Advanced Scripting Languages: Mobile Device Security Analysis Report
VerifiedAdded on 2021/04/24
|14
|4570
|66
Report
AI Summary
This report delves into the critical aspects of mobile device security, a paramount concern in today's technology-driven world. The study investigates the vulnerabilities inherent in mobile devices, including smartphones, focusing on operating systems like Android. It examines hardware and software-related security threats, such as storage systems, network access, and encryption methods. Several mobile devices were analyzed and tested to identify security features and weaknesses. The research highlights various vulnerabilities, including data privacy breaches, data leaks, unauthorized access, and malware threats. The report reviews existing literature and discusses the evolution of mobile devices and the security challenges they present, emphasizing the need for improved security measures to protect user data. The analysis encompasses static and live analysis techniques, revealing the structure of files, temporary data, browser history, and application data, including user profiles and passwords. The study concludes with an overview of the prevalent mobile threats and proposes actionable solutions to mitigate risks and enhance mobile device security.

Advanced scripting languages
By
(Name)
(Course)
(Professor’s Name)
(Institution)
(State)
(Date)
By
(Name)
(Course)
(Professor’s Name)
(Institution)
(State)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract.
Mobile devices have become part and parcel of out today lives, thanks to technology.
These devices run on operating systems such as android, windows or IOS with hardware
compatibility giving them the ability to connect to each other and to the internet for functions
and services such as data sharing, web browsing, email services, social media, entertainment
and google maps. The scope of mobile phone security threats covers hardware and software
related factors such as storage systems, network access and encryption. Several mobile
devices were taken as case studies for this research. The devices were analysed and tested for
both their security features and vulnerabilities for unauthorized access. We find that these
mobile devices have a lot of security vulnerabilities relating to data privacy, data leaks,
unauthorized access and malware.
Keywords.
Mobile devices, vulnerabilities, internet, encryption, privacy, unauthorized.
INTRODUCTION.
Mobile devices have evolved to become more efficient and perform computerized
capabilities and thus achieve more adoption in the public by the consumers from individual
persons, organizations and the governments and as such have become necessary companions
for these consumers at work or at home to perform tasks, entertain and socialize. Major
improvements have been made in the field relating to the hardware and software
compatibilities. These improvements have also enabled accomplishment of more advanced
tasks using the mobile devices. As an advantage, the improvements have also made the
mobile devices more attractive to attackers, Becher (2011).
Mobile devices run on different operating system platforms. Examples include
Windows, produced by Microsoft, Google’s Android and Iphone’s iOS. Android is the most
used and widely accepted operating system with thousands of companies use the platform to
produce and run their mobile devices such as smartphones, smart televisions, portable routers
and other physical entities connected to the Internet of Things. Android is an open source
project meaning that different users of the platform can edit and use it to suit their business or
personal needs and objectives in performing different functions and delivery of services. The
open source model has led to it being a prime target to attacks by malicious individuals using
Mobile devices have become part and parcel of out today lives, thanks to technology.
These devices run on operating systems such as android, windows or IOS with hardware
compatibility giving them the ability to connect to each other and to the internet for functions
and services such as data sharing, web browsing, email services, social media, entertainment
and google maps. The scope of mobile phone security threats covers hardware and software
related factors such as storage systems, network access and encryption. Several mobile
devices were taken as case studies for this research. The devices were analysed and tested for
both their security features and vulnerabilities for unauthorized access. We find that these
mobile devices have a lot of security vulnerabilities relating to data privacy, data leaks,
unauthorized access and malware.
Keywords.
Mobile devices, vulnerabilities, internet, encryption, privacy, unauthorized.
INTRODUCTION.
Mobile devices have evolved to become more efficient and perform computerized
capabilities and thus achieve more adoption in the public by the consumers from individual
persons, organizations and the governments and as such have become necessary companions
for these consumers at work or at home to perform tasks, entertain and socialize. Major
improvements have been made in the field relating to the hardware and software
compatibilities. These improvements have also enabled accomplishment of more advanced
tasks using the mobile devices. As an advantage, the improvements have also made the
mobile devices more attractive to attackers, Becher (2011).
Mobile devices run on different operating system platforms. Examples include
Windows, produced by Microsoft, Google’s Android and Iphone’s iOS. Android is the most
used and widely accepted operating system with thousands of companies use the platform to
produce and run their mobile devices such as smartphones, smart televisions, portable routers
and other physical entities connected to the Internet of Things. Android is an open source
project meaning that different users of the platform can edit and use it to suit their business or
personal needs and objectives in performing different functions and delivery of services. The
open source model has led to it being a prime target to attacks by malicious individuals using

mobile applications or network access using command execution to access and harvest the
user’s private data.
All the consumers of mobile devices are apprehensive about their data security,
accuracy and integrity. This provides a need to the producers of the mobile devices to
increase and improve the security features of the devices to meet the security needs of the
users. These obligations include data security, reduce data loss and leaks and prevent
unauthorized access by third party applications or individuals such as malware and spyware.
Stricter levels of security and protection should therefore be implemented more than what the
producers of the mobile devices are able to provide.
The ever increasing mobile technology to increase user productivity and efficiency
puts a need on the producers of mobile devices to properly secure their products. As an
example, user store private and confidential data on the hand held devices such as
smartphones not limited to bank account details and passwords that in malicious hands can be
devastating. The benefits of the mobile devices are numerous and worth however have been
thwarted by security risks leading to fraud, loss of privacy and data losses.
The scope of the mobile device security investigation.
Digital investigation of the mobile system security vulnerabilities includes the
scientific techniques and practices used in the determining the functionalities of the device
and the security loopholes left behind. The world has shifted from the internet and world
wide web to a mobile society where almost all tasks are accomplished using the mobile
devices such as smartphones. These mobile devices are used to access information from the
internet that was done by the computers in the older days. Most mobile devices consumers
use the gadgets in their day to day activities and therefore the devices receive, generate and
store more and more of the users’ private data. With the need to protect their data, mobile
device security becomes a human need and primary enforcer and not a human want nor
secondary enforcer, Ghosh & Swaminatha (2011). This paper reviews to determine the
overview of mobile device security including the application layer, data link layers and
storage services of the applications installed and running on the devices. The research further
focuses on the attack made using third party applications such as web browsers and the
mobile application user as an attack enabler. The paper intends to show the main aspects of
the security of mobile devices that exposes the users to the risks involved.
user’s private data.
All the consumers of mobile devices are apprehensive about their data security,
accuracy and integrity. This provides a need to the producers of the mobile devices to
increase and improve the security features of the devices to meet the security needs of the
users. These obligations include data security, reduce data loss and leaks and prevent
unauthorized access by third party applications or individuals such as malware and spyware.
Stricter levels of security and protection should therefore be implemented more than what the
producers of the mobile devices are able to provide.
The ever increasing mobile technology to increase user productivity and efficiency
puts a need on the producers of mobile devices to properly secure their products. As an
example, user store private and confidential data on the hand held devices such as
smartphones not limited to bank account details and passwords that in malicious hands can be
devastating. The benefits of the mobile devices are numerous and worth however have been
thwarted by security risks leading to fraud, loss of privacy and data losses.
The scope of the mobile device security investigation.
Digital investigation of the mobile system security vulnerabilities includes the
scientific techniques and practices used in the determining the functionalities of the device
and the security loopholes left behind. The world has shifted from the internet and world
wide web to a mobile society where almost all tasks are accomplished using the mobile
devices such as smartphones. These mobile devices are used to access information from the
internet that was done by the computers in the older days. Most mobile devices consumers
use the gadgets in their day to day activities and therefore the devices receive, generate and
store more and more of the users’ private data. With the need to protect their data, mobile
device security becomes a human need and primary enforcer and not a human want nor
secondary enforcer, Ghosh & Swaminatha (2011). This paper reviews to determine the
overview of mobile device security including the application layer, data link layers and
storage services of the applications installed and running on the devices. The research further
focuses on the attack made using third party applications such as web browsers and the
mobile application user as an attack enabler. The paper intends to show the main aspects of
the security of mobile devices that exposes the users to the risks involved.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The ebb and flow examine proposes, utilizing a benchmarking and exploitative tools
technique to enable the planning of a measurable, presentable and applicable examination to
cell phones with Android working framework; in view of the chain of care rules, consistence
stages, and stages and to identify discoveries, dissentions, find vulnerabilities. In light of this
procedure, we can decide the starting point of the main sources of various kinds of occasions
or targets directed towards a cell phone as a mobile device. Also, utilizing a choice lattice, the
best programming for playing out the scientific examination is picked and utilizing Balanced
Scorecard, markers are assessed.
The research focused on the different mobile threats prevalently are categorized into
three:
The threats originating from the installation and use of mobile applications which
include adware, malware and spyware.
Threats arising from the connection of the mobile device to the internet on different
networks such as data loss, unauthorized access, data leaks and “man-in-the-middle”
eavesdrop.
Physical vulnerabilities of using small, portable handheld devices such as getting lost,
water and dust destruction and theft.
This paper focuses on the mobile security that is specific to the mobile devices and not how
the normal security of other computer systems can be implemented to the field and offer
protection to the user data.
Literature review.
In the paper by Shon & Choi (2017, September). “Mobile Phone Usage Patterns,
Security Concerns, and Security Practices of Digital Generation” by Sonya Zhang and Saree
Costa, the authors determined the patterns of use of the mobile devices by the students. The
randomly selected 262 students, were also interviewed about their mobile device practices
and security concerns. The study concluded that mostly the students used their devices for
entertainment and productivity purposes. The authors determined that most mobile device
consumers are aware of the security threats involved with using the devices from the physical
risks of theft to online and application threats. The participants ranked data privacy as the
primary threat they were worried of. In so doing, the participants regularly updated the
software component of their mobile devices and used passwords and pin codes to secure the
technique to enable the planning of a measurable, presentable and applicable examination to
cell phones with Android working framework; in view of the chain of care rules, consistence
stages, and stages and to identify discoveries, dissentions, find vulnerabilities. In light of this
procedure, we can decide the starting point of the main sources of various kinds of occasions
or targets directed towards a cell phone as a mobile device. Also, utilizing a choice lattice, the
best programming for playing out the scientific examination is picked and utilizing Balanced
Scorecard, markers are assessed.
The research focused on the different mobile threats prevalently are categorized into
three:
The threats originating from the installation and use of mobile applications which
include adware, malware and spyware.
Threats arising from the connection of the mobile device to the internet on different
networks such as data loss, unauthorized access, data leaks and “man-in-the-middle”
eavesdrop.
Physical vulnerabilities of using small, portable handheld devices such as getting lost,
water and dust destruction and theft.
This paper focuses on the mobile security that is specific to the mobile devices and not how
the normal security of other computer systems can be implemented to the field and offer
protection to the user data.
Literature review.
In the paper by Shon & Choi (2017, September). “Mobile Phone Usage Patterns,
Security Concerns, and Security Practices of Digital Generation” by Sonya Zhang and Saree
Costa, the authors determined the patterns of use of the mobile devices by the students. The
randomly selected 262 students, were also interviewed about their mobile device practices
and security concerns. The study concluded that mostly the students used their devices for
entertainment and productivity purposes. The authors determined that most mobile device
consumers are aware of the security threats involved with using the devices from the physical
risks of theft to online and application threats. The participants ranked data privacy as the
primary threat they were worried of. In so doing, the participants regularly updated the
software component of their mobile devices and used passwords and pin codes to secure the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

devices. However, the paper does not fully explain the vulnerabilities in the mobile devices
even with or without updates and thus formed the basis for this research.
La Polla et al (2013), in their article titled “Mobile device security: Understanding
vulnerabilities and managing risks”, determine and compare the security configurations in
blackberry OS and iPhone OS. The authors use the devices running on blackberry OS and
iPhone OS with and without the security configuration, testing mobile applications installed
on the devices and determining the security vulnerabilities against the features implemented
in the security configuration. The article concludes that Blackberry offers a more secure
operating system and mobile application platform than both iPhone and Android operating
systems. The article however, does not provide the specific security vulnerabilities in the
application, data link and storage layers of the mobile devices.
In the text “Smart bombs: Mobile Vulnerability and Exploitation”, by John Sawyer,
Tom Eston and Kevin Johnson, they conclude that even though mobile devices are more
common, most consumers use the devices without knowledge of the security. From the tests
and exploitation, the authors determine that the developers use the same codes to build
applications and therefore repeat the same mistakes and vulnerabilities in the developed
systems. The authors suggest a need to improve the security of the mobile devices to secure
the user data.
MOBILE SECURITY.
A mobile device is defined as a physical entity, portable, that is controlled by a
simcard connected to a registered operator. The definition covers entities that are not covered
in the case study but are also affected by the same security vulnerability. Such devices
include Point of Sale systems and smart watches. This paper focuses on smart phones, which
are handheld devices running on a firmware that allows installation and running of custom
applications to deliver the different needs of the consumer. These mobile devices, offer a lot
of productive functionality to the users and consumers not restricted to messaging, web
browsing, e-mailing and entertainment. In more recent times, smart phones are equipped with
the ability to also perform online transactions such as purchase and payments, Al-Muhtadi et
al (2012).
even with or without updates and thus formed the basis for this research.
La Polla et al (2013), in their article titled “Mobile device security: Understanding
vulnerabilities and managing risks”, determine and compare the security configurations in
blackberry OS and iPhone OS. The authors use the devices running on blackberry OS and
iPhone OS with and without the security configuration, testing mobile applications installed
on the devices and determining the security vulnerabilities against the features implemented
in the security configuration. The article concludes that Blackberry offers a more secure
operating system and mobile application platform than both iPhone and Android operating
systems. The article however, does not provide the specific security vulnerabilities in the
application, data link and storage layers of the mobile devices.
In the text “Smart bombs: Mobile Vulnerability and Exploitation”, by John Sawyer,
Tom Eston and Kevin Johnson, they conclude that even though mobile devices are more
common, most consumers use the devices without knowledge of the security. From the tests
and exploitation, the authors determine that the developers use the same codes to build
applications and therefore repeat the same mistakes and vulnerabilities in the developed
systems. The authors suggest a need to improve the security of the mobile devices to secure
the user data.
MOBILE SECURITY.
A mobile device is defined as a physical entity, portable, that is controlled by a
simcard connected to a registered operator. The definition covers entities that are not covered
in the case study but are also affected by the same security vulnerability. Such devices
include Point of Sale systems and smart watches. This paper focuses on smart phones, which
are handheld devices running on a firmware that allows installation and running of custom
applications to deliver the different needs of the consumer. These mobile devices, offer a lot
of productive functionality to the users and consumers not restricted to messaging, web
browsing, e-mailing and entertainment. In more recent times, smart phones are equipped with
the ability to also perform online transactions such as purchase and payments, Al-Muhtadi et
al (2012).

In this case study, analysis was focussed on mobile device running on Qualcomm and
mediate processors. The identified devices were running on the latest version of android,
Android Oreo and had received the latest security past in not more than a month.
Static analysis.
The case study smart phones are handheld devices with a capacitive touch screen to
allow user interaction. The device runs on an operating system, android 8. The case study
smart phones have an integrated data card for wireless connection to Bluetooth, Wi-Fi and
cellular networks.
The static analysis reveals that the devices are equipped with a 2 gigabyte capacity of
dynamic random access memory. The devices are packed with 16 gigabytes of internal
memory that can be expanded to 64 gigabytes of standard memory cards. Using command
executions from a Linux computer, the android system is debugged and displays the
information of the operating system that include the ability of the RAM to buffer to increase
the performance of the device. These dump files in the buffer can be collected by third party
application and hence are a potential for research in this paper. The program HelixPro was
used to identify the vulnerabilities in the file system and manual execution and data
acquisition was used to observe the data that would be considered private to the device user.
Live analysis.
The functional aspect of a smart phone is very dynamic and cannot be defined by a
single handset. With the increasing need for portable mini computers being the primary
driving force in the development of the mobile devices, more of this entities are shipped
prepacked with file systems with the same capabilities to computers. Live analysis of the
storage system of the NAND memory with is a FAT file system was analysed using the hex
editor to extract data from memory file. The analysis revealed that android operating system
uses the SQLite database to store information in the memory that deleted files are only
marked as deleted and allows overwriting. File system analysis was important in
mediate processors. The identified devices were running on the latest version of android,
Android Oreo and had received the latest security past in not more than a month.
Static analysis.
The case study smart phones are handheld devices with a capacitive touch screen to
allow user interaction. The device runs on an operating system, android 8. The case study
smart phones have an integrated data card for wireless connection to Bluetooth, Wi-Fi and
cellular networks.
The static analysis reveals that the devices are equipped with a 2 gigabyte capacity of
dynamic random access memory. The devices are packed with 16 gigabytes of internal
memory that can be expanded to 64 gigabytes of standard memory cards. Using command
executions from a Linux computer, the android system is debugged and displays the
information of the operating system that include the ability of the RAM to buffer to increase
the performance of the device. These dump files in the buffer can be collected by third party
application and hence are a potential for research in this paper. The program HelixPro was
used to identify the vulnerabilities in the file system and manual execution and data
acquisition was used to observe the data that would be considered private to the device user.
Live analysis.
The functional aspect of a smart phone is very dynamic and cannot be defined by a
single handset. With the increasing need for portable mini computers being the primary
driving force in the development of the mobile devices, more of this entities are shipped
prepacked with file systems with the same capabilities to computers. Live analysis of the
storage system of the NAND memory with is a FAT file system was analysed using the hex
editor to extract data from memory file. The analysis revealed that android operating system
uses the SQLite database to store information in the memory that deleted files are only
marked as deleted and allows overwriting. File system analysis was important in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

understanding the structure of the files, data on the files in form of temporary files and cache,
browser history, application statistics and app data including user profiles and passwords.
The android platform, although more developed, was vulnerable to brute force data
acquisition to access the data available on the device flash memory. The data included all the
deleted files and temporary application data.
Mobile devices have become part and parcel of out today lives, thanks to technology.
These devices run on operating systems such as android, windows or IOS with hardware
compatibility giving them the ability to connect to each other and to the internet for functions
and services such as data sharing, web browsing, email services, social media, entertainment
and google maps. The scope of mobile phone security threats covers hardware and software
related factors such as storage systems, network access and encryption. Several mobile
devices were taken as case studies for this research. The devices were analysed and tested for
both their security features and vulnerabilities for unauthorized access. We find that these
mobile devices have a lot of security vulnerabilities relating to data privacy, data leaks,
unauthorized access and malware.
Live analysis of the mobile device connection to the internet revealed the use of
computer protocols to access through the wireless application protocol. This protocol
includes the HTTPS and the TLS protocols. The connection process is through three steps,
the client, which is the consumer’s mobile device seeks a connection to the server, the server
authenticates the connection using the client’s IP address and the connection is confirmed
when the authentication certificates are confirmed. Just like any other computer connection,
this was vulnerable to exploitation from 3rd party applications and malicious unauthorized
access.
Methodology.
In order to check the smart vulnerabilities, static analysis and live analysis were
conducted on the devices using data exploitation tools in the market used by ethical hackers
to evaluate the security levels of the mobile devices. Primarily in static analysis, the storage
repositories of the smart phones were exploited to find and access the data on the image file
of the operating system in the NAND memory.
browser history, application statistics and app data including user profiles and passwords.
The android platform, although more developed, was vulnerable to brute force data
acquisition to access the data available on the device flash memory. The data included all the
deleted files and temporary application data.
Mobile devices have become part and parcel of out today lives, thanks to technology.
These devices run on operating systems such as android, windows or IOS with hardware
compatibility giving them the ability to connect to each other and to the internet for functions
and services such as data sharing, web browsing, email services, social media, entertainment
and google maps. The scope of mobile phone security threats covers hardware and software
related factors such as storage systems, network access and encryption. Several mobile
devices were taken as case studies for this research. The devices were analysed and tested for
both their security features and vulnerabilities for unauthorized access. We find that these
mobile devices have a lot of security vulnerabilities relating to data privacy, data leaks,
unauthorized access and malware.
Live analysis of the mobile device connection to the internet revealed the use of
computer protocols to access through the wireless application protocol. This protocol
includes the HTTPS and the TLS protocols. The connection process is through three steps,
the client, which is the consumer’s mobile device seeks a connection to the server, the server
authenticates the connection using the client’s IP address and the connection is confirmed
when the authentication certificates are confirmed. Just like any other computer connection,
this was vulnerable to exploitation from 3rd party applications and malicious unauthorized
access.
Methodology.
In order to check the smart vulnerabilities, static analysis and live analysis were
conducted on the devices using data exploitation tools in the market used by ethical hackers
to evaluate the security levels of the mobile devices. Primarily in static analysis, the storage
repositories of the smart phones were exploited to find and access the data on the image file
of the operating system in the NAND memory.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In the live analysis, the Core Impact exploitation tool was used to perform a series of
exploitation to identify the vulnerable aspects of the android operating system. The operating
system, Android 8, was tested using the exploitation tools and the findings recorded.
The system specifications for the case study mobile devices was:
Processors: Qualcomm, 2.1 GHz quad core.
Mediatek 1.9 GHz quad core.
Random access memory. DRAM 2GB
DRAM 2 GB.
Android operating system. Android Oreo.
FINDINGS.
The exploitation of the case study smart phones for mobile device vulnerabilities
indicated both static and live potential to allow malicious, unauthorized access to the
consumers’ data. The way the mobile devices have been set up and developed in terms of the
physical hardware and software specifications offers a high level of security and intrusion
detection. However, the security level is not up to par with the developed exploitation tools
and techniques used by the attackers.
The problems arising from the research concerning the security vulnerabilities are
categorized into static and live for ease of understanding and mitigation. The vulnerabilities
are thus a subset of the possible attack points for data loss, data access and modification.
1.1. Static analysis.
The volatility of data collected in the static analysis of the mobile devices used the
memory dump and the NAND memory to check for the system files, temporary files, cache
and application data.
Android devices use the SQLite database model to store data. The database selects the
directory to where the temporary data of an application is to be saved. The database has a
security vulnerability that allows the data be stored in the application parent folder and
therefore expose the data to access by unauthorized individuals or 3rd party applications such
as malware, spyware or remote commands from connected computers. Application temporary
exploitation to identify the vulnerable aspects of the android operating system. The operating
system, Android 8, was tested using the exploitation tools and the findings recorded.
The system specifications for the case study mobile devices was:
Processors: Qualcomm, 2.1 GHz quad core.
Mediatek 1.9 GHz quad core.
Random access memory. DRAM 2GB
DRAM 2 GB.
Android operating system. Android Oreo.
FINDINGS.
The exploitation of the case study smart phones for mobile device vulnerabilities
indicated both static and live potential to allow malicious, unauthorized access to the
consumers’ data. The way the mobile devices have been set up and developed in terms of the
physical hardware and software specifications offers a high level of security and intrusion
detection. However, the security level is not up to par with the developed exploitation tools
and techniques used by the attackers.
The problems arising from the research concerning the security vulnerabilities are
categorized into static and live for ease of understanding and mitigation. The vulnerabilities
are thus a subset of the possible attack points for data loss, data access and modification.
1.1. Static analysis.
The volatility of data collected in the static analysis of the mobile devices used the
memory dump and the NAND memory to check for the system files, temporary files, cache
and application data.
Android devices use the SQLite database model to store data. The database selects the
directory to where the temporary data of an application is to be saved. The database has a
security vulnerability that allows the data be stored in the application parent folder and
therefore expose the data to access by unauthorized individuals or 3rd party applications such
as malware, spyware or remote commands from connected computers. Application temporary

files in theory contain the data that should not be shared such as user profiles and passwords,
pin codes and encryption keys.
Android devices uses the FAT file system to store data on the memory slots. The model
and architecture for data storage is vulnerable to data recovery since the data, before being
overwritten, is only marked as deleted when a delete command is used. This security
vulnerability exposes the user data such as private images, videos, contacts, dex and xml files
to unintentional or intentional unauthorized access by third party apps and individuals.
The android operating system is an open source project. Even though attempts have been
made by the producers of the mobile devices to lock the bootloaders and protect the NAND
memory and flash files, vulnerabilities in the code allows for 3rd party programs and
commands to unlock the bootloaders and acquire super user access to the system image file.
This process, known as rooting in android and jailbreaking in iPhone devices, allows
unauthorized access and installation of third party firmware or applications that can collect
user sensitive data.
1.2. Live analysis.
According to Mulliner (2009, March), The android architecture is built on the ability to
allow permission to the 3rd party applications and commands trying to execute commands to
access resources. This permission-based architecture is vulnerable to security threats due to
erratic permission control mechanisms.
1.2.1: The user as an attack and security vulnerability.
The average user of mobile devices is not able to compliment the permission-based
architecture of the android operating system. Android developers have made every possible
attempt to simplify for the user the security interface of the operating system, however, the
simplified security solutions could not be utilized well by the average users. This exposed
their data to 3rd party applications and unauthorized access due to permissions being granted
to applications more than what was intended to due to the inability to understand the risks
involved. Android applications request user permissions to access data such as those not
limited to information contained in the internal and external memories, contacts, call logs and
messages.
Typical examples of user authenticated bad file permissions include setting wrong 3rd
party application permissions to allow the apps to read and write on the storage directories
pin codes and encryption keys.
Android devices uses the FAT file system to store data on the memory slots. The model
and architecture for data storage is vulnerable to data recovery since the data, before being
overwritten, is only marked as deleted when a delete command is used. This security
vulnerability exposes the user data such as private images, videos, contacts, dex and xml files
to unintentional or intentional unauthorized access by third party apps and individuals.
The android operating system is an open source project. Even though attempts have been
made by the producers of the mobile devices to lock the bootloaders and protect the NAND
memory and flash files, vulnerabilities in the code allows for 3rd party programs and
commands to unlock the bootloaders and acquire super user access to the system image file.
This process, known as rooting in android and jailbreaking in iPhone devices, allows
unauthorized access and installation of third party firmware or applications that can collect
user sensitive data.
1.2. Live analysis.
According to Mulliner (2009, March), The android architecture is built on the ability to
allow permission to the 3rd party applications and commands trying to execute commands to
access resources. This permission-based architecture is vulnerable to security threats due to
erratic permission control mechanisms.
1.2.1: The user as an attack and security vulnerability.
The average user of mobile devices is not able to compliment the permission-based
architecture of the android operating system. Android developers have made every possible
attempt to simplify for the user the security interface of the operating system, however, the
simplified security solutions could not be utilized well by the average users. This exposed
their data to 3rd party applications and unauthorized access due to permissions being granted
to applications more than what was intended to due to the inability to understand the risks
involved. Android applications request user permissions to access data such as those not
limited to information contained in the internal and external memories, contacts, call logs and
messages.
Typical examples of user authenticated bad file permissions include setting wrong 3rd
party application permissions to allow the apps to read and write on the storage directories
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

containing sensitive data. The standard user has little knowledge on data encryption
techniques while saving important data on their device’s SD card either in the internal or the
external memory. Additionally, the average user, who make the large percent of mobile
device users, do not know the best practices in sensitive client data storage mechanisms. In
such circumstances, the user stores their private data such as emails, addresses, account
numbers, identification pin codes, registration numbers and passwords within data files that
are not encrypted and are easy to retrieve such as app manifests, XML files, log files and
SQLite databases.
1.2.2: Poor quality and inefficient data encryption tools.
Developers use the same codes to set up, design and develop android operating
systems and 3rd party applications. These codes use the same old and outdated cryptographic
tools to encrypt user data. This is an old trick to give the user a confidence level about their
data privacy and protection mechanism. However, a bad data encryption method is equal to
not encrypting at all. Running exploitation tools, security vulnerabilities in the data
encryption methods applied in the android operating system and 3rd party application renders
the encryption easy to crack by the attackers and are only meant to give the user a false sense
of data encryption and society.
1.2.3: Authentication.
For years, mobile devices use the hardware identifies such as IMEI numbers and
MAC addresses to authenticate the user during connections. On the hardware layer of the
mobile device, these authentication values cannot be modified or edited. However, a
vulnerability in the authentication process allow the values to be modified on the software
level. The control of the mobile device identifiers on the software level exposes the user to
threats such as unauthorized data access and eavesdropping by the man-in-the-middle in
established communications. Android is the most used and widely accepted operating system
with thousands of companies use the platform to produce and run their mobile devices such
as smartphones, smart televisions, portable routers and other physical entities connected to
the Internet of Things. Android is an open source project meaning that different users of the
platform can edit and use it to suit their business or personal needs and objectives in
performing different functions and delivery of services.
1.2.4. Vulnerability in the implicit intent in the Android’s Inter Process Communication.
techniques while saving important data on their device’s SD card either in the internal or the
external memory. Additionally, the average user, who make the large percent of mobile
device users, do not know the best practices in sensitive client data storage mechanisms. In
such circumstances, the user stores their private data such as emails, addresses, account
numbers, identification pin codes, registration numbers and passwords within data files that
are not encrypted and are easy to retrieve such as app manifests, XML files, log files and
SQLite databases.
1.2.2: Poor quality and inefficient data encryption tools.
Developers use the same codes to set up, design and develop android operating
systems and 3rd party applications. These codes use the same old and outdated cryptographic
tools to encrypt user data. This is an old trick to give the user a confidence level about their
data privacy and protection mechanism. However, a bad data encryption method is equal to
not encrypting at all. Running exploitation tools, security vulnerabilities in the data
encryption methods applied in the android operating system and 3rd party application renders
the encryption easy to crack by the attackers and are only meant to give the user a false sense
of data encryption and society.
1.2.3: Authentication.
For years, mobile devices use the hardware identifies such as IMEI numbers and
MAC addresses to authenticate the user during connections. On the hardware layer of the
mobile device, these authentication values cannot be modified or edited. However, a
vulnerability in the authentication process allow the values to be modified on the software
level. The control of the mobile device identifiers on the software level exposes the user to
threats such as unauthorized data access and eavesdropping by the man-in-the-middle in
established communications. Android is the most used and widely accepted operating system
with thousands of companies use the platform to produce and run their mobile devices such
as smartphones, smart televisions, portable routers and other physical entities connected to
the Internet of Things. Android is an open source project meaning that different users of the
platform can edit and use it to suit their business or personal needs and objectives in
performing different functions and delivery of services.
1.2.4. Vulnerability in the implicit intent in the Android’s Inter Process Communication.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Mobile devices running on android platform acquire stability and smooth
functionality due to application of the internal communication mechanisms that operate on
the ability of the applications to send intents to each other in form of explicit and implicit
intents. Intents are used by the applications to execute commands in to other apps to provide
services such as data. A vulnerability in the implicit intent allow any app to initiate a process
or service in another app without specifying the apps allowed to send such intents. Intents can
therefore be send by a malicious third party app and initiate a process such as data collection,
device control and trigger commands such as denial of service and compromise user privacy.
1.2.5. transport layer security vulnerabilities.
The transport layer security protocol and the HTTPS protocols are used in the mobile
device web browsing and application that require wireless or wired connection to the server.
These security protocols provide encryption to the transport layer during communication to
prevent man-in-the-middle attacks. In the development of the transport layer protocols,
compression was allowed during encryption to reduce bandwidth, reduce data loss and
improve security. This new development enabled attacker exploit a vulnerability in the
compression protocol in Compression Ratio Info-leak Made Easy attacks in TSL protocols
and Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext attacks
on HTTP connections. CRIME and BREACH attacks on the transport layer utilize on the
security vulnerability in the security protocol to inject characters derived from the cookies
generated by the server and thus perform man-in-the-middle attacks.
functionality due to application of the internal communication mechanisms that operate on
the ability of the applications to send intents to each other in form of explicit and implicit
intents. Intents are used by the applications to execute commands in to other apps to provide
services such as data. A vulnerability in the implicit intent allow any app to initiate a process
or service in another app without specifying the apps allowed to send such intents. Intents can
therefore be send by a malicious third party app and initiate a process such as data collection,
device control and trigger commands such as denial of service and compromise user privacy.
1.2.5. transport layer security vulnerabilities.
The transport layer security protocol and the HTTPS protocols are used in the mobile
device web browsing and application that require wireless or wired connection to the server.
These security protocols provide encryption to the transport layer during communication to
prevent man-in-the-middle attacks. In the development of the transport layer protocols,
compression was allowed during encryption to reduce bandwidth, reduce data loss and
improve security. This new development enabled attacker exploit a vulnerability in the
compression protocol in Compression Ratio Info-leak Made Easy attacks in TSL protocols
and Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext attacks
on HTTP connections. CRIME and BREACH attacks on the transport layer utilize on the
security vulnerability in the security protocol to inject characters derived from the cookies
generated by the server and thus perform man-in-the-middle attacks.
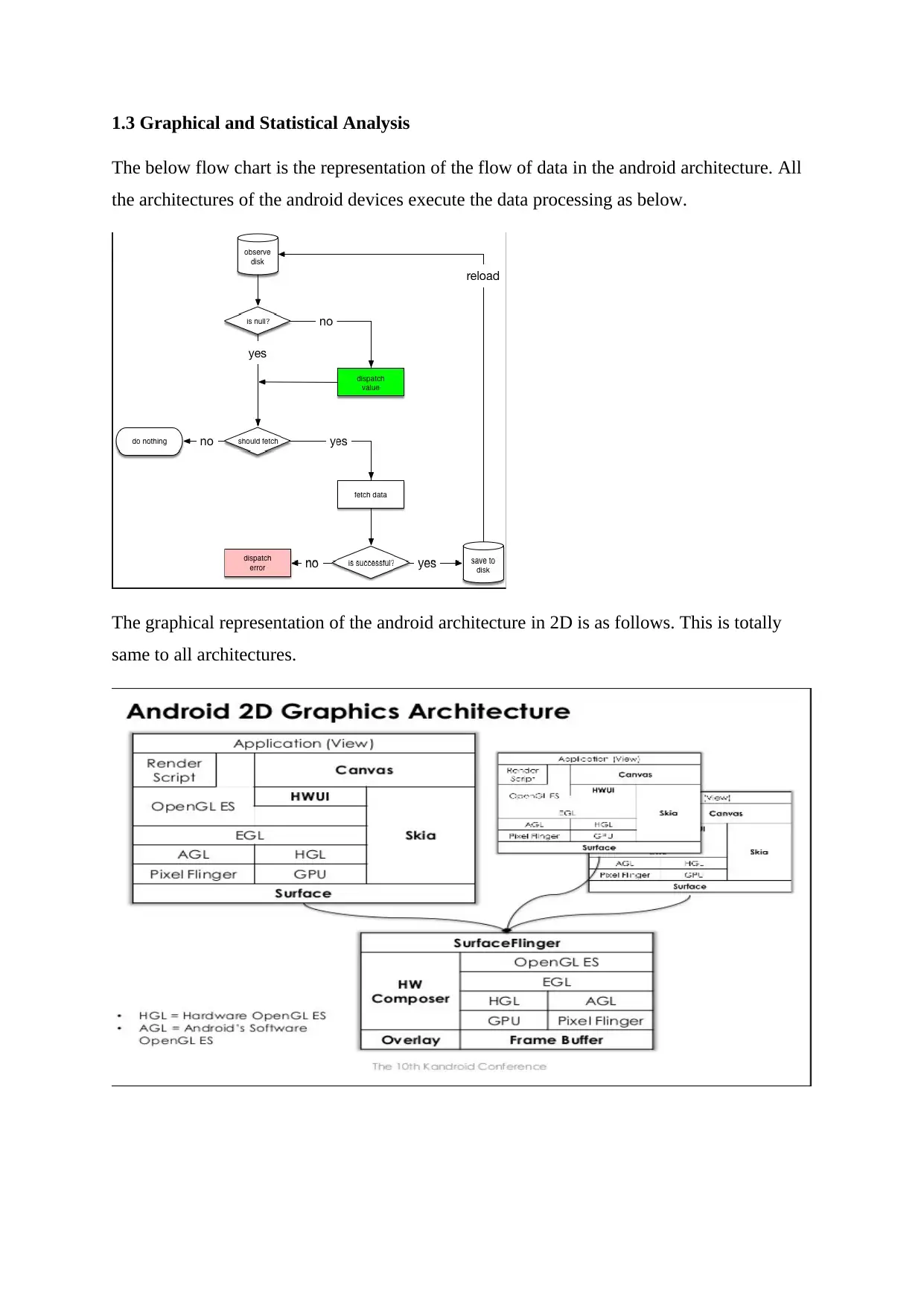
1.3 Graphical and Statistical Analysis
The below flow chart is the representation of the flow of data in the android architecture. All
the architectures of the android devices execute the data processing as below.
The graphical representation of the android architecture in 2D is as follows. This is totally
same to all architectures.
The below flow chart is the representation of the flow of data in the android architecture. All
the architectures of the android devices execute the data processing as below.
The graphical representation of the android architecture in 2D is as follows. This is totally
same to all architectures.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





