Comprehensive Literature Review: Mobile Security and Privacy Analysis
VerifiedAdded on 2024/05/30
|20
|3334
|285
Literature Review
AI Summary
This assignment presents a literature review focused on mobile security and privacy, examining relevant research papers to identify key issues and challenges. The review begins with a broad scan of available literature, narrowing down to a focused review of selected papers. The core analysis explores reasons for mobile security and privacy concerns, including advancements in technology that have made mobile devices vulnerable to malware and security breaches. It further discusses the importance of mobile security in terms of app security and network security, highlighting the need for robust measures to protect personal and business information. The review also references specific studies and frameworks used to understand mobile security threats, such as the use of storyboards to illustrate mobile security hacks. The assignment concludes with a final outline of the literature review chapter, providing a structured overview of the topics covered. Desklib offers a platform to access this and many more solved assignments.

Assignment 2 – Literature Review
By
………..
Student Id:
Submitted to:
…………..
1
By
………..
Student Id:
Submitted to:
…………..
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Chapter 1 Literature Review............................................................................................................3
1.1 Broad Scan.............................................................................................................................4
1.1.1 Research journal..............................................................................................................4
1.1.2 Filing system...................................................................................................................5
1.1.3 Bibliographic file from broad scan..................................................................................6
1.2 Focused Review.....................................................................................................................8
1.2.1 Updated Filing System....................................................................................................9
1.2.2 Updated bibliographic file from focused review...........................................................10
1.3 Reasons of Mobile security and privacy..............................................................................11
1.3.1 Background...................................................................................................................12
1.3.2 Framework and Methods...............................................................................................12
1.3.3 Overview:......................................................................................................................13
1.3.4 Discussion.....................................................................................................................14
1.4 Importance of mobile security and privacy..........................................................................15
1.4.1 Security in terms of Apps..............................................................................................15
1.4.2 Network security:..........................................................................................................15
1.4.3 Conclusion.....................................................................................................................15
1.5 Final Outline of the Literature review Chapter....................................................................16
1.6 Introduction..........................................................................................................................17
2
Chapter 1 Literature Review............................................................................................................3
1.1 Broad Scan.............................................................................................................................4
1.1.1 Research journal..............................................................................................................4
1.1.2 Filing system...................................................................................................................5
1.1.3 Bibliographic file from broad scan..................................................................................6
1.2 Focused Review.....................................................................................................................8
1.2.1 Updated Filing System....................................................................................................9
1.2.2 Updated bibliographic file from focused review...........................................................10
1.3 Reasons of Mobile security and privacy..............................................................................11
1.3.1 Background...................................................................................................................12
1.3.2 Framework and Methods...............................................................................................12
1.3.3 Overview:......................................................................................................................13
1.3.4 Discussion.....................................................................................................................14
1.4 Importance of mobile security and privacy..........................................................................15
1.4.1 Security in terms of Apps..............................................................................................15
1.4.2 Network security:..........................................................................................................15
1.4.3 Conclusion.....................................................................................................................15
1.5 Final Outline of the Literature review Chapter....................................................................16
1.6 Introduction..........................................................................................................................17
2
List of References..........................................................................................................................18
3
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Chapter 1 Literature Review
This assignment is based on the literature review on the specific topic which is called mobile
security and privacy. Herein in this, there is a review of the two papers which are based on the
topic. I am selecting the two papers wherein the first paper shows the issues in the mobile
security and privacy while the second paper shows the importance of mobile security and privacy
This helps in the effective analysis of the facts and the understanding regarding the increased
technology and the importance related to the mobile security. The stages which are followed by
me are provided thereunder:
Section 1.1 is a part of the wider scan wherein there is involvement of the research regarding the
collection of the papers and then marking it as a bibliography. Section 1.2 is considered to be an
approach based study wherein there is a selection of the some of the best paper used in the
assignment. After this stage, there is a rearrangement of the bibliography. The next phases which
are 1.3 and 1.4 are related to the literature review wherein there is a study and analysis of the
best two papers. Section 1.4 provides the discussion of the plan made while section1.6 provides
the subject outline.
4
This assignment is based on the literature review on the specific topic which is called mobile
security and privacy. Herein in this, there is a review of the two papers which are based on the
topic. I am selecting the two papers wherein the first paper shows the issues in the mobile
security and privacy while the second paper shows the importance of mobile security and privacy
This helps in the effective analysis of the facts and the understanding regarding the increased
technology and the importance related to the mobile security. The stages which are followed by
me are provided thereunder:
Section 1.1 is a part of the wider scan wherein there is involvement of the research regarding the
collection of the papers and then marking it as a bibliography. Section 1.2 is considered to be an
approach based study wherein there is a selection of the some of the best paper used in the
assignment. After this stage, there is a rearrangement of the bibliography. The next phases which
are 1.3 and 1.4 are related to the literature review wherein there is a study and analysis of the
best two papers. Section 1.4 provides the discussion of the plan made while section1.6 provides
the subject outline.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1.1 Broad Scan
In this scan, there is an effective nomination of the subject and the topic is examined on the
internet with the varied keywords. The platform which is used by me as a basis is Scholar, IEEE.
There is an election of the first 20 papers at this stage.
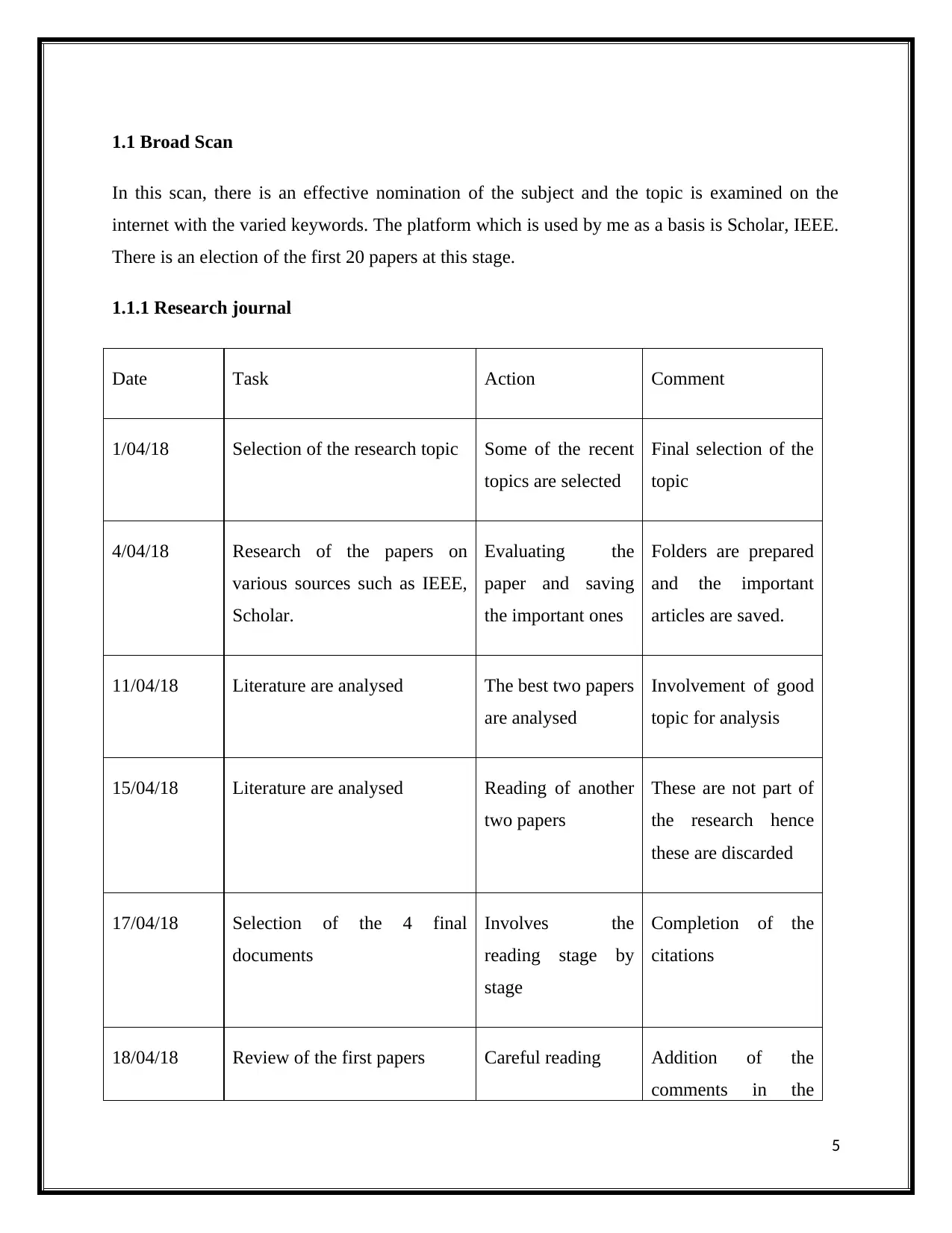
1.1.1 Research journal
Date Task Action Comment
1/04/18 Selection of the research topic Some of the recent
topics are selected
Final selection of the
topic
4/04/18 Research of the papers on
various sources such as IEEE,
Scholar.
Evaluating the
paper and saving
the important ones
Folders are prepared
and the important
articles are saved.
11/04/18 Literature are analysed The best two papers
are analysed
Involvement of good
topic for analysis
15/04/18 Literature are analysed Reading of another
two papers
These are not part of
the research hence
these are discarded
17/04/18 Selection of the 4 final
documents
Involves the
reading stage by
stage
Completion of the
citations
18/04/18 Review of the first papers Careful reading Addition of the
comments in the
5
In this scan, there is an effective nomination of the subject and the topic is examined on the
internet with the varied keywords. The platform which is used by me as a basis is Scholar, IEEE.
There is an election of the first 20 papers at this stage.
1.1.1 Research journal
Date Task Action Comment
1/04/18 Selection of the research topic Some of the recent
topics are selected
Final selection of the
topic
4/04/18 Research of the papers on
various sources such as IEEE,
Scholar.
Evaluating the
paper and saving
the important ones
Folders are prepared
and the important
articles are saved.
11/04/18 Literature are analysed The best two papers
are analysed
Involvement of good
topic for analysis
15/04/18 Literature are analysed Reading of another
two papers
These are not part of
the research hence
these are discarded
17/04/18 Selection of the 4 final
documents
Involves the
reading stage by
stage
Completion of the
citations
18/04/18 Review of the first papers Careful reading Addition of the
comments in the
5
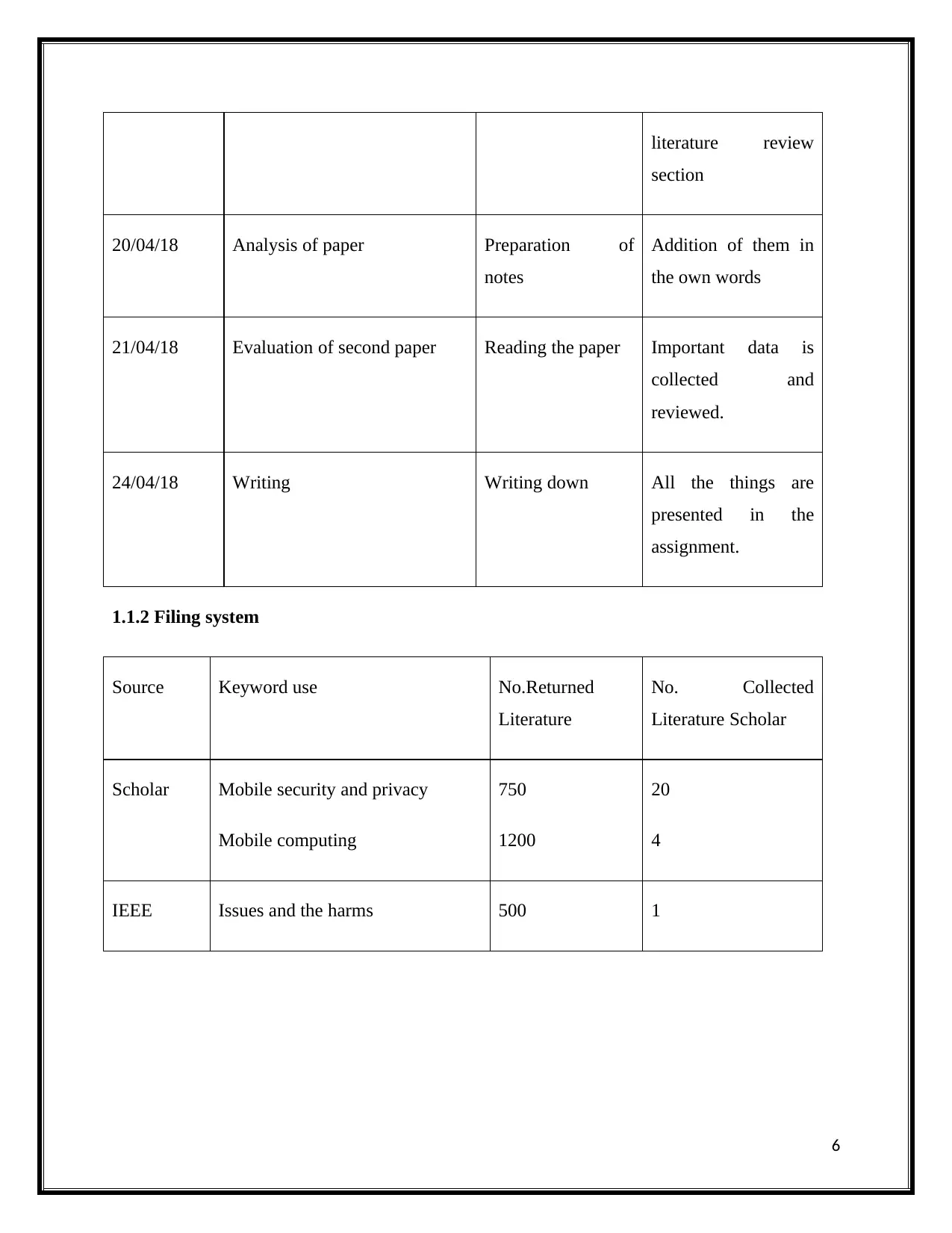
literature review
section
20/04/18 Analysis of paper Preparation of
notes
Addition of them in
the own words
21/04/18 Evaluation of second paper Reading the paper Important data is
collected and
reviewed.
24/04/18 Writing Writing down All the things are
presented in the
assignment.
1.1.2 Filing system
Source Keyword use No.Returned
Literature
No. Collected
Literature Scholar
Scholar Mobile security and privacy
Mobile computing
750
1200
20
4
IEEE Issues and the harms 500 1
6
section
20/04/18 Analysis of paper Preparation of
notes
Addition of them in
the own words
21/04/18 Evaluation of second paper Reading the paper Important data is
collected and
reviewed.
24/04/18 Writing Writing down All the things are
presented in the
assignment.
1.1.2 Filing system
Source Keyword use No.Returned
Literature
No. Collected
Literature Scholar
Scholar Mobile security and privacy
Mobile computing
750
1200
20
4
IEEE Issues and the harms 500 1
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.1.3 Bibliographic file from broad scan
Agrawal, D. P., & Zeng, Q. A. (2015). Introduction to wireless and mobile systems.
Cengage learning.
Arora, S., Yttri, J., & Nilsen, W. (2014). Privacy and security in mobile health (mHealth)
research. Alcohol research: current reviews, 36(1), 143.
Asrani, P. (2013). Mobile cloud computing. International Journal of Engineering and
Advanced Technology, 2(4), 606-609.
Bergman, N., Stanfield, M., Rouse, J., Scambray, J., Geethakumar, S., Deshmukh, S., ...
& Price, M. (2013). Hacking exposed: Mobile security secrets & solutions. McGraw-Hill.
Chen, W., & Paik, I. (2015). Toward Better Quality of Service Composition Based on a
Global Social Service Network. IEEE Transactions on Parallel and Distributed Systems,
26(5), 1466-1476.
Dehling, T., Gao, F., Schneider, S., & Sunyaev, A. (2015). Exploring the far side of
mobile health: information security and privacy of mobile health apps on iOS and
Android. JMIR mHealth and uHealth, 3(1).
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud
computing: architecture, applications, and approaches. Wireless communications and
mobile computing, 13(18), 1587-1611.
El-Gayar, O., Timsina, P., Nawar, N., & Eid, W. (2013). Mobile applications for diabetes
self-management: status and potential. Journal of diabetes science and technology, 7(1),
247-262.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An
analysis of security issues for cloud computing. Journal of internet services and
applications, 4(1), 5.
Holzinger, A., Schantl, J., Schroettner, M., Seifert, C., & Verspoor, K. (2014).
Biomedical text mining: state-of-the-art, open problems and future challenges. Interactive
Knowledge Discovery and Data Mining in Biomedical Informatics (pp. 271-300).
Springer Berlin Heidelberg.
7
Agrawal, D. P., & Zeng, Q. A. (2015). Introduction to wireless and mobile systems.
Cengage learning.
Arora, S., Yttri, J., & Nilsen, W. (2014). Privacy and security in mobile health (mHealth)
research. Alcohol research: current reviews, 36(1), 143.
Asrani, P. (2013). Mobile cloud computing. International Journal of Engineering and
Advanced Technology, 2(4), 606-609.
Bergman, N., Stanfield, M., Rouse, J., Scambray, J., Geethakumar, S., Deshmukh, S., ...
& Price, M. (2013). Hacking exposed: Mobile security secrets & solutions. McGraw-Hill.
Chen, W., & Paik, I. (2015). Toward Better Quality of Service Composition Based on a
Global Social Service Network. IEEE Transactions on Parallel and Distributed Systems,
26(5), 1466-1476.
Dehling, T., Gao, F., Schneider, S., & Sunyaev, A. (2015). Exploring the far side of
mobile health: information security and privacy of mobile health apps on iOS and
Android. JMIR mHealth and uHealth, 3(1).
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud
computing: architecture, applications, and approaches. Wireless communications and
mobile computing, 13(18), 1587-1611.
El-Gayar, O., Timsina, P., Nawar, N., & Eid, W. (2013). Mobile applications for diabetes
self-management: status and potential. Journal of diabetes science and technology, 7(1),
247-262.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An
analysis of security issues for cloud computing. Journal of internet services and
applications, 4(1), 5.
Holzinger, A., Schantl, J., Schroettner, M., Seifert, C., & Verspoor, K. (2014).
Biomedical text mining: state-of-the-art, open problems and future challenges. Interactive
Knowledge Discovery and Data Mining in Biomedical Informatics (pp. 271-300).
Springer Berlin Heidelberg.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hoog, A. (2011). Android forensics: investigation, analysis and mobile security for
Google Android. Elsevier.
Hoog, A., & Strzempka, K. (2011). iPhone and iOS forensics: Investigation, analysis and
mobile security for Apple iPhone, iPad and iOS devices. Elsevier.
Huang, D., & Wu, H. (2017). Mobile Cloud Computing: Foundations and Service
Models. Morgan Kaufmann.
Kraus, L., (2017). User experience with mobile security and privacy mechanisms.
Radesky, J. S., Kistin, C. J., Zuckerman, B., Nitzberg, K., Gross, J., Kaplan-Sanoff,
M., ... & Silverstein, M. (2014). Patterns of mobile device use by caregivers and children
during meals in fast food restaurants. Pediatrics, peds-2013.
Rodrigues, J. J., De La Torre, I., Fernández, G., & López-Coronado, M. (2013). Analysis
of the security and privacy requirements of cloud-based electronic health records
systems. Journal of medical Internet research, 15(8).
Vylegzhanina, V., Schmidt, D. C., & White, J. (2015, October). Gaps and future
directions in mobile security research. In Proceedings of the 3rd International Workshop
on Mobile Development Lifecycle (pp. 49-50). ACM.
Wallace, S., Clark, M., & White, J. (2012). ‘It's on my iPhone’: attitudes to the use of
mobile computing devices in medical education, a mixed-methods study. BMJ open, 2(4),
e001099.
Zaidi, S.F.A., Shah, M.A., Kamran, M., Javaid, Q. and Zhang, S., (2016). A Survey on
security for smartphone device. IJACSA) International Journal of Advanced Computer
Science and Applications, 7, pp.206-219.
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future
Generation computer systems, 28(3), 583-592.
8
Google Android. Elsevier.
Hoog, A., & Strzempka, K. (2011). iPhone and iOS forensics: Investigation, analysis and
mobile security for Apple iPhone, iPad and iOS devices. Elsevier.
Huang, D., & Wu, H. (2017). Mobile Cloud Computing: Foundations and Service
Models. Morgan Kaufmann.
Kraus, L., (2017). User experience with mobile security and privacy mechanisms.
Radesky, J. S., Kistin, C. J., Zuckerman, B., Nitzberg, K., Gross, J., Kaplan-Sanoff,
M., ... & Silverstein, M. (2014). Patterns of mobile device use by caregivers and children
during meals in fast food restaurants. Pediatrics, peds-2013.
Rodrigues, J. J., De La Torre, I., Fernández, G., & López-Coronado, M. (2013). Analysis
of the security and privacy requirements of cloud-based electronic health records
systems. Journal of medical Internet research, 15(8).
Vylegzhanina, V., Schmidt, D. C., & White, J. (2015, October). Gaps and future
directions in mobile security research. In Proceedings of the 3rd International Workshop
on Mobile Development Lifecycle (pp. 49-50). ACM.
Wallace, S., Clark, M., & White, J. (2012). ‘It's on my iPhone’: attitudes to the use of
mobile computing devices in medical education, a mixed-methods study. BMJ open, 2(4),
e001099.
Zaidi, S.F.A., Shah, M.A., Kamran, M., Javaid, Q. and Zhang, S., (2016). A Survey on
security for smartphone device. IJACSA) International Journal of Advanced Computer
Science and Applications, 7, pp.206-219.
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future
Generation computer systems, 28(3), 583-592.
8

1.2 Focused Review
Herein the research is formulated on the basis of the papers which are selected to complete the
research topics. Herein there are 10 selections among the papers then the papers which are best
for the assignment are selected.
9
Herein the research is formulated on the basis of the papers which are selected to complete the
research topics. Herein there are 10 selections among the papers then the papers which are best
for the assignment are selected.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
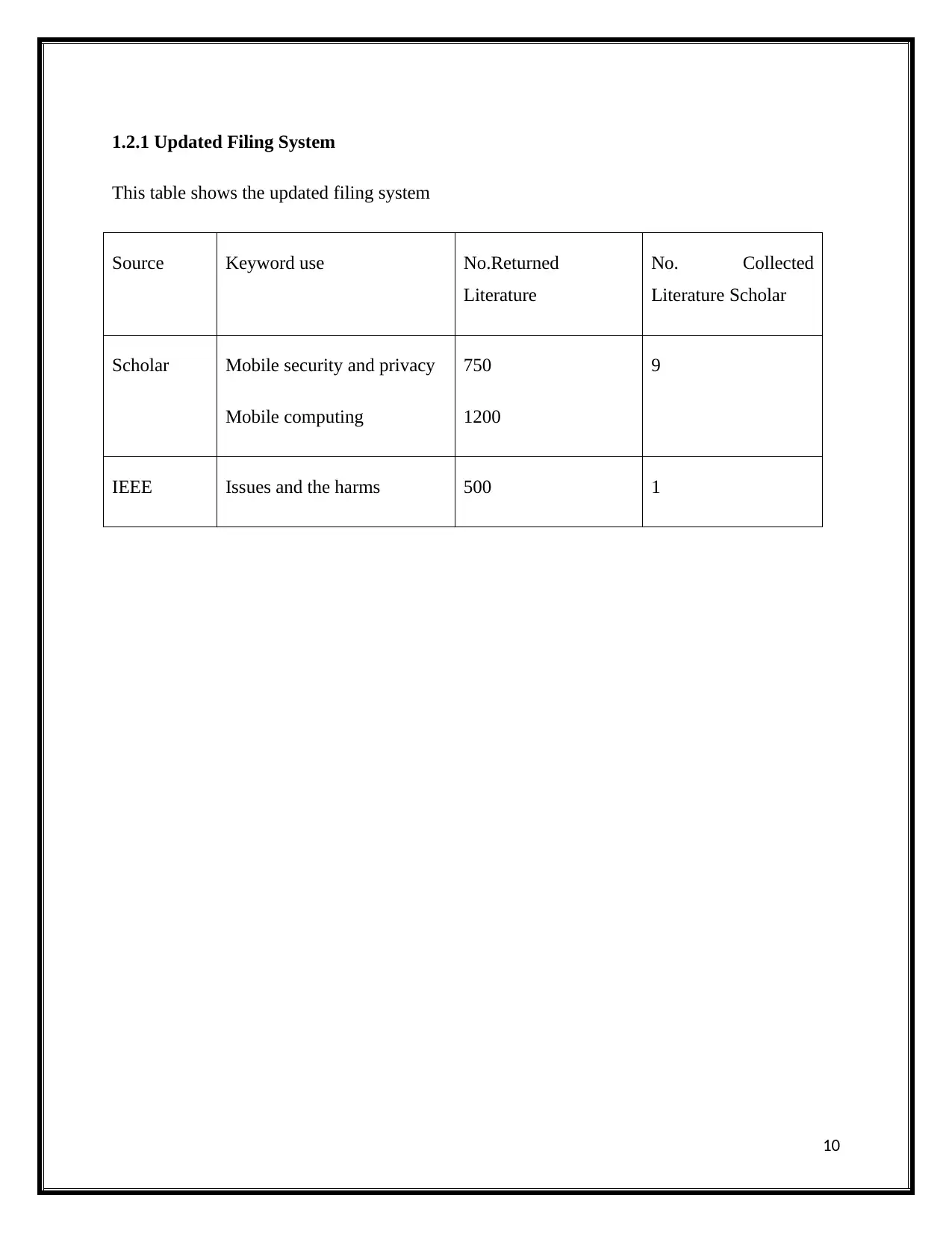
1.2.1 Updated Filing System
This table shows the updated filing system
Source Keyword use No.Returned
Literature
No. Collected
Literature Scholar
Scholar Mobile security and privacy
Mobile computing
750
1200
9
IEEE Issues and the harms 500 1
10
This table shows the updated filing system
Source Keyword use No.Returned
Literature
No. Collected
Literature Scholar
Scholar Mobile security and privacy
Mobile computing
750
1200
9
IEEE Issues and the harms 500 1
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.2.2 Updated bibliographic file from focused review
Arora, S., Yttri, J., & Nilsen, W. (2014). Privacy and security in mobile health (mHealth)
research. Alcohol research: current reviews, 36(1), 143.
Asrani, P. (2013). Mobile cloud computing. International Journal of Engineering and
Advanced Technology, 2(4), 606-609.
Chen, W., & Paik, I. (2015). Toward Better Quality of Service Composition Based on a
Global Social Service Network. IEEE Transactions on Parallel and Distributed Systems,
26(5), 1466-1476.
Dehling, T., Gao, F., Schneider, S., & Sunyaev, A. (2015). Exploring the far side of
mobile health: information security and privacy of mobile health apps on iOS and
Android. JMIR mHealth and uHealth, 3(1).
Kraus, L., (2017). User experience with mobile security and privacy mechanisms.
Kraus, L., (2017). User experience with mobile security and privacy mechanisms.
Radesky, J. S., Kistin, C. J., Zuckerman, B., Nitzberg, K., Gross, J., Kaplan-Sanoff,
M., ... & Silverstein, M. (2014). Patterns of mobile device use by caregivers and children
during meals in fast food restaurants. Pediatrics, peds-2013.
Radesky, J. S., Kistin, C. J., Zuckerman, B., Nitzberg, K., Gross, J., Kaplan-Sanoff,
M., ... & Silverstein, M. (2014). Patterns of mobile device use by caregivers and children
during meals in fast food restaurants. Pediatrics, peds-2013.
Rodrigues, J. J., De La Torre, I., Fernández, G., & López-Coronado, M. (2013). Analysis
of the security and privacy requirements of cloud-based electronic health records
systems. Journal of medical Internet research, 15(8).
Zaidi, S.F.A., Shah, M.A., Kamran, M., Javaid, Q. and Zhang, S., (2016). A Survey on
security for smartphone device. IJACSA) International Journal of Advanced Computer
Science and Applications, 7, pp.206-219.
11
Arora, S., Yttri, J., & Nilsen, W. (2014). Privacy and security in mobile health (mHealth)
research. Alcohol research: current reviews, 36(1), 143.
Asrani, P. (2013). Mobile cloud computing. International Journal of Engineering and
Advanced Technology, 2(4), 606-609.
Chen, W., & Paik, I. (2015). Toward Better Quality of Service Composition Based on a
Global Social Service Network. IEEE Transactions on Parallel and Distributed Systems,
26(5), 1466-1476.
Dehling, T., Gao, F., Schneider, S., & Sunyaev, A. (2015). Exploring the far side of
mobile health: information security and privacy of mobile health apps on iOS and
Android. JMIR mHealth and uHealth, 3(1).
Kraus, L., (2017). User experience with mobile security and privacy mechanisms.
Kraus, L., (2017). User experience with mobile security and privacy mechanisms.
Radesky, J. S., Kistin, C. J., Zuckerman, B., Nitzberg, K., Gross, J., Kaplan-Sanoff,
M., ... & Silverstein, M. (2014). Patterns of mobile device use by caregivers and children
during meals in fast food restaurants. Pediatrics, peds-2013.
Radesky, J. S., Kistin, C. J., Zuckerman, B., Nitzberg, K., Gross, J., Kaplan-Sanoff,
M., ... & Silverstein, M. (2014). Patterns of mobile device use by caregivers and children
during meals in fast food restaurants. Pediatrics, peds-2013.
Rodrigues, J. J., De La Torre, I., Fernández, G., & López-Coronado, M. (2013). Analysis
of the security and privacy requirements of cloud-based electronic health records
systems. Journal of medical Internet research, 15(8).
Zaidi, S.F.A., Shah, M.A., Kamran, M., Javaid, Q. and Zhang, S., (2016). A Survey on
security for smartphone device. IJACSA) International Journal of Advanced Computer
Science and Applications, 7, pp.206-219.
11
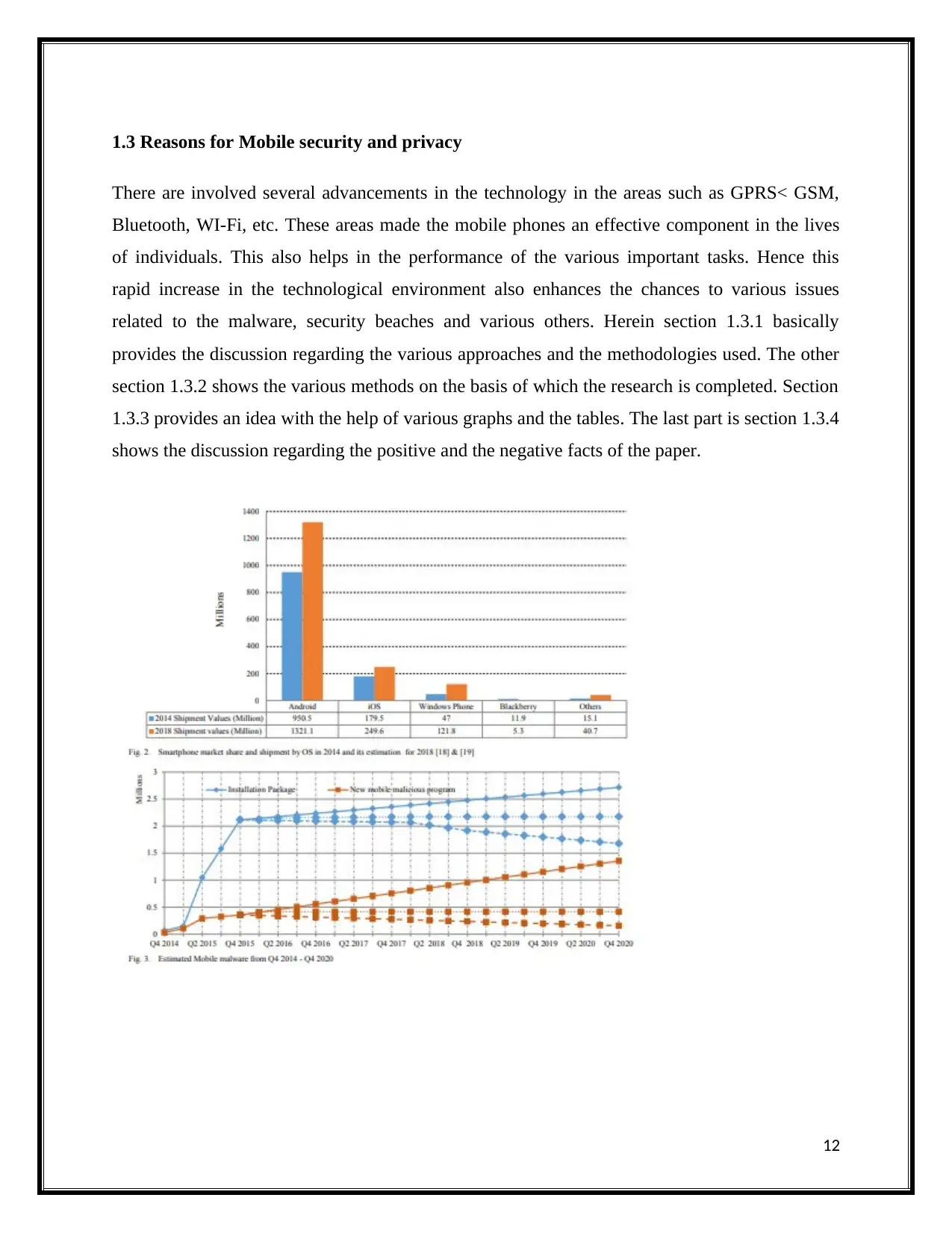
1.3 Reasons for Mobile security and privacy
There are involved several advancements in the technology in the areas such as GPRS< GSM,
Bluetooth, WI-Fi, etc. These areas made the mobile phones an effective component in the lives
of individuals. This also helps in the performance of the various important tasks. Hence this
rapid increase in the technological environment also enhances the chances to various issues
related to the malware, security beaches and various others. Herein section 1.3.1 basically
provides the discussion regarding the various approaches and the methodologies used. The other
section 1.3.2 shows the various methods on the basis of which the research is completed. Section
1.3.3 provides an idea with the help of various graphs and the tables. The last part is section 1.3.4
shows the discussion regarding the positive and the negative facts of the paper.
12
There are involved several advancements in the technology in the areas such as GPRS< GSM,
Bluetooth, WI-Fi, etc. These areas made the mobile phones an effective component in the lives
of individuals. This also helps in the performance of the various important tasks. Hence this
rapid increase in the technological environment also enhances the chances to various issues
related to the malware, security beaches and various others. Herein section 1.3.1 basically
provides the discussion regarding the various approaches and the methodologies used. The other
section 1.3.2 shows the various methods on the basis of which the research is completed. Section
1.3.3 provides an idea with the help of various graphs and the tables. The last part is section 1.3.4
shows the discussion regarding the positive and the negative facts of the paper.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





