University IT Ethics Essay: Mobile Threats, Spoofing Enterprise Apps
VerifiedAdded on 2022/12/20
|5
|645
|26
Essay
AI Summary
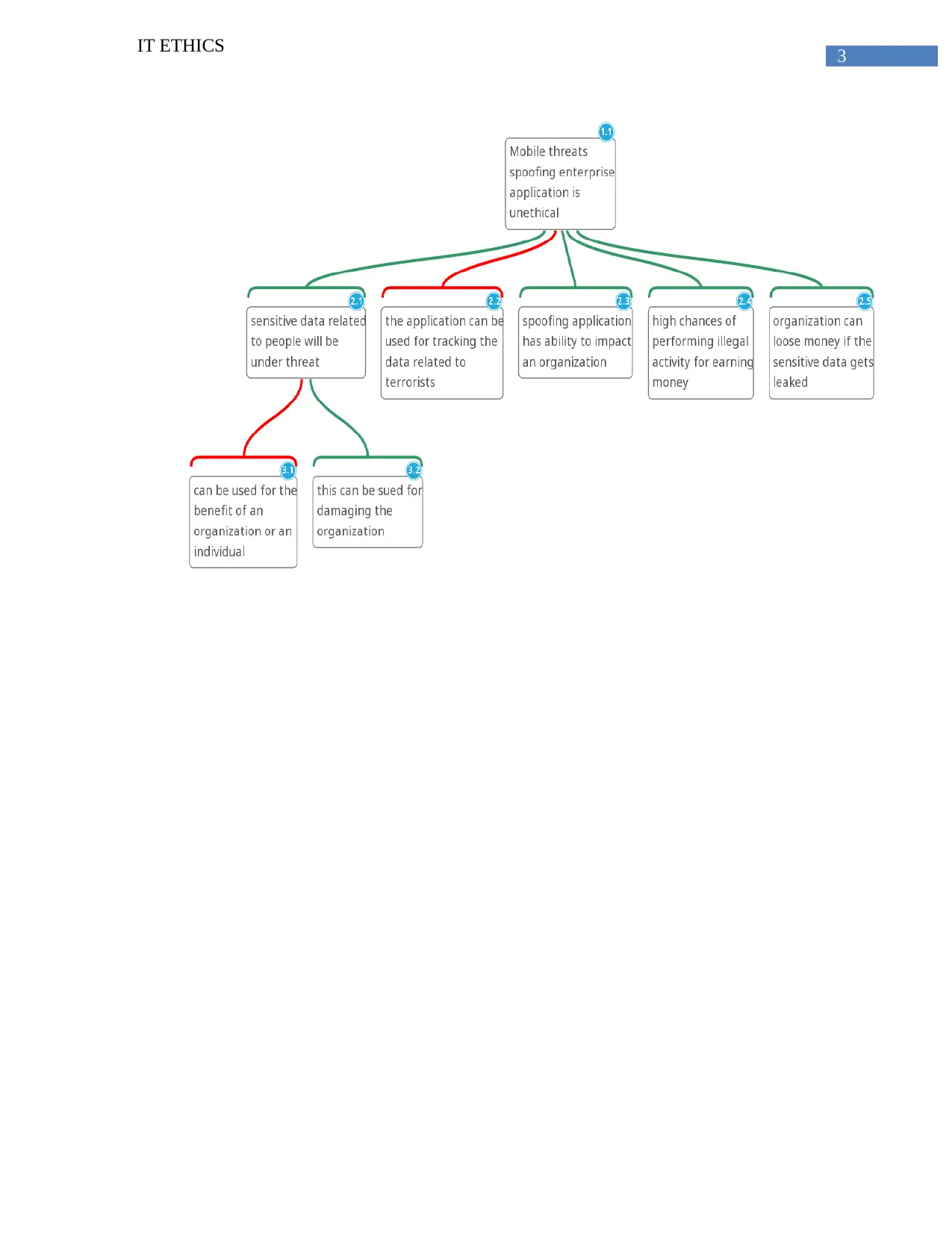
This essay examines the ethical implications of mobile threat spoofing in enterprise applications. It argues that such practices are unethical due to their potential to compromise sensitive user information and facilitate illegal activities. The essay employs four classical ethical theories—utilitarianism, deontology, contract theory, and virtue ethics—to support its stance. Utilitarianism is used to demonstrate that the disadvantages of the application outweigh the benefits, while deontology highlights the inherent wrongness of the actions. The contract theory emphasizes the lack of transparency and informed consent, and virtue ethics focuses on the damage to individuals and organizations. The conclusion is that the use of mobile threat spoofing applications is unethical and should be avoided.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)