Digital Forensics Report: Investigating Mobile Communication and Data
VerifiedAdded on 2023/06/04
|12
|1876
|318
Report
AI Summary
This digital forensics report details an investigation into potential intellectual property theft, focusing on the analysis of mobile device data. The report outlines a scenario involving suspected individuals, Randall Simpson and Sarah Jensen, and their mobile communications. It describes the use of forensic tools, particularly Oxygen Forensics, to extract and analyze data from SIM cards and cloud backups. The report covers key aspects of the forensic process, including seizure, separation, and documentation of evidence. It explores the types of data that can be recovered, such as call logs, SMS messages, multimedia files, location data, application data, and internet history. The analysis includes a step-by-step approach to mobile device examination, emphasizing the importance of maintaining chain of custody and proper documentation. The report also discusses the significance of cloud backups and the various types of evidence that can be found on mobile devices, providing valuable insights into digital forensics investigations.

Digital Forensics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task – 1: Recovering the Scrambled Bits..............................................................................2
Task- 2: Digital Forensics Report...........................................................................................2
Introduction..........................................................................................................................2
Analysis.................................................................................................................................2
Conclusion.............................................................................................................................7
References.................................................................................................................................8
1
Task – 1: Recovering the Scrambled Bits..............................................................................2
Task- 2: Digital Forensics Report...........................................................................................2
Introduction..........................................................................................................................2
Analysis.................................................................................................................................2
Conclusion.............................................................................................................................7
References.................................................................................................................................8
1
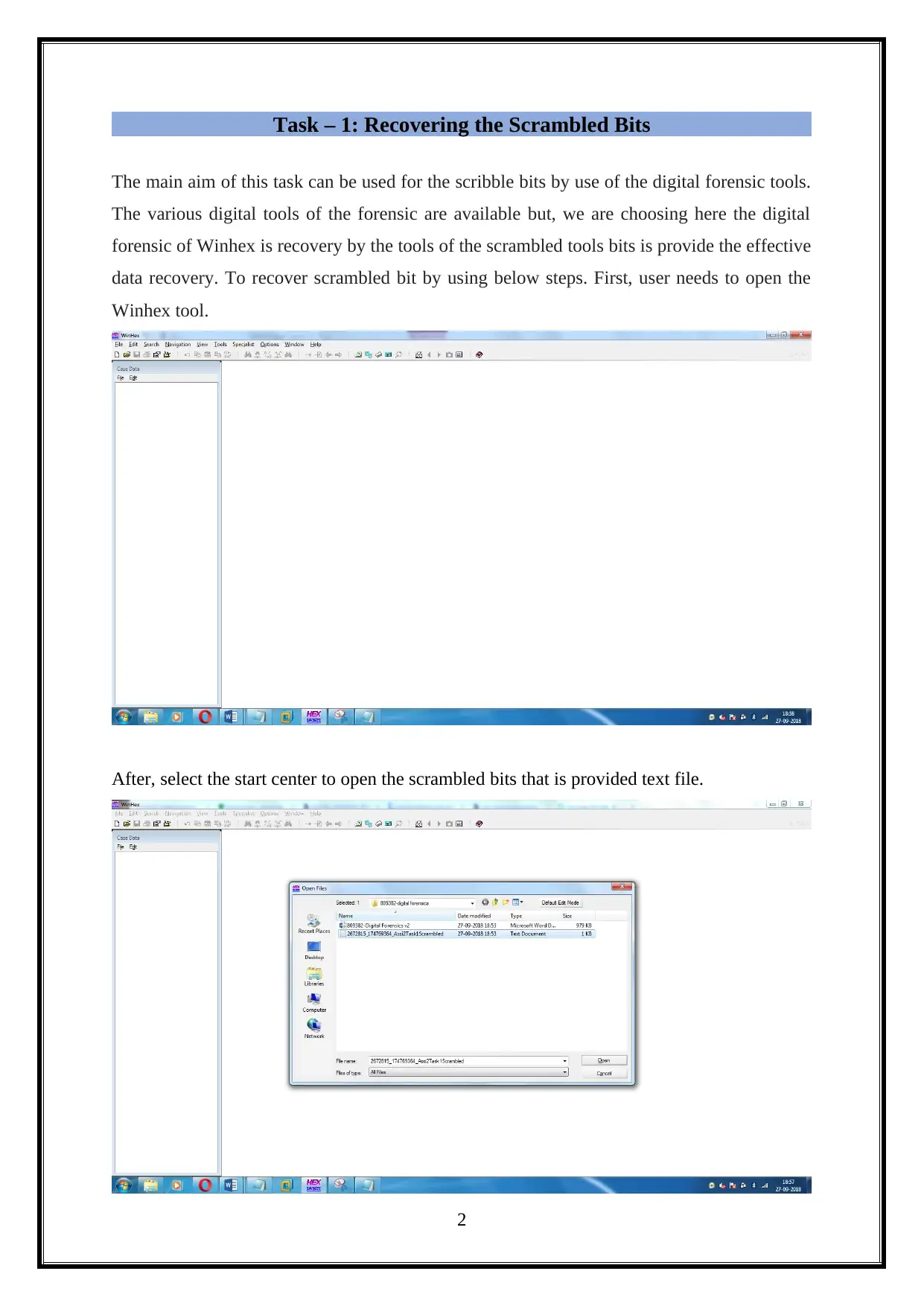
Task – 1: Recovering the Scrambled Bits
The main aim of this task can be used for the scribble bits by use of the digital forensic tools.
The various digital tools of the forensic are available but, we are choosing here the digital
forensic of Winhex is recovery by the tools of the scrambled tools bits is provide the effective
data recovery. To recover scrambled bit by using below steps. First, user needs to open the
Winhex tool.
After, select the start center to open the scrambled bits that is provided text file.
2
The main aim of this task can be used for the scribble bits by use of the digital forensic tools.
The various digital tools of the forensic are available but, we are choosing here the digital
forensic of Winhex is recovery by the tools of the scrambled tools bits is provide the effective
data recovery. To recover scrambled bit by using below steps. First, user needs to open the
Winhex tool.
After, select the start center to open the scrambled bits that is provided text file.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
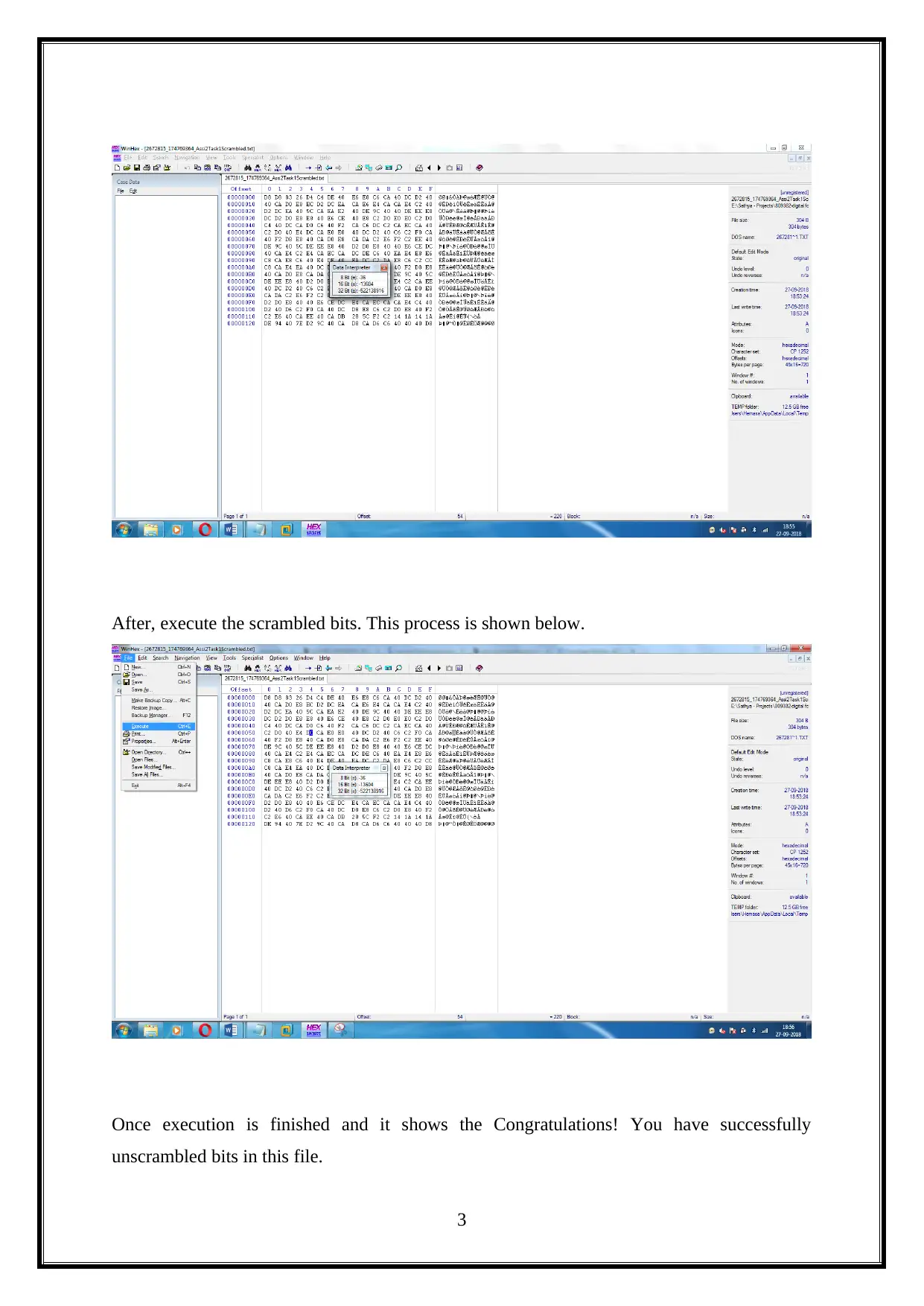
After, execute the scrambled bits. This process is shown below.
Once execution is finished and it shows the Congratulations! You have successfully
unscrambled bits in this file.
3
Once execution is finished and it shows the Congratulations! You have successfully
unscrambled bits in this file.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Task- 2: Digital Forensics Report
Introduction
This project aims to prepare the digital forensic report for provided case scenario. In
this case scenario needs to investigate SIM card data and also determine the text messages,
SMS massages, phone numbers and other data on Mobile phone. Randall Simpson, the CIO
of Flash bills, and Sarah Jensen, the lead developer at Desert Oasis Funding are suspected of
intellectual property theft. After, user needs to investigate this theft based on Randall
Simpson and Sarah Jensen mobile communication because two have been calling and e-
mailing each other. So, user needs to hired the Cellebrite mobile synchronization limited to
investigate the mobile But, these is no text messages, SMS, phones or other data. Finally, the
digital forensic investigator able to get a warrant for cloud backup of Randall’s and Sarah’s
mobile devices. This investigation using the oxygen forensics tool to analysis the mobile
device to provide the digital forensics report. The investigation of this case scenario will be
discussed in detail.
Analysis
This analysis is done by using the oxygen forensics tool. This tools ready to remove the
vital information like call logs, SMS, MMS, E-mail, Photos, Videos, sound documents, Geo
4
Introduction
This project aims to prepare the digital forensic report for provided case scenario. In
this case scenario needs to investigate SIM card data and also determine the text messages,
SMS massages, phone numbers and other data on Mobile phone. Randall Simpson, the CIO
of Flash bills, and Sarah Jensen, the lead developer at Desert Oasis Funding are suspected of
intellectual property theft. After, user needs to investigate this theft based on Randall
Simpson and Sarah Jensen mobile communication because two have been calling and e-
mailing each other. So, user needs to hired the Cellebrite mobile synchronization limited to
investigate the mobile But, these is no text messages, SMS, phones or other data. Finally, the
digital forensic investigator able to get a warrant for cloud backup of Randall’s and Sarah’s
mobile devices. This investigation using the oxygen forensics tool to analysis the mobile
device to provide the digital forensics report. The investigation of this case scenario will be
discussed in detail.
Analysis
This analysis is done by using the oxygen forensics tool. This tools ready to remove the
vital information like call logs, SMS, MMS, E-mail, Photos, Videos, sound documents, Geo
4

area and different application data from fake versatile by utilizing oxygen forensics tool. This
tool can secure information from unstable memory of the cell phones (Ali, Abd Razak,
Othman, Mohammed & Saeed, 2017). This analysis is partitioned into three sections,
Seizure
The seizure segment principally includes the legal significances. On the off
chance that you don't have a legal ideal to analyse the gadget or its substance then you
are probably going to have all the proof smothered regardless of how hard you have
functioned.
Separation
The disconnection part is the most vital in light of the fact that the mobile information
it can be changed, adjusted of the erased over the air (OTA). The transporter fit for the
doing this not of the exclusively of the data remotely can be utilized the application
'wipe' the information for the gadget.
Documentation
The reports of the procedure include the capturing the mobile of the season in
which seizure activity it should be the time settings of the photographs with the
demonstrate attributes and the condition of the gadget ("Forensics Analysis on Smart
Phones Using Mobile Forensics Tools", 2018).
After the Mobile is taken to the computerized forensics tool specialist, the gadget ought to be
analysed with an expert apparatus. Exploring Mobiles physically is a final resort. Manual
analysis should just be utilized if no device available can bolster the gadget. Present day
mobile phones resemble small scale PCs that require a refined programming programs for far
reaching analysis. While looking at while looking at a mobile or phone, shield form the
remote access of the vital system signals. The PDA is the United States and the majority it an
utilizing of jammers are illegal in the metallic work to the wrap of the safely and after that
setting the flight mode for the transportation is used for the mobile into the reserve mode.,
shooting, and afterward putting the Mobile in a state to be inspected Spreads out the
procedure stream as takes after.
Achieve and keep up arrange separation.
Thoroughly archive the gadget, noticing all data accessible. Utilize documentation
which help this photography.
If a SIM card is set up, expel, read, and picture the SIM card.
Clone the SIM card.
5
tool can secure information from unstable memory of the cell phones (Ali, Abd Razak,
Othman, Mohammed & Saeed, 2017). This analysis is partitioned into three sections,
Seizure
The seizure segment principally includes the legal significances. On the off
chance that you don't have a legal ideal to analyse the gadget or its substance then you
are probably going to have all the proof smothered regardless of how hard you have
functioned.
Separation
The disconnection part is the most vital in light of the fact that the mobile information
it can be changed, adjusted of the erased over the air (OTA). The transporter fit for the
doing this not of the exclusively of the data remotely can be utilized the application
'wipe' the information for the gadget.
Documentation
The reports of the procedure include the capturing the mobile of the season in
which seizure activity it should be the time settings of the photographs with the
demonstrate attributes and the condition of the gadget ("Forensics Analysis on Smart
Phones Using Mobile Forensics Tools", 2018).
After the Mobile is taken to the computerized forensics tool specialist, the gadget ought to be
analysed with an expert apparatus. Exploring Mobiles physically is a final resort. Manual
analysis should just be utilized if no device available can bolster the gadget. Present day
mobile phones resemble small scale PCs that require a refined programming programs for far
reaching analysis. While looking at while looking at a mobile or phone, shield form the
remote access of the vital system signals. The PDA is the United States and the majority it an
utilizing of jammers are illegal in the metallic work to the wrap of the safely and after that
setting the flight mode for the transportation is used for the mobile into the reserve mode.,
shooting, and afterward putting the Mobile in a state to be inspected Spreads out the
procedure stream as takes after.
Achieve and keep up arrange separation.
Thoroughly archive the gadget, noticing all data accessible. Utilize documentation
which help this photography.
If a SIM card is set up, expel, read, and picture the SIM card.
Clone the SIM card.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

With the cloned SIM card introduced, complete an intelligent extraction of the cell
gadget with an apparatus. On the off chance that examining a non-SIM gadget, begin
here.
Examine the removed information from the sensible analysis.
If upheld by both the model and the device, complete a physical extraction of the
cell gadget.
View parsed information from physical extraction, which will differ significantly
relying upon the make model of the mobile phone and the apparatus being utilized.
Carve crude picture for different record composes or strings of information.
Basically, the mobile phone contain a myriad of potential sources which is used for
evidence for an investigation ("Mobile device forensics: A snapshot", 2018). These are,
Backup and cloud data
Multimedia Files
Location data
Application and communication data
Malware
Internet History and Email.
This case scenario, we have the SIM card details and Mobile backup. These are shown in
below.
6
gadget with an apparatus. On the off chance that examining a non-SIM gadget, begin
here.
Examine the removed information from the sensible analysis.
If upheld by both the model and the device, complete a physical extraction of the
cell gadget.
View parsed information from physical extraction, which will differ significantly
relying upon the make model of the mobile phone and the apparatus being utilized.
Carve crude picture for different record composes or strings of information.
Basically, the mobile phone contain a myriad of potential sources which is used for
evidence for an investigation ("Mobile device forensics: A snapshot", 2018). These are,
Backup and cloud data
Multimedia Files
Location data
Application and communication data
Malware
Internet History and Email.
This case scenario, we have the SIM card details and Mobile backup. These are shown in
below.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
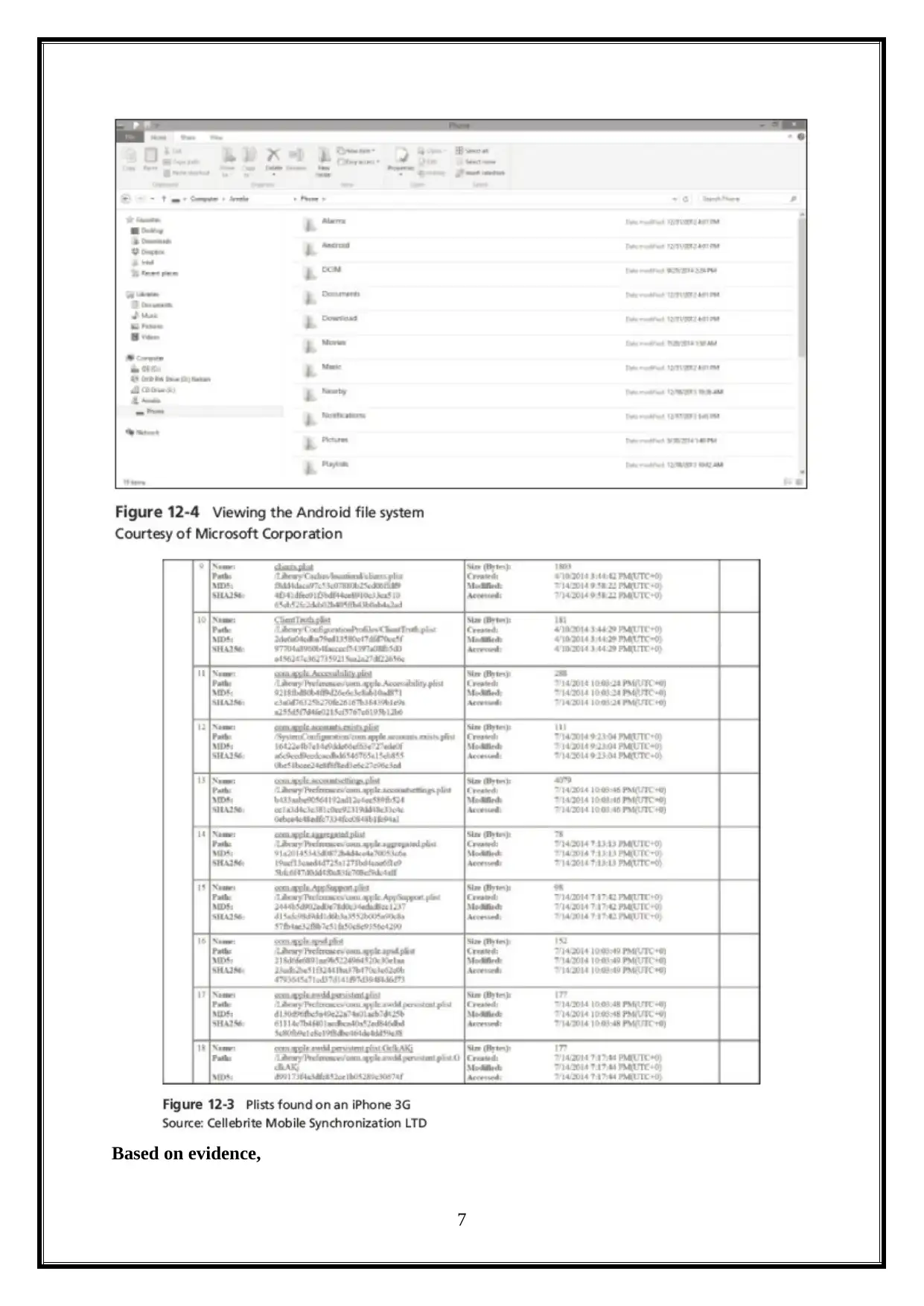
Based on evidence,
7
7

It contains the following information ("Mobile Devices, Data Collection and the Next
E-Discovery Front", 2018). These are,
Backup and cloud information
Due to the versatile idea of cell phones, the danger of information misfortune
increments as the physical gadget might be stolen, disappear or glitch. Numerous people
decide to either reinforcement their gadget locally (to a PC) or to back up their gadget to a
cloud administration to decrease this hazard. These reinforcement destinations can have an
abundance of data as various memorable reinforcements can be put away and in this manner
got to utilizing criminological systems.
Multimedia records
Large storing limits in cell phones can result in a great many pictures, recordings,
music documents and other media being put away. Such documents can be utilized as proof
in an examination as an inspector can follow their cause and recognize in the event that it was
gotten from an outside substance or downloaded from the web. With current cell phones, area
based information is frequently installed inside media documents, unbeknown to the client.
By using proper legal strategies, this data can be gotten to and displayed ("Mobile Phone
Investigations: Best Practices", 2018).
Location information
Various area following innovations executed in cell phones can give profitable data in
an examination. At the point when a man is voyaging, for instance, their cell phone could be
interfacing with wandering systems, Wi-Fi hotspots, cell site towers, and so on. Every one of
these activities leave an "impression" of areas that a man has visited. Such data is
exceptionally profitable to an examination when attempting to put a person at a specific area
where an episode is known to have occurred. It is likewise conceivable to track when and for
to what extent the cell phone was set on charge in a given area ("Oxygen Forensic®
Detective Getting Started Guide", 2018).
Application and correspondence information
Communication information comprises of information, for example, contacts, call
logs, messages, talk information, messages and online networking accounts. Application
information alludes to the data put away inside outsider applications on the cell phone. This
data can in addition to other things, help build up correspondences between an individual and
outer elements. It can likewise recognize a person's relatives, companions, associates and
adversaries. The information can be utilized to build up a system of a man's "nearby
8
E-Discovery Front", 2018). These are,
Backup and cloud information
Due to the versatile idea of cell phones, the danger of information misfortune
increments as the physical gadget might be stolen, disappear or glitch. Numerous people
decide to either reinforcement their gadget locally (to a PC) or to back up their gadget to a
cloud administration to decrease this hazard. These reinforcement destinations can have an
abundance of data as various memorable reinforcements can be put away and in this manner
got to utilizing criminological systems.
Multimedia records
Large storing limits in cell phones can result in a great many pictures, recordings,
music documents and other media being put away. Such documents can be utilized as proof
in an examination as an inspector can follow their cause and recognize in the event that it was
gotten from an outside substance or downloaded from the web. With current cell phones, area
based information is frequently installed inside media documents, unbeknown to the client.
By using proper legal strategies, this data can be gotten to and displayed ("Mobile Phone
Investigations: Best Practices", 2018).
Location information
Various area following innovations executed in cell phones can give profitable data in
an examination. At the point when a man is voyaging, for instance, their cell phone could be
interfacing with wandering systems, Wi-Fi hotspots, cell site towers, and so on. Every one of
these activities leave an "impression" of areas that a man has visited. Such data is
exceptionally profitable to an examination when attempting to put a person at a specific area
where an episode is known to have occurred. It is likewise conceivable to track when and for
to what extent the cell phone was set on charge in a given area ("Oxygen Forensic®
Detective Getting Started Guide", 2018).
Application and correspondence information
Communication information comprises of information, for example, contacts, call
logs, messages, talk information, messages and online networking accounts. Application
information alludes to the data put away inside outsider applications on the cell phone. This
data can in addition to other things, help build up correspondences between an individual and
outer elements. It can likewise recognize a person's relatives, companions, associates and
adversaries. The information can be utilized to build up a system of a man's "nearby
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

partners," which can help with specific kinds of examinations, for example, tricks or cartel
action where in excess of one individual is included.
Malware
Like PC frameworks, cell phones are additionally defenceless against malware. Legal
apparatuses can identify malware on cell phones. Facilitate investigation can help reveal what
impact the malware has on the cell phone and to comprehend if touchy data was stolen from
the gadget or if an outsider was checking interchanges.
Internet history and email
Internet capacity on modem day cell phones can equal that of numerous PCs. A
further developed cell phone will furthermore store a web history, web reserve, web
bookmarks and email. Email, web program history and bookmarks can give awesome legal
knowledge, and cell phones give another wellspring of this information ("Your Mobile
Device – The Best Piece of Evidence in an Investigation", 2018).
Conclusion
This paper concentrated on the reproducing the past events in useful utilizing legal
forensics tool. The information can be recovered from the gadget, and support documents on
PCs and furthermore the sent and got messages from the two people and gatherings, shifting
message composes and connections, message, and gadget states, e.g., disconnected, on the
web, blocked, evacuated, erased which are helpful for the criminal analysis. This information
was then broke down by an analyst amid the measurable analysis.
9
action where in excess of one individual is included.
Malware
Like PC frameworks, cell phones are additionally defenceless against malware. Legal
apparatuses can identify malware on cell phones. Facilitate investigation can help reveal what
impact the malware has on the cell phone and to comprehend if touchy data was stolen from
the gadget or if an outsider was checking interchanges.
Internet history and email
Internet capacity on modem day cell phones can equal that of numerous PCs. A
further developed cell phone will furthermore store a web history, web reserve, web
bookmarks and email. Email, web program history and bookmarks can give awesome legal
knowledge, and cell phones give another wellspring of this information ("Your Mobile
Device – The Best Piece of Evidence in an Investigation", 2018).
Conclusion
This paper concentrated on the reproducing the past events in useful utilizing legal
forensics tool. The information can be recovered from the gadget, and support documents on
PCs and furthermore the sent and got messages from the two people and gatherings, shifting
message composes and connections, message, and gadget states, e.g., disconnected, on the
web, blocked, evacuated, erased which are helpful for the criminal analysis. This information
was then broke down by an analyst amid the measurable analysis.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Ali, A., Abd Razak, S., Othman, S., Mohammed, A., & Saeed, F. (2017). A metamodel for
mobile forensics investigation domain. PLOS ONE, 12(4), e0176223. doi:
10.1371/journal.pone.0176223
Forensics Analysis On Smart Phones Using Mobile Forensics Tools. (2018). Retrieved from
https://www.ripublication.com/ijcir17/ijcirv13n8_03.pdf
Mobile device forensics: A snapshot. (2018). Retrieved from
https://aic.gov.au/publications/tandi/tandi460
Mobile Devices, Data Collection and the Next E-Discovery Front. (2018). Retrieved from
https://www.ftitechnology.com/resources/white-papers/mobile-devices-data-collection-
and-the-next-e-discovery-front
Mobile Phone Investigations: Best Practices. (2018). Retrieved from
https://www.forensicmag.com/article/2011/03/mobile-phone-investigations-best-
practices
10
Ali, A., Abd Razak, S., Othman, S., Mohammed, A., & Saeed, F. (2017). A metamodel for
mobile forensics investigation domain. PLOS ONE, 12(4), e0176223. doi:
10.1371/journal.pone.0176223
Forensics Analysis On Smart Phones Using Mobile Forensics Tools. (2018). Retrieved from
https://www.ripublication.com/ijcir17/ijcirv13n8_03.pdf
Mobile device forensics: A snapshot. (2018). Retrieved from
https://aic.gov.au/publications/tandi/tandi460
Mobile Devices, Data Collection and the Next E-Discovery Front. (2018). Retrieved from
https://www.ftitechnology.com/resources/white-papers/mobile-devices-data-collection-
and-the-next-e-discovery-front
Mobile Phone Investigations: Best Practices. (2018). Retrieved from
https://www.forensicmag.com/article/2011/03/mobile-phone-investigations-best-
practices
10

Oxygen Forensic® Detective Getting Started Guide. (2018). Retrieved from
https://www.oxygen-forensic.com/en/uploads/doc_guide/Oxygen_Forensic_Detective_G
etting_started2.pdf
Your Mobile Device – The Best Piece of Evidence in an Investigation. (2018). Retrieved
from https://www.alvarezandmarsal.com/insights/your-mobile-device-best-piece-
evidence-investigation
11
https://www.oxygen-forensic.com/en/uploads/doc_guide/Oxygen_Forensic_Detective_G
etting_started2.pdf
Your Mobile Device – The Best Piece of Evidence in an Investigation. (2018). Retrieved
from https://www.alvarezandmarsal.com/insights/your-mobile-device-best-piece-
evidence-investigation
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




