ISYS 326: Critical Analysis of Mobile and Wireless Security, 2018
VerifiedAdded on 2023/06/03
|10
|615
|231
Report
AI Summary
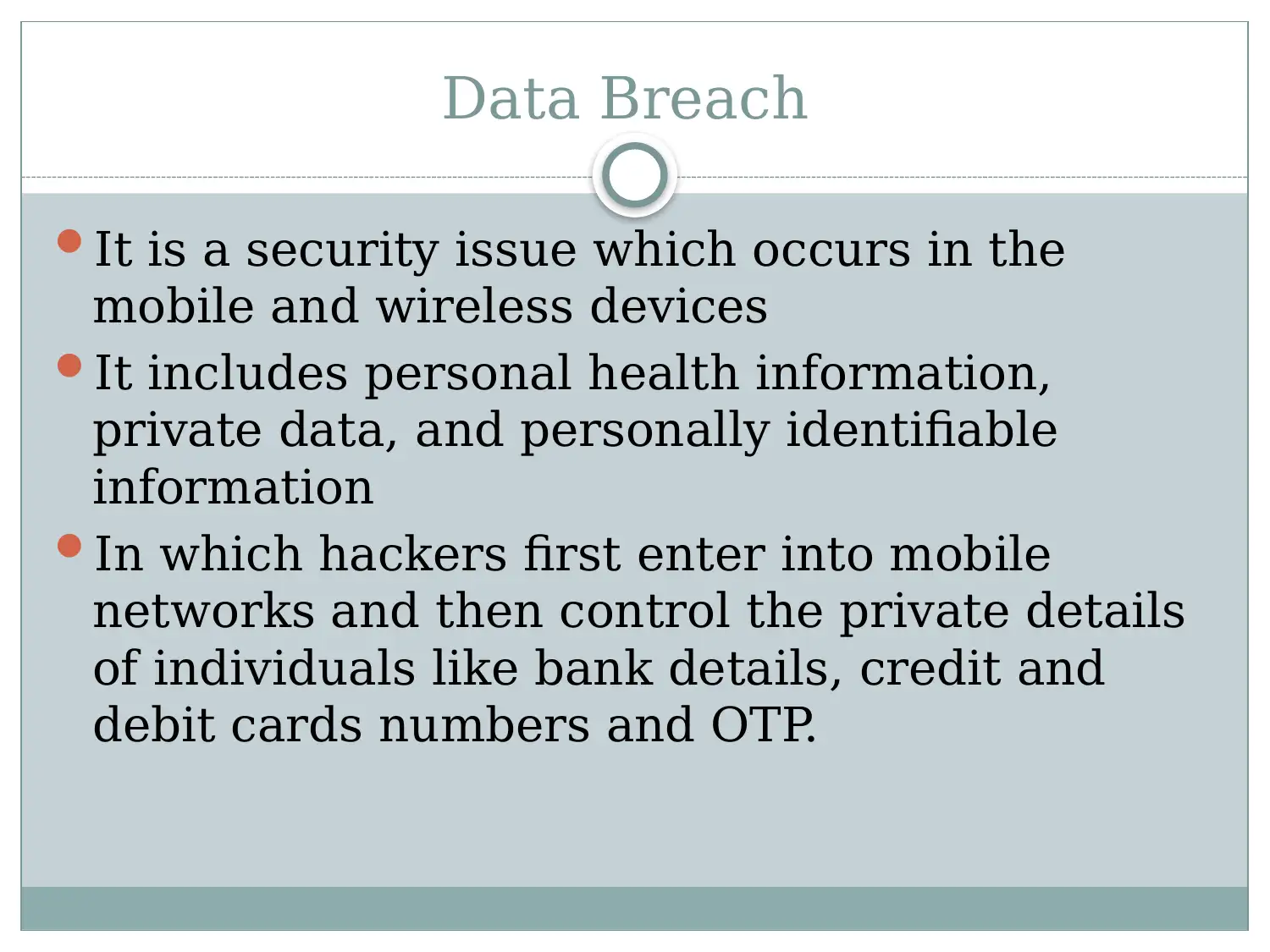
This report provides a comprehensive overview of mobile and wireless security, highlighting the increasing reliance on these technologies and the associated security risks. It identifies key issues such as DOS and DDOS attacks, data breaches, traffic analysis, spoofing, and push/pull attacks. The report details the mechanisms of these attacks and their potential impact on users and organizations. Furthermore, it explores methods and techniques to improve mobile and wireless security, including encryption, cryptography, access control, memory randomization, and robust technologies. The report concludes with recommendations for users to enhance their security posture, such as using authentic websites, regularly updating software, and employing password-based systems. References to relevant research papers are included to support the analysis and recommendations.
1 out of 10













![[object Object]](/_next/static/media/star-bottom.7253800d.svg)