IT Networking Design & Proposal for MonkeyNet Canberra Hospital-CIT
VerifiedAdded on 2023/06/16
|11
|1524
|110
Report
AI Summary
This report presents an IT networking design proposal for MonkeyNet Canberra Hospital, focusing on upgrading the current network infrastructure to connect different floors and improve network security. The proposal addresses the need to reduce network load, enhance security, and efficiently allocate bandwidth for remote clinics. It identifies drawbacks in the current infrastructure and provides solutions to minimize network downtime and increase efficiency, including the implementation of wireless routers with different subnets. The design includes logical and physical network diagrams, aligning with the hospital's business requirements and goals. Cost analysis, project scheduling, and resource allocation are considered for budget planning and project advancement. A layered approach with VLANs and access control lists is used to segment the network and secure access, aiming to meet business requirements, improve network performance, and ensure scalability while staying within budget. The design incorporates fault tolerance and server security measures, utilizing an IP subnet plan and firewalls to enhance overall network security and manageability. The document is contributed by a student and available on Desklib.

Running head: IT NETWORKING DESIGNING
IT Networking and Designing: Proposal for MonkeyNet
Canberra Hospital
Name of the Student
Name of the University
Author’s Note
IT Networking and Designing: Proposal for MonkeyNet
Canberra Hospital
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT NETWORKING DESIGNING
Executive Summary
The report is prepared for MonkeyNet Canberra Hospital for the up gradation of the current
network infrastructure and connect with the different floors of the building. The main
requirement of the organization is to reduce the load on the current network and improve the
security of the network framework. The remote clinic connected with the network and efficient
bandwidth is allocated for reducing congestion in the network channel. The drawback of the
current network infrastructure is found and a solution is created for reducing the network
downtime and increasing the efficiency of the solution. Wireless routers are also installed with
different subnet for increasing the flexibility of the network. Logical and physical network
diagram is created for the development of the network solution. The requirement of the customer
is analyzed for the development of the network design and aligning the business process for the
deployment of the networking device in the organization. The cost of the devices and calculated
by creating a project schedule and assigning resources for the development of the network
infrastructure. The cost of the project should be calculated for preparation of a budget plan and a
proper planning is made for the advancement of the project. The network design is created
according to the project plan and the network design is created into two different parts such as
logical design and physical design for segmenting the network and making the requirement clear.
A network development model is selected for the development of the network infrastructure and
flexibility and scalability of the network is considered for the development of the network. A
layer 3 switch is used for the network and different VLAN are created for the different
departments for reducing congestion in the network. The routers are configured with access
control list for denying access of the unauthorized users and securing the network. The main aim
of the network administrator is to reduce the network downtime and develop the network
infrastructure within the estimated project budget. The project implementation plan is created
IT NETWORKING DESIGNING
Executive Summary
The report is prepared for MonkeyNet Canberra Hospital for the up gradation of the current
network infrastructure and connect with the different floors of the building. The main
requirement of the organization is to reduce the load on the current network and improve the
security of the network framework. The remote clinic connected with the network and efficient
bandwidth is allocated for reducing congestion in the network channel. The drawback of the
current network infrastructure is found and a solution is created for reducing the network
downtime and increasing the efficiency of the solution. Wireless routers are also installed with
different subnet for increasing the flexibility of the network. Logical and physical network
diagram is created for the development of the network solution. The requirement of the customer
is analyzed for the development of the network design and aligning the business process for the
deployment of the networking device in the organization. The cost of the devices and calculated
by creating a project schedule and assigning resources for the development of the network
infrastructure. The cost of the project should be calculated for preparation of a budget plan and a
proper planning is made for the advancement of the project. The network design is created
according to the project plan and the network design is created into two different parts such as
logical design and physical design for segmenting the network and making the requirement clear.
A network development model is selected for the development of the network infrastructure and
flexibility and scalability of the network is considered for the development of the network. A
layer 3 switch is used for the network and different VLAN are created for the different
departments for reducing congestion in the network. The routers are configured with access
control list for denying access of the unauthorized users and securing the network. The main aim
of the network administrator is to reduce the network downtime and develop the network
infrastructure within the estimated project budget. The project implementation plan is created

2
IT NETWORKING DESIGNING
and project scope is developed for allowing the network to expand according to the growth of the
organization. The network should be able to tolerate fault and the servers installed in the network
should be installed in a separate zone for blocking the physical access of the servers. The
network design meets all the business requirement and goals of the organization for increasing
the efficiency of the network. An IP subnet plan is created for the development of a high level
security design and proper routing and switching protocol is used for communicating with the
remote clinics connected with the network. For increasing the security of the network solution
firewall is used and the unwanted traffic are blocked. A class B IP address is used and proper
subnet is used for the allowing the host to be connected in the network. Internal NAT is used and
wireless access point is installed in different location of the campus for allowing the authorized
users to connect their wireless device with the organizational network.
IT NETWORKING DESIGNING
and project scope is developed for allowing the network to expand according to the growth of the
organization. The network should be able to tolerate fault and the servers installed in the network
should be installed in a separate zone for blocking the physical access of the servers. The
network design meets all the business requirement and goals of the organization for increasing
the efficiency of the network. An IP subnet plan is created for the development of a high level
security design and proper routing and switching protocol is used for communicating with the
remote clinics connected with the network. For increasing the security of the network solution
firewall is used and the unwanted traffic are blocked. A class B IP address is used and proper
subnet is used for the allowing the host to be connected in the network. Internal NAT is used and
wireless access point is installed in different location of the campus for allowing the authorized
users to connect their wireless device with the organizational network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT NETWORKING DESIGNING
Table of Contents
Step 1: MonkeyNet Canberra Hospital Requirements.....................................................................4
Advantages of hierarchical model...............................................................................................4
Business Requirements and Goals:..............................................................................................4
Technical Requirements and Goals:............................................................................................4
Logical Design:............................................................................................................................5
Physical Design:..........................................................................................................................6
Step 4: High level security design...................................................................................................6
Key business security requirement..............................................................................................6
Security design for the remote clinics.........................................................................................6
Suitable IP subletting for Intranet, Internet, DMZ and VPNs.....................................................7
Design and routing and switching protocols...............................................................................9
Bibliography..................................................................................................................................10
IT NETWORKING DESIGNING
Table of Contents
Step 1: MonkeyNet Canberra Hospital Requirements.....................................................................4
Advantages of hierarchical model...............................................................................................4
Business Requirements and Goals:..............................................................................................4
Technical Requirements and Goals:............................................................................................4
Logical Design:............................................................................................................................5
Physical Design:..........................................................................................................................6
Step 4: High level security design...................................................................................................6
Key business security requirement..............................................................................................6
Security design for the remote clinics.........................................................................................6
Suitable IP subletting for Intranet, Internet, DMZ and VPNs.....................................................7
Design and routing and switching protocols...............................................................................9
Bibliography..................................................................................................................................10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT NETWORKING DESIGNING
Step 1: MonkeyNet Canberra Hospital Requirements
Advantages of hierarchical model
Flexibility and scalability
Cost savings
Modularity
Easily modified
Allows for network growth
Fault isolation
Facilitates summarization
Business Requirements and Goals:
Expanding clinic and another emergency room
Enlarge main campus
improve productivity
upgrade time frame 6-12 months
Technical Requirements and Goals:
Deploy cutting-edge technology
Improve Network downtime and slowness for patient care
Network manageability.
Current network uses inexpensive switches from several vendor, purchase over time and
comply with various standards.
Current Switches are not SNMP-manageable, upgrades required to SNMP-manageable
switches.
IT NETWORKING DESIGNING
Step 1: MonkeyNet Canberra Hospital Requirements
Advantages of hierarchical model
Flexibility and scalability
Cost savings
Modularity
Easily modified
Allows for network growth
Fault isolation
Facilitates summarization
Business Requirements and Goals:
Expanding clinic and another emergency room
Enlarge main campus
improve productivity
upgrade time frame 6-12 months
Technical Requirements and Goals:
Deploy cutting-edge technology
Improve Network downtime and slowness for patient care
Network manageability.
Current network uses inexpensive switches from several vendor, purchase over time and
comply with various standards.
Current Switches are not SNMP-manageable, upgrades required to SNMP-manageable
switches.
5
IT NETWORKING DESIGNING
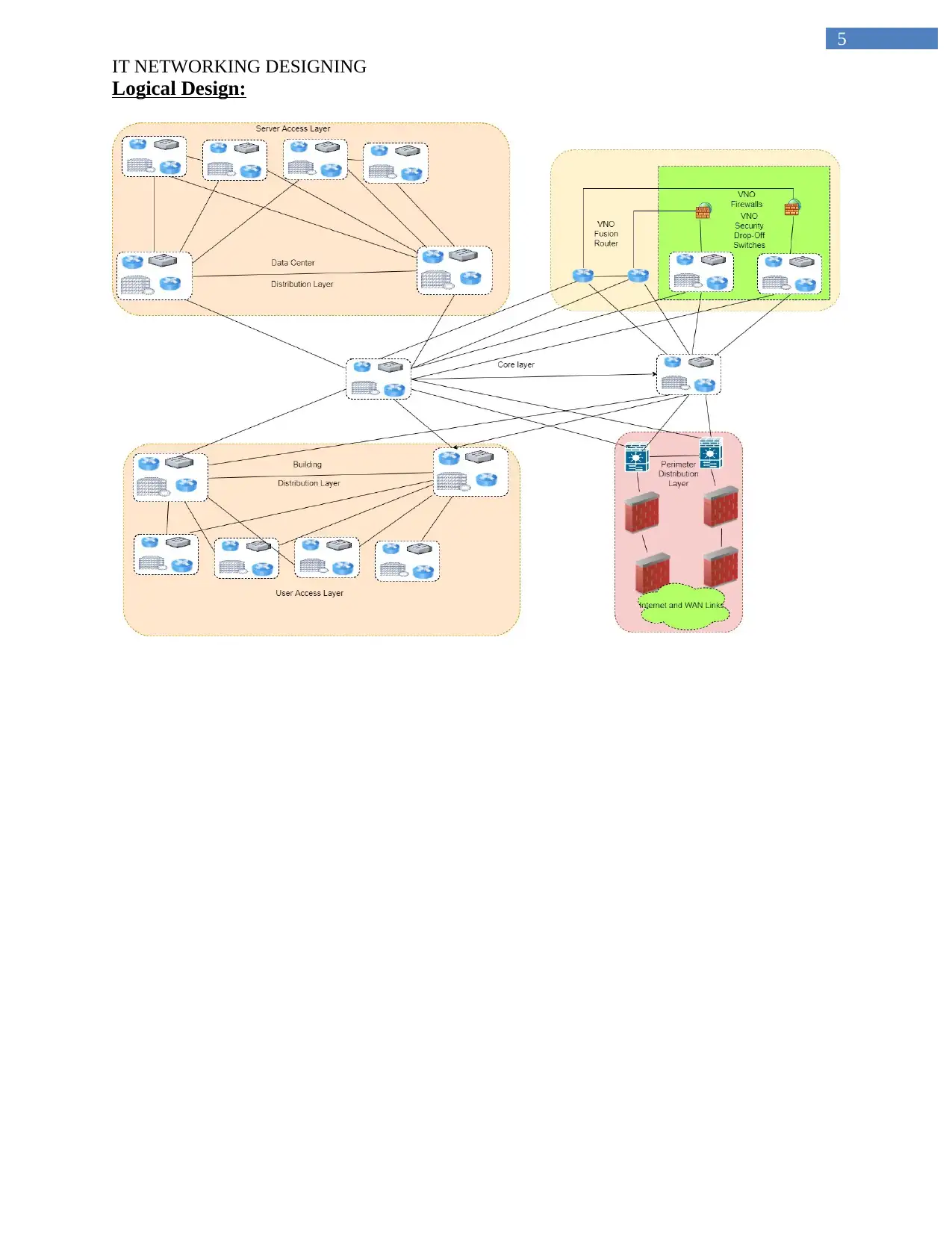
Logical Design:
IT NETWORKING DESIGNING
Logical Design:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT NETWORKING DESIGNING
Physical Design:
Step 4: High level security design
Key business security requirement
The main requirement for designing the network is to improve the security if the network
and the risk associated with the development of the network should be eliminated for increasing
the efficiency of the network solution. The unauthorized users should not be able to access the
devices installed in the core part of the network. The routers and servers should be installed in
the DMZ zone for restriction of the physical access of the device sand eliminate the risk of data
loss.
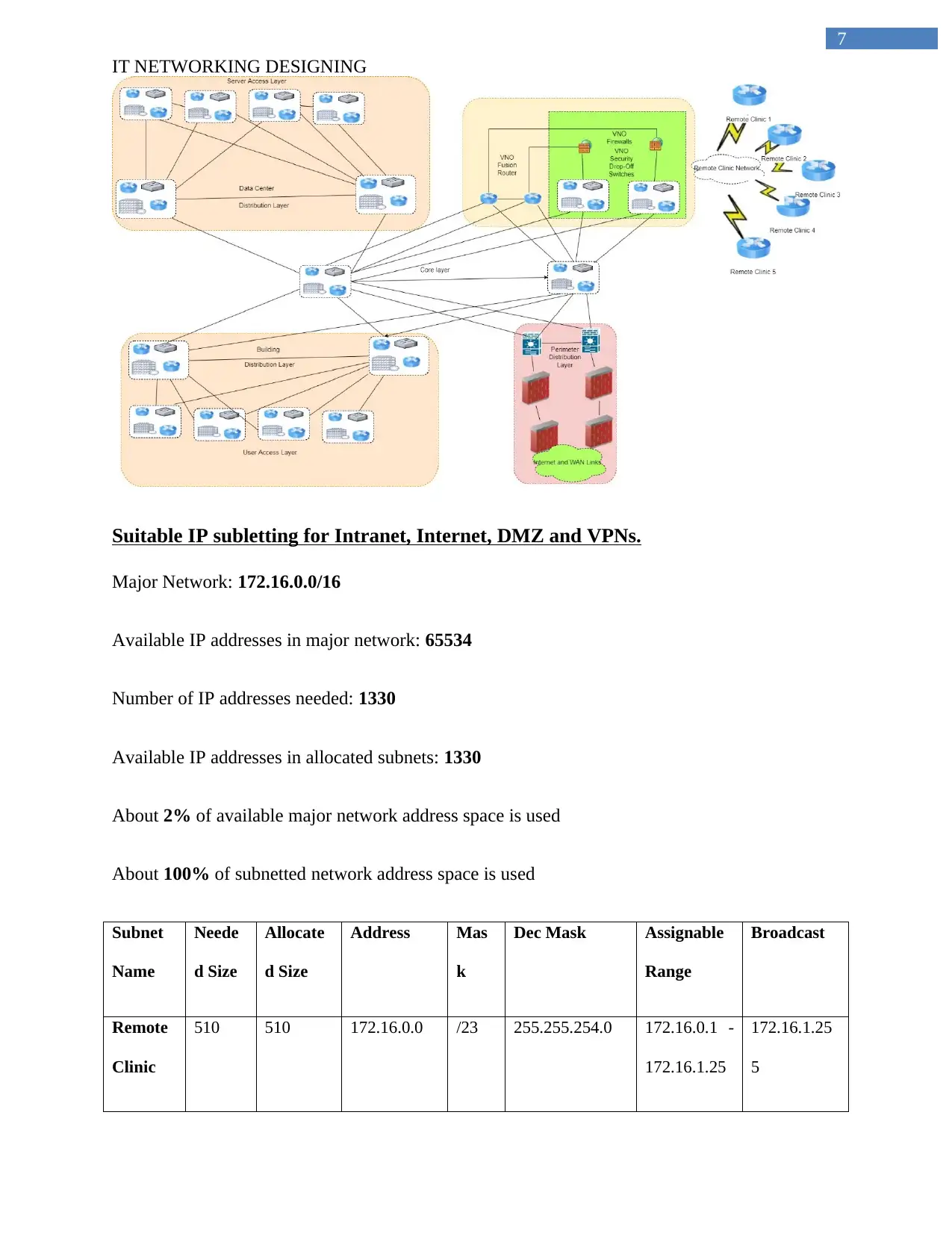
Security design for the remote clinics
A security design is created for connecting the remote clinic with the organizational
network and demonstrated below.
IT NETWORKING DESIGNING
Physical Design:
Step 4: High level security design
Key business security requirement
The main requirement for designing the network is to improve the security if the network
and the risk associated with the development of the network should be eliminated for increasing
the efficiency of the network solution. The unauthorized users should not be able to access the
devices installed in the core part of the network. The routers and servers should be installed in
the DMZ zone for restriction of the physical access of the device sand eliminate the risk of data
loss.
Security design for the remote clinics
A security design is created for connecting the remote clinic with the organizational
network and demonstrated below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT NETWORKING DESIGNING
Suitable IP subletting for Intranet, Internet, DMZ and VPNs.
Major Network: 172.16.0.0/16
Available IP addresses in major network: 65534
Number of IP addresses needed: 1330
Available IP addresses in allocated subnets: 1330
About 2% of available major network address space is used
About 100% of subnetted network address space is used
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Remote
Clinic
510 510 172.16.0.0 /23 255.255.254.0 172.16.0.1 -
172.16.1.25
172.16.1.25
5
IT NETWORKING DESIGNING
Suitable IP subletting for Intranet, Internet, DMZ and VPNs.
Major Network: 172.16.0.0/16
Available IP addresses in major network: 65534
Number of IP addresses needed: 1330
Available IP addresses in allocated subnets: 1330
About 2% of available major network address space is used
About 100% of subnetted network address space is used
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Remote
Clinic
510 510 172.16.0.0 /23 255.255.254.0 172.16.0.1 -
172.16.1.25
172.16.1.25
5
8
IT NETWORKING DESIGNING
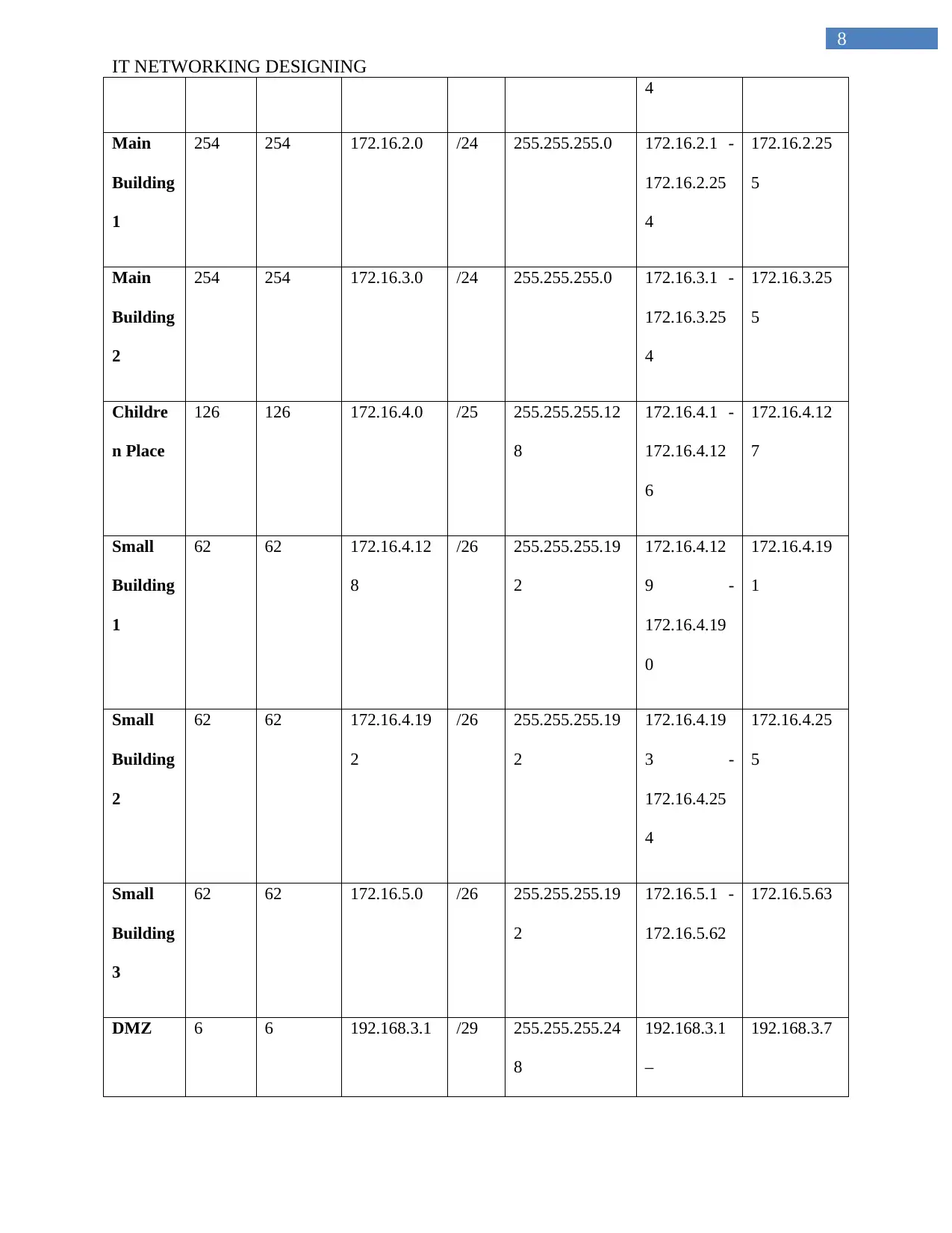
4
Main
Building
1
254 254 172.16.2.0 /24 255.255.255.0 172.16.2.1 -
172.16.2.25
4
172.16.2.25
5
Main
Building
2
254 254 172.16.3.0 /24 255.255.255.0 172.16.3.1 -
172.16.3.25
4
172.16.3.25
5
Childre
n Place
126 126 172.16.4.0 /25 255.255.255.12
8
172.16.4.1 -
172.16.4.12
6
172.16.4.12
7
Small
Building
1
62 62 172.16.4.12
8
/26 255.255.255.19
2
172.16.4.12
9 -
172.16.4.19
0
172.16.4.19
1
Small
Building
2
62 62 172.16.4.19
2
/26 255.255.255.19
2
172.16.4.19
3 -
172.16.4.25
4
172.16.4.25
5
Small
Building
3
62 62 172.16.5.0 /26 255.255.255.19
2
172.16.5.1 -
172.16.5.62
172.16.5.63
DMZ 6 6 192.168.3.1 /29 255.255.255.24
8
192.168.3.1
–
192.168.3.7
IT NETWORKING DESIGNING
4
Main
Building
1
254 254 172.16.2.0 /24 255.255.255.0 172.16.2.1 -
172.16.2.25
4
172.16.2.25
5
Main
Building
2
254 254 172.16.3.0 /24 255.255.255.0 172.16.3.1 -
172.16.3.25
4
172.16.3.25
5
Childre
n Place
126 126 172.16.4.0 /25 255.255.255.12
8
172.16.4.1 -
172.16.4.12
6
172.16.4.12
7
Small
Building
1
62 62 172.16.4.12
8
/26 255.255.255.19
2
172.16.4.12
9 -
172.16.4.19
0
172.16.4.19
1
Small
Building
2
62 62 172.16.4.19
2
/26 255.255.255.19
2
172.16.4.19
3 -
172.16.4.25
4
172.16.4.25
5
Small
Building
3
62 62 172.16.5.0 /26 255.255.255.19
2
172.16.5.1 -
172.16.5.62
172.16.5.63
DMZ 6 6 192.168.3.1 /29 255.255.255.24
8
192.168.3.1
–
192.168.3.7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT NETWORKING DESIGNING
192.168.3.6
Internet - - 151.150.2.0 /24 255.255.255.0 - -
Design and routing and switching protocols
For the development of the network design the application of proper network routing and
switching protocol is important. The router should be configured with proper IP addressing
scheme following the addressing plan. The interface of the router should be assigned with the IP
address and the subnet for connecting with the network device installed in the network (Zhang et
al. 2014). The routers should be configured with IP routing protocol for communicating with the
different departments and it should also be configured with ACL for blocking the unauthorized
users from accessing the core components.
The switch should be configured with spanning tree and VLAN for allocating different IP
address for each of the VLAN created. Each of the buildings are assigned with different VLAN
and layer 3 switch is used for the connection of the different departments (Horst and Miller
2013). The device used in the network should be password protected such that unauthorized user
does not have access of the device for intruding into the organizational network.
IT NETWORKING DESIGNING
192.168.3.6
Internet - - 151.150.2.0 /24 255.255.255.0 - -
Design and routing and switching protocols
For the development of the network design the application of proper network routing and
switching protocol is important. The router should be configured with proper IP addressing
scheme following the addressing plan. The interface of the router should be assigned with the IP
address and the subnet for connecting with the network device installed in the network (Zhang et
al. 2014). The routers should be configured with IP routing protocol for communicating with the
different departments and it should also be configured with ACL for blocking the unauthorized
users from accessing the core components.
The switch should be configured with spanning tree and VLAN for allocating different IP
address for each of the VLAN created. Each of the buildings are assigned with different VLAN
and layer 3 switch is used for the connection of the different departments (Horst and Miller
2013). The device used in the network should be password protected such that unauthorized user
does not have access of the device for intruding into the organizational network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT NETWORKING DESIGNING
Bibliography
Conti, M. and Giordano, S., 2014. Mobile ad hoc networking: milestones, challenges, and new
research directions. IEEE Communications Magazine, 52(1), pp.85-96.
Grassi, G., Pesavento, D., Pau, G., Vuyyuru, R., Wakikawa, R. and Zhang, L., 2014, April.
VANET via named data networking. In Computer Communications Workshops (INFOCOM
WKSHPS), 2014 IEEE Conference on (pp. 410-415). IEEE.
Horst, H.A. and Miller, D. eds., 2013. Digital anthropology. A&C Black.
Rakotoarivelo, T., Jourjon, G. and Ott, M., 2014. Designing and orchestrating reproducible
experiments on federated networking testbeds. Computer Networks, 63, pp.173-187.
Rennie, F. and Morrison, T., 2013. E-learning and social networking handbook: Resources for
higher education. Routledge.
Zhang, Z., Long, K., Wang, J. and Dressler, F., 2014. On swarm intelligence inspired self-
organized networking: its bionic mechanisms, designing principles and optimization approaches.
IEEE Communications Surveys & Tutorials, 16(1), pp.513-537.
IT NETWORKING DESIGNING
Bibliography
Conti, M. and Giordano, S., 2014. Mobile ad hoc networking: milestones, challenges, and new
research directions. IEEE Communications Magazine, 52(1), pp.85-96.
Grassi, G., Pesavento, D., Pau, G., Vuyyuru, R., Wakikawa, R. and Zhang, L., 2014, April.
VANET via named data networking. In Computer Communications Workshops (INFOCOM
WKSHPS), 2014 IEEE Conference on (pp. 410-415). IEEE.
Horst, H.A. and Miller, D. eds., 2013. Digital anthropology. A&C Black.
Rakotoarivelo, T., Jourjon, G. and Ott, M., 2014. Designing and orchestrating reproducible
experiments on federated networking testbeds. Computer Networks, 63, pp.173-187.
Rennie, F. and Morrison, T., 2013. E-learning and social networking handbook: Resources for
higher education. Routledge.
Zhang, Z., Long, K., Wang, J. and Dressler, F., 2014. On swarm intelligence inspired self-
organized networking: its bionic mechanisms, designing principles and optimization approaches.
IEEE Communications Surveys & Tutorials, 16(1), pp.513-537.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




