEEE 8th
International
Conference on Cloud
Computing
2015
Application optimization in
mobile cloud computing:
Motivation, taxonomies,
and open challenges
Ahmed, Ejaz, Abdullah
Gani, Mehdi Sookhak, Siti
Hafizah Ab Hamid, and
Feng Xia
Journal of Network
and Computer
Applications
2015
A game-theoretic approach
to computation offloading
in mobile cloud computing
Cardellini, Valeria, Vittoria
De Nitto Personé, Valerio
Di Valerio, Francisco
Facchinei, Vincenzo Grassi,
Francesco Lo Presti, and
Veronica Piccialli
Mathematical
Programming
2016
Application partitioning
algorithms in mobile cloud
computing: Taxonomy,
review and future directions
Liu, Jieyao, Ejaz Ahmed,
Muhammad Shiraz,
Abdullah Gani, Rajkumar
Buyya, and Ahsan Qureshi
Journal of Network
and Computer
Applications
2015
A privacy-aware
authentication scheme for
distributed mobile cloud
computing services
Tsai, Jia-Lun, and Nai-Wei
Lo
IEEE systems journal 2015
Mobile cloud computing
model and big data analysis
for healthcare applications
Lo’ai, A. Tawalbeh, Rashid
Mehmood, Elhadj
Benkhlifa, and Houbing
Song
IEEE Access 2016
Authentication in mobile
cloud computing: A survey
Alizadeh, Mojtaba, Saeid
Abolfazli, Mazdak Zamani,
Sabariah Baharun, and
Kouichi Sakurai
Journal of Network
and Computer
Applications
2016
Mobile edge computing:
Progress and challenges
Li, Hongxing, Guochu
Shou, Yihong Hu, and
Zhigang Guo
IEEE international
conference on mobile
cloud computing,
services, and
engineering
(MobileCloud)
2016
The promise of edge
computing
Shi, Weisong, and
Schahram Dustdar
Computer 2016
A context sensitive
offloading scheme for
mobile cloud computing
service
Zhou, Bowen, Amir Vahid
Dastjerdi, Rodrigo N.
Calheiros, Satish Narayana
Srirama, and Rajkumar
Buyya
IEEE 8th
International
Conference on Cloud
Computing
2015
Application optimization in
mobile cloud computing:
Motivation, taxonomies,
and open challenges
Ahmed, Ejaz, Abdullah
Gani, Mehdi Sookhak, Siti
Hafizah Ab Hamid, and
Feng Xia
Journal of Network
and Computer
Applications
2015
A game-theoretic approach
to computation offloading
in mobile cloud computing
Cardellini, Valeria, Vittoria
De Nitto Personé, Valerio
Di Valerio, Francisco
Facchinei, Vincenzo Grassi,
Francesco Lo Presti, and
Veronica Piccialli
Mathematical
Programming
2016
Application partitioning
algorithms in mobile cloud
computing: Taxonomy,
review and future directions
Liu, Jieyao, Ejaz Ahmed,
Muhammad Shiraz,
Abdullah Gani, Rajkumar
Buyya, and Ahsan Qureshi
Journal of Network
and Computer
Applications
2015
A privacy-aware
authentication scheme for
distributed mobile cloud
computing services
Tsai, Jia-Lun, and Nai-Wei
Lo
IEEE systems journal 2015
Mobile cloud computing
model and big data analysis
for healthcare applications
Lo’ai, A. Tawalbeh, Rashid
Mehmood, Elhadj
Benkhlifa, and Houbing
Song
IEEE Access 2016
Authentication in mobile
cloud computing: A survey
Alizadeh, Mojtaba, Saeid
Abolfazli, Mazdak Zamani,
Sabariah Baharun, and
Kouichi Sakurai
Journal of Network
and Computer
Applications
2016
Mobile edge computing:
Progress and challenges
Li, Hongxing, Guochu
Shou, Yihong Hu, and
Zhigang Guo
IEEE international
conference on mobile
cloud computing,
services, and
engineering
(MobileCloud)
2016
The promise of edge
computing
Shi, Weisong, and
Schahram Dustdar
Computer 2016
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SECURITY IN MOBILE COMPUTING
A cooperative scheduling
scheme of local cloud and
internet cloud for delay-
aware mobile cloud
computing
Zhao, Tianchu, Sheng Zhou,
Xueying Guo, Yun Zhao,
and Zhisheng Niu
IEEE Globecom
Workshops (GC
Wkshps)
2015
Review and Summary – Based on the search of the initial search results over the article,
I have been able to discuss and understand about the certain requirements that would be
extremely crucial for developing several applications. It has been seen that in the recent years, a
vast number of technologies such as fog computing, mobile cloud computing, mobile edge
computing have evolved. Based on the review over the article, I have been also able to
understand about analysing security challenges, threats and other mechanisms that would be
inherent in various edge paradigms.
A cooperative scheduling
scheme of local cloud and
internet cloud for delay-
aware mobile cloud
computing
Zhao, Tianchu, Sheng Zhou,
Xueying Guo, Yun Zhao,
and Zhisheng Niu
IEEE Globecom
Workshops (GC
Wkshps)
2015
Review and Summary – Based on the search of the initial search results over the article,
I have been able to discuss and understand about the certain requirements that would be
extremely crucial for developing several applications. It has been seen that in the recent years, a
vast number of technologies such as fog computing, mobile cloud computing, mobile edge
computing have evolved. Based on the review over the article, I have been also able to
understand about analysing security challenges, threats and other mechanisms that would be
inherent in various edge paradigms.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
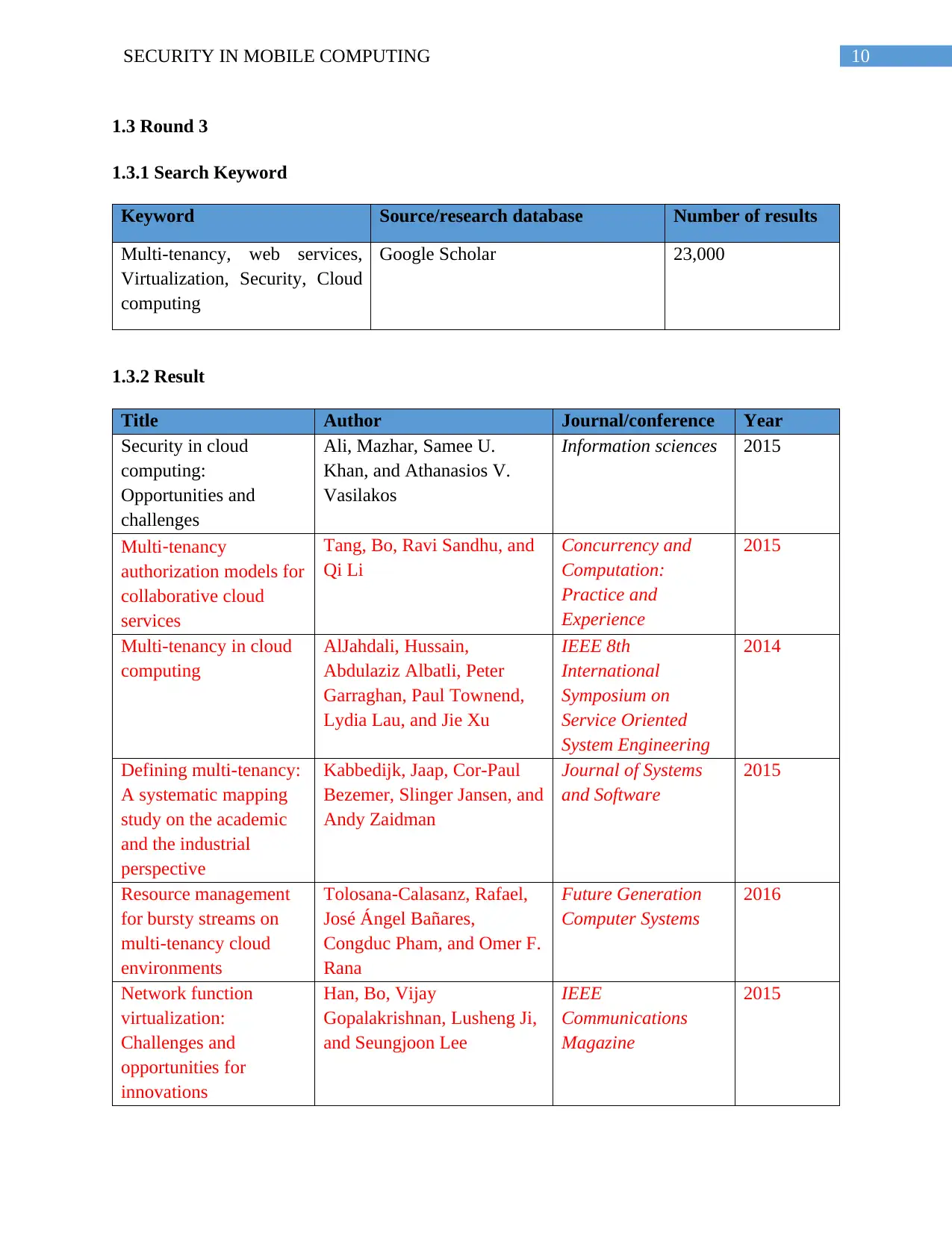
10SECURITY IN MOBILE COMPUTING
1.3 Round 3
1.3.1 Search Keyword
Keyword Source/research database Number of results
Multi-tenancy, web services,
Virtualization, Security, Cloud
computing
Google Scholar 23,000
1.3.2 Result
Title Author Journal/conference Year
Security in cloud
computing:
Opportunities and
challenges
Ali, Mazhar, Samee U.
Khan, and Athanasios V.
Vasilakos
Information sciences 2015
Multi‐tenancy
authorization models for
collaborative cloud
services
Tang, Bo, Ravi Sandhu, and
Qi Li
Concurrency and
Computation:
Practice and
Experience
2015
Multi-tenancy in cloud
computing
AlJahdali, Hussain,
Abdulaziz Albatli, Peter
Garraghan, Paul Townend,
Lydia Lau, and Jie Xu
IEEE 8th
International
Symposium on
Service Oriented
System Engineering
2014
Defining multi-tenancy:
A systematic mapping
study on the academic
and the industrial
perspective
Kabbedijk, Jaap, Cor-Paul
Bezemer, Slinger Jansen, and
Andy Zaidman
Journal of Systems
and Software
2015
Resource management
for bursty streams on
multi-tenancy cloud
environments
Tolosana-Calasanz, Rafael,
José Ángel Bañares,
Congduc Pham, and Omer F.
Rana
Future Generation
Computer Systems
2016
Network function
virtualization:
Challenges and
opportunities for
innovations
Han, Bo, Vijay
Gopalakrishnan, Lusheng Ji,
and Seungjoon Lee
IEEE
Communications
Magazine
2015
1.3 Round 3
1.3.1 Search Keyword
Keyword Source/research database Number of results
Multi-tenancy, web services,
Virtualization, Security, Cloud
computing
Google Scholar 23,000
1.3.2 Result
Title Author Journal/conference Year
Security in cloud
computing:
Opportunities and
challenges
Ali, Mazhar, Samee U.
Khan, and Athanasios V.
Vasilakos
Information sciences 2015
Multi‐tenancy
authorization models for
collaborative cloud
services
Tang, Bo, Ravi Sandhu, and
Qi Li
Concurrency and
Computation:
Practice and
Experience
2015
Multi-tenancy in cloud
computing
AlJahdali, Hussain,
Abdulaziz Albatli, Peter
Garraghan, Paul Townend,
Lydia Lau, and Jie Xu
IEEE 8th
International
Symposium on
Service Oriented
System Engineering
2014
Defining multi-tenancy:
A systematic mapping
study on the academic
and the industrial
perspective
Kabbedijk, Jaap, Cor-Paul
Bezemer, Slinger Jansen, and
Andy Zaidman
Journal of Systems
and Software
2015
Resource management
for bursty streams on
multi-tenancy cloud
environments
Tolosana-Calasanz, Rafael,
José Ángel Bañares,
Congduc Pham, and Omer F.
Rana
Future Generation
Computer Systems
2016
Network function
virtualization:
Challenges and
opportunities for
innovations
Han, Bo, Vijay
Gopalakrishnan, Lusheng Ji,
and Seungjoon Lee
IEEE
Communications
Magazine
2015

11SECURITY IN MOBILE COMPUTING
ClickOS and the art of
network function
virtualization
Martins, Joao, Mohamed
Ahmed, Costin Raiciu,
Vladimir Olteanu, Michio
Honda, Roberto Bifulco, and
Felipe Huici
{USENIX}
Symposium on
Networked Systems
Design and
Implementation
({NSDI}
2014
Network virtualization
in multi-tenant
datacenters
Koponen, Teemu, Keith
Amidon, Peter Balland,
Martín Casado, Anupam
Chanda, Bryan Fulton, Igor
Ganichev et al.
{USENIX}
Symposium on
Networked Systems
Design and
Implementation
({NSDI}
2014
Hypervisors vs.
lightweight
virtualization: a
performance
comparison
Morabito, Roberto, Jimmy
Kjällman, and Miika Komu
International
Conference on Cloud
Engineering
2015
A survey of mobile
cloud computing
application models
Othman, Mazliza, Sajjad
Ahmad Madani, and Samee
Ullah Khan
IEEE
Communications
Surveys & Tutorials
2014
A hierarchical edge
cloud architecture for
mobile computing
Tong, Liang, Yong Li, and
Wei Gao
The 35th Annual
IEEE International
Conference on
Computer
Communications
2016
Dynamic energy-aware
cloudlet-based mobile
cloud computing model
for green computing
Gai, Keke, Meikang Qiu,
Hui Zhao, Lixin Tao, and
Ziliang Zong
Journal of Network
and Computer
Applications
2016
An experimental
analysis on cloud-based
mobile augmentation in
mobile cloud computing
Abolfazli, Saeid, Zohreh
Sanaei, Mojtaba Alizadeh,
Abdullah Gani, and Feng Xia
IEEE Transactions
on Consumer
Electronics
2014
Fog computing:
Focusing on mobile
users at the edge
Luan, Tom H., Longxiang
Gao, Zhi Li, Yang Xiang,
Guiyi Wei, and Limin Sun
arXiv preprint arXiv 2015
User profiling for
energy optimisation in
mobile cloud computing
Benkhelifa, Elhadj, Thomas
Welsh, Loai Tawalbeh,
Yaser Jararweh, and Anas
Basalamah
Procedia Computer
Science
2015
ClickOS and the art of
network function
virtualization
Martins, Joao, Mohamed
Ahmed, Costin Raiciu,
Vladimir Olteanu, Michio
Honda, Roberto Bifulco, and
Felipe Huici
{USENIX}
Symposium on
Networked Systems
Design and
Implementation
({NSDI}
2014
Network virtualization
in multi-tenant
datacenters
Koponen, Teemu, Keith
Amidon, Peter Balland,
Martín Casado, Anupam
Chanda, Bryan Fulton, Igor
Ganichev et al.
{USENIX}
Symposium on
Networked Systems
Design and
Implementation
({NSDI}
2014
Hypervisors vs.
lightweight
virtualization: a
performance
comparison
Morabito, Roberto, Jimmy
Kjällman, and Miika Komu
International
Conference on Cloud
Engineering
2015
A survey of mobile
cloud computing
application models
Othman, Mazliza, Sajjad
Ahmad Madani, and Samee
Ullah Khan
IEEE
Communications
Surveys & Tutorials
2014
A hierarchical edge
cloud architecture for
mobile computing
Tong, Liang, Yong Li, and
Wei Gao
The 35th Annual
IEEE International
Conference on
Computer
Communications
2016
Dynamic energy-aware
cloudlet-based mobile
cloud computing model
for green computing
Gai, Keke, Meikang Qiu,
Hui Zhao, Lixin Tao, and
Ziliang Zong
Journal of Network
and Computer
Applications
2016
An experimental
analysis on cloud-based
mobile augmentation in
mobile cloud computing
Abolfazli, Saeid, Zohreh
Sanaei, Mojtaba Alizadeh,
Abdullah Gani, and Feng Xia
IEEE Transactions
on Consumer
Electronics
2014
Fog computing:
Focusing on mobile
users at the edge
Luan, Tom H., Longxiang
Gao, Zhi Li, Yang Xiang,
Guiyi Wei, and Limin Sun
arXiv preprint arXiv 2015
User profiling for
energy optimisation in
mobile cloud computing
Benkhelifa, Elhadj, Thomas
Welsh, Loai Tawalbeh,
Yaser Jararweh, and Anas
Basalamah
Procedia Computer
Science
2015
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




