University Mobile Network Engineering - Assignment 2, Part 1 Report
VerifiedAdded on 2022/10/06
|12
|2576
|11
Report
AI Summary
This report delves into the core components of IoT systems, including sensors, connectivity, data processing, and user interfaces, providing a comprehensive understanding of their functions and applications. It examines the IoT reference framework, detailing its four levels and their roles in system architecture. The report then analyzes the advantages, disadvantages, and key requirements of different data acquisition methods such as sensors, RFID, and video, along with their practical applications. Furthermore, it explores MQTT and DDS RTPS protocols, comparing their features, advantages, and use cases in IoT implementations. Finally, the report investigates the AWS IoT Core platform, explaining its functionality, key features, and device management capabilities, offering a complete overview of the technologies driving modern mobile network engineering.

Running head: MOBILE NETWORK ENGINEERING 1
MOBILE NETWORK ENGINEERING
STUDENT’S NAME
UNIVERSITY
DATE
MOBILE NETWORK ENGINEERING
STUDENT’S NAME
UNIVERSITY
DATE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MOBILE NEYWORK ENGINEERING 2
2.1 A.
Components of IoT
Internet of things is the latest technological advancement which has a vision of becoming a
global network of devices and machines which are able to interact through a connection. IoT is
envisioned as one of the technology which will overtake the current version of technology
available.
IoT components
Sensor devices. Their sole purpose in internet of things is to collect minute data in the
surrounding environment (Gubbi & Buyya, 2013). The data collected will then be relayed
through a medium to the server. Data collected ranges from different degree of its
complexion. It can be inform of a simple temperature checking of the room or control to
a more complex full video view monitoring of a room for example CCTV camera. One
device may have single sensors while others might have multiple sensors which perform
different task. For instance a phone has got different sensors like GPS accelerometers and
camera but does not have a sensor. The sole purpose of the sensor is to collect vital data
or information in the surround environment.
Connectivity. Once the data has been collected by a sensor, this information has to be
transferred to the servers. For this to be achieved there has to be a medium. These devices
can be connected by several means for example, cellular network, Wi-Fi, Bluetooth or
wide area network (WAN). It is important to choose the best and more reliable medium
which will achieve the set specification and trade-off between power consumption and
bandwidth.
Data processing- when the data gets to the server, it has to be processed for appropriate
response. It may involve simple data processing like counter checking if the temperature
of the room is within the allowed range, and if its outside the range it has to correct it or
relay data to a user to correct it. It can also be a complex process identification of objects
if there is an intruder in the compound. This is achieved by the use of computer vision on
a video. At some point in the data processing may require the user to interpret it.
2.1 A.
Components of IoT
Internet of things is the latest technological advancement which has a vision of becoming a
global network of devices and machines which are able to interact through a connection. IoT is
envisioned as one of the technology which will overtake the current version of technology
available.
IoT components
Sensor devices. Their sole purpose in internet of things is to collect minute data in the
surrounding environment (Gubbi & Buyya, 2013). The data collected will then be relayed
through a medium to the server. Data collected ranges from different degree of its
complexion. It can be inform of a simple temperature checking of the room or control to
a more complex full video view monitoring of a room for example CCTV camera. One
device may have single sensors while others might have multiple sensors which perform
different task. For instance a phone has got different sensors like GPS accelerometers and
camera but does not have a sensor. The sole purpose of the sensor is to collect vital data
or information in the surround environment.
Connectivity. Once the data has been collected by a sensor, this information has to be
transferred to the servers. For this to be achieved there has to be a medium. These devices
can be connected by several means for example, cellular network, Wi-Fi, Bluetooth or
wide area network (WAN). It is important to choose the best and more reliable medium
which will achieve the set specification and trade-off between power consumption and
bandwidth.
Data processing- when the data gets to the server, it has to be processed for appropriate
response. It may involve simple data processing like counter checking if the temperature
of the room is within the allowed range, and if its outside the range it has to correct it or
relay data to a user to correct it. It can also be a complex process identification of objects
if there is an intruder in the compound. This is achieved by the use of computer vision on
a video. At some point in the data processing may require the user to interpret it.

MOBILE NEYWORK ENGINEERING 3
User interface- processed data may have to be relayed to the end user. This can be
achieved through various methods. Like the use of alarm notification via the use of the
phone, emails or text.in some cases a user might want to check actively on the internet of
things. For instance a user can install a camera in the house and might want to check
video recording and all that feeds through a web server. With more advanced systems the
relayed data might be automatically processed and information relayed back to correct or
make an improvement on what needs to be checked.
2.1 C.
The basic description of MQTT and DDS RTPS
Message Queue Telemetry Transport is a simple messaging protocol made for
devices with low bandwidth. It allows users to publish and receive messages using
publish/subscribe paradigm. It allows users to send commands to the control output,
permitting read and publish data from nodes. It has identifying features rarely found in
other protocols.it is a lightweight protocol based on messaging techniques (Sankar,
2016). It minimizes data packets and offers real time connectivity.it works on basis of
client and server. A server handles requests or simply receives data from one device to
the other.
DDS RTPS is a real-time publish/subscribe protocol. It has best efforts and is
reliable publish/subscribe communication over unreliable transport. With this protocol,
unicast and multicast communications are possible.it has interoperability characteristic
for data distribution service implementation. It is widely used in aerospace and defense
sector for real time devices. It has the following features:
i. Performance and quality of service
ii. It is fault tolerant
iii. Extensible with plug and play connectivity
iv. Can be configured.
Major advantages of MQTT and DDS RTPS over Client-Server
i. MQTT and DDS use publish/subscribe mechanism making them lightweight. Client-
server paradigm has high overload( (Shinde, NImkar, Singh, Salpe, & Jadhav, 2016)
User interface- processed data may have to be relayed to the end user. This can be
achieved through various methods. Like the use of alarm notification via the use of the
phone, emails or text.in some cases a user might want to check actively on the internet of
things. For instance a user can install a camera in the house and might want to check
video recording and all that feeds through a web server. With more advanced systems the
relayed data might be automatically processed and information relayed back to correct or
make an improvement on what needs to be checked.
2.1 C.
The basic description of MQTT and DDS RTPS
Message Queue Telemetry Transport is a simple messaging protocol made for
devices with low bandwidth. It allows users to publish and receive messages using
publish/subscribe paradigm. It allows users to send commands to the control output,
permitting read and publish data from nodes. It has identifying features rarely found in
other protocols.it is a lightweight protocol based on messaging techniques (Sankar,
2016). It minimizes data packets and offers real time connectivity.it works on basis of
client and server. A server handles requests or simply receives data from one device to
the other.
DDS RTPS is a real-time publish/subscribe protocol. It has best efforts and is
reliable publish/subscribe communication over unreliable transport. With this protocol,
unicast and multicast communications are possible.it has interoperability characteristic
for data distribution service implementation. It is widely used in aerospace and defense
sector for real time devices. It has the following features:
i. Performance and quality of service
ii. It is fault tolerant
iii. Extensible with plug and play connectivity
iv. Can be configured.
Major advantages of MQTT and DDS RTPS over Client-Server
i. MQTT and DDS use publish/subscribe mechanism making them lightweight. Client-
server paradigm has high overload( (Shinde, NImkar, Singh, Salpe, & Jadhav, 2016)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

MOBILE NEYWORK ENGINEERING 4
ii. MQTT and DDS offer security since authentication is achieved by use of message
broker. Client-Server only concerns with establishment of connection, irrespective of
security aspect.
iii. MQTT and DDS have good Quality of Service, aiding in handling unreliable
networks.
iv. It supports multicasting unlike client-server multicast that supports unicast
communication
v. By using SSL encryption, MQTT is able to establish end to end encryption.
Differences between MQTT and DDS RTPS
i. MQTT is used in telemetry while DDS is used in intelligent systems
ii. MQTT is centralized and server based while DDS is distributed and only embedded
at the edge
iii. MQTT is used mostly with WAN networks while DDS is used with LAN, WAN and
shared memory.
iv. MQTT requires some configuration involving IT administrator. DDS is often
autonomous, requiring no IT admin
v. MQTT consists of 3 main components: Publisher, Subscriber and Broker. DDS has
no broker. It has pub/sub
vi. MQTT is a transport layer protocol while DDS is a session layer protocol.
vii. MQTT supports fewer messages per second per every device while DDS supports up-
to 10000S of messages per second per device.
viii. With MQTT, service interruptions are tolerated unlike DDS where an occurrence of
service interruption can be detrimental
Use cases for using MQTT and DDS and why
MQTT - A company producing energy can monitor oil pipelines located many kilometers away.
If flow issues are detected, the company can cut off oil flow remotely. MQTT is useful here
since it supports WAN and is lightweight.
ii. MQTT and DDS offer security since authentication is achieved by use of message
broker. Client-Server only concerns with establishment of connection, irrespective of
security aspect.
iii. MQTT and DDS have good Quality of Service, aiding in handling unreliable
networks.
iv. It supports multicasting unlike client-server multicast that supports unicast
communication
v. By using SSL encryption, MQTT is able to establish end to end encryption.
Differences between MQTT and DDS RTPS
i. MQTT is used in telemetry while DDS is used in intelligent systems
ii. MQTT is centralized and server based while DDS is distributed and only embedded
at the edge
iii. MQTT is used mostly with WAN networks while DDS is used with LAN, WAN and
shared memory.
iv. MQTT requires some configuration involving IT administrator. DDS is often
autonomous, requiring no IT admin
v. MQTT consists of 3 main components: Publisher, Subscriber and Broker. DDS has
no broker. It has pub/sub
vi. MQTT is a transport layer protocol while DDS is a session layer protocol.
vii. MQTT supports fewer messages per second per every device while DDS supports up-
to 10000S of messages per second per device.
viii. With MQTT, service interruptions are tolerated unlike DDS where an occurrence of
service interruption can be detrimental
Use cases for using MQTT and DDS and why
MQTT - A company producing energy can monitor oil pipelines located many kilometers away.
If flow issues are detected, the company can cut off oil flow remotely. MQTT is useful here
since it supports WAN and is lightweight.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MOBILE NEYWORK ENGINEERING 5
DDS – A company generating power using oil or gas can use DDS to mange its production. DDS
provides for high tolerance and high sensor performance capabilities. Since it does not have a
broker, DDS makes deployment easy.
IoT architecture is a system of several elements. These elements includes: sensors, protocols,
actuators, cloud services and layers. There area four stages or levels in IoT architecture that have
been designed to track the consistency of system layers. Layers are also used to distinguish the
functions of various components. The following discussion gives an insight into the main actions
and importance of each level.
The first stage of IoT architecture comprises the network of things. These include sensors, and
actuators. Sensors are designed to obtain information from the real world. They then transform
this information into data for analysis. Actuators on the other hand have the capability of
intervening. For example actuators can switch on the light and modify the temperature of the
surrounding environment depending on the desired needs.
Stage two is made up of data aggregation systems. This stage requires working closely with
sensors and actuators. It also works hand in hand with internet gateways and data acquisition
systems. The internet gateways operate via Wi-Fi and LANs and perform further data analysis.
Ata these stage large amounts of information collected from the previous stage are compressed
into an optimum size for further analysis. The data is digitized and aggregated at this stage.
The third stage is the introduction of Edge IT Solutions. The prepared data is transferred in to
the IT systems. These systems preform highly enhanced analytics and pre-processing of the
collected data. Some additional processing of data is done before data can reach the data center.
This stage is closely enjoined with the previous stage in the design of IoT architecture.
The last stage is analysis, management and storage of data. The main processes happen in data
center. This level allows for an in-depth processing and analysis of data and feedback. After
meeting all quality demands, the output is brought back to the real world but in a processed and
accurately analyzed form.
DDS – A company generating power using oil or gas can use DDS to mange its production. DDS
provides for high tolerance and high sensor performance capabilities. Since it does not have a
broker, DDS makes deployment easy.
IoT architecture is a system of several elements. These elements includes: sensors, protocols,
actuators, cloud services and layers. There area four stages or levels in IoT architecture that have
been designed to track the consistency of system layers. Layers are also used to distinguish the
functions of various components. The following discussion gives an insight into the main actions
and importance of each level.
The first stage of IoT architecture comprises the network of things. These include sensors, and
actuators. Sensors are designed to obtain information from the real world. They then transform
this information into data for analysis. Actuators on the other hand have the capability of
intervening. For example actuators can switch on the light and modify the temperature of the
surrounding environment depending on the desired needs.
Stage two is made up of data aggregation systems. This stage requires working closely with
sensors and actuators. It also works hand in hand with internet gateways and data acquisition
systems. The internet gateways operate via Wi-Fi and LANs and perform further data analysis.
Ata these stage large amounts of information collected from the previous stage are compressed
into an optimum size for further analysis. The data is digitized and aggregated at this stage.
The third stage is the introduction of Edge IT Solutions. The prepared data is transferred in to
the IT systems. These systems preform highly enhanced analytics and pre-processing of the
collected data. Some additional processing of data is done before data can reach the data center.
This stage is closely enjoined with the previous stage in the design of IoT architecture.
The last stage is analysis, management and storage of data. The main processes happen in data
center. This level allows for an in-depth processing and analysis of data and feedback. After
meeting all quality demands, the output is brought back to the real world but in a processed and
accurately analyzed form.
MOBILE NEYWORK ENGINEERING 6
2.1B
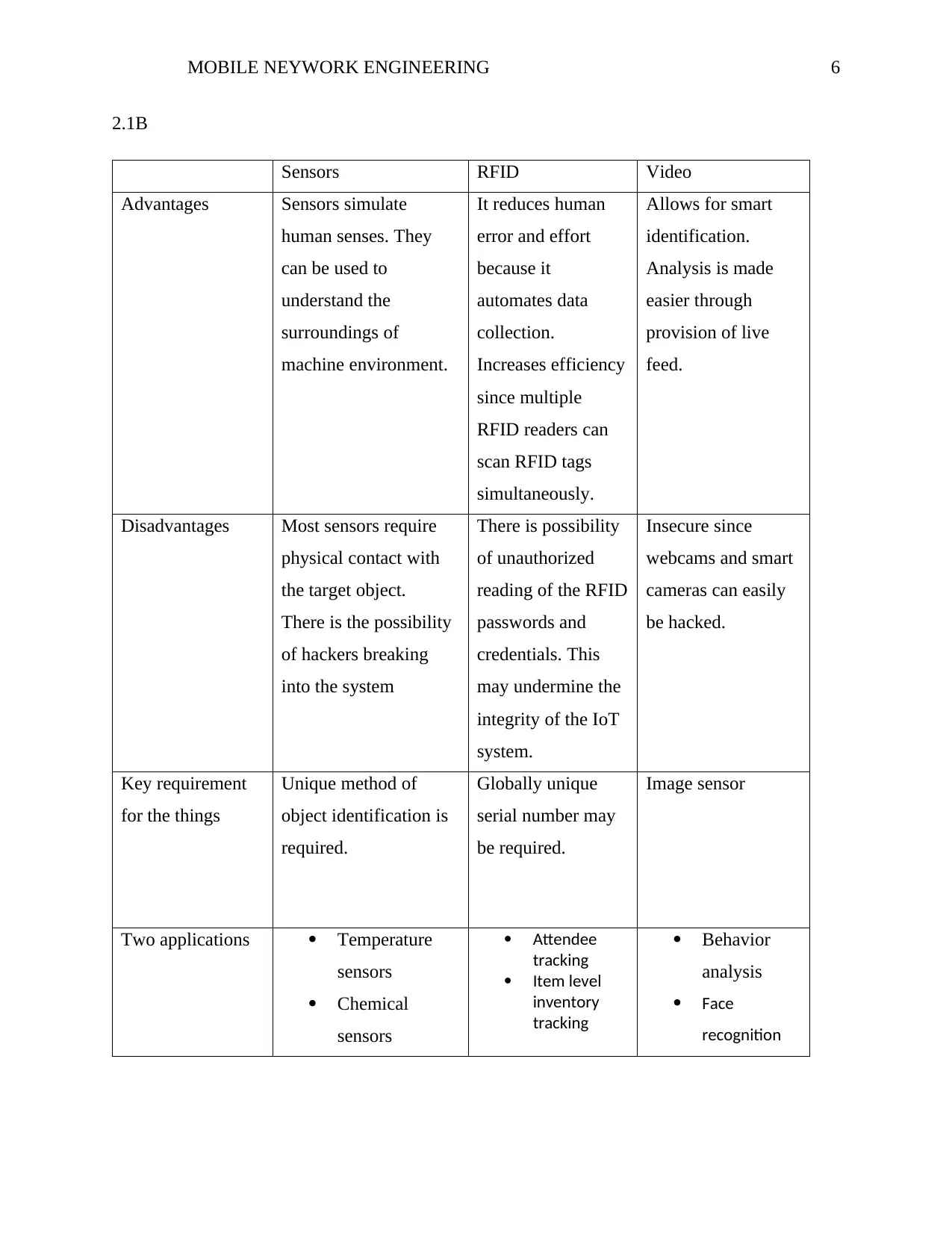
Sensors RFID Video
Advantages Sensors simulate
human senses. They
can be used to
understand the
surroundings of
machine environment.
It reduces human
error and effort
because it
automates data
collection.
Increases efficiency
since multiple
RFID readers can
scan RFID tags
simultaneously.
Allows for smart
identification.
Analysis is made
easier through
provision of live
feed.
Disadvantages Most sensors require
physical contact with
the target object.
There is the possibility
of hackers breaking
into the system
There is possibility
of unauthorized
reading of the RFID
passwords and
credentials. This
may undermine the
integrity of the IoT
system.
Insecure since
webcams and smart
cameras can easily
be hacked.
Key requirement
for the things
Unique method of
object identification is
required.
Globally unique
serial number may
be required.
Image sensor
Two applications Temperature
sensors
Chemical
sensors
Attendee
tracking
Item level
inventory
tracking
Behavior
analysis
Face
recognition
2.1B
Sensors RFID Video
Advantages Sensors simulate
human senses. They
can be used to
understand the
surroundings of
machine environment.
It reduces human
error and effort
because it
automates data
collection.
Increases efficiency
since multiple
RFID readers can
scan RFID tags
simultaneously.
Allows for smart
identification.
Analysis is made
easier through
provision of live
feed.
Disadvantages Most sensors require
physical contact with
the target object.
There is the possibility
of hackers breaking
into the system
There is possibility
of unauthorized
reading of the RFID
passwords and
credentials. This
may undermine the
integrity of the IoT
system.
Insecure since
webcams and smart
cameras can easily
be hacked.
Key requirement
for the things
Unique method of
object identification is
required.
Globally unique
serial number may
be required.
Image sensor
Two applications Temperature
sensors
Chemical
sensors
Attendee
tracking
Item level
inventory
tracking
Behavior
analysis
Face
recognition
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
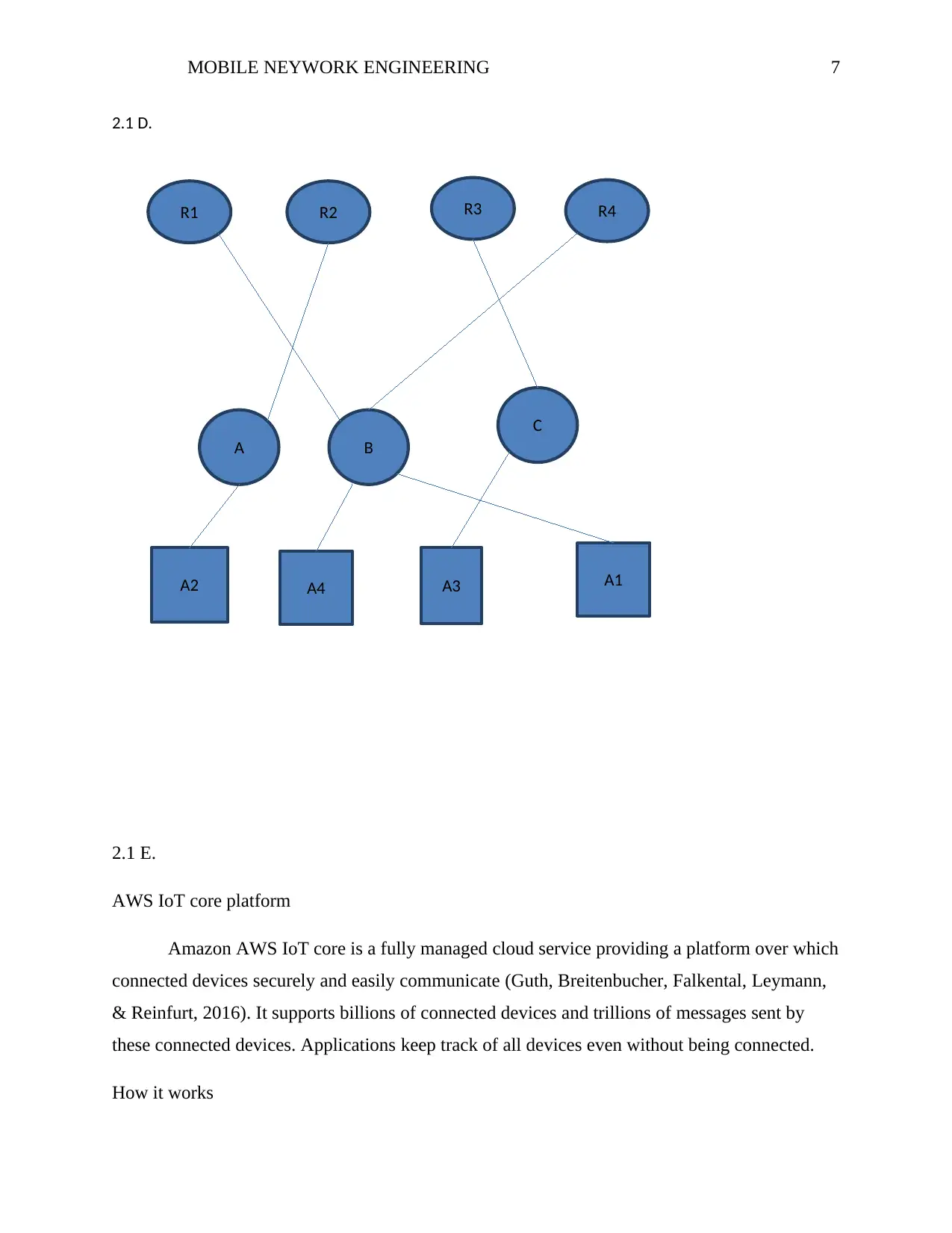
R2R1 R3 R4
A2 A3A4 A1
A B
C
MOBILE NEYWORK ENGINEERING 7
2.1 D.
2.1 E.
AWS IoT core platform
Amazon AWS IoT core is a fully managed cloud service providing a platform over which
connected devices securely and easily communicate (Guth, Breitenbucher, Falkental, Leymann,
& Reinfurt, 2016). It supports billions of connected devices and trillions of messages sent by
these connected devices. Applications keep track of all devices even without being connected.
How it works
A2 A3A4 A1
A B
C
MOBILE NEYWORK ENGINEERING 7
2.1 D.
2.1 E.
AWS IoT core platform
Amazon AWS IoT core is a fully managed cloud service providing a platform over which
connected devices securely and easily communicate (Guth, Breitenbucher, Falkental, Leymann,
& Reinfurt, 2016). It supports billions of connected devices and trillions of messages sent by
these connected devices. Applications keep track of all devices even without being connected.
How it works
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MOBILE NEYWORK ENGINEERING 8
AWS IoT core connects and manages all your IoT devices. Users can easily connect
devices to other devices and to the cloud.
It supports hypertext transfer protocol HTTP, MQT and Websocket protocol.
Through MQT, this platform tolerates intermittent connectivity and reduced bandwidth
requirements. Devices using different protocols can be able to communicate.
After establishing connection, AWS IoT core secures connections and data.
Authentication and data encryption is provided across all connection points, to prevent
data exchange between devices and core without proven identity. Granular permissions
can also be used to establish secure access to your devices.
Transmitted and received data is then processed and acted upon. A user can filter and
transform device data using prior defined rules.
After processing of data, device state can be read and set any time. Every device’s state
is stored when connected. This makes your device appear to be online all time, allowing
all your applications to read device state even when that particular device is disconnected.
A user is able to set device state when that device re-establishes connection.
Key features
Device SDK- allows quick and easy connection to hardware device. It also allows connection of
mobile application to AWS IoT core. Using different protocols, SDK allows IoT devices to
connect and exchange messages securely.
Device Gateway- this serves as an entry point for all IoT devices to connect to the core. It
manages all active connections, implementing semantics through which different protocols can
communicate. Device gateway supports HTTP V1.1, Websocket and MQTT protocols. Gateway
maintains long lived connections to and from AWS IoT core. Devices will be able to
communicate securely and with low latency.
Message Broker- it has high throughput enabling secure transmission of messages between IoT
devices and the core. One to one messaging command patterns are supported by message broker.
Besides, one to one million broadcast notifications system.
Authentication and authorization- mutual authentication is provided through this mechanism. No
data exchanges happen between unauthenticated devices.
AWS IoT core connects and manages all your IoT devices. Users can easily connect
devices to other devices and to the cloud.
It supports hypertext transfer protocol HTTP, MQT and Websocket protocol.
Through MQT, this platform tolerates intermittent connectivity and reduced bandwidth
requirements. Devices using different protocols can be able to communicate.
After establishing connection, AWS IoT core secures connections and data.
Authentication and data encryption is provided across all connection points, to prevent
data exchange between devices and core without proven identity. Granular permissions
can also be used to establish secure access to your devices.
Transmitted and received data is then processed and acted upon. A user can filter and
transform device data using prior defined rules.
After processing of data, device state can be read and set any time. Every device’s state
is stored when connected. This makes your device appear to be online all time, allowing
all your applications to read device state even when that particular device is disconnected.
A user is able to set device state when that device re-establishes connection.
Key features
Device SDK- allows quick and easy connection to hardware device. It also allows connection of
mobile application to AWS IoT core. Using different protocols, SDK allows IoT devices to
connect and exchange messages securely.
Device Gateway- this serves as an entry point for all IoT devices to connect to the core. It
manages all active connections, implementing semantics through which different protocols can
communicate. Device gateway supports HTTP V1.1, Websocket and MQTT protocols. Gateway
maintains long lived connections to and from AWS IoT core. Devices will be able to
communicate securely and with low latency.
Message Broker- it has high throughput enabling secure transmission of messages between IoT
devices and the core. One to one messaging command patterns are supported by message broker.
Besides, one to one million broadcast notifications system.
Authentication and authorization- mutual authentication is provided through this mechanism. No
data exchanges happen between unauthenticated devices.

MOBILE NEYWORK ENGINEERING 9
Registry – This allows easy tracking of devices as it establishes their identities. Every device is
assigned a unique credential.
Device shadow – this is a virtual version of each device connected to core. It contains
information on device state that enables devices can interact with each other, reading messages
securely. Applications can be built to easily interact with devices using REST APIs.
How AWS IoT core manages IoT devices
Device management is essential to enable tracking and monitoring of all connected devices.
AWS IoT device management allows easy to organize and remotely manage devices to securely
communicate.
Devices can be registered in bulk or individually. Permissions are managed to secure
devices.
Devices can be organized and managed, troubleshooting functionality and updating
firmware. With device management, users can achieve fast device onboarding, simple
organization of IoT devices, quick location of devices, and easy device management.
Every device once connected has credentials to access message broker and device
shadow service. Transport Layer Security encrypts all traffic between IoT core and
devices. Every device’s credential has to be kept safely to enable secure transfer of data
to message broker.
Security mechanism in AWS IoT core enables data protection between connected devices
and the core. A user manages device credentials and AWS IoT policies. X.509 certificate
is used (Ammar, Russello, & Crispo, 2018).
Device connects to core using X.509 certificates and amazon cognito identities.
Message broker authenticates all user actions. It authenticates connected devices, ingests
device data securely and adheres to access permissions that a user places on device
policies.
Device shadow service encrypts device communications with Transport Layer Security
version 1.2. This ensures confidentiality of protocols supported.
When using MQTT protocol, connection is encrypted between message broker and the
device. TLS client authentication is used to identify devices (Clark & Linh, 2013).
Registry – This allows easy tracking of devices as it establishes their identities. Every device is
assigned a unique credential.
Device shadow – this is a virtual version of each device connected to core. It contains
information on device state that enables devices can interact with each other, reading messages
securely. Applications can be built to easily interact with devices using REST APIs.
How AWS IoT core manages IoT devices
Device management is essential to enable tracking and monitoring of all connected devices.
AWS IoT device management allows easy to organize and remotely manage devices to securely
communicate.
Devices can be registered in bulk or individually. Permissions are managed to secure
devices.
Devices can be organized and managed, troubleshooting functionality and updating
firmware. With device management, users can achieve fast device onboarding, simple
organization of IoT devices, quick location of devices, and easy device management.
Every device once connected has credentials to access message broker and device
shadow service. Transport Layer Security encrypts all traffic between IoT core and
devices. Every device’s credential has to be kept safely to enable secure transfer of data
to message broker.
Security mechanism in AWS IoT core enables data protection between connected devices
and the core. A user manages device credentials and AWS IoT policies. X.509 certificate
is used (Ammar, Russello, & Crispo, 2018).
Device connects to core using X.509 certificates and amazon cognito identities.
Message broker authenticates all user actions. It authenticates connected devices, ingests
device data securely and adheres to access permissions that a user places on device
policies.
Device shadow service encrypts device communications with Transport Layer Security
version 1.2. This ensures confidentiality of protocols supported.
When using MQTT protocol, connection is encrypted between message broker and the
device. TLS client authentication is used to identify devices (Clark & Linh, 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

MOBILE NEYWORK ENGINEERING 10
When using HTTP, AWS signature V4.0 is used to authenticate devices
When using HTTP, AWS signature V4.0 is used to authenticate devices
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MOBILE NEYWORK ENGINEERING 11
References
Ammar, M., Russello, G., & Crispo, B. (2018). Internet of Things: A survey on the security of IoT
frameworks. Journal of Informaation Security and Applications.
Clark, A. S., & Linh, H. (2013). MQTT for sensor Networks (MQTT-SN) protocol specification version 1.2.
Gubbi, J., & Buyya, R. (2013). Internet of Things (IoT): A vision architectural elements, and future
directions. Future Generation Computer Systems .
Guth, J., Breitenbucher, U., Falkental, M., Leymann, F., & Reinfurt, L. (2016). Comparison of IoT platform
Architectures: A field study based on a reference architecture. Cloudification of the Internet of
Things.
Sankar, P. S. (2016). A secure and fast Authentication implementation between entities using trust
aware algorithm. Internationl research Journal of Egnineering.
Shinde, S. A., NImkar, P. A., Singh, S. P., Salpe, v. D., & Jadhav, y. (2016). MQTT-message queing
telementry transport protocol. International Journal of Research.
References
Ammar, M., Russello, G., & Crispo, B. (2018). Internet of Things: A survey on the security of IoT
frameworks. Journal of Informaation Security and Applications.
Clark, A. S., & Linh, H. (2013). MQTT for sensor Networks (MQTT-SN) protocol specification version 1.2.
Gubbi, J., & Buyya, R. (2013). Internet of Things (IoT): A vision architectural elements, and future
directions. Future Generation Computer Systems .
Guth, J., Breitenbucher, U., Falkental, M., Leymann, F., & Reinfurt, L. (2016). Comparison of IoT platform
Architectures: A field study based on a reference architecture. Cloudification of the Internet of
Things.
Sankar, P. S. (2016). A secure and fast Authentication implementation between entities using trust
aware algorithm. Internationl research Journal of Egnineering.
Shinde, S. A., NImkar, P. A., Singh, S. P., Salpe, v. D., & Jadhav, y. (2016). MQTT-message queing
telementry transport protocol. International Journal of Research.

MOBILE NEYWORK ENGINEERING 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




