Network Design Proposal: Mobile Services for Fruit Distribution
VerifiedAdded on 2023/04/23
|18
|4007
|286
Report
AI Summary
This report provides a comprehensive network design proposal for a fresh fruit distribution organization with depots in Leeds, Manchester, Liverpool, and Edinburgh, and headquarters in London. The proposal focuses on improving communication and coordination between depots, inter-depot transfer services, and collection/delivery services. The design incorporates a VPN for secure and cost-effective connectivity, microwave links for depots with limited infrastructure, and video conferencing capabilities for enhanced communication. It also includes a data center design with power backup and a disaster recovery plan with weekly and daily data backups. The report details the IP addressing scheme, maintenance strategies, and an overview of Internet of Things (IoT) technology and its potential applications within the organization. The design prioritizes redundancy, security, and scalability, while considering the advantages and disadvantages of network convergence.

NETWORK AND SECURITY ASSIGNMENT 1
NETWORK & SECURITY ASSIGNMENT
Student Name
Institution Affiliation
Facilitator
Course
Date
NETWORK & SECURITY ASSIGNMENT
Student Name
Institution Affiliation
Facilitator
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND SECURITY ASSIGNMENT 2
ICA COMPONENT 1
INTRODUCTION
The fresh fruit organization in this case study needs to have a network to coordinate all its
operations. This organization distributes fresh fruits. This company aspires to coordinate all the
operations across its depots in Leeds, Manchester, Liverpool, and Edinburgh through a large data
center. According to company needs, it must coordinate all its depots, its inter-depot transfer
services as well as its collection and delivery services. The head offices for this company are
based in London and its depots in the four towns listed above. The company must have a data
center and a disaster recovery plan which will be helpful in case of emergencies. Also, because
not all its depots have limited technologies, the ways to connect some of those depots will be
discussed. This report will, therefore, be based on the implementation of a branched network to
meet the needs of the company (Risso, Nesmachnow and Robledo, 2018, p.600).
OBJECTIVES
Based on the company needs, below are the six major objectives of the network design to be
implemented
Realizing a reliable network design that can interconnect the company depots and head
offices
Realizing remote access to the network by the employees
Implementation of a data center
A disaster recovery plan
IP PBX to facilitate communication among the depots
Video conferencing capabilities among depots
ICA COMPONENT 1
INTRODUCTION
The fresh fruit organization in this case study needs to have a network to coordinate all its
operations. This organization distributes fresh fruits. This company aspires to coordinate all the
operations across its depots in Leeds, Manchester, Liverpool, and Edinburgh through a large data
center. According to company needs, it must coordinate all its depots, its inter-depot transfer
services as well as its collection and delivery services. The head offices for this company are
based in London and its depots in the four towns listed above. The company must have a data
center and a disaster recovery plan which will be helpful in case of emergencies. Also, because
not all its depots have limited technologies, the ways to connect some of those depots will be
discussed. This report will, therefore, be based on the implementation of a branched network to
meet the needs of the company (Risso, Nesmachnow and Robledo, 2018, p.600).
OBJECTIVES
Based on the company needs, below are the six major objectives of the network design to be
implemented
Realizing a reliable network design that can interconnect the company depots and head
offices
Realizing remote access to the network by the employees
Implementation of a data center
A disaster recovery plan
IP PBX to facilitate communication among the depots
Video conferencing capabilities among depots

NETWORK AND SECURITY ASSIGNMENT 3
DESIGN
This section describes both the technical and physical aspects of the proposed network design.
The figure below describes the geographical location of the network to be implemented.
(Yıldız, Karaşan and Yaman, 2018, p.160)
As observed in the above diagram, all the company depots: Leeds, Manchester,
Liverpool, and Edinburgh will be connected to a VPN through the internet. The VPN services
will be outsourced from the local service providers. Some of the reasons behind using the VPN
are: (1) through it, it’s easier to add more sites as the company expands (2) It’s cheaper and
secure (3) it will allow the company employees to remotely connect to the company’s internal
DESIGN
This section describes both the technical and physical aspects of the proposed network design.
The figure below describes the geographical location of the network to be implemented.
(Yıldız, Karaşan and Yaman, 2018, p.160)
As observed in the above diagram, all the company depots: Leeds, Manchester,
Liverpool, and Edinburgh will be connected to a VPN through the internet. The VPN services
will be outsourced from the local service providers. Some of the reasons behind using the VPN
are: (1) through it, it’s easier to add more sites as the company expands (2) It’s cheaper and
secure (3) it will allow the company employees to remotely connect to the company’s internal
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK AND SECURITY ASSIGNMENT 4
network at any place and lastly (4) it can easily allow new depots to be added on the network as
the company grows (Cheruku et al, 2018, p.103).
Since not all depots have wireless connections or wired connections for them to be
directly connected to the VPN, microwaves will be used in such cases to link the depots to the
nearest one where they can then be comfortably connected to the VPN. In order to facilitate
company meetings without necessarily traveling, video conferencing and voice calling
capabilities among the depots will be established. The Head offices in London will be connected
to the depot offices through the global VPN. The design will mainly use Cisco networking
devices for routing and switching. This is because they are trustworthy and the best in the field.
They are sold with warranties; the company gives support after selling their devices, affordable
and durable (Soleimani and Kannan, 2015, p.4000).
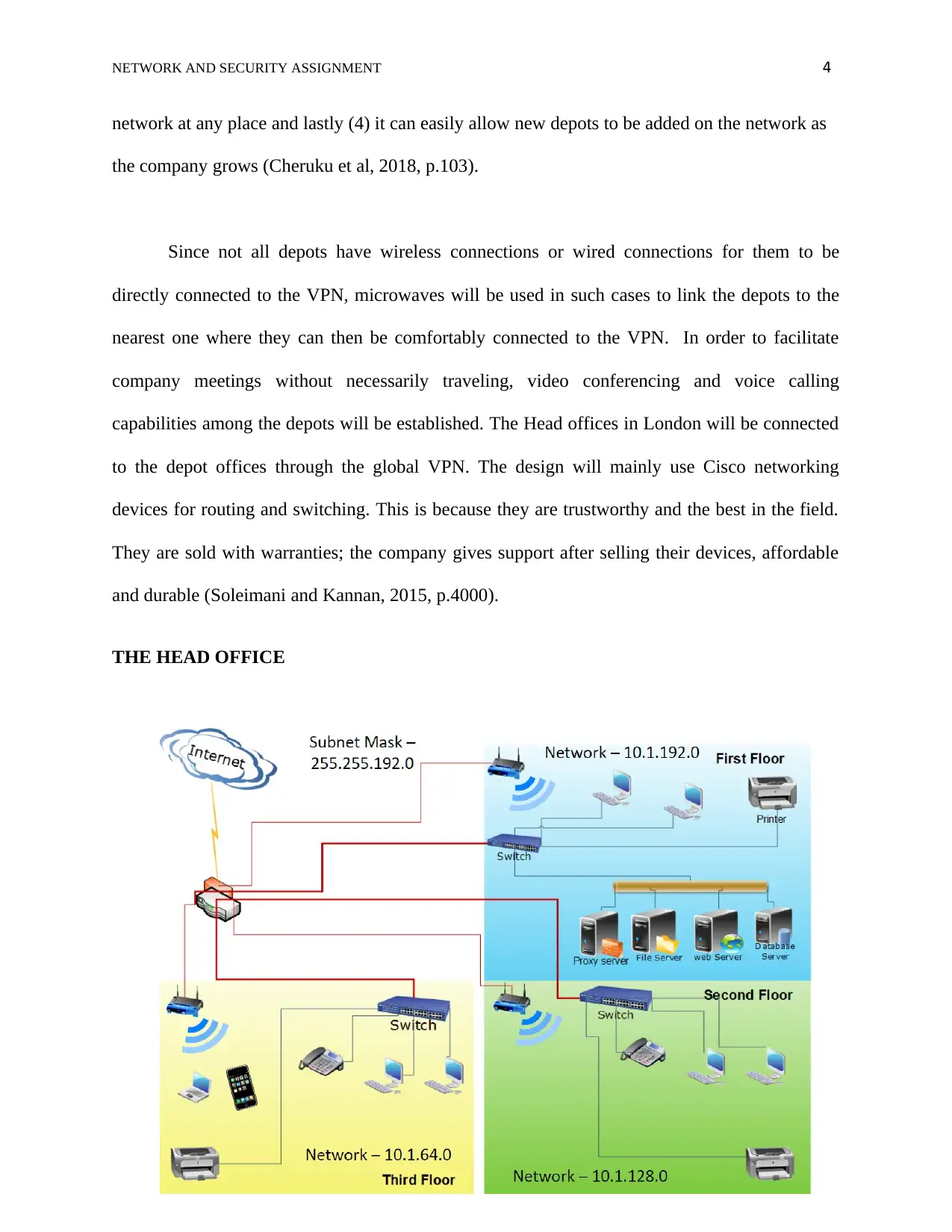
THE HEAD OFFICE
network at any place and lastly (4) it can easily allow new depots to be added on the network as
the company grows (Cheruku et al, 2018, p.103).
Since not all depots have wireless connections or wired connections for them to be
directly connected to the VPN, microwaves will be used in such cases to link the depots to the
nearest one where they can then be comfortably connected to the VPN. In order to facilitate
company meetings without necessarily traveling, video conferencing and voice calling
capabilities among the depots will be established. The Head offices in London will be connected
to the depot offices through the global VPN. The design will mainly use Cisco networking
devices for routing and switching. This is because they are trustworthy and the best in the field.
They are sold with warranties; the company gives support after selling their devices, affordable
and durable (Soleimani and Kannan, 2015, p.4000).
THE HEAD OFFICE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND SECURITY ASSIGNMENT 5
(Mollah et al, 2018, p.400)
In the ground floor of this building, the servers will be installed. The total number of
servers, in this case, is four: Database server, Web Server, File server and Proxy server. Each
floor will have a separated LAN facilitated by a single switch per floor. Also, each floor will
have a dedicated printer and workstations interconnected via a switch. There will also be a Wi-Fi
router on each floor to facilitate internet connection for smartphones and laptops. The building
will be networked using CAT 6 cables and wall plates in each office, room and so on. A single
ASA (Adaptive security appliance) firewall will be used for the purposes of routing and
accessing the VPN. The ground floor will have 30 workstations; the second floor will have 20
workstations; while the third floor will have 40 workstations. Cisco 50 port switch will be used
on each floor in order to make it easy to add more workstations in the future ( Mbuagbaw et al,
2017, p.79).
There will be two more unique buildings with storehouse connected directly to the head
office. The key network features will be incorporated in each floor of the building but the
number of workstations in each floor will be different. The storehouse will have10 workstations
interlinked by a small switch.
DEPOTS AND REGIONAL CENTRES
The major depots for this company are situated in Leeds, Manchester, Liverpool, and
Edinburgh. In case any of these depots doesn’t have wired connections but has WiMAX and 3G,
such a depot will be connected to the internet through a high-speed mobile broadband connection
which then will be used to connect the depot to the VPN. Alternatively, a microwave link
(Mollah et al, 2018, p.400)
In the ground floor of this building, the servers will be installed. The total number of
servers, in this case, is four: Database server, Web Server, File server and Proxy server. Each
floor will have a separated LAN facilitated by a single switch per floor. Also, each floor will
have a dedicated printer and workstations interconnected via a switch. There will also be a Wi-Fi
router on each floor to facilitate internet connection for smartphones and laptops. The building
will be networked using CAT 6 cables and wall plates in each office, room and so on. A single
ASA (Adaptive security appliance) firewall will be used for the purposes of routing and
accessing the VPN. The ground floor will have 30 workstations; the second floor will have 20
workstations; while the third floor will have 40 workstations. Cisco 50 port switch will be used
on each floor in order to make it easy to add more workstations in the future ( Mbuagbaw et al,
2017, p.79).
There will be two more unique buildings with storehouse connected directly to the head
office. The key network features will be incorporated in each floor of the building but the
number of workstations in each floor will be different. The storehouse will have10 workstations
interlinked by a small switch.
DEPOTS AND REGIONAL CENTRES
The major depots for this company are situated in Leeds, Manchester, Liverpool, and
Edinburgh. In case any of these depots doesn’t have wired connections but has WiMAX and 3G,
such a depot will be connected to the internet through a high-speed mobile broadband connection
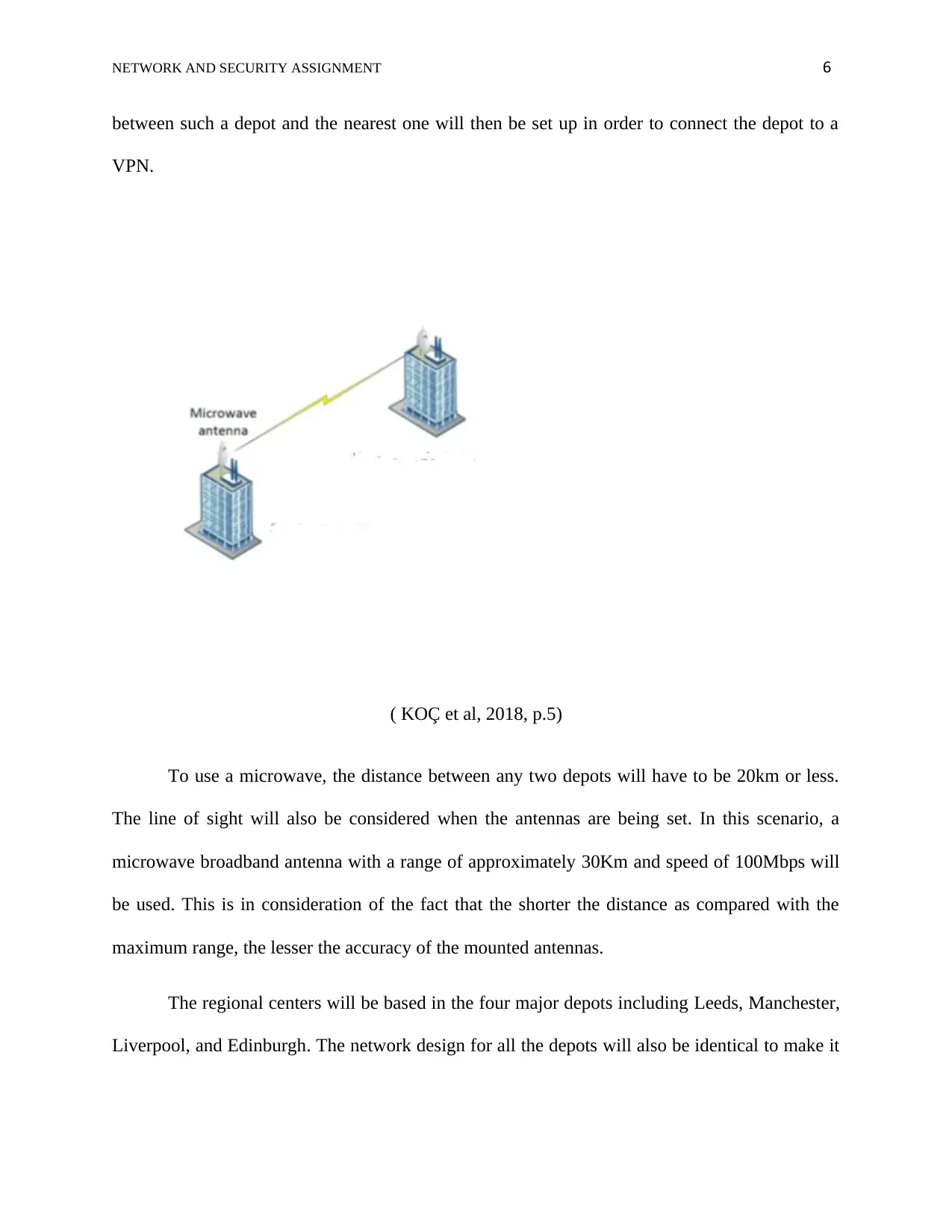
which then will be used to connect the depot to the VPN. Alternatively, a microwave link
NETWORK AND SECURITY ASSIGNMENT 6
between such a depot and the nearest one will then be set up in order to connect the depot to a
VPN.
( KOÇ et al, 2018, p.5)
To use a microwave, the distance between any two depots will have to be 20km or less.
The line of sight will also be considered when the antennas are being set. In this scenario, a
microwave broadband antenna with a range of approximately 30Km and speed of 100Mbps will
be used. This is in consideration of the fact that the shorter the distance as compared with the
maximum range, the lesser the accuracy of the mounted antennas.
The regional centers will be based in the four major depots including Leeds, Manchester,
Liverpool, and Edinburgh. The network design for all the depots will also be identical to make it
between such a depot and the nearest one will then be set up in order to connect the depot to a
VPN.
( KOÇ et al, 2018, p.5)
To use a microwave, the distance between any two depots will have to be 20km or less.
The line of sight will also be considered when the antennas are being set. In this scenario, a
microwave broadband antenna with a range of approximately 30Km and speed of 100Mbps will
be used. This is in consideration of the fact that the shorter the distance as compared with the
maximum range, the lesser the accuracy of the mounted antennas.
The regional centers will be based in the four major depots including Leeds, Manchester,
Liverpool, and Edinburgh. The network design for all the depots will also be identical to make it
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND SECURITY ASSIGNMENT 7
easier to manage. Additionally, just like in the case depots, all regional centers will be equipped
with VoIP and video conferencing capabilities.
The personal computers belonging to top-level managers in the regional centers and the
head offices will be equipped with the Cisco webcams with the ability to integrate with
Communication Servers and Call Manager Express. The webcams will be installed on top level
manager’s computers because not all the employees will require video conferencing facility.
However, in case additional webcams are required they will be purchased. A high-performance
MCU will be used to set up video conferencing to make it easier when it comes to configurations
in the head office to control and access the depots as shown below
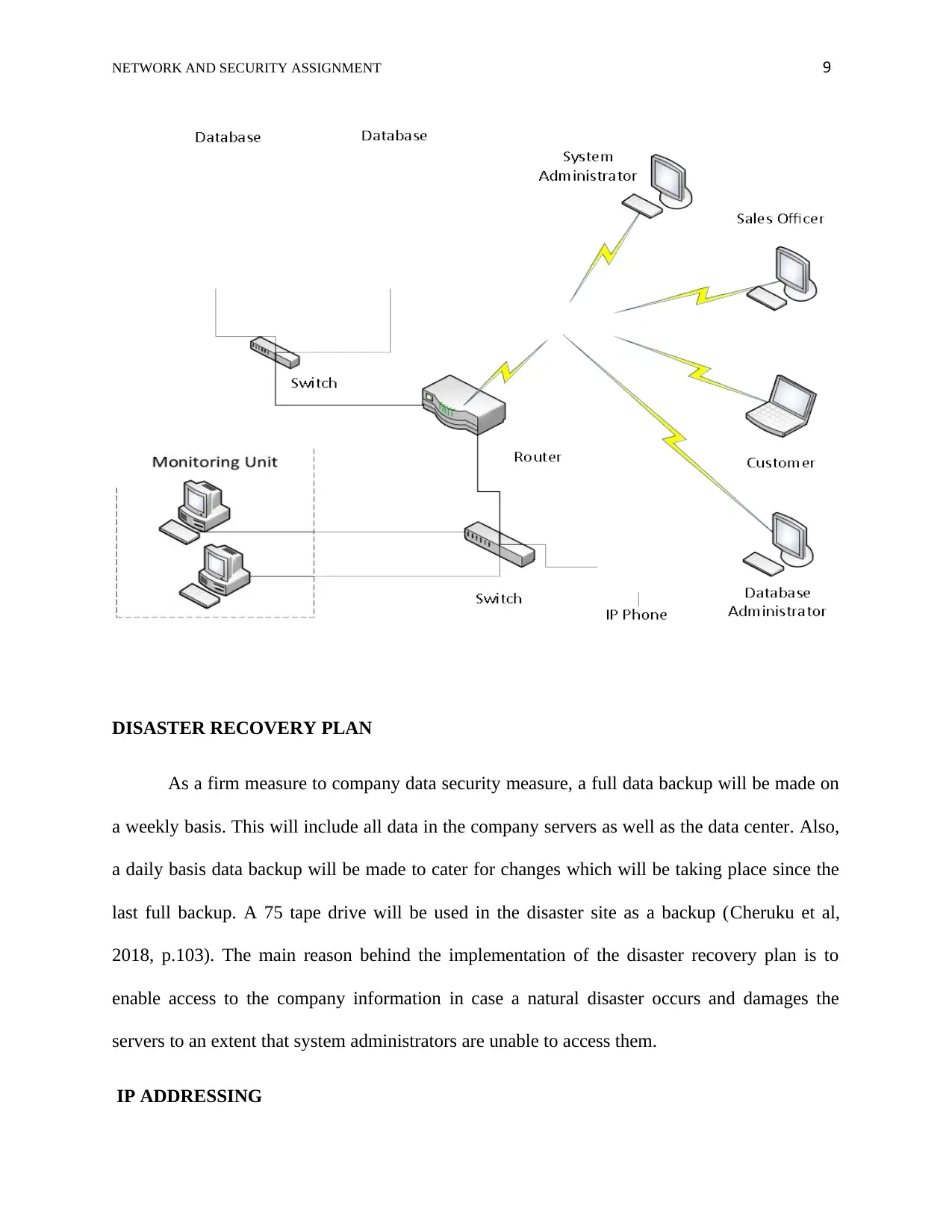
DATA CENTER
easier to manage. Additionally, just like in the case depots, all regional centers will be equipped
with VoIP and video conferencing capabilities.
The personal computers belonging to top-level managers in the regional centers and the
head offices will be equipped with the Cisco webcams with the ability to integrate with
Communication Servers and Call Manager Express. The webcams will be installed on top level
manager’s computers because not all the employees will require video conferencing facility.
However, in case additional webcams are required they will be purchased. A high-performance
MCU will be used to set up video conferencing to make it easier when it comes to configurations
in the head office to control and access the depots as shown below
DATA CENTER
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND SECURITY ASSIGNMENT 8
Establishing a data center is among the objectives of this company. The data center will
be designed as follows: First of all, the data center will have a power backup plan as a measure
of ensuring that the company data is secure. Additionally, all the company workstations either in
the head office or in the depots, the company servers, and other important devices will have
backup batteries to support them for some time in case of power failure. In this case,
CyberPower CP600LCD backup facilities will be used and replaced with a backup generator
whenever power failure persists for a long period (Cheruku et al, 2018, p.103). The Courier
officers, Database Administrators, System administrators will be able to access the database
remotely using VPN client software. On the other hand, customers will also be able to check the
availability of fruits to purchase through the company’s website.
Establishing a data center is among the objectives of this company. The data center will
be designed as follows: First of all, the data center will have a power backup plan as a measure
of ensuring that the company data is secure. Additionally, all the company workstations either in
the head office or in the depots, the company servers, and other important devices will have
backup batteries to support them for some time in case of power failure. In this case,
CyberPower CP600LCD backup facilities will be used and replaced with a backup generator
whenever power failure persists for a long period (Cheruku et al, 2018, p.103). The Courier
officers, Database Administrators, System administrators will be able to access the database
remotely using VPN client software. On the other hand, customers will also be able to check the
availability of fruits to purchase through the company’s website.
NETWORK AND SECURITY ASSIGNMENT 9
DISASTER RECOVERY PLAN
As a firm measure to company data security measure, a full data backup will be made on
a weekly basis. This will include all data in the company servers as well as the data center. Also,
a daily basis data backup will be made to cater for changes which will be taking place since the
last full backup. A 75 tape drive will be used in the disaster site as a backup (Cheruku et al,
2018, p.103). The main reason behind the implementation of the disaster recovery plan is to
enable access to the company information in case a natural disaster occurs and damages the
servers to an extent that system administrators are unable to access them.
IP ADDRESSING
DISASTER RECOVERY PLAN
As a firm measure to company data security measure, a full data backup will be made on
a weekly basis. This will include all data in the company servers as well as the data center. Also,
a daily basis data backup will be made to cater for changes which will be taking place since the
last full backup. A 75 tape drive will be used in the disaster site as a backup (Cheruku et al,
2018, p.103). The main reason behind the implementation of the disaster recovery plan is to
enable access to the company information in case a natural disaster occurs and damages the
servers to an extent that system administrators are unable to access them.
IP ADDRESSING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND SECURITY ASSIGNMENT 10
A private IP addressing scheme within the range of 10.0.0.0/16 will be used in this network
design and which is within the range of a Class A IP address
The Head office in London will be given an IP address range of 10.1.0.0/24. To separate the
LANs inside this network, a VLSM subnetting approach will be used. Below are the LANs on
each floor of the Head office building.
10.1. 00 00 0000.0 – 10.1.0.0 the unused subnet
10.1. 01 00 0000.0 – 10.1.64.0 Third floor
10.1. 10 00 0000.0 – 10.1.128.0 Second floor
10.1. 11 00 0000.0 – 10.1.192.0 First floor
Subnet mask – 255.255.192.0
The IP range to be used for all the routers which will be connected to the VPN is 10.0.10.0/24
while the subnet mask will be 255.255.255.0
Likewise, all the depots, regional centers, disaster recovery site, couriers etc will be using an IP
ranges of 10.2.0.0/24, 10.3.0.0/24 etc.
MAINTENANCE
An inclusive training session will be provided for to all the company IT staff on a day to
day maintenance of company servers and other network equipment. Because troubleshooting
won’t be effective if done by the company’s IT staff, the company may embark on outsourcing
the service from other companies which provide such services on contract bases. The VPN will,
however, be maintained by the service providers while Internet connections will be maintained
by Internet Service Providers.
A private IP addressing scheme within the range of 10.0.0.0/16 will be used in this network
design and which is within the range of a Class A IP address
The Head office in London will be given an IP address range of 10.1.0.0/24. To separate the
LANs inside this network, a VLSM subnetting approach will be used. Below are the LANs on
each floor of the Head office building.
10.1. 00 00 0000.0 – 10.1.0.0 the unused subnet
10.1. 01 00 0000.0 – 10.1.64.0 Third floor
10.1. 10 00 0000.0 – 10.1.128.0 Second floor
10.1. 11 00 0000.0 – 10.1.192.0 First floor
Subnet mask – 255.255.192.0
The IP range to be used for all the routers which will be connected to the VPN is 10.0.10.0/24
while the subnet mask will be 255.255.255.0
Likewise, all the depots, regional centers, disaster recovery site, couriers etc will be using an IP
ranges of 10.2.0.0/24, 10.3.0.0/24 etc.
MAINTENANCE
An inclusive training session will be provided for to all the company IT staff on a day to
day maintenance of company servers and other network equipment. Because troubleshooting
won’t be effective if done by the company’s IT staff, the company may embark on outsourcing
the service from other companies which provide such services on contract bases. The VPN will,
however, be maintained by the service providers while Internet connections will be maintained
by Internet Service Providers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND SECURITY ASSIGNMENT 11
ICA COMONENT 2
Internet of Things (IoT)
Introduction
IoT is an abbreviation for the Internet of Things. It refers to an emerging network of
devices that utilizes the IP addressing technology for internet connectivity and communication
between devices and other internet-based systems. IoT technology has extended internet
connectivity beyond the traditional devices such as laptops, desktops, tablets, and smartphones to
a diverse range of devices that use embedded technology for communication and interaction
purposes with external environments through the Internet. Some of the devices that fall under the
scope of IoT include thermostats, networked security systems, electronic appliances, alarm
clocks, speaker systems, and vending machines (Beyene et al, 2017, p.26). IoT technology has
impacted the world in different ways. For instance, business organizations are currently
leveraging on IoT applications to performing real-time testing using networked cameras,
automate safety measures and to detect customer-product engagement using sensors. This paper
gives a brief overview of IoT technology and its impacts on lifestyle.
Description of the area of research
IoT has increasingly hit the headlines as a hot topic of discussion both in the workplaces
and other sectors. It's a technology that has shown its potential to impact the current lifestyle as
well as how people work. This technology has been engulfed with a lot of complexities but the
paper will stick to the basics. It’s important to understand some few things which have played a
major role in realizing the current trend in the growth of this technology like the wide coverage
of broadband internet. The wide availability of broadband internet has seen the average cost of
ICA COMONENT 2
Internet of Things (IoT)
Introduction
IoT is an abbreviation for the Internet of Things. It refers to an emerging network of
devices that utilizes the IP addressing technology for internet connectivity and communication
between devices and other internet-based systems. IoT technology has extended internet
connectivity beyond the traditional devices such as laptops, desktops, tablets, and smartphones to
a diverse range of devices that use embedded technology for communication and interaction
purposes with external environments through the Internet. Some of the devices that fall under the
scope of IoT include thermostats, networked security systems, electronic appliances, alarm
clocks, speaker systems, and vending machines (Beyene et al, 2017, p.26). IoT technology has
impacted the world in different ways. For instance, business organizations are currently
leveraging on IoT applications to performing real-time testing using networked cameras,
automate safety measures and to detect customer-product engagement using sensors. This paper
gives a brief overview of IoT technology and its impacts on lifestyle.
Description of the area of research
IoT has increasingly hit the headlines as a hot topic of discussion both in the workplaces
and other sectors. It's a technology that has shown its potential to impact the current lifestyle as
well as how people work. This technology has been engulfed with a lot of complexities but the
paper will stick to the basics. It’s important to understand some few things which have played a
major role in realizing the current trend in the growth of this technology like the wide coverage
of broadband internet. The wide availability of broadband internet has seen the average cost of

NETWORK AND SECURITY ASSIGNMENT 12
internet connectivity decrease, the creation of more devices with Wi-Fi capabilities and inbuilt
sensors, a decline in the cost of technology and smartphone penetration has sky-rocketed. All of
these trends have created a “perfect storm” for the IoT (Dan et al, 2015, p.490).
So, the Internet of Things is basically the concept of connecting all the devices with an on
and an off switch to the internet. This entails all devices from cellphones, headphones, wearable
devices, coffee makers, lamps, washing machines and all other devices which can be thought of.
The technology also applies to other machine components such as jet engines of airplanes and
drillers of oil rigs. As mentioned earlier, if a device has an on and off switch, the chances of it
being used as part of IoT technology are very high (Qian and WANG, 2012, p.26).
According to the technology innovators, any device that can be connected will be
connected and this will have huge impacts on people’s lifestyle. The burning question is,
however, why so many devices must be connected and talking to each other? The potential value
for this large network of devices has been demonstrated in various incidences. For instance,
when a person is on his way to a business meeting; the car will be able to access his calendar and
decide on the best route to follow. When the traffic is heavy, the car will be able to send texts to
other members to notify them that the person will be late. Alarm clocks will have the ability to
wake a person at the set time and notify his/her coffee maker to start preparing the coffee.
Offices equipment will be able to detect when running short of resource supply and re-order
more automatically (Watteyne et al, 2016, p.30). Wearable devices used in the workplace will be
in a position to tell when a person is highly active and productive and share the information with
other devices used by the same person.
internet connectivity decrease, the creation of more devices with Wi-Fi capabilities and inbuilt
sensors, a decline in the cost of technology and smartphone penetration has sky-rocketed. All of
these trends have created a “perfect storm” for the IoT (Dan et al, 2015, p.490).
So, the Internet of Things is basically the concept of connecting all the devices with an on
and an off switch to the internet. This entails all devices from cellphones, headphones, wearable
devices, coffee makers, lamps, washing machines and all other devices which can be thought of.
The technology also applies to other machine components such as jet engines of airplanes and
drillers of oil rigs. As mentioned earlier, if a device has an on and off switch, the chances of it
being used as part of IoT technology are very high (Qian and WANG, 2012, p.26).
According to the technology innovators, any device that can be connected will be
connected and this will have huge impacts on people’s lifestyle. The burning question is,
however, why so many devices must be connected and talking to each other? The potential value
for this large network of devices has been demonstrated in various incidences. For instance,
when a person is on his way to a business meeting; the car will be able to access his calendar and
decide on the best route to follow. When the traffic is heavy, the car will be able to send texts to
other members to notify them that the person will be late. Alarm clocks will have the ability to
wake a person at the set time and notify his/her coffee maker to start preparing the coffee.
Offices equipment will be able to detect when running short of resource supply and re-order
more automatically (Watteyne et al, 2016, p.30). Wearable devices used in the workplace will be
in a position to tell when a person is highly active and productive and share the information with
other devices used by the same person.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
