An Analysis Report: Mobile Device Insecurities and Vulnerabilities
VerifiedAdded on 2021/04/21
|13
|854
|176
Report
AI Summary
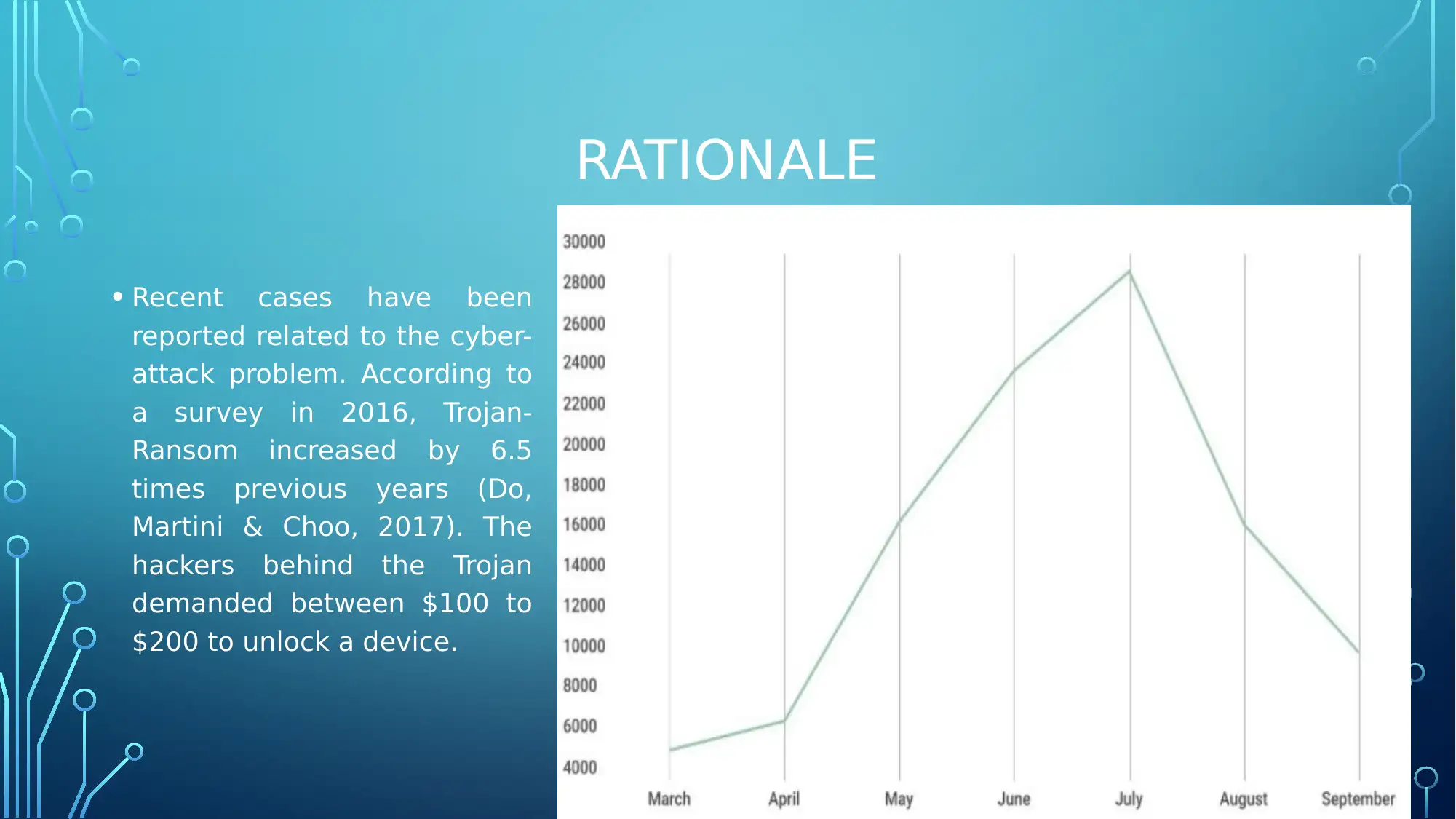
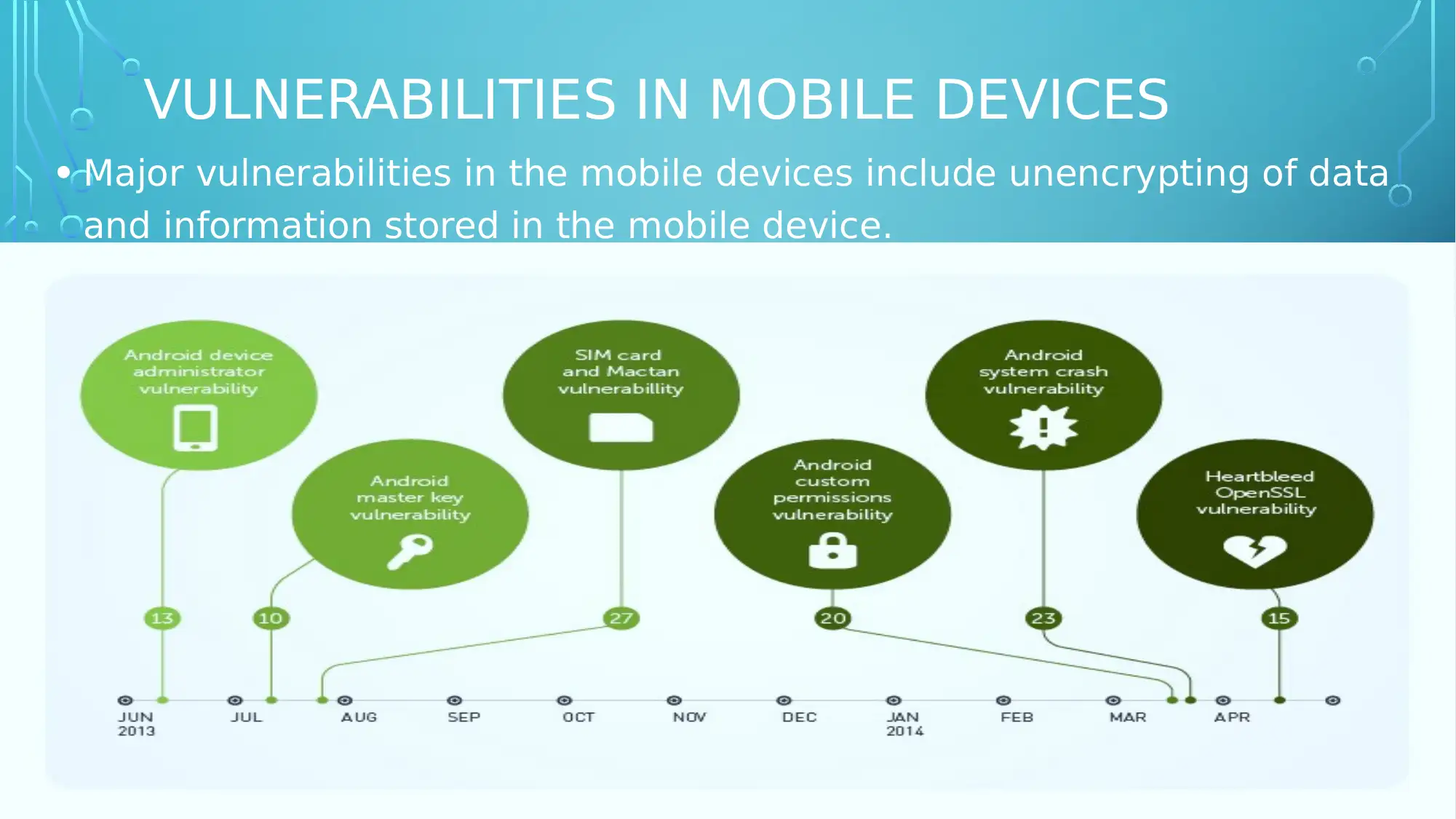
This report delves into the critical topic of mobile device security, investigating the insecurities and vulnerabilities inherent in modern mobile devices. It begins by establishing the significance of mobile phones in both organizational and personal contexts, highlighting the rise in cyber-attacks and the financial implications of data breaches. The report aims to identify and analyze the various insecurities and vulnerabilities present in mobile devices, including data unencryption. It then explores the impact of these vulnerabilities on mobile users, considering potential risks to data privacy and security. The research employs a secondary data collection approach, drawing from online journals, books, and government databases, with thematic analysis used to interpret the collected information. The expected outcomes of this research include a better understanding of mobile device threats and the development of effective strategies to mitigate these risks, ultimately contributing to enhanced mobile security practices.
1 out of 13
















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)