FIT2093 Assignment 1: Analyzing Encryption & Vulnerabilities at Monash
VerifiedAdded on 2023/03/30
|8
|456
|107
Homework Assignment
AI Summary
This document presents a solution to an information security assignment, likely for the FIT2093 course. It covers hybrid encryption methods, including key generation using RSA, and decryption processes. The assignment delves into practical implementation with Java code for key generation and discusses mathematical formulas relevant to ciphertext analysis. Additionally, it addresses vulnerabilities by analyzing corrupted blocks in ciphertext files and attempting plaintext recovery using online converters. The solution provides insights into the practical aspects of encryption and decryption, alongside vulnerability assessment in ciphertext files. Desklib offers more resources for students.

University
Semester
Information Security
Student ID
Student Name
Submission Date
1
Semester
Information Security
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 2.........................................................................................................................................................3
a) Hybrid Encryption Method..........................................................................................................3
b) Decryption Process........................................................................................................................5
c) Mathematical Formula..................................................................................................................7
d) Vulnerability..................................................................................................................................8
2
Task 2.........................................................................................................................................................3
a) Hybrid Encryption Method..........................................................................................................3
b) Decryption Process........................................................................................................................5
c) Mathematical Formula..................................................................................................................7
d) Vulnerability..................................................................................................................................8
2

Task 2
a) Hybrid Encryption Method
package com.mkyong.keypair;
import java.io.File;
import java.io.FileOutputStream;
import java.io.IOException;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.NoSuchAlgorithmException;
import java.security.NoSuchProviderException;
import java.security.PrivateKey;
import java.security.PublicKey;
public class GenerateKeys {
private KeyPairGenerator keyGen;
private KeyPair pair;
private PrivateKey privateKey;
private PublicKey publicKey;
public GenerateKeys(int keylength)
throws NoSuchAlgorithmException, NoSuchProviderException {
this.keyGen = KeyPairGenerator.getInstance("RSA");
this.keyGen.initialize(keylength);
}
public void createKeys() {
this.pair = this.keyGen.generateKeyPair();
this.privateKey = pair.getPrivate();
this.publicKey = pair.getPublic();
}
3
a) Hybrid Encryption Method
package com.mkyong.keypair;
import java.io.File;
import java.io.FileOutputStream;
import java.io.IOException;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.NoSuchAlgorithmException;
import java.security.NoSuchProviderException;
import java.security.PrivateKey;
import java.security.PublicKey;
public class GenerateKeys {
private KeyPairGenerator keyGen;
private KeyPair pair;
private PrivateKey privateKey;
private PublicKey publicKey;
public GenerateKeys(int keylength)
throws NoSuchAlgorithmException, NoSuchProviderException {
this.keyGen = KeyPairGenerator.getInstance("RSA");
this.keyGen.initialize(keylength);
}
public void createKeys() {
this.pair = this.keyGen.generateKeyPair();
this.privateKey = pair.getPrivate();
this.publicKey = pair.getPublic();
}
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

public PrivateKey getPrivateKey() {
return this.privateKey;
}
public PublicKey getPublicKey() {
return this.publicKey;
}
public void writeToFile(String path, byte[] key) throws IOException {
File f = new File(path);
f.getParentFile().mkdirs();
FileOutputStream fos = new FileOutputStream(f);
fos.write(key);
fos.flush();
fos.close();
}
public static void main(String[] args)
throws NoSuchAlgorithmException, NoSuchProviderException, IOException {
GenerateKeys gk_Alice;
GenerateKeys gk_Bob;
gk_Alice = new GenerateKeys(1024);
gk_Alice.createKeys();
gk_Alice.writeToFile("KeyPair/publicKey_Alice", gk_Alice.getPublicKey().getEncoded());
gk_Alice.writeToFile("KeyPair/privateKey_Alice", gk_Alice.getPrivateKey().getEncoded());
gk_Bob = new GenerateKeys(1024);
gk_Bob.createKeys();
gk_Bob.writeToFile("KeyPair/publicKey_Bob", gk_Bob.getPublicKey().getEncoded());
gk_Bob.writeToFile("KeyPair/privateKey_Bob", gk_Bob.getPrivateKey().getEncoded());
}
}
4
return this.privateKey;
}
public PublicKey getPublicKey() {
return this.publicKey;
}
public void writeToFile(String path, byte[] key) throws IOException {
File f = new File(path);
f.getParentFile().mkdirs();
FileOutputStream fos = new FileOutputStream(f);
fos.write(key);
fos.flush();
fos.close();
}
public static void main(String[] args)
throws NoSuchAlgorithmException, NoSuchProviderException, IOException {
GenerateKeys gk_Alice;
GenerateKeys gk_Bob;
gk_Alice = new GenerateKeys(1024);
gk_Alice.createKeys();
gk_Alice.writeToFile("KeyPair/publicKey_Alice", gk_Alice.getPublicKey().getEncoded());
gk_Alice.writeToFile("KeyPair/privateKey_Alice", gk_Alice.getPrivateKey().getEncoded());
gk_Bob = new GenerateKeys(1024);
gk_Bob.createKeys();
gk_Bob.writeToFile("KeyPair/publicKey_Bob", gk_Bob.getPublicKey().getEncoded());
gk_Bob.writeToFile("KeyPair/privateKey_Bob", gk_Bob.getPrivateKey().getEncoded());
}
}
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

b) Decryption Process
-----BEGIN PGP PRIVATE KEY BLOCK-----
lQPGBFy4DpABCADH4G4mNU1EpuL7xfNF9Cy7rjyoGRAdIe5LVhwHRvQG9W8zT483
b1AsBB/K5YmIgpmjFOBQ1oqT2PY73aUNDOBMVSWmnc5QkPryf4OOEpcw/JrK1r/9
7kthCS5JXbGIjhXsfI79hLQO3jYa6vRlin33vWriXCzXawcUe9scyrAe20GEW2+g
cn43VGseNhsTT9Jv+M6rfzCSBP+1fo3cEYM0qDXgiteiHNIJne9XlbsZuLxp3IEE
3sPkwMBYGqmHfM6MiwfhvtkJEUWpymrinmuKg+rqdj9e1T4nC6nVV862v+RekNar
ozXX+C0xcCI/6oiTZM9qnLSYPrKBMreqMs7lABEBAAH+BwMCywYWui00qzHxwz5c
4ia+jz819Kw+BSkrnmdYCb4cgsbnmKIAw2lUOoon2bktqBLZE6b8/D6d//5vH6t9
dhTR889nnqznYMLxPplcFT7D47vORy3H+3+gt7ygi3iEXx9PDSNv9zNNsl8ZREvV
JXFksxtUoibeSm+D4vvRLbY3h4oHgYTXm2vNfyOYBibiPEJT47cv1JnZVWtOc4jF
iZHYsHvtKtO+qYjqeu1z8qtiyPgEBWKJCqGNnTT+5JSPejva91Y1kDZ1Vgbuvvm9
0/kCJw2DtenhXeIWEWNDbKP3Demh9IF/Js77ySX0qL3tqAbtW3Wm+lXvrSVEXPgG
t8XWCO4F6Lf6J7vZ/svM4R8VBrugmBU/KN+W79DADrKMbGTrxLa4Sgad0o3sR0E9
Q9f2X/4RLuwOEun7//IH8dZ2ox8i9vdGtpbty5CgCES9Snv40Y2zp5w04BrV0mYS
TbctBM8QO040qboHfyyRYAMAmzWO6kaQ5mAbB3ggBYExxNnVP51WhK4FNFSPEHDg
W/rX2wqP9UeO8XBqunutu8F5HaVxYtk8Ds4R/ikCI0uTTvnSgddUc/Tu/7AAwgjl
u9gVHj8WGSLvPOpCY/Jui7Id+v9EY9ePUq/ZE+rpEEoQk3jZTgvX1qgNywt2/jka
k07DScEDCT0aghNSR4x56tCzfI1OqH65omOY4VsbSxIHhoFZqZvt0hW+ORixbW6J
Mx35QQan+X1R5wXiO5zJ+BGP8sfvFxt/SGzLt5fDKlk34ZLdGLpsfNItVunbJh0K
WzWSy4EW4TnXms40XAJWZ+HcaOEN7x7naB2/5zuutcnUWCW8NFtUQfm1gRRwysIE
ZVhMP+DFnJQYfCWchDvSHYRxahcIinRatuuZTNygh0VEeEY8x5FTlooOu3QjkQAa
7Ufi25pPOLvatBdCb2JieSA8Ym9iQGZpdDIwOTMuZWR1PokBTgQTAQgAOBYhBEC9
cTjsQYEh8xVLMMFtGjUPrG7GBQJcuA6QAhsDBQsJCAcCBhUKCQgLAgQWAgMBAh4B
AheAAAoJEMFtGjUPrG7GtyEIAJdg8KQiEDFPwciKStEpIGfgU561ExrPgtolwfgL
5zXfudDofk1fj0Yss7z9OdcN5PZ+q9iWuytn9zOMHU9d+0bVYxW7QN+SHzxkiPdc
dNjrFWRcf6CNlBI6yFFfKe2/BmWl/IDSGmHfcZfoFsioHqG4eSN2xmYteAP21QQI
sI/zCRA0rh/fwhw2vu8LOacGJiLBaTKILWGPMvhm4ZHrcj7d3GwTbrb7v69ehOs+
R9IYyj4p0YiDWecgcTQM1I7JGBIkHVMF9WKMjYSycoim/x1CiSw88IXMX5maCj2w
5
-----BEGIN PGP PRIVATE KEY BLOCK-----
lQPGBFy4DpABCADH4G4mNU1EpuL7xfNF9Cy7rjyoGRAdIe5LVhwHRvQG9W8zT483
b1AsBB/K5YmIgpmjFOBQ1oqT2PY73aUNDOBMVSWmnc5QkPryf4OOEpcw/JrK1r/9
7kthCS5JXbGIjhXsfI79hLQO3jYa6vRlin33vWriXCzXawcUe9scyrAe20GEW2+g
cn43VGseNhsTT9Jv+M6rfzCSBP+1fo3cEYM0qDXgiteiHNIJne9XlbsZuLxp3IEE
3sPkwMBYGqmHfM6MiwfhvtkJEUWpymrinmuKg+rqdj9e1T4nC6nVV862v+RekNar
ozXX+C0xcCI/6oiTZM9qnLSYPrKBMreqMs7lABEBAAH+BwMCywYWui00qzHxwz5c
4ia+jz819Kw+BSkrnmdYCb4cgsbnmKIAw2lUOoon2bktqBLZE6b8/D6d//5vH6t9
dhTR889nnqznYMLxPplcFT7D47vORy3H+3+gt7ygi3iEXx9PDSNv9zNNsl8ZREvV
JXFksxtUoibeSm+D4vvRLbY3h4oHgYTXm2vNfyOYBibiPEJT47cv1JnZVWtOc4jF
iZHYsHvtKtO+qYjqeu1z8qtiyPgEBWKJCqGNnTT+5JSPejva91Y1kDZ1Vgbuvvm9
0/kCJw2DtenhXeIWEWNDbKP3Demh9IF/Js77ySX0qL3tqAbtW3Wm+lXvrSVEXPgG
t8XWCO4F6Lf6J7vZ/svM4R8VBrugmBU/KN+W79DADrKMbGTrxLa4Sgad0o3sR0E9
Q9f2X/4RLuwOEun7//IH8dZ2ox8i9vdGtpbty5CgCES9Snv40Y2zp5w04BrV0mYS
TbctBM8QO040qboHfyyRYAMAmzWO6kaQ5mAbB3ggBYExxNnVP51WhK4FNFSPEHDg
W/rX2wqP9UeO8XBqunutu8F5HaVxYtk8Ds4R/ikCI0uTTvnSgddUc/Tu/7AAwgjl
u9gVHj8WGSLvPOpCY/Jui7Id+v9EY9ePUq/ZE+rpEEoQk3jZTgvX1qgNywt2/jka
k07DScEDCT0aghNSR4x56tCzfI1OqH65omOY4VsbSxIHhoFZqZvt0hW+ORixbW6J
Mx35QQan+X1R5wXiO5zJ+BGP8sfvFxt/SGzLt5fDKlk34ZLdGLpsfNItVunbJh0K
WzWSy4EW4TnXms40XAJWZ+HcaOEN7x7naB2/5zuutcnUWCW8NFtUQfm1gRRwysIE
ZVhMP+DFnJQYfCWchDvSHYRxahcIinRatuuZTNygh0VEeEY8x5FTlooOu3QjkQAa
7Ufi25pPOLvatBdCb2JieSA8Ym9iQGZpdDIwOTMuZWR1PokBTgQTAQgAOBYhBEC9
cTjsQYEh8xVLMMFtGjUPrG7GBQJcuA6QAhsDBQsJCAcCBhUKCQgLAgQWAgMBAh4B
AheAAAoJEMFtGjUPrG7GtyEIAJdg8KQiEDFPwciKStEpIGfgU561ExrPgtolwfgL
5zXfudDofk1fj0Yss7z9OdcN5PZ+q9iWuytn9zOMHU9d+0bVYxW7QN+SHzxkiPdc
dNjrFWRcf6CNlBI6yFFfKe2/BmWl/IDSGmHfcZfoFsioHqG4eSN2xmYteAP21QQI
sI/zCRA0rh/fwhw2vu8LOacGJiLBaTKILWGPMvhm4ZHrcj7d3GwTbrb7v69ehOs+
R9IYyj4p0YiDWecgcTQM1I7JGBIkHVMF9WKMjYSycoim/x1CiSw88IXMX5maCj2w
5

RQzc2PpxI4ePa0OxSCyxLI9glTeCjswGKGe31k4AO4U+J1ydA8YEXLgOkAEIAK00
myChnYLpMCnBbjCYnUJhAmuYNpFAQGmRMwNeet1BuOGzFx+wPqKHDBLW+kGPeIRi
Qf4y+OFw3iPk0HUlW5uNGI7kXQ0aoCOk3HoYqLyX7G3d8anQmcKZgu9HUguKy/v8
WcWZeU4SfyvfU/igkhE4PT20+U42FRQN+ojSJbI9qI82qJ/pfq+rzLFge69OKGAZ
++/zxxjI/SVEDX+/4oEW5v3/n4BK+gIuiuGRfgM6fbw3prkgDGI6F8HVIsdkODVn
LmY7hWaxiA6b+1sXVJclbnmHGeo5KEMtc3AThza3rzqKSjOU1ei8Ne/EneBO9x7F
jFKWjWkedGsZYhRSsVkAEQEAAf4HAwKGIh+S6lRw3/GMJHETweUdnSve00laiA6D
kKSB0AM6SYlohTGe4KeSJ6Fle+M9/QyBWrOtekowEjs1e2S3OiDDEioKUHD45QdR
cA2aEnyqSff7ybL4Y///EHPSlKKxLRVcJcpnEFlMq/xmNFqAW7t4afFj6MS3fhXd
RVzWEcpiZm2iyxVvdZgVYeHnRTohtpQBIqh/gWGxAJShEoz/ruvjZjwW2B2tMPma
hGv33XTXtgX6jlzuNXidaeAo2jhJ+sQinUiCvVd01q0busL5AsePL8NXQTxXQFH1
2ffLHrrO8brb4bhZJEnAaT8aRpXENc0KPYVuyVI8xJvEvJuASdwWnJv/0jUM1dIH
J1L96w6ueblUy/fsnDoAHdstenrQt2tsfIE3yWpcFI8XRsI/yDUNbd1P2YV7POow
T4uKuVxemlXKK7GEBsJJII1TML/9MRI4RbXMqiaLAnjmH35KyEI05fgWAVorfSlA
rx13yXSAr+DUUmGgvUbQ6sOsZKRi6W8lv3f58zCAPPDj/0/1ZSq++QDWMZ7r3HQc
UjHvAr1xwlupj1dfS+FesQGpRAto7Rt+4yavFp/JeDpcJnqHluaGJv3UZJTL4Dom
GayeLNJjGv9DK8DKR+LVN5u5RwuOUAL/IWR1ujTzgyLk7neTd9+5GaDPWWeVas3I
xlWTKkmlp/ef4h4987Mfdc+CpTgznqA0ftb/eSwTCDfYut3KUfy9C/Uy2pph3jjs
OiPtfkKX+wjxP+X7r46wVPsHbxMoUyIIaD4995wx3vp5IcUCM6TQ6CizXOOWLtaK
5kXWaa8bq3vbTwFs6/SvUdHLZqq//cBWOL6+OdA5/R0lNeWtp9eIYIz3rf+e36Wc
j5ZB57AnG1UGpq8MizI+xqzgRDxXSyWpvFUxciBEUIeoELdI+xzt8r7V/46JATUE
GAEIACAWIQRAvXE47EGBIfMVSzDBbRo1D6xuxgUCXLgOkAIbDAAKCRDBbRo1D6xu
xmrSB/j1tncqn7kO/eLViwrikdLFpU8qccfPYjQj7bijj9VHJupgpWUjyY14RaaH
MRy2lByeQ35/1dqRboB3/8NLF5oUzZ3MgXoWNLR84bIFB/hEGnTGS6VdY1TimmN+
f3j4VFmLWdtKYikVrT7PUAC44y+NxFbLYoyQ2mSdWqKjXvvBMJA1XBTmDZ8DaH4h
if89/NdJY9Ii4GIUfxmnbm28mBcVbHTc/JrqVyZIvI8W/KYvzoOWlUcJExwdcZZ1
eX9seM933WjY53U0NzcpFZQxslP+9hC2xw76ywpm2f1duYkPQ1gzIKbJk3ln4/1d
2mAHPi5mI+jWWjLTgY2Q66YKob4=
=Dojk
6
myChnYLpMCnBbjCYnUJhAmuYNpFAQGmRMwNeet1BuOGzFx+wPqKHDBLW+kGPeIRi
Qf4y+OFw3iPk0HUlW5uNGI7kXQ0aoCOk3HoYqLyX7G3d8anQmcKZgu9HUguKy/v8
WcWZeU4SfyvfU/igkhE4PT20+U42FRQN+ojSJbI9qI82qJ/pfq+rzLFge69OKGAZ
++/zxxjI/SVEDX+/4oEW5v3/n4BK+gIuiuGRfgM6fbw3prkgDGI6F8HVIsdkODVn
LmY7hWaxiA6b+1sXVJclbnmHGeo5KEMtc3AThza3rzqKSjOU1ei8Ne/EneBO9x7F
jFKWjWkedGsZYhRSsVkAEQEAAf4HAwKGIh+S6lRw3/GMJHETweUdnSve00laiA6D
kKSB0AM6SYlohTGe4KeSJ6Fle+M9/QyBWrOtekowEjs1e2S3OiDDEioKUHD45QdR
cA2aEnyqSff7ybL4Y///EHPSlKKxLRVcJcpnEFlMq/xmNFqAW7t4afFj6MS3fhXd
RVzWEcpiZm2iyxVvdZgVYeHnRTohtpQBIqh/gWGxAJShEoz/ruvjZjwW2B2tMPma
hGv33XTXtgX6jlzuNXidaeAo2jhJ+sQinUiCvVd01q0busL5AsePL8NXQTxXQFH1
2ffLHrrO8brb4bhZJEnAaT8aRpXENc0KPYVuyVI8xJvEvJuASdwWnJv/0jUM1dIH
J1L96w6ueblUy/fsnDoAHdstenrQt2tsfIE3yWpcFI8XRsI/yDUNbd1P2YV7POow
T4uKuVxemlXKK7GEBsJJII1TML/9MRI4RbXMqiaLAnjmH35KyEI05fgWAVorfSlA
rx13yXSAr+DUUmGgvUbQ6sOsZKRi6W8lv3f58zCAPPDj/0/1ZSq++QDWMZ7r3HQc
UjHvAr1xwlupj1dfS+FesQGpRAto7Rt+4yavFp/JeDpcJnqHluaGJv3UZJTL4Dom
GayeLNJjGv9DK8DKR+LVN5u5RwuOUAL/IWR1ujTzgyLk7neTd9+5GaDPWWeVas3I
xlWTKkmlp/ef4h4987Mfdc+CpTgznqA0ftb/eSwTCDfYut3KUfy9C/Uy2pph3jjs
OiPtfkKX+wjxP+X7r46wVPsHbxMoUyIIaD4995wx3vp5IcUCM6TQ6CizXOOWLtaK
5kXWaa8bq3vbTwFs6/SvUdHLZqq//cBWOL6+OdA5/R0lNeWtp9eIYIz3rf+e36Wc
j5ZB57AnG1UGpq8MizI+xqzgRDxXSyWpvFUxciBEUIeoELdI+xzt8r7V/46JATUE
GAEIACAWIQRAvXE47EGBIfMVSzDBbRo1D6xuxgUCXLgOkAIbDAAKCRDBbRo1D6xu
xmrSB/j1tncqn7kO/eLViwrikdLFpU8qccfPYjQj7bijj9VHJupgpWUjyY14RaaH
MRy2lByeQ35/1dqRboB3/8NLF5oUzZ3MgXoWNLR84bIFB/hEGnTGS6VdY1TimmN+
f3j4VFmLWdtKYikVrT7PUAC44y+NxFbLYoyQ2mSdWqKjXvvBMJA1XBTmDZ8DaH4h
if89/NdJY9Ii4GIUfxmnbm28mBcVbHTc/JrqVyZIvI8W/KYvzoOWlUcJExwdcZZ1
eX9seM933WjY53U0NzcpFZQxslP+9hC2xw76ywpm2f1duYkPQ1gzIKbJk3ln4/1d
2mAHPi5mI+jWWjLTgY2Q66YKob4=
=Dojk
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
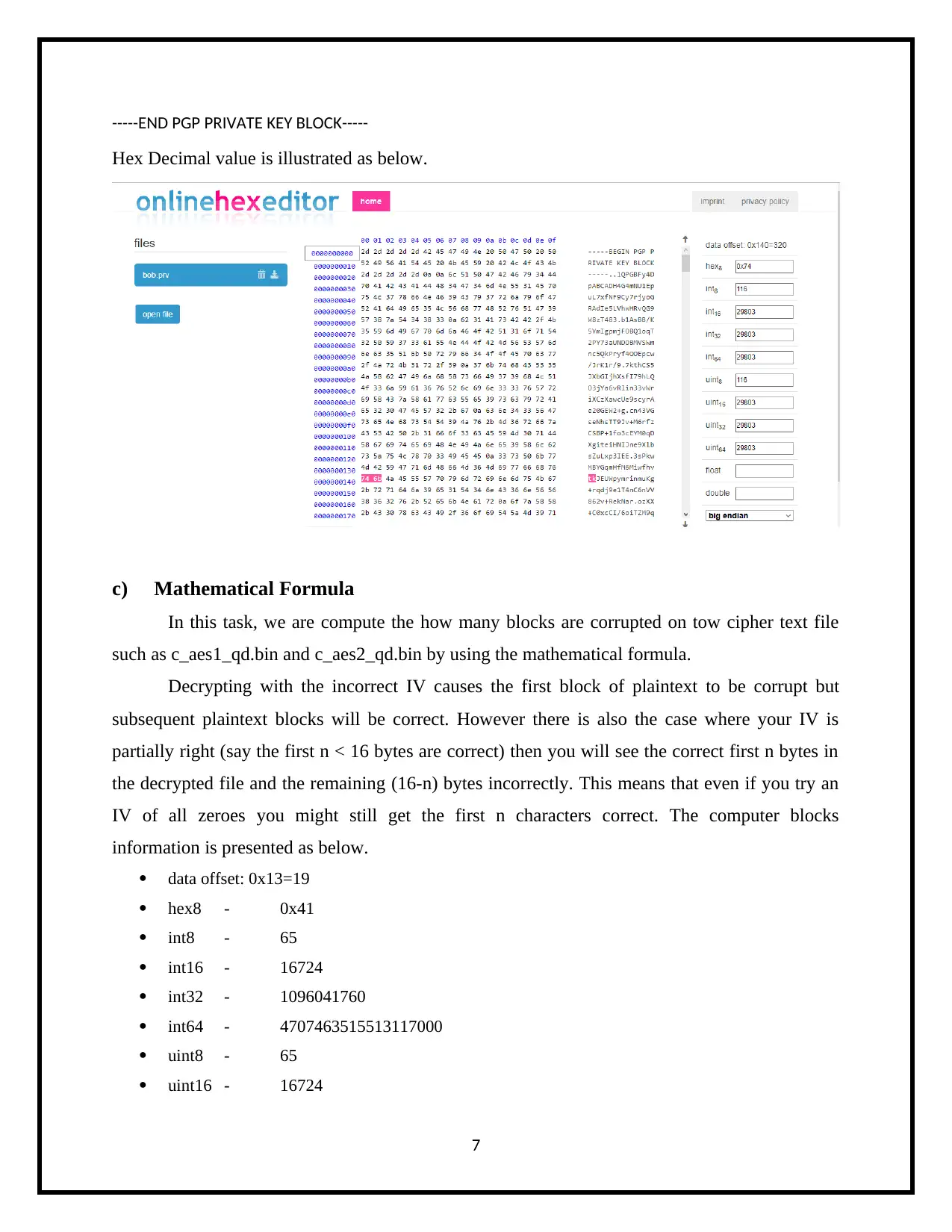
-----END PGP PRIVATE KEY BLOCK-----
Hex Decimal value is illustrated as below.
c) Mathematical Formula
In this task, we are compute the how many blocks are corrupted on tow cipher text file
such as c_aes1_qd.bin and c_aes2_qd.bin by using the mathematical formula.
Decrypting with the incorrect IV causes the first block of plaintext to be corrupt but
subsequent plaintext blocks will be correct. However there is also the case where your IV is
partially right (say the first n < 16 bytes are correct) then you will see the correct first n bytes in
the decrypted file and the remaining (16-n) bytes incorrectly. This means that even if you try an
IV of all zeroes you might still get the first n characters correct. The computer blocks
information is presented as below.
data offset: 0x13=19
hex8 - 0x41
int8 - 65
int16 - 16724
int32 - 1096041760
int64 - 4707463515513117000
uint8 - 65
uint16 - 16724
7
Hex Decimal value is illustrated as below.
c) Mathematical Formula
In this task, we are compute the how many blocks are corrupted on tow cipher text file
such as c_aes1_qd.bin and c_aes2_qd.bin by using the mathematical formula.
Decrypting with the incorrect IV causes the first block of plaintext to be corrupt but
subsequent plaintext blocks will be correct. However there is also the case where your IV is
partially right (say the first n < 16 bytes are correct) then you will see the correct first n bytes in
the decrypted file and the remaining (16-n) bytes incorrectly. This means that even if you try an
IV of all zeroes you might still get the first n characters correct. The computer blocks
information is presented as below.
data offset: 0x13=19
hex8 - 0x41
int8 - 65
int16 - 16724
int32 - 1096041760
int64 - 4707463515513117000
uint8 - 65
uint16 - 16724
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

uint32 - 1096041760
uint64 - 4707463515513117000
d) Vulnerability
In this task, we are compute the plain text on two cipher text file such as c_aes1_qd.bin
and c_aes2_qd.bin by using the converter in online which is illustrated as below.
Plain Text is shown below.
c_aes1_qd
`....I...% .GA$
..AH..-....?....
.a....E......p..
c_aes1_qd
.n2`.GC8..e#..a.
G..2af....]...!.
....."...:}..Y..
8
uint64 - 4707463515513117000
d) Vulnerability
In this task, we are compute the plain text on two cipher text file such as c_aes1_qd.bin
and c_aes2_qd.bin by using the converter in online which is illustrated as below.
Plain Text is shown below.
c_aes1_qd
`....I...% .GA$
..AH..-....?....
.a....E......p..
c_aes1_qd
.n2`.GC8..e#..a.
G..2af....]...!.
....."...:}..Y..
8
1 out of 8
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
