Mobile Device Investigation: Extraction Methods Report for CO4516
VerifiedAdded on 2022/08/29
|15
|2750
|18
Report
AI Summary
This report provides an in-depth analysis of mobile device extraction methods, focusing on logical, file system, and physical extraction techniques facilitated by Cellebrite UFED4PC and Cellebrite Physical Analyzer software. It evaluates the characteristics, strengths, and weaknesses of each method, along with the range of data that can be recovered. The report examines logical extraction, often utilizing APIs, which offers ease of use but may have limitations in data access. Physical extraction, involving a bit-by-bit copy of the device's memory, is explored for its ability to bypass lock screens and recover deleted data, despite potential drawbacks like slower speed and lack of end-to-end encryption. File system extraction, providing direct access to internal memory, is also assessed for its ability to retrieve various file types, including databases and logs. The report also addresses the role of proportionality in selecting the appropriate extraction method and outlines a process model for the forensic investigation of mobile devices, considering the importance of evidence acquisition, analysis, and reporting. The report concludes with an emphasis on the need for tested, validated, and documented methods to ensure the reliability and reproducibility of findings in mobile forensics.

CO4516 Mobile Device Investigation
[Type the author name]
[Pick the date]
[Type the author name]
[Pick the date]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction.................................................................................................................................................3
Logical, File System as well as Physical extraction methods afforded by the Cellebrite UFED4PC and
Cellebrite Physical Analyzer software..........................................................................................................3
Logical extraction.....................................................................................................................................4
Strength...............................................................................................................................................5
Weakness............................................................................................................................................5
Physical Extraction...................................................................................................................................5
Strength...............................................................................................................................................5
Weakness............................................................................................................................................5
File System Extraction..............................................................................................................................6
Strength...............................................................................................................................................6
Weakness............................................................................................................................................6
The role that proportionality plays in selecting the evidence extraction method for mobile devices.........6
Process Model for the Forensic Investigation of Mobile Devices................................................................8
Conclusion.................................................................................................................................................10
References.................................................................................................................................................12
Appendix...................................................................................................................................................13
Introduction.................................................................................................................................................3
Logical, File System as well as Physical extraction methods afforded by the Cellebrite UFED4PC and
Cellebrite Physical Analyzer software..........................................................................................................3
Logical extraction.....................................................................................................................................4
Strength...............................................................................................................................................5
Weakness............................................................................................................................................5
Physical Extraction...................................................................................................................................5
Strength...............................................................................................................................................5
Weakness............................................................................................................................................5
File System Extraction..............................................................................................................................6
Strength...............................................................................................................................................6
Weakness............................................................................................................................................6
The role that proportionality plays in selecting the evidence extraction method for mobile devices.........6
Process Model for the Forensic Investigation of Mobile Devices................................................................8
Conclusion.................................................................................................................................................10
References.................................................................................................................................................12
Appendix...................................................................................................................................................13

Introduction
Mobile forensics is a necessary field in today's society. Over the years the technology has
improved as well as expanded the function of a mobile phone to the likes of carrying a small
computer around in your pocket. A handheld device of the 80s, as well as today's mini-
computers, still use radio signals to communicate with towers that provide a signal over a wide
area (network). There are two dominant networks in use today among other smaller common
networks. Each network follows its own distinct set of rules (protocols) as well as are
incompatible with each other
Logical, File System as well as Physical extraction methods afforded by
the Cellebrite UFED4PC and Cellebrite Physical Analyzer software
The UFED Ultimate provides market-leading digital device access as well as outstanding
capabilities to extract as well as decode all ounce data. Not only does it thoroughly investigate
logical file systems as well as physically extracted data, but it does it thoroughly, discovers
important evidence, as well as easily shares findings with the entire research team. With UFED
Ultimate, you can expose hidden evidence on popular social media sites as well as provide more
evidence as well as deeper insight. Continuous software updates, as well as support across a
variety of hardware platforms, enable teams to use the most advanced digital forensic checking
capabilities when as well as where they need it (Andrei and Calder, 2018).
There are two distinct techniques for information extraction for cell phones: coherent just as
physical. (The third extraction type, File System Extraction, is ordered into the Logical heading.)
If upheld by the gadget, you can utilize various information types from every extraction class, as
appeared in the accompanying outline. Much of the time, a cell phone is associated with a UFED
gadget through a USB link association that speaks with the telephone to separate information. A
USB association gives a demonstrated, solid channel for duplicating information from a proof
gadget to a criminological picture. Contingent upon the OS of the cell phone you are keen on, the
intelligent extraction may utilize the USB/Bluetooth convention API rather, or the sequential
convention on more seasoned gadgets. The administrator must record the association type
utilized for every extraction. In uncommon cases, if the extraction comes up short, the client
must begin the extraction once more. The disappointment just influences the sending of
Mobile forensics is a necessary field in today's society. Over the years the technology has
improved as well as expanded the function of a mobile phone to the likes of carrying a small
computer around in your pocket. A handheld device of the 80s, as well as today's mini-
computers, still use radio signals to communicate with towers that provide a signal over a wide
area (network). There are two dominant networks in use today among other smaller common
networks. Each network follows its own distinct set of rules (protocols) as well as are
incompatible with each other
Logical, File System as well as Physical extraction methods afforded by
the Cellebrite UFED4PC and Cellebrite Physical Analyzer software
The UFED Ultimate provides market-leading digital device access as well as outstanding
capabilities to extract as well as decode all ounce data. Not only does it thoroughly investigate
logical file systems as well as physically extracted data, but it does it thoroughly, discovers
important evidence, as well as easily shares findings with the entire research team. With UFED
Ultimate, you can expose hidden evidence on popular social media sites as well as provide more
evidence as well as deeper insight. Continuous software updates, as well as support across a
variety of hardware platforms, enable teams to use the most advanced digital forensic checking
capabilities when as well as where they need it (Andrei and Calder, 2018).
There are two distinct techniques for information extraction for cell phones: coherent just as
physical. (The third extraction type, File System Extraction, is ordered into the Logical heading.)
If upheld by the gadget, you can utilize various information types from every extraction class, as
appeared in the accompanying outline. Much of the time, a cell phone is associated with a UFED
gadget through a USB link association that speaks with the telephone to separate information. A
USB association gives a demonstrated, solid channel for duplicating information from a proof
gadget to a criminological picture. Contingent upon the OS of the cell phone you are keen on, the
intelligent extraction may utilize the USB/Bluetooth convention API rather, or the sequential
convention on more seasoned gadgets. The administrator must record the association type
utilized for every extraction. In uncommon cases, if the extraction comes up short, the client
must begin the extraction once more. The disappointment just influences the sending of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
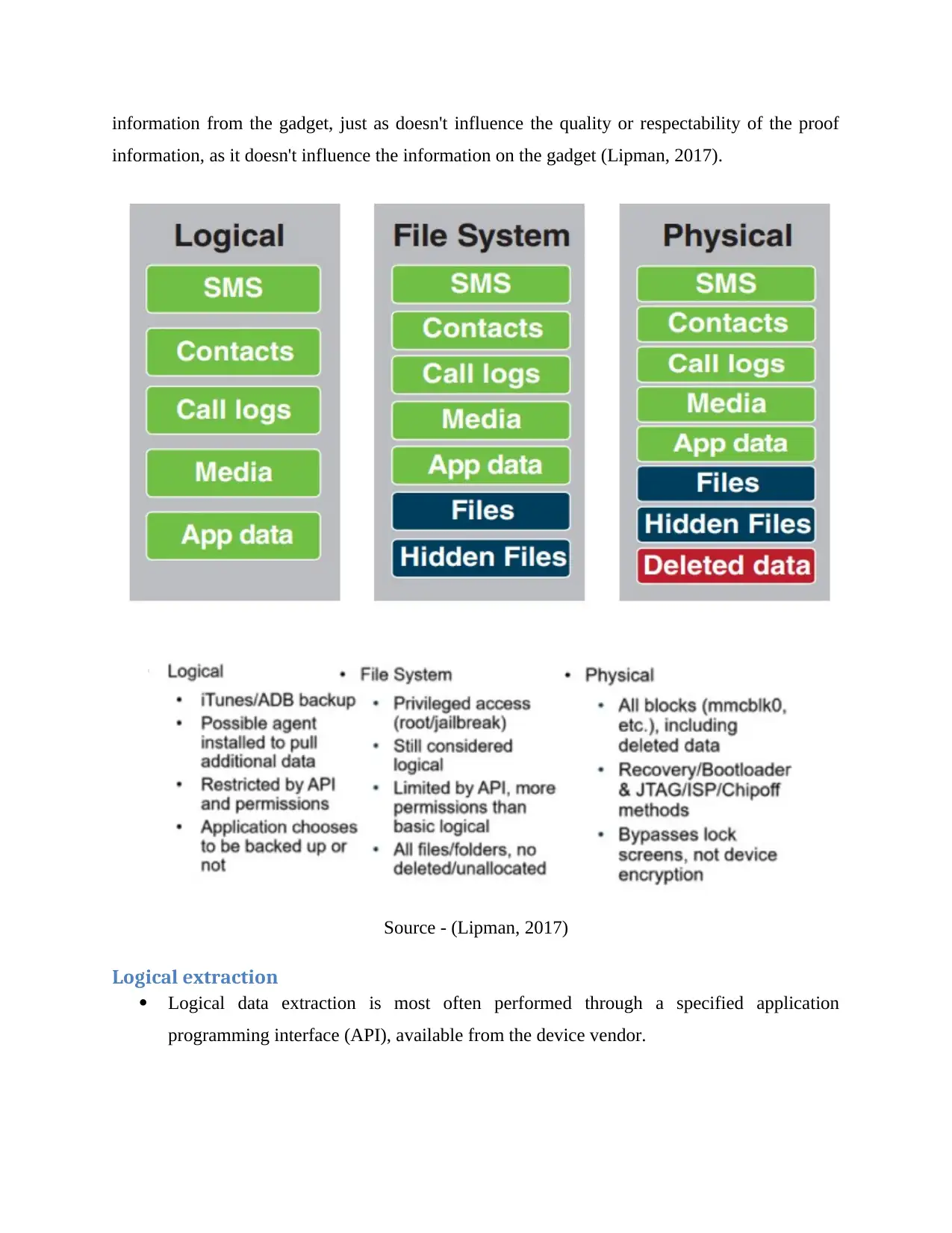
information from the gadget, just as doesn't influence the quality or respectability of the proof
information, as it doesn't influence the information on the gadget (Lipman, 2017).
Source - (Lipman, 2017)
Logical extraction
Logical data extraction is most often performed through a specified application
programming interface (API), available from the device vendor.
information, as it doesn't influence the information on the gadget (Lipman, 2017).
Source - (Lipman, 2017)
Logical extraction
Logical data extraction is most often performed through a specified application
programming interface (API), available from the device vendor.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Enables legal as well as sound data extraction, as well as APIs, enable communication
between commercial third-party apps as well as device operating systems (OSs).
When connected, UFED loads the associated vendor API into the device.
UFED then makes a read-only API call to request data from the phone (Supporting new
extraction methods and devices - Cellebrite, 2020).
Strength
Easily able to back the iTunes as well as ADP
Additional data can be pulled by the possible agents
Weakness
Not able to choose whether the backup is required or not
Does not have a functionality of Privileged access
Physical Extraction
Enable debugging. This was done manually as needed.
Turn off the phone as well as connect to the UFED hardware through a USB connection.
Connect UFED to a USB port on a computer or laptop running Cellebrite Physical
Analyzer software.
Follow the prompts provided by UFED to start the extraction process through software
running on the computer.
Physical extraction performs a bit-by-bit copy of the entire flash memory content of the
mobile device. This extract collects all live data as well as deleted or hidden data
(Supporting new extraction methods and devices - Cellebrite, 2020).
Strength
It bypasses the lock screen
Recovery of data is possible
Weakness
It does not do end to end encryption
The recovery process is very slow
between commercial third-party apps as well as device operating systems (OSs).
When connected, UFED loads the associated vendor API into the device.
UFED then makes a read-only API call to request data from the phone (Supporting new
extraction methods and devices - Cellebrite, 2020).
Strength
Easily able to back the iTunes as well as ADP
Additional data can be pulled by the possible agents
Weakness
Not able to choose whether the backup is required or not
Does not have a functionality of Privileged access
Physical Extraction
Enable debugging. This was done manually as needed.
Turn off the phone as well as connect to the UFED hardware through a USB connection.
Connect UFED to a USB port on a computer or laptop running Cellebrite Physical
Analyzer software.
Follow the prompts provided by UFED to start the extraction process through software
running on the computer.
Physical extraction performs a bit-by-bit copy of the entire flash memory content of the
mobile device. This extract collects all live data as well as deleted or hidden data
(Supporting new extraction methods and devices - Cellebrite, 2020).
Strength
It bypasses the lock screen
Recovery of data is possible
Weakness
It does not do end to end encryption
The recovery process is very slow

File System Extraction
The main difference between logical extraction as well as file system extraction is that
the forensic tool does not have to communicate through the API for each type of data, as
well as can access files directly in the mobile device's internal memory.
This direct access allows the forensic tool to extract all files that exist in internal memory,
such as database files, system files, as well as logs.
File system extraction can help you determine file structure, web browsing history, as
well as mobile device app usage history (Supporting new extraction methods and devices
- Cellebrite, 2020).
Strength
The functionality of privileged access
It includes the backup of all the files as well as folders
Weakness
API functionality is very limited
Less functionality then physical model
You can potentially restore deleted data by creating a per-bit copy. This means data outside the
active user data, or database files such as images, videos, installed applications, location
information, as well as email. Also, you can extract them as well as restore deleted versions of
items (Pavych and Pavych, 2019).
Driven by continuous advances in mobile technology, more people are using mobile devices as
their primary work tools. The need for BYOD policies or the need to collect these devices for
eDiscovery as well as compliance is increasing. By understanding the key differences in how
mobile devices are extracted, your team is ready for mobile discovery nuances (Pavych and
Pavych, 2019).
The role that proportionality plays in selecting the evidence extraction
method for mobile devices
Proof extraction just as criminological testing for every cell phone can be extraordinary.
Nonetheless, after a predictable assessment procedure can help guarantee that the proof removed
from each telephone by the measurable overseer is all around reported just as that the outcomes
The main difference between logical extraction as well as file system extraction is that
the forensic tool does not have to communicate through the API for each type of data, as
well as can access files directly in the mobile device's internal memory.
This direct access allows the forensic tool to extract all files that exist in internal memory,
such as database files, system files, as well as logs.
File system extraction can help you determine file structure, web browsing history, as
well as mobile device app usage history (Supporting new extraction methods and devices
- Cellebrite, 2020).
Strength
The functionality of privileged access
It includes the backup of all the files as well as folders
Weakness
API functionality is very limited
Less functionality then physical model
You can potentially restore deleted data by creating a per-bit copy. This means data outside the
active user data, or database files such as images, videos, installed applications, location
information, as well as email. Also, you can extract them as well as restore deleted versions of
items (Pavych and Pavych, 2019).
Driven by continuous advances in mobile technology, more people are using mobile devices as
their primary work tools. The need for BYOD policies or the need to collect these devices for
eDiscovery as well as compliance is increasing. By understanding the key differences in how
mobile devices are extracted, your team is ready for mobile discovery nuances (Pavych and
Pavych, 2019).
The role that proportionality plays in selecting the evidence extraction
method for mobile devices
Proof extraction just as criminological testing for every cell phone can be extraordinary.
Nonetheless, after a predictable assessment procedure can help guarantee that the proof removed
from each telephone by the measurable overseer is all around reported just as that the outcomes
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

are reproducible just as solid. There is no settled standard procedure for portable legal. Be that as
it may, the accompanying graph plots the procedure contemplations for removing proof from cell
phones. All techniques used to remove information from cell phones must be tried, approved,
just as recorded (Gabdrakhmanova, Izmaylova, Larin and Kuleshova, 2019).
Source - (Gabdrakhmanova, Izmaylova, Larin and Kuleshova, 2019)
The proof obtaining stage is the commencement stage, which incorporates a solicitation structure
just as possession data, a record to report the sort of episode engaged with the cell phone, just as
a review of the kind of information or data the requester needs. Defining explicit objectives for
every test is a significant piece of this stage (Palkowski, 2015).
Cell phones are intended to impart through PDA systems, Bluetooth, infrared just as remote (Wi-
Fi) organizing. At the point when the telephone is associated with the system, new information is
added to the telephone through approaching calls, messages, just as application information, just
as the proof of the telephone is changed. You can likewise utilize the remote access or wipe
order to obliterate information. Hence, it is imperative to isolate the gadget from the
it may, the accompanying graph plots the procedure contemplations for removing proof from cell
phones. All techniques used to remove information from cell phones must be tried, approved,
just as recorded (Gabdrakhmanova, Izmaylova, Larin and Kuleshova, 2019).
Source - (Gabdrakhmanova, Izmaylova, Larin and Kuleshova, 2019)
The proof obtaining stage is the commencement stage, which incorporates a solicitation structure
just as possession data, a record to report the sort of episode engaged with the cell phone, just as
a review of the kind of information or data the requester needs. Defining explicit objectives for
every test is a significant piece of this stage (Palkowski, 2015).
Cell phones are intended to impart through PDA systems, Bluetooth, infrared just as remote (Wi-
Fi) organizing. At the point when the telephone is associated with the system, new information is
added to the telephone through approaching calls, messages, just as application information, just
as the proof of the telephone is changed. You can likewise utilize the remote access or wipe
order to obliterate information. Hence, it is imperative to isolate the gadget from the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

correspondence source before it is recovered just as reviewed. Telephone disconnection should
be possible either to the telephone or by utilizing a Faraday investigation that closes down radio
signs from the telephone. Accordingly, organize detachment is prescribed. This should be
possible by putting the telephone on the radio recurrence shield fabric just as setting the
telephone in-plane or flight mode. At the point when the telephone is isolated from the
correspondence organize, the real preparation of the cell phone starts. The telephone ought to be
acquired utilizing a tried strategy that is repeatable just as that seems like legal at whatever point
conceivable. The physical catch is the prescribed strategy since it separates crude memory
information just as the gadget normally kills power during the catch procedure. For most
gadgets, changes that happen to the gadget during a physical recovery are negligible. On the off
chance that physical recovery is absurd or fizzles, attempt to get the cell phone's document
framework. Coherent recoveries contain just parsed information just as may give pointers to
looking at crude memory pictures, so they ought to consistently be recovered (Zhu and Li, 2014).
You should hash all picture documents after recovery to guarantee that the information isn't
changed. If record framework extraction is bolstered, the examiner removes the document
framework just as figures the hash of the extricated record. At that point, the document hash is
registered independently, just as it is checked against the first incentive to confirm its
respectability. The hash esteem confound must be elucidating (for instance, on the off chance
that the gadget is fueled on just as at that point recovered once more, the hash esteem is
extraordinary). Criminological agents must report the whole screening process as a simultaneous
notice of what was finished during the catch just as a survey. When the inspector has finished the
study, the outcomes must pass some friend audits to guarantee that the information is being
checked just as that the study is finished (Borodin, 2013).
Process Model for the Forensic Investigation of Mobile Devices
Another procedure model has been proposed to assess the security occurrence on the PC. To
improve the general research process, this model consolidates two ideas: episode reaction just as
PC criminological. The focal point of this model is fundamentally examination. In this way, the
means incorporate pre-episode readiness, pre-investigation, pre-examination, just as post-
investigation. All means just as exercises performed before the real examination starts are
remembered for the pre-examination organize, yet the post-examination arrange archives the
be possible either to the telephone or by utilizing a Faraday investigation that closes down radio
signs from the telephone. Accordingly, organize detachment is prescribed. This should be
possible by putting the telephone on the radio recurrence shield fabric just as setting the
telephone in-plane or flight mode. At the point when the telephone is isolated from the
correspondence organize, the real preparation of the cell phone starts. The telephone ought to be
acquired utilizing a tried strategy that is repeatable just as that seems like legal at whatever point
conceivable. The physical catch is the prescribed strategy since it separates crude memory
information just as the gadget normally kills power during the catch procedure. For most
gadgets, changes that happen to the gadget during a physical recovery are negligible. On the off
chance that physical recovery is absurd or fizzles, attempt to get the cell phone's document
framework. Coherent recoveries contain just parsed information just as may give pointers to
looking at crude memory pictures, so they ought to consistently be recovered (Zhu and Li, 2014).
You should hash all picture documents after recovery to guarantee that the information isn't
changed. If record framework extraction is bolstered, the examiner removes the document
framework just as figures the hash of the extricated record. At that point, the document hash is
registered independently, just as it is checked against the first incentive to confirm its
respectability. The hash esteem confound must be elucidating (for instance, on the off chance
that the gadget is fueled on just as at that point recovered once more, the hash esteem is
extraordinary). Criminological agents must report the whole screening process as a simultaneous
notice of what was finished during the catch just as a survey. When the inspector has finished the
study, the outcomes must pass some friend audits to guarantee that the information is being
checked just as that the study is finished (Borodin, 2013).
Process Model for the Forensic Investigation of Mobile Devices
Another procedure model has been proposed to assess the security occurrence on the PC. To
improve the general research process, this model consolidates two ideas: episode reaction just as
PC criminological. The focal point of this model is fundamentally examination. In this way, the
means incorporate pre-episode readiness, pre-investigation, pre-examination, just as post-
investigation. All means just as exercises performed before the real examination starts are
remembered for the pre-examination organize, yet the post-examination arrange archives the
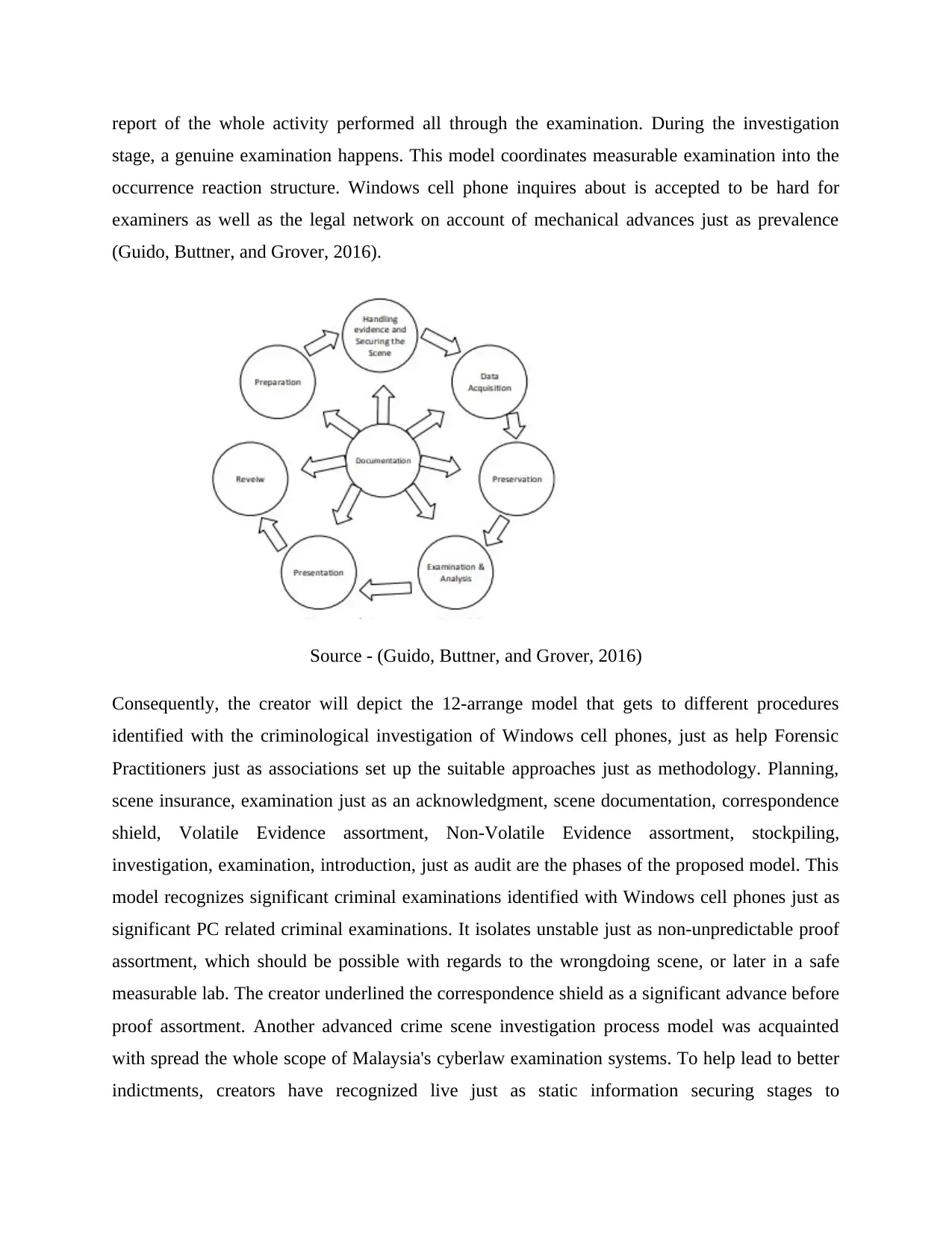
report of the whole activity performed all through the examination. During the investigation
stage, a genuine examination happens. This model coordinates measurable examination into the
occurrence reaction structure. Windows cell phone inquires about is accepted to be hard for
examiners as well as the legal network on account of mechanical advances just as prevalence
(Guido, Buttner, and Grover, 2016).
Source - (Guido, Buttner, and Grover, 2016)
Consequently, the creator will depict the 12-arrange model that gets to different procedures
identified with the criminological investigation of Windows cell phones, just as help Forensic
Practitioners just as associations set up the suitable approaches just as methodology. Planning,
scene insurance, examination just as an acknowledgment, scene documentation, correspondence
shield, Volatile Evidence assortment, Non-Volatile Evidence assortment, stockpiling,
investigation, examination, introduction, just as audit are the phases of the proposed model. This
model recognizes significant criminal examinations identified with Windows cell phones just as
significant PC related criminal examinations. It isolates unstable just as non-unpredictable proof
assortment, which should be possible with regards to the wrongdoing scene, or later in a safe
measurable lab. The creator underlined the correspondence shield as a significant advance before
proof assortment. Another advanced crime scene investigation process model was acquainted
with spread the whole scope of Malaysia's cyberlaw examination systems. To help lead to better
indictments, creators have recognized live just as static information securing stages to
stage, a genuine examination happens. This model coordinates measurable examination into the
occurrence reaction structure. Windows cell phone inquires about is accepted to be hard for
examiners as well as the legal network on account of mechanical advances just as prevalence
(Guido, Buttner, and Grover, 2016).
Source - (Guido, Buttner, and Grover, 2016)
Consequently, the creator will depict the 12-arrange model that gets to different procedures
identified with the criminological investigation of Windows cell phones, just as help Forensic
Practitioners just as associations set up the suitable approaches just as methodology. Planning,
scene insurance, examination just as an acknowledgment, scene documentation, correspondence
shield, Volatile Evidence assortment, Non-Volatile Evidence assortment, stockpiling,
investigation, examination, introduction, just as audit are the phases of the proposed model. This
model recognizes significant criminal examinations identified with Windows cell phones just as
significant PC related criminal examinations. It isolates unstable just as non-unpredictable proof
assortment, which should be possible with regards to the wrongdoing scene, or later in a safe
measurable lab. The creator underlined the correspondence shield as a significant advance before
proof assortment. Another advanced crime scene investigation process model was acquainted
with spread the whole scope of Malaysia's cyberlaw examination systems. To help lead to better
indictments, creators have recognized live just as static information securing stages to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
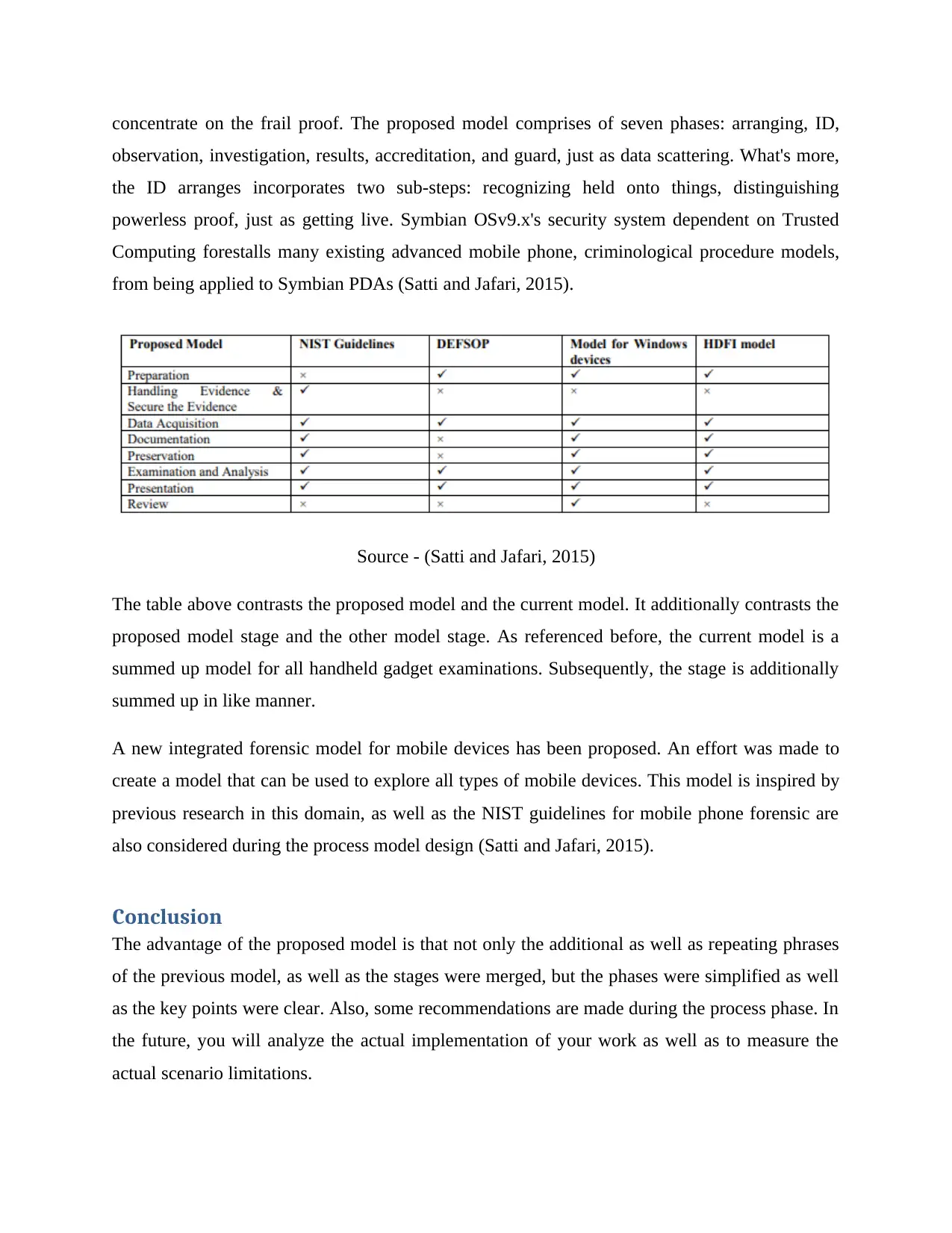
concentrate on the frail proof. The proposed model comprises of seven phases: arranging, ID,
observation, investigation, results, accreditation, and guard, just as data scattering. What's more,
the ID arranges incorporates two sub-steps: recognizing held onto things, distinguishing
powerless proof, just as getting live. Symbian OSv9.x's security system dependent on Trusted
Computing forestalls many existing advanced mobile phone, criminological procedure models,
from being applied to Symbian PDAs (Satti and Jafari, 2015).
Source - (Satti and Jafari, 2015)
The table above contrasts the proposed model and the current model. It additionally contrasts the
proposed model stage and the other model stage. As referenced before, the current model is a
summed up model for all handheld gadget examinations. Subsequently, the stage is additionally
summed up in like manner.
A new integrated forensic model for mobile devices has been proposed. An effort was made to
create a model that can be used to explore all types of mobile devices. This model is inspired by
previous research in this domain, as well as the NIST guidelines for mobile phone forensic are
also considered during the process model design (Satti and Jafari, 2015).
Conclusion
The advantage of the proposed model is that not only the additional as well as repeating phrases
of the previous model, as well as the stages were merged, but the phases were simplified as well
as the key points were clear. Also, some recommendations are made during the process phase. In
the future, you will analyze the actual implementation of your work as well as to measure the
actual scenario limitations.
observation, investigation, results, accreditation, and guard, just as data scattering. What's more,
the ID arranges incorporates two sub-steps: recognizing held onto things, distinguishing
powerless proof, just as getting live. Symbian OSv9.x's security system dependent on Trusted
Computing forestalls many existing advanced mobile phone, criminological procedure models,
from being applied to Symbian PDAs (Satti and Jafari, 2015).
Source - (Satti and Jafari, 2015)
The table above contrasts the proposed model and the current model. It additionally contrasts the
proposed model stage and the other model stage. As referenced before, the current model is a
summed up model for all handheld gadget examinations. Subsequently, the stage is additionally
summed up in like manner.
A new integrated forensic model for mobile devices has been proposed. An effort was made to
create a model that can be used to explore all types of mobile devices. This model is inspired by
previous research in this domain, as well as the NIST guidelines for mobile phone forensic are
also considered during the process model design (Satti and Jafari, 2015).
Conclusion
The advantage of the proposed model is that not only the additional as well as repeating phrases
of the previous model, as well as the stages were merged, but the phases were simplified as well
as the key points were clear. Also, some recommendations are made during the process phase. In
the future, you will analyze the actual implementation of your work as well as to measure the
actual scenario limitations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


References
Andrei, O. and Calder, M., 2018. Data-driven modeling and probabilistic analysis of interactive
software usage. Journal of Logical and Algebraic Methods in Programming, 100, pp.195-214.
Borodin, V., 2013. THE FACE EXTRACTION METHOD FOR MOBILE
DEVICES. Proceedings of National Aviation University, 56(3).
Gabdrakhmanova, K., Izmaylova, G., Larin, P. and Kuleshova, L., 2019. Method for selecting
geothermal energy extraction technologies using nomograms. Journal of Physics: Conference
Series, 1333, p.072006.
Guido, M., Buttner, J. and Grover, J., 2016. Rapid differential forensic imaging of mobile
devices. Digital Investigation, 18, pp.S46-S54.
Lipman, R., 2017. STEP File Analyzer Software. Journal of Research of the National Institute of
Standards and Technology, 122.
Pavych, N. and Pavych, T., 2019. Method for Time Minimization of Api Requests Service From
Cyber-Physical System to Cloud Database Management System. Advances in Cyber-Physical
Systems, 4(2), pp.125-131.
PAŁKOWSKI, M., 2015. Automatic Extraction of Parallelism for Mobile Devices. PRZEGLĄD
ELEKTROTECHNICZNY, 1(11), pp.164-168.
Satti, R. and Jafari, F., 2015. Domain Specific Cyber Forensic Investigation Process
Model. Journal of Advances in Computer Networks, 3(1), pp.75-81.
Cellebrite. 2020. Supporting New Extraction Methods And Devices - Cellebrite. [online]
Available at: <https://www.cellebrite.com/en/productupdates/supporting-new-extraction-
methods-and-devices/> [Accessed 24 March 2020].
Zhu, L. and Li, W., 2014. Feature Extraction Method Based on Content-Aware Tiling on Mobile
Devices. Advanced Materials Research, 926-930, pp.3509-3512.
Andrei, O. and Calder, M., 2018. Data-driven modeling and probabilistic analysis of interactive
software usage. Journal of Logical and Algebraic Methods in Programming, 100, pp.195-214.
Borodin, V., 2013. THE FACE EXTRACTION METHOD FOR MOBILE
DEVICES. Proceedings of National Aviation University, 56(3).
Gabdrakhmanova, K., Izmaylova, G., Larin, P. and Kuleshova, L., 2019. Method for selecting
geothermal energy extraction technologies using nomograms. Journal of Physics: Conference
Series, 1333, p.072006.
Guido, M., Buttner, J. and Grover, J., 2016. Rapid differential forensic imaging of mobile
devices. Digital Investigation, 18, pp.S46-S54.
Lipman, R., 2017. STEP File Analyzer Software. Journal of Research of the National Institute of
Standards and Technology, 122.
Pavych, N. and Pavych, T., 2019. Method for Time Minimization of Api Requests Service From
Cyber-Physical System to Cloud Database Management System. Advances in Cyber-Physical
Systems, 4(2), pp.125-131.
PAŁKOWSKI, M., 2015. Automatic Extraction of Parallelism for Mobile Devices. PRZEGLĄD
ELEKTROTECHNICZNY, 1(11), pp.164-168.
Satti, R. and Jafari, F., 2015. Domain Specific Cyber Forensic Investigation Process
Model. Journal of Advances in Computer Networks, 3(1), pp.75-81.
Cellebrite. 2020. Supporting New Extraction Methods And Devices - Cellebrite. [online]
Available at: <https://www.cellebrite.com/en/productupdates/supporting-new-extraction-
methods-and-devices/> [Accessed 24 March 2020].
Zhu, L. and Li, W., 2014. Feature Extraction Method Based on Content-Aware Tiling on Mobile
Devices. Advanced Materials Research, 926-930, pp.3509-3512.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





